A Blockchain-Driven Cyber-Systemic Approach to Hybrid Reality
Abstract
1. Introduction
1.1. HyR Definition, Examples, and Issues
- Human actors, workers, and organizations do not always accept being controlled by sensors and monitors;
- In particular, small and medium enterprises have to overcome many cost, technological, and procedural barriers to deal with increased digitization and sustainability requirements from regulations and laws;
- Some of the information has to remain hidden between the participants in the supply chain, although continuous improvements require technological upgrades and global optimizations across all the participants;
- A chain of trust has to be created in order to address the Farm-to-Fork sustainability, which involves automation, technologies, and humans at the same time.
1.2. Research Question and Proposed Approach
Is it possible to establish a comprehensive cyber-systemic methodology that makes HyR a controllable and sustainable phenomenon?
1.3. Nature and Plan of the Study
- The first step is a thorough operational definition of an HyR model that crisply situates the area of intervention of the HyR (Section 3.1) and related formal tools to enable algorithmic processes in HyR (Section 3.2).
- The second step is the positioning of the HyR problem under the perspective of Ross Ashby’s Law of Requisite Variety and cybernetics (Section 3.3).
- The final step is to use the former methods to define a systematic workflow (Section 4.1), which is a container that integrates the methodological components based on SD (Section 4.2), the design of HyR regulators (Section 4.3), and the introduction of the BC framework possibilities (Section 4.4). As shown in the following, SD methods will place a decisive role in BC-related technologies when it comes to the dynamics of control in the HyR problem by means of tailored systems engineering processes.
2. Background, Context, and Motivation
2.1. Challenges in Human–Machine Interaction
2.2. Cybernetics in Sustainable Systems Design
2.3. Holonic Agents in HyR
2.4. A Role for Blockchain Technologies in Industrial HyR Cases
2.5. Purpose and Relevance
3. Methods
3.1. Operational Definition of Scope of Hybrid Reality
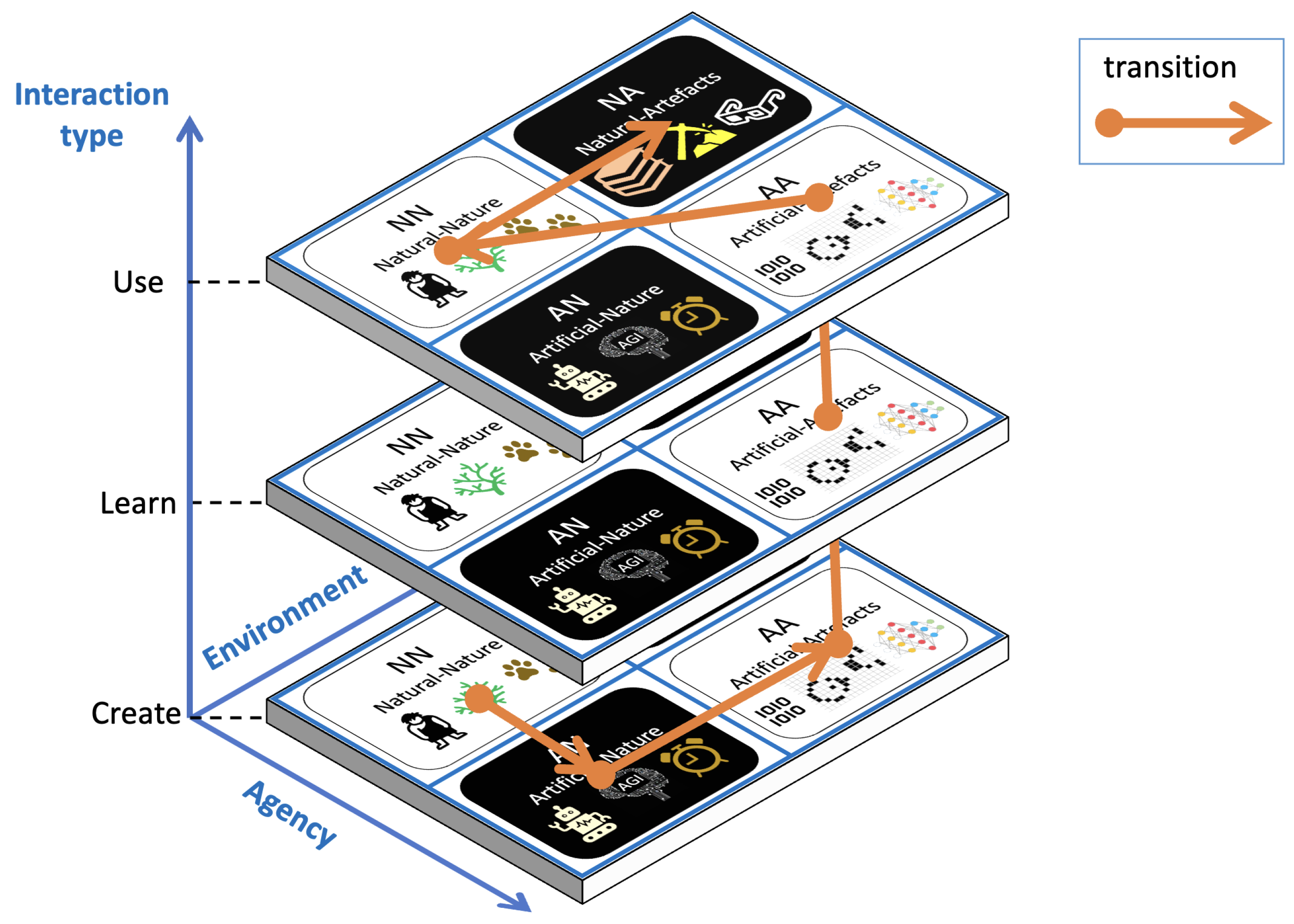
3.1.1. Definition of Agency and Environment
3.1.2. The Agency–Environment Matrix
- Create—The action of creating or changing the structure and configuration of some kind of environment by the agency.
- Learn—All the actions that pertain to observing, sensing, perceiving, and learning that the agency performs in the interested environment, mostly to gather and process information, are collected in this category.
- Use—The agency at some points performs actions that exploit the structure, the substance, and the essence of the environment. This interaction is the “doing” beyond observing.
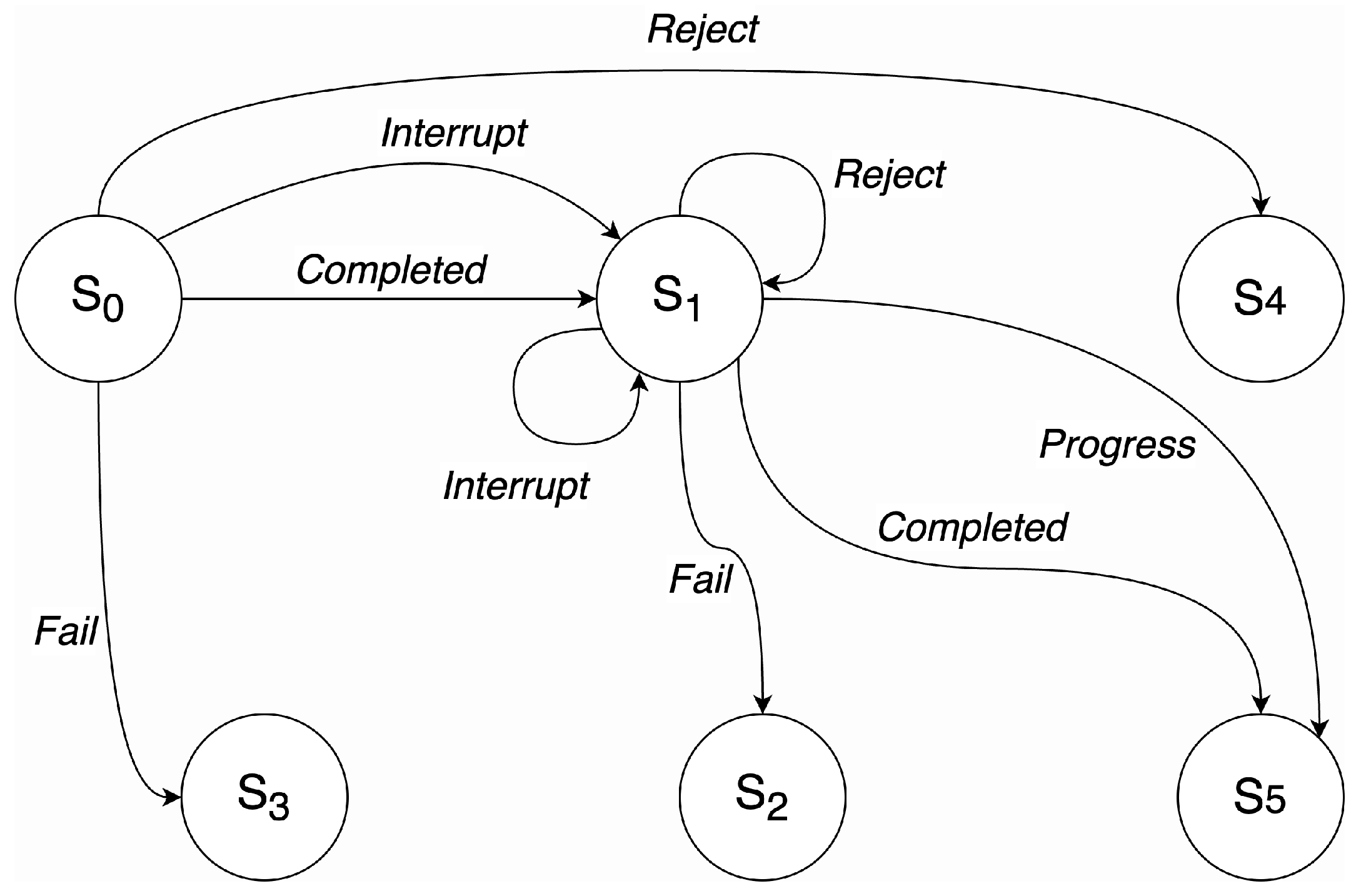
3.2. Formal Tools for HyR
- Completed—The event that is triggered by the completion of an interaction in a certain state . It means that the purpose of the interaction between the agent and the environment is fulfilled and it makes no sense to continue in the same state.
- Progress—This is the event that is triggered when the agent does not see an opportunity to continue with the same interaction because other opportunities to change the current state are found; the change to another state occurs before the interaction in that state is completed.
- Interrupt—The agent’s interaction is interrupted by some external and unforeseen conditions. A switch of the state is needed to try other routes.
- Fail—The agent at some point does not find a possibility to complete the interaction in the current state and is forced to switch.
- Reject—In this case, the agent sees no opportunities or rewards in continuing with the interaction. A state switch is made to try to land into a better situation.
3.3. The Cybernetics of HyR
4. Resulting Methodology
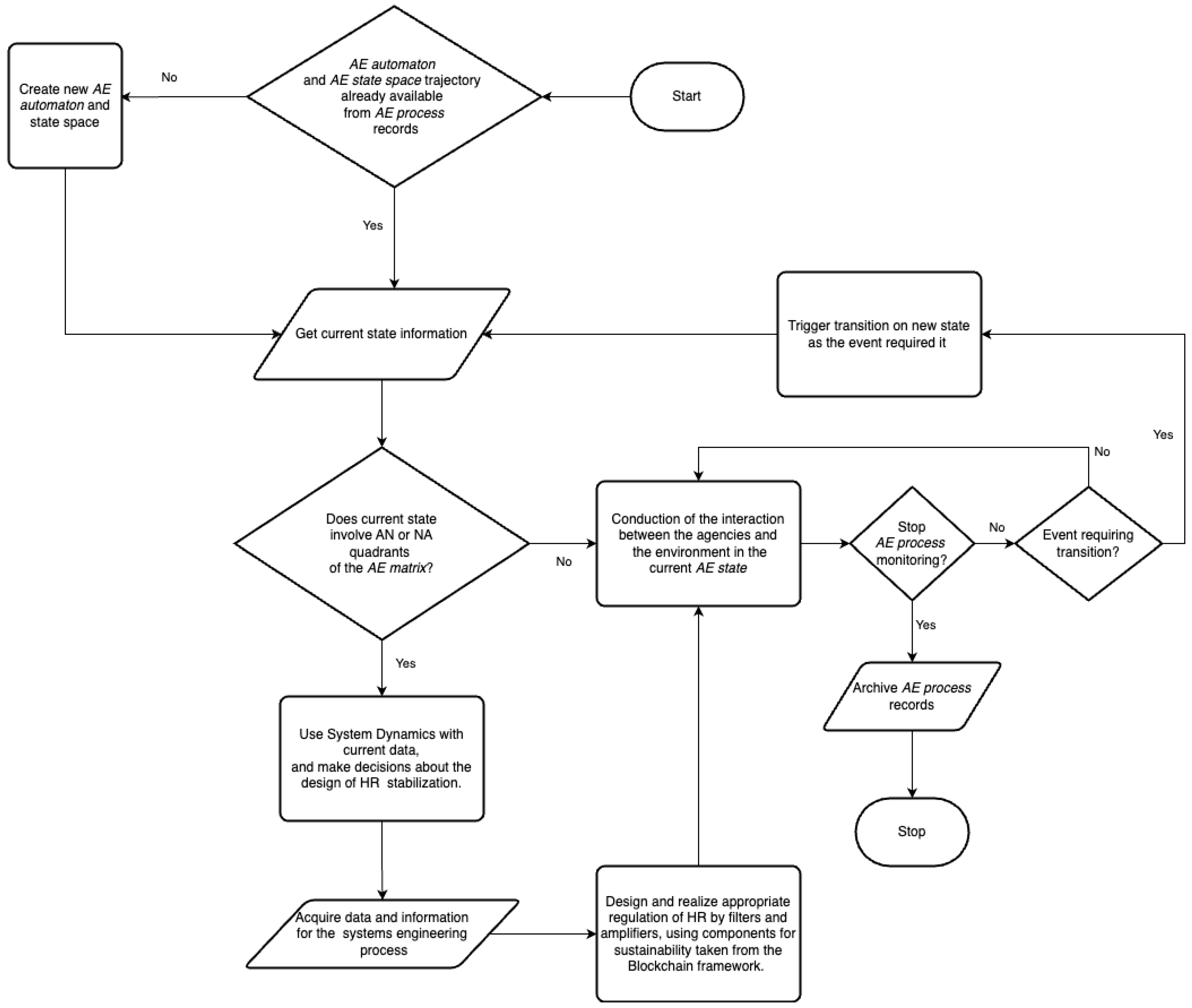
4.1. Definition of the AE Workflow
4.2. System Dynamics of HyR
4.3. Regulation of HyR Through Law of Requisite Variety
4.4. Role of the Blockchain Framework
5. Seven Steps of the Methodology for a Use Case
5.1. An HyR Scenario in Supply Chains
5.2. Envisioned Steps
5.2.1. Step 1: HyR Process Modeling
5.2.2. Step 2: AE Workflow Execution
5.2.3. Step 3: Cybernetics of HyR
5.2.4. Step 4: System Dynamics
5.2.5. Step 5: Realization of the G and F Systems
5.2.6. Step 6: Choice of System Components
5.2.7. Step 7: Holonic Integration and Recursion
6. Discussion, Related Work, and Applications
6.1. Sustainable Cybernetics
6.2. A Focus on Ethics and Societal Implications
6.3. Challenges to the Applicability of the Cybersystemic Security Kit
6.4. A Unifying Layer for Methodological Pluralism
7. Conclusions
- Definition adoption. Adopt the definitions provided for Hybrid Reality in terms of the Agency–Environment state space. These definitions must be mapped onto the process under study. The process is viewed as a sequence of interactions between agencies and environments. The collection of these interactions defines the state space, and trajectories within this space form a trace that informs the workflow model of the Agency–Environment system.
- Workflow execution. Execute the workflow derived from the mapped Agency–Environment interactions. This operational phase sets in motion subsequent methodological actions at pre-defined points.
- Application of Ross Ashby’s law. Apply Ross Ashby’s law of requisite variety to interpret specific Agent–Environment interactions as cybernetic causal loops, establishing a unified framework for analysis.
- System Dynamics modeling. Once the cybernetic interaction is defined, apply System Dynamics methods—such as Causal Loop Diagrams—to model the behavior of the system. Other tools like Stock and Flow Diagrams may also be employed depending on the complexity of the scenario.
- Design of control elements. Use model-based systems engineering techniques to design the amplifiers and filters necessary to bring the Hybrid Reality cybernetic loop to equilibrium. This phase focuses on engineering the mechanisms required to manage system variety.
- Technology-agency integration. Align the designed solutions with an appropriate mix of technologies and natural agencies. This step includes instantiating components from the Cybersistemic Security Kit—i.e., the available Blockchain technologies—to ensure secure and effective system implementation.
- Recursive holonic design. Introduce holonic paradigms to recursively apply the methodology at deeper levels of granularity, if needed. At each level, a new Agency–Environment process can be defined and analyzed in the same structured way.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AA | Artificial–Artifacts |
| ABM | agent-based modeling |
| AE | Agency–Environment |
| AI | artificial intelligence |
| AN | Artificial–Nature |
| BC | Blockchain |
| BPMN | Business Process Model and Notation |
| CLD | causal loop diagram |
| DCS | distributed control system |
| DFA | deterministic finite automaton |
| EU | European Union |
| GDPR | General Data Protection Regulation |
| FT | Fungible Token |
| GHG | greenhouse gases |
| HCA | holonic control architectures |
| HyR | Hybrid Reality |
| ICT | information and communication technologies |
| IoT | Internet of things |
| LLM | large language model |
| MBSE | model-based systems engineering |
| NA | Natural–Artifacts |
| NFA | non-deterministic finite automaton |
| NFT | Non-Fungible Token |
| NN | Natural–Nature |
| SBT | Soulbound Token |
| SD | System Dynamics |
| SDG | Sustainable Development Goal |
| SDS | Smart Data System |
| SFD | Stock and flow diagram |
| SSI | Self-sovereign identity |
| UN | United Nations |
| VSM | Viable System Model |
| ZKP | zero-knowledge proof |
| zk-SNARK | zero-knowledge succinct non-interactive arguments of knowledge |
| zk-STARK | zero-knowledge scalable transparent arguments of knowledge |
| XAI | explainable artificial intelligence |
Appendix A. More on Automata
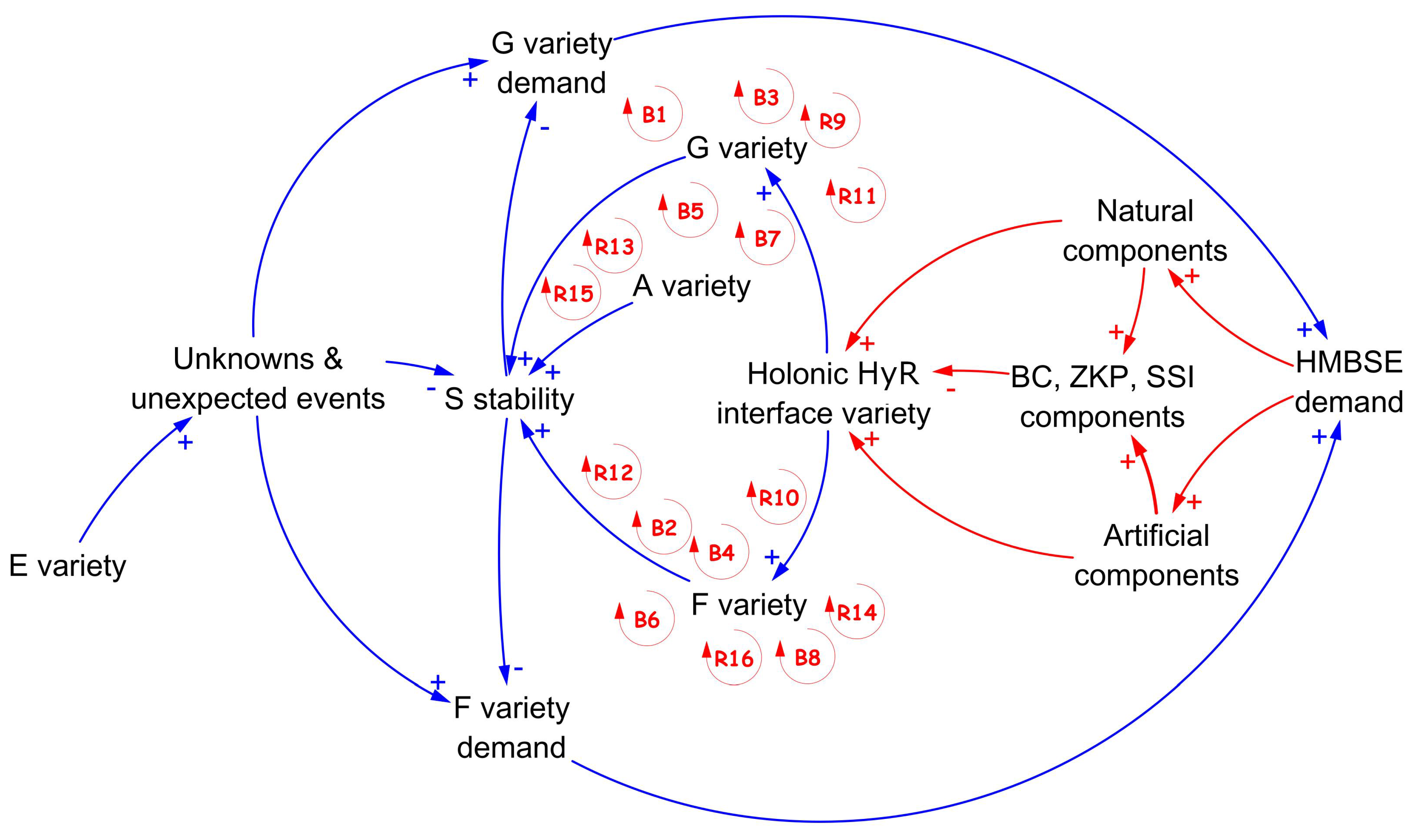
Appendix B. Details of the CLD
| Loop Tag | Description of Causality | Variables Involved in Loop [with Polarity] |
|---|---|---|
| B1 | Stability of S reduces the demand for G and new designs associated with increasing the variety of G | S stability [−], G variety demand [+], HMBSE demand [+], Natural components [+], Holonic HyR interface variety [+], G variety [+] |
| B2 | Stability of S reduces the demand for G and new designs associated with increasing the variety of F that matches and balances G | S stability [−], G variety demand [+], HMBSE demand [+], Natural components [+], Holonic HyR interface variety [+], F variety [+] |
| B3 | Stability of S reduces the demand for G and new designs associated with increasing the variety of G | S stability [−], G variety demand [+], HMBSE demand [+], Artificial components [+], Holonic HyR interface variety [+], G variety [+] |
| B4 | Stability of S reduces the demand for G and new designs associated with increasing the variety of F that matches and balances G | S stability [−], G variety demand [+], HMBSE demand [+], Artificial components [+], Holonic HyR interface variety [+], F variety [+] |
| B5 | Stability of S reduces the demand for F and new designs associated with increasing the variety of G that matches and balances F | S stability [−], F variety demand [+], HMBSE demand [+], Natural components [+], Holonic HyR interface variety [+], G variety [+] |
| B6 | Stability of S reduces the demand for F and new designs associated with increasing the variety of F | S stability [−], F variety demand [+], HMBSE demand [+], Natural components [+], Holonic HyR interface variety [+], F variety [+] |
| B7 | Stability of S reduces the demand for F and new designs associated with increasing the variety of G that matches and balances F | S stability [−], F variety demand [+], HMBSE demand [+], Artificial components [+], Holonic HyR interface variety [+], G variety [+] |
| B8 | Stability of S reduces the demand for F and new designs associated with increasing the variety of F | S stability [−], F variety demand [+], HMBSE demand [+], Artificial components [+], Holonic HyR interface variety [+], F variety [+] |
| R9 | S stability reduces G demand and the need for new components and security, increasing reliance on the holonic interface, which raises G variety | S stability [−], G variety demand [+], HMBSE demand [+], Natural components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], G variety [+] |
| R10 | S stability reduces G demand and the need for new components and security, increasing reliance on the holonic interface, which raises F variety | S stability [−], G variety demand [+], HMBSE demand [+], Natural components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], F variety [+] |
| R11 | S stability reduces G demand and the need for new components and security, increasing reliance on the holonic interface, which raises G variety | S stability [−], G variety demand [+], HMBSE demand [+], Artificial components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], G variety [+] |
| R12 | S stability reduces G demand and the need for new components and security, increasing reliance on the holonic interface, which raises F variety | S stability [−], G variety demand [+], HMBSE demand [+], Artificial components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], F variety [+] |
| R13 | S stability reduces F demand and the need for new components and security, increasing reliance on the holonic interface, which raises G variety | S stability [−], F variety demand [+], HMBSE demand [+], Natural components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], G variety [+] |
| R14 | S stability reduces F demand and the need for new components and security, increasing reliance on the holonic interface, which raises F variety | S stability [−], F variety demand [+], HMBSE demand [+], Natural components [+], BC, ZKP, SSI components [−], Holonic HyR interface variety [+], F variety [+] |
| R15 | S stability reduces F demand and the need for new components and security, increasing reliance on the holonic interface, which raises G variety | S stability [−], F variety demand [+], HMBSE demand [+], Artificial components [+], BC, ZKP, SSI components [+], Holonic HyR interface variety [+], G variety [+] |
| R16 | S stability reduces F demand and the need for new components and security, increasing reliance on the holonic interface, which raises F variety | S stability [−], F variety demand [+], HMBSE demand [+], Artificial components [+], BC, ZKP, SSI components [+], Holonic HyR interface variety [+], F variety [+] |
References
- Perko, I. Hybrid reality development-can social responsibility concepts provide guidance? Kybernetes 2021, 50, 676–693. [Google Scholar] [CrossRef]
- Totschnig, W. War or peace between humanity and artificial intelligence. Foresight 2025. [Google Scholar] [CrossRef]
- European Commission. Horizon 2020 Research and Innovation Programme. ENOUGH Project: European Food Chain Supply to Reduce GHG Emissions by 2050. 2021. Available online: https://cordis.europa.eu/project/id/101036588 (accessed on 12 April 2025).
- Raikov, A.; Giretti, A.; Pirani, M.; Spalazzi, L.; Guo, M. Accelerating human–computer interaction through convergent conditions for LLM explanation. Front. Artif. Intell. 2024, 7, 1406773. [Google Scholar] [CrossRef] [PubMed]
- Lee, E.A. The Coevolution: The Entwined Futures of Humans and Machines; MIT Press: Cambridge, MA, USA, 2020. [Google Scholar]
- Raikov, A.N.; Pirani, M. Human-machine duality: What’s next in cognitive aspects of artificial intelligence? IEEE Access 2022, 10, 56296–56315. [Google Scholar] [CrossRef]
- Raikov, A.N.; Pirani, M. Contradiction of modern and social-humanitarian artificial intelligence. Kybernetes 2022, 51, 186–198. [Google Scholar] [CrossRef]
- Rosenblueth, A.; Wiener, N.; Bigelow, J. Behavior, Purpose and Teleology. Philos. Sci. 1943, 10, 18–24. [Google Scholar] [CrossRef]
- UN. Transforming Our World: The 2030 Agenda for Sustainable Development; A/RES/70/1; United Nations: New York, NY, USA, 2015. [Google Scholar]
- Pirani, M.; Cucchiarelli, A.; Spalazzi, L. A Role of RMAS, Blockchain, and Zero-Knowledge Proof in Sustainable Supply Chains. In Proceedings of the IECON 2024—50th Annual Conference of the IEEE Industrial Electronics Society, Chicago, IL, USA, 3–6 November 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Gu, B.; Nawab, F. zk-Oracle: Trusted off-chain compute and storage for decentralized applications. Distrib. Parallel Databases 2024, 42, 525–548. [Google Scholar] [CrossRef]
- Six, N.; Herbaut, N.; Salinesi, C. Blockchain software patterns for the design of decentralized applications: A systematic literature review. Blockchain Res. Appl. 2022, 3, 100061. [Google Scholar] [CrossRef]
- Liu, P.; Xian, Y.; Yao, C.; Wang, P.; Wang, L.E.; Li, X. A Trustworthy and Consistent Blockchain Oracle Scheme for Industrial Internet of Things. IEEE Trans. Netw. Serv. Manag. 2024, 21, 5135–5148. [Google Scholar] [CrossRef]
- You, S.; Radivojevic, K.; Nabrzyski, J.; Brenner, P. Persona preserving reputation protocol (P2RP) for enhanced security, privacy, and trust in blockchain oracles. Clust. Comput. 2024, 27, 3945–3956. [Google Scholar] [CrossRef]
- Ezzat, S.K.; Saleh, Y.N.M.; Abdel-Hamid, A.A. Blockchain Oracles: State-of-the-Art and Research Directions. IEEE Access 2022, 10, 67551–67572. [Google Scholar] [CrossRef]
- Lu, S.; Pei, J.; Zhao, R.; Yu, X.; Zhang, X.; Li, J.; Yang, G. CCIO: A Cross-Chain Interoperability Approach for Consortium Blockchains Based on Oracle. Sensors 2023, 23, 1864. [Google Scholar] [CrossRef]
- Sheldon, M.D. Preparing Auditors for the Blockchain Oracle Problem. Curr. Issues Audit. 2021, 15, P27–P39. [Google Scholar] [CrossRef]
- Caldarelli, G. Understanding the Blockchain Oracle Problem: A Call for Action. Information 2020, 11, 509. [Google Scholar] [CrossRef]
- Almi’Ani, K.; Lee, Y.C.; Alrawashdeh, T.; Pasdar, A. Graph-Based Profiling of Blockchain Oracles. IEEE Access 2023, 11, 24995–25007. [Google Scholar] [CrossRef]
- Woo, S.; Song, J.; Park, S. A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications. Sensors 2020, 20, 2725. [Google Scholar] [CrossRef]
- Cai, Y.; Irtija, N.; Tsiropoulou, E.E.; Veneris, A. Truthful Decentralized Blockchain Oracles. Int. J. Netw. Manag. 2022, 32, e2179. [Google Scholar] [CrossRef]
- Dora, M.; Kumar, A.; Mangla, S.K.; Pant, A.; Kamal, M.M. Critical success factors influencing artificial intelligence adoption in food supply chains. Int. J. Prod. Res. 2021, 60, 4621–4640. [Google Scholar] [CrossRef]
- Gama, F.; Magistretti, S. Artificial intelligence in innovation management: A review of innovation capabilities and a taxonomy of AI applications. J. Prod. Innov. Manag. 2025, 42, 76–111. [Google Scholar] [CrossRef]
- Habibipour, A. Responsible living labs: What can go wrong? J. Inf. Commun. Ethics Soc. 2024, 22, 205–218. [Google Scholar] [CrossRef]
- Kaasinen, E.; Anttila, A.H.; Heikkilä, P.; Laarni, J.; Koskinen, H.; Väätänen, A. Smooth and Resilient Human–Machine Teamwork as an Industry 5.0 Design Challenge. Sustainability 2022, 14, 2773. [Google Scholar] [CrossRef]
- Longo, F.; Padovano, A.; Umbrello, S. Value-Oriented and Ethical Technology Engineering in Industry 5.0: A Human-Centric Perspective for the Design of the Factory of the Future. Appl. Sci. 2020, 10, 4182. [Google Scholar] [CrossRef]
- Wu, X.; Su, C.; Yan, L. Human–Machine Shared Steering Control for Vehicle Lane Changing Using Adaptive Game Strategy. Machines 2023, 11, 838. [Google Scholar] [CrossRef]
- Huang, C.; Huang, H.; Zhang, J.; Hang, P.; Hu, Z.; Lv, C. Human-Machine Cooperative Trajectory Planning and Tracking for Safe Automated Driving. IEEE Trans. Intell. Transp. Syst. 2022, 23, 12050–12063. [Google Scholar] [CrossRef]
- Ghaffarzadegan, N.; Majumdar, A.; Williams, R.; Hosseinichimeh, N. Generative agent-based modeling: An introduction and tutorial. Syst. Dyn. Rev. 2024, 40, e1761. [Google Scholar] [CrossRef]
- Han, S.; Zhang, Q.; Yao, Y.; Jin, W.; Xu, Z.; He, C. LLM multi-agent systems: Challenges and open problems. arXiv 2024, arXiv:2402.03578. [Google Scholar]
- Macal, C.M. Everything you need to know about agent-based modelling and simulation. J. Simul. 2016, 10, 144–156. [Google Scholar] [CrossRef]
- Luck, M.; McBurney, P.; Preist, C. A Manifesto for Agent Technology: Towards Next Generation Computing. Auton. Agents Multi-Agent Syst. 2004, 9, 203–252. [Google Scholar] [CrossRef]
- Fortino, G.; Russo, W.; Savaglio, C.; Shen, W.; Zhou, M. Agent-Oriented Cooperative Smart Objects: From IoT System Design to Implementation. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 1939–1956. [Google Scholar] [CrossRef]
- Utomo, D.S.; Onggo, B.S.; Eldridge, S. Applications of agent-based modelling and simulation in the agri-food supply chains. Eur. J. Oper. Res. 2018, 269, 794–805. [Google Scholar] [CrossRef]
- Nugroho, S.; Uehara, T. Systematic review of agent-based and system dynamics models for social-ecological system case studies. Systems 2023, 11, 530. [Google Scholar] [CrossRef]
- Ben-Eli, M. The cybernetics of sustainability: Definition and underlying principles. In Enough for All Forever: A Handbook for Learning About Sustainability; Common Ground Publishers: Champaign, IL, USA, 2012; pp. 255–268. [Google Scholar]
- Salden, A.; Kempen, M. Sustainable Cybernetics Systems: Backbones of Ambient Intelligent Environments. In Ambient Intelligence; Springer: New York, NY, USA, 2005; pp. 213–238. [Google Scholar] [CrossRef]
- Štrukelj, T.; Dankova, P.; Hrast, N. Strategic Transition to Sustainability: A Cybernetic Model. Sustainability 2023, 15, 15948. [Google Scholar] [CrossRef]
- Božičnik, S.; Mulej, M. A new—4th order cybernetics and sustainable future. Kybernetes 2011, 40, 670–684. [Google Scholar] [CrossRef]
- Yolles, M. Metacybernetics: Towards a General Theory of Higher Order Cybernetics. Systems 2021, 9, 34. [Google Scholar] [CrossRef]
- Zatuliveter, Y.; Fishchenko, E. Cybernetics in the Era of Digital Transformation. In World Organization of Systems and Cybernetics 18. Congress-WOSC2021; Springer International Publishing: Cham, Switzerland, 2022; pp. 163–172. [Google Scholar] [CrossRef]
- Biggiero, L. Providing sound theoretical roots to sustainability science: Systems science and (second-order) cybernetics. Sustain. Sci. 2018, 13, 1323–1335. [Google Scholar] [CrossRef]
- Koestler, A. Beyond atomism and holism—The concept of the holon. Perspect. Biol. Med. 1970, 13, 131–154. [Google Scholar] [CrossRef]
- Ross Ashby, W. An Introduction to Cybernetics; Chapman and Hall Ltd.: London, UK, 1961. [Google Scholar]
- Pirani, M.; Carbonari, A.; Cucchiarelli, A.; Giretti, A.; Spalazzi, L. The Meta Holonic Management Tree: Review, steps, and roadmap to industrial Cybernetics 5.0. J. Intell. Manuf. 2024. [Google Scholar] [CrossRef]
- Cardin, O.; Derigent, W.; Trentesaux, D. Evolution of holonic control architectures towards Industry 4.0: A short overview. IFAC-PapersOnLine. In Proceedings of the 16th IFAC Symposium on Information Control Problems in Manufacturing INCOM 2018, Bergamo, Italy, 11–13 June 2018; Volume 51, pp. 1243–1248. [Google Scholar] [CrossRef]
- Derigent, W.; Cardin, O.; Trentesaux, D. Industry 4.0: Contributions of holonic manufacturing control architectures and future challenges. J. Intell. Manuf. 2021, 32, 1797–1818. [Google Scholar] [CrossRef]
- Valckenaers, P.; Van Brussel, H. Design for the Unexpected: From Holonic Manufacturing Systems Towards a Humane Mechatronics Society; Butterworth-Heinemann: Oxford, UK, 2015. [Google Scholar]
- Pineda, M.; Jabba, D.; Nieto-Bernal, W. Blockchain Architectures for the Digital Economy: Trends and Opportunities. Sustainability 2024, 16, 442. [Google Scholar] [CrossRef]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-Layer Blockchain-Based Security Architecture for Internet of Things. Sensors 2021, 21, 772. [Google Scholar] [CrossRef]
- Maesa, D.D.F.; Lisi, A.; Mori, P.; Ricci, L.; Boschi, G. Self sovereign and blockchain based access control: Supporting attributes privacy with zero knowledge. J. Netw. Comput. Appl. 2023, 212, 103577. [Google Scholar] [CrossRef]
- Vazquez Melendez, E.I.; Bergey, P.; Smith, B. Blockchain technology for supply chain provenance: Increasing supply chain efficiency and consumer trust. Supply Chain. Manag. Int. J. 2024, 29, 706–730. [Google Scholar] [CrossRef]
- Queiroz, M.M.; Telles, R.; Bonilla, S.H. Blockchain and supply chain management integration: A systematic review of the literature. Supply Chain. Manag. Int. J. 2019, 25, 241–254. [Google Scholar] [CrossRef]
- Tyagi, A.K.; Dananjayan, S.; Agarwal, D.; Thariq Ahmed, H.F. Blockchain—Internet of Things Applications: Opportunities and Challenges for Industry 4.0 and Society 5.0. Sensors 2023, 23, 947. [Google Scholar] [CrossRef]
- Cheng, M.; Liu, G.; Xu, Y.; Chi, M. When Blockchain Meets the AEC Industry: Present Status, Benefits, Challenges, and Future Research Opportunities. Buildings 2021, 11, 340. [Google Scholar] [CrossRef]
- Demirkesen, S.; Tezel, A.; Uysal, F.; Ozturk, Z. Investigating the Impact of Blockchain on Project Risk Management Success: A Structural Equation Model. IEEE Trans. Eng. Manag. 2024, 71, 8356–8368. [Google Scholar] [CrossRef]
- Spalazzi, L.; Spegni, F.; Corneli, A.; Naticchia, B. Blockchain based choreographies: The construction industry case study. Concurr. Comput. Pract. Exp. 2023, 35, e6740. [Google Scholar] [CrossRef]
- Spegni, F.; Fratini, L.; Pirani, M.; Spalazzi, L. ChoEn: A Smart Contract Based Choreography Enforcer. In Proceedings of the 2023 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Atlanta, GA, USA, 13–17 March 2023; pp. 86–91. [Google Scholar] [CrossRef]
- Ahmed, W.A.; MacCarthy, B.L.; Treiblmaier, H. Why, where and how are organizations using blockchain in their supply chains? Motivations, application areas and contingency factors. Int. J. Oper. Prod. Manag. 2022, 42, 1995–2028. [Google Scholar] [CrossRef]
- González-Mendes, S.; Alonso-Muñoz, S.; García-Muiña, F.E.; González-Sánchez, R. Discovering the conceptual building blocks of blockchain technology applications in the agri-food supply chain: A review and research agenda. Br. Food J. 2024, 126, 182–206. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, X.; Zhao, Z.; Xu, J.; Jiang, Z.; Yu, J.; Cui, X. Research on Grain Food Blockchain Traceability Information Management Model Based on Master-Slave Multichain. Comput. Intell. Neurosci. 2022, 2022, 7498025. [Google Scholar] [CrossRef]
- Sharma, A.; Sharma, A.; Singh, R.K.; Bhatia, T. Blockchain adoption in agri-food supply chain management: An empirical study of the main drivers using extended UTAUT. Bus. Process. Manag. J. 2023, 29, 737–756. [Google Scholar] [CrossRef]
- Malisic, B.; Misic, N.; Krco, S.; Martinovic, A.; Tinaj, S.; Popovic, T. Blockchain Adoption in the Wine Supply Chain: A Systematic Literature Review. Sustainability 2023, 15, 14408. [Google Scholar] [CrossRef]
- Cao, S.; Xu, H.; Bryceson, K.P. Blockchain Traceability for Sustainability Communication in Food Supply Chains: An Architectural Framework, Design Pathway and Considerations. Sustainability 2023, 15, 13486. [Google Scholar] [CrossRef]
- Erol, I.; Ar, I.M.; Ozdemir, A.I.; Peker, I.; Asgary, A.; Medeni, I.T.; Medeni, T. Assessing the feasibility of blockchain technology in industries: Evidence from Turkey. J. Enterp. Inf. Manag. 2020, 34, 746–769. [Google Scholar] [CrossRef]
- Gupta, R.; Meena, A.; Dhir, S. Blockchain in the age of industrial revolution: A systematic literature review using bibliometric analysis. Glob. Bus. Organ. Excell. 2024, 43, 5–23. [Google Scholar] [CrossRef]
- Gladysz, B.; anh Tran, T.; Romero, D.; van Erp, T.; Abonyi, J.; Ruppert, T. Current development on the Operator 4.0 and transition towards the Operator 5.0: A systematic literature review in light of Industry 5.0. J. Manuf. Syst. 2023, 70, 160–185. [Google Scholar] [CrossRef]
- Zhang, Z.; Yang, T.; Liu, Y. SABlockFL: A blockchain-based smart agent system architecture and its application in federated learning. Int. J. Crowd Sci. 2020, 4, 133–147. [Google Scholar] [CrossRef]
- Alzhrani, F.; Saeedi, K.; Zhao, L. Architectural Patterns for Blockchain Systems and Application Design. Appl. Sci. 2023, 13, 11533. [Google Scholar] [CrossRef]
- Valencia-Arias, A.; González-Ruiz, J.D.; Verde Flores, L.; Vega-Mori, L.; Rodríguez-Correa, P.; Sánchez Santos, G. Machine Learning and Blockchain: A Bibliometric Study on Security and Privacy. Information 2024, 15, 65. [Google Scholar] [CrossRef]
- Di Paolo, E.A.; Lawler, D.; Vaccari, A.P. Toward an Enactive Conception of Productive Practices: Beyond Material Agency. Philos. Technol. 2023, 36, 31. [Google Scholar] [CrossRef]
- Varela, F.; Thompson, E.; Rosch, E. Enaction: Embodied cognition. In The Embodied Mind: Cognitive Science and Human Experience; MIT Press: Boston, MA, USA, 1991; pp. 147–182. [Google Scholar]
- Di Paolo, E.A. F/acts ways of enactive worldmaking. J. Conscious. Stud. 2023, 30, 159–189. [Google Scholar] [CrossRef]
- Lepskiy, V. Decision support ontologies in self-developing reflexive-active environments. IFAC-PapersOnLine 2018, 51, 504–509. [Google Scholar] [CrossRef]
- Ross Ashby, W. Requisite variety and its implications for the control of complex systems. Cybernetica 1958, 1, 83–99. [Google Scholar] [CrossRef]
- Ashby, M. Ethical regulators and super-ethical systems. Systems 2020, 8, 53. [Google Scholar] [CrossRef]
- Ventana Systems, Inc. Vensim, Version 9.0. 2024. Available online: https://vensim.com (accessed on 12 April 2025).
- Sterman, J.D. System Dynamics Modeling: Tools for Learning in a Complex World. Calif. Manag. Rev. 2001, 43, 8–25. [Google Scholar] [CrossRef]
- Sterman, J. Business Dynamics; Irwin/McGraw-Hill c2000: Boston, MA, USA, 2010. [Google Scholar]
- Conant, R.C.; Ross Ashby, W. Every good regulator of a system must be a model of that system. Int. J. Syst. Sci. 1970, 1, 89–97. [Google Scholar] [CrossRef]
- Simon, H.A. The Architecture of Complexity: Hierarchic Systems. In The Sciences of the Artificial; MIT Press: Cambridge, MA, USA, 1996; pp. 183–216. [Google Scholar]
- Beer, S. Diagnosing the System for Organizations; John Wiley & Sons: Chichester, UK, 1985. [Google Scholar]
- Beer, S. The Heart of the Enterprise; John Wiley & Sons: Chichester, UK, 1979. [Google Scholar]
- Beer, S. Brain of the Firm, 2nd ed.; John Wiley & Sons: Chichester, UK, 1981. [Google Scholar]
- Ernstberger, J.; Chaliasos, S.; Zhou, L.; Jovanovic, P.; Gervais, A. Do You Need a Zero Knowledge Proof? Cryptology ePrint Archive. 2024. Available online: https://eprint.iacr.org/2024/050 (accessed on 12 April 2025).
- Sun, X.; Yu, F.R.; Zhang, P.; Sun, Z.; Xie, W.; Peng, X. A Survey on Zero-Knowledge Proof in Blockchain. IEEE Netw. 2021, 35, 198–205. [Google Scholar] [CrossRef]
- Satybaldy, A.; Ferdous, M.S.; Nowostawski, M. A taxonomy of challenges for self-sovereign identity systems. IEEE Access 2024, 12, 16151–16177. [Google Scholar] [CrossRef]
- Taherdoost, H. Smart Contracts in Blockchain Technology: A Critical Review. Information 2023, 14, 117. [Google Scholar] [CrossRef]
- Porkodi, S.; Kesavaraja, D. Smart contract: A survey towards extortionate vulnerability detection and security enhancement. Wirel. Netw. 2024, 30, 1285–1304. [Google Scholar] [CrossRef]
- Cheng, M.; Chong, H.Y.; Xu, Y. Blockchain-smart contracts for sustainable project performance: Bibliometric and content analyses. Environ. Dev. Sustain. 2024, 26, 8159–8182. [Google Scholar] [CrossRef]
- Herian, R. Smart contracts: A remedial analysis. Inf. Commun. Technol. Law 2020, 30, 17–34. [Google Scholar] [CrossRef]
- Ni, J. Intelligent Contracts and the Principle of Contractual Freedom: A Classical Legal Examination in the Era of Emerging Technologies. Front. Bus. Econ. Manag. 2024, 14, 5–9. [Google Scholar] [CrossRef]
- Negara, E.; Hidayanto, A.; Andryani, R.; Syaputra, R. Survey of Smart Contract Framework and Its Application. Information 2021, 12, 257. [Google Scholar] [CrossRef]
- Kang, Y.; Kim, W.; Kim, H.; Lee, M.; Song, M.; Seo, H. Malicious Contract Detection for Blockchain Network Using Lightweight Deep Learning Implemented through Explainable AI. Electronics 2023, 12, 3893. [Google Scholar] [CrossRef]
- Krichen, M. Strengthening the Security of Smart Contracts through the Power of Artificial Intelligence. Computers 2023, 12, 107. [Google Scholar] [CrossRef]
- Battah, A.; Madine, M.; Yaqoob, I.; Salah, K.; Hasan, H.R.; Jayaraman, R. Blockchain and NFTs for Trusted Ownership, Trading, and Access of AI Models. IEEE Access 2022, 10, 112230–112249. [Google Scholar] [CrossRef]
- Partala, J.; Nguyen, T.H.; Pirttikangas, S. Non-Interactive Zero-Knowledge for Blockchain: A Survey. IEEE Access 2020, 8, 227945–227961. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Rusnak, A.; Yezhov, A.; Kanonik, D.; Kuznetsova, K.; Karashchuk, S. Enhanced Security and Efficiency in Blockchain With Aggregated Zero-Knowledge Proof Mechanisms. IEEE Access 2024, 12, 49228–49248. [Google Scholar] [CrossRef]
- Šimunić, S.; Bernaca, D.; Lenac, K. Verifiable Computing Applications in Blockchain. IEEE Access 2021, 9, 156729–156745. [Google Scholar] [CrossRef]
- Lee, S.; Ko, H.; Kim, J.; Oh, H. vCNN: Verifiable Convolutional Neural Network Based on zk-SNARKs. IEEE Trans. Dependable Secur. Comput. 2024, 21, 4254–4270. [Google Scholar] [CrossRef]
- Oude Roelink, B.; El-Hajj, M.; Sarmah, D. Systematic review: Comparing zk-SNARK, zk-STARK, and bulletproof protocols for privacy-preserving authentication. Secur. Priv. 2024, 7, e401. [Google Scholar] [CrossRef]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Agarwal, P.; Idrees, S.M. Land Registry Framework Based on Self-Sovereign Identity (SSI) for Environmental Sustainability. Sustainability 2022, 14, 5400. [Google Scholar] [CrossRef]
- Mohammadzadeh, N.; Dorri Nogoorani, S.; Muñoz-Tapia, J.L. Decentralized Factoring for Self-Sovereign Identities. Electronics 2021, 10, 1467. [Google Scholar] [CrossRef]
- Yildiz, H.; Küpper, A.; Thatmann, D.; Göndör, S.; Herbke, P. Toward Interoperable Self-Sovereign Identities. IEEE Access 2023, 11, 114080–114116. [Google Scholar] [CrossRef]
- Wittek, K.; Lazzati, L.; Bothe, D.; Sinnaeve, A.J.; Pohlmann, N. An SSI Based System for Incentivized and SelfDetermined Customer-to-Business Data Sharing in a Local Economy Context. In Proceedings of the 2020 IEEE European Technology and Engineering Management Summit (E-TEMS), Dortmund, Germany, 5–7 March 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Dieye, M.; Valiorgue, P.; Gelas, J.P.; Diallo, E.H.; Ghodous, P.; Biennier, F.; Peyrol, Ã. A Self-Sovereign Identity Based on Zero-Knowledge Proof and Blockchain. IEEE Access 2023, 11, 49445–49455. [Google Scholar] [CrossRef]
- Pirani, M.; Cacopardo, A.; Cucchiarelli, A.; Spalazzi, L. A Soulbound Token-based Reputation System in Sustainable Supply Chains. In Proceedings of the 2023 International Conference on Embedded Wireless Systems and Networks, EWSN ’23, New York, NY, USA, 25–27 September 2023; pp. 363–368. [Google Scholar]
- Choi, W.; Woo, J.; Hong, J.W.K. Fractional non-fungible tokens: Overview, evaluation, marketplaces, and challenges. Int. J. Netw. Manag. 2024, 34, e2260. [Google Scholar] [CrossRef]
- Ko, K.; Jeong, T.; Woo, J.; Hong, J.W.K. Survey on blockchain-based non-fungible tokens: History, technologies, standards, and open challenges. Int. J. Netw. Manag. 2024, 34, e2245. [Google Scholar] [CrossRef]
- Weyl, E.G.; Ohlhaver, P.; Buterin, V. Decentralized Society: Finding Web3’s Soul. SSRN Electron. J. 2022. [Google Scholar] [CrossRef]
- Pinna, A.; Lunesu, M.I.; Tonelli, R.; Sansoni, S. Soulbound token applications. A case study in the health sector. Distrib. Ledger Technol. Res. Pract. 2024. [Google Scholar] [CrossRef]
- Zülch, F.; Holle, M.; Hofmann, A. Theoretical design of blockchain-based traceability for organic egg supply chains according to regulation (EU) 2018/848. PLoS ONE 2024, 19, e0304791. [Google Scholar] [CrossRef]
- Cabot-Nadal, M.A.; Mut-Puigserver, M.; Payeras-CapellÃ, M.M.; Pericà s Gornals, R. Confidential Certified Notification Protocol Using Rejectable Soulbound Tokens and Identity-Based Cryptography. IEEE Access 2023, 11, 142495–142514. [Google Scholar] [CrossRef]
- Saito, Y.; Rose, J.A. Reputation-based Decentralized Autonomous Organization for the non-profit sector: Leveraging blockchain to enhance good governance. Front. Blockchain 2023, 5, 1083647. [Google Scholar] [CrossRef]
- Ghobakhloo, M.; Iranmanesh, M.; Morales, M.E.; Nilashi, M.; Amran, A. Actions and approaches for enabling Industry 5.0-driven sustainable industrial transformation: A strategy roadmap. Corp. Soc. Responsib. Environ. Manag. 2023, 30, 1473–1494. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Rosado da Cruz, A.M.; Lopes, S.I. An Overview of Blockchain for Industry 5.0: Towards Human-Centric, Sustainable and Resilient Applications. IEEE Access 2024, 12, 116162–116201. [Google Scholar] [CrossRef]
- OMG. Business Process Model and Notation (BPMN), Version 2.0.2. 2013. Available online: https://www.omg.org/spec/BPMN/2.0.2/PDF (accessed on 12 April 2025).
- Pirani, M.; Cucchiarelli, A.; Spalazzi, L. Paradigms for database-centric application interfaces. Procedia Comput. Sci. 2023, 217, 835–845. [Google Scholar] [CrossRef]
- Pirani, M.; Bonci, A.; Longhi, S. Towards a formal model of computation for RMAS. Procedia Comput. Sci. 2022, 200, 865–877. [Google Scholar] [CrossRef]
- Casciaro, S.; Mainetti, L.; Vergallo, R. A systematic review on One-Time Programs. Res. Sq. 2024. [Google Scholar] [CrossRef]
- Kopanaki, E. Conceptualizing supply chain resilience: The role of complex IT infrastructures. Systems 2022, 10, 35. [Google Scholar] [CrossRef]
- Schwaninger, M. Organizing for sustainability: A cybernetic concept for sustainable renewal. Kybernetes 2015, 44, 935–954. [Google Scholar] [CrossRef]
- Bonci, A.; Pirani, M.; Carbonari, A.; Naticchia, B.; Cucchiarelli, A.; Longhi, S. Holonic Overlays in Cyber-Physical System of Systems. In Proceedings of the 2018 IEEE 23rd International Conference on Emerging Technologies and Factory Automation (ETFA), Torino, Italy, 4–7 September 2018; Volume 1, pp. 1240–1243. [Google Scholar] [CrossRef]
- Bonci, A.; Pirani, M.; Cucchiarelli, A.; Carbonari, A.; Naticchia, B.; Longhi, S. A Review of Recursive Holarchies for Viable Systems in CPSs. In Proceedings of the 2018 IEEE 16th International Conference on Industrial Informatics (INDIN), Porto, Portugal, 18–20 July 2018; pp. 37–42. [Google Scholar] [CrossRef]
- Lee, E.A. Plato and the NERD: The Creative Partnership of Humans and Technology; MIT Press: Cambridge, MA, USA, 2017. [Google Scholar]
- European Commission. The European Green Deal. ESDN Rep. 2020, 2, 53. [Google Scholar]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2018, 57, 2117–2135. [Google Scholar] [CrossRef]
- Chandan, A.; John, M.; Potdar, V. Achieving UN SDGs in Food Supply Chain Using Blockchain Technology. Sustainability 2023, 15, 2109. [Google Scholar] [CrossRef]
- Ahmed, A.A.; Nazzal, M.A.; Darras, B.M. Cyber-Physical Systems as an Enabler of Circular Economy to Achieve Sustainable Development Goals: A Comprehensive Review. Int. J. Precis. Eng. Manuf.-Green Technol. 2022, 9, 955–975. [Google Scholar] [CrossRef]
- Liu, X.; Feng, J. Trusted Blockchain Oracle Scheme Based on Aggregate Signature. J. Comput. Commun. 2021, 9, 95–109. [Google Scholar] [CrossRef]
- Zhang, M.; Wang, Y.; Zhang, Y. Research on Supply Chain Coordination Decision Making under the Influence of Lead Time Based on System Dynamics. Systems 2024, 12, 32. [Google Scholar] [CrossRef]
- Kruger, H.; Verhoef, A.; Preiser, R. The Epistemological Implications of Critical Complexity Thinking for Operational Research. Systems 2019, 7, 5. [Google Scholar] [CrossRef]
- Pirani, M.; Dragoni, A.F.; Longhi, S. Towards Sustainable Models of Computation for Artificial Intelligence in Cyber-Physical Systems. In Proceedings of the IECON 2021—47th Annual Conference of the IEEE Industrial Electronics Society, Toronto, ON, Canada, 13–16 October 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Veldhuis, G.; van Wermeskerken, F.; Visker, O.; Steinmann, P.; Deuten, S.; van Waas, R. From Data to Model Structure: A Generative Algorithm to Develop System Dynamics Models. 2024. Available online: https://ssrn.com/abstract=4921086 (accessed on 12 April 2025).
- Abdelbari, H.; Shafi, K. A system dynamics modeling support system based on computational intelligence. Systems 2019, 7, 47. [Google Scholar] [CrossRef]



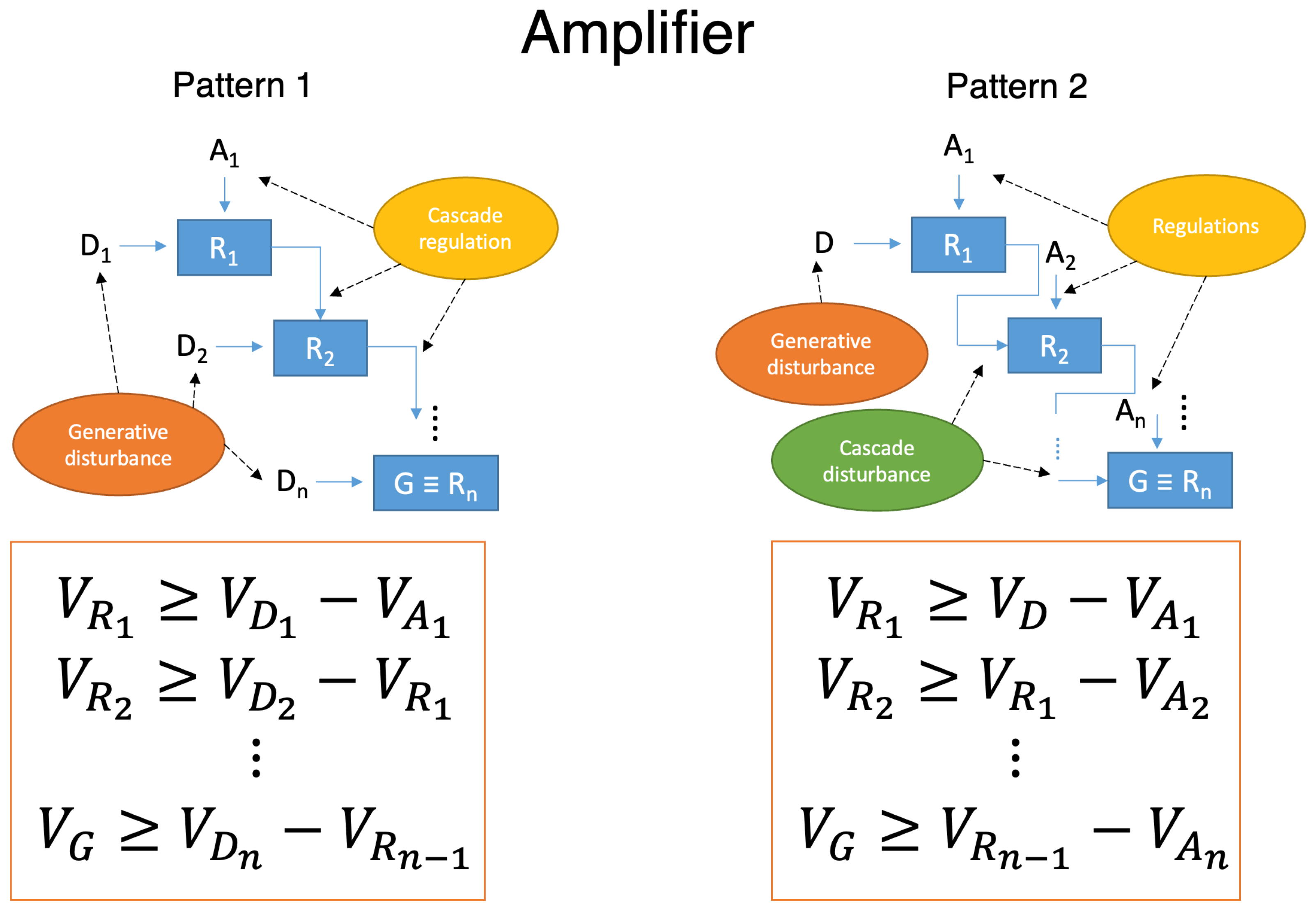

| Challenge | Description and Reference(s) |
|---|---|
| AI as a stakeholder | Co-creation of experiences in HyR requires recognition of AI’s active role in human–AI reciprocity [1,5]. |
| Ethical decision-making and stakeholder engagement | Organizations must consider ethical implications of AI involvement in decisions, especially in supply chains [22]. Multidisciplinary engagement is crucial for fostering innovation with transdisciplinary skills in cybersecurity [23]. Proactive strategies are needed to address AI’s societal and environmental consequences [24]. |
| Human-centered and value sensitive design | Emphasizing joint cognitive systems and user motivations helps align Industry 5.0 teams with sustainability goals [25]. Integration of sustainable values into HMI design improves user experience and satisfaction [26]. |
| Shared control systems | Intelligent, context-aware systems support hybrid capabilities between humans and machines [27,28]. |
| Systems engineering and AI integration | Difficulties remain in applying System Dynamics methods to LLM-based simulations [4,29,30]. |
| Modeling complexity in HyR | While agent-based systems support autonomy and collaboration, they are not yet sufficient for complex modeling and control as required by HyR [31,32,33,34,35]. |
| Agency–Environment (AE) Quadrant | Agency | Environment | Create | Learn | Use |
|---|---|---|---|---|---|
| Natural–Nature (NN) | Natural elements; natural biological structures; animals; humans | Natural elements; biological entities; animals; humans | Giving birth; allopoiesis; proliferations; natural transformations | Naturalistic sciences; observations; natural learning | Living; natural processes |
| Natural–Artifacts (NA) | Natural elements; natural biological structures; animals; humans | Tools; artifacts; machines; computing systems; virtual worlds | Design and production; writing documents; virtual reality creations; digital twin creation; hypothesis abduction | Observe; natural learning; understanding | Use of tools or artifacts; disruption or dissolution of artifacts |
| Artificial–Nature (AN) | Computational system; autonomous machine; software program; artifacts and objects; automation; mechanic system; robotic system; embodiment of AGI (artificial general intelligence) | Physical world; biological structures; animals and humans | Production of data, information, and knowledge through communication; enable or disable autopoies or allopoiesis of new biological structures | Photography; sensors; machine learning; monitoring; transduction | Energy intake by transformation of raw material; material for productions; good, bad, or purposeful effects on humans and animals; transduction; communications |
| Artificial–Artifacts (AA) | Computational system; autonomous machine; software program; artifacts and objects; automation; mechanic system; robotic system; AGI (artificial general intelligence) | Digital worlds; cellular automata; evolutionary algorithms; multi-agent systems; artificial life; emergence; artificial self; autonomic systems; mechanic systems; artifacts | Program creation; self-rewriting; agent offspring spawning; delegated MAS [48]; digital allopoiesis; digital genetic offsprings; production of artifacts; production of data, information, and knowledge; synthesis of artficial structures; synthesis of biological structures | Self-learning; state observers; machine learning; sensors | Program execution; communications; material for productions; good, bad, or purposeful effects on artifacts or artificial objects |
| Regulation Type | Pattern | Use Case Example |
|---|---|---|
| Amplifier | Pattern 1 (Figure 7, left) | Current generative pre-trained transformers (GPTs) can provide a human agent with more information than they have at the beginning of an inquiry. In this case, the agent is learning something from the environment, which is the digital information available to the GPT. In this learning interaction, the agent devises a prompting scheme that can be seen as a cascade of regulators that amplifies the variety in two steps. The data resulting from the first inquiry () are cascaded as input to the second stage of the prompt (). and give the incremental generative information that the GPT produces and that is regulated by the agent’s prompting skills. For example, the agent instructs the GPT that after first inquiry, like “find me references about projects on food supply chain,” it then should execute the following: “Without waiting for further user input, the assistant anticipate what would be useful next, with tabular comparisons of the references obtained in the first inquiry”. |
| Pattern 2 (Figure 7, right) | An example might be a cascade consisting of the accelerator pedal and the steering of a car. The generative disturbance D is the motor power available. At a first stage , the agent chooses the input level. The output is a linear forward movement that, as a disturbance, must be regulated by a steering action on the steering system of the car. | |
| Filter | Pattern 1 (Figure 8, left) | In almost all the applications for video call conferences, today it is possible to select a fancy background to apply to the speaker’s image. In this case, the E is the full video signal. is the action for selecting the speaker’s contours in order to extract the foreground image from the background. Through the identification of the contours as output of , a second regulation stage provides Gaussian noise (blurred background) from a pseudorandom signal generator as , and applies it only to background, having received in the input the contours of the part of the image that must be passed untouched. |
| Pattern 2 (Figure 8, right) | A typical use case is that of a passband filter for processing radio frequency signals. The first filtering action may perform a low-pass filtering of the E signal at regulation stage . The output is sent as disturbance to the regulation stage and filtered with a high-pass filtering action . |
| Technology of BC Framework | Maturity Level (for Relevant Intended Purposes) | Essential Background and Description | Use in HMBSE |
|---|---|---|---|
| Smart Contract | Medium. Smart contracts are a rather mature technology. They can reliably be used although still research is ongoing on their security and scalability [88,89,90,91,92,93,94,95,96]. | Smart contracts represent an automatic programming framework executed even among untrusted parties by eliminating third parties. Smart contracts are containers of code that encapsulate and replicate the terms of real-world contracts in the digital domain [88,93]. | Contracts are fundamentally a legally binding agreement between two or more parties, with each party committed to fulfilling its commitments. The interface between HMBSE components becomes trusted and sustainable with this technology [90,94,95]. |
| Oracle | Low. There are still open problems in this technology and research is ongoing [11,12,13,14,15,16,17,18,19,20,21]. | Oracle and Reverse Oracle are patterns that enable communication between on-chain smart contracts and off-chain components [12,15]. The open problems are the trustworthiness, sustainability, and scalability of these operations [11,13,14]. | Accuracy and trustability of data across the transactions that the components of the HMBSE should be preserved with the Oracle and Reverse Oracle. With these technologies, the actors (human or artificial) in the system gain and preserve reputation [14,16,17]. |
| Zero-Knowledge Proof (ZKP) | Medium. The technology has many variants and tools available [85,86,97,98,99,100,101]. Nonetheless, still, the non-interactive proof in general bears high computational costs and limitations [99]. | ZKP is a method by which the prover can prove to the verifier that some statement is true without revealing any information other than the fact that the statement is true. This process can be made non-interactive and succinct in many but not all cases [85,97,99]. | ZKP is essential for actors and components in the HMBSE to prove their correctness and trustworthiness while retaining privacy, secrecy, and autonomy. Documents and computations can be verified. ZKP is the key enabling technology for others like the Oracles and SSI [10,99,100,101]. |
| Self-Sovereign Identity (SSI) | Medium. It is a very promising and well-investigated technology, as it is an acknowledged game changer for many distributed privacy-preserving and democracy-driven applications [87,102,103,104]. | SSI allows actors to be the only owners of their data and to decide what to share and in which granularity; they can only share the minimum amount of information that is needed for their or societal benefit [51,87,102,103,105]. | In the search for sustainability, the actors in the system would be allowed to retain ownership of selected part of their credentials and at the same time provide a strong but democratic system of role-based access control on information for decision making [51,105,106]. |
| Tokens | High. Fungible, Non-Fungible, and Soulbound Tokens are well supported today and they can be efficiently included in applications that feature smart contracts [10,105,107,108,109,110,111,112,113]. | Tokens are digital assets representing ownership, value, or utility within a BC ecosystem. They are created and managed typically using smart contracts, and can serve various purposes like cryptocurrency, utility, security, non-fungible uniqueness [109], and identity, credentials, or personal achievements [107,108,109,110,111,112,114]. | Tokens are an essential feature when it comes to recording, exchanging, transferring, or retrieving values or credentials from any actor in a collective system. They are key enablers in reputation and value creation systems [105,107,114]. |
| Technology | Strengths and Applications | Challenges and Open Issues |
|---|---|---|
| Blockchain | Enhances traceability, security, and sustainability; supports automation in hazardous contexts [116] | Scalability, energy use, legal uncertainty, technical complexity, interoperability gaps |
| Smart Contracts | Used in supply chains and healthcare; enables automation [88] | Limited processing, post-deployment inflexibility, verification gaps [89,91,92,93] |
| AI + Smart Contracts | Helps mitigate smart contract vulnerabilities [95] | Explainability and transparency concerns [4,94,96] |
| Oracles | Bridge on-chain and off-chain data; key for BC applications [12]; trusted schemes, reputation protocols, distributed models [14,16,17,20,130] | Data manipulation, re-centralization, IoT complexity [11,13,15,18,19], lack of integrated HyR system frameworks despite AI support [21] |
| ZKP | Verifies data integrity without revealing it; used in supply chains and collectives [10,85]; recursive aggregation, hybrid models, AI integration [86,98,100] | Computation cost, trusted setup vulnerabilities, oracle integration difficulty [97,99], performance bottlenecks, lack of explainability [101] |
| SSI | Empowers agent-controlled credentials, aligns with ethical AI [102], GDPR-compliance, AI explainability, ZKP-enabled access control [51,103,105,106] | Scalability, integration, interdisciplinary gaps [87,104] |
| Blockchain Tokens | Used for flexible, ethical incentives; supports traceability [107] | Regulatory and technical feasibility for fractional NFTs [108,109] |
| Soulbound Tokens (SBTs) | Decentralized identity, ethical AI, privacy with structure rejection [110,111,112,113] | Smart contract complexity to preserve privacy and immutability at the same time |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pirani, M.; Cucchiarelli, A.; Naeem, T.; Spalazzi, L. A Blockchain-Driven Cyber-Systemic Approach to Hybrid Reality. Systems 2025, 13, 294. https://doi.org/10.3390/systems13040294
Pirani M, Cucchiarelli A, Naeem T, Spalazzi L. A Blockchain-Driven Cyber-Systemic Approach to Hybrid Reality. Systems. 2025; 13(4):294. https://doi.org/10.3390/systems13040294
Chicago/Turabian StylePirani, Massimiliano, Alessandro Cucchiarelli, Tariq Naeem, and Luca Spalazzi. 2025. "A Blockchain-Driven Cyber-Systemic Approach to Hybrid Reality" Systems 13, no. 4: 294. https://doi.org/10.3390/systems13040294
APA StylePirani, M., Cucchiarelli, A., Naeem, T., & Spalazzi, L. (2025). A Blockchain-Driven Cyber-Systemic Approach to Hybrid Reality. Systems, 13(4), 294. https://doi.org/10.3390/systems13040294







