Abstract
Confusion, diffusion, and encryption keys affect the quality of image encryption. This research proposes combining bit- and pixel-level permutation and substitution methods based on three advanced chaotic logistic map methods. The three chaotic methods are the 2D Logistic-adjusted-Sine map (2D-LASM), the 2D Logistic-sine-coupling map (2D-LSCM), and the 2D Logistic ICMIC cascade map (2D-LICM). The encryption method’s design consists of six stages of encryption, involving permutation operations based on chaotic order, substitution based on modulus and bitXOR, and hash functions. Hash functions are employed to enhance key space and key sensitivity quality. Several testing tools are utilized to assess encryption performance, including histogram and chi-square analysis, information entropy, correlation of adjacent pixels, differential analysis, key sensitivity and key space analysis, data loss and noise attacks, NIST randomness tests, and TestU01. Compared to using a single 2D logistic map, the amalgamation of bit-level and pixel-level encryption and the utilization of three 2D cascade logistic maps has improved encryption security performance. This method successfully passes the NIST, TestU01, and chi-square tests. Furthermore, it outperforms the previous method regarding correlation, information entropy, NPCR, and UACI tests.
1. Introduction
Image encryption is the process of securing an image by converting the original image into an unreadable form. Without an appropriate decryption key, the image cannot be restored and understood [1,2]. Image encryption aims to protect the privacy and security of images, especially in situations where images are sensitive and confidential, such as medical [3,4], and military [5] images. In the context of encryption methods, Shannon’s theory emphasizes the importance of the two main concepts of confusion and diffusion [3,6,7]. Combining these two concepts aims to create a strong dependency between encrypted data and encryption keys. Confusion in the encryption process makes the statistical relationship between the original and encrypted images complex and challenging to predict, while diffusion distributes information in its original form evenly and efficiently to all parts of the encrypted image. Both confusion and diffusion can be achieved in the encryption method by performing intensive permutations and substitutions for each pixel and/or image bit. Permutation involves randomizing the order of bits or pixels in an image [8], aiming to hide the statistical relationship between pixels in an image. Substitution is carried out by changing the bit or pixel value in the image with a different value. Substitution can be carried out using various methods such as substitution-box (S-box) [9,10,11,12], XOR [13,14], and modulus [15,16] operations. With increasingly chaotic patterns of permutations and substitutions, it will be more complex and difficult to predict. Therefore, a combination of permutations and substitutions must be performed at the bit- and pixel level.
The important thing to note in the encryption method is the key. Keys play a critical role in the security and confidentiality of encrypted data. Therefore, the key must fulfil several requirements, such as uniqueness, randomness, length or space, and complexity [17,18,19]. This is so that the input key from the user to encrypt the image needs to be processed first to generate a more complex key, such as a Pseudorandom Number Generator (PRNG) [5,20] and hash function [21]. However, these keys can also be compromised with chosen plaintext attacks if only standard operations are performed, such as stream image shuffling (permutation), image blocking, and sub-image encryption [22]. More complex and combined operations can certainly improve security. In today’s modern image encryption, keys, including the chaotic method, can be made very complex. In the key terminology, the chaotic method is used to produce chaotic sequences. Chaotic sequences are susceptible to initial conditions, with different initial parameters resulting in entirely different chaotic sequences, thus providing a very high level of security [18,19,23,24]. The chaotic method has many variations, some famous for image encryption, such as the logistic map, Henon map, Tent map, Arnold map, and Lorentz system [6]. Others include memristive hyperchaotic maps [25] and their development for 3D settings [26]. Focus on the logistic map method. This method has been developed and has several derivatives such as an Improved Logistic Map (ILM) [7], 2D Logistic-adjusted-Sine map (2D-LASM) [27], 2D Logistic-sine-coupling map (2D-LSCM) [28], and 2D Logistic ICMIC cascade map (2D-LICM) [29]. Derivatives from the logistic map have several advantages, namely an increase in the Lyapunov exponent (LE), which enhances randomness and sensitivity, resulting in a more chaotic, unique, and secure sequence. Of the four logistic map derivatives, 2D-LASM, 2D-LICM, and 2D-LSCM have the advantage of having more dimensions and higher complexity. Based on the literature, this study has the following objectives and contributions:
- Proposing a combination of 2D-LASM, 2D-LICM, and 2D-LSCM to improve image encryption security based on various assessments.
- Proposing a combination of substitution and permutation techniques based on chaotic sequences at the bit and pixel levels in six stages to improve confusion and diffusion quality.
- Using a hash function on the private key to produce greater key space before using it to generate a chaotic sequence.
The rest of this paper is written in several sections, namely: related work, which goes into more detail about the hypotheses and work related to this research; a section outlining the proposed approach, which explains the stages in the proposed method; the results and discussion section, which presents research results, discussions, and comparisons with related methods; and lastly is the conclusion, which presents conclusions and research suggestions.
2. Related Work
The previous sections have discussed the importance of confusion and diffusion qualities in image encryption, which are implemented through permutation and substitution processes. Another aspect to note is the quality of the encryption keys. Literature related to the development of permutation and substitution techniques and the improvement of key qualities has motivated this research. Initially, permutation and/or substitution encryption methods were applied only to pixels. Furthermore, permutations and substitutions at the bit level have become a trend, as seen in studies [27,29,30,31,32,33]. Bit-level encryption can be carried out on the bit plane or by directly converting the image into bits for the encryption process. One simple method is proposed by [33], which involves the conversion of the RGB image into a bit form. First, the image channels are split, then each channel is converted into a bit form and integrated. After integration, permutation-diffusion is carried out using the chaotic tent map method. Study [31] also employs a fairly simple bit-level technique, namely the bit swapping method and the modulus operation with the piecewise linear chaotic map (PWLCM).
Study [30] employs a more complex algorithm on grayscale images. The image matrix is converted using the bit-plane decomposition technique and then transformed into a vector form. Next, the diffusion process is carried out with cyclic shift permutation and modulus substitution functions for confusion. The diffusion and confusion stages are conducted in several rounds. The results are transformed into a bit-plane form and finally restored into an encrypted image matrix. Further research [29] proposed an improved method, with the main contribution being the use of 2D-LICM, which possesses a much higher Lyapunov exponent (LE) value than the standard logistic map. Encryption is accomplished by converting the image into bit-plane decomposition, followed by cyclic shift and XOR operations on rows and columns based on 2D-LICM. Furthermore, the encrypted bits are reassembled into an encrypted image matrix. Apart from 2D-LICM, other methods have also been developed, such as 2D-LASM [27], whose LE is also better than the standard logistic map. A study [32] introduces a new combined chaotic system (NCCS) based on three chaotic models, namely the Logistic-Sine map, Logistic-Tent map, and Sine-Tent map. These three chaotic models are combined with a hash function to generate the keystream. During the encryption stage, two levels of bit confusion and one label bit diffusion are carried out.
Pixel-level image encryption is proposed once again by [13]. Although it appears simple, the advantage of this method lies in its potential implementation in future quantum computing technology. Hilbert scrambling and XOR operations are performed to encrypt the image. The combination of bit- and pixel-level encryption is proposed in the studies [28,34,35,36]. Study [34] proposes four levels of encryption. The first involves pixel-level permutation, the second is a new permutation, the third is column permutation, and finally, the fourth is the bitXOR-based diffusion block. These four levels utilize the same chaotic method, namely PWLCM. Another study [28] suggests 2D-LSCM for performing two levels of image encryption. The first level is based on scrambling using 2D-LSCM on rows and columns of image pixels. The second level also employs 2D-LSCM on the rows and columns of image bits. Study [35] introduces the Logistic-Chebyshev map (LCM) and employs the SHA-512 hash operation to enrich the keys pace. The encryption operations conducted in this study include row and column scrambling on pixels, circular shift on bit-planes, and XOR diffusion. Study [36] proposes image encryption by combining the Hilbert curve, cyclic shift, and 2D Henon map. The Hilbert curve is utilized for pixel permutations, cyclic shifts are employed for bit permutations, and 2D Henon maps are used for diffusion processes.
Based on the reviewed research above, it is apparent that the proposed encryption methods are generally developed using bit-level encryption techniques with reliable chaotic methods such as [27,29,30,31,32,33]. Furthermore, a combination of bit- and pixel-level encryption was developed [28,34,35,36]. We conclude that chaotics such as 2D-LASM, 2D-LICM, and 2D-LSCM have the potential to achieve better encryption quality if combined at both the bit- and pixel levels. Additionally, the use of the hash function will increase the key space. Thus, 2D-LASM, 2D-LICM, 2D-LSCM, and the hash operation are proposed in this study. A more detailed description of the proposed method is presented in Section 3.
3. Proposed Approach
The approach suggested in this research involves integrating three distinct types of chaotic maps, namely 2D-LASM, 2D-LSCM, and 2D-LICM. These chaotic methods are utilized in the permutation and substitution processes, operating at both the bit- and pixel levels across six encryption stages. Figure 1 illustrates the proposed method, while the specific details of the method are outlined as follows:
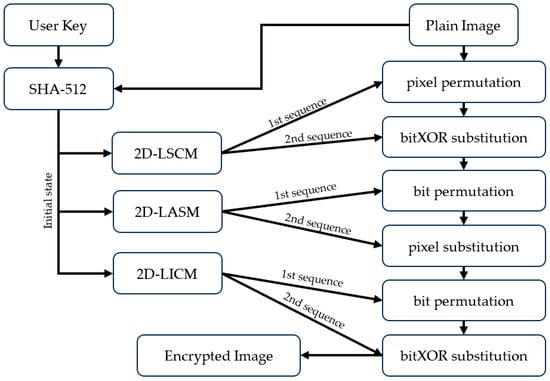
Figure 1.
Illustration of proposed encryption method.
- Read the user key and plain image as input for the SHA-512 hash function, and the output is 64 characters each, i.e., and .
- Generate initial value ( for 2D-LSCM, ( for 2D-LASM, and ( for 2D-LICM. To generate these, use Equations (1)–(6).
- Generate chaotic sequence-based 2D-LSCM using Equation (7).where , , and .
- Generate chaotic sequence-based 2D-LASM using Equation (8).where , , and .
- Generate chaotic sequence-based 2D-LICM using Equation (9).where , , , and .
- Each 2D-LSCM, 2D-LASM, and 2D-LICM has two sequences. Sort the first sequence of 2D-LSCM. Based on the sorting index, perform pixel permutation to perform first-stage encryption.
- In the second stage of encryption, first transform the second sequence 2D-LSCM with Equation (10). Next, perform bitXOR substitution between the encrypted first stage image and the transformed second sequence of 2D-LSCM.where second sequence of 2D-LSCM () , is a symbol of the bitXOR operator.
- In the third stage, encryption is conducted using bit-level permutation, so the encrypted second-stage image () needs to be converted to binary form. At this stage, sort the first 2D-LASM sequence. Then, perform permutation based on the sorting index.
- The image, which is still in binary form, is restored to decimal form () to perform pixel substitution in the fourth stage. At this stage, the second sequence of 2D-LASM must be converted with Equation (11), then carry out the modulus operation with Equation (12).where second sequence of 2D-LASM () , .
- The bit-level permutation is performed in the fifth stage based on the first 2D-LICM sequence. Then, the image is converted back into binary form, then sorting the first 2D-LICM sequence. Then, perform a permutation based on the first 2D-LICM index sorting sequence in the encrypted fourth-stage image ().
- Restore the encrypted fifth stage image to decimal form, then convert the second sequence from 2D-LICM with Equation (13). Then, perform the bitXOR operation on the encrypted fifth stage image () with the second sequence from 2D-LICM to obtain the final encrypted image (), see Equation (14).where second sequence of 2D-LICM () , .
The encryption method proposed above has six stages consisting of one pixel-level permutation stage, two bit-level permutation stages, a one-pixel substitution stage, and two bitXOR substitution stages. Meanwhile, perform image decryption can be performed with the reverse step.
4. Results and Discussion
The experiments conducted in this research were performed using Matlab R2021a, an i7 11th gen processor with 16 GB of memory. Two types of images were tested, namely 8-bit grayscale and 24-bit color (red, green, and blue) images. The images used were standard test images and random samples from the BossBase dataset. The image dimensions were 512 × 512 pixels, and a sample image used is presented in Figure 2. It is important to note that the proposed method is primarily designed for 8-bit images. The channels are separated first for color images, and then the proposed method is applied to each channel. After encryption, all channels are combined into one encrypted color image. Sample encrypted results for grayscale images are shown in Figure 3, while Figure 4 displays the results for color images. To assess image encryption security, several tests, such as histogram and chi-square , entropy, correlation coefficient, differential, key space, and key sensitivity analysis. The NIST and TestU01 randomness suite tests, noise and data loss attacks, and ablation studies are conducted, as presented in Section 4.1, Section 4.2, Section 4.3, Section 4.4, Section 4.5, Section 4.6, Section 4.7, Section 4.8, Section 4.9 and Section 4.10.
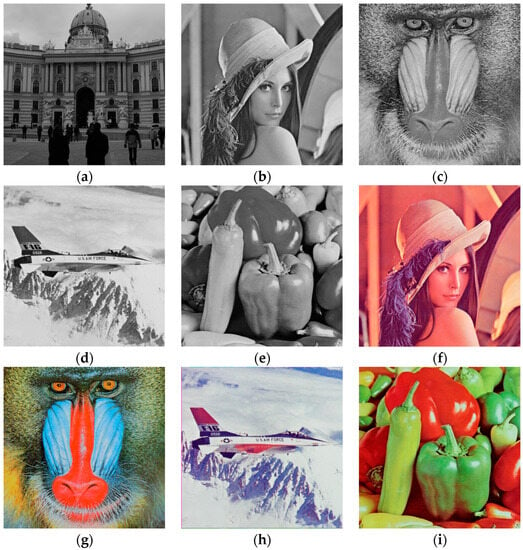
Figure 2.
Sample image dataset. (a) 1013.pgm; (b) Lena grayscale; (c) baboon grayscale; (d) airplane grayscale; (e) peppers grayscale; (f) Lena color; (g) baboon color; (h) airplane color; and (i) peppers color.
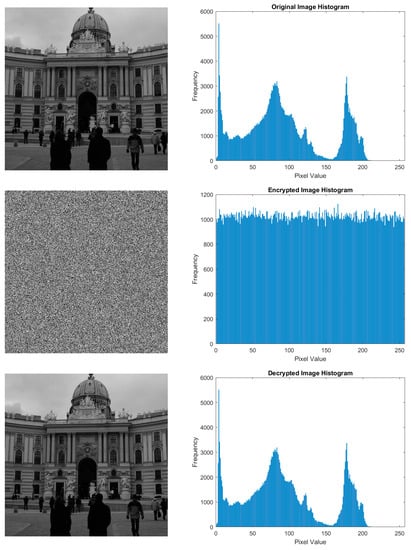
Figure 3.
Sample results of grayscale image (row 1: original image; row 2: encrypted image; row 3: decrypted image).
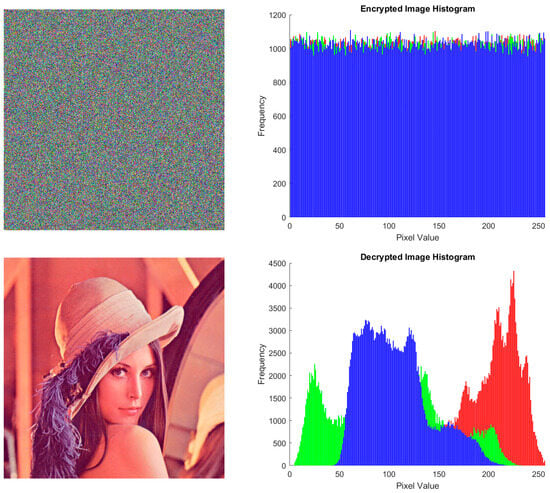
Figure 4.
Sample results of the color image (row 1: original image; row 2; encrypted image; row 3: decrypted image).
4.1. Histogram and Chi-Square () Test
The image histogram is a visual representation of the pixel intensity distribution in the image. Histograms can provide important information about image characteristics, including contrast, brightness, intensity distribution, and color variation. In the context of image encryption, the image histogram needs to change significantly. Besides that, the histogram distribution must be nearly uniform. The histogram of the encrypted image presented in Figure 3 and Figure 4, row 2, appears visually uniform. However, validation of histogram uniformity was carried out using analysis. If the calculated value is less than or equal to 293.2478 with a significance level () of 0.05 and freedom degrees () of 255, it indicates that the histogram is considered to be uniformly distributed. Equation (15) is used to calculate the chi-square value.
In Matlab, the index range for is from 1 to 256, as it starts indexing from 1. The grey recurrence value () represents the value assigned to each occurrence of the ith grey value.
Based on the results presented in Table 1, all image histograms are confirmed to be uniform. This is evidenced by the value, which is smaller than 293.2478. This also proves that the performance of the proposed encryption method is excellent based on the histogram and chi-square analysis. As a note, for RGB images, the chi-square value is taken from the mean value of the R, G, and B channels.

Table 1.
Chi-square test results.
4.2. Correlation Coefficient of Adjacent Pixel Test
Analyzing the correlation coefficient () between adjacent pixels is a technique employed to assess the level of interdependence between neighboring pixels in an image following the encryption process. This analysis evaluates the level of randomness or irregularity in the arrangement of encrypted pixels. In addition, this analysis can indicate patterns or structures that still exist in encrypted images. The range of measurements is −1 to 1. A value closer to −1 or 1 shows an inverse or high correlation, while the optimal value is close to zero. A value closer to zero indicates the minimum correlation, signifying encryption at the highest level of randomness. Equation (16) is used to calculate the .
Equation (16) uses the symbol to represent the total number of pixels in the image. The variables and refer to two neighboring pixels positioned diagonally, horizontally, or vertically. and represent the expectations or average values of and , respectively. Figure 5 represents a sample of the correlation coefficient of adjacent pixels plot results.
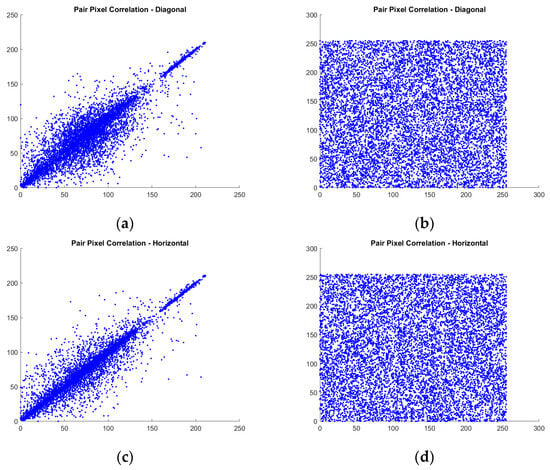
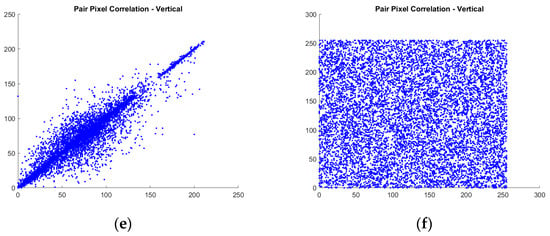
Figure 5.
Sample results of plot correlation coefficient of adjacent pixels of 1013.pgm image: (a) diagonal of the original image; (b) diagonal of encrypted image; (c) horizontal of the original image; (d) horizontal of encrypted image; (e) vertical of the original image; (f) vertical of encrypted image.
The results presented in Table 2 show that all images correlate closely to zero. This indicates that the proposed method performs well based on the analysis. In Table 3, a correlation comparison with related work is also carried out on the Lena image, and it can be seen that the proposed method has the best correlation value in the vertical direction because it is closest to zero. However, compared to related methods, the proposed method is superior in diagonal correlation (marked with bold text), while horizontal and vertical correlation is the second best (marked with underlined text). It can also be seen that no related method excels at all correlation values, while the proposed method holds a relative advantage across all correlation values. As a note, the correlation value is taken from the average value of the R, G, and B channels for RGB images.

Table 2.
The correlation coefficient of adjacent pixel results of the encrypted image.

Table 3.
Comparison of correlation coefficient of the adjacent pixel of encrypted Lena Image (grayscale).
4.3. Information Entropy Test
Entropy measures the level of randomness or uncertainty in data distribution. In image encryption terminology, entropy can be used to evaluate the effectiveness of encryption methods to measure the degree of randomness or uncertainty in data distribution. The entropy of 8-bit images generally has a range of 0 to 8, where high entropy means an increasingly random distribution of pixel values, making it difficult to guess the actual pixel value. Conversely, low entropy indicates a clear pattern or dependency between pixel values, making the image vulnerable to statistical attacks. Entropy can be measured by Equation (17).
where H is entropy, which is calculated to involve the total number of symbols (), the information of the source (encrypted image) represented by , and the probability of occurrence of the represented by .
Based on the results presented in Table 4, all images have very high entropy values: the lowest is 7.9993 and the highest is 7.9994. It can also be concluded that the entropy value is very stable, both in grayscale and RGB images. In RGB images, the entropy value presented is the mean value of all channels. The results presented in Table 5 also confirm that the proposed method has an advantage in entropy values compared to related methods.

Table 4.
Information entropy results.

Table 5.
Comparison of information entropy of encrypted Lena image.
4.4. Key Sensitivity Test
The key sensitivity test is essential in image encryption, and its purpose is to evaluate the sensitivity of the encryption to small changes in the encryption key. During image encryption, a transformation occurs in the original image, which the encryption key affects. By introducing variations to the encryption key, key sensitivity tests examine the impact of these changes on the resulting encrypted image. To test key sensitivity, at least two encryptions are performed on an image with different keys. This difference is generally a single bit, which can be at the key’s start, end, or middle. The sample test results presented in Figure 6 confirm that the proposed method satisfies the requirements of this test, as even a single-bit difference results in significant variation, making precise image decryption impossible.
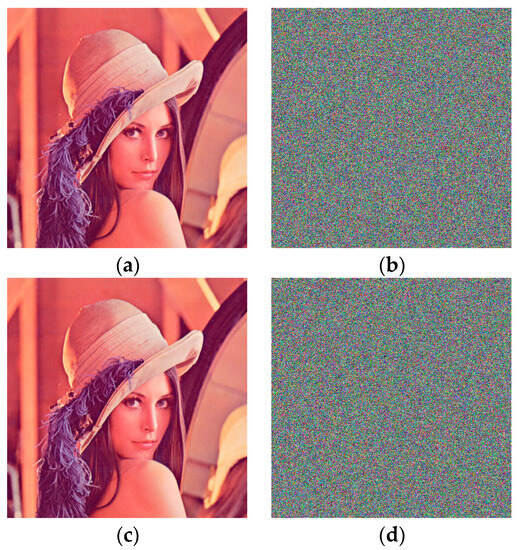
Figure 6.
Sample results of key sensitivity decryption test: (a) original image; (b) encrypted image; (c) decrypted image with correct key; (d) decrypted image with single-bit key modification.
4.5. Differential Test
The differential test in image encryption is a crucial evaluation process commonly employing the Normalized Pixel Change Rate (NPCR) and Unified Average Changing Intensity (UACI) metrics. NPCR assesses the impact of changes in the encryption key on the resulting encrypted image by calculating the percentage of differing pixels between two encrypted images generated using slightly different encryption keys. A higher NPCR value indicates that even slight changes in the encryption key lead to significant variations in the encrypted image. On the other hand, UACI measures the average intensity changes in encrypted images caused by modifications in the encryption key. UACI quantifies the difference in pixel intensity between two encrypted images produced using slightly different encryption keys. A higher UACI value signifies those alterations in the encryption key result in notable intensity changes in the encrypted image. The optimal NPCR value is approximately 99.6094%, while the ideal UACI value is around 33.4635%. Equations (18) and (19) are utilized to calculate NPCR and UACI, respectively.
where and represent the original cipher and the altered cipher, respectively. and correspond to the width and height dimensions, respectively, and and indicate the coordinates of individual pixels.
Based on the NPCR and UACI tests, the proposed method produces an average NPCR and UACI value that is very close to the ideal value, see Table 6. The average NPCR value is 99.9060, the difference is only 0.0004 from the ideal NPCR value. Meanwhile, the average UACI value is 33.4611, and the difference is only 0.0024. This indicates that the performance based on NPCR and UACI is very satisfying. Based on Table 7, the NPCR value of the proposed method outperforms the related methods. Meanwhile, UACI is the second best.

Table 6.
NPCR and UACI results.

Table 7.
Comparison of NPCR and UACI of Lena image.
4.6. NIST Randomness Test
The National Institute of Standards and Technology (NIST) developed a series of tests that are used to assess the randomness or random nature of a data or bit stream. This randomness test serves as a standard for measuring the security of cryptographic algorithms. The NIST randomness test comprises 15 statistical tests, which include tests such as the frequency test, run test, run-bit test, long-term test, and others. For each test, a p-value is generated ranging from 0 to 1. To assess the effectiveness of encryption and ensure compliance with test standards, each test requires a sequence of at least 106 bits and must generate a p-value greater than 0.01 to pass. In terms of image encryption, the results of image encryption can be directly tested. The encrypted image must first be converted into a binary file, then saved with the .dat extension. This .dat file is input for testing through a series of NIST tests. The test results, including the average p-values of all encrypted images, are documented in Table 8. The statistical test results obtained from the NIST tool indicate that the proposed method successfully passed all tests and demonstrated resistance to various attacks. The results presented in Table 8 confirm that the proposed method successfully passed all tests, as evidenced by the average p-value of all tests being greater than 0.49.

Table 8.
Average NIST randomness test results from all images.
4.7. TestU01
TestU01 is a statistical testing software suite used to assess the quality and randomness of a random number generator [37]. In this case, it is the second chaotic sequence because TestU01 requires integer input and all three are converted, as explained in Section 3. To test the randomness, we use two battery tests, namely Rabbit and Alphabit. Rabbit is a test suite designed to evaluate a random number generator’s correlation between the generated bits. This test consists of 39 different statistical sub-tests to help identify imbalances or patterns in the distribution of bits produced by the generator. Alphabit consists of 17 more general sub-tests involving basic statistical tests and distribution tests to identify abnormalities in the distribution of random numbers. The number of sub-tests in Rabbit and Alphabit is generally used for bitstreams with a length of bits [38,39,40]. The test results presented in Table 9 show that all chaotic sequences have passed all tests and are proven to exhibit randomness that meets the criteria of TestU01.

Table 9.
TestU01 results of -bits length bitstream.
4.8. Data Loss and Noise Attack Test
Data loss and noise attack testing in image encryption is an important process to evaluate the robustness of image encryption methods against attacks that result in data loss. This helps determine how the image encryption method can maintain confidentiality, overcome damage, and ensure data integrity despite data loss or increased noise. Additionally, it can help reveal potential weaknesses in image encryption methods against data loss or noise attacks. In this section, the proposed method is tested, as presented in Figure 7. While, visually, the attack of data loss can be seen, the addition of noise may not be obvious. The results of the description show that the proposed method is able to restore the image in all forms with scattered noise. This test confirms the statistical measurement tools that have been tested, such as chi-square, correlation of adjacent pixels, entropy, differential analysis, and NIST. This is evidenced by the even distribution of noise in the decryption process.
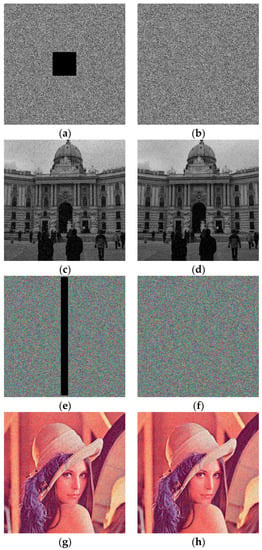
Figure 7.
Sample results of data loss and noise attack: (a) data loss attack of gray image; (b) salt and pepper noise attack (0.05) of gray image; (c) decrypted gray image of data loss attack; (d) decrypted gray image of noise attack; (e) data loss attack of color image; (f) salt and pepper noise attack (0.05) of color image; (g) decrypted color image of data loss attack; (h) decrypted color image of noise attack.
4.9. Key Space Analysis
The analysis of key space plays a crucial role in image encryption as it encompasses the entire range of potential encryption keys utilized within a specific encryption system. In the context of image encryption, the key space holds significant importance since a larger key space presents a greater challenge in guessing the correct encryption key. The key space must be extensive in an effective encryption system to prevent successful brute force attacks. The key space must have or more possibilities [41,42]. The proposed method has several parameters, a dynamic initial value, and a hash operation, from which the proposed method can calculate the key space. The total key space of the proposed method is , as presented in detail in Table 10. This shows that the proposed method will be highly reliable and resistant to brute-force attacks.

Table 10.
Total key space of proposed method.
4.10. Ablation Study
Ablation studies constitute the final part of this section. They are conducted to perform a more in-depth analysis by removing certain components of the proposed encryption method to observe how these changes affect security quality and encryption performance. As explained earlier, the proposed encryption method consists of six stages, with each of the two stages being based on one 2D logistic map. Upon reviewing the results presented in Table 11, one of the weaknesses of the proposed method is its slightly slower encryption time. However, this is reasonable due to combining three 2D logistic maps. Moreover, the encryption time remains reasonable, totaling less than two seconds, with the difference being no more than half a second. Another observation from combining these three 2D logistic maps is the enhancement in all security aspects, as demonstrated by chi-square, IE, CC, NPCR, and UACI assessments. Furthermore, it can be elucidated that the two stages utilizing 2D-LICM have a more significant impact on improving the performance against differential attacks. The two stages employing 2D-LSCM tend to increase IE and CC. Meanwhile, the two stages of 2D-LASM tend to strongly influence the chi-square value. In short, despite the increase in computational time, the proposed method’s combination provides notable encryption security advantages.

Table 11.
Ablation study results.
5. Conclusions
In this study, a proposal has been made to combine the 2D-LASM, 2D-LICM, and 2D-LSCM methods for image encryption. Substitution and permutation techniques are also employed based on chaotic sequences at both the bit- and pixel levels. A hash function is also utilized on the private key to enhance the key space quality before generating a garbled sequence. The test results, encompassing histogram and chi-square analysis, information entropy, adjacent pixel correlation, differential analysis, key sensitivity analysis, key space analysis, data loss, noise attacks, NIST randomness test, and TestU01 test, affirm that the method introduced in this study produced highly satisfactory outcomes. In fact, most of the test results exhibit superior performance when compared to related studies’ test results. Based on these findings, it can be concluded that the proposed method significantly enhances image encryption security. The comprehensive test outcomes demonstrate that this method fulfills essential cryptographic requirements, such as randomness, resistance against attacks, and data loss prevention. Hence, this method has the potential to be a strong contender in meeting the demands for privacy protection and image security. This research could be extended in the future by incorporating a memristive concept to enhance computational efficiency and effectiveness.
Author Contributions
Conceptualization, D.R.I.M.S.; methodology, D.R.I.M.S.; software, N.R.; validation, D.R.I.M.S. and N.R.; formal analysis, D.R.I.M.S.; investigation, D.R.I.M.S.; resources, N.R.; data curation, N.R.; writing—original draft preparation, D.R.I.M.S.; writing—review and editing, N.R.; visualization, N.R.; supervision, D.R.I.M.S.; project administration, N.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Directorate General of Higher Education, Research and Technology of Indonesia, grant number 182/E5/PG.02.00.PL/2023, 026/LL6/PB/AL.04/2023, and 065/A38-04/UDN-09/VII/2023.
Acknowledgments
The author is very grateful to LPPM Dian Nuswantoro University and the Ministry of Education, Culture, Research, and Technology of Indonesia for their support for this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An Overview of Encryption Algorithms in Color Images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Setiadi, D.R.I.M.; Rustad, S.; Andono, P.N.; Shidik, G.F. Digital Image Steganography Survey and Investigation (Goal, Assessment, Method, Development, and Dataset). Signal Process. 2023, 206, 108908. [Google Scholar] [CrossRef]
- Santos, D.F.; Espitia, H.E. Secure Medical Image Transmission Scheme Using Lorenz’s Attractor Applied in Computer Aided Diagnosis for the Detection of Eye Melanoma. Computation 2022, 10, 158. [Google Scholar] [CrossRef]
- Setiadi, D.R.I.M.; Rachmawanto, E.H.; Zulfiningrum, R. Medical Image Cryptosystem Using Dynamic Josephus Sequence and Chaotic-Hash Scrambling. J. King Saud Univ.—Comput. Inf. Sci. 2022, 34, 6818–6828. [Google Scholar] [CrossRef]
- Alnajim, A.M.; Abou-Bakr, E.; Alruwisan, S.S.; Khan, S.; Elmanfaloty, R.A. Hybrid Chaotic-Based PRNG for Secure Cryptography Applications. Appl. Sci. 2023, 13, 7768. [Google Scholar] [CrossRef]
- Andono, P.N.; Setiadi, D.R.I.M. Improved Pixel and Bit Confusion-Diffusion Based on Mixed Chaos and Hash Operation for Image Encryption. IEEE Access 2022, 10, 115143–115156. [Google Scholar] [CrossRef]
- Winarno, E.; Nugroho, K.; Adi, P.W.; Setiadi, D.R.I.M. Combined Interleaved Pattern to Improve Confusion-Diffusion Image Encryption Based on Hyperchaotic System. IEEE Access 2023, 11, 69005–69021. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, D.; Sun, K.; Rawat, U. Color Image Encryption Using Non-Dominated Sorting Genetic Algorithm with Local Chaotic Search Based 5D Chaotic Map. Future Gener. Comput. Syst. 2020, 107, 333–350. [Google Scholar] [CrossRef]
- Alexan, W.; Chen, Y.-L.; Por, L.Y.; Gabr, M. Hyperchaotic Maps and the Single Neuron Model: A Novel Framework for Chaos-Based Image Encryption. Symmetry 2023, 15, 1081. [Google Scholar] [CrossRef]
- Alexan, W.; Alexan, N.; Gabr, M. Multiple-Layer Image Encryption Utilizing Fractional-Order Chen Hyperchaotic Map and Cryptographically Secure PRNGs. Fractal Fract. 2023, 7, 287. [Google Scholar] [CrossRef]
- Jun, W.J.; Fun, T.S. A New Image Encryption Algorithm Based on Single S-Box and Dynamic Encryption Step. IEEE Access 2021, 9, 120596–120612. [Google Scholar] [CrossRef]
- Ramzan, M.; Shah, T.; Hazzazi, M.M.; Aljaedi, A.; Alharbi, A.R. Construction of S-Boxes Using Different Maps over Elliptic Curves for Image Encryption. IEEE Access 2021, 9, 157106–157123. [Google Scholar] [CrossRef]
- Gao, J.; Wang, Y.; Song, Z.; Wang, S. Quantum Image Encryption Based on Quantum DNA Codec and Pixel-Level Scrambling. Entropy 2023, 25, 865. [Google Scholar] [CrossRef] [PubMed]
- Ali, W.; Zhu, C.; Latif, R.; Asim, M.; Tariq, M.U. Image Encryption Scheme Based on Orbital Shift Pixels Shuffling with ILM Chaotic System. Entropy 2023, 25, 787. [Google Scholar] [CrossRef] [PubMed]
- Huang, Z.-W.; Zhou, N.-R. Image Encryption Scheme Based on Discrete Cosine Stockwell Transform and DNA-Level Modulus Diffusion. Opt. Laser Technol. 2022, 149, 107879. [Google Scholar] [CrossRef]
- Bufalo, M.; Bufalo, D.; Orlando, G. Some Properties of the Computation of the Modular Inverse with Applications in Cryptography. Computation 2023, 11, 70. [Google Scholar] [CrossRef]
- Zhao, J.; Wang, S.; Zhang, L. Block Image Encryption Algorithm Based on Novel Chaos and DNA Encoding. Information 2023, 14, 150. [Google Scholar] [CrossRef]
- Moya-Albor, E.; Romero-Arellano, A.; Brieva, J.; Gomez-Coronel, S.L. Color Image Encryption Algorithm Based on a Chaotic Model Using the Modular Discrete Derivative and Langton’s Ant. Mathematics 2023, 11, 2396. [Google Scholar] [CrossRef]
- Abu-Faraj, M.; Al-Hyari, A.; Obimbo, C.; Aldebei, K.; Altaharwa, I.; Alqadi, Z.; Almanaseer, O. Protecting Digital Images Using Keys Enhanced by 2D Chaotic Logistic Maps. Cryptography 2023, 7, 20. [Google Scholar] [CrossRef]
- Choi, U.S.; Cho, S.J.; Kim, J.G.; Kang, S.W.; Kim, H.D. Color Image Encryption Based on Programmable Complemented Maximum Length Cellular Automata and Generalized 3-D Chaotic Cat Map. Multimed. Tools Appl. 2020, 79, 22825–22842. [Google Scholar] [CrossRef]
- Vaidyanathan, S.; Kammogne, A.S.T.; Tlelo-Cuautle, E.; Talonang, C.N.; Abd-El-Atty, B.; Abd El-Latif, A.A.; Kengne, E.M.; Mawamba, V.F.; Sambas, A.; Darwin, P.; et al. A Novel 3-D Jerk System, Its Bifurcation Analysis, Electronic Circuit Design and a Cryptographic Application. Electronics 2023, 12, 2818. [Google Scholar] [CrossRef]
- Ma, Y.; Li, C.; Ou, B. Cryptanalysis of an Image Block Encryption Algorithm Based on Chaotic Maps. J. Inf. Secur. Appl. 2020, 54, 102566. [Google Scholar] [CrossRef]
- Mfungo, D.E.; Fu, X.; Xian, Y.; Wang, X. A Novel Image Encryption Scheme Using Chaotic Maps and Fuzzy Numbers for Secure Transmission of Information. Appl. Sci. 2023, 13, 7113. [Google Scholar] [CrossRef]
- Ciylan, F.; Ciylan, B.; Atak, M. FPGA-Based Chaotic Image Encryption Using Systolic Arrays. Electronics 2023, 12, 2729. [Google Scholar] [CrossRef]
- Lai, Q.; Yang, L.; Liu, Y. Design and Realization of Discrete Memristive Hyperchaotic Map with Application in Image Encryption. Chaos Solitons Fractals 2022, 165, 112781. [Google Scholar] [CrossRef]
- Lai, Q.; Wan, Z.; Zhang, H.; Chen, G. Design and Analysis of Multiscroll Memristive Hopfield Neural Network with Adjustable Memductance and Application to Image Encryption. IEEE Trans. Neural Netw. Learn. Syst. 2022, 1–14. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. Image Encryption Using 2D Logistic-Adjusted-Sine Map. Inf. Sci. 2016, 339, 237–253. [Google Scholar] [CrossRef]
- Demirtaş, M. A New RGB Color Image Encryption Scheme Based on Cross-Channel Pixel and Bit Scrambling Using Chaos. Optik 2022, 265, 169430. [Google Scholar] [CrossRef]
- Cao, C.; Sun, K.; Liu, W. A Novel Bit-Level Image Encryption Algorithm Based on 2D-LICM Hyperchaotic Map. Signal Process. 2018, 143, 122–133. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A Novel Bit-Level Image Encryption Algorithm Based on Chaotic Maps. Opt. Lasers Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
- Hasheminejad, A.; Rostami, M.J. A Novel Bit Level Multiphase Algorithm for Image Encryption Based on PWLCM Chaotic Map. Optik 2019, 184, 205–213. [Google Scholar] [CrossRef]
- Zhou, W.; Wang, X.; Wang, M.; Li, D. A New Combination Chaotic System and Its Application in a New Bit-Level Image Encryption Scheme. Opt. Lasers Eng. 2022, 149, 106782. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Meng, J. A Chaotic Color Image Encryption Using Integrated Bit-Level Permutation. Multimed. Tools Appl. 2018, 77, 6883–6896. [Google Scholar] [CrossRef]
- Patro, K.A.K.; Acharya, B. Secure Multi–Level Permutation Operation Based Multiple Colour Image Encryption. J. Inf. Secur. Appl. 2018, 40, 111–133. [Google Scholar] [CrossRef]
- Wang, X.; Du, X. Pixel-Level and Bit-Level Image Encryption Method Based on Logistic-Chebyshev Dynamic Coupled Map Lattices. Chaos Solitons Fractals 2022, 155, 111629. [Google Scholar] [CrossRef]
- Shahna, K.U.; Mohamed, A. A Novel Image Encryption Scheme Using Both Pixel Level and Bit Level Permutation with Chaotic Map. Appl. Soft Comput. J. 2020, 90, 106162. [Google Scholar] [CrossRef]
- L’Ecuyer, P.; Simard, R. TestU01. ACM Trans. Math. Softw. 2007, 33, 1–40. [Google Scholar] [CrossRef]
- Trujillo-Toledo, D.A.; López-Bonilla, O.R.; García-Guerrero, E.E.; Esqueda-Elizondo, J.J.; Cárdenas-Valdez, J.R.; Tamayo-Pérez, U.J.; Aguirre-Castro, O.A.; Inzunza-González, E. Real-Time Medical Image Encryption for H-IoT Applications Using Improved Sequences from Chaotic Maps. Integration 2023, 90, 131–145. [Google Scholar] [CrossRef]
- De la Fraga, L.G.; Ovilla-Martínez, B. A Chaotic PRNG Tested with the Heuristic Differential Evolution. Integration 2023, 90, 22–26. [Google Scholar] [CrossRef]
- Yang, Z.; Liu, Y.; Wu, Y.; Qi, Y.; Ren, F.; Li, S. A High Speed Pseudo-Random Bit Generator Driven by 2D-Discrete Hyperchaos. Chaos Solitons Fractals 2023, 167, 113039. [Google Scholar] [CrossRef]
- Wu, J.; Liao, X.; Yang, B. Color Image Encryption Based on Chaotic Systems and Elliptic Curve ElGamal Scheme. Signal Process. 2017, 141, 109–124. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, J. A Multidimensional Chaotic Image Encryption Algorithm Based on DNA Coding. Multimed. Tools Appl. 2020, 79, 21579–21601. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).