Public Key Encryption with Equality Test in a Cloud Environment
Abstract
:1. Introduction
1.1. Our Work
1.2. Related Work
1.3. Organizational Structure
2. Preliminaries
2.1. Bilinear Mapping
- (1)
- Bilinearity: holds for every , where .
- (2)
- Non-degeneracy: There exists , such that .
- (3)
- Computability: Given , there is an efficient algorithm to compute .
2.2. Isomorphism Theorem of Finite Field
2.3. Forking Lemma
2.4. The Discrete Logarithm Problem (DLP)
2.5. Two Types of Security Threats
2.6. Security Model
- (1)
- Type-I adversaries: After obtaining the trapdoor corresponding to the challenge ciphertext, try to guess the plaintext corresponding to the challenge ciphertext.
- (2)
- Type-II adversaries: Fail to obtain the trapdoor corresponding to the challenge ciphertext, but try to distinguish which plaintext the challenge ciphertext corresponds to.
3. Encryption and Authorization Scheme
3.1. System Initialization
3.2. Key Generation Algorithm
3.3. Encryption Algorithm
- (1)
- Let be the companion matrix of . According to the isomorphism theorem of finite fields we have .
- (2)
- Let . Then, generate the ciphertext , where is an n-dimensional vector composed of coefficients of , and is an matrix in which every element belongs to , so the ciphertext space after the first encryption is .
3.4. Decryption Algorithm
3.5. Authorization Algorithm
- (1)
- : User-level authorization. All of the ciphertexts of the users can be tested. The authorization algorithm is as follows: input the private key of user , and output a trapdoor ;
- (2)
- : Ciphertext-level authorization. The ciphertexts designated by the users can be tested. Let the ciphertext to be tested be . The authorization algorithm is as follows: input the private key of user and the designated ciphertext , and output a trapdoor .
3.6. Test Algorithm
- (1)
- : If the authorization is user-level authorization, the cloud server obtains the trapdoor . First, calculate , , and then judge whether is true. If not, the server outputs 0; otherwise, the server outputs 1. Then, continue to judge whether is true. If so, it means that the plaintext messages corresponding to the two ciphertexts are equal, and the server outputs 1. If not, it indicates that the plaintext messages are not equal, and the server outputs 0.
- (2)
- : If the authorization is ciphertext-level authorization, the cloud server obtains the trapdoor , . First, calculate , , and then judge whether is true. If not, the server outputs 0; otherwise, the server outputs 1. Then, continue to judge whether is true. If so, it means that the plaintext messages corresponding to the two ciphertexts are equal, and the server outputs 1. If not, it indicates that the plaintext messages are not equal, and the server outputs 0.
- (3)
- : If one of the authorizations is user-level authorization and the other is ciphertext-level authorization (it may be assumed that the user submits the user-level authorization and the user submits the ciphertext-level authorization), the cloud server obtains the trapdoor , . First, calculate , , and then judge whether is true. If not, the server outputs 0; otherwise, the server outputs 1. Then, continue to judge whether is true. If so, it means that the plaintext messages corresponding to the two ciphertexts are equal, and the server outputs 1. If not, it indicates that the plaintext messages are not equal, and the server outputs 0.
4. Scheme Analysis
4.1. Correctness Analysis
- (1)
- (Decryption correctness): For any plaintext message , there is .
- (2)
- (Test consistency): For any , if and , then .
- (3)
- (Test reliability): For any , if and , then .
- (4)
- For any ciphertext , can be recovered.
- (5)
- A logical equivalent expression can be derived from the construction process of the scheme as follows: . Given the ciphertext , , it can be calculated in three cases:① For a user-level authorization trapdoor , calculate:If , then . Continue to calculate:If , then . Therefore, can be obtained from ; that is, holds.② For a ciphertext-level authorization trapdoor , calculate:If , then . Continue to calculate:If , then . Therefore, can be obtained from ; that is, holds.③ For two different types of authorization, where one is user-level authorization and the other is ciphertext-level authorization (let user submit the user-level authorization trapdoor , and user submit the ciphertext-level authorization trapdoor ), calculate:If , then . Continue to calculate:If , then . Therefore, can be obtained from ; that is, holds.□
4.2. Security Analysis
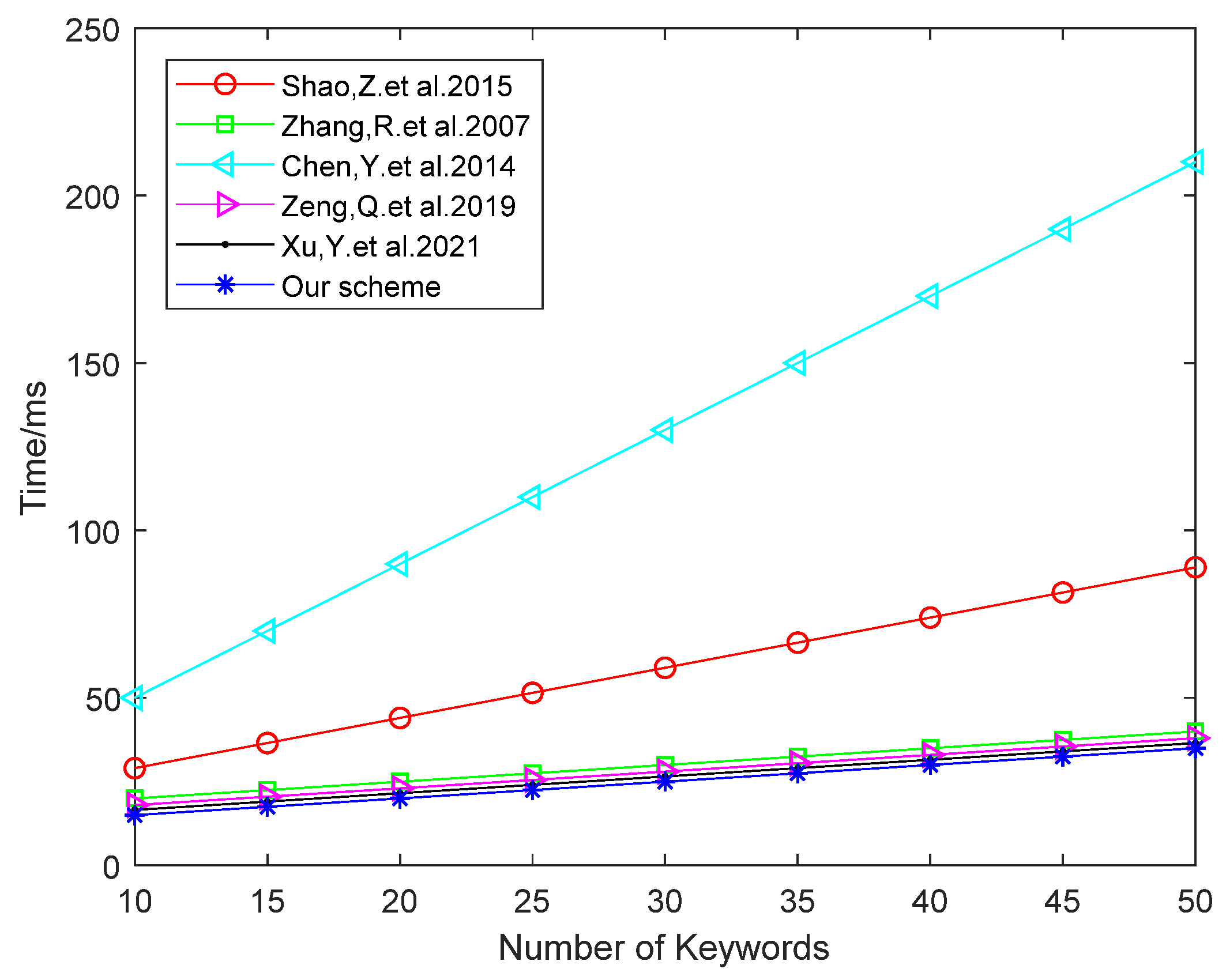
5. Performance Analysis
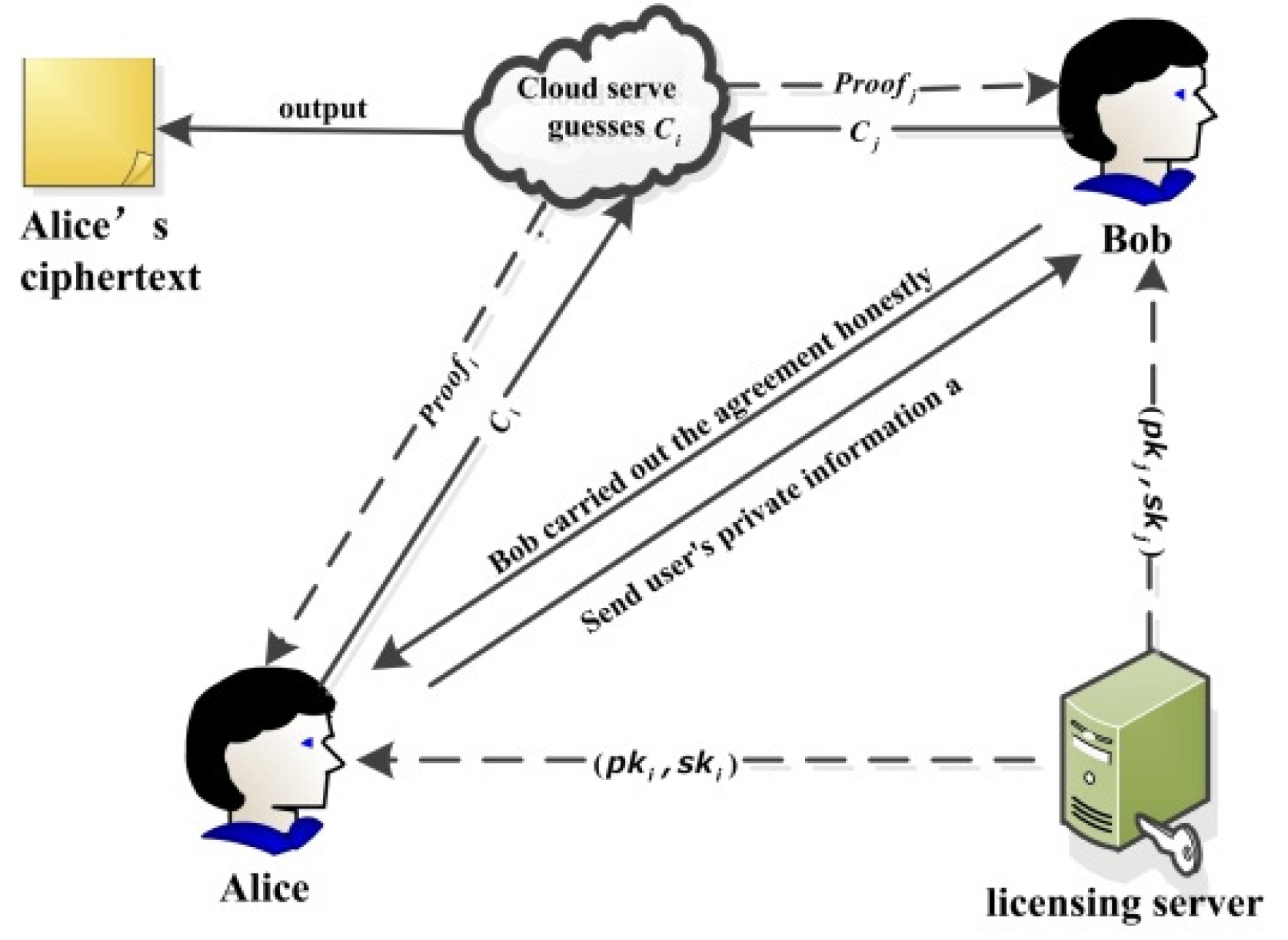
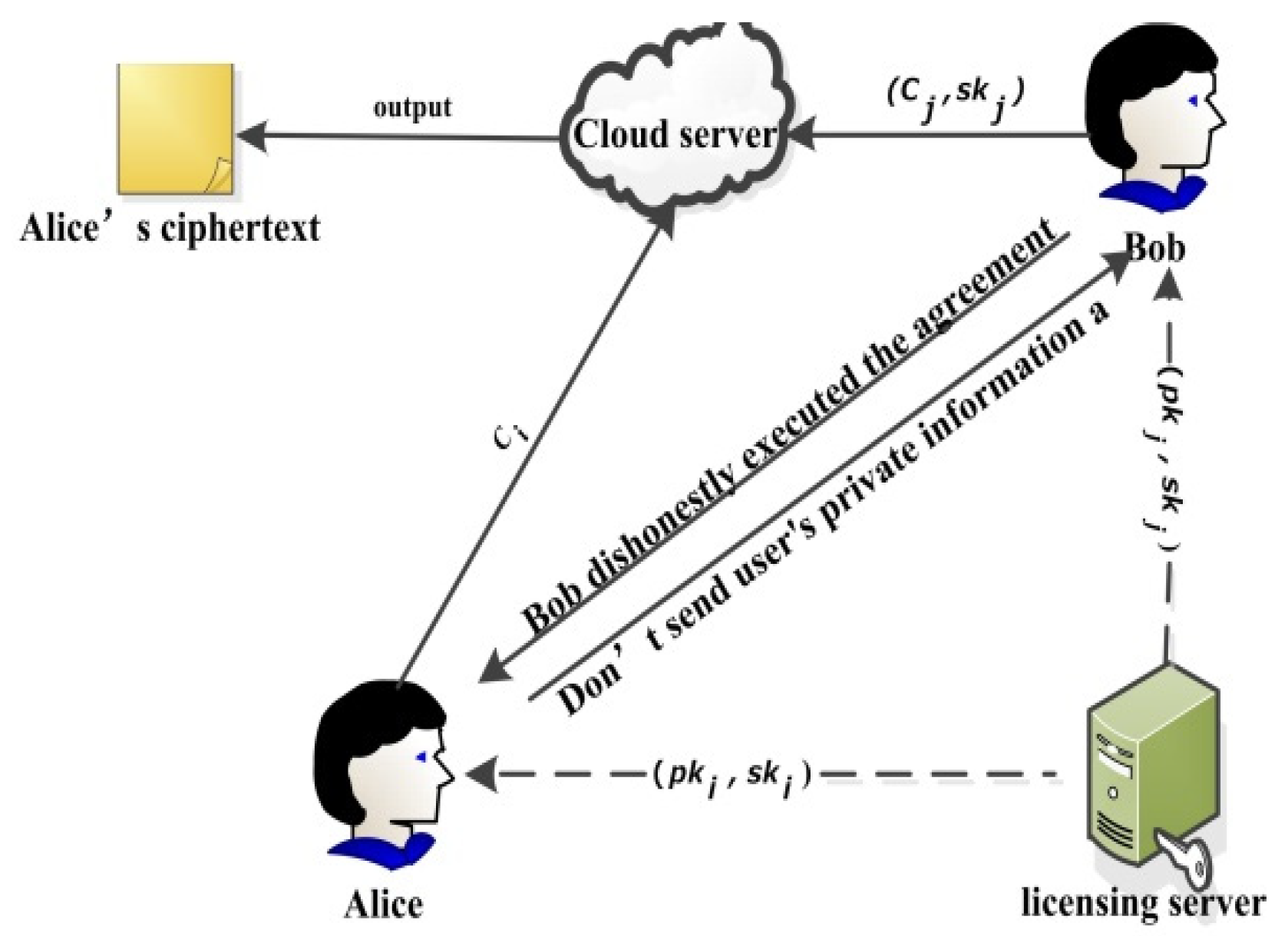
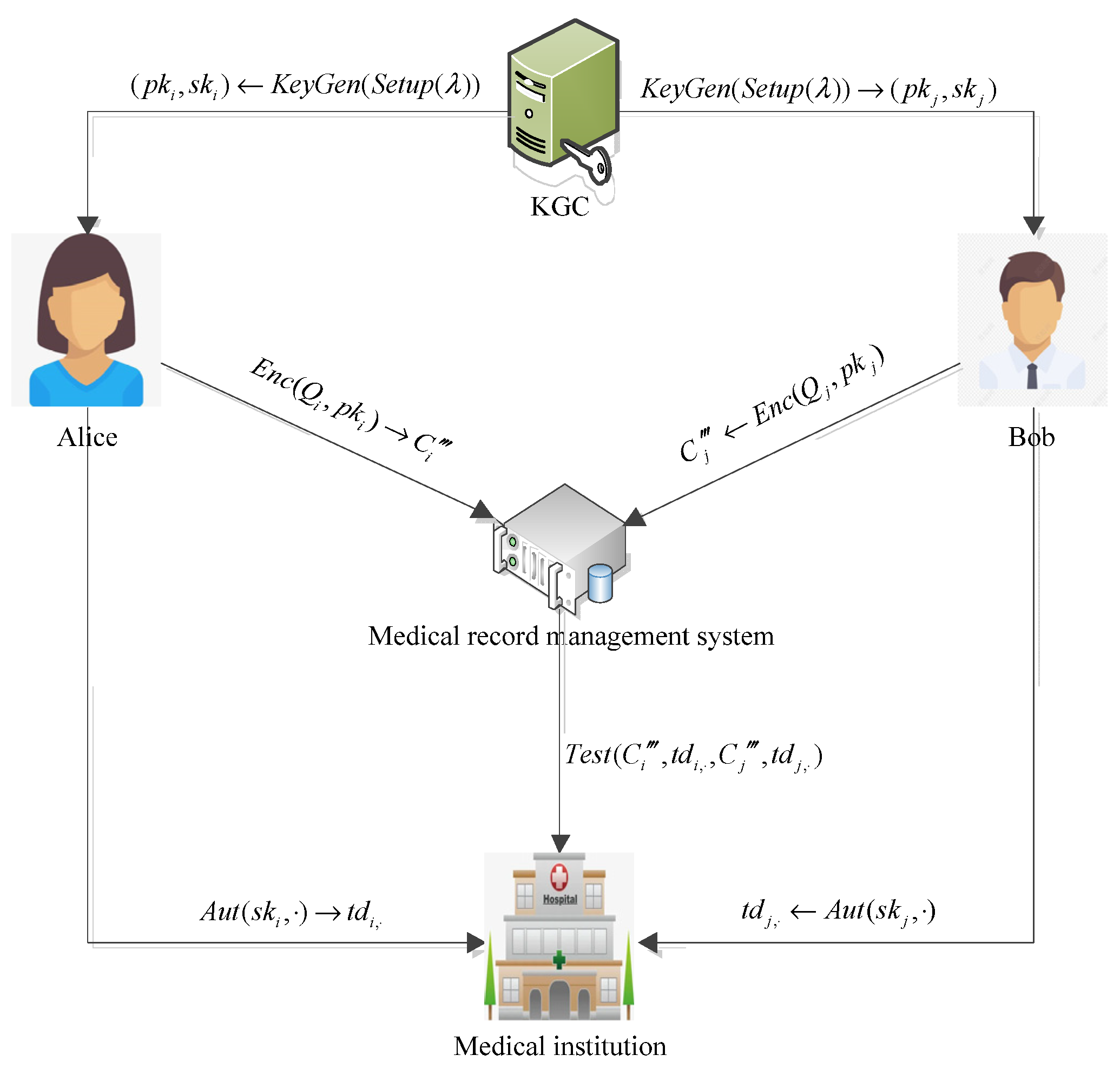
6. Application in Medical System
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bao, G.; Wang, S.; Li, Y. Research on data security protection method based on privacy perception in cloud computing. Netinfo Secur. 2017, 17, 84–89. [Google Scholar]
- Wang, Y.; Zhang, J.; Cheng, S.; Xiaohui, T. An improved design of homomorphic encryption for Cloud Computing. Netinfo Secur. 2017, 17, 21–26. [Google Scholar]
- Li, Z.; Hu, X. Research on data security and privacy protection in the background of big data. Internet Things 2020, 10, 76–78. [Google Scholar]
- Wu, H. Research on privacy data security for Internet of things. Wirel. Internet Technol. 2020, 17, 21–22. [Google Scholar]
- Shao, Z.; Yang, B. On security against the server indesignated tester public key encryption with keyword search. Inf. Process. Lett. 2015, 115, 957–961. [Google Scholar] [CrossRef]
- Zhang, R.; Imai, H. Generic combination of public key encryption with keyword search and public key encryption. In Proceedings of the International Conference on Cryptology and Network Security, Singapore, 8–10 December 2007; pp. 159–174. [Google Scholar]
- Chen, Y.; Zhang, J.; Lin, D. Generic construction of integrated PHE and PEKS. J. Des. Codes Cryptogr. 2014, 78, 493–526. [Google Scholar] [CrossRef]
- Yang, N.; Zhou, Q.; Xu, S. Searchable encryption scheme with unpaired public key authentication. J. Comput. Res. Dev. 2020, 57, 2125–2135. [Google Scholar]
- Ming, Y.; Wang, E. Identity-Based Encryption with Filtered Equality Test for Smart City Applications. J. Sens. 2019, 19, 3046. [Google Scholar] [CrossRef] [Green Version]
- Dan, B.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004. [Google Scholar]
- Baek, J.; Safavi-Nanin, R.; Susilo, W. Public key encryption with keyword search revisited. In Proceedings of the International Conference on Computational Science and Its Applications, Perugia, Italy, 30 June–3 July 2008; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Rhee, H.S.; Park, J.H.; Susilo, W.; Lee, D.H. Improved searchable public key encryption with designated tester. In Proceedings of the 4th International Symposium on Information, Computer, and Communications Security, Sydney, Australia, 10–12 March 2009. [Google Scholar]
- Fang, L.; Susilow, W.; Ge, C.; Wang, J. A secure channel free public key encryption with keyword search scheme without random oracle. In Proceedings of the International Conference on Cryptology and Network Security, Kanazawa, Japan, 12–14 December 2009; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Fang, L.; Susilow, W.; Ge, C.; Wang, J. Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inf. Sci. 2013, 238, 221–241. [Google Scholar] [CrossRef] [Green Version]
- Zeng, Q.; Han, X.; Cao, Y. An encryption scheme combining public key encryption and keyword searchable encryption. Comput. Mod. 2019, 103–107. [Google Scholar] [CrossRef]
- Wang, S.H.; Zhang, Y.X.; Wang, H.Q.; Xiao, F.; Wang, R.C. Efficient public key searchable encryption scheme against internal keyword guessing attack. Comput. Sci. 2019, 46, 91–95. [Google Scholar]
- Du, R.; Tan, A.; Tian, J. Blockchain-based public key searchable encryption scheme. J. Commun. 2020, 41, 114–122. [Google Scholar]
- Zhang, Y.; Wen, L.; Wang, H. Searchable encryption scheme without certificate authentication in multi-user environment. J. Electron. Inf. Technol. 2020, 42, 1094–1101. [Google Scholar]
- Chen, N.; Liu, C.; Huang, R. Fast public key searchable encryption scheme against internal keyword guessing attack in cloud environment. J. Electron. Inf. Technol. 2021, 43, 467–474. [Google Scholar]
- Li, Z.; Wang, X.; Wang, Z. A dynamic asymmetric searchable encryption scheme resistant to keyword guessing attack. Comput. Mod. 2021, 100–106. [Google Scholar] [CrossRef]
- Yang, G.; Tan, C.H.; Huang, Q.; Wong, D.S. Probabilistic public key encryption with equality test. In Proceedings of the Cryptogapllers’ Track at the RSA Conference, San Francisco, CA, USA, 1–5 March 2010; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Ma, S.; Huang, Q.; Zhang, M.; Yang, B. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 2015, 10, 458–470. [Google Scholar] [CrossRef]
- Lin, X.J.; Qu, H.; Zhang, X. Public Key Encryption Supporting Equality Test and Flexible Authorization without Bilinear Pairings. IACR Cryptol. Eprint Arch. 2016, 2016, 277. [Google Scholar] [CrossRef]
- Lee, H.T.; Ling, S.; Seo, J.H.; Wang, H. CCA2 Attack and Modification of Huang et al.’s Public Key Encryption with Authorized Equality Test. Comput. J. 2016, 59, 1689–1694. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K.R.; He, D. Efficient Identity-based Encryption Scheme with Equality Test for Smart City. IEEE Trans. Sustain. Comput. 2018, 3, 44–55. [Google Scholar] [CrossRef]
- Tang, Q. Towards Public Key Encryption Scheme Supporting Equality Test with Fine-grained Authorization. In Proceedings of the 16th Australasian Conference on Information Security and Privacy, Melbourne, Australia, 11–13 July 2011; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Tang, Q. Public Key Encryption Supporting Plaintext Equaliy Text and User-specified Authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef] [Green Version]
- Huang, K.; Tso, R.; Chen, Y.C.; Rahman, S.; Almogren, A.; Alamri, A. PKE-AET: Public key Encryption with Authorized Equality Test. Comput. J. 2015, 58, 2686–2697. [Google Scholar] [CrossRef]
- Xu, Y.; Wang, M.; ZHong, H.; ZHong, S. IBEET-AOK: ID-based encryption with equality test against off-line KGAs for cloud medical services. Front. Comput. Sci. 2021, 15, 178–180. [Google Scholar] [CrossRef]
- Hu, L.; Li, X.; Lu, L. An identity-based cryptosystem and elliptic curve Tate pair. Inf. Netw. Secur. 2005, 64–66. [Google Scholar] [CrossRef]
- Roger, A.H.; Charles, R.J. Matrix Analysis, 2nd ed.; China Machine Press: Beijing, China, 2014; Volume 9, pp. 86–92. [Google Scholar]
- Li, K.; Liu, H. On the trace of k elements in a finite field. Pure Math. Appl. Math. 2019, 35, 394–407. [Google Scholar]
| Scheme | Encryption Cost | Decryption Cost | Test Cost | Resist KGAs |
|---|---|---|---|---|
| Scheme in [5] | 9m + 3e + 3h | 2m | 5m + 4e + h | Yes |
| Scheme in [6] | 4m + 6e + 2h | h | e + 2m + h | No |
| Scheme in [7] | 13m + 10e + 4h | 2m + e | 3m + 2e | No |
| Scheme in [15] | 4m + 8e + 5h | e + 2h | 2m + e | Yes |
| Scheme in [29] | 6m + 2e + 2h | m + 2e + 2h | 4m + 6e + 4h | Yes |
| RKGA-CET | 8m + 3h | 2m + h | 6m + 6e + 3h | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, P.; Li, J.; Fu, Z. Public Key Encryption with Equality Test in a Cloud Environment. Information 2022, 13, 265. https://doi.org/10.3390/info13060265
Zhang P, Li J, Fu Z. Public Key Encryption with Equality Test in a Cloud Environment. Information. 2022; 13(6):265. https://doi.org/10.3390/info13060265
Chicago/Turabian StyleZhang, Ping, Jinbo Li, and Zhumu Fu. 2022. "Public Key Encryption with Equality Test in a Cloud Environment" Information 13, no. 6: 265. https://doi.org/10.3390/info13060265
APA StyleZhang, P., Li, J., & Fu, Z. (2022). Public Key Encryption with Equality Test in a Cloud Environment. Information, 13(6), 265. https://doi.org/10.3390/info13060265