Reducing Terrorism Casualties: Analyzing Policies Effectiveness under a Systems Perspective
Abstract
1. Introduction
2. Context and Previous Research
2.1. The Al Qaeda Factor
- Command and Control
- Suggested/Endorsed
- Inspired
2.2. Orsini’s Model
2.3. Comparison and Conclusions
- Attacks with ISIS involvement (ISIS-led cells and trained lone wolves)
- Attacks without ISIS involvement (autonomous cells and untrained lone wolves)
2.4. Silber and Bhatt Model
- Pre-radicalization: this is the starting point, when individuals come into contact with the jihadi or other terrorist ideology. There is no initial condition of relative deprivation that would spur radicalization. It is the terrorist ideology itself and a “cognitive opening” [17] (that will be explained in the next step) that would push otherwise “normal” people to begin the radicalization process.
- Self-Identification: after a cognitive opening, individuals begin approaching the terrorist ideology, meeting with like-minded people and begin the process of changing their identity. The concept of “cognitive opening” refers to a catalyst that opens individuals to great change and is a crucial element. In this model, the cognitive opening will take the form of a great trauma to the individual in question, be it Economic, Political, Social or Personal. An example of an Economic trauma could be the loss of a job; a Political trauma could be the start of an international conflict; a Social trauma may be an inability to integrate into a new community following migration; finally, a personal trauma may be the death of a friend or family member. Whatever specific form it takes, this trauma will make the individual question their previously held beliefs, and begin looking for a “solution”: something that will help them reorient themselves. At this stage the terrorist ideology can become a “beacon of salvation”, offering a new way of life; as such it is clear that ideology plays a key role in this model, as without it the radicalization process may not even begin.
- Indoctrination: in this phase the individual will, as the name implies, be indoctrinated, usually with the assistance of a person well integrated into the terrorist organization. This “contact point” is important and has been mentioned before by Silber in “The Al Qaeda Factor”. This person is the so called “Link man”, who puts the radicalizing individual in contact with a terrorist group and will eventually facilitate his joining of said group. As the indoctrination continues (in a far more intense manner if a terrorist group is joined) the individual will become gradually more radical, and they will begin to believe that it is time for action. As such, in this phase the mental preparation to commit a terror attack begins.
- Jihadization: at this stage the radicalization process is complete, and the individual will accept that a terror attack is necessary. As such he will begin to plan a terror attack, alone or with others, by selecting a target, obtaining materials, creating a plan, etc. This phase is much faster than the others and may in some cases last only a few days.
2.5. DRIA Model
- D—Disintegration of Social Identity: this is the starting point of the radicalization process, where an individual through some great event or trauma has his previous identity destroyed. This trauma leads to the “Cognitive Opening” that was explored in Silber and Bhatt’s model. In the present model, the cognitive opening represents a turning point for the individual in question; given the destruction of what they believed to be “real” they seek new answers and a new way of life. At this stage there are many paths forward, and radicalization is but one of them. Indeed, individuals may choose to remain passive and not enact any change, or they may reinvent themselves in a “healthy” manner; embracing a radical ideology is just one of the many paths one may take at the crossroads of the first step [19,20]. As such, once again ideology is at the forefront of the radicalization process, as it is the key in determining whether the process will even begin: indeed, if there is no terrorist ideology, or if the ideology is not “convincing” then radicalization under the DRIA model will not even begin.
- R—Reconstruction of Social Identity: at this step, individuals that come into contact with the Jihadi ideology may choose to use it as the basis for rebuilding themselves, as was said before. The Jihadi ideology is excellent at providing “lost souls” with a new purpose. Indeed, it is an ideology that gives a clear “mission” that is filled with meaning; the perfect remedy for people who have lost their sense of orientation and truth as a result of the first stage of the model, the Disintegration of Social Identity. During the process of reconstruction under a Jihadi ideology, individuals will create a new “radical mental universe” for themselves, inspired by the radical ideology, that mutates their worldview into a categorical “us-versus-them” mentality.
- I—Integration in a Revolutionary Sect: at this stage the now cognitively-radicalized individuals will seek out likeminded people. Some will succeed in establishing contact with other radicalized individuals or with terrorist organizations and some will not. In the case of those that do not, they may still believe themselves to be a part of the organization through an imagined community, meaning they identify with the organization despite not having ever had contact. From this step we can see the groundwork for Orsini’s model for terror attacks, based on what type of contact cognitively radicalized individuals will make. If they make contact with other radicalized individuals, but not a terror group they may evolve into an autonomous cell; if they contact a terror group they may evolve into either a trained lone wolf or a terror group (ISIS) led cell; if they are unable to establish any form of contact they may become untrained lone wolves.
- A—Alienation from the Surrounding World: the final stage in radicalization is crucial in enabling individuals to actually kill another human being. Alienation from the outside world is as simple as the name implies; the group into which an individual has integrated will forbid contact with the western world, which allows time for “traditional” morals to phase out and the radical ideology to fully mature. However, alienation may also be manifested on an individual basis, given that, as was seen in the previous step, it is not assured that a cognitively-radicalized individual will succeed in establishing contact with others, be they radicals or a terror group. After sufficient alienation, individuals will now be able to kill others, and as such the radicalization process is complete.
2.6. Quintan Wiktorowicz’s Model
3. Methodological Approach
- The Level of Ambition is an arbitrary value that measures the number of casualties a terror group would like to reach per year. It drives other variables in the system, such as the desired level of CF, by calculating what inputs are required to reach the desired output.
- The non-prepared lethality and lethality variables have been calculated by looking at terror attacks conducted over the past 15 years, dividing the attacks into either “lone wolf” or “terror group controlled” with reference to the literature reviewed above, counting the number of casualties for each attack and thus calculating how many casualties one terrorist is able to produce on average. As such it was found that a trained and terror group supported terrorist can produce, on average, 66 casualties while a lone wolf can produce six.
- The territory controlled was arbitrarily set in order to match a “large terror group”, using ISIS’s maximum expansion as a reference.
4. Model Simulation and Result Analysis
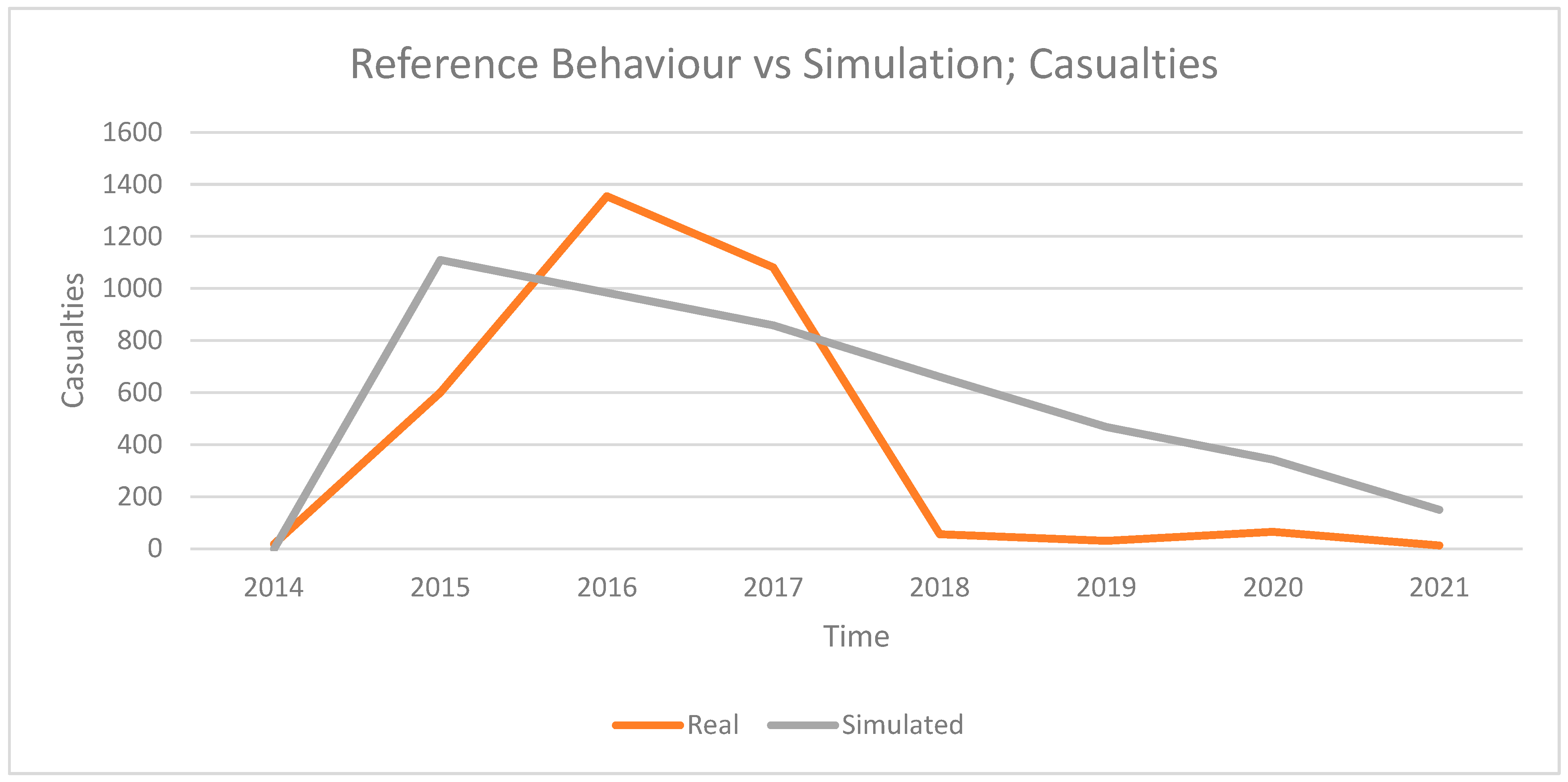
4.1. “Real-World” Scenario
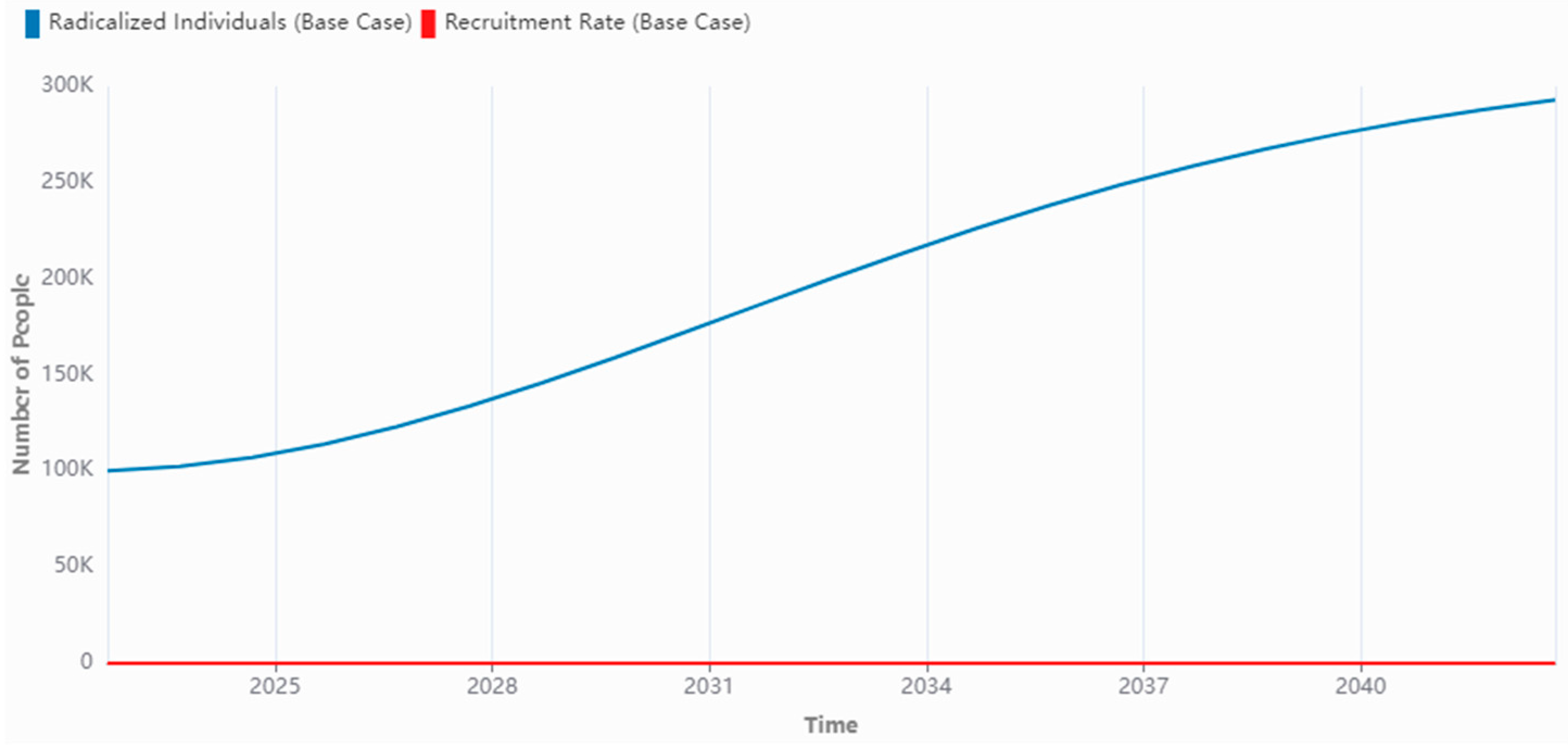
4.2. Baseline Simulations & Simulation Analysis
4.3. High Leverage Points for Policies
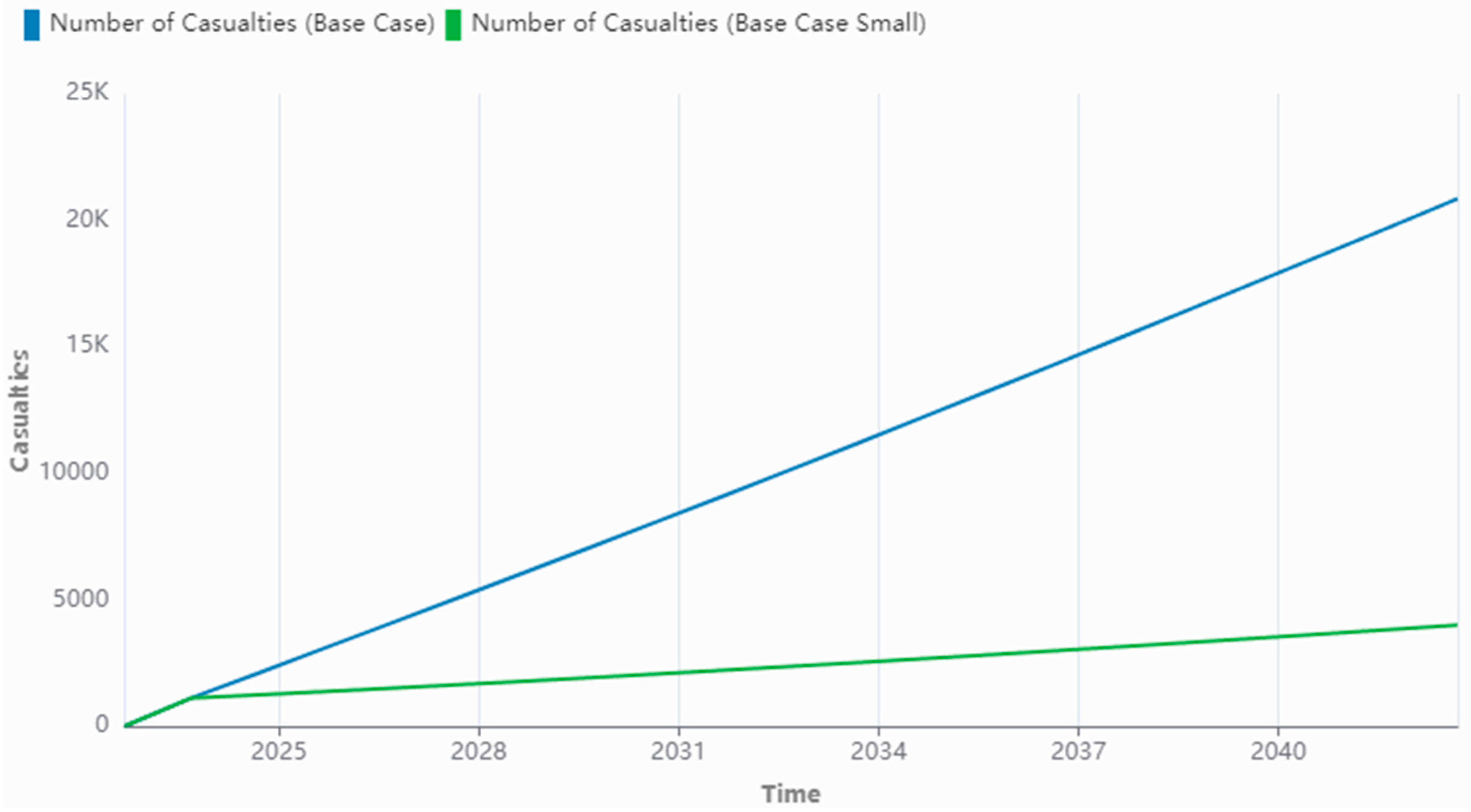
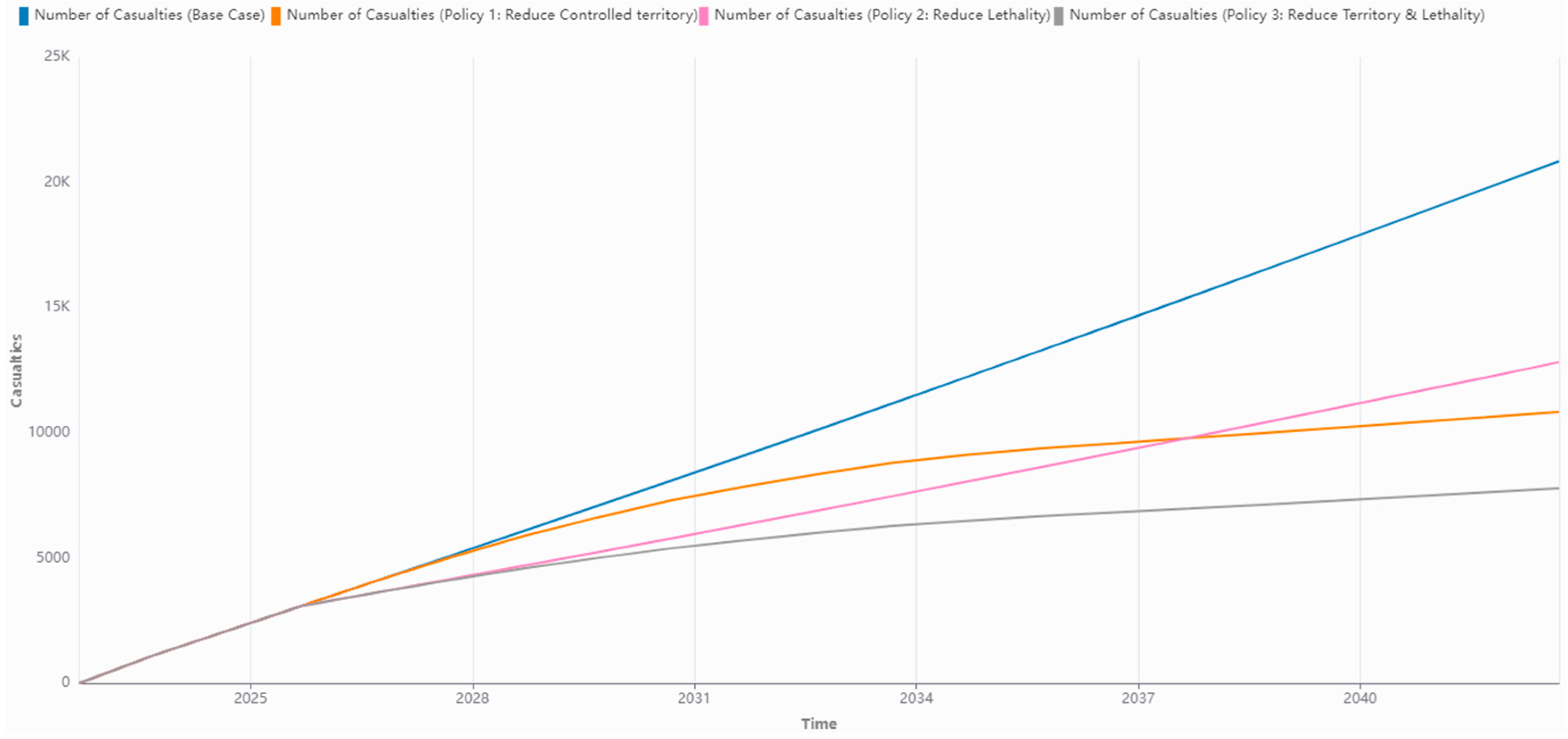
4.4. Large Terror Groups
- Reduce the controlled territory of the group while also reducing their lethality.
- Reduce the controlled territory of the group.
- Reduce the lethality of the group.
4.5. Small Terror Groups
- Censor digital terror propaganda and implement deradicalization programs;
- Implement deradicalization programs;
- Censor digital terror propaganda.
5. Discussion and Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Schmid, A.P. (Ed.) The Routledge Handbook of Terrorism Research; Taylor & Francis: Abingdon, UK, 2011; Volume 6. [Google Scholar]
- Sterman, J. Business Dynamics; Irwin/McGraw-Hill c2000: New York, NY, USA, 2010; p. 982. [Google Scholar]
- Forrester, J.W. Industrial dynamics. J. Oper. Res. Soc. 1997, 48, 1037–1041. [Google Scholar] [CrossRef]
- Silber, M.D. The al Qaeda factor. In The Al Qaeda Factor; University of Pennsylvania Press: Philadelphia, PA, USA, 2011. [Google Scholar]
- Orsini, A. L’ISIS Non È Morto; Rizzoli: Milano, Italy, 2018. [Google Scholar]
- Orsini, A. Gli attentati dell’Isis in Europa occidentale. Un’interpretazione sociologica. Democr. E Sicur. Democr. Secur. Rev. 2019, 3, 101–133. [Google Scholar]
- Aljazeera.com. Barcelona and Cambrils Attack: What We Know So Far. 2017. Available online: https://www.aljazeera.com/news/2017/8/22/barcelona-and-cambrils-attacks-what-where-and-when (accessed on 4 May 2022).
- RTE.ie. Paris attacks death toll rises to 130. 2015. Available online: https://www.rte.ie/news/2015/1120/747897-paris/ (accessed on 6 April 2023).
- Weber, M. From Max Weber: Essays in Sociology; Routledge: Florence, Italy, 2009. [Google Scholar]
- Orsini, A. Interview With a Terrorist by Vocation: A Day Among the Diehard Terrorists, Part II. Stud. Confl. Terror. 2013, 36, 672–684. [Google Scholar] [CrossRef]
- Morgan, M.J. The Impact of 9/11 on Politics and War: The Day that Changed Everything? Palgrave, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; p. 222. ISBN 978-0-230-60763-7. [Google Scholar]
- The Independent. 7/7 Bombings: Who Were the 52 Victims of the London Terror Attacks? 2015. Available online: https://www.independent.co.uk/news/uk/home-news/7-7-bombings-london-anniversary-live-the-52-victims-of-the-london-terror-attacks-remembered-10369569.html (accessed on 4 May 2022).
- February 26, 1993 Commemoration. Available online: https://www.911memorial.org/connect/commemoration/February26-1993 (accessed on 12 December 2022).
- Ray, M. Madrid Train Bombings of 2004. Encyclopedia Britannica. 4 March 2022. Available online: https://www.britannica.com/event/Madrid-train-bombings-of-2004 (accessed on 7 March 2023).
- Solla, F.; Carboni, J.; Bréaud, J.; Babe, P.; Brézac, G.; Chivoret, N.; Dupont, A.; Fernandez, A. July 14, 2016, terror attack in Nice, France. Acad. Pediatr. 2018, 18, 361–363. [Google Scholar] [CrossRef] [PubMed]
- Silber, M.D.; Bhatt, A.; Analysts, S.I. Radicalization in the West: The Homegrown Threat; Police Department: New York, NY, USA, 2007; pp. 1–90.
- Van der Kolk, B. The Body Keeps the Score: Mind, Brain and Body in the Transformation of Trauma; Penguin: London, UK, 2014. [Google Scholar]
- Orsini, A. What Everybody Should Know about Radicalization and the DRIA Model. Stud. Confl. Terror. 2020, 46, 1–33. [Google Scholar] [CrossRef]
- Ritzer, G.; Stepnisky, J. Contemporary Sociological Theory and Its Classical Roots: The Basics; Sage Publications: Singapore, 2022. [Google Scholar]
- Geertz, C. The Interpretation of Cultures; Basic books: New York, NY, USA, 1973; Volume 5019. [Google Scholar]
- Wiktorowicz, Q. Radical Islam Rising: Muslim Extremism in the West; Rowman & Littlefield Publishers: Lanham, MD, USA, 2005. [Google Scholar]
- Spradley, J.P. Participant Observation; Waveland Press: Illinois, UK, 2016. [Google Scholar]
- Moghaddam, F.M. The staircase to terrorism: A psychological exploration. Am. Psychol. 2005, 60, 161. [Google Scholar] [CrossRef] [PubMed]
- Kruglanski, A.W.; Bélanger, J.J.; Gunaratna, R. The Three Pillars of Radicalization: Needs, Narratives, and Networks; Oxford University Press: Cary, NC, USA, 2019. [Google Scholar]
- Swann, W.B., Jr.; Buhrmester, M.D. Identity fusion. Curr. Dir. Psychol. Sci. 2015, 24, 52–57. [Google Scholar] [CrossRef]
- McCauley, C.; Moskalenko, S. Friction: How Radicalization Happens to Them and Us; Oxford University Press: Cary, NC, USA, 2011. [Google Scholar]
- Armenia, S.; De Angelis, A. Proposal of a ‘Goldilocks’ methodology for the assessment of an international crisis. In Proceedings of the 31st International System Dynamics Conference (ISDC), Cambridge, MA, USA, 21–25 July 2013. [Google Scholar]
- Cardazzone, A.; Armenia, S. Analyzing counter-terrorism and asymmetric conflict policies by means of a system dynamics approach. In Proceedings of the 32nd International Conference of the System Dynamics Society, Delft, The Netherlands, 20–24 July 2014. [Google Scholar]
- Pruyt, E.; Armenia, S.; Tsaples, G.; Antinori, A.; Onori, R. Fighting Foreign Fighters. But What About Potential and Returning Foreign Fighters? In Proceedings of the 33rd International System Dynamics Conference (ISDC), Cambridge, MA, USA, 19–23 July 2015. [Google Scholar]
- De Angelis, T. A systemic Analysis of Terrorism in the West; Luiss Guido Carli: Rome, Italy, 2022. [Google Scholar]
- Schuurman, B.; Lindekilde, L.; Malthaner, S.; O’Connor, F.; Gill, P.; Bouhana, N. End of the lone wolf: The typology that should not have been. Stud. Confl. Terror. 2019, 42, 771–778. [Google Scholar] [CrossRef]
- Ec.europa.eu. Living Conditions in Europe—Poverty and Social Exclusion—Statistics Explained. 2021. Available online: https://ec.europa.eu/eurostat/statistics-explained/index.php?title=Living_conditions_in_Europe_-_poverty_and_social_exclusion (accessed on 29 August 2022).
- Eurostat First-and Second-Generation Immigrants Living in the EU. 2017. Available online: https://ec.europa.eu/eurostat/en/web/products-eurostat-news/-/ddn-20170322-1 (accessed on 29 August 2022).
- Eurostat Educational Attainment Level (ISCED11) Distribution by Sex, Age, Migration Status and Educational Attainment Level of Parents (ISCED11F). 2021. Available online: https://ec.europa.eu/eurostat/databrowser/view/lfso_14beduc/default/table?lang=en (accessed on 29 August 2022).
- Maragkos, K.E.; Maravelakis, P.E. Extracting Primary Emotions and Topics from the Al-Hayat Media Centre Magazine Publications, Using Topic Modelling and Lexicon-Based Approaches. Soc. Sci. Comput. Rev. 2022. [Google Scholar] [CrossRef]
- CIGI. Share of Internet Users Who Have Used Technologies that Allow Access to the Dark Web as of February 2019, by Region. Statista Inc.. 2019. Available online: https://www.statista.com/statistics/1015238/dark-web-access-technology-usage-by-region/ (accessed on 22 August 2022).
- McCarthy, N. ISIS Is Expanding Its Reach On Twitter. Statista Inc.. 2015. Available online: https://www.statista.com/chart/3308/isis-is-expanding-its-reach-on-twitter/ (accessed on 26 August 2022).
- Facebook. Global Number of Content Containing Terrorist Propaganda Removed by Facebook from 4th Quarter 2017 to 1st Quarter 2022 (in Millions). Statista Inc.. 2022. Available online: https://www.statista.com/statistics/1013864/facebook-terrorist-propaganda-removal-quarter/ (accessed on 30 August 2022).
- Allievi, S. Mosques in Western Europe—Stefano Allievi. 2014. Available online: https://stefanoallievi.it/anno/mosques-in-western-europe/ (accessed on 22 August 2022).
- Eurostat. Prisoners by Age and Sex—Number and Rate for the Relevant Sex and Age Groups. 2020. Available online: https://ec.europa.eu/eurostat/databrowser/view/crim_pris_age/default/table?lang=en (accessed on 23 August 2022).
- Wilson Center. Timeline: The Rise, Spread, and Fall of the Islamic State. 2019. Available online: https://www.wilsoncenter.org/article/timeline-the-rise-spread-and-fall-the-islamic-state (accessed on 19 September 2022).
- Heißner, S.; Neumann, P.R.; Holland-McCowan, J.; Basra, R. Caliphate in Decline: An Estimate of Islamic State’s Financial Fortunes; International Centre for the Study of Radicalisation and Political Violence: London, UK, 2017. [Google Scholar]
- Europol. EU Terrorism Situation & Trend Report (TE-SAT). 2022. Available online: https://www.europol.europa.eu/publications-events/main-reports/tesat-report (accessed on 17 September 2022).
- Eurostat. Available online: https://ec.europa.eu/eurostat/web/main/home (accessed on 20 December 2022).
- IEP. Global Terrorism Index|Countries Most Impacted by Terrorism. 2022. Available online: https://www.visionofhumanity.org/maps/global-terrorism-index/#/ (accessed on 20 August 2022).
- Silico.app. Available online: https://silico.app/ (accessed on 9 February 2023).
- The Syrian Observatory For Human Rights. Although They have been Besieged by Russia, Iran, and the Regime for Two Years, Thousands of ISIS Members are Still within an Area of 4000 km2 without Any Intention to Launch a Military Operation against Them. 2019. Available online: https://www.syriahr.com/en/117051/ (accessed on 23 March 2023).
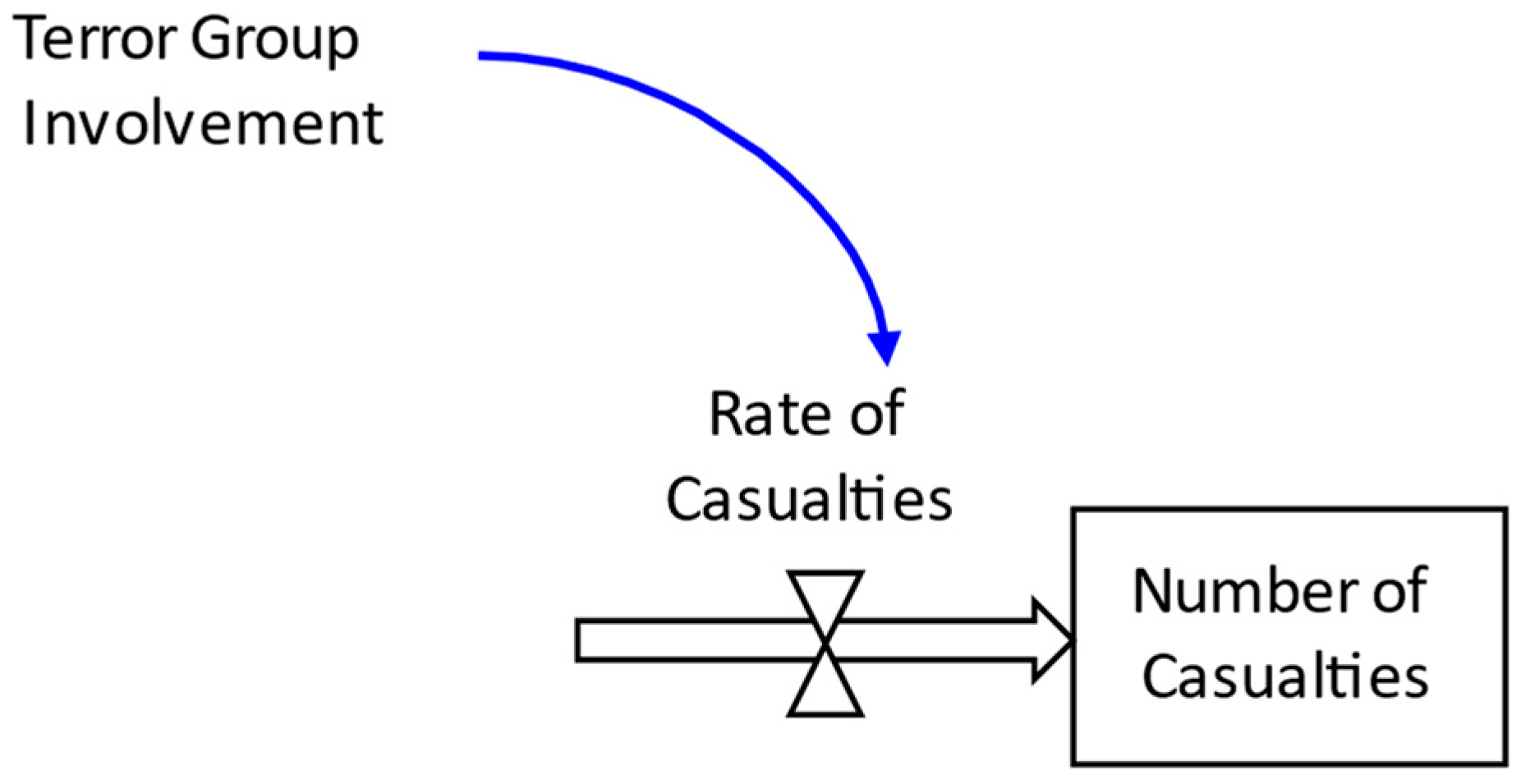
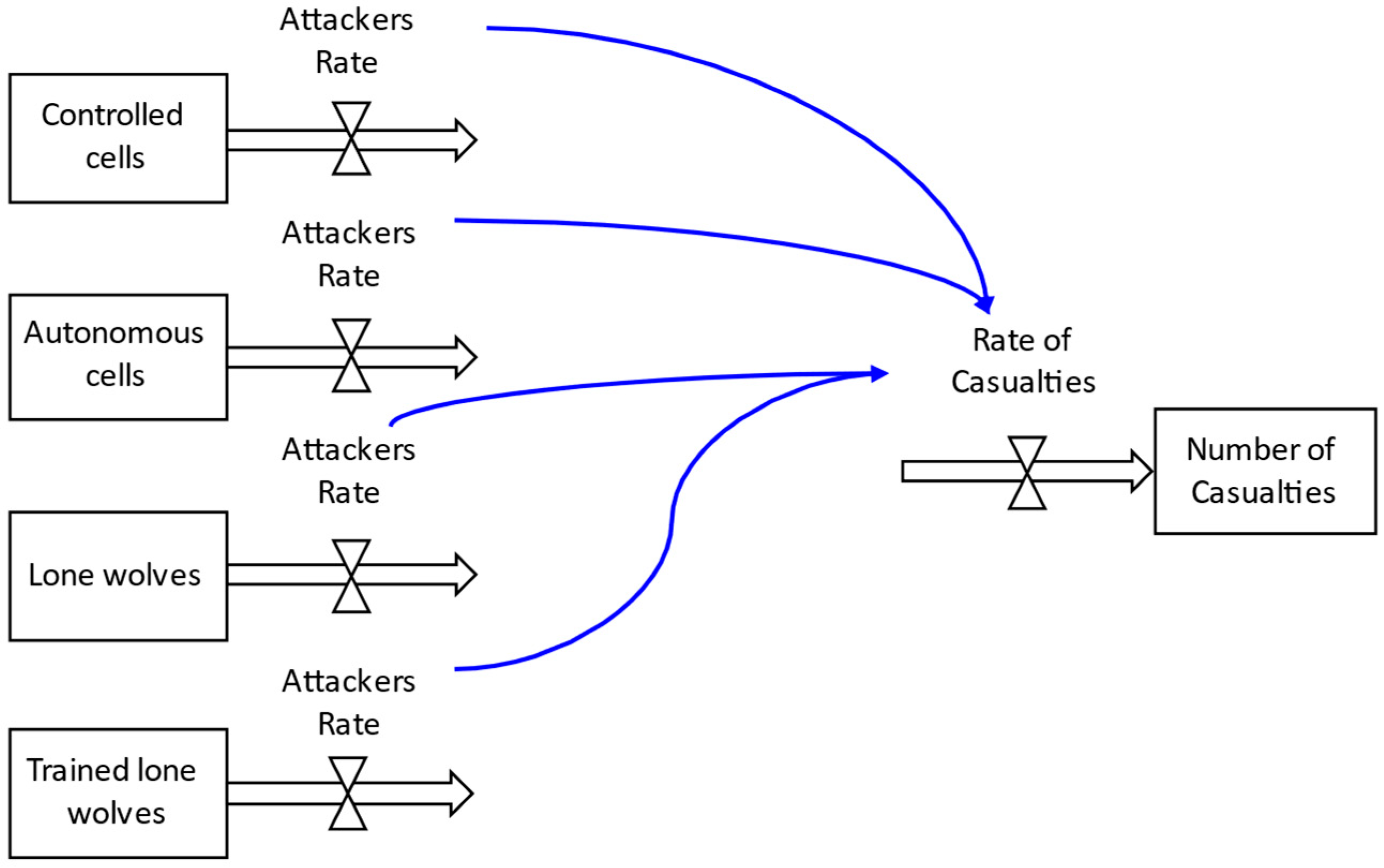
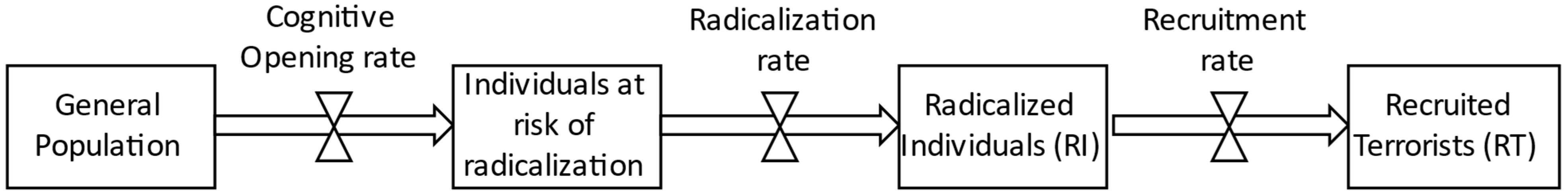
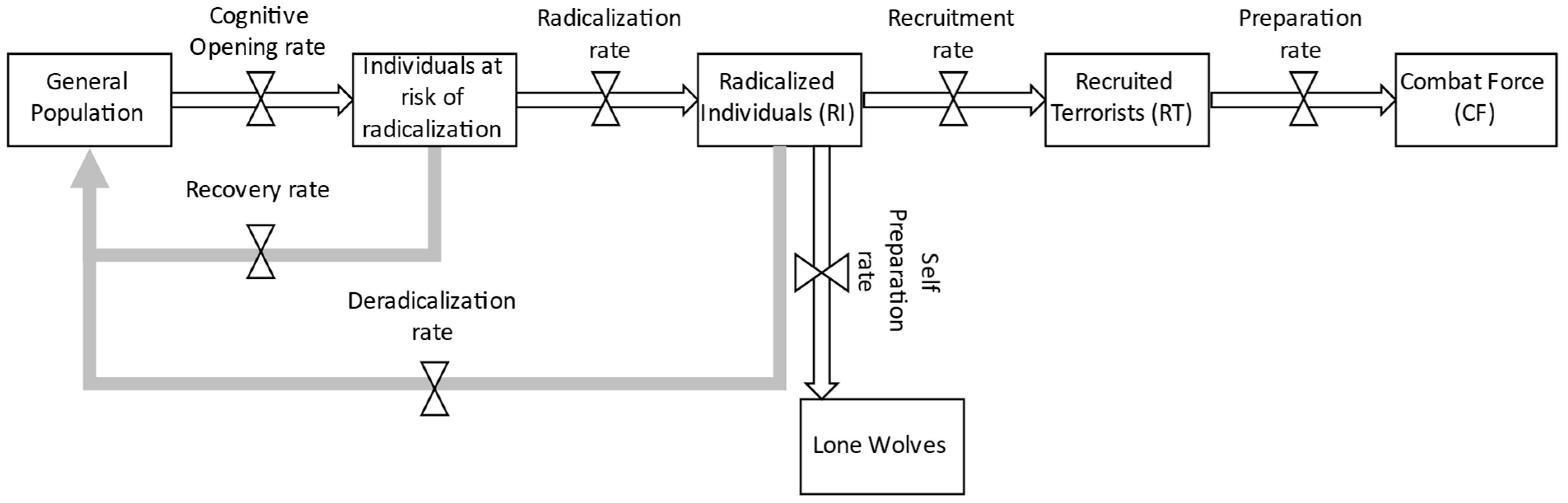





| VARIABLE | BASE CASE VALUE |
|---|---|
| Immigrants (Number of People) | 23,700,000 |
| Poverty (Number of People) | 96,500,000 |
| Low Education (Number of People) | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 |
| Level of Ambition (Number of People) | 1000 |
| Non-Prepared Lethality (Number of People) | 6 |
| Lethality (Number of People) | 66 |
| Deradicalization over time (% of People) | 0 |
| Territory Controlled (Km2) | 100,000 |
| STOCK | BASE CASE VALUE |
|---|---|
| General Population (Number of People) | 447,010,000 |
| At Risk Individuals (Number of People) | 200,000 |
| Radicalized Individuals (Number of People) | 100,000 |
| Lone Wolves (Number of People) | 9 |
| Recruited Terrorists (Number of People) | 16 |
| Combat Force (Number of People) | 16 |
| Number of Casualties (Number of People) | 0 |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 100,000–19,200 per tick (min 4000) |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 1000 |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 100,000–10,000 per tick, starting from tick 2 (min 1000) |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 until tick 2, then 33 for the rest of the simulation |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 100,000 |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 until tick 2, then 33 for the rest of the simulation |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 100,000–10,000 per tick, starting from tick 2 (min 1000) |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 11,000 at tick 1 and 0 from tick 2 onwards |
| Twitter Accounts (Number of Accounts) | 1000 | 500 at tick 1 and 0 from tick 2 onwards |
| Facebook Radical Content Views (Number of Views) | 10,000 | 5000 at tick 1 and 0 from tick 2 onwards |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | 0 |
| Territory Controlled (Km2) | 100,000 | 1000 |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 22,000 |
| Twitter Accounts (Number of Accounts) | 1000 | 1000 |
| Facebook Radical Content Views (Number of Views) | 10,000 | 10,000 |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | +0.05 per tick, starting from tick 2, (max 0.7) |
| Territory Controlled (Km2) | 100,000 | 1000 |
| VARIABLE | BASE CASE VALUE | SCENARIO VALUE |
|---|---|---|
| Immigrants (Number of People) | 23,700,000 | 23,700,000 |
| Poverty (Number of People) | 96,500,000 | 96,500,000 |
| Low Education (Number of People) | 102,812,300 | 102,812,300 |
| Dark Web Users (Number of People) | 22,000 | 11,000 at tick 1 and 0 from tick 2 onwards |
| Twitter Accounts (Number of Accounts) | 1000 | 500 at tick 1 and 0 from tick 2 onwards |
| Facebook Radical Content Views (Number of Views) | 10,000 | 5000 at tick 1 and 0 from tick 2 onwards |
| Level of Ambition (Number of People) | 1000 | 1000 |
| Non-Prepared Lethality | 6 | 6 |
| Lethality (Number of People) | 66 | 66 |
| Deradicalization over time (% of People) | 0 | +0.05 per tick, starting from tick 2, (max 0.7) |
| Territory Controlled (Km2) | 100,000 | 1000 |
| INPUTS | OUTPUTS (At Tick 20) | |
|---|---|---|
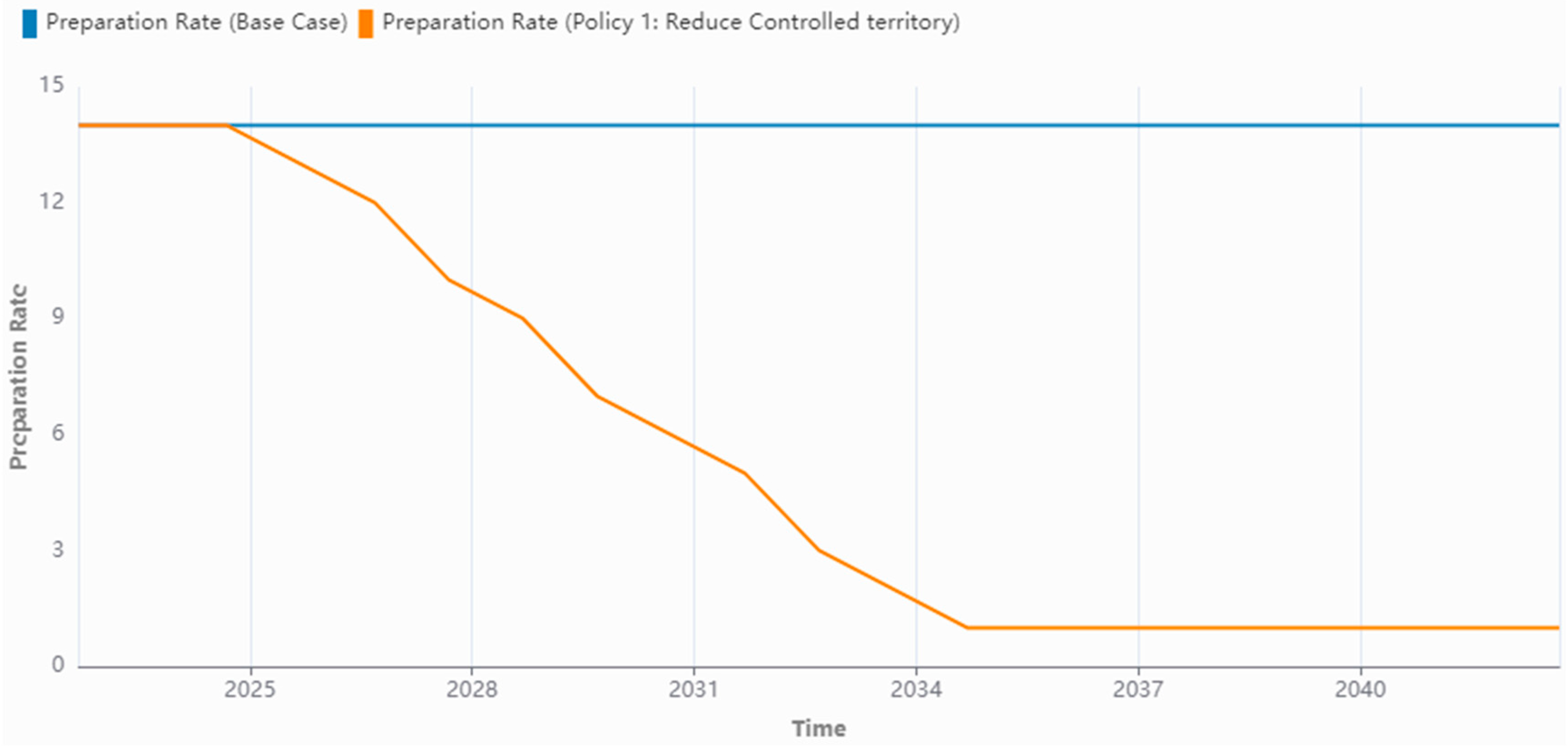
| Policy 1: Reduce Territory (Large Terror Group) | The Controlled Territory has been reduced by 10,000 Km2 per tick, down to a minimum of 1000 Km2. | Casualties drops from 20,850 to 10,836; Combat Force drops from 14 to 1; Lone Wolves drop from 29 to 25; Radicalized Individuals drops from 293,078 to 246,645; At Risk Individuals increases from 195,515 to 260,816. |
| Policy 2: Reduce Lethality (Large Terror Group) | Lethality has been halved from 66 to 33, starting from tick 2. | Casualties drops from 20,850 to 12,822; Lone Wolves drop from 29 to 25; Radicalized Individuals drops from 293,078 to 255,049; At Risk Individuals increases from 195,515 to 256,342. |
| Policy 3: Reduce Territory and Lethality (Large Terror Group) | The Controlled Territory has been reduced by 10,000 Km2 per tick, down to a minimum of 1000 Km2; Lethality has been halved from 66 to 33, starting from tick 2. | Casualties drops from 20,850 to 7788; Combat Force drops from 14 to 1; Lone Wolves drop from 29 to 23; Radicalized Individuals drops from 293,078 to 223,044; At Risk Individuals increases from 195,515 to 300,308. |
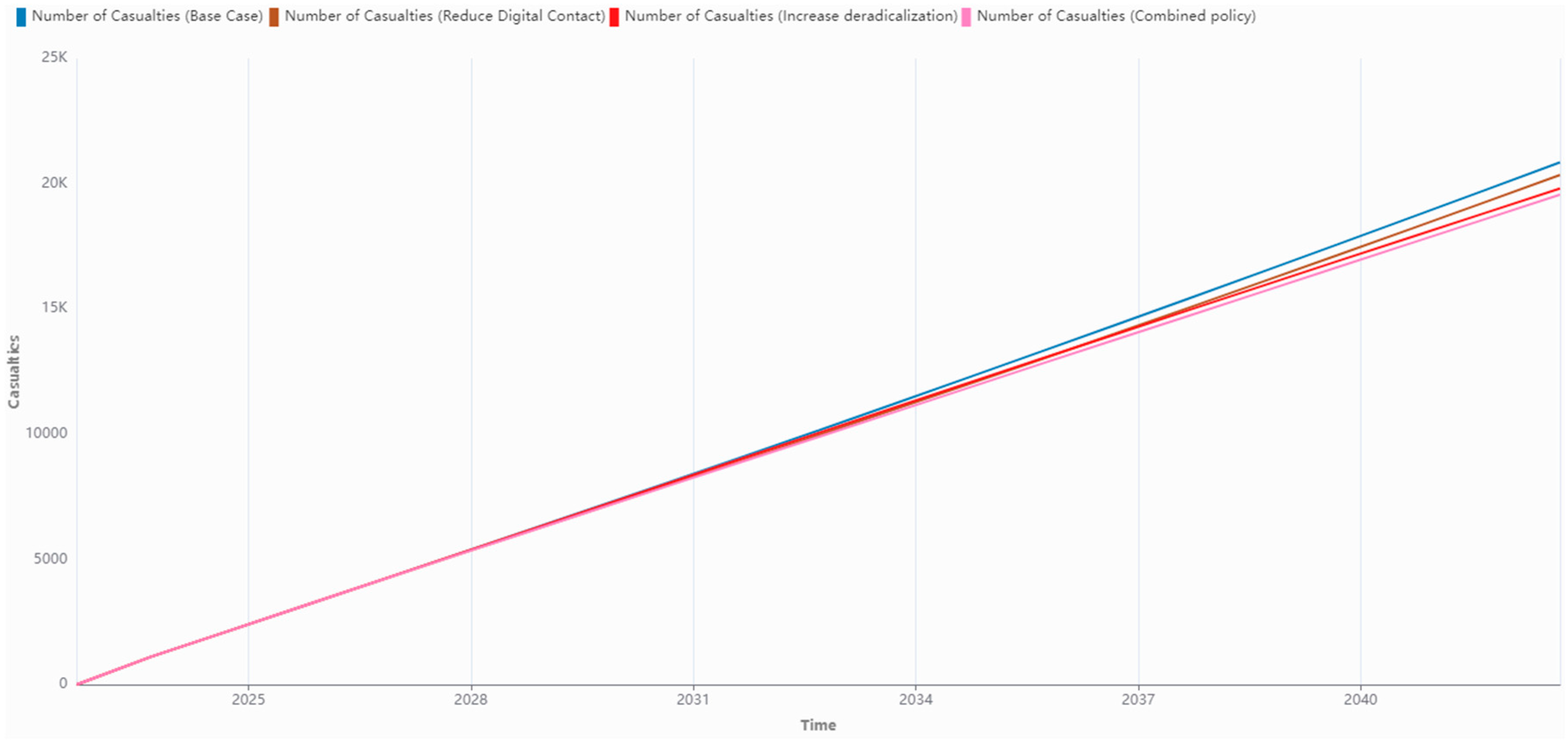
| Policy 4: Reduce Digital Contact (Small Terror Group) | Digital Contact has been halved at tick 1 and reduced to 0 from tick 2 onwards. | Casualties drops from 3966 to 3294; Lone Wolves drops from 18 to 10; Radicalized Individuals drops from 180,496 to 95,746; At Risk Individuals increases from 373,989 to 524,709. |
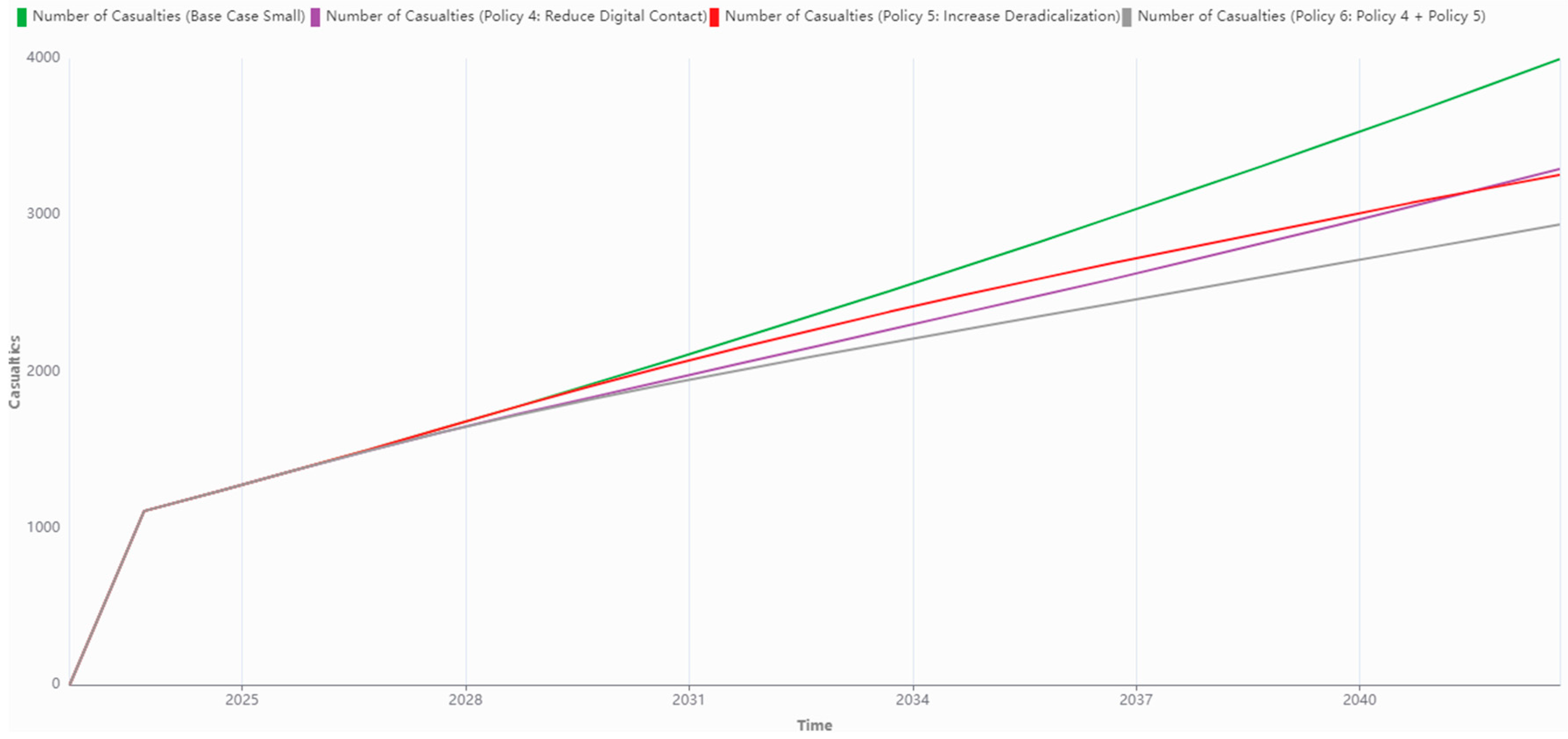
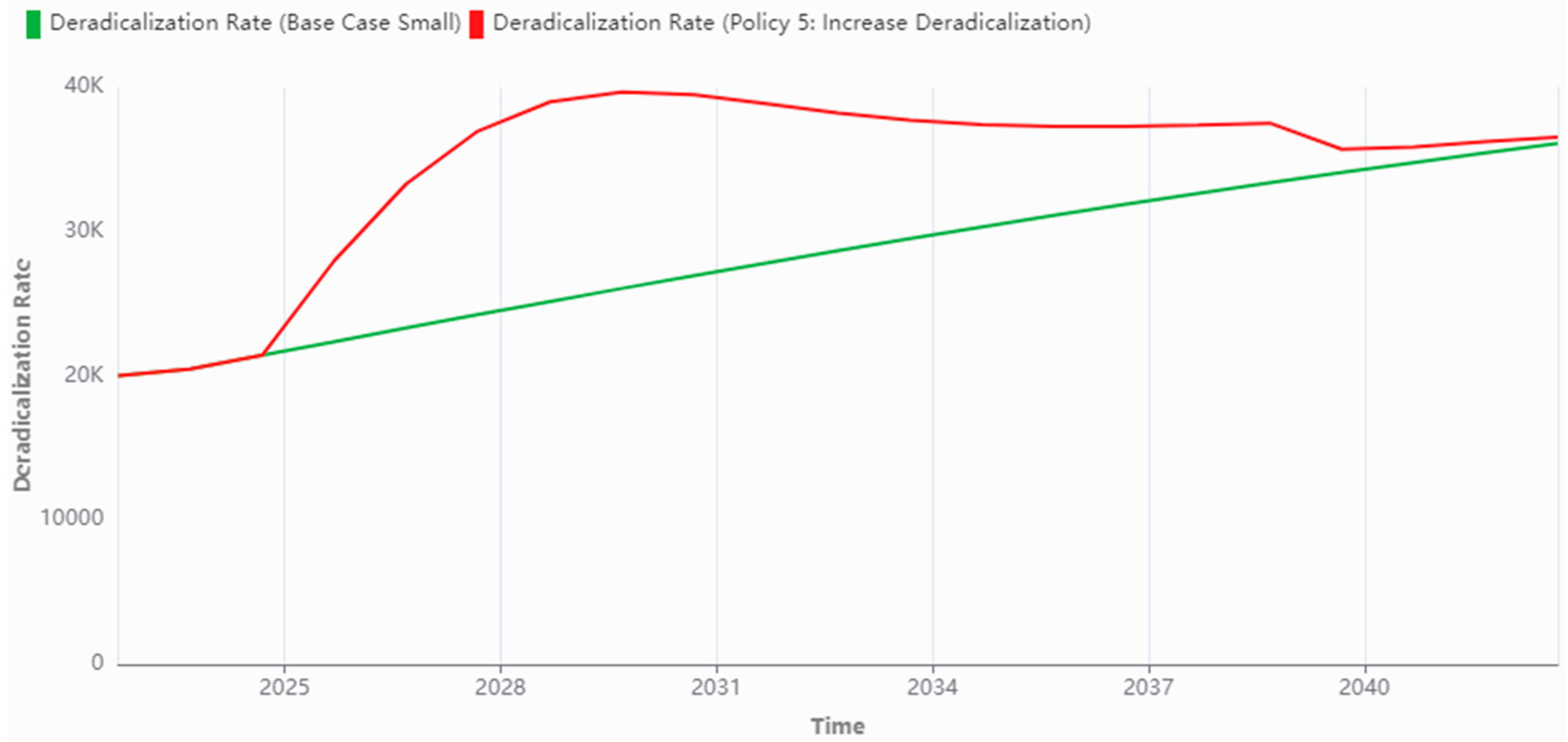
| Policy 5: Increase Deradicalization (Small Terror Group) | Deradicalization Over Time is increased by 0.05 per tick, starting from tick 2, until a maximum of 0.7. | Casualties drops from 3966 to 3258; Lone Wolves drops from 18 to 5; Radicalized Individuals drops from 180,496 to 40,605. |
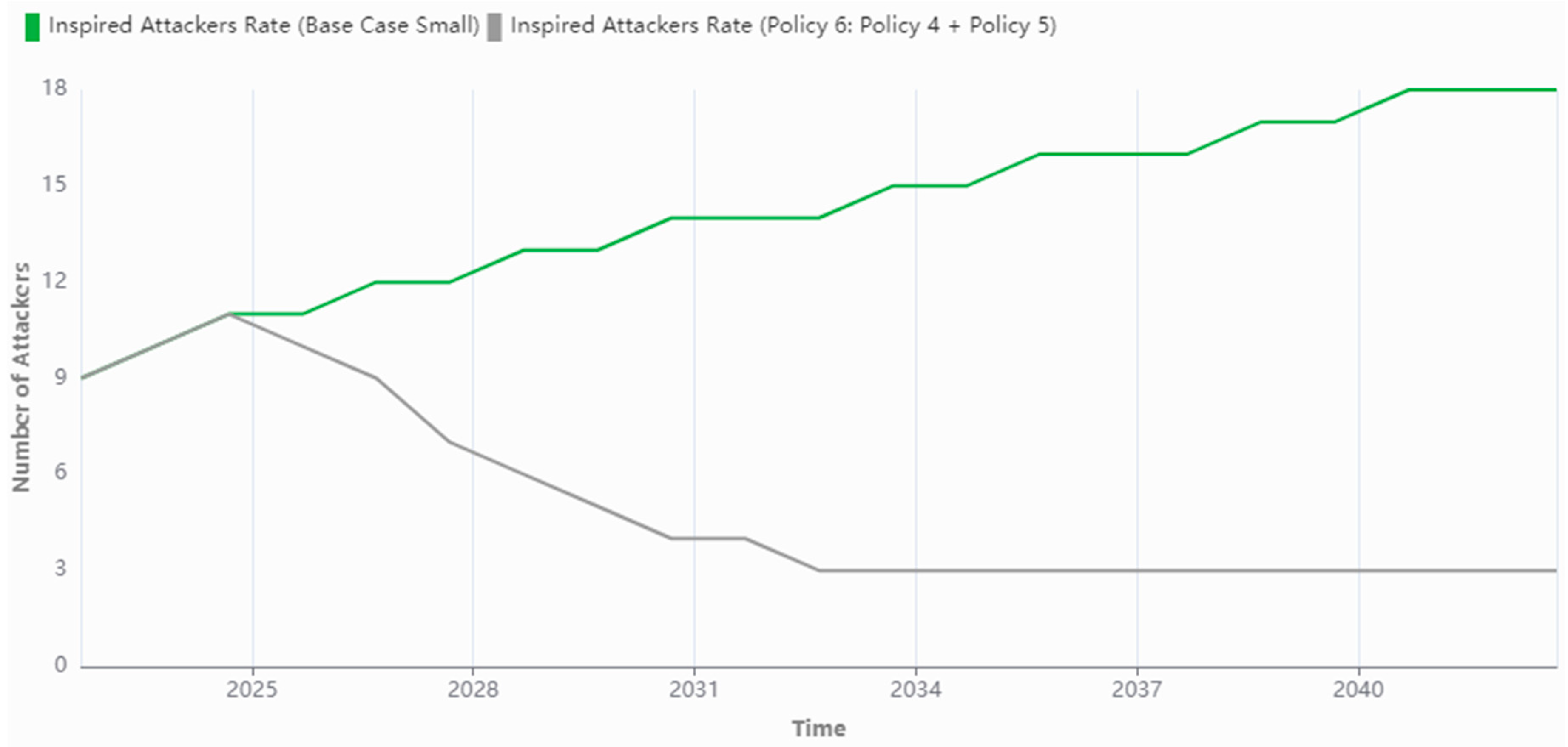
| Policy 6: Reduce Digital Contact & Increase Deradicalization (Small Terror Group) | Digital Contact has been halved at tick 1 and reduced to 0 from tick 2 onwards; Deradicalization Over Time is increased by 0.05 per tick, starting from tick 2, until a maximum of 0.7. | Casualties drops from 3966 to 2940; Lone Wolves drops from 18 to 3; Radicalized Individuals drops from 180,496 to 22,635; At Risk Individuals increases from 373,989 to 530,996. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
De Angelis, T.; Armenia, S.; De Angelis, A. Reducing Terrorism Casualties: Analyzing Policies Effectiveness under a Systems Perspective. Systems 2023, 11, 199. https://doi.org/10.3390/systems11040199
De Angelis T, Armenia S, De Angelis A. Reducing Terrorism Casualties: Analyzing Policies Effectiveness under a Systems Perspective. Systems. 2023; 11(4):199. https://doi.org/10.3390/systems11040199
Chicago/Turabian StyleDe Angelis, Thomas, Stefano Armenia, and Angelo De Angelis. 2023. "Reducing Terrorism Casualties: Analyzing Policies Effectiveness under a Systems Perspective" Systems 11, no. 4: 199. https://doi.org/10.3390/systems11040199
APA StyleDe Angelis, T., Armenia, S., & De Angelis, A. (2023). Reducing Terrorism Casualties: Analyzing Policies Effectiveness under a Systems Perspective. Systems, 11(4), 199. https://doi.org/10.3390/systems11040199








