Investigation into Phishing Risk Behaviour among Healthcare Staff
Abstract
:1. Introduction
1.1. Perception and Work Factors with a Phishing Simulation Study
1.2. Work Factors and Security Practice
- RQ1: What is the state-of-the arts in phishing simulation studies in healthcare?
- RQ2: How can phishing attack simulation study be conducted successfully in healthcare without interfering with the hospital’s normal operations and exposing their system to potential attacks?
- RQ3: Are healthcare workers susceptible to phishing attacks?
- RQ4: What circumstances trigger healthcare workers to click on malicious links?
- RQ5: What is the relationship between the actual behaviour and self-reported behaviour among healthcare workers?
- RQ6: What are the ethical requirements for an in-the-wild-field study in phishing simulation?
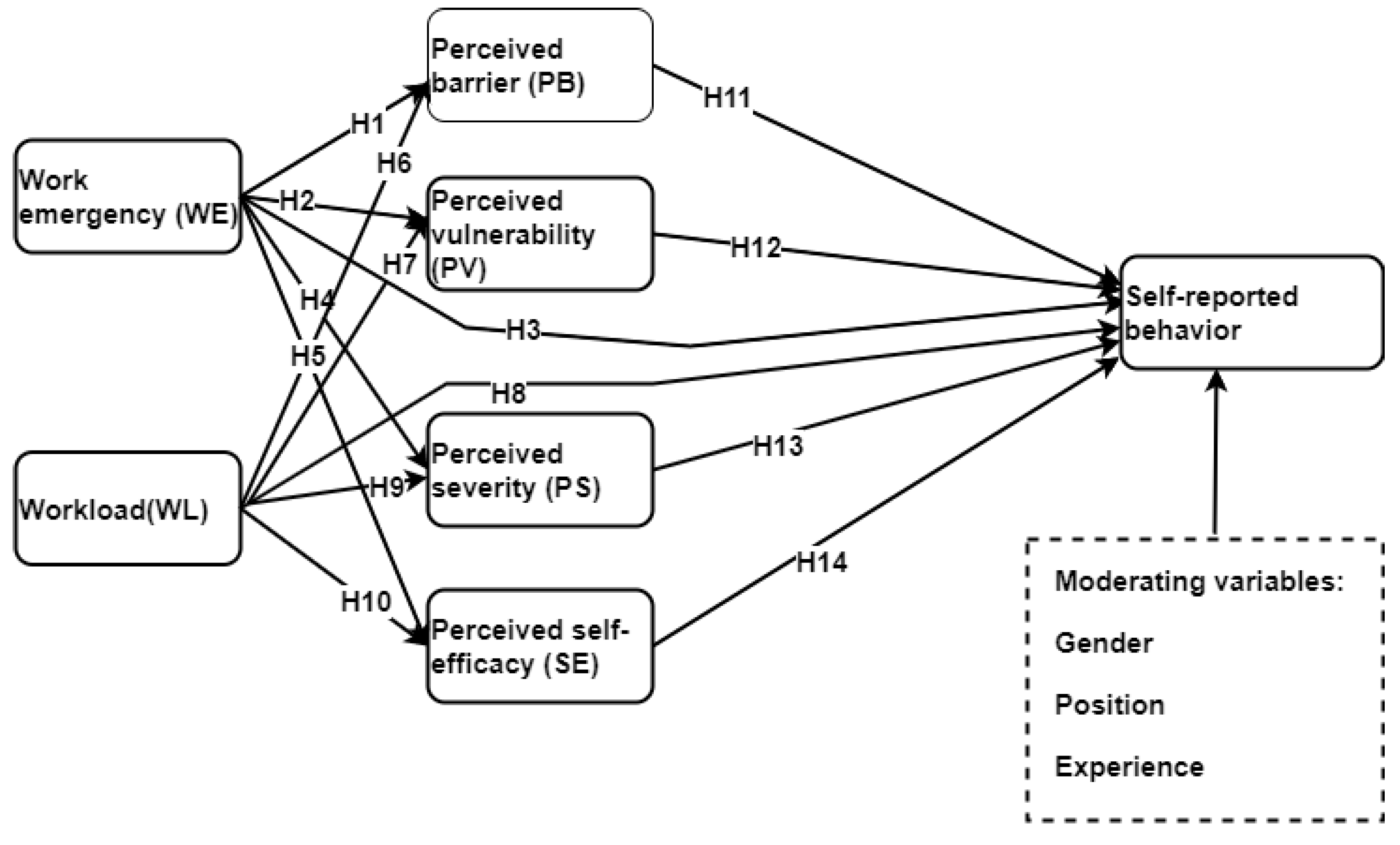
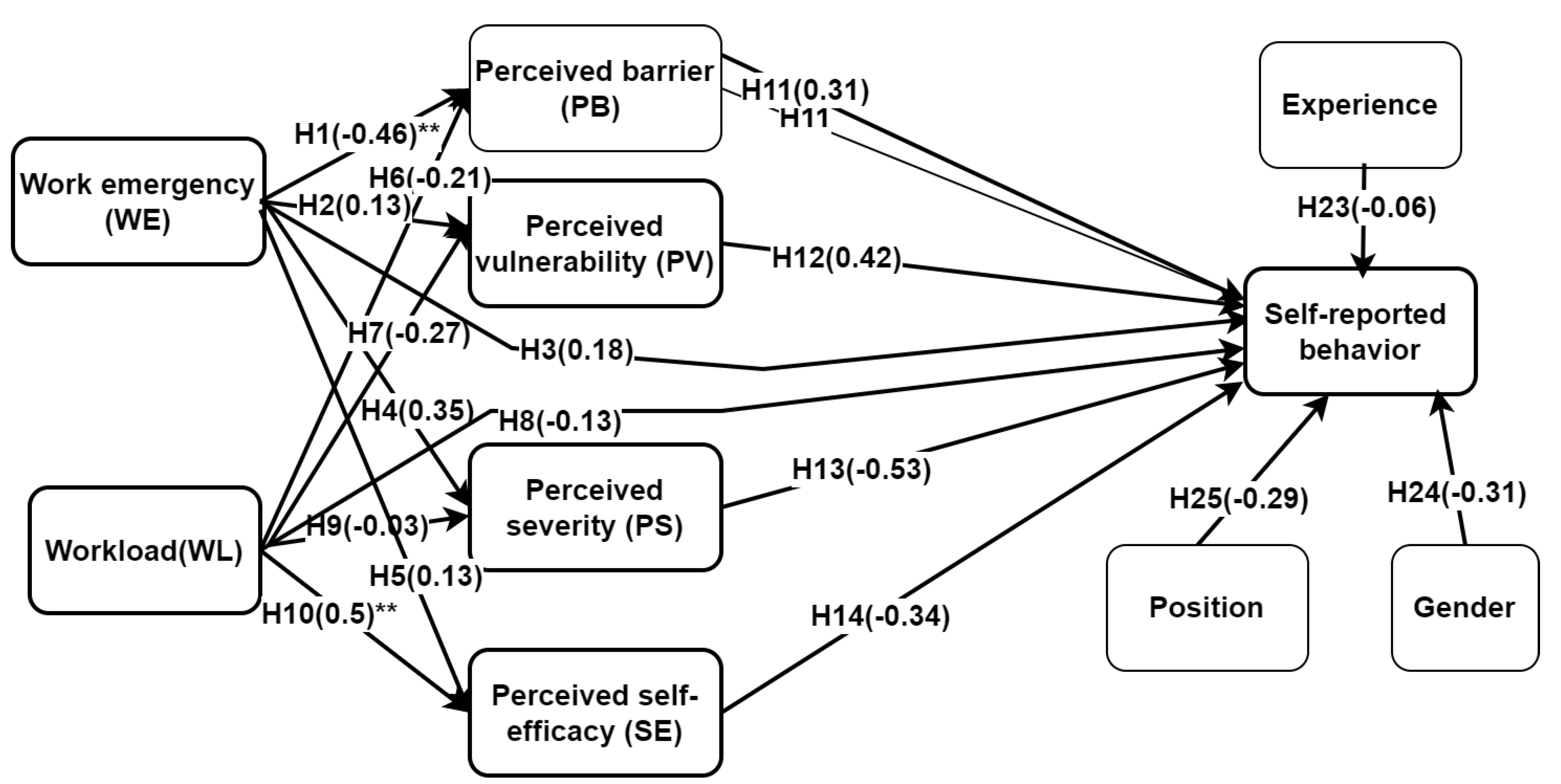
- H1: Work emergency has a negative influence on perceived barrier.
- H2: Work emergency negatively influences perceived vulnerability.
- H3: Work emergency has a negative influence on self-reported security behaviour (IB).
- H4: Work emergency is negatively related to perceived severity risk.
- H5: Work emergency has a negative effect on perceived self-efficacy.
- H6: Workload has adverse influence on perceived barrier.
- H7: Workload is negatively related to perceived vulnerability.
- H8: Workload has a negative effect on self-reported security behaviour.
- H9: Workload has negative influence on perceived severity.
- H10: Workload has a negative influence on perceived self-efficacy.
- H11: Perceived barrier has a negative influence on self-reported security behaviour.
- H12: Perceived vulnerability has a positive influence on self-reported security behaviour.
- H13: Perceived severity has a positive influence on self-reported security behaviour.
- H14: Perceived self-efficacy has a positive influence on self-reported security behaviour.
- H15: Perceived barrier has a negative mediating effect on work emergency and self-reported security behaviour.
- H16: Perceived barrier has a negative mediating effect on workload and self-reported security behaviour.
- H17: Perceived vulnerability has a positive mediating effect on work emergency and self-reported security behaviour.
- H18: Perceived severity has a positive mediating effect on workload and self-reported security behaviour.
- H19: Perceived self-efficacy has a positive mediating effect on work emergency and self-reported security behaviour.
- H20: Perceived self-efficacy has a positive mediating effect on workload and self-reported security behaviour.
- H21: Perceived vulnerability has a positive mediating effect on workload and self-reported security behaviour.
- H22: Perceived severity has a positive mediating effect on work emergency and self-reported security behaviour.
- H23, H24, and H25 are respectively moderating variables of experience, gender, and position that have potential effect on self-reported behaviour.
2. Research Methodology
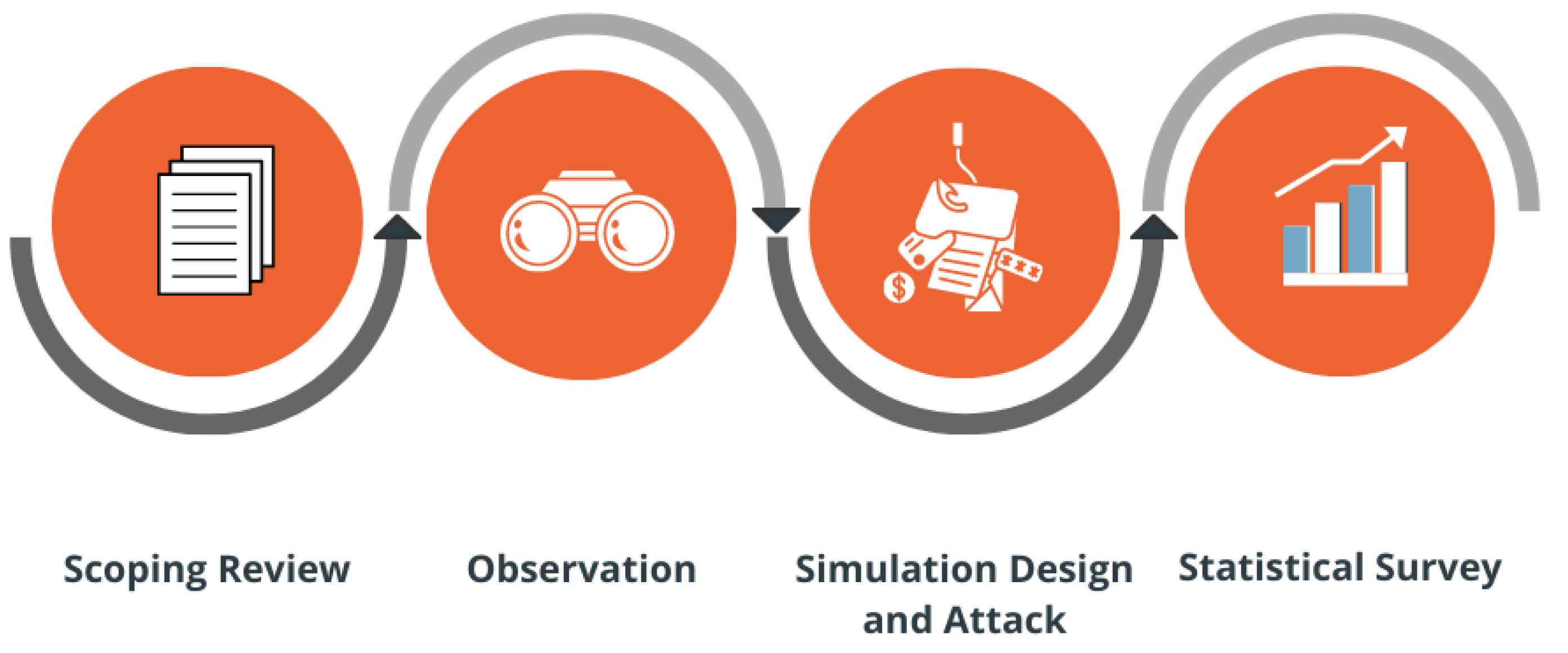
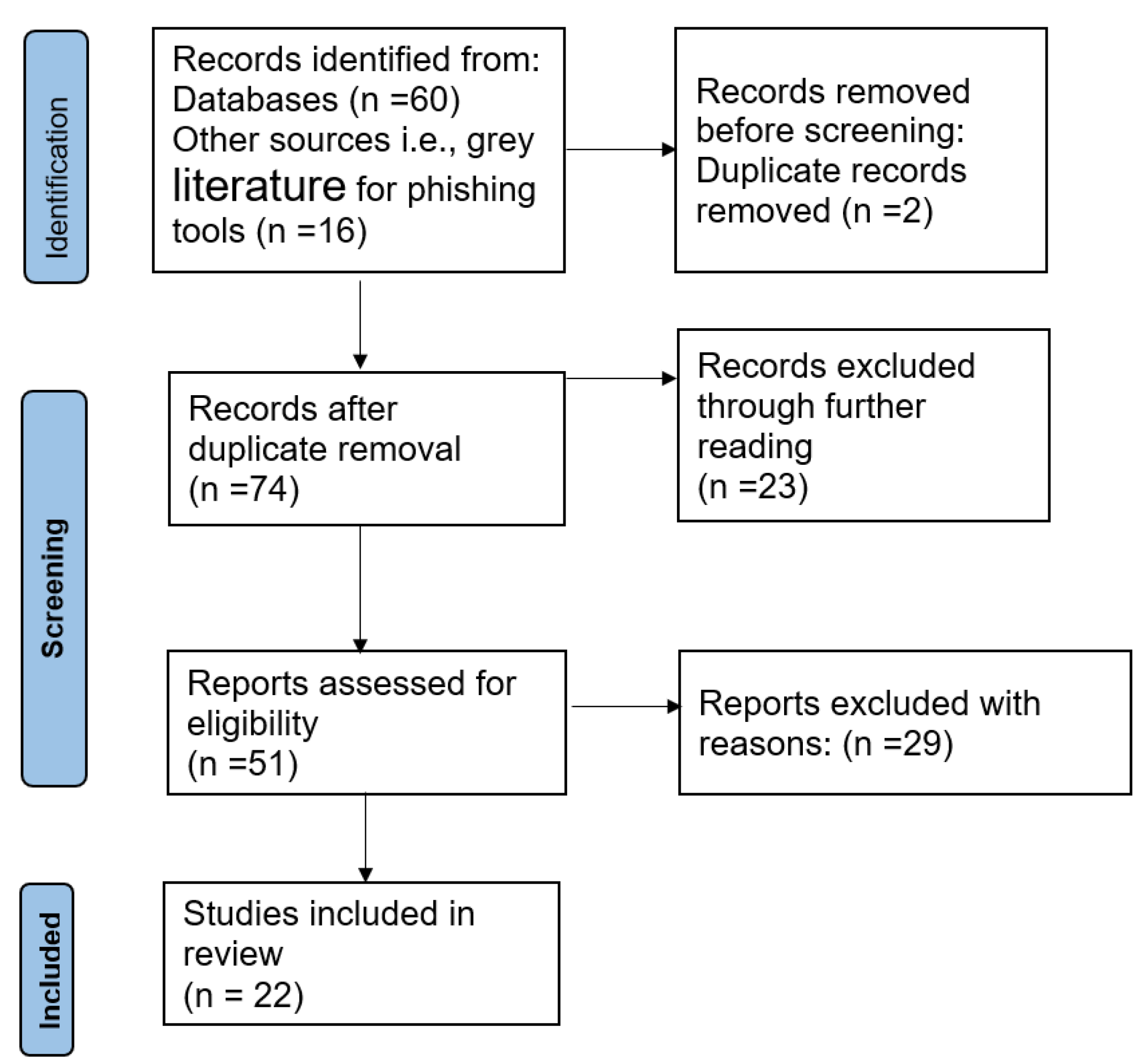
2.1. Scoping Review
2.1.1. Inclusion and Exclusion Criteria
2.1.2. Data Collection, Categorization, and Analysis
2.2. Observation at the Hospitals
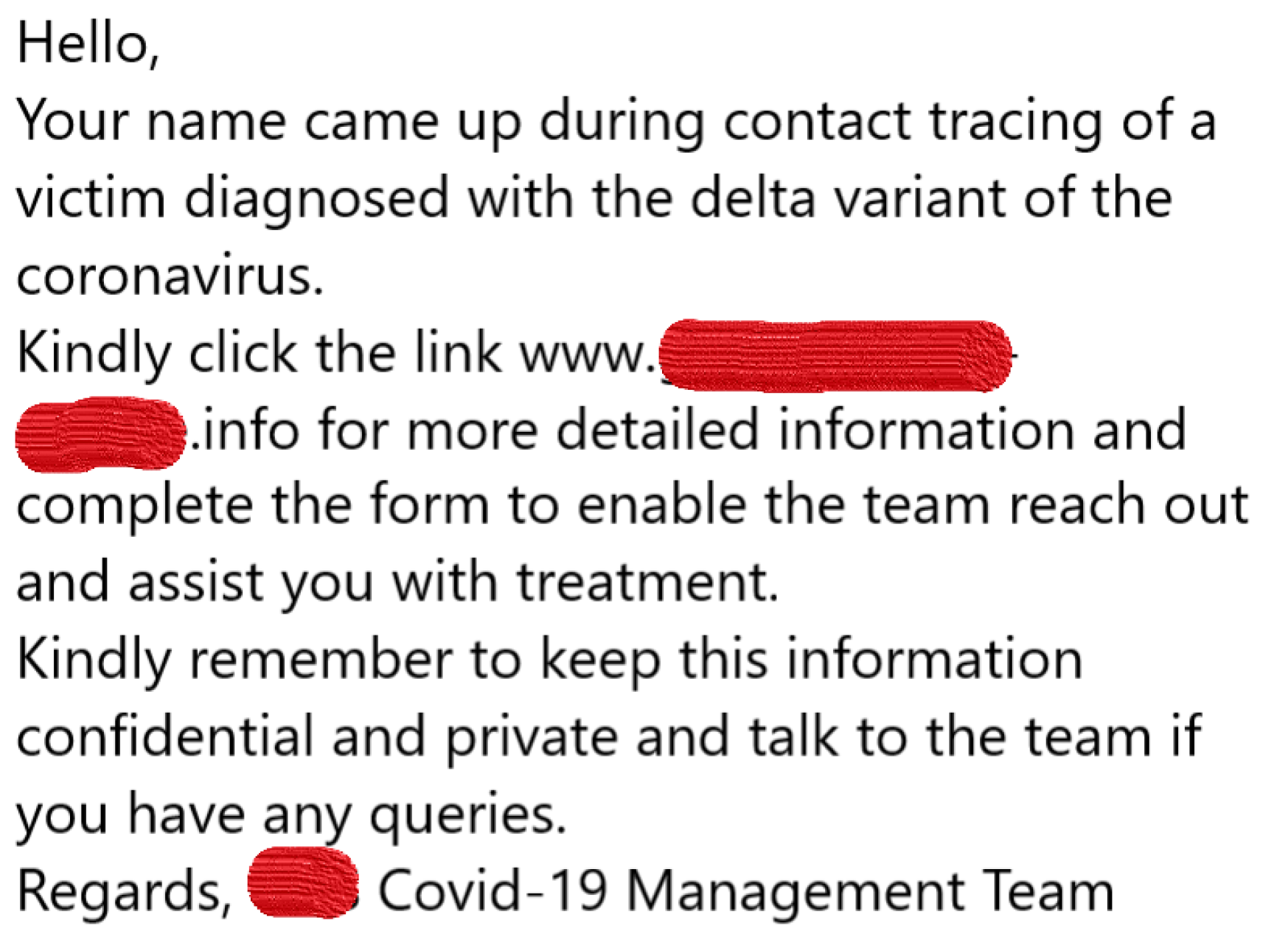
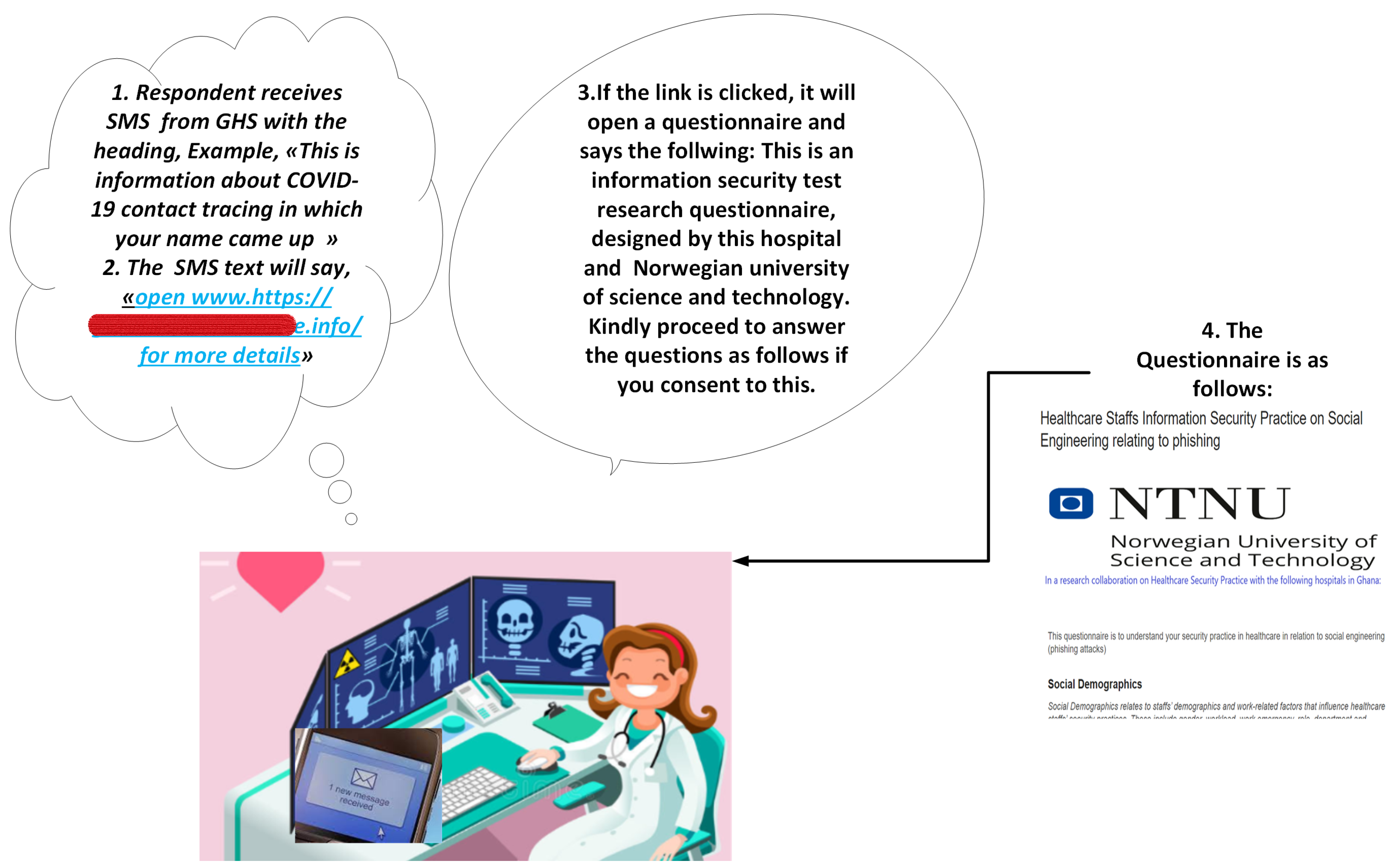
2.3. Phishing Simulation Design and Attack
2.4. Statistical Survey
2.5. Ethical, Privacy, and Security Measures
- Pre-launch of phishing: prepare fraudulent text, issue press release to administrators, and pre-inform consent;
- Launch of the attack: consider data protection, consider the well-being of the participants;
- Post-launch: consider debriefing, post informed consent and data protection.
3. Findings of this Study
3.1. Scoping Review Findings
3.2. Observation Study
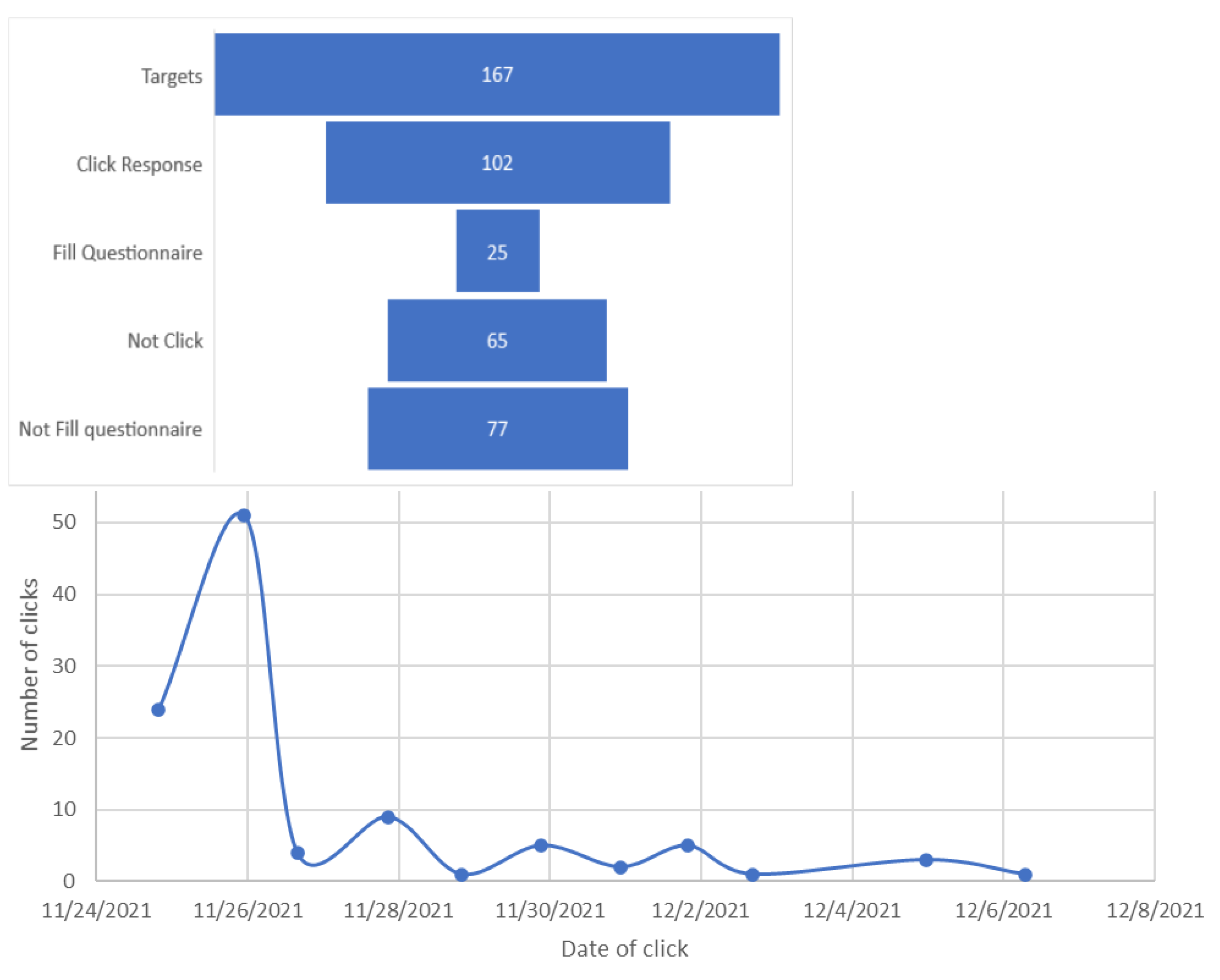
3.3. Phishing Clicks
4. Statistical Analyses
4.1. Reliability, Validity, Fit, Structural Model, and Correlation
Views of Targets Who Did Not Click the Link
5. Discussion
5.1. Principal Findings
5.2. Work Factors and Perception Risks in Relation to Self-Reported Phishing Risk Behaviour
5.3. Phishing Attack Methods, Tools, Risks Measures, Payload, and Storyline
5.4. Phishing Attack Risk among Healthcare Staff
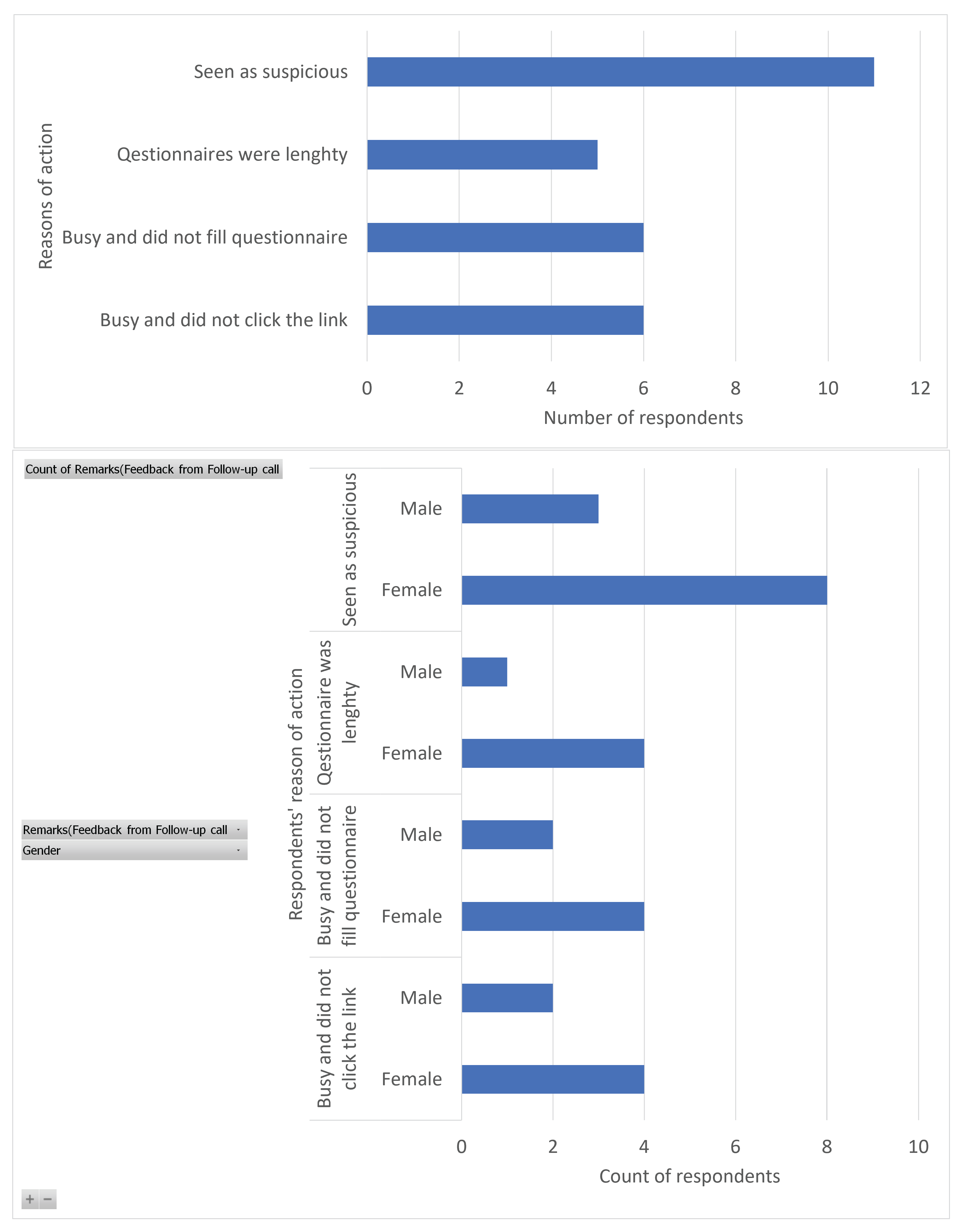
5.5. Survivorship Bias and Feedback from Respondents Who Neither Clicked the Link nor Filled the Questionnaire and Those Who Clicked the Link but Failed to Fill the Questionnaire
5.6. Implication of the Study
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| No | Item | Construct | Ref |
|---|---|---|---|
| 1 | It is inconvenient to check the security of an email with attachment | ||
| 2 | I do not have the time to check for phishing clues in an email | ||
| 3 | I do not have the knowledge to check for phishing clues in an email | ||
| 4 | I have not been trained properly to identify phishing related clues | PB | [17,25] |
| 5 | My hospital can not be hacked if I click on a malicious link | ||
| 6 | Loss of data resulting from hacking is a serious problem for my hospital | ||
| 7 | Giving out my password and username to external person can lead to unauthorized access in my hospital systems | ||
| 8 | My hospital can be attacked by ransomware if I click on a malicious link | PV | [17,25,91] |
| 9 | I have the skills to identify malicious or phishing links in emails | ||
| 10 | I am confident that I cannot download malicious attachment | ||
| 11 | I am confident that I cannot share my username and password with others through phishing attack | ||
| 12 | I am confident that I will not download malicious software on my computer | SE | [17,92,93] |
| 13 | I feel that my chance of receiving an email attachment with a virus is high | ||
| 14 | I feel that I could fall victim to a malicious attack if i fail to comply with my organization’s information security policy | ||
| 15 | My organization’s data and resources may be compromised if I don’t pay adequate attention to phishing attack tricks | ||
| 16 | It is not likely that an information security breach can occur at my workplace through clicking email links | PS | [17,25] |
| 17 | I check the links in my email or SMS to be sure it is not harmful before clicking | ||
| 18 | I do not open email attachments from people whom I do not know | ||
| 19 | I do not enter usernames, passwords and other sensitive information on pop-up windows | ||
| 20 | I always verify the source of the email or SMS before accessing its content | IB | [17,25,94] |
| 21 | I was called to attend to urgent issues prior to clicking the link | ||
| 22 | Prior to clicking the link, the work i was performing required URGENT or IMMEDIATE intervention to prevent a worsening condition which poses an immediate risk to health and life | ||
| 23 | I was called outside my shift time to attend to urgent issues prior to clicking the link | ||
| 24 | I was preparing to receive an emergency case prior to clicking the link | WE | |
| 25 | In my workplace, I SKIPPED my daily break or I was in a hurry in order to keep up with my workload prior to clicking the link | ||
| 26 | I was at work early or I stayed late outside of my regular or normal working hours in order to keep up with my workload prior to clicking the link | ||
| 27 | Prior to clicking this link, I had performed some mind draining activities (thinking, deciding, calculating, remembering, looking, searching, etc.) which affected my ability to pay much attention to the message details and the SMS links before clicking. | ||
| 28 | Prior to clicking this link, I had performed some amount of physical activities (e.g., pushing, pulling, turning, controlling, activating, etc.) which affected my ability to pay much attention to message details and the SMS link before clicking. | WL | [24] |
References
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of human factors on cyber security within healthcare organisations: A systematic review. Sensors 2021, 21, 5119. [Google Scholar] [CrossRef] [PubMed]
- Faddis, A. The digital transformation of healthcare technology management. Biomed. Instrum. Technol. 2018, 52, 34–38. [Google Scholar] [CrossRef] [PubMed]
- WHO. Technical Series on Primary Healthcare; WHO: Geneva, Switzerland, 2021. [Google Scholar]
- Yeng, P.; Yang, B.; Wolthusen, S.D. Legal Requirements towards Enhancing the Security of Medical Devices. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 666–675. [Google Scholar] [CrossRef]
- Yeng, P.K.; Woldaregay, A.Z.; Hartvigsen, G. K-CUSUM: Cluster Detection Mechanism in EDMON; Linköping University Electronic Press: Linköping, Sweden, 2019. [Google Scholar]
- Adu, E.K.; Mills, A.; Todorova, N. Factors influencing individuals’ personal health information privacy concerns. A study in Ghana. Inf. Technol. Dev. 2021, 27, 208–234. [Google Scholar] [CrossRef]
- Osei, E.; Agyei, K.; Tlou, B.; Mashamba-Thompson, T.P. Availability and Use of Mobile Health Technology for Disease Diagnosis and Treatment Support by Health Workers in the Ashanti Region of Ghana: A Cross-sectional Survey. Diagnostics 2021, 11, 1233. [Google Scholar] [CrossRef]
- Ayakwah, A.; Damoah, I.S.; Osabutey, E.L. Digitalization in Africa: The Case of Public Programs in Ghana. In Business in Africa in the Era of Digital Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 7–25. [Google Scholar]
- Verizon2021. 2021 Data Breach Investigations Report; Verizon: New York, NY, USA, 2021. [Google Scholar]
- Ransomware Is Leading Hospital Boards to Pour More Money into Cybersecurity. Available online: https://www.healthcareitnews.com/news/ransomware-leading-hospital-boards-pour-more-money-cybersecurity (accessed on 4 August 2022).
- Chernyshev, M.; Zeadally, S.; Baig, Z. Healthcare data breaches: Implications for digital forensic readiness. J. Med. Syst. 2019, 43, 7. [Google Scholar] [CrossRef]
- Spence, N.; Paul, D.P.; Coustasse, A. Ransomware in Healthcare Facilities: The Future is Now. Available online: https://mds.marshall.edu/mgmt_faculty/185/ (accessed on 4 August 2022).
- Sonowal, G. Phishing Kits. In Phishing and Communication Channels; Springer: Berlin/Heidelberg, Germany, 2022; pp. 115–135. [Google Scholar]
- Mishra, S.; Soni, D. SMS Phishing and Mitigation Approaches. In Proceedings of the 2019 Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 8–10 August 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Ulfath, R.E.; Sarker, I.H.; Chowdhury, M.J.M.; Hammoudeh, M. Detecting Smishing Attacks Using Feature Extraction and Classification Techniques. In Proceedings of the International Conference on Big Data, IoT, and Machine Learning, Sydney, NSW, Australia, 22–23 October 2022; pp. 677–689. [Google Scholar]
- Wayne, W. LaMorte. Behaviour Change Models: The Health Belief Model. Available online: https://sphweb.bumc.bu.edu/otlt/mph-modules/sb/behavioralchangetheories/#headingtaglink_1 (accessed on 4 August 2022).
- Ng, B.Y.; Kankanhalli, A.; Xu, Y.C. Studying users’ computer security behavior: A health belief perspective. Decis. Support Syst. 2009, 46, 815–825. [Google Scholar] [CrossRef]
- Cazares, M.F.; Arévalo, D.; Andrade, R.O.; Fuertes, W.; Sánchez-Rubio, M. A Training Web Platform to Improve Cognitive Skills for Phishing Attacks Detection. In Intelligent Sustainable Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 33–42. [Google Scholar]
- Abdelhamid, M. The role of health concerns in phishing susceptibility: Survey design study. J. Med. Internet Res. 2020, 22, e18394. [Google Scholar] [CrossRef] [PubMed]
- Gordon, W.J.; Wright, A.; Aiyagari, R.; Corbo, L.; Glynn, R.J.; Kadakia, J.; Kufahl, J.; Mazzone, C.; Noga, J.; Parkulo, M.; et al. Assessment of employee susceptibility to phishing attacks at US health care institutions. JAMA Netw. Open 2019, 2, e190393. [Google Scholar] [CrossRef]
- Gordon, W.J.; Wright, A.; Glynn, R.J.; Kadakia, J.; Mazzone, C.; Leinbach, E.; Landman, A. Evaluation of a mandatory phishing training program for high-risk employees at a US healthcare system. J. Am. Med. Inform. Assoc. 2019, 26, 547–552. [Google Scholar] [CrossRef] [PubMed]
- Priestman, W.; Anstis, T.; Sebire, I.G.; Sridharan, S.; Sebire, N.J. Phishing in healthcare organisations: Threats, mitigation and approaches. BMJ Health Care Inform. 2019, 26, e100031. [Google Scholar] [CrossRef] [PubMed]
- Slonka, K.J.; Shrift, B.F. Phishing our clients: A Step toward improving training via social engineering. Issues Inf. Syst. 2016, 17, 231–241. [Google Scholar]
- Jalali, M.S.; Bruckes, M.; Westmattelmann, D.; Schewe, G. Why employees (still) click on phishing links: Investigation in hospitals. J. Med. Internet Res. 2020, 22, e16775. [Google Scholar] [CrossRef] [PubMed]
- Anwar, M.; He, W.; Ash, I.; Yuan, X.; Li, L.; Xu, L. Gender difference and employees’ cybersecurity behaviors. Comput. Hum. Behav. 2017, 69, 437–443. [Google Scholar] [CrossRef]
- Humaidi, N.; Balakrishnan, V. The influence of security awareness and security technology on users’ behavior towards the implementation of health information system: A conceptual framework. In Proceedings of the 2nd International Conference on Management and Artificial Intelligence IPEDR, Bangkok, Thailand, 7–8 April 2012; IACSIT Press: Singapore, 2012; Volume 35, pp. 1–6. [Google Scholar]
- Yeng, P.K.; Szekeres, A.; Yang, B.; Snekkenes, E.A. Mapping the Psychosocialcultural Aspects of Healthcare Professionals’ Information Security Practices: Systematic Mapping Study. JMIR Hum. Factors 2021, 8, e17604. [Google Scholar] [CrossRef]
- Chen, Y.; Ramamurthy, K.; Wen, K.W. Organizations’ information security policy compliance: Stick or carrot approach? J. Manag. Inf. Syst. 2012, 29, 157–188. [Google Scholar] [CrossRef]
- Chen, Y.; Xia, W.; Cousins, K. Voluntary and instrumental information security policy compliance: An integrated view of prosocial motivation, self-regulation and deterrence. Comput. Secur. 2022, 113, 102568. [Google Scholar] [CrossRef]
- Champion, V.L.; Skinner, C.S. The health belief model. Health Behav. Health Educ. Theory Res. Pract. 2008, 4, 45–65. [Google Scholar]
- Humaidi, N.; Balakrishnan, V.; Shahrom, M. Exploring user’s compliance behavior towards Health Information System security policies based on extended Health Belief Model. In Proceedings of the 2014 IEEE Conference on e-Learning, e-Management and e-Services (IC3e), Hawthorne, VIC, Australia, 10–12 December 2014; pp. 30–35. [Google Scholar]
- Mou, J.; Cohen, J.F.; Bhattacherjee, A.; Kim, J. A Test of Protection Motivation Theory in the Information Security Literature: A Meta-Analytic Structural Equation Modeling Approach. J. Assoc. Inf. Syst. 2022, 23, 196–236. [Google Scholar] [CrossRef]
- Ifinedo, P. Understanding information systems security policy compliance: An integration of the theory of planned behavior and the protection motivation theory. Comput. Secur. 2012, 31, 83–95. [Google Scholar] [CrossRef]
- Yeng, P.K.; Yang, B.; Snekkenes, E.A. Healthcare Staffs’ Information Security Practices Towards Mitigating Data Breaches: A Literature Survey. Stud. Health Technol. Inform. 2019, 261, 239–245. [Google Scholar] [PubMed]
- Ansari, Z.M.; Yasin, H.; Zehra, N.; Faisal, A. Occupational stress among emergency department (ED) staff and the need for investment in health care; a view from Pakistan. J. Adv. Med. Med. Res. 2015, 10, 1–9. [Google Scholar] [CrossRef]
- Yeng, P.K.; Yang, B.; Snekkenes, E.A. Framework for healthcare security practice analysis, modeling and incentivization. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; pp. 3242–3251. [Google Scholar]
- Cocker, F.; Joss, N. Compassion fatigue among healthcare, emergency and community service workers: A systematic review. Int. J. Environ. Res. Public Health 2016, 13, 618. [Google Scholar] [CrossRef]
- Safa, N.S.; Sookhak, M.; Von Solms, R.; Furnell, S.; Ghani, N.A.; Herawan, T. Information security conscious care behaviour formation in organizations. Comput. Secur. 2015, 53, 65–78. [Google Scholar] [CrossRef]
- PRISMA. PRISMA:Preferred Reporting Items for Systematic Reviews and Meta-Analyses. Available online: http://www.prismastatement.org (accessed on 4 August 2022).
- Salah El-Din, R. To Deceive or Not to Deceive! Ethical Questions in Phishing Research. In Proceedings of the HCI Research in Sensitive Contexts: Ethical Considerations workshop at HCI 2012, Birmingham, UK, 10–14 September 2012. [Google Scholar]
- Parsons, K.; McCormac, A.; Butavicius, M.; Pattinson, M.; Jerram, C. The Development of the Human Aspects of Information Security Questionnaire (HAIS-Q); RMIT University: Melbourne, VIC, Australia, 2013. [Google Scholar]
- Parsons, K.; Calic, D.; Pattinson, M.; Butavicius, M.; McCormac, A.; Zwaans, T. The human aspects of information security questionnaire (HAIS-Q): Two further validation studies. Comput. Secur. 2017, 66, 40–51. [Google Scholar] [CrossRef]
- Yeng, P.; Yang, B.; Snekkenes, E. Observational Measures for Effective Profiling of Healthcare StaffsŚecurity Practices. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 2, pp. 397–404. [Google Scholar]
- The University of Oslo. Web Form for Questionnaire Registrations; The University of Oslo: Oslo, Norway, 2022. [Google Scholar]
- Ball, R.; Watts, R. Some additional evidence on survival biases. J. Financ. 1979, 34, 197–206. [Google Scholar] [CrossRef]
- Athanassoulis, N.; Wilson, J. When is deception in research ethical? Clin. Ethics 2009, 4, 44–49. [Google Scholar] [CrossRef]
- Sieber, J.E. Deception in social research I: Kinds of deception and the wrongs they may involve. IRB Ethics Hum. Res. 1982, 4, 1–5. [Google Scholar] [CrossRef]
- McElwee, S.; Murphy, G.; Shelton, P. Influencing outcomes and behaviors in simulated phishing exercises. In Proceedings of the SoutheastCon 2018, St. Petersburg, FL, USA, 19–22 April 2018; pp. 1–6. [Google Scholar]
- Rakhra, M.; Kaur, D. Studying user’s computer security behaviour in developing an effective antiphishing educational framework. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 832–836. [Google Scholar]
- Li, Y.; Xiong, K.; Li, X. Understanding user behaviors when phishing attacks occur. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; p. 222. [Google Scholar]
- Flores, W.R.; Holm, H.; Svensson, G.; Ericsson, G. Using phishing experiments and scenario-based surveys to understand security behaviours in practice. Inf. Manag. Comput. Secur. 2014, 22, 393–406. [Google Scholar] [CrossRef]
- Öğütçü, G.; Testik, Ö.M.; Chouseinoglou, O. Analysis of personal information security behavior and awareness. Comput. Secur. 2016, 56, 83–93. [Google Scholar] [CrossRef]
- Campbell, C.C. Solutions for counteracting human deception in social engineering attacks. Inf. Technol. People 2019, 32, 1130–1152. [Google Scholar] [CrossRef]
- Open-Source Phishing Framework. Available online: https://getgophish.com/ (accessed on 4 August 2022).
- Phishing All the Chings. Available online: https://www.phishingfrenzy.com (accessed on 4 August 2022).
- King-Phisher. Available online: https://www.kali.org/tools/king-phisher/ (accessed on 4 August 2022).
- sptoolkit. sptoolkit Rebirth–Simple Phishing Toolki. Available online: https://www.darknet.org.uk/2015/04/sptoolkit-rebirth-simple-phishing-toolkit/ (accessed on 4 August 2022).
- TrustedSec. The Social-Engineer Toolkit (SET). Available online: https://www.trustedsec.com/tools/the-social-engineer-toolkit-set/ (accessed on 4 August 2022).
- SPF. SPF–Speed Phishing Framework. Available online: https://sectechno.com/spf-speedphishing-framework/ (accessed on 4 August 2022).
- Kennedy, D. Introducing Spearphisher—A Simple Phishing Email Generation Tool. Available online: https://www.faqlogin.com/login/spearphisher-a-simple-phishing-email-generation-tool (accessed on 4 August 2022).
- Barracuda. Barracuda PhishLine:Fight Phishing with Continuous Simulation and Training. Available online: https://www.barracuda.com/resource/data_sheets/Barracuda_PhishLine_DS_US (accessed on 4 August 2022).
- Cofense. Security Solutions Built to Stop Phish. Available online: https://cofense.com/ (accessed on 4 August 2022).
- Hoxhunt. Enterprise Security Awareness, Re-Invented. Available online: https://www.hoxhunt.com/ (accessed on 4 August 2022).
- Infosecinstitute. Prepare Every Employee with Phishing Simulations & Training. Available online: https://www.infosecinstitute.com/iq/phishing-simulations/ (accessed on 4 August 2022).
- IronScales. Phishing Simulation & Training: Anti Phishing Simulations and Customized Training Based on Real-Time Data and Real World Situations. Available online: https://ironscales.com/ (accessed on 4 August 2022).
- Lucy. Cyber Security Training Solutions. Available online: https://lucysecurity.com/ (accessed on 4 August 2022).
- Mimecast. Relentless Protection Starts Here. Available online: https://www.mimecast.com/ (accessed on 4 August 2022).
- KnowBe4. Phishing. Available online: https://www.knowbe4.com/ (accessed on 4 August 2022).
- proofpoint. Attackers Start with People. Your Cybersecurity Strategy Should too. Available online: https://www.proofpoint.com/us (accessed on 4 August 2022).
- Nasser, G.; Morrison, B.W.; Bayl-Smith, P.; Taib, R.; Gayed, M.; Wiggins, M.W. The Role of Cue Utilization and Cognitive Load in the Recognition of Phishing Emails. Front. Big Data 2020, 3, 33. [Google Scholar] [CrossRef]
- Stewart, H.; Jürjens, J. Information security management and the human aspect in organizations. Inf. Comput. Secur. 2017, 25, 494–534. [Google Scholar] [CrossRef]
- Shah, M. Perception of Managers on the Effectiveness of the Internal Audit Functions: A Case Study in Tnb. Available online: https://www.semanticscholar.org/paper/PERCEPTION-OF-MANAGERS-ON-THE-EFFECTIVENESS-OF-THE-Shamsuddin-Shah/fe1a47ff6304041398376b1e7fefe0021d21dd6e (accessed on 4 August 2022).
- Hair, J.F.; Page, M.; Brunsveld, N. Essentials of Business Research Methods; Routledge: London, UK, 2019. [Google Scholar]
- Anawar, S.; Kunasegaran, D.L.; Mas’ud, M.Z.; Zakaria, N.A. Analysis of phishing susceptibility in a workplace: A big-five personality perspectives. J. Eng. Sci. Technol. 2019, 14, 2865–2882. [Google Scholar]
- Goel, S.; Williams, K.; Huang, J.; Warkentin, M. Understanding the Role of Incentives in Security Behavior. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Honolulu, HI, USA, 7–10 January 2020. [Google Scholar]
- Leguina, A. A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM). Int. J. Res. Method Educ. 2015, 38, 220–221. [Google Scholar] [CrossRef]
- Henseler, J.; Ringle, C.M.; Sarstedt, M. A new criterion for assessing discriminant validity in variance-based structural equation modeling. J. Acad. Mark. Sci. 2015, 43, 115–135. [Google Scholar] [CrossRef]
- Falk, R.F.; Miller, N.B. A Primer for Soft Modeling; University of Akron Press: Akron, OH, USA, 1992. [Google Scholar]
- Statology. What is a Good R-Squared Value? Available online: https://www.statology.org/good-r-squared-value/ (accessed on 4 August 2022).
- Houle, D. High Enthusiasm and Low R-Squared. Evolution 1998, 52, 1872–1876. [Google Scholar] [CrossRef]
- Anderson, J.C.; Gerbing, D.W. Structural equation modeling in practice: A review and recommended two-step approach. Psychol. Bull. 1988, 103, 411. [Google Scholar] [CrossRef]
- Ringle, C.M.; Becker, V. “SmartPLS 3”. Available online: http://www.smartpls.com (accessed on 4 August 2022).
- Bollen, K.A.; Pearl, J. Eight myths about causality and structural equation models. In Handbook of Causal Analysis for Social Research; Springer: Berlin/Heidelberg, Germany, 2013; pp. 301–328. [Google Scholar]
- Morolong, M.P.; Shava, F.B.; Shilongo, V.G. Designing an Email Security Awareness Program for State-Owned Enterprises in Namibia. In IOT with Smart Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 679–688. [Google Scholar]
- Chaudhry, J.A.; Chaudhry, S.A.; Rittenhouse, R.G. Phishing attacks and defenses. Int. J. Secur. Its Appl. 2016, 10, 247–256. [Google Scholar] [CrossRef]
- Yeng, P.; Woldaregay, A.Z.; Hartvigsen, G. K-cusum: Cluster detection mechanism in edmon. In Proceedings of the 17th Scandinavian Conference on Health Informatics, Oslo, Norway, 12–13 November 2019; Linköping University Electronic Press, Linköpings Universitet, LiU: Linkopings, Sweden, 2019; pp. 141–147. [Google Scholar]
- Baig, A. Understanding Data Encryption Requirements for GDPR, CCPA, LGPD & HIPAA. Available online: https://www.thesslstore.com/blog/understanding-data-encryption-requirements-for-gdpr-ccpa-lgpd-hipaa/ (accessed on 4 August 2022).
- Prosper Kandabongee Yeng, M.A.F.; Yang, B. Assessing the effect of human factors in healthcare cybersecurity practice: An empirical study. In Proceedings of the Volos ’21: Volos ’2021: 25th Pan-Hellenic Conference on Informatics, Volos, Greece, 26–28 November 2021; ACM: New York, NY, USA, 2021. [Google Scholar]
- Opoku, S.Y.; Benwell, M.; Yarney, J. Knowledge, attitudes, beliefs, behaviour and breast cancer screening practices in Ghana, West Africa. Pan Afr. Med. J. 2012, 11, 1–10. [Google Scholar]
- Atinga, R.A.; Abekah-Nkrumah, G.; Domfeh, K.A. Managing healthcare quality in Ghana: A necessity of patient satisfaction. Int. J. Health Care Qual. Assur. 2011, 24, 548–563. [Google Scholar] [CrossRef] [PubMed]
- Mohamed, N.; Ahmad, I.H. Information privacy concerns, antecedents and privacy measure use in social networking sites: Evidence from Malaysia. Comput. Hum. Behav. 2012, 28, 2366–2375. [Google Scholar] [CrossRef]
- Rhee, H.S.; Kim, C.; Ryu, Y.U. Self-efficacy in information security: Its influence on end users’ information security practice behavior. Comput. Secur. 2009, 28, 816–826. [Google Scholar] [CrossRef]
- Ifinedo, P. Information systems security policy compliance: An empirical study of the effects of socialisation, influence, and cognition. Inf. Manag. 2014, 51, 69–79. [Google Scholar] [CrossRef]
- Shih, D.H.; Lin, B.; Chiang, H.S.; Shih, M.H. Security aspects of mobile phone virus: A critical survey. Ind. Manag. Data Syst. 2008, 108, 478–494. [Google Scholar] [CrossRef]

| No | Categorisation | Definitions |
|---|---|---|
| 1 | Methods/Technique | The scientific approach which was used in the study (e.g., a survey, simulated attack, interview) |
| 2 | Tools | Social engineering tools which were used in the study (e.g., gophish,) |
| 3 | Psychological, social, and demographic (PSC) factors | Social engineering theories used to coerce targets into clicking on malicious links (PMT, TPB, and TTAT) |
| 4 | Storyline strategy | Context within which adversaries craft phishing messages to bait targets |
| 5 | Cue | This defines the clue used in the study |
| 6 | Security and privacy measure of tools | This describes the behaviour of the tools (e.g., whether the tool collects some sensitive data of the target hospital and targeted persons in the study) |
| 7 | Ethical measures | This defines the consideration of the relative effect on participants (e.g., whether participants consented to the study) |
| 8 | Risk measures and measures to be adopted to conduct risk-free assessment in the target environment. | |
| 9 | Social demographic factors | Factors such as gender, workload, and emergency situations which were considered in the attack |
| 10 | Situational context of healthcare staff prior to clicking the link | This defines what the healthcare workers were immediately engaged in prior to clicking the link |
| 11 | Susceptibility reasons | This defines the reasons for clicking the link by the staff |
| 12 | Survivors bias | Analysis of the characteristics of healthcare workers who only clicked the link without considering those who did not click the link. |
| Article | Method | Tool | Payload | Story Line | Attack Types |
|---|---|---|---|---|---|
| [24] | 1.in-the-wild field study, 2. survey | third-party company | simulated malicious link | ||
| [19] | survey | health, concerns, disposition to trust, and risk-taking propensity | |||
| [20] | in-the-wild field study | custom-developed software tools. | simulated malicious link | ||
| [21] | in-the-wild field study | Cofense, formerly PhishMe (commercial ) | simulated malicious link | ||
| [22] | in-the-wild field study | third-party company | credential harvesting, batch files obfuscated | marketing, advertising potential employment positions | |
| [23] | in-the-wild field study | custom-developed software tools | simulated malicious link | IT support request |
| No | Tool Name | Type | Cloud/On-Premise |
|---|---|---|---|
| 1 | GoPhish [54] | OpenSource | On-premise |
| 2 | Phishing Frenzy [55] | Open-source | On-premise |
| 3 | King Phisher [56] | Open-Source | On-premise |
| 4 | Simple Phishing Toolkit (sptoolkit) [57] | Open-source On-premise | |
| 5 | Social Engineer Toolkit (SET) [58] | Open-source | On-premise |
| 6 | SpeedPhish Framework (SPF) [59] | Open-source | On-premise |
| 7 | SpearPhisher BETA [60] | Open-source | |
| 8 | Barracuda Phishline [61] | Commercial | Cloud |
| 9 | Cofense [62] | Commercial | Cloud |
| 10 | Hoxhunt [63] | Commercial | Cloud |
| 11 | InfoSec [64] | Commercial | Cloud |
| 12 | IronScales [65] | Commercial | Cloud |
| 13 | Lucy [66] | Commercial | Both |
| 14 | Mimecast [67] | ||
| 15 | KnowBe4 [68] | Commercial | Cloud |
| 16 | Proofpoint [69] | Commercial | Cloud |
| Category | Value | Freq. | % |
|---|---|---|---|
| Gender | Male | 11 | 44.0 |
| Female | 14 | 56.0 | |
| Age range | 20–29 | 6 | 24.0 |
| 30–39 | 18 | 72.0 | |
| 50–59 | 1 | 4.0 | |
| Position | Pharmacists | 2 | 8.0 |
| Doctor | 2 | 8.0 | |
| Nurse | 13 | 52.0 | |
| IT personnel | 1 | 4. | |
| Lab personnel | 1 | 4. | |
| Data manager | 1 | 4.0 | |
| Public health | 4 | 16.0 | |
| Others | 1 | 4.0 | |
| Work experience | <1 Year | 2 | 8.0 |
| 1–5 Years | 11 | 44.0 | |
| 6–10 Years | 6 | 24.0 | |
| 11–15 Years | 5 | 20.0 | |
| 21–25 Years | 1 | 4.0 | |
| Total | 25 | 100.0 | |
| Click location | Off-duty | 14 | 56.0 |
| On-duty | 11 | 44.0 | |
| Total | 25 | 100.0 | |
| Engaged in | Not disclosed | 10 | 40.0 |
| Patient care | 8 | 32.0 | |
| Admin duties | 2 | 8.0 | |
| Leisure | 3 | 12.0 | |
| House chores | 2 | 8.0 | |
| Expectation | Believed in the subject of the message | 17 | 68.0 |
| Was curious | 6 | 24.0 | |
| Not disclosed | 2 | 8.0 |
| Construct | Reliability and Validity | Discriminate Analysis: Heterotrait–Monotrait Ratio (HTMT) | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| CA | rho_A | CR | Average Variance Extracted (AVE) | IB | PB | PS | PV | SE | WE | WL | |
| IB | 0.835 | 0.934 | 0.886 | 0.664 | |||||||
| PB | 0.799 | 0.826 | 0.881 | 0.714 | 0.578 | ||||||
| PS | 0.746 | 1.043 | 0.839 | 0.638 | 0.400 | 0.666 | |||||
| PV | 0.772 | 0.921 | 0.892 | 0.805 | 0.248 | 0.444 | 0.652 | ||||
| SE | 0.701 | 0.703 | 0.834 | 0.626 | 0.596 | 0.613 | 0.434 | 0.494 | |||
| WE | 0.667 | 0.675 | 0.857 | 0.750 | 0.364 | 0.715 | 0.415 | 0.163 | 0.277 | ||
| WL | 0.429 | 0.572 | 0.758 | 0.619 | 0.789 | 0.730 | 0.071 | 0.367 | 0.765 | 0.371 | |
| Path | Hypothesis | Original Sample (O) | Sample Mean (M) | Standard Deviation (STDEV) | p Values |
|---|---|---|---|---|---|
| Work emergency → Perceived barrier | H1 | −0.46 | −0.48 | 0.14 | 0.00 |
| Work emergency → Perceived vulnerability | H2 | 0.13 | 0.12 | 0.25 | 0.60 |
| Work emergency → Self-reported behaviour | H3 | 0.18 | 0.15 | 0.26 | 0.49 |
| Work emergency → Perceived severity | H4 | 0.35 | 0.35 | 0.26 | 0.18 |
| Work emergency → Self-efficacy | H5 | 0.13 | 0.09 | 0.24 | 0.60 |
| Workload → Perceived barrier | H6 | −0.31 | −0.32 | 0.19 | 0.10 |
| Workload → Perceived vulnerability | H7 | −0.27 | −0.20 | 0.30 | 0.38 |
| Workload → Self-reported behaviour | H8 | −0.13 | −0.17 | 0.30 | 0.66 |
| Workload → Perceived severity | H9 | −0.03 | −0.03 | 0.28 | 0.91 |
| Workload → Self-efficacy | H10 | 0.50 | 0.52 | 0.21 | 0.02 |
| Perceived barrier → Self-reported behaviour | H11 | 0.31 | 0.27 | 0.32 | 0.32 |
| Perceived vulnerability → Self-reported behaviour | H12 | 0.42 | 0.35 | 0.29 | 0.14 |
| Perceived severity → Self-reported behaviour | H13 | −0.53 | −0.45 | 0.34 | 0.12 |
| Self-efficacy → Self-reported behaviour | H14 | −0.34 | −0.34 | 0.32 | 0.29 |
| Indirect effect | |||||
| Work emergency → Perceived barrier → Self-reported behaviour | H15 | −0.14 | −0.13 | 0.16 | 0.37 |
| Workload → Perceived barrier → Self-reported behaviour | H16 | −0.10 | −0.09 | 0.13 | 0.47 |
| Work emergency → Perceived vulnerability → Self-reported behaviour | H17 | 0.05 | 0.05 | 0.12 | 0.66 |
| Workload → Perceived severity → Self-reported behaviour | H18 | 0.02 | 0.04 | 0.17 | 0.92 |
| Work emergency → Self-efficacy → Self-reported behaviour | H19 | −0.04 | −0.03 | 0.11 | 0.71 |
| Workload → Self-efficacy → Self-reported behaviour | H20 | −0.17 | −0.19 | 0.21 | 0.41 |
| Workload → Perceived vulnerability → Self-reported behaviour | H21 | −0.11 | −0.06 | 0.15 | 0.45 |
| Work emergency → Perceived severity → Self-reported behaviour | H22 | −0.18 | −0.17 | 0.18 | 0.30 |
| Experience → Self-reported behaviour | H23 | −0.06 | −0.01 | 0.18 | 0.86 |
| Gender → Self-reported behaviour | H24 | −0.31 | −0.32 | 0.96 | 0.34 |
| Position → Self-reported behaviour | H25 | −0.29 | −0.26 | 0.32 | 0.38 |
| Perceived barrier | 0.369 | 0.312 | |||
| Perceived severity | 0.116 | 0.036 | |||
| Perceived vulnerability | 0.086 | 0.003 | |||
| Self-efficacy | 0.293 | 0.229 | |||
| Self-reported behaviour | 0.554 | 0.405 | |||
| Correlations | |||||||
|---|---|---|---|---|---|---|---|
| WL | WE | PB | PS | SE | PV | IB | |
| WL | – | ||||||
| WE | 0.458 * | – | |||||
| 0.021 | |||||||
| PB | −0.334 | −0.401 * | – | ||||
| 0.102 | 0.047 | ||||||
| PS | 0.023 | 0.208 | −0.566 ** | – | |||
| 0.912 | 0.319 | 0.003 | |||||
| SE | 0.494 * | 0.241 | −0.441 * | 0.038 | – | ||
| 0.012 | 0.245 | 0.027 | 0.857 | ||||
| PV | 0.003 | 0.291 | −0.441 * | 0.450 * | −0.102 | ||
| 0.987 | 0.157 | 0.027 | 0.024 | 0.627 | |||
| IB | −0.391 | -0.197 | 0.571 ** | −0.238 | −0.483 * | 0.015 | |
| 0.053 | 0.346 | 0.003 | 0.252 | 0.014 | 0.944 | ||
| No | Research Question (RQ) and Hypothesis (H) | Principal Finding | Remark |
|---|---|---|---|
| 1 | RQ1 |
| |
| 2 | RQ2 |
| |
| 3 | RQ3 | 102 (61.1%) healthcare staff clicked the simulated malicious link. | |
| 4 | RQ4 |
| |
| 5 | RQ5 | Self-reported behaviour and perception risks were generally lower than their actual behaviour, as shown in Figure 7 | |
| 6 | RQ6 | Deceptiveness can be used in research but certain procedures are needed. These include:
| |
| 7 | H1 | Significant estimate (value −0.46, p-value = 0.00) between work emergency and perceived barrier. | This was confirmed with Pearson’s correlation coefficient (−0.494, p-value = 0.00). |
| 8 | H10 | Significant estimate (value 0.5, p-value = 0.02) between workload and self-efficacy. | This was confirmed with Pearson’s correlation coefficient value 0.494, p-value = 0.05). |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yeng, P.K.; Fauzi, M.A.; Yang, B.; Nimbe, P. Investigation into Phishing Risk Behaviour among Healthcare Staff. Information 2022, 13, 392. https://doi.org/10.3390/info13080392
Yeng PK, Fauzi MA, Yang B, Nimbe P. Investigation into Phishing Risk Behaviour among Healthcare Staff. Information. 2022; 13(8):392. https://doi.org/10.3390/info13080392
Chicago/Turabian StyleYeng, Prosper Kandabongee, Muhammad Ali Fauzi, Bian Yang, and Peter Nimbe. 2022. "Investigation into Phishing Risk Behaviour among Healthcare Staff" Information 13, no. 8: 392. https://doi.org/10.3390/info13080392
APA StyleYeng, P. K., Fauzi, M. A., Yang, B., & Nimbe, P. (2022). Investigation into Phishing Risk Behaviour among Healthcare Staff. Information, 13(8), 392. https://doi.org/10.3390/info13080392






