Attack Graph Utilization for Wastewater Treatment Plant
Abstract
1. Introduction
State of Art
2. System Architecture
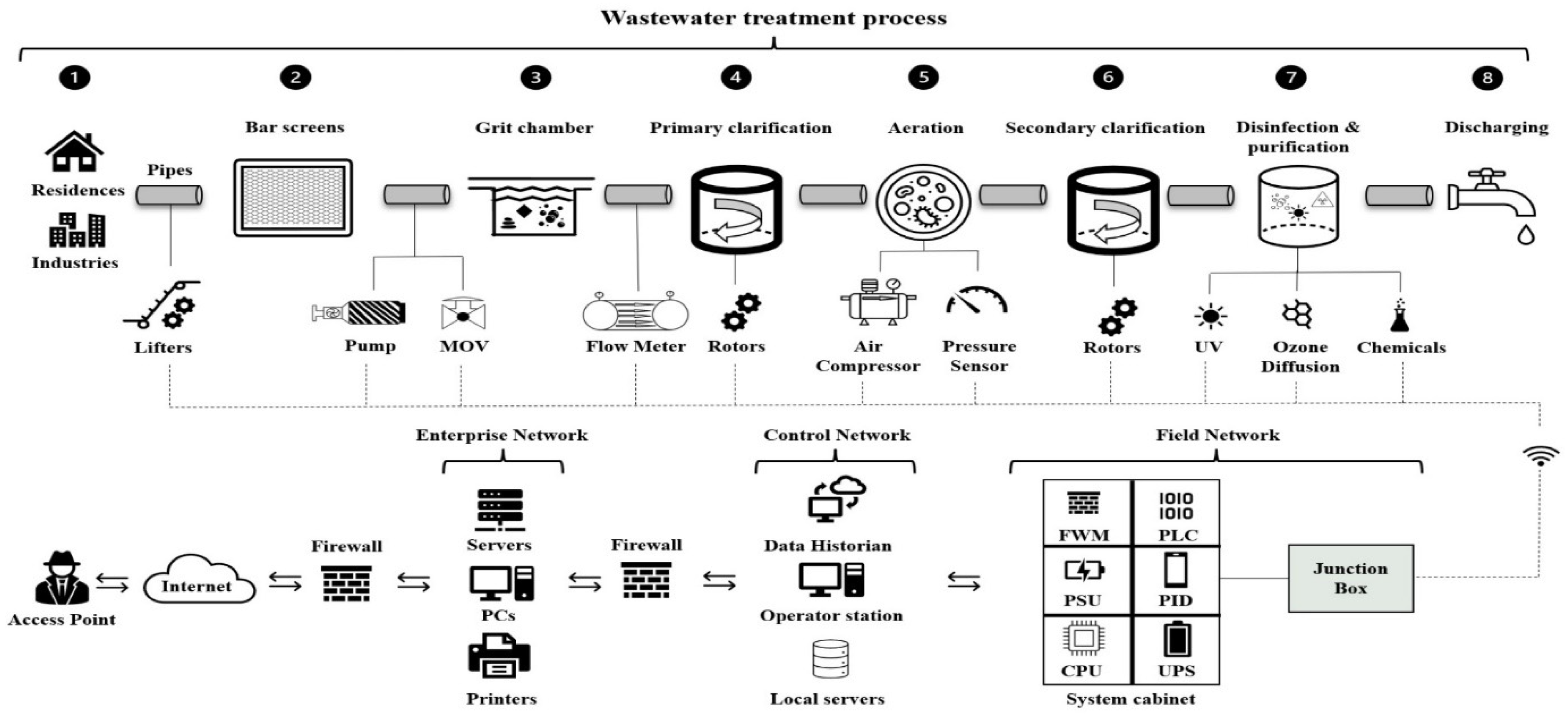
2.1. Water Treatment Process (WTP)
- Water collection: to get the water to the treatment facility, it is collected from residences and businesses and carried there using trucks or sewage pipes [20].
- Screening procedure: bar screens are used [21] to filter out any inorganic particles present in the wastewater stream, as well as trash, toys, papers, firearms, and other detritus.
- Gritting process: in order to remove heavier inorganic grit particles from the water, such as sand, silt, clay, coffee grounds, etc., a grit chamber [22] must be used.
- Primary clarifiers: These are employed to separate the wastewater’s organic components [23]. A rotating skimmer pushes floatable solids such as grease and oil into collection trough teeth at the edges of the tank and lets the water pass through while holding back the floating debris, oil, and fat. Water flows through circular basins called sedimentation tanks, where the repulsion slows the flow rate to aid the settling process. Settable solids create sludge by sinking to the angled bottom of the tank, which is then scraped into a sludge pit by scraper arms.
- Aeration: In this procedure, wastewater is infused with beneficial bacteria. These microorganisms may eat biodegradable substances such as soap, food, human waste, and detergents [24]. To provide the oxygen that these beneficial bacteria need to survive, air is pumped through the mixture.
- Secondary clarifiers: Like the primary clarifiers [25], these remove clumps that drop to the bottom of the tank. Because these clumps still contain active microbes, they can be employed again throughout the aeration process.
- Disinfection and purification: The processed water travels through pipes and pumps to the disinfection process, which is the last step. In order to eradicate the microorganisms, this technique calls for the use of ultraviolet (UV) emissions [26] inside the tank. These emissions subject the water to ultraviolet light.
- Discharging: this step involves transferring the water to other treatment facilities, rivers, or natural areas for additional testing and purification [27].
2.2. WTP Topology
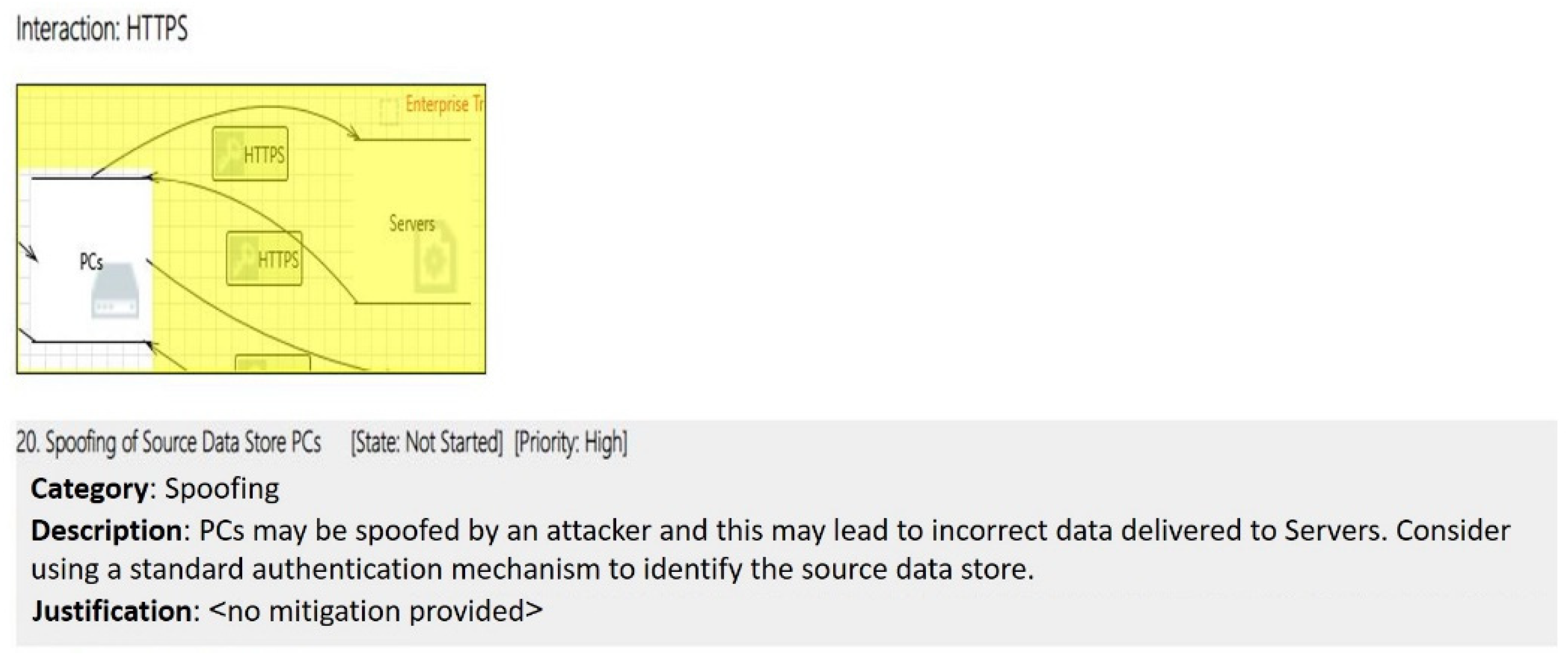
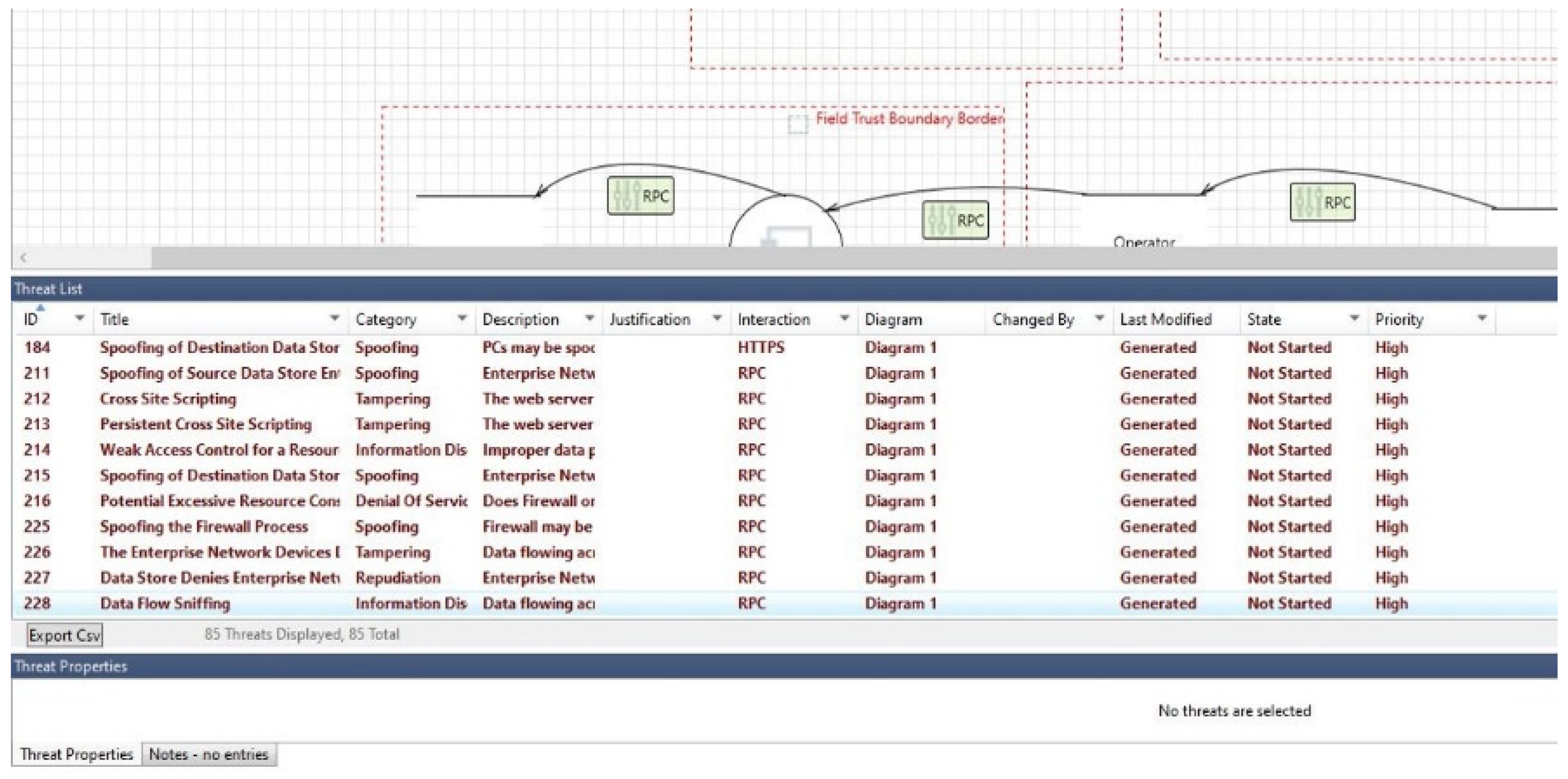
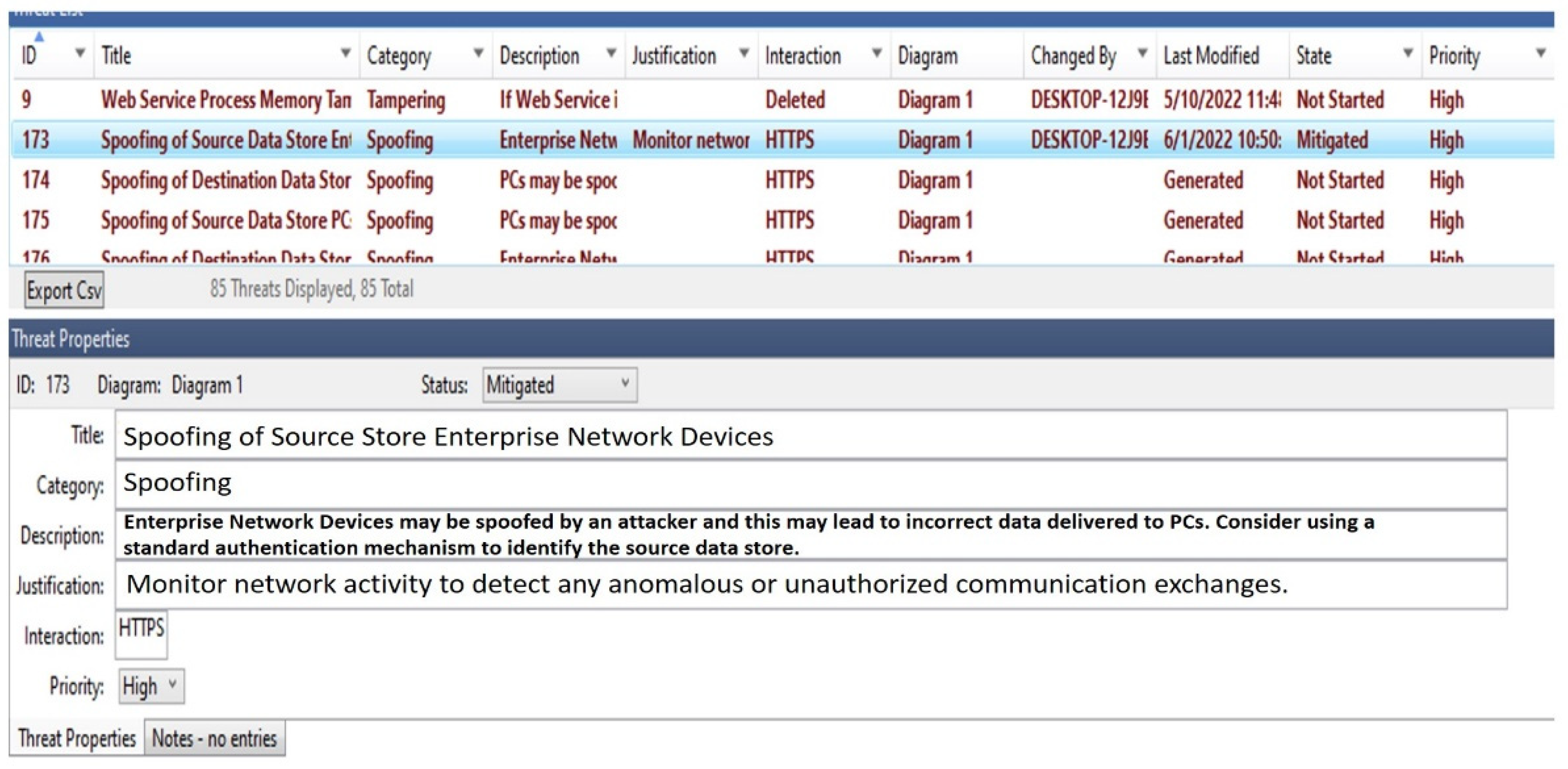
- Enterprise Level (E): In charge of overseeing workplace operations, plant finances, input on general performance, and data gathered from other plant levels. Personal computers (PCs), printers, and servers are included in this level [28]. A firewall (FW) is positioned between the outside access point (AP) and the enterprise network (EN) and monitors network traffic to block any unauthorized access or suspicious activity.
- Control Network Level (C): This level is made up of numerous components that handle incoming data from the field level network and manage terminals, network access, remote management, servers, and backups [6]. Wi-Fi connections are used to link it to the enterprise level. The C level is made up of three main parts:
- The Operator Station (OS) processes incoming data from the field network devices using supervision interfaces for the operators and engineering staff [29].
- Data Historian (DH): this program is designed to handle time series data events that are logged and recorded [30] for a variety of internal plant processes.
- Local Servers (LSs): In the event of rare occurrences [31] such as data corruption or illegal cyber activity, these save all data and backups offered by the field level devices.
- Field Level (F): this includes the following items:
- System Cabinet (SC): This serves as a link between the junction box and the control network (CN) level [32]. It uses communication modules to send and receive data to and from the sensors and actuators through the junction box. It includes the following elements:
- Power supply units (PSUs): These devices give modules power, including central processing units (CPUs) and programmable logic controllers (PLCs) [33]. When there are abrupt surges or blackouts, this module is responsible for turning on and adjusting the incoming and outgoing power supplies and providing feedback.
- Uninterrupted Power Supply (UPS): this gadget is plugged into the infrastructure cabinet and provides power if there is a malfunction or damage to the power supply units [34].
- Central Processing Unit (CPU): this component processes incoming data signals to carry out specific commands in response to input from field instruments [35].
- Programmable Logic Controller (PLC): after the CPU has processed the data, the PLC processes the given data as inputs, runs the program that has been written inside of it, and outputs the results according to the input data and programmed logic [36].
- Firewall Module (FWM): this limits access to network resources [37].
- Proportional Integral Derivative Module (PID): this is a control loop mechanism [38] that automatically calculates the errors between a desired set point and a measured process field variable and performs corrections as needed.
- Junction Box: This device, also known as a fieldbus junction box, transmits signals from field devices to the system cabinet [39].
- Industrial communication protocols such as Modbus, Profinet, and DNP3 are used by sensors and actuators in the field including pumps, flow meters and pressure sensors, motors and valves, ultraviolet radiators, ozone diffusers, and chemical releasers. They use transmitters that are included with the sensors or actuators to wirelessly communicate signals to the junction box. All incoming transmission signals from the sensors and actuators are gathered by the junction box and then forwarded to the system cabinet for computation. Feedback signals are transmitted from the system cabinet’s firewall module to the control network, where incoming data is displayed, processed, saved, and managed. The enterprise network handles the control network’s processed data, which is transferred after passing through a firewall that guards against illegal access from anyone without access rights.
2.3. Vulnerabilities and Types of Attacks
- Intelligence Gathering (IG): This can be done by gathering information that is open to the public and can be obtained without the need for special access. For the other type, specifications and data concerning the COTS- and Internet of Things (IoT)-run equipment would need to be gathered [42].
- Man-in-the-Middle (MITM): The attacker stands between the two parties as a sort of intermediary. Gaining access to the plant network opens the door to this kind of attack [43].
- Denial-of-Service (DoS): By inundating the victim or its surrounding structure with Internet traffic, the attacker disrupts the flow of traffic on a target server, resource, or network [44].
- Phishing (PH): this is a type of social engineering in which an attacker sends a false message with the goal of tricking a victim into disclosing sensitive information [45].
- Malware Injection (MI): This is the use of reconnaissance attacks by hackers to gather information and data about the network architecture and protocols [46]. As a result, the attackers will have the ability to modify and manipulate system commands as well as remote plant process units.
- Zero-Day Exploit (0-DAY): hackers can destroy networks, data, and applications by taking advantage of zero-day vulnerabilities.
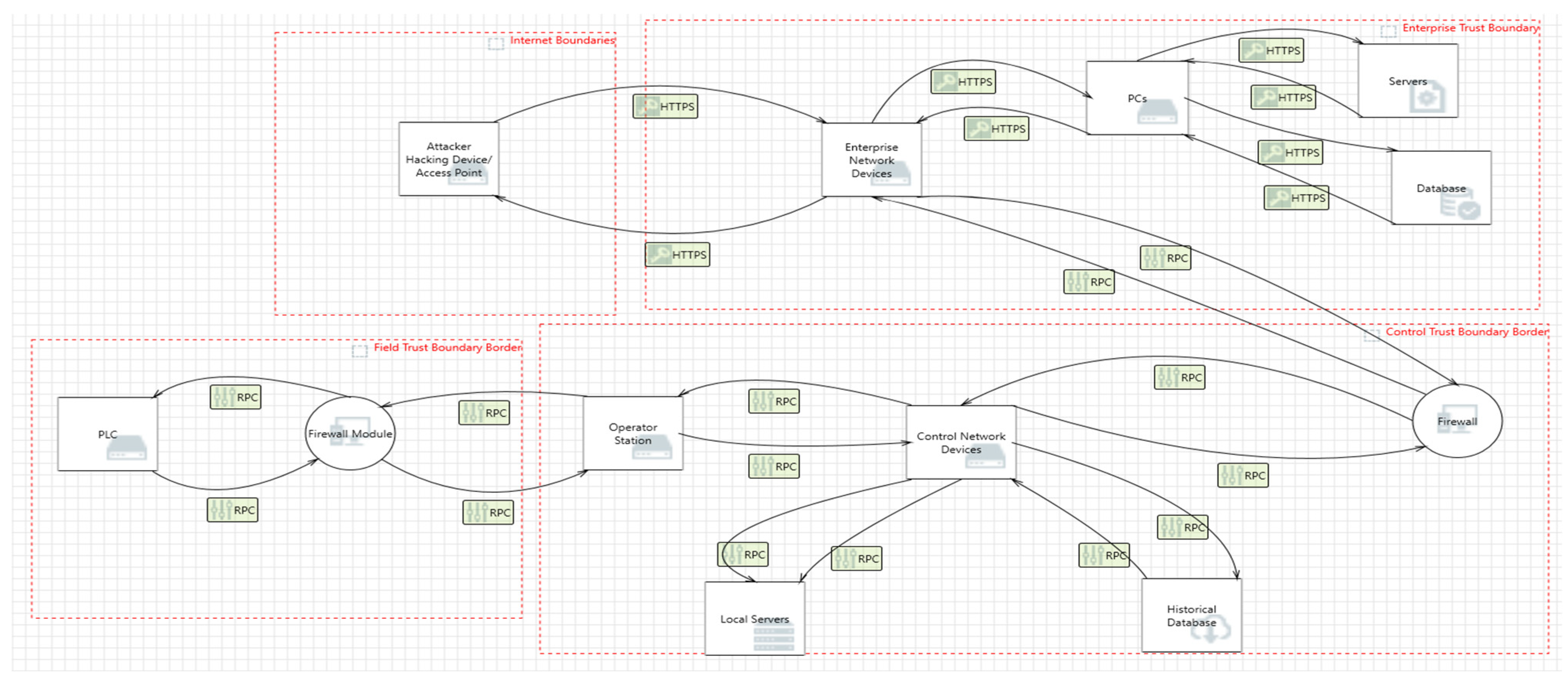
3. Attack Graph Implementation
3.1. Official Description of the WTP
- Attack starting point with root privileges is set at (AP) (static).
- Elements of Enterprise Network, EN; parameter en ∈ [PC, SE, PR] (static).
- Elements of Control Network level, CN; parameter cn ∈ [HD, OS, LS] (static).
- Elements at the Field Network level, FN; parameter fn ∈ [PLC, Sen, Act] (static).
- System connectedness, L ⊆ [EN × EN, EN × CN, CN × CN, CN × FN]; lij = 1 if component i and component j are fastened.
- Vulnerabilities V: Boolean υi = 1 if host i has susceptibility υ ∈ {COTS, Zero-Day, firmware}.
- Attacks A; parameter a ∈ {IG, MITM, DoS, PH, MI, 0-DAY}.
- Attack incidences, AI ⊆ A × {EN × EN, EN × CN, CN × CN, CN × FN}; named aij ≡ host i ambushes host j.
- Attack Permission P on host/device j ∈ [EN, CN, FN]; parameter pj ∈ {none, root}.
- Info K, Boolean kj = 1 if attacker discloses information about host j.
- Data Manipulation G, parameter gj = 1 if the attacker was successful in changing j’s data.
- Hardware administration H on appliance i ∈ {CN, FN}; Boolean hi = 1 if an attacker manages to control the device’s firmware.
- Attack pre-requirements:
- Pre(IGij) ≡ (lij = 1) ⋀ (pi = none).
- Pre(MITMij) ≡ (lij = 1) ⋀ (pi = root) ⋀ (hi = 1).
- Pre(DoSij) ≡ (lij = 1) ⋀ (pi = root) ⋀ (COTSj = 1 ⋁ firmwarej = 1).
- Pre(PHij) ≡ (lij = 1) ⋀ (pi = root) ⋀ (Ǝy ∈ EN: (ky = 1)).
- Pre(MIij) ≡ (lij = 1) ⋀ (pi = root) ⋀ (COTSj = 1 ⋁ firmwarej = 1) ⋀ (Ǝy ∈ {CN, FN}: ky = 1).
- Pre(0-DAYij) ≡ (lij = 1) ⋀ (Zero-Dayj = 1) ⋀ (Ǝy ∈ {CN, FN}: ky = 1) ⋀ (pi = root).
- Attack post-requirements:
- Post(IGij) ≡ (kj = 1).
- Post(MITMij) ≡ (kj = 1) ⋀ (gj = 1) ⋀ (pj = root) ⋀ (hj = 1).
- Post(DoSij) ≡ (kj = 1) ⋀ (gj = 1) ⋀ (pj = root) ⋀ (hj = 1).
- Post(PHij) ≡ (kj = 1) ⋀ (pj = root).
- Post(MIij) ≡ (kj = 1) ⋀ (gj = 1) ⋀ (pj = root).
- Post(0-DAYij) ≡ (pj = root).
- Preliminary status: pAP = root ⋀ (Ɐj ∈ {EN, CN, FN}: pj = none ⋀ (kj = gj = hj = 0)).
- Security indicator α demonstrates the attacker’s failure to hack WTP. The indicator’s computational tree logic (CTL) expression is as follows:α ≡ AG((hFN = 0), that is AG(¬ (hFN = 1)).
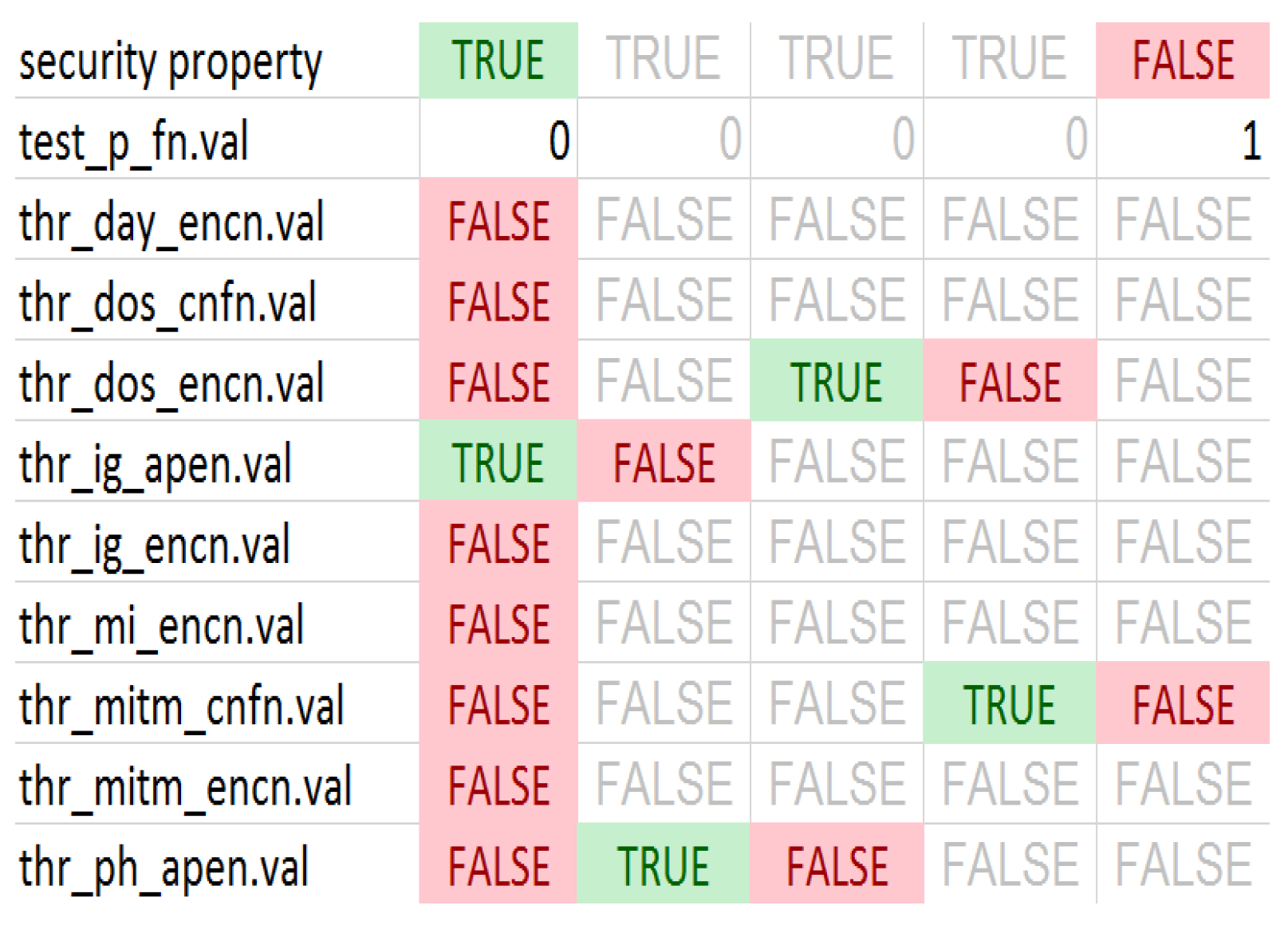
3.2. Attack Scenario Generation
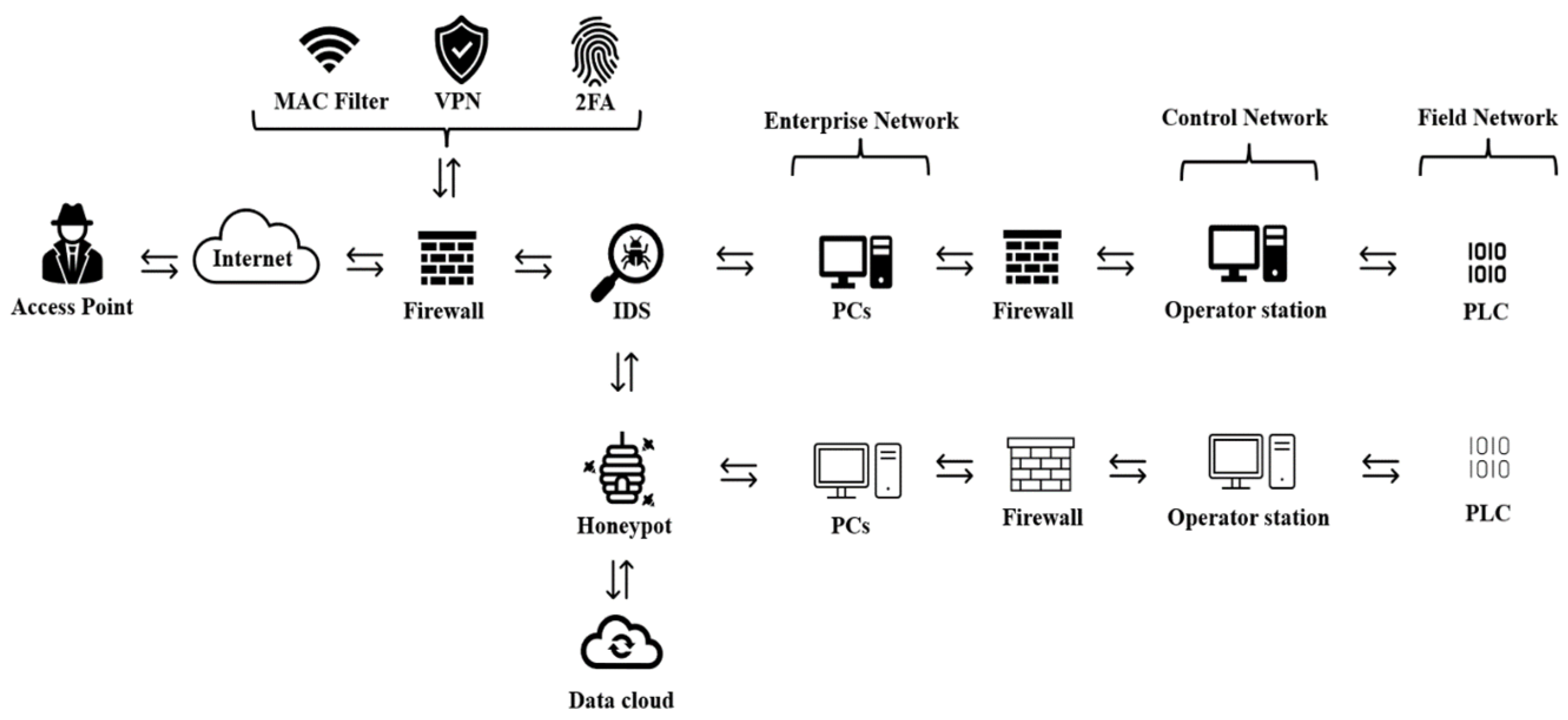
4. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gerston, J. Water and Wastewater Utilities Enhance System Security. Available online: https://twri.tamu.edu/media/3885/volume-27-december-2002.pdf (accessed on 20 September 2022).
- Lemaire, L.; Lapon, J.; Decker, B.D.; Naessens, V. A SysML Extension for Security Analysis of Industrial Control Systems. Available online: https://ucl.scienceopen.com/document_file/341d79cf-3e6e-4778-9994-73bdd4222907/ScienceOpen/001_Lemaire.pdf (accessed on 20 September 2022).
- Lemaire, L.; Vossaert, J.; Jansen, J.; Naessens, V. A logic-based framework for the security analysis of Industrial Control Systems. Autom. Control Comput. Sci. 2017, 51, 114–123. [Google Scholar] [CrossRef]
- Stanculescu, M.; Badea, C.A.; Marinescu, I.; Andrei, P.; Drosu, O.; Andrei, H. Vulnerability of SCADA and security solutions for a waste water treatment plant. In Proceedings of the 11th International Symposium on Advanced Topics in Electrical Engineering (ATEE), Bucharest, Romania, 28–30 March 2019. [Google Scholar]
- Azevedo, M.T.; Martins, A.B.; Kofuji, S.T. ISA99-Security Standards in water treatment plants. In Proceedings of the Water/Wastewater Automatic Controls Symposium, Orlando, FL, USA, 6–8 August 2013. [Google Scholar]
- Tuptuk, N.; Hazell, P.; Watson, J.; Hailes, S. A Systematic Review of the State of Cyber-Security in Water Systems. Water 2021, 13, 81. [Google Scholar] [CrossRef]
- Gunda, T.; Hess, D.; Hornberger, G.M.; Worland, S. Water security in practice: The quantity-quality-society nexus. Water Secur. 2018, 6, 100022. [Google Scholar] [CrossRef]
- Grigg, N.S. Water Utility Security: Multiple Hazards and Multiple Barriers. J. Infrastruct. Syst. 2003, 9, 81–88. [Google Scholar] [CrossRef]
- Panguluri, S.; Phillips, W.; Cusimano, J. Protecting water and wastewater infrastructure from cyber attacks. Front. Earth Sci. 2011, 5, 406–413. [Google Scholar] [CrossRef]
- Iaiani, M.; Moreno, V.C.; Reniers, G.; Tugnoli, A.; Cozzani, V. Analysis of events involving the intentional release of hazardous substances from industrial facilities. Reliab. Eng. Syst. Saf. 2021, 212, 107593. [Google Scholar] [CrossRef]
- Hassanzadeh, A.; Rasekh, A.; Galelli, S.; Aghashahi, M.; Taormina, R.; Ostfeld, A.; Banks, K. A review of cybersecurity incidents in the water sector. arXiv 2020, arXiv:2001.11144. [Google Scholar] [CrossRef]
- Ackerman, G.; Abhayaratne, P.; Bale, J.; Bhattacharjee, A.; Blair, C.; Hansell, L.; Jayne, A.; Kosal, M.; Lucas, S.; Moran, K.; et al. Assessing Terrorist Motivations for Attacking Critical Infrastructure; Lawrence Livermore National Lab.: Livermore, CA, USA, 2006. [Google Scholar] [CrossRef]
- Ibrahim, M.; Elhafiz, R. Security Analysis of Smart Grids. Secur. Commun. Netw. 2022, 2022, 7199301. [Google Scholar] [CrossRef]
- Kaynar, K.; Sivrikaya, F. Distributed attack graph generation. In IEEE Transactions on Dependable and Secure Computing; IEEE Computer Society Press: Los Alamitos, CA, USA, 2015; Volume 13, pp. 519–532. [Google Scholar]
- Stan, O.; Bitton, R.; Ezrets, M.; Dadon, M.; Inokuchi, M.; Ohta, Y.; Yamada, Y.; Yagyu, T.; Elovici, Y.; Shabtai, A. Extending Attack Graphs to Represent Cyber-Attacks in Communication Protocols and Modern IT Networks. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1936–1954. [Google Scholar] [CrossRef]
- Feng, Y.; Sun, G.; Liu, Z.; Wu, C.; Zhu, X.; Wang, Z.; Wang, B. Attack Graph Generation and Visualization for Industrial Control Network. In Proceedings of the 2020 39th Chinese Control Conference (CCC), Shenyang, China, 27–29 July 2020; pp. 7655–7660. [Google Scholar] [CrossRef]
- Imano, M.; Yuan, X. Evaluating the effectiveness of microsoft threat modeling tool. In Proceedings of the 2015 Information Security Curriculum Development Conference, Kennesaw, GA, USA, 10 October 2015. [Google Scholar]
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-Attack Modeling Analysis Techniques: An Overview. In Proceedings of the 4th International Conference on Future Internet of Things and Cloud Workshops, Vienna, Austria, 22–24 August 2016. [Google Scholar]
- Jbair, M.; Ahmad, B.; Maple, C.; Harrison, R. Threat modelling for industrial cyber physical systems in the era of smart manufacturing. Comput. Ind. 2022, 137, 103611. [Google Scholar] [CrossRef]
- PCS 7 Water Unit Template—External Pump Station of a Wastewater Treatment Plant (WWTP) with S7-300. Available online: https://support.industry.siemens.com/cs/document/109481486/pcs-7-water-unit-template-%E2%80%93-external-pump-station-of-a-wastewater-treatment-plant-(wwtp)-?dti=0&lc=en-CR (accessed on 8 August 2022).
- Water and Wastewater Treatment Solutions for Wastewater and Drinking Water Treatment. Available online: https://www.phoenixcontact.com/assets/downloads_ed/global/web_dwl_promotion/5177187_EN_HQ_water_management_LoRes.pdf (accessed on 8 August 2022).
- U.S. Department of Homeland Security. Characteristics and common vulnerabilities infrastructure category: Community wastewater treatment facilities. In Protective Security Division Department of Homeland Security DRAFT—Version 1; U.S. Department of Homeland Security: Williston, VT, USA, 2004. [Google Scholar]
- Abdelrahman, A.M.; Aras, M.F.; Cicekalan, B.; Fakioglu, M.; Cingoz, S.; Basa, S.; Guven, H.; Ozgun, H.; Ozturk, I.; Koyuncu, I.; et al. Primary and A-sludge treatment by anaerobic membrane bioreactors in view of energy-positive wastewater treatment plants. Bioresour. Technol. 2022, 351, 126965. [Google Scholar] [CrossRef] [PubMed]
- Instrumentation for the Water & Wastewater Industries Enhanced Plant Performance, Efficiency, and Reliability. Available online: https://library.e.abb.com/public/4c9318456366bf77c1257b1a005b4fcf/PB_WaterIndustry_Issue%201-low.pdf (accessed on 8 August 2022).
- Abbasi, N.; Ahmadi, M.; Naseri, M. Quality and cost analysis of a wastewater treatment plant using GPS-X and CapdetWorks simulation programs. J. Environ. Manag. 2021, 284, 111993. [Google Scholar] [CrossRef] [PubMed]
- The Water Research Commission. Handbook for the Operation of Water Treatment Works; Schutte, K., Ed.; The Water Institute of Southern Africa: Randjespark, South Africa, 2006. [Google Scholar]
- Baruth, E.E. American Water Works Association American Society of Civil Engineers. In Water Treatment Plant Design; American Water Works Association: Denver, CO, USA, 2005. [Google Scholar]
- Calvo, I.; Etxeberria-Agiriano, I.; Iñigo, M.A.; González-Nalda, P. Key Vulnerabilities of Industrial Automation and Control Systems and Recommendations to Prevent Cyber-Attacks. Int. J. Online Eng. 2016, 12, 9–16. [Google Scholar] [CrossRef]
- Shen, J.; Feng, D. Vulnerability analysis of CSP based on stochastic game theory. J. Control Sci. Eng. 2016, 2016, 4147251. [Google Scholar] [CrossRef]
- Zhu, W.; Wang, Z.; Zhang, Z. Renovation of Automation System Based on Industrial Internet of Things: A Case Study of a Sewage Treatment Plant. Sensors 2020, 20, 2175. [Google Scholar] [CrossRef]
- Iaiani, M.; Tugnoli, A.; Bonvicini, S.; Cozzani, V. Analysis of Cybersecurity-related Incidents in the Process Industry. Reliab. Eng. Syst. Saf. 2021, 209, 107485. [Google Scholar] [CrossRef]
- Guruprakash, S.; Rajendra, S.; Singh, P. Automation and supply of distributed control systems for crude oil field industries. Int. Res. J. Eng. Technol. IRJET 2020, 7, 6155–6161. [Google Scholar]
- Pongswatd, S.; Smerpitak, K.; Asadi, F.; Thepmanee, T. Design of PLC-based system for linearity output voltage of AC–DC converter. Energy Rep. 2021, 8, 972–978. [Google Scholar] [CrossRef]
- Fan, Y.; Qian, F.; Huang, Y.; Sifat, I.; Zhang, C.; Depasquale, A.; Wang, L.; Li, B. Miniature microbial fuel cells integrated with triggered power management systems to power wastewater sensors in an uninterrupted mode. Appl. Energy 2021, 302, 117556. [Google Scholar] [CrossRef]
- Vadi, S.; Bayindir, R.; Toplar, Y.; Colak, I. Induction motor control system with a Programmable Logic Controller (PLC) and Profibus communication for industrial plants—An experimental setup. ISA Trans. 2021, 122, 459–471. [Google Scholar] [CrossRef]
- Rais, M.H.; Awad, R.A.; Lopez, J., Jr.; Ahmed, I. Memory forensic analysis of a programmable logic controller in industrial control systems. Forensic Sci. Int. Digit. Investig. 2022, 40, 301339. [Google Scholar] [CrossRef]
- Okhravi, H.; Sheldon, F.T.; Haines, J. Data Diodes in Support of Trustworthy Cyber Infrastructure and Net-Centric Cyber Decision Support. In Optimization and Security Challenges in Smart Power Grids. Energy Systems; Springer: Berlin/Heidelberg, Germany, 2013; pp. 203–216. [Google Scholar] [CrossRef]
- Lin, Q.; Yuan, Y.; Zan, F.; Lu, H.; Wang, Z.; Guo, G. A novel online analyzer for accurate and rapid measurement of volatile fatty acids in anaerobic wastewater treatment. J. Environ. Sci. 2022, 122, 72–82. [Google Scholar] [CrossRef]
- Petersena, S.; Myhrea, B.; Røstumb, J. CCWIWireless instrumentation for the water and wastewater industry. In Proceedings of the 12th International Conference on Computing and Control for the Water Industry, Perugia, Italy, 2–4 September 2013. [Google Scholar]
- Longueira-Romero, Á.; Iglesias, R.; Flores, J.L.; Garitano, I. A Novel Model for Vulnerability Analysis through Enhanced Directed Graphs and Quantitative Metrics. Sensors 2022, 22, 2126. [Google Scholar] [CrossRef] [PubMed]
- Tran, H.; Campos-Nanez, E.; Fomin, P.; Wasek, J. Cyber resilience recovery model to combat zero-day malware attacks. Comput. Secur. 2016, 61, 19–31. [Google Scholar] [CrossRef]
- Elvis, E.Y.-B.; Elvis, A.-B. Cyber-Security Intelligence Gathering: Issues with Knowledge Management. In Cyber Security and Threats: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2018. [Google Scholar]
- Khelif, M.A.; Lorandel, J.; Romain, O.; Regnery, M.; Baheux, D.; Barbu, G. Toward a hardware man-in-the-middle attack on PCIe bus. Microprocess. Microsystems 2020, 77, 103198. [Google Scholar] [CrossRef]
- Ramtin, A.R.; Nain, P.; Menasche, D.S.; Towsley, D.; de Souza, E. Fundamental scaling laws of covert DDoS attacks. Perform. Eval. 2021, 151, 102236. [Google Scholar] [CrossRef]
- Qabajeh, I.; Thabtah, F.; Chiclana, F. A recent review of conventional vs. automated cybersecurity anti-phishing techniques. Comput. Sci. Rev. 2018, 29, 44–55. [Google Scholar] [CrossRef]
- Huda, S.; Abawajy, J.; Al-Rubaie, B.; Pan, L.; Hassan, M.M. Automatic extraction and integration of behavioural indicators of malware for protection of cyber–physical networks. Futur. Gener. Comput. Syst. 2019, 101, 1247–1258. [Google Scholar] [CrossRef]
- Sari, R.D.; Supiyandi, S.; Siahaan, A.P.U. A Review of IP and MAC Address Filtering in Wireless Network Security. Int. J. Sci. Res. Sci. Technol. 2017, 3, 470–473. [Google Scholar] [CrossRef]
- Jaha, A.A.; Ben Shatwan, F.; Ashibani, M. Proper Virtual Private Network (VPN) Solution. In Proceedings of the 2008 The Second International Conference on Next Generation Mobile Applications, Services, and Technologies, Cardiff, UK, 16–19 September 2008; pp. 309–314. [Google Scholar] [CrossRef]
- Nath, A.; Mondal, T. Issues and Challenges in Two Factor Authentication Algorithms. Int. J. Latest Trends Eng. Technol. 2016, 6, 318–327. [Google Scholar]
- Jain, Y.K.; Singh, S. Honeypot based Secure Network System. Int. J. Comput. Sci. Eng. 2021, 3, 612–620. [Google Scholar]
- Scandariato, R.; Wuyts, K.; Joosen, W. A descriptive study of Microsoft’s threat modeling technique. Requir. Eng. 2013, 20, 163–180. [Google Scholar] [CrossRef]
- Al Ghazo, A.; Ibrahim, M.; Ren, H.; Kumar, R. A2G2V: Automatic Attack Graph Generation and Visualization and Its Ap-plications to Computer and SCADA Networks. IEEE Trans. Syst. Man Cybern Syst. 2019, 50, 3488–3498. [Google Scholar] [CrossRef]
- Schnoebelen, P. The Complexity of Temporal Logic Model Checking. Adv. Modal Log. 2002, 4, 35–79. [Google Scholar]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ibrahim, M.; Al-Wadi, A. Attack Graph Utilization for Wastewater Treatment Plant. Information 2022, 13, 494. https://doi.org/10.3390/info13100494
Ibrahim M, Al-Wadi A. Attack Graph Utilization for Wastewater Treatment Plant. Information. 2022; 13(10):494. https://doi.org/10.3390/info13100494
Chicago/Turabian StyleIbrahim, Mariam, and Abdallah Al-Wadi. 2022. "Attack Graph Utilization for Wastewater Treatment Plant" Information 13, no. 10: 494. https://doi.org/10.3390/info13100494
APA StyleIbrahim, M., & Al-Wadi, A. (2022). Attack Graph Utilization for Wastewater Treatment Plant. Information, 13(10), 494. https://doi.org/10.3390/info13100494





