1. Introduction
The development of new information technologies is accompanied by negative phenomena such as industrial espionage, computer crimes, and unauthorized access to confidential information.
Due to humans’ growing dependence on information technology and the need to ensure information security, the protection of information, including the use of cryptographic methods, has become important for society as a whole.
Modern cryptography is a specific research area at the intersection of mathematics and computer science, which forms one of the main subsystems of any information security system. Of the means of cryptographic protection, symmetric block ciphers have gained widespread popularity due to their practicality.
A strong block cipher must satisfy certain conditions. These conditions are formulated in [
1], which is fundamental in the theory of encryption. A strong cipher must have confusion and diffusion properties. Confusion hides the relationship between the ciphertext and the key, while diffusion hides the relationship between the ciphertext and the plaintext.
To meet the requirements for block ciphers, modern encryption algorithms use various cryptographic transformations. This also applies to linear transformations, including MDS matrices over finite fields.
As a result of scientific developments, new-generation algorithms with the SP-network structure have appeared. The general design of these algorithms is a variant of the substitution–permutation network (SP network). This network uses an iterative transformation consisting of a substitution layer (non-linear elements), a linear (mixing) layer, and a key adding layer. By transforming the entire data block at each iteration, this design provides much faster mixing of the input vector compared to the Feistel network. This effect is enhanced by an MDS matrix (Maximal Distance Separable matrix) in the linear layer. This matrix provides the maximum possible dependence of the bits of the output vector on the bits of the input, and it is used in linear transformations in many well-known encryption algorithms [
2].
In [
3], a new method for estimating the integral property, truncated, and impossible differentials for substitution–permutation network (SPN) block ciphers is proposed. This method was tested only for truncated algorithms.
The paper [
4] considers the structure and properties of a cryptographic information protection algorithm model based on non-positional polynomial notations (NPNs) and constructed on the basis of a SP network. Taking into account the properties of the NPN, the speed of the algorithm in the case of its implementation was not considered.
In symmetric block algorithms, a well-tested MDS transform is used as a linear transformation block. It gives the best diffusion properties. MDS codes (Maximum Distance Separable codes) are mainly used to multiply an original text vector by some matrix of constants, which is usually called an MDS matrix [
5]. The scheme for generating subkeys (round keys) of known algorithms has the following disadvantages:
- –
The ability to restore the master key using one subkey;
- –
Fairly simple dependencies between subkeys (vulnerability to attacks on related keys);
- –
The first of the subkeys is the master key;
- –
The weak influence of changes in the master key bits on the bits of the first subkeys;
- –
Use in the unfolding scheme of another design, different from the cyclic function;
- –
Different complexity of generating a sequence of subkeys for encryption and decryption.
When designing block algorithms, their structural components, such as
S-boxes, Boolean functions, and polynomials, play an important role. Depending on their characteristics and properties, block algorithms provide a certain level of security. In [
6], the influence of the properties of
S-boxes on the reliability of algorithms is considered.
The article [
7] presents differential cryptanalysis of the Boron block cipher. The authors use differentials consisting of several differential characteristics with the same input and output differences. Each characteristic that corresponds to a given differential increases its overall probability.
By evaluating the strength of round key algorithms, potential loopholes in the overall encryption process can be anticipated. The paper [
8] proposes a criterion for estimating the cryptographic strength of round key algorithms. This criterion includes various methods for generating data from subsections and a suitable set of statistical tests.
Quantum cryptography or quantum key distribution is considered one of the information technologies capable of shaping the image of the telecommunications networks of the future. It allows two parties connected over an open communication channel to create a common random key known only to them and use it to encrypt and decrypt messages. The authors of [
9] were devoted to ensuring the security of quantum key distribution. The article, which consists of ten chapters, describes almost all practical aspects of security in creating and breaking quantum code. The conclusion includes a systematic and staged presentation of the research results. Technical aspects related to phase synchronization, which provides a high key transfer rate, are studied in [
10]. When using single-photon sources in the Z-basis, their protocol provides security up to a higher error rate by establishing non-trivial mutual information between the bit-flip and phase error patterns, thereby achieving a higher key rate. In the history of the development of quantum cryptography, the quantum digital signature also plays an important role. Existing quantum digital signature schemes use non-orthogonal quantum states distributed as “quantum signatures”. Modern schemes allow a message to be securely signed so that one or more recipients can be sure of its authenticity. The use of quantum digital signatures and their exchange protocols is described in more detail in [
11,
12].
Thus, when developing a symmetric block encryption algorithm, it is necessary to take into account the features of the cryptographic procedures mentioned above. As a rule, when creating a new algorithm or modifying an existing encryption algorithm, its properties are first analyzed.
2. Materials and Methods
When constructing ciphers, the main issue is to ensure their strength. So far, there is no complete theory of block ciphers, which would allow the development of a full-fledged method for evaluating strength. Only some general requirements for the quality of encryption transformations are proposed. If the cipher satisfies such requirements, then we speak of provable security (against known methods of cryptanalysis) or the achievement of guaranteed properties of ciphering transformations.
The main methods for evaluating the strength of cryptographic algorithms include the assessment of their statistical security. Statistical tests are used to experimentally evaluate whether a ciphertext is as good as a random sequence in its properties.
The following test suites are known: NIST, CRYPT-X, DIEHARD, TESTU01, and test sets by Donald Knuth and Ali Doganaksoy. They are used to study the statistical properties of cryptographic primitives and make it possible to obtain a preliminary estimate of cryptographic strength.
To analyze the reliability of block encryption algorithms, powerful attacks such as linear and differential cryptanalysis have been developed [
13,
14]. Knowledge of these methods of analysis makes it possible, even at the design stage of ciphers, to provide for their excessive security and exclude the possibility of their breaking via these techniques.
The goal of linear cryptanalysis is to find the next “efficient” linear expression for a given encryption algorithm:
where
and
denote fixed bit positions, and Equation (1) is satisfied with probability
p ≠ ½ for an arbitrarily given plaintext A corresponding to ciphertext
C and key
K.
Linear cryptanalysis is implemented in two steps. The first is to build relationships between the plaintext, the ciphertext, and the key that are true, with high probability. The second is to use these relationships, along with known plaintext–ciphertext pairs, to derive the key bits. To estimate linear analysis, we use the following two lemmas [
15].
Lemma 1. (Piling-up lemma). Let be independent random variables whose values are 0 with probabilityor 1 with probability. Then, the probability thatis.
Lemma 2. Let N be the number of given random plaintexts and p be the probability that Equation (1) is satisfied, and letbe sufficiently small. Then, the probability of success of Algorithm 1 is
If it is possible to obtain an effective linear expression, then based on the maximum likelihood method, the following algorithm can determine one bit of the key
:
| Algorithm 1: Steps to determine one bit of the key |
Step 1. Let T be the number of plaintexts, such that the left side of Equation (1) is equal to zero.
Step 2. If T > N/2 (N stands for the number of plaintexts),
then we set = 0 (for p > 1/2) or 1 (for p < 1/2).
Otherwise, = 1 (for p > 1/2) or 0 (for p < 1/2). |
The probability of success of this method obviously increases with increasing N or |p − ½|. Now, consider the most efficient linear expression (i.e., |p − ½| is the maximum) as the best expression and the probability p as the best probability. Then, our main task is the following:
Methods for finding effective linear expressions.
An explicit description of the probability of success in terms of N and p.
Finding the best expression and calculating the best probability.
When designing an encryption algorithm, it is also necessary that the cipher satisfy the avalanche criterion. The avalanche effect is an important cryptographic property for encryption. It means that changing the value of a small number of bits in the input text or the key leads to an avalanche change in the values of the output bits of the ciphertext. To characterize the degree of the avalanche effect in a cryptographic transformation, an avalanche parameter is determined and used: the numerical value of the deviation of the probability of a bit change in the output sequence when a bit in the input sequence changes from the required probability value equal to 0.5.
In this work, we will follow the methodology for analyzing statistical security indicators, described in [
16]. Here, we consider such indicators of statistical security as:
- -
Degree of completeness (dc);
- -
Degree of avalanche effect (da);
- -
Degree of strict avalanche criterion (dsa).
The verification of the statistical security indicators of the cipher begins with the construction of the dependency matrix A and the distance matrix B of the cipher described by the function for a set of X inputs, where X is the set itself or a randomly chosen subset of the set .
If such matrices are constructed, then the degree of completeness is defined as:
The degree of the avalanche effect is defined as:
The degree of the strict avalanche criterion is defined as:
For the avalanche criterion, the value of the avalanche parameter is determined by the formula , where is the number of the changed bit in the input sequence, is the probability of changing half of the bits in the output sequence when the i-th bit at the input changes compared to the original (unchanged) input sequence.
3. Building the AL02 Encryption Algorithm
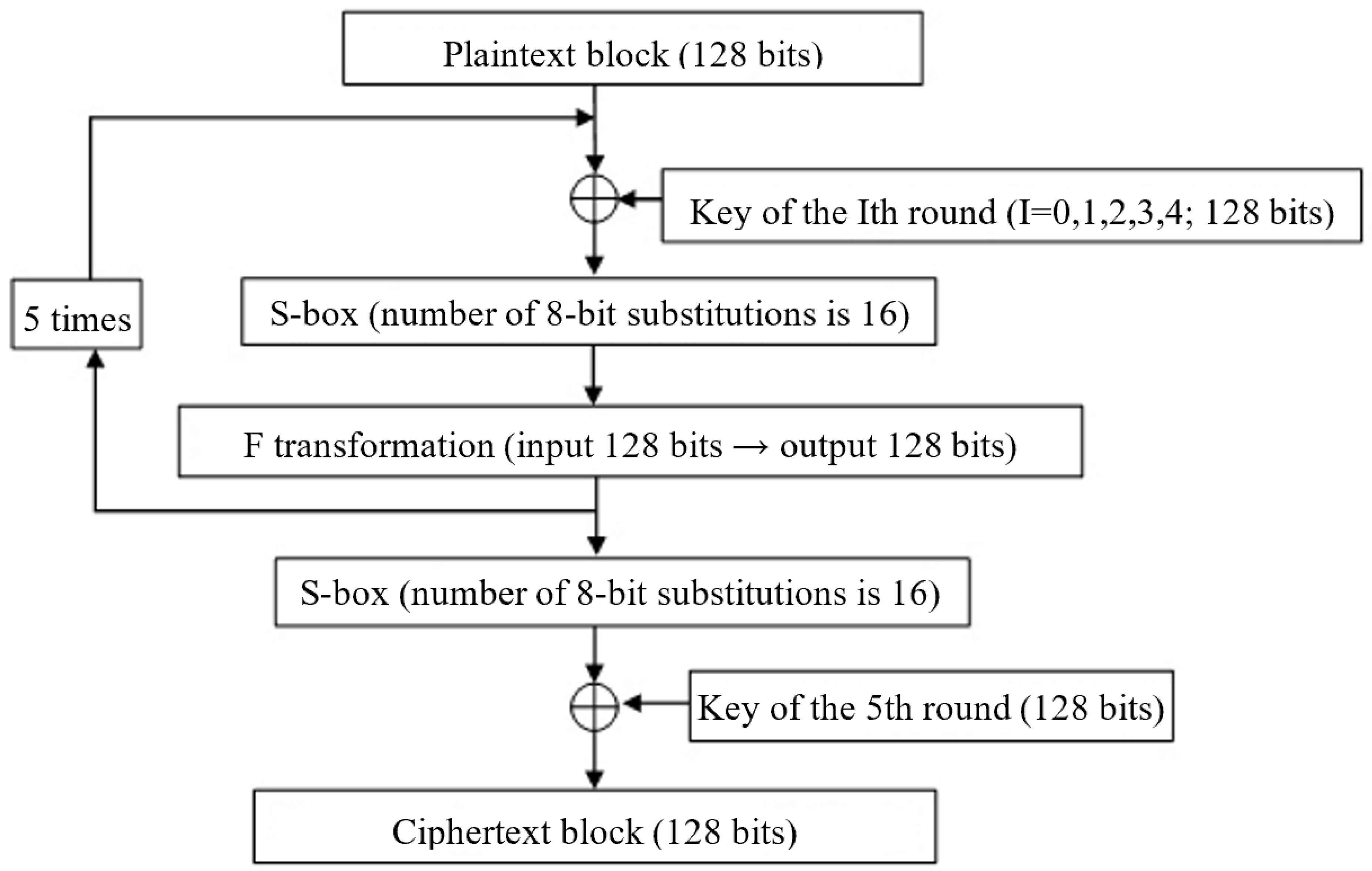
We have developed the AL02 encryption algorithm, which is new in its architecture and meets modern requirements.
Algorithm parameters: the block length is 128 bits. The number of rounds is five. The data size at the input and output of the S-box, which is used in the algorithm as a non-linear function, is 8 bits. The main transformations used are “modulo 2 addition” and S-box substitution, as well as the F transformation based on these two transformations.
The scheme of this algorithm is shown in
Figure 1.
After the fifth round, the encryption result is passed through the S-box, and bitwise addition with the key is performed.
3.1. Encryption
A 128-bit block is an input as a sequence of 16 bytes:
This sequence can be represented as a 4 × 4 square matrix:
The transformation is repeated five times. In the sixth round, the transformation of the obtained values is performed to get an encrypted block.
Thus, each block is encrypted according to the following scheme:
Here, is the plain text, is the ciphertext, is the XOR operation, is the S-box transformation, is a non-linear transformation, and is an intermediate value.
transformation of a block. Take four elements with intermediate values corresponding to each row of the matrix and perform a bitwise addition using the following formula:
that is, the value of the first element is summed modulo 2 with the value obtained by applying the
S-box to the second element and with the value obtained by applying the
S-box to the result of bitwise addition of the third and fourth elements.
The resulting four values are added modulo 2, and the sum is converted using the
S-box, which is taken as the first element of the first row of the matrix:
The remaining elements of the new matrix are calculated as follows.
The second, third, and fourth elements of each row are obtained by applying an
S-box to the result of the bitwise addition of the processed element of the transformed matrix with the previous element of the same row of the transformed matrix:
To get the first element of a row, the
S-box is applied to the result of the bitwise addition of the processed element of the transformed matrix and the last element of the previous row of the transformed matrix:
All elements of the transformed matrix are calculated in the same way.
3.2. Decryption
Text decryption is performed by the sequential processing of 16-byte blocks using inverse transformation. Each block is represented as a 16-byte vector or 4 × 4 square matrix:
or
To obtain a plaintext block, it is necessary to repeat the inverse transformation five times and then perform the transformation using the compositional method.
Each block is decrypted as per the following scheme:
where
is the plain text,
is the ciphertext,
is the XOR operation,
is the inverse
S-box,
is the inverse non-linear transformation, and
is an intermediate value.
(reverse) block transformation: As a result of applying the inverse transformation to the matrix of ciphertext elements, a new matrix is obtained. In reverse transformation, calculations start from the second element of the first row. The inverse
S-box is applied to the second, third, and fourth elements of each row of the matrix to be transformed. After that, bitwise addition is performed with the previous element of the same row, resulting in an element of the transformed matrix located in the same position:
The first element of the second, third, and fourth row is calculated by applying the inverse
S-box to the corresponding element of the matrix to be transformed, and then adding modulo 2 to the last element of the previous row:
B as a result of this transformation, we get all the elements of the resulting matrix, except for the first element in the first row. To get the first element of the first row, the following steps are performed. Starting from the second line, three intermediate values,
,
, and
, are calculated by “modulo 2 addition” of the value of the first element, the value obtained by applying the
S-box to the second element, and the value obtained by applying the
S-box to the bit sum of the third and fourth elements:
The intermediate value
is obtained from the matrix element located at the intersection of the first row and the first column by applying the inverse
S-box to it, and bitwise addition with the other three intermediate values:
To find the first element of the first row of the inverted matrix, the resulting intermediate value
is summed modulo 2 with the two results of applying the
S-box, i.e., with the result of applying the
S-box to the second element of the first row, and the value obtained as a result of applying the
S-box to the bit sum of the second and third elements:
To obtain a plaintext block, it is necessary to repeat the inverse transformation five times using the compositional method.
The method of obtaining the S-box is the same as in the Rijndael encryption algorithm, except for the chosen irreducible polynomials and the matrix for multiplications. As a result of the study, we made sure that when choosing any irreducible polynomial, the cryptographic strength of the S-box does not decrease. However, the row elements of the selected matrix must be linearly independent. The irreducible polynomial , the vector v, and the matrix used to construct the S-box are: , .
Let us show how to get the output element corresponding to each input element of the S-box:
In the field , we get the inverse value for each element.
Next, the following transformation is performed:
where
,
are the coefficients of the obtained inverse elements in the field
.
3.3. Round Key Algorithm
The 128-bit seed key is set randomly. Based on this key, round keys are formed for each iteration of this transformation.
Figure 2 shows the scheme for generating round keys, where G is a non-linear transformation.
G transformation: The value of the initial key is chosen as input for the key transformation. After the input data are defined, we can proceed to the transformation itself.
First, 16 bytes of input data are represented as a 16-byte vector
or a 4 × 4 square matrix
The first element of the first row of the matrix is summed as modulo 2 with the value obtained by applying the S-box to the second element, and with the result of applying the S-box to the sum of the third and fourth elements. The resulting sum is then converted using the S-box.
The resulting value
is added to the first element of the second row, then to the value obtained by applying the
S-box to the second element, and then to the value obtained by applying the
S-box to the bit sum of the third and fourth elements. The resulting bit sum is also converted using the
S-box:
The same steps are repeated for the third and fourth lines:
Next, the byte matrix is represented as a 128-bit sequence and rotated left by 3 bits, and then the 8-bit elements of the resulting sequence are converted using the S-box.
This byte matrix transformation can be represented as follows:
rotate left by three bits and
where the elements
of the transformed matrix are obtained as follows:
where,
As the first element of the first row of the matrix after the key transformation, the value obtained as a result of applying the
S-box to the bit sum of
b3 and
is taken:
The values of the remaining elements of the transformed matrix are obtained by applying the
S-box to the sum of the previous element of the transformed matrix with the corresponding element of the transformed matrix:
To obtain the first elements of the remaining rows of the transformed matrix, it is necessary to calculate the value obtained as a result of applying the
S-box to the bit sum of the last element of the previous row of the transformed matrix with the corresponding element of the transformed matrix:
In this way, all elements of the transformed matrix are calculated. In the case of the key generation algorithm, the key transformation is repeated five times using the compositional method.
When generating round keys, the matrix obtained as a result of a subsequent step of the key transformation is taken as the next round key.
To determine the number of rounds providing non-linearity, each round of the algorithm was considered to evaluate the algebraic normal forms (ANF) of the used permutation functions in the initial 128-bit key space. Since the round keys depend on the initial keys, in each round, the output bit of the ANF is evaluated by the monomial (single term) and the degree of the ANF. To ensure good statistical performance, each ANF should consist of approximately monomials and have a degree of 127. With 128 variables in the ANF, the maximum number of monomials is and the exponent is 128. It was found that in the considered algorithm, after the third round, the output bit in the ANF equation has monomials and a degree of 127. As the number of rounds increases, the number of monomials increases correspondingly. It turned out that five rounds are sufficient for the algorithm.
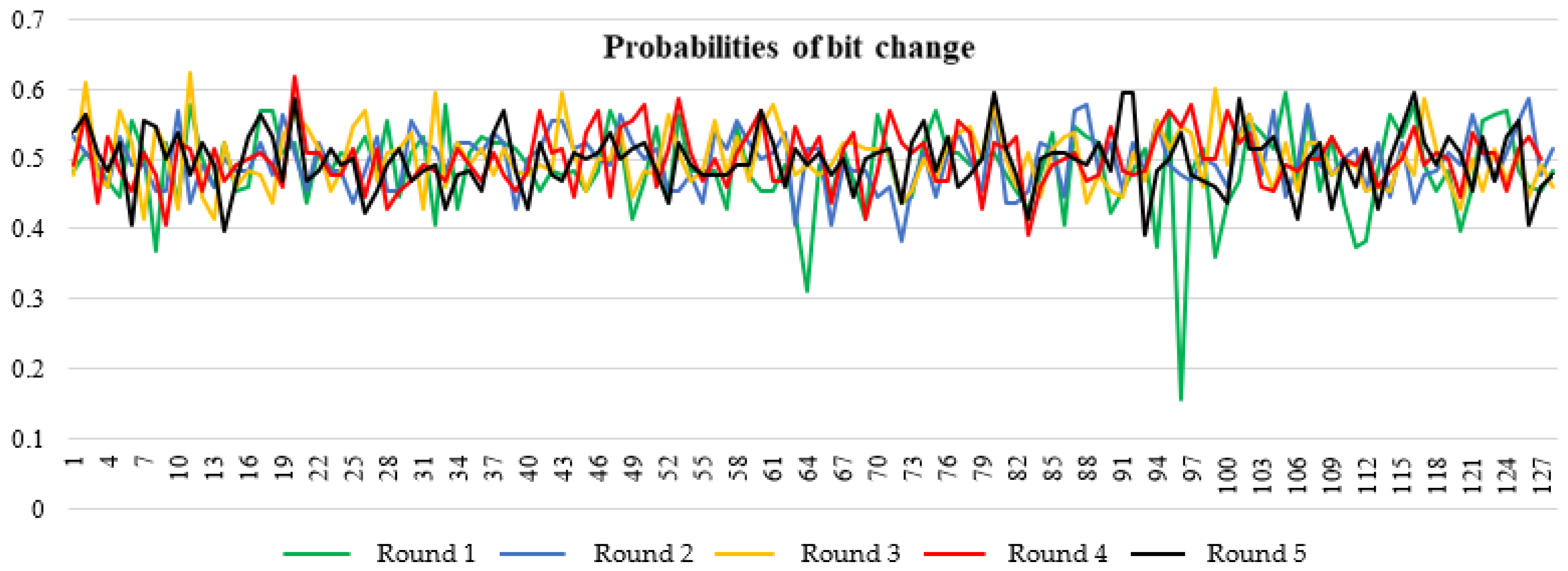
The sufficiency of five rounds was assessed using statistical tests and an avalanche test (
Table 3 and
Figure 3) for one file.
The analysis results shown in
Table 3 show that the AL02 algorithm passes all tests after the third round.
Figure 3 shows data on the “avalanche effect” property with positive results after the second round of encryption. This confirms the adequacy of the established number of rounds of the algorithm.
Table 4 shows an example of encryption for the AL02 algorithm.
Table 5 shows the experimental results of the performance characteristics of different encryption algorithms. The experiment was conducted on a computer with the following parameters: Processor: Intel(R) Core(TM) i7-10700 CPU @ 2.90 GHz 2.90 GHz, RAM: 16.0 GB (available: 15.7 GB), System type: 64-bit operating system Windows 10 Pro.
4. Cryptographic Security Analysis of the Developed Encryption Algorithm
4.1. Statistical Analysis
For a computer study of the developed algorithm, 20 files with different extensions and 5 keys were used. The file characteristics were as follows: 1.docx (108 KB), 2.xls (20.0 KB), 3.pptx (453 KB), 4.pdf (561 KB), 5.rar (1059 KB), 6.zip (1063 KB), 7.jpg (205 KB), 8.png (889 KB), 9.txt (45 KB), 10.html (281 KB), 11.html (17 KB), 12.cat (928 KB), 13.mp4 (39 KB), 14.wmz (70 KB), 15.dll (210 KB), 16.log (508 KB), 17.lex (396 KB), 18.djvu (354 KB), 19. xml (689 KB), and 20 mp3 (193 KB).
Using the selected keys and plaintexts for the developed AL02 symmetric block encryption algorithm, 100 ciphertexts were obtained, which were tested for statistical security. For testing, a developed software package was used, which implements a system for assessing the quality of ciphertexts according to tests from the sets by D. Knuth and NIST-822 STS.
The results of statistical tests for different keys with a probability value of 0.5 and with a probability value of α are shown in
Table 6 and
Table 7.
The number of sequences that successfully passed each of the statistical tests was determined. The significance level α was set as 0.001, 0.01, and 0.05.
The statistical parameters of the ciphertexts were evaluated using the NIST-822 STS package (
Table 8).
For convenience, the experimental verification of the files under study in the NIST-822 CTC environment is presented in the form of a table, the last column of which contains the percentages of the tests passed.
Ciphers with good statistical security indicators should have
,
, and
values satisfying the following conditions:
≈ 1,
≈ 1,
≈ 1 [
16].
Table 9 shows the comparative indicators of the statistical security of the algorithms AL02 and AES128.
4.2. Avalanche Effect
The avalanche effect was tested in two versions. In the first version, 129 blocks of plain texts were used, which differed from each other by one bit. These files were encrypted with the AL02 algorithm using the same key. Then, the encrypted files were checked for a match by the location of the bits. In the second version, the check was carried out for 129 different keys and with one plaintext, where the keys were selected in such a way that they differed from each other by only one bit. The resulting ciphertexts were also checked for matches in terms of bit arrangement. The test results are shown in
Figure 4, where the blue line shows the results of the first option, and the orange line shows the results of the second option.
In the first test, the chi-square value for a degree of freedom of 127 is 62.203, and in the second test, the chi-square value is 77.313.
4.3. Differential Analysis of the AL02 Algorithm
For the differential analysis of the AL02 algorithm, the difference values for each function of a single round are first estimated. The AL02 algorithm consists of an XOR operation, a non-linear transformation using an S-box, and the F-function.
The XOR operation is linear, so the difference has the same value for both the input and the output, so the probability is one. The maximum substitution difference using the S-box is 4, so in this case, the probability will be 2–6.
For the F function of the AL02 algorithm, the finding of the round keys with respect to pairs of ciphertexts and the correspondence with the chosen pair of plaintexts are evaluated.
Differences between selected plaintexts
A and
are presented as a matrix
:
Intermediate values bi and for plaintexts are and . The first element of the first row of the new matrix is:
This implies , , , since the first row of the difference of the new matrices is completely equal to zero. The second row changes depending on the key or plaintext. If one bit of the key or plaintext has been changed, then completely different values are obtained in the second row.
As a result of the differential analysis of the F-function, the maximum probability is 2–12 and the minimum probability is 2–60, so the input of the function is selected in such a way as to minimize the use of the S-box. In this case, the minimum S-box usage is 2 (the maximum S-box usage is 10).
Differential analysis was carried out to obtain the upper bound for each round for the selected pairs of open and closed texts (
Table 10).
This algorithm does not allow us to keep the minimum difference at the input of any of the rounds [
17,
18].
4.4. Linear Analysis
Before performing a linear analysis, the non-linear functions of the algorithm are first examined separately. In the linear analysis table, the considered S-box has significant deviations from the linear approximation, which is equal to 16. The maximum probability of deviation is 0.5625. The overall linear analysis bound is determined by the upper value. Consider each transformation applied in the encryption algorithm. The cipher uses bitwise addition (XOR), substitution (S-box), and cyclic shifts. The bitwise addition operation and cyclic shifts are linear functions.
Lemmas 1 and 2 show that the probability of finding linear equations in one round is
, since the corresponding obtained equations of one round of input and output variables of the linear approximation pass through the
S-box 10 times. Hence, to find a key with a probability of 0.97,
pairs of plaintexts and ciphertexts are required (
Table 11). For the full five rounds, the probability of finding linear equations given 40
S-boxes is
.
Therefore, to determine the key with a probability of 0.97, 2302 pairs of plaintexts and ciphertexts are required.
5. Conclusions
Symmetric cryptographic primitives are widely used due to their high performance and low implementation complexity. Such algorithms use non-linear operations for confusion and linear transformations for diffusion. Consistent repeated application of confusion and diffusion makes it possible to achieve a high level of cryptographic strength. We have developed a new symmetric block cipher algorithm AL02, the architecture of which includes non-linear substitution nodes in the form of substitution tables, the F function, and the round key scheduling algorithm. The advantage of the developed algorithm is the possibility of its effective implementation on specialized equipment designed to perform encryption and decryption operations. Theoretical and experimental tests have shown that the algorithm fully complies with the basic cryptographic requirements. The study of the cryptographic strength of the encryption algorithm will be continued in subsequent works.
The developed algorithm was investigated for reliability using well-known cryptanalysis methods. It was shown that the parameters correspond to the requirements imposed on them.
The algorithm was tested for randomness using statistical tests from the NIST and D. Knuth sets. Based on the study results, it was found that the binary sequence obtained after encryption by the proposed algorithm is close to random. Additionally, the S-box and the AL02 encryption algorithm were tested for the presence of an avalanche effect. Based on the tests and studies carried out, it has been established that the proposed S-box and the AL02 encryption algorithm itself effectively provide a good avalanche effect.
It was also shown that the necessary level of resistance of the developed encryption algorithm to linear and differential cryptanalysis is provided. Research is ongoing to test the reliability of the algorithm against other existing cryptographic attacks.
Author Contributions
Conceptualization, N.K. and D.D.; data curation, N.K.; formal analysis, K.S. and K.A.; funding acquisition, N.K.; investigation, D.D.; methodology, K.A.; project administration N.K.; resources, K.A.; software, K.S.; supervision, K.S.; validation, N.K., K.S. and K.A.; visualization, N.K.; writing—original draft preparation, N.K.; writing—review and editing, D.D. All authors have read and agreed to the published version of the manuscript.
Funding
The research work was funded by the Ministry of Science and Higher Education of Kazakhstan and carried out within the framework of the project AP14870719 “Development and study of post-quantum cryptography algorithms based on hash functions” at the Institute of Information and Computational Technologies.
Data Availability Statement
Not applicable.
Acknowledgments
The authors are grateful to all lab members of “Information security laboratory” (Institute of Information and Computational Technologies) for their useful suggestions and support.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Haitner, I.; Vadhan, S. The Many Entropies in One-Way Functions. In Tutorials on the Foundations of Cryptography. Information Security and Cryptography; Lindell, Y., Ed.; Springer: Cham, Switzerland, 2017; pp. 159–217. [Google Scholar] [CrossRef]
- Panasenko, S.P. Encryption Algorithms; Special Reference-Book; S-P, BHV-Petersburg: Saint Petersburg, Russia, 2009; p. 576. [Google Scholar]
- Zhang, W.; Cao, M.; Guo, J.; Pasalic, E. Improved Security Evaluation of SPN Block Ciphers and its Applications in the Single-key Attack on SKINNY. IACR Trans. Symmetric Cryptol. 2019, 4, 171–191. [Google Scholar] [CrossRef]
- Kapalova, N.; Haumen, A. The model of encryption algorithm based on non-positional polynomial notations and constructed on an SP network. Open Eng. 2018, 1, 140–146. [Google Scholar] [CrossRef]
- Bondarenko, A.; Marshalko, G.; Shishkin, V. GOST R 34.12–2015: What to expect from the new standard? Inf. Secur. 2015, 4, 48–50. [Google Scholar]
- Dragomir, I.; Măluţan, S.; Lazar, M. An analysis of cryptographic algorithm strength based on S-box properties. In Proceedings of the 2019 11th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Pitesti, Romania, 27–29 June 2019; pp. 1–4. [Google Scholar]
- Teh, J.S.; Tham, L.J.; Norziana Jamil, N.; Yap, W. New differential cryptanalysis results for the lightweight block cipher BORON. J. Inf. Secur. Appl. 2022, 66, 103129. [Google Scholar] [CrossRef]
- Afzal, S.; Yousaf, M.; Afzal, H.; Alharbe, N.; Rafiq, M. Mufti Cryptographic Strength Evaluation of Key Schedule Algorithms. Secur. Commun. Netw. 2020, 5, 3189601. [Google Scholar]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.-K.; Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Xie, Y.; Lu, Y.; Weng, C.; Cao, X.; Jia, Z.; Bao, Y.; Wang, Y.; Fu, Y.; Yin, H.; Chen, Z. Breaking the Rate-Loss Relationship of Quantum Key Distribution with Asynchronous Two-Photon Interference. arXiv 2021, arXiv:2112.11635. [Google Scholar] [CrossRef]
- Yin, H.; Fu, Y.; Chen, Z. Practical quantum digital signature. Phys. Rev. A 2016, 93, 032316. [Google Scholar] [CrossRef]
- Lu, Y.S.; Cao, X.Y.; Weng, C.X.; Gu, J.; Xie, Y.M.; Zhou, M.G.; Yin, H.L.; Chen, Z.B. Efficient quantum digital signatures without symmetrization step. Opt. Express 2021, 29, 10162–10171. [Google Scholar] [CrossRef] [PubMed]
- Babenko, L.K.; Ischukova, E.A. Modern Block Cipher Algorithms and Methods for Their Analysis; Helios ARV: Moscow, Russia, 2006; p. 376. Available online: http://www.tnu.in.ua/study/books/entry-1782833.html (accessed on 5 June 2022).
- Vergili, I.; Yücel, M.D. Avalanche and Bit Independence Properties for the Ensembles of Randomly Cho-sen S-Boxes. Turk. J. Electr. Eng. 2001, 2, 137–145. [Google Scholar]
- Matsui, M. Linear Cryptanalysis Method for DES Cipher. In Advances in Cryptology; EUROCRYPT ‘93, LNCS; Helleseth, T., Ed.; Springer: Berlin/Heidelberg, Germany, 23–27 May 1993; pp. 386–397. Available online: https://link.springer.com/content/pdf/10.1007/3-540-48285-7_33.pdf (accessed on 10 September 2022).
- Pascale, S. The Degrees of Completeness, of Avalanche Effect, and of Strict Avalanche Criterion for MARS, RC6, Rijndael, Serpent, and Twofish with Reduced Number of Rounds; Siemens AG, ZT IK 3; KU Leuven, ESAT/COSIC: Leuven, Belgium, 3 April 2000; Available online: https://www.cosic.esat.kuleuven.be/nessie/reports/phase1/sagwp3-003.pdf (accessed on 3 September 2022).
- Dyusenbaev, D.S.; Algazy, K.T.; Sakan, K.S. Study of nonlinear knots used in symmetric ciphers. In Proceedings of the Actual Problems of Information Security in Kazakhstan APIBK-2020, Almaty, Kazakhstan, 11 June 2021; pp. 34–39. Available online: https://conf.iict.kz/wp-content/uploads/2021/06/collection-apibk2021.pdf (accessed on 3 September 2022).
- Algazy, K.T.; Babenko, L.K.; Biyashev, R.G.; Ishchukova, E.A.; Kapalova, N.A.; Nyssanbaeva, S.E.; Smolarz, A. Differential Cryptanalysis of New Qamal Encryption Algorithm. Int. J. Electron. Telecommun. 2019, 66, 647–653. [Google Scholar] [CrossRef]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).