ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management
Abstract
1. Introduction
1.1. Chain-of-Custody Integration with Blockchain
1.2. Blockchain in IoT Digital Forensics
1.3. Blockchain and Cloud Forensics
1.4. Specialized Forensic Systems and Applications
2. Background
2.1. Digital Forensics
2.2. Blockchain
Components of Blockchain
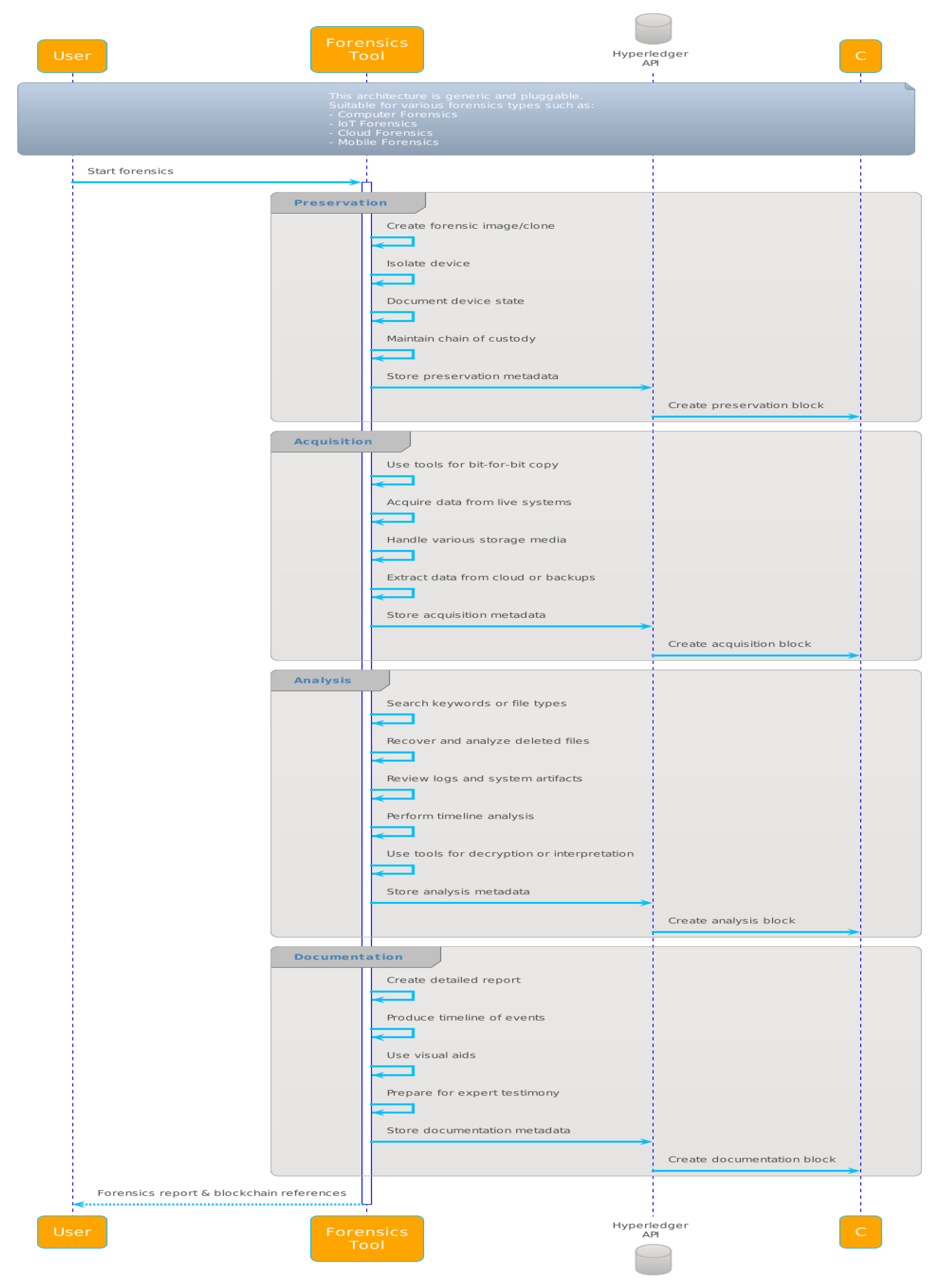
3. Proposed Solution
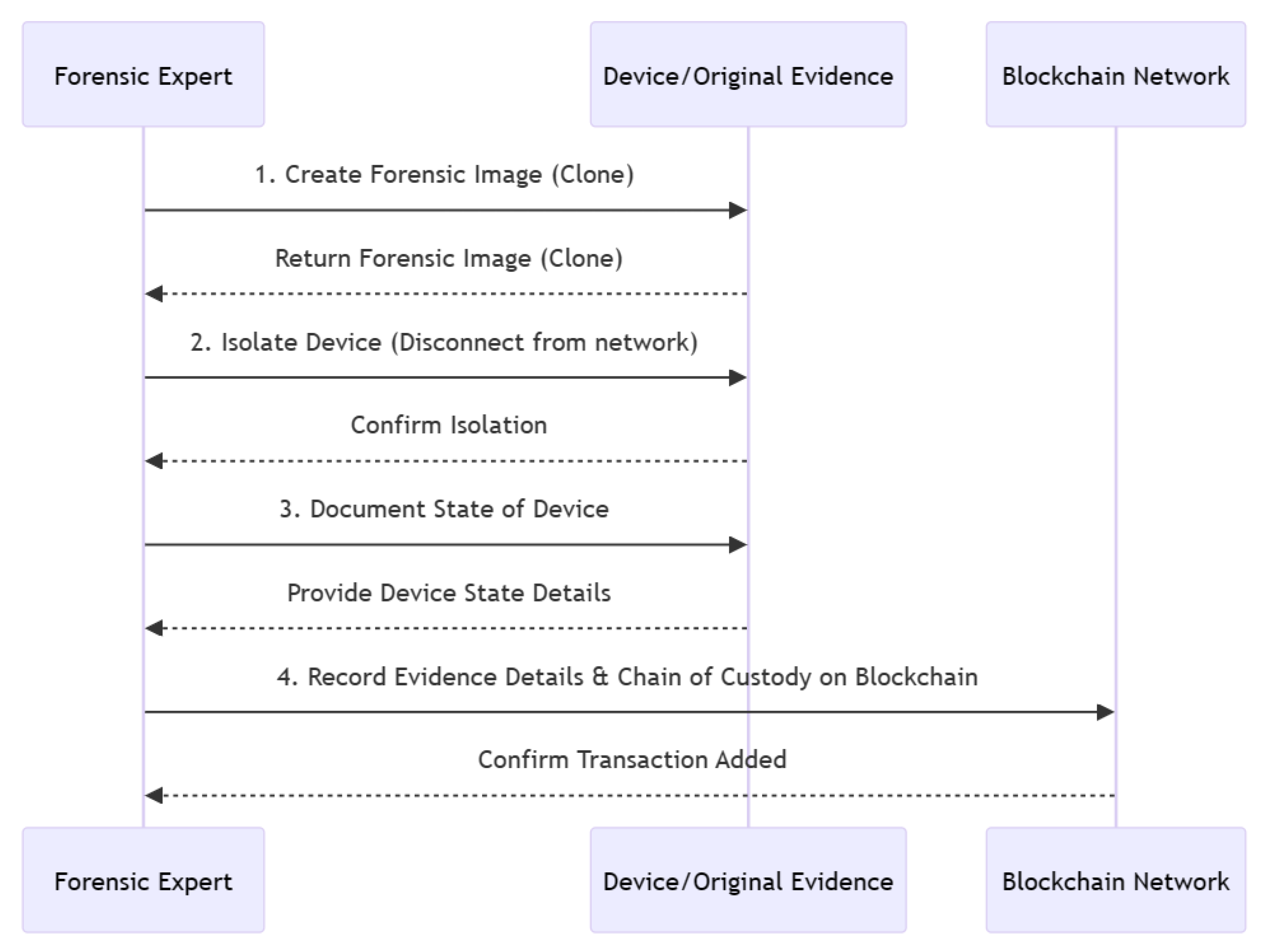
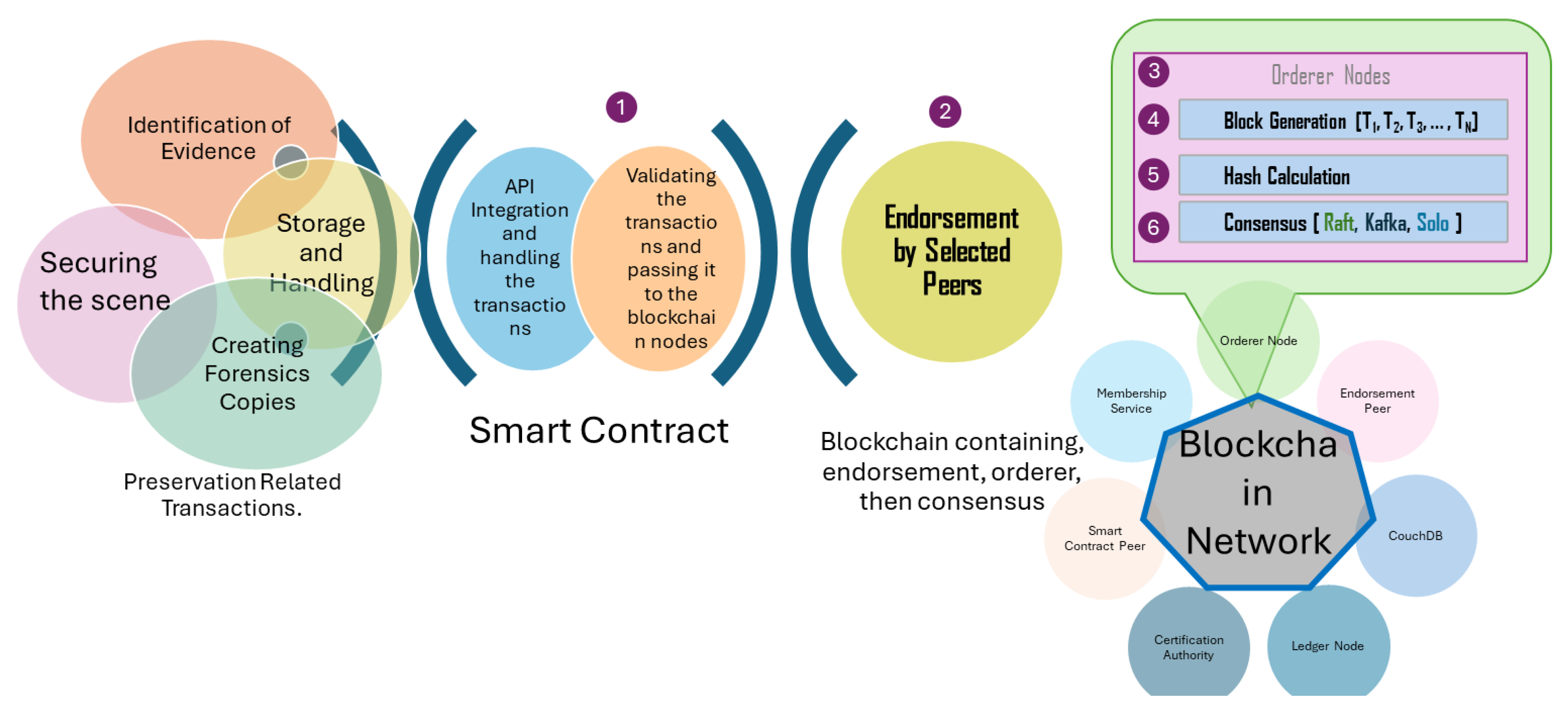
3.1. Data Preservation with Blockchain
Formal Definition

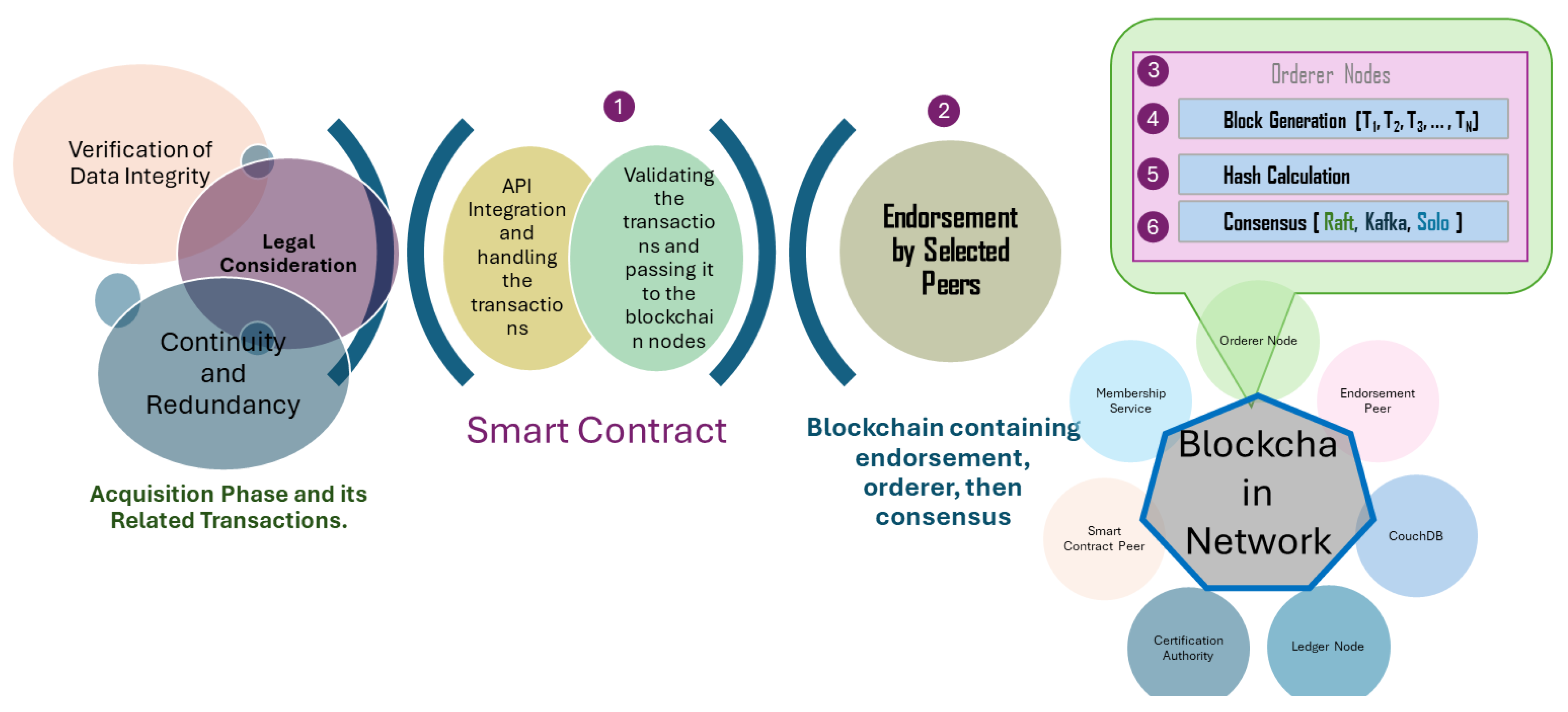
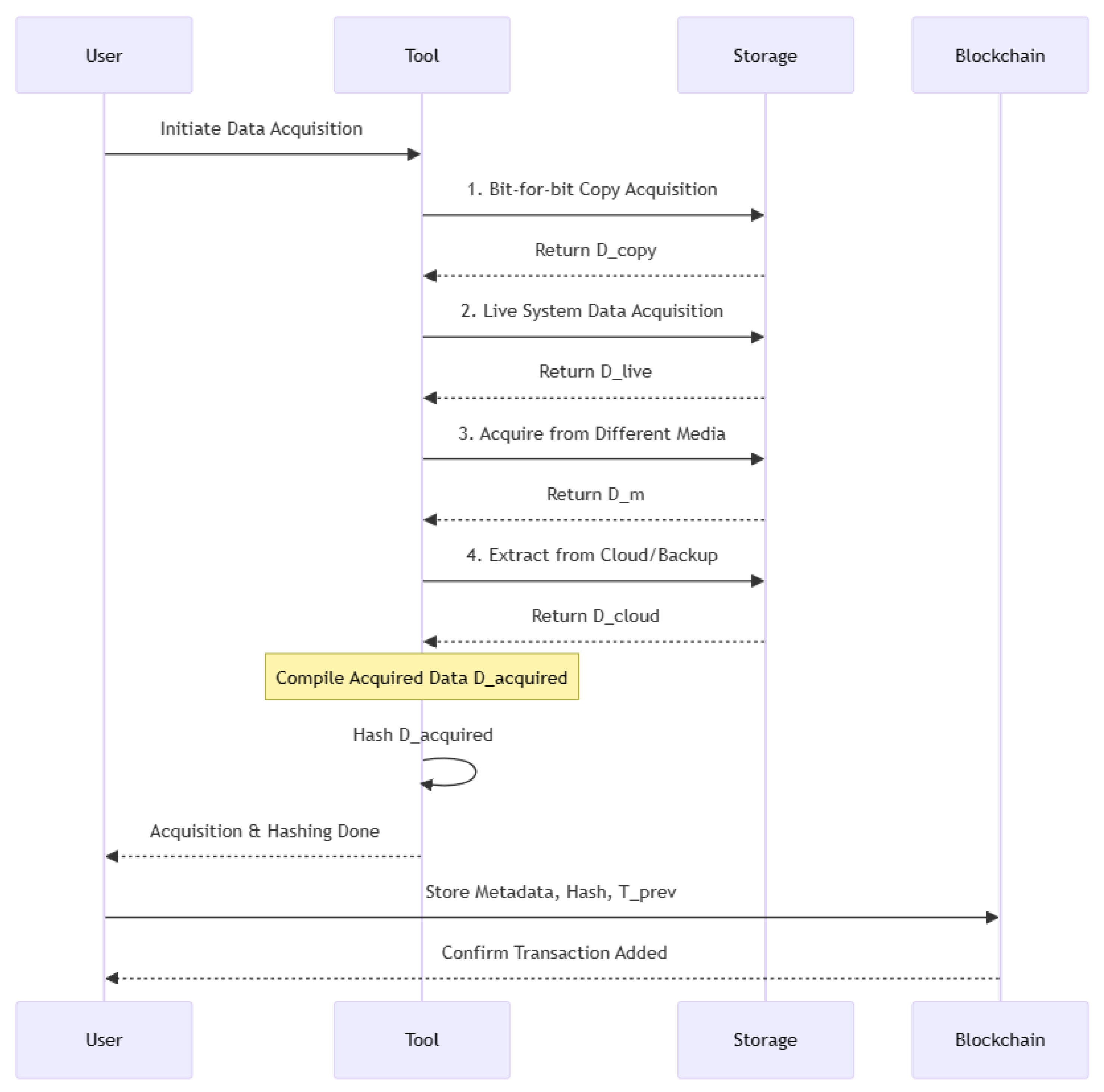
3.2. Data Acquisition with Blockchain
Formal Definition of Acquisition Transactions

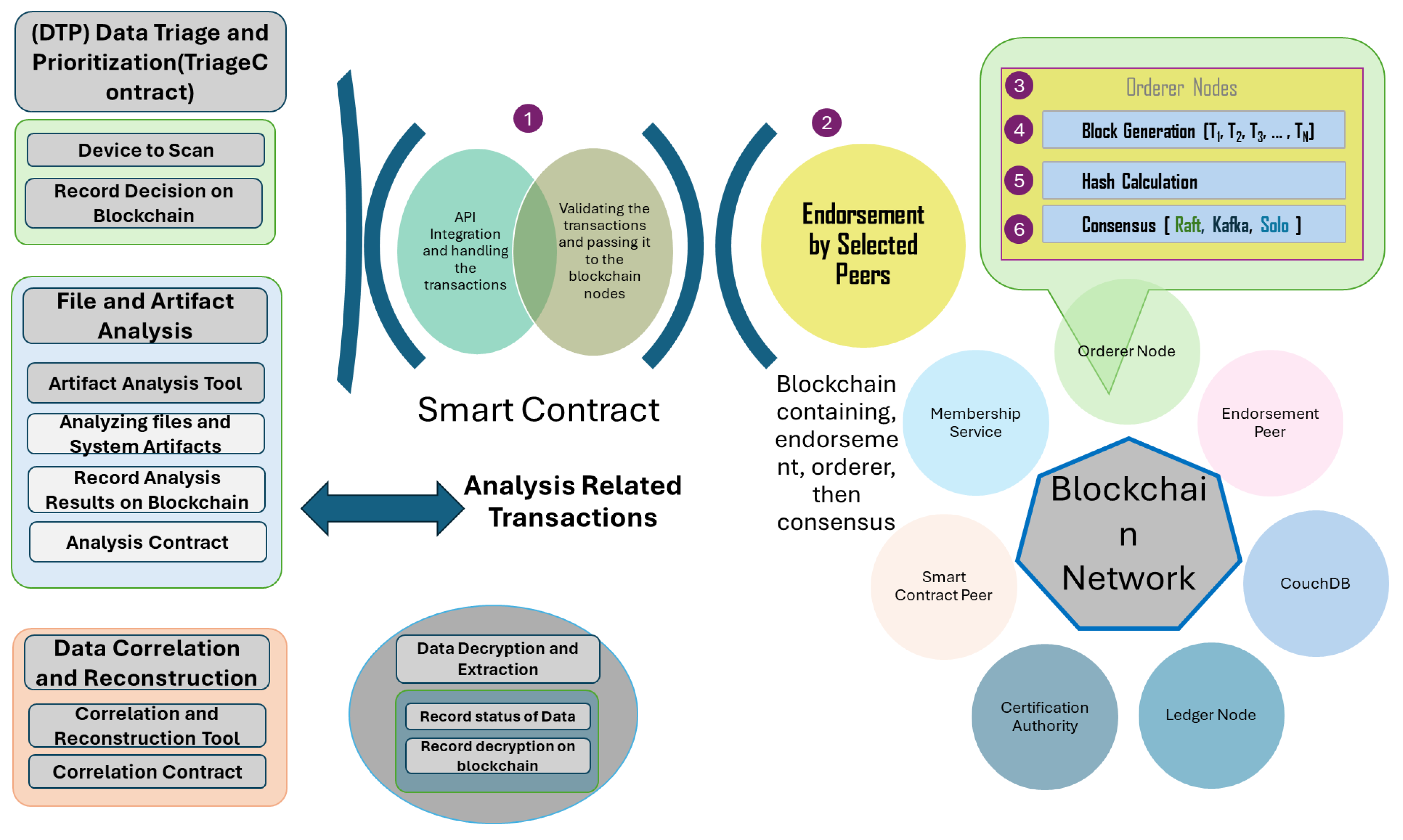
3.3. Analysis-Related Transactions with Blockchain
3.3.1. Formal Definition for Analysis Related Transaction Monitoring
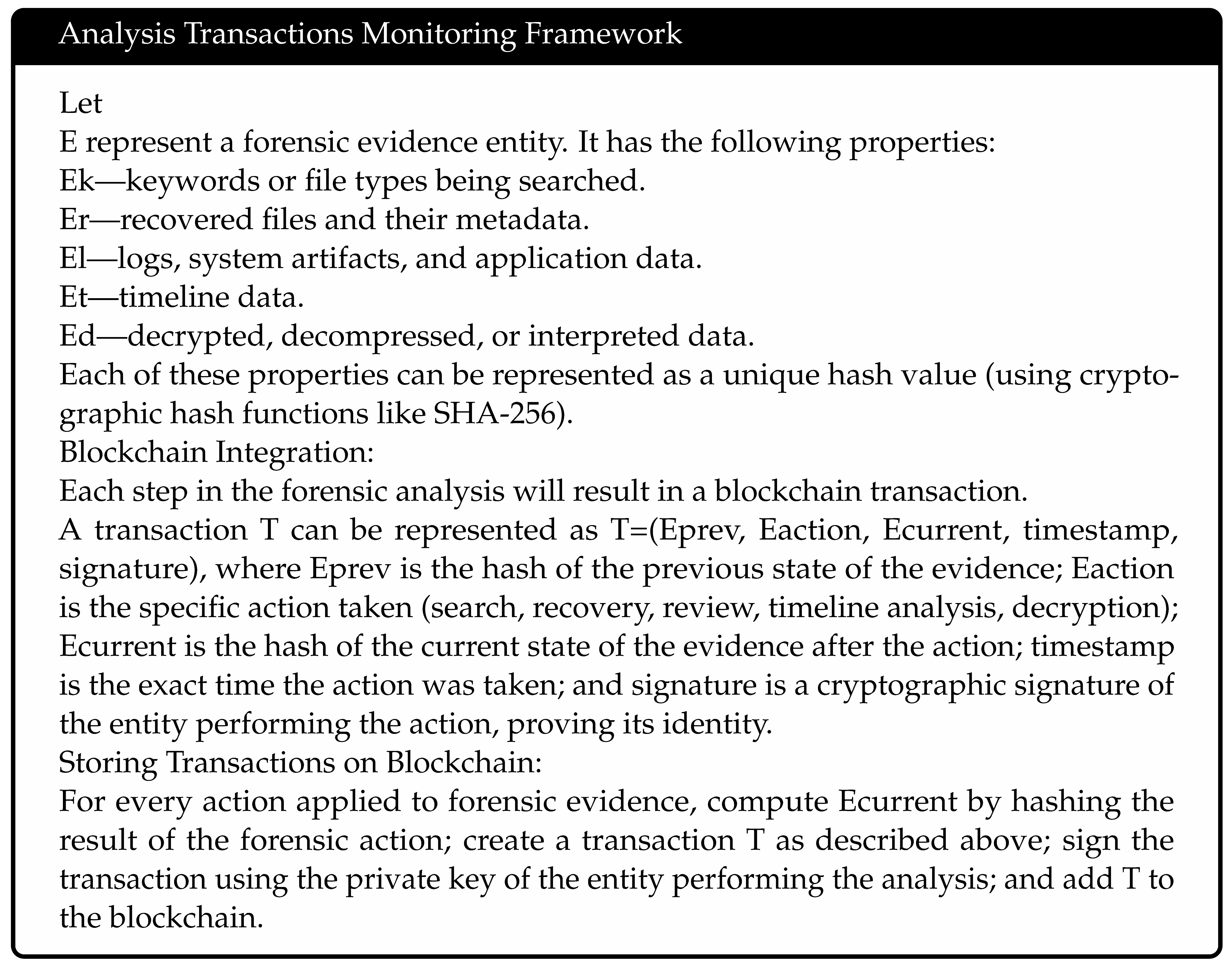
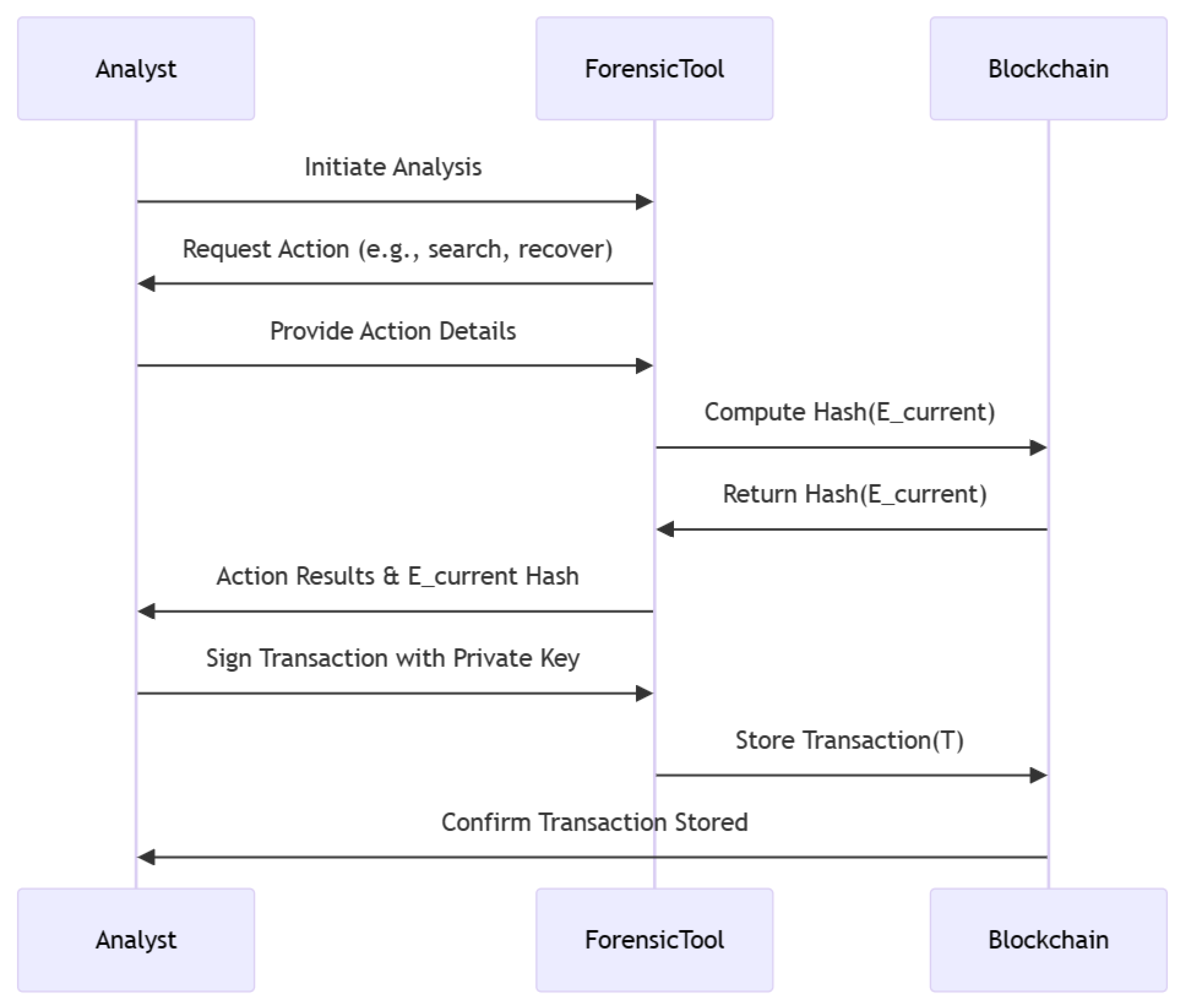
3.3.2. Example Process Flow
3.4. Documentation and Recording
3.4.1. Formal Definition of Documentation Related Transactions
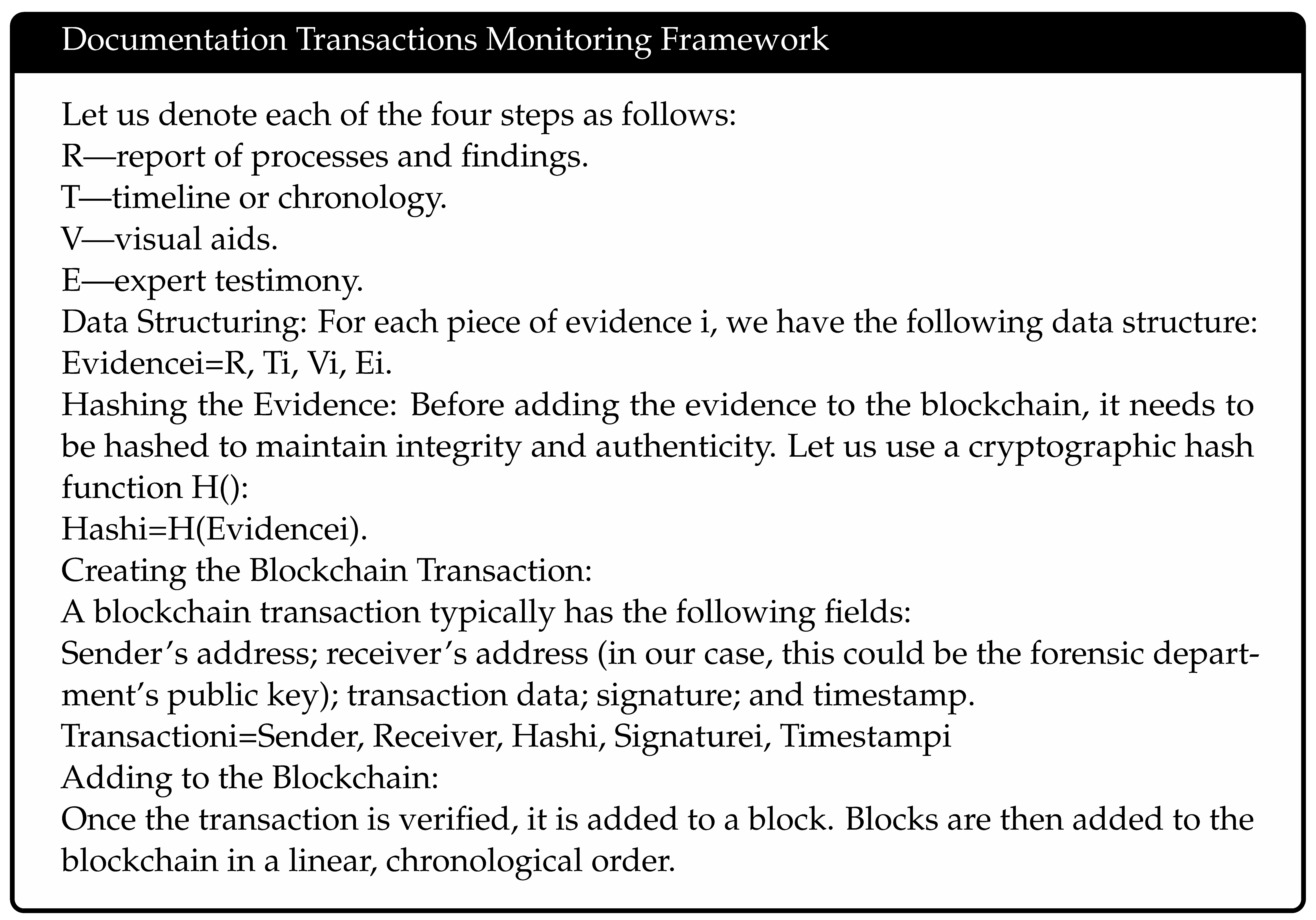
3.4.2. Integration Model
4. Implementation
4.1. Implementation of Data Preservation
| Listing 1. Code Snippet of Preservation Related transaction integration with Blockchain. |
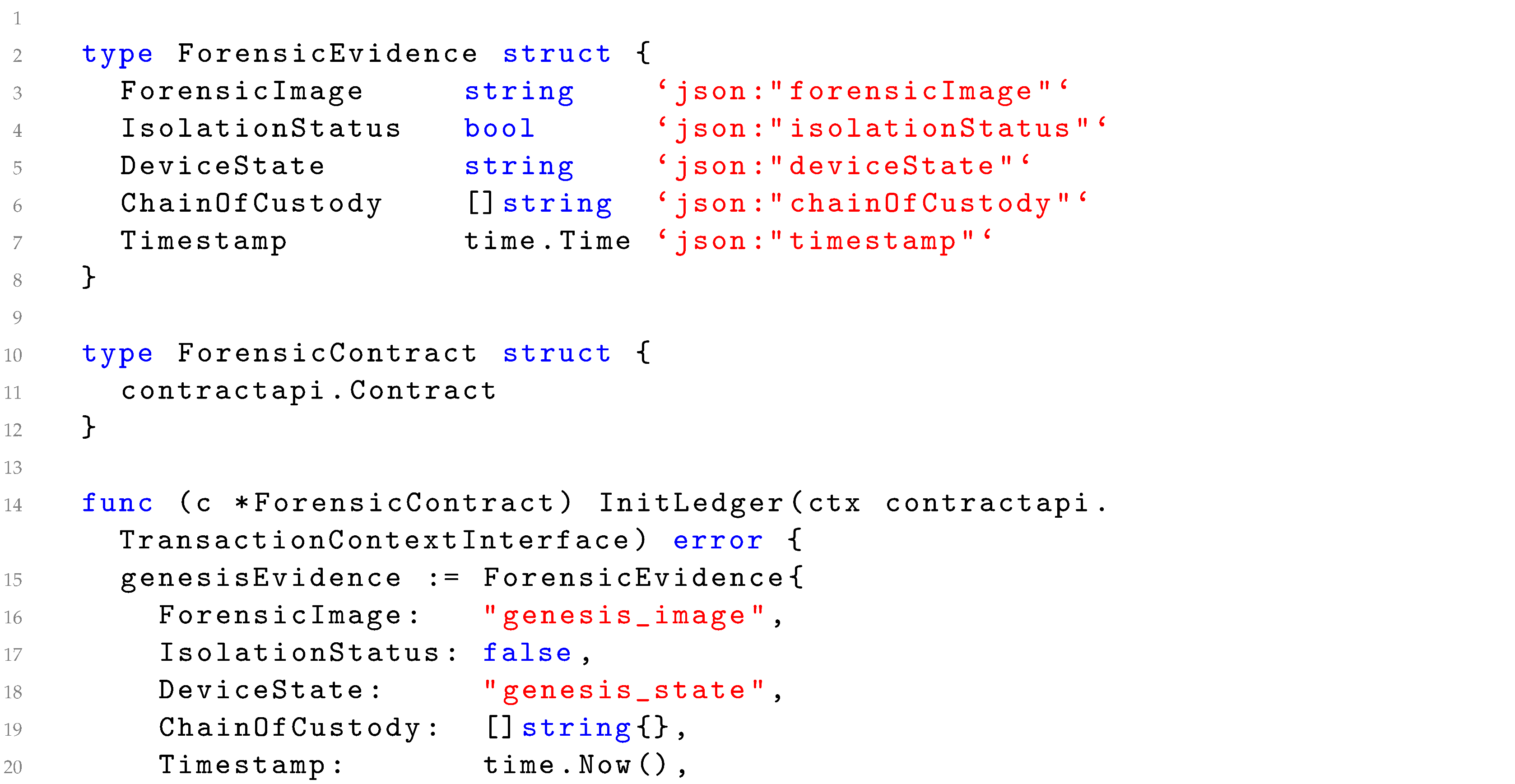 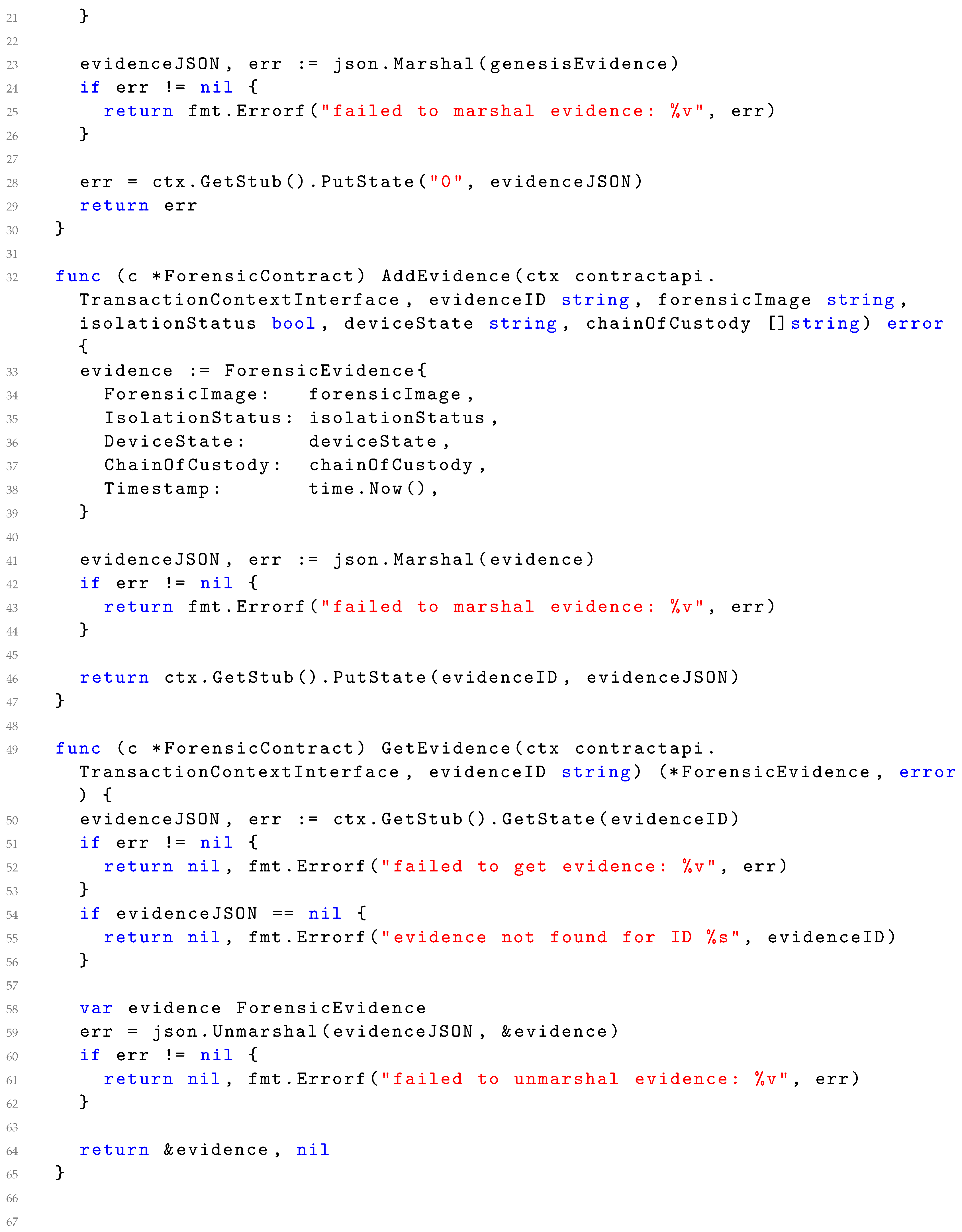 |
4.2. Implementation of Data Acquisition
| Listing 2. Code Snippet of Smart Contract for Acquisition Related transaction integration with Blockchain. |
 |
4.3. Implementation of Data Analysis
| Listing 3. Code Snippet of Smart Contract for Analysis Related transaction integration with Blockchain. |
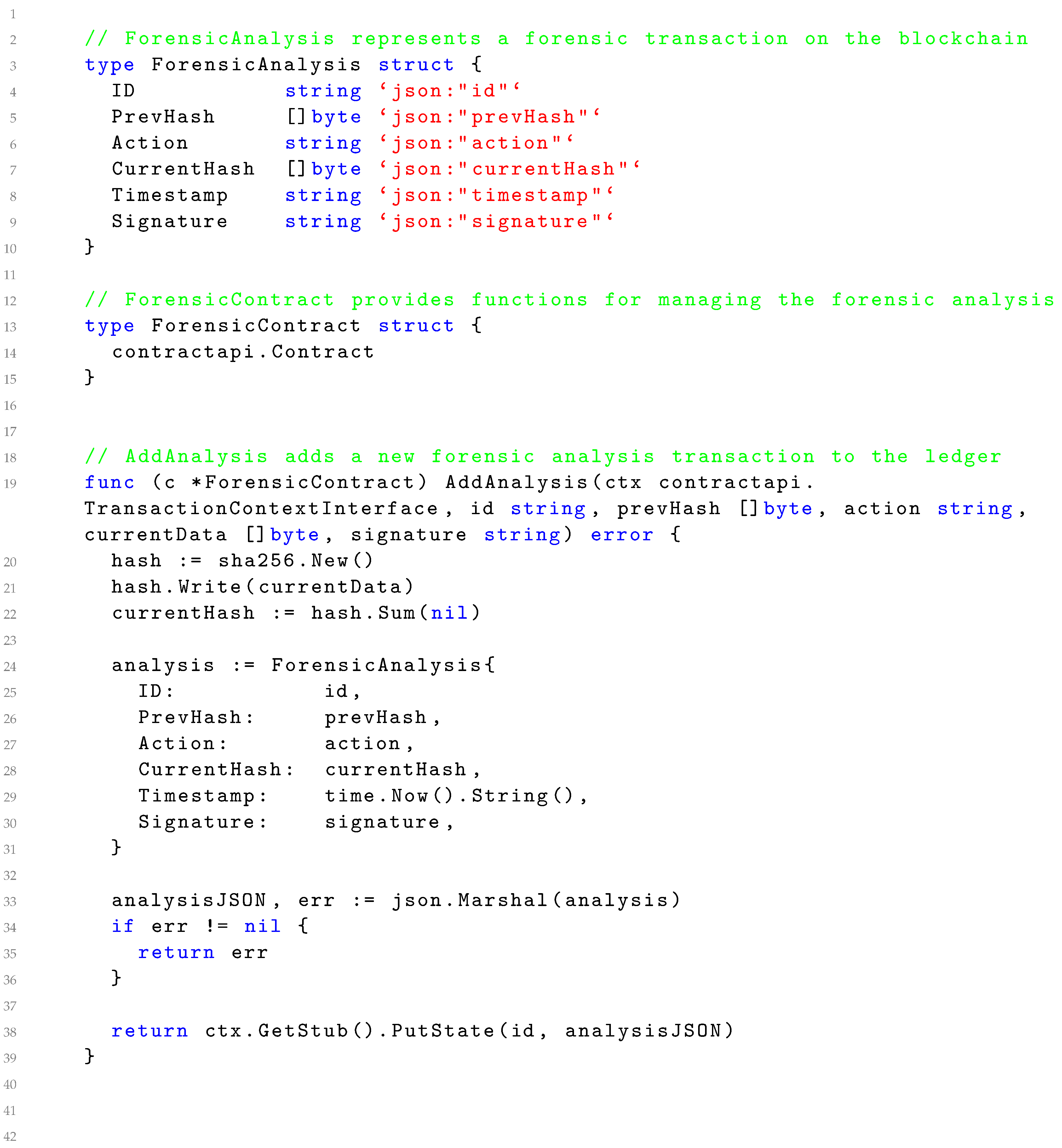 |
4.4. Implementation of Data Documentation
| Listing 4. Code Snippet of Smart Contract for Documentation Related transaction integration with Blockchain. |
 |
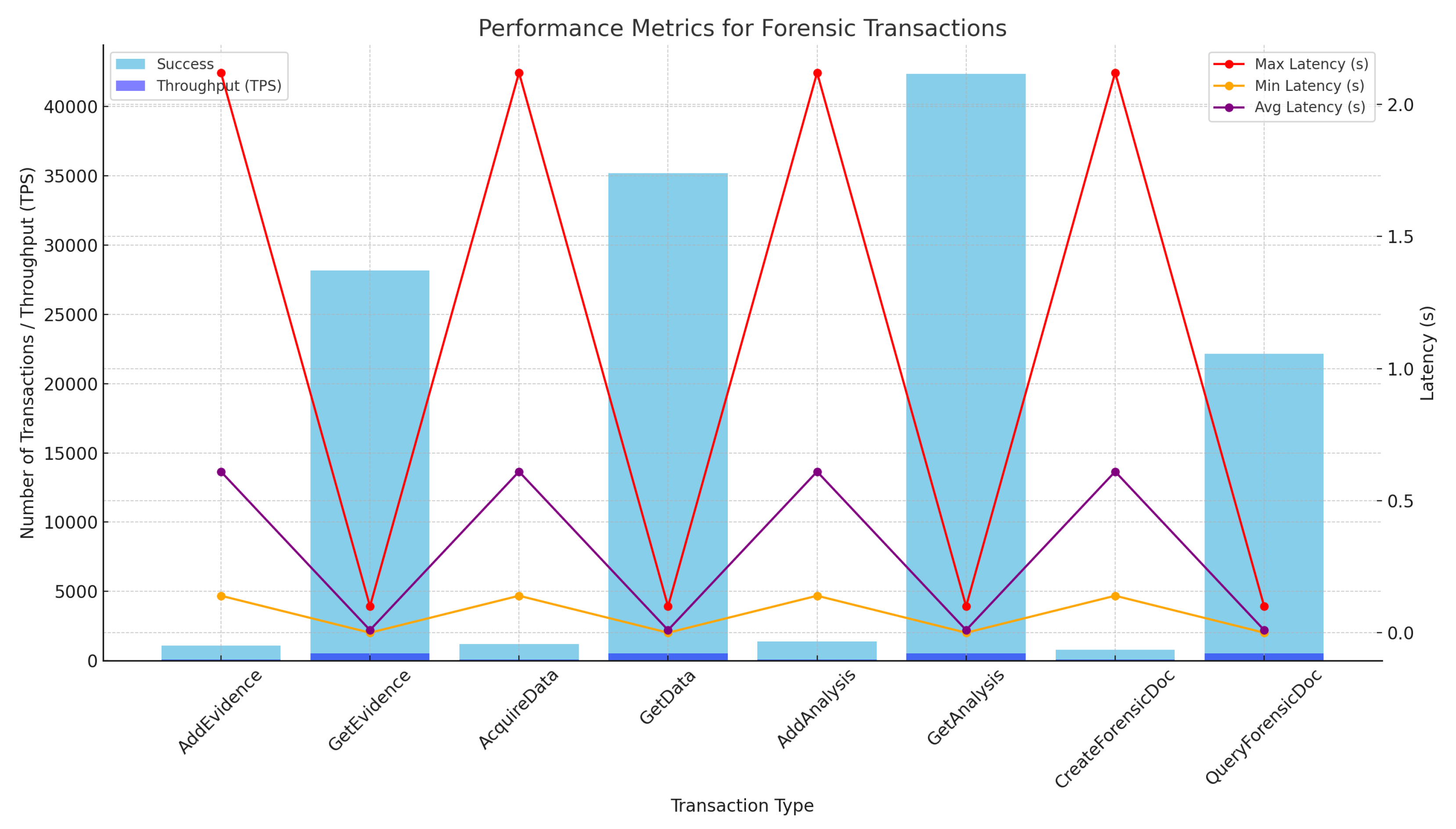
5. Results
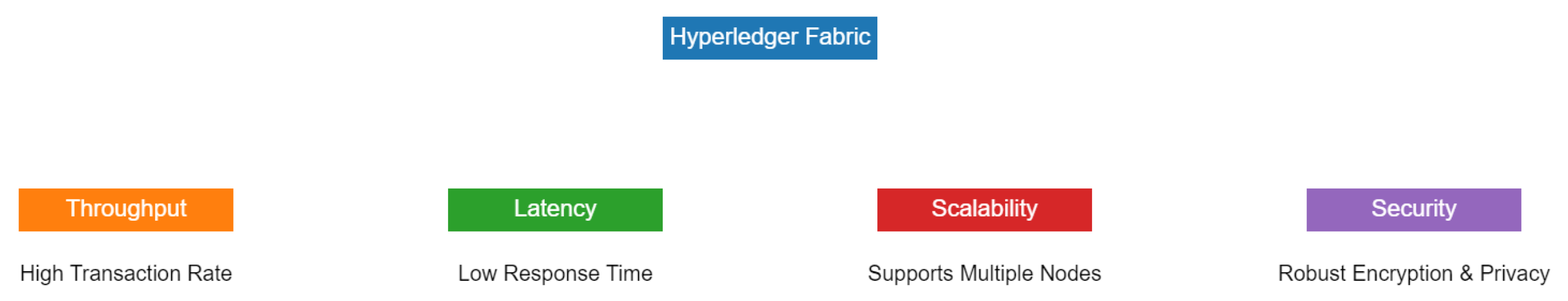
- 1.
- Throughput is a measure of how many transactions the system can process within a given time frame. In the context of the graph, it emphasizes a high transaction rate, indicating that Hyperledger Fabric is designed to handle a significant volume of transactions efficiently.
- 2.
- Latency refers to the time taken to process a single transaction, or the response time. The graph underscores the importance of a low response time, suggesting that transactions in Hyperledger Fabric are processed swiftly.
- 3.
- Scalability concerns the system’s ability to grow and manage increased demand. The diagram points out that Hyperledger Fabric supports multiple nodes, highlighting its ability to expand and accommodate a growing network.
- 4.
- Security is paramount in any blockchain framework. The graph emphasizes robust encryption and privacy features in Hyperledger Fabric, ensuring that data remain secure and private transactions are well protected.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Business, F. The Compound Annual Growth Rate. 2024. Available online: https://connect.comptia.org/blog/blockchain-statistics (accessed on 25 January 2024).
- Carter, R. The Ultimate List of Blockchain Statistics. 2023. Available online: https://www.founderjar.com/blockchain-statistics/ (accessed on 16 October 2023).
- Ali, M.; Ismail, A.; Elgohary, H.; Darwish, S.; Mesbah, S. A Procedure for Tracing Chain of Custody in Digital Image Forensics: A Paradigm Based on Grey Hash and Blockchain. Symmetry 2022, 14, 334. [Google Scholar] [CrossRef]
- Yan, W.; Shen, J.; Cao, Z.; Dong, X. Blockchain based digital evidence chain of custody. In Proceedings of the 2020 The 2nd International Conference on Blockchain Technology, Hilo, HI, USA, 12–14 March 2020; pp. 19–23. [Google Scholar]
- Silva, W.; Garcia, A.C.B. Where is our data? A blockchain-based information chain of custody model for privacy improvement. In Proceedings of the 2021 IEEE 24th International Ctoonference on Computer Supported Cooperative Work in Design (CSCWD), Dalian, China, 5–7 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 329–334. [Google Scholar]
- Lone, A.H.; Mir, R.N. Forensic-chain: Blockchain based digital forensics chain of custody with PoC in Hyperledger Composer. Digit. Investig. 2019, 28, 44–55. [Google Scholar] [CrossRef]
- Al-Khateeb, H.; Epiphaniou, G.; Daly, H. Blockchain for modern digital forensics: The chain-of-custody as a distributed ledger. In Blockchain and Clinical Trial: Securing Patient Data; Springer: Cham, Switzerland, 2019; pp. 149–168. [Google Scholar]
- Li, M.; Lal, C.; Conti, M.; Hu, D. LEChain: A blockchain-based lawful evidence management scheme for digital forensics. Future Gener. Comput. Syst. 2021, 115, 406–420. [Google Scholar] [CrossRef]
- Gopalan, S.H.; Suba, S.A.; Ashmithashree, C.; Gayathri, A.; Andrews, V.J. Digital forensics using blockchain. Int. J. Recent Technol. Eng. 2019, 8, 182–184. [Google Scholar]
- Patil, S.; Kadam, S.; Katti, J. Security enhancement of forensic evidences using blockchain. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 263–268. [Google Scholar]
- Khan, A.A.; Uddin, M.; Shaikh, A.A.; Laghari, A.A.; Rajput, A.E. MF-ledger: Blockchain hyperledger sawtooth-enabled novel and secure multimedia chain of custody forensic investigation architecture. IEEE Access 2021, 9, 103637–103650. [Google Scholar] [CrossRef]
- Zou, R.; Lv, X.; Wang, B. Blockchain-based photo forensics with permissible transformations. Comput. Secur. 2019, 87, 101567. [Google Scholar] [CrossRef]
- Pocher, N.; Zichichi, M.; Merizzi, F.; Shafiq, M.Z.; Ferretti, S. Detecting anomalous cryptocurrency transactions: An AML/CFT application of machine learning-based forensics. Electron. Mark. 2023, 33, 37. [Google Scholar] [CrossRef]
- Lusetti, M.; Salsi, L.; Dallatana, A. A blockchain based solution for the custody of digital files in forensic medicine. Forensic Sci. Int. Digit. Investig. 2020, 35, 301017. [Google Scholar] [CrossRef]
- Kotsiuba, I.; Velykzhanin, A.; Biloborodov, O.; Skarga-Bandurova, I.; Biloborodova, T.; Yanovich, Y.; Zhygulin, V. Blockchain evolution: From bitcoin to forensic in smart grids. In Proceedings of the 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 3100–3106. [Google Scholar]
- Brotsis, S.; Kolokotronis, N.; Limniotis, K.; Shiaeles, S.; Kavallieros, D.; Bellini, E.; Pavué, C. Blockchain solutions for forensic evidence preservation in IoT environments. In Proceedings of the 2019 IEEE Conference on Network Softwarization (NetSoft), Paris, France, 24–28 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 110–114. [Google Scholar]
- Liao, Z.; Pang, X.; Zhang, J.; Xiong, B.; Wang, J. Blockchain on security and forensics management in edge computing for IoT: A comprehensive survey. IEEE Trans. Netw. Serv. Manag. 2021, 19, 1159–1175. [Google Scholar] [CrossRef]
- Kamal, R.; Hemdan, E.E.D.; El-Fishway, N. A review study on blockchain-based IoT security and forensics. Multimed. Tools Appl. 2021, 80, 36183–36214. [Google Scholar] [CrossRef]
- Li, S.; Qin, T.; Min, G. Blockchain-based digital forensics investigation framework in the internet of things and social systems. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1433–1441. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Lal, C.; Conti, M. Internet-of-Forensic (IoF): A blockchain based digital forensics framework for IoT applications. Future Gener. Comput. Syst. 2021, 120, 13–25. [Google Scholar] [CrossRef]
- Ryu, J.H.; Sharma, P.K.; Jo, J.H.; Park, J.H. A blockchain-based decentralized efficient investigation framework for IoT digital forensics. J. Supercomput. 2019, 75, 4372–4387. [Google Scholar] [CrossRef]
- Le, D.P.; Meng, H.; Su, L.; Yeo, S.L.; Thing, V. BIFF: A blockchain-based IoT forensics framework with identity privacy. In Proceedings of the TENCON 2018—2018 IEEE Region 10 Conference, Jeju, Republic of Korea, 28–31 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 2372–2377. [Google Scholar]
- Pourvahab, M.; Ekbatanifard, G. An efficient forensics architecture in software-defined networking-IoT using blockchain technology. IEEE Access 2019, 7, 99573–99588. [Google Scholar] [CrossRef]
- Khanji, S.; Alfandi, O.; Ahmad, L.; Kakkengal, L.; Al-kfairy, M. A systematic analysis on the readiness of blockchain integration in IoT forensics. Forensic Sci. Int. Digit. Investig. 2022, 42, 301472. [Google Scholar] [CrossRef]
- Akinbi, A.; MacDermott, Á.; Ismael, A.M. A systematic literature review of blockchain-based Internet of Things (IoT) forensic investigation process models. Forensic Sci. Int. Digit. Investig. 2022, 42, 301470. [Google Scholar] [CrossRef]
- Mercan, S.; Cebe, M.; Tekiner, E.; Akkaya, K.; Chang, M.; Uluagac, S. A cost-efficient iot forensics framework with blockchain. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Mercan, S.; Cebe, M.; Aygun, R.S.; Akkaya, K.; Toussaint, E.; Danko, D. Blockchain-based video forensics and integrity verification framework for wireless Internet-of-Things devices. Secur. Priv. 2021, 4, e143. [Google Scholar] [CrossRef]
- Sakshi; Malik, A.; Sharma, A.K. Blockchain-based digital chain of custody multimedia evidence preservation framework for internet-of-things. J. Inf. Secur. Appl. 2023, 77, 103579. [Google Scholar] [CrossRef]
- Zhang, Y.; Wu, S.; Jin, B.; Du, J. A blockchain-based process provenance for cloud forensics. In Proceedings of the 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 2470–2473. [Google Scholar]
- Pourvahab, M.; Ekbatanifard, G. Digital forensics architecture for evidence collection and provenance preservation in iaas cloud environment using sdn and blockchain technology. IEEE Access 2019, 7, 153349–153364. [Google Scholar] [CrossRef]
- Ricci, J.; Baggili, I.; Breitinger, F. Blockchain-based distributed cloud storage digital forensics: Where’s the beef? IEEE Secur. Priv. 2019, 17, 34–42. [Google Scholar] [CrossRef]
- Awuson-David, K.; Al-Hadhrami, T.; Alazab, M.; Shah, N.; Shalaginov, A. BCFL logging: An approach to acquire and preserve admissible digital forensics evidence in cloud ecosystem. Future Gener. Comput. Syst. 2021, 122, 1–13. [Google Scholar] [CrossRef]
- Akter, O.; Akther, A.; Uddin, M.A.; Islam, M.M. Cloud forensics: Challenges and blockchain based solutions. Int. J. Wirel. Microw. Technol. 2020, 10, 1–12. [Google Scholar] [CrossRef]
- Ahmed, M.; Reno, S.; Akter, N.; Haque, F. Securing medical forensic system using hyperledger based private blockchain. In Proceedings of the 2020 23rd International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 19–21 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Li, M.; Chen, Y.; Lal, C.; Conti, M.; Alazab, M.; Hu, D. Eunomia: Anonymous and secure vehicular digital forensics based on blockchain. IEEE Trans. Dependable Secur. Comput. 2021, 20, 225–241. [Google Scholar] [CrossRef]
- Billard, D. Weighted forensics evidence using blockchain. In Proceedings of the 2018 International Conference on Computing and Data Engineering, Shanghai, China, 4–6 May 2018; pp. 57–61. [Google Scholar]
- Mahrous, W.A.; Farouk, M.; Darwish, S.M. An enhanced blockchain-based IoT digital forensics architecture using fuzzy hash. IEEE Access 2021, 9, 151327–151336. [Google Scholar] [CrossRef]
- Lone, A.H.; Mir, R.N. Forensic-chain: Ethereum blockchain based digital forensics chain of custody. Sci. Pract. Cyber Secur. J. 2018, 1, 21–27. [Google Scholar]
- Khan, A.A.; Shaikh, A.A.; Laghari, A.A. IoT with multimedia investigation: A secure process of digital forensics chain-of-custody using blockchain hyperledger sawtooth. Arab. J. Sci. Eng. 2023, 48, 10173–10188. [Google Scholar] [CrossRef]
- Tyagi, R.; Sharma, S.; Mohan, S. Blockchain Enabled Intelligent Digital Forensics System for Autonomous Connected Vehicles. In Proceedings of the 2022 International Conference on Communication, Computing and Internet of Things (IC3IoT), Chennai, India, 10–11 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Malamas, V.; Dasaklis, T.; Kotzanikolaou, P.; Burmester, M.; Katsikas, S. A forensics-by-design management framework for medical devices based on blockchain. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 2642, pp. 35–40. [Google Scholar]
- Dasaklis, T.K.; Casino, F.; Patsakis, C. Sok: Blockchain solutions for forensics. In Technology Development for Security Practitioners; Springer: Cham, Switzerland, 2021; pp. 21–40. [Google Scholar]
- Liu, G.; He, J.; Xuan, X. A data preservation method based on blockchain and multidimensional hash for digital forensics. Complexity 2021, 2021, 5536326. [Google Scholar] [CrossRef]
- Oladejo, M.T.; Jack, L. Fraud prevention and detection in a blockchain technology environment: Challenges posed to forensic accountants. Int. J. Econ. Account. 2020, 9, 315–335. [Google Scholar] [CrossRef]
- Ahmad, L.; Khanji, S.; Iqbal, F.; Kamoun, F. Blockchain-based chain of custody: Towards real-time tamper-proof evidence management. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual, 25–28 August 2020; pp. 1–8. [Google Scholar]
- Nyaletey, E.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R. BlockIPFS-blockchain-enabled interplanetary file system for forensic and trusted data traceability. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 18–25. [Google Scholar]
- Ugwu, M.C.; Okpala, I.U.; Oham, C.I.; Nwakanma, C.I. A tiered blockchain framework for vehicular forensics. Int. J. Netw. Secur. Its Appl. 2018, 10. Available online: https://aircconline.com/ijnsa/V10N5/10518ijnsa03.pdf (accessed on 1 January 2024).
- Duy, P.T.; Do Hoang, H.; Hien, D.T.T.; Khanh, N.B.; Pham, V.H. Sdnlog-foren: Ensuring the integrity and tamper resistance of log files for sdn forensics using blockchain. In Proceedings of the 2019 6th NAFOSTED Conference on Information and Computer Science (NICS), Hanoi, Vietnam, 12–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 416–421. [Google Scholar]
- Srivasthav, D.P.; Maddali, L.P.; Vigneswaran, R. Study of blockchain forensics and analytics tools. In Proceedings of the 2021 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 39–40. [Google Scholar]
- Verma, A.; Bhattacharya, P.; Saraswat, D.; Tanwar, S. NyaYa: Blockchain-based electronic law record management scheme for judicial investigations. J. Inf. Secur. Appl. 2021, 63, 103025. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Spathoulas, G.P.; Anagnostopoulos, M.; Ghosal, A.; Borocz, I.; Solanas, A.; Conti, M.; Patsakis, C. Research trends, challenges, and emerging topics in digital forensics: A review of reviews. IEEE Access 2022, 10, 25464–25493. [Google Scholar] [CrossRef]
- Amato, F.; Castiglione, A.; Cozzolino, G.; Narducci, F. A semantic-based methodology for digital forensics analysis. J. Parallel Distrib. Comput. 2020, 138, 172–177. [Google Scholar] [CrossRef]
- Dimitriadis, A.; Ivezic, N.; Kulvatunyou, B.; Mavridis, I. D4I-Digital forensics framework for reviewing and investigating cyber attacks. Array 2020, 5, 100015. [Google Scholar] [CrossRef]
- Tully, G.; Cohen, N.; Compton, D.; Davies, G.; Isbell, R.; Watson, T. Quality standards for digital forensics: Learning from experience in England & Wales. Forensic Sci. Int. Digit. Investig. 2020, 32, 200905. [Google Scholar]
- Butt, G.Q.; Sayed, T.A.; Riaz, R.; Rizvi, S.S.; Paul, A. Secure healthcare record sharing mechanism with blockchain. Appl. Sci. 2022, 12, 2307. [Google Scholar] [CrossRef]
- Syed, T.A.; Siddique, M.S.; Nadeem, A.; Alzahrani, A.; Jan, S.; Khattak, M.A.K. A novel blockchain-based framework for vehicle life cycle tracking: An end-to-end solution. IEEE Access 2020, 8, 111042–111063. [Google Scholar] [CrossRef]
- Ali, T.; Nadeem, A.; Alzahrani, A.; Jan, S. A transparent and trusted property registration system on permissioned blockchain. In Proceedings of the 2019 International Conference on Advances in the Emerging Computing Technologies (AECT), Al Madinah Al Munawwarah, Saudi Arabia, 10 February 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Syed, T.A.; Jan, S.; Siddiqui, M.S.; Alzahrani, A.; Nadeem, A.; Ali, A.; Ullah, A. CAR-tourist: An integrity-preserved collaborative augmented reality framework-tourism as a use-case. Appl. Sci. 2022, 12, 12022. [Google Scholar] [CrossRef]
- Jan, S.; Musa, S.; Ali, T.; Nauman, M.; Anwar, S.; Ali Tanveer, T.; Shah, B. Integrity verification and behavioral classification of a large dataset applications pertaining smart OS via blockchain and generative models. Expert Syst. 2021, 38, e12611. [Google Scholar] [CrossRef]
- Jan, S.; Ali, T.; Alzahrani, A.; Musa, S. Deep convolutional generative adversarial networks for intent-based dynamic behavior capture. Int. J. Eng. Technol. 2018, 7, 101–103. [Google Scholar]
- Ali, S.; Wang, G.; White, B.; Cottrell, R.L. A blockchain-based decentralized data storage and access framework for pinger. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1303–1308. [Google Scholar]
- Abdeen, M.A.; Ali, T.; Khan, Y.; Yagoub, M. Fusing identity management, HL7 and Blockchain into a global healthcare record sharing architecture. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 630–636. [Google Scholar] [CrossRef]
- Syed, T.A.; Siddiqui, M.S.; Abdullah, H.B.; Jan, S.; Namoun, A.; Alzahrani, A.; Nadeem, A.; Alkhodre, A.B. In-depth review of augmented reality: Tracking technologies, development tools, AR displays, collaborative AR, and security concerns. Sensors 2022, 23, 146. [Google Scholar] [CrossRef] [PubMed]
- Ali, M.S.; Vecchio, M.; Putra, G.D.; Kanhere, S.S.; Antonelli, F. A decentralized peer-to-peer remote health monitoring system. Sensors 2020, 20, 1656. [Google Scholar] [CrossRef] [PubMed]
- Abutaleb, R.A.; Alqahtany, S.S.; Syed, T.A. Integrity and Privacy-Aware, Patient-Centric Health Record Access Control Framework Using a Blockchain. Appl. Sci. 2023, 13, 1028. [Google Scholar] [CrossRef]
- Syed, F.; Gupta, S.K.; Hamood Alsamhi, S.; Rashid, M.; Liu, X. A survey on recent optimal techniques for securing unmanned aerial vehicles applications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4133. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A survey on blockchain technology and its security. Blockchain Res. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A Survey on Blockchain Technology: Evolution, Architecture and Security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A.B. Performance analysis of hyperledger fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alqahtany, S.S.; Syed, T.A. ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management. Information 2024, 15, 109. https://doi.org/10.3390/info15020109
Alqahtany SS, Syed TA. ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management. Information. 2024; 15(2):109. https://doi.org/10.3390/info15020109
Chicago/Turabian StyleAlqahtany, Saad Said, and Toqeer Ali Syed. 2024. "ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management" Information 15, no. 2: 109. https://doi.org/10.3390/info15020109
APA StyleAlqahtany, S. S., & Syed, T. A. (2024). ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management. Information, 15(2), 109. https://doi.org/10.3390/info15020109




