RSA-CP-IDABE: A Secure Framework for Multi-User and Multi-Owner Cloud Environment
Abstract
1. Introduction
- (a)
- An Automated Cloud Authority (ACA) is established to issue the certificates and keys for both the user and multi owners only after the registration in the cloud.
- (b)
- Each of the users and secondary owners is provided with the distinct secret keys to access the data on the cloud-based on their attributes.
- (c)
- Since the data is double encrypted, only authorized people can access the data or make any modifications.
- (d)
- With the usage of different secret keys on both the user and the owner’s side, the confidentiality and integrity of the data are ensured through the proposed scheme.
- (e)
- Prevents the MITM attack effectively in the cloud environment.
2. Related Work
3. Preliminaries
3.1. CP-IDABE
- Attributes: In the proposed model, the attributes of the user/owner can be anything coming from the set of five random questions provided randomly by ACA. The five random questions provided in the present schemes are (i) primary job (ii) last three digits of credit card (iii) native place (iv) favorite sports (v) favorite team.
- Policy: The access policy is very significant in the proposed model, as it is established over the multi-owner and multi-user cloud environment through ACA. In addition to the authorized access to the data, the access policy also provides privileges like editing and removing the data for multiple owners. However, users must be restricted only to access the data, and they do not have the privileges to edit it. In general, the access policy for the owners are defined as (AO , and the users are defined as (AU . When the above conditions are satisfied, the access will be approved, or else it will be denied.
- 1.
- Setup (): The public key, PUK, and the master key, MAK, are generated for the user and the owner based on security parameter P through ACA. Similarly, the public key and the master key are generated for the RSA algorithm as PUKR and MAKR, respectively.
- 2.
- KeyGen (MAK, AO, IDi): given the owner attributes AO and MAK, with the identity (IDi), this algorithm yields the private key of owner OSKi.
- 3.
- Enc (PUK, M, IDi, A): given PUK, user identity IDi with access policy set A, the ciphertext Et is generated with the message M.
- 4.
- Dec (OSKi, Et): given the secret key OSKi, a ciphertext Et is decrypted through the owner attributes AO and user identity IDi to get the message M.
- KeyGen (MAK, AU, IDj): given the owner attributes AU and MAK, with the identity (IDj), this algorithm yields the private key of owner USKi.
- Enc (PUK, M, IDj, A): given PUK, user identity IDj with access policy set A, the ciphertext Et is generated with the message M.
- Dec (USKi, Et): given the secret key USKi, a ciphertext Et is decrypted through the AU and IDj to get the message M.
3.2. RSA-Cryptology
- Enc (M’, PUKR): given key PUKR, a message M’ yield final ciphertext Et’.
- Dec (KRi, Et’): given key KRi, this algorithm yields the message M’ from Et’.
- Step 1:
- estimate N = LxM
- Step 2:
- estimate
- Step 3:
- choose integer e
- Step 4:
- GCD (; 1 < e <
- Step 5:
- calculate d
- de mod
- public key PUKR = {e, n}
- private key KR = {d, n}.
3.3. Digital Signature
- SignGen (IDi, IDj, A): with the user/owner identity along with their access policy A, yields digital signature DU and DO for the user and owner, respectively, with the verifying message VM.
4. System Model
4.1. Description of the System Model
- Automated Cloud Authority (ACA): This component is employed to register the users and the owners of the data. Initially, the primary owner of the data registers and obtains the secret key for uploading and accessing the cloud data. The principal owner approves other owners through ACA only. The owners can approve any users through the ACA. The ACA access the attribute set of both the user and owner and generate the keys that are used by them to access the data. The ACA controls access over the data through verification of the keys for both users and owners distinctly.
- Cloud: It is a vital component in the proposed framework that stores the encrypted data. The encryption over the data is initially performed with the CP-IDABE using the attribute policy set. Then, the RSA algorithm is applied over encrypted data and stored in the cloud. The user processes the request for data from the cloud and receives it for accessing it.
- Multi-owner: It is the group of people who possess the privilege to access the data and modify or update it regularly. In the proposed framework, the data has one primary owner who monitors and controls other owners through ACA. The multi-owners provide access to multiple users and track their access over the data. The primary owner can revoke the secondary owner at any stage. Similarly, the owner can revoke the user over suspicious activity through ACA.
- Multi-user: The user in the cloud environment accesses the data through a secret key. The user is authorized by anyone of the multi-owners of the data in the cloud. The user has the privilege to access the data, but they are not allowed to modify or update the cloud data. The data owner through ACA can revoke the user at the time because of any suspicious activities.
4.2. Security Analysis
5. Construction of the Algorithm
5.1. Digital Signature
5.1.1. For Owners
- DO, VMO ← SignGen (IDi, AO): the ACA gets the identity of the owner IDi along with the attributes of the owner AO to generate the digital signature DO with the verifying message VMO.
- Verify ← DO, VMO: the owner can be verified with the generated digital signature DO and verifying message VMO.
5.1.2. For Users
- DU, VMU ← SignGen (IDj, AU): the ACA gets the identity of the user IDj along with the attributes of the user AU to generate the digital signature DU with the verifying message VMU.
- Verify ← DU, VMU: the user can be verified with the generated digital signature DU and verifying message VMU.
5.2. Key Generation with CP-IDABE & RSA
5.2.1. For Owners
- OSKi ← KeyGen (MAK, AO IDi): this algorithm uses the master key, MAK, generated by the ACA, along with the identity IDi and attributes of the owner, AO, respectively, to generate the secret key for the owner OSKi.
- Et ← Enc (PUK, M, IDi, A): based on the attribute policy set A, the identity of the owner IDi and the public key, PUK, the data is encrypted with the message M to obtain the ciphertext, Et.
- Et’ ← Enc (Et, M’, PUKR): when the ciphertext Et is obtained, by applying the public key, PUKR, with the message M’, the ciphertext is again encrypted as Et’.
- M’ ← Dec (KRi, Et’): using the secret key KRi, the encrypted data Et’ will yield the decrypted message M’.
- M ← Dec (OSKi, Et): using the secret key OSKi, a ciphertext Et is decrypted through the message M.
5.2.2. For Users
- USKj ← KeyGen (MAK, AU, IDj): this algorithm uses the master key, MAK, generated by the ACA along with the identity and attributes of the user IDj and AU, respectively, to generate the secret key for the owner USKj.
- Et ← Enc (PUK, M, IDj, A): based on the attribute policy set A, the identity of the user, IDj, and the public key, PUK, the data is encrypted with the message M to obtain the ciphertext, Et.
- Et’ ← Enc (Et, M’, PUKR): when the ciphertext Et is attained, by applying the public key, PUKR, with the message M’, the ciphertext is again encrypted as Et’.
- M’ ← Dec (KRj, Et’): using the secret key KRj, the encrypted data Et’ will yield the decrypted message M’.
- M ← Dec (USKj, Et): using the secret key USKj, a ciphertext Et is decrypted through the message M.
6. Results & Discussion
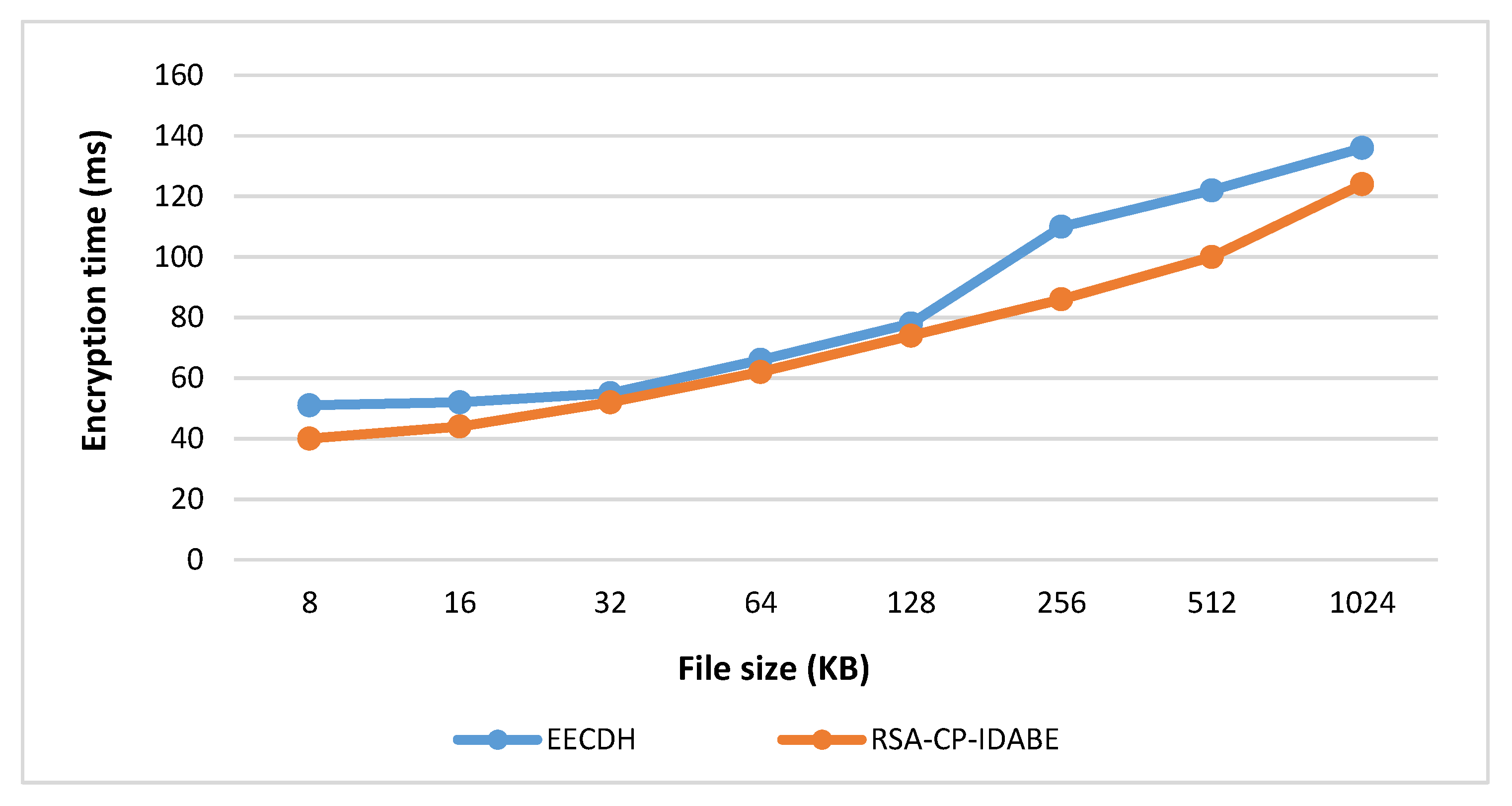
6.1. Encryption Time
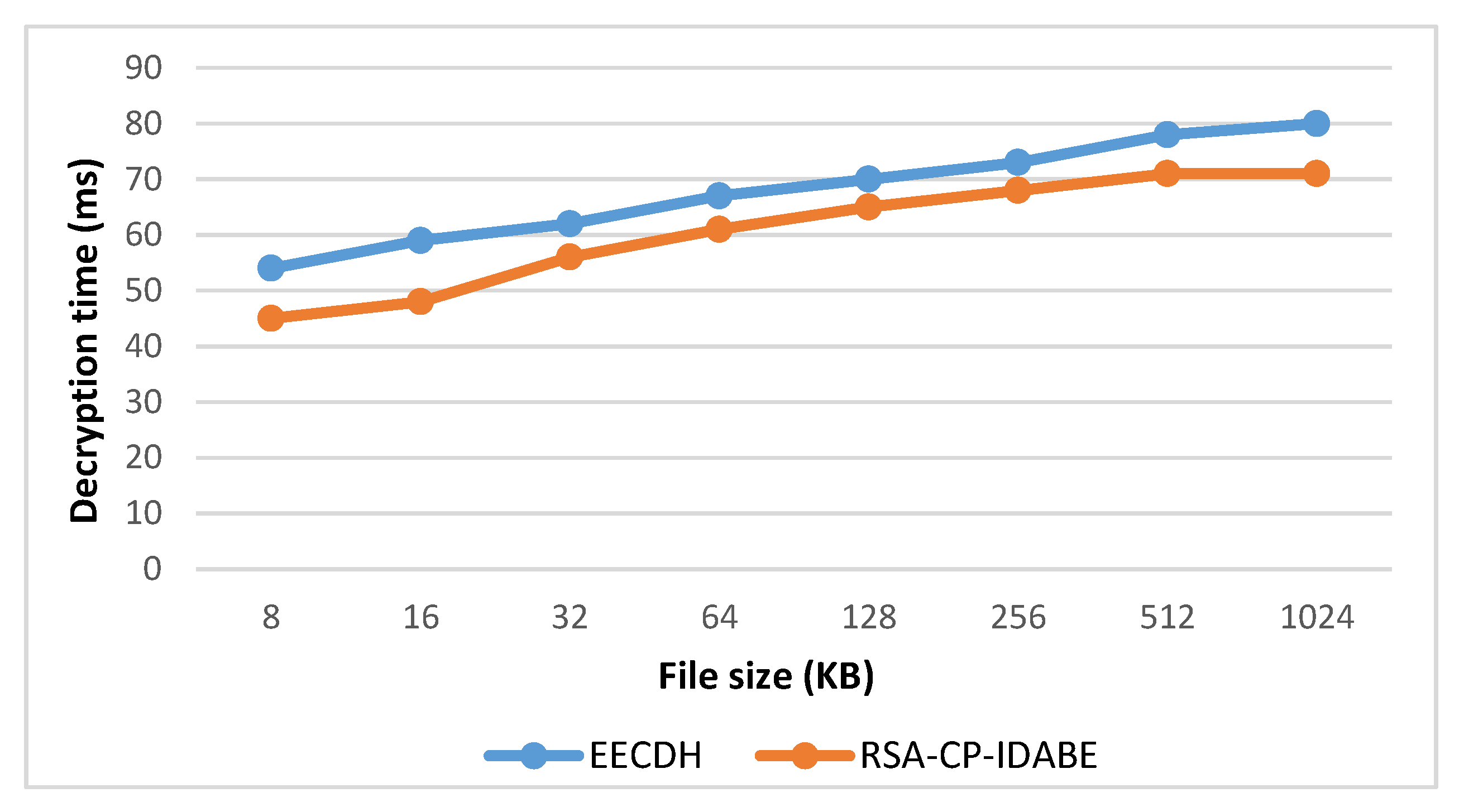
6.2. Decryption Time
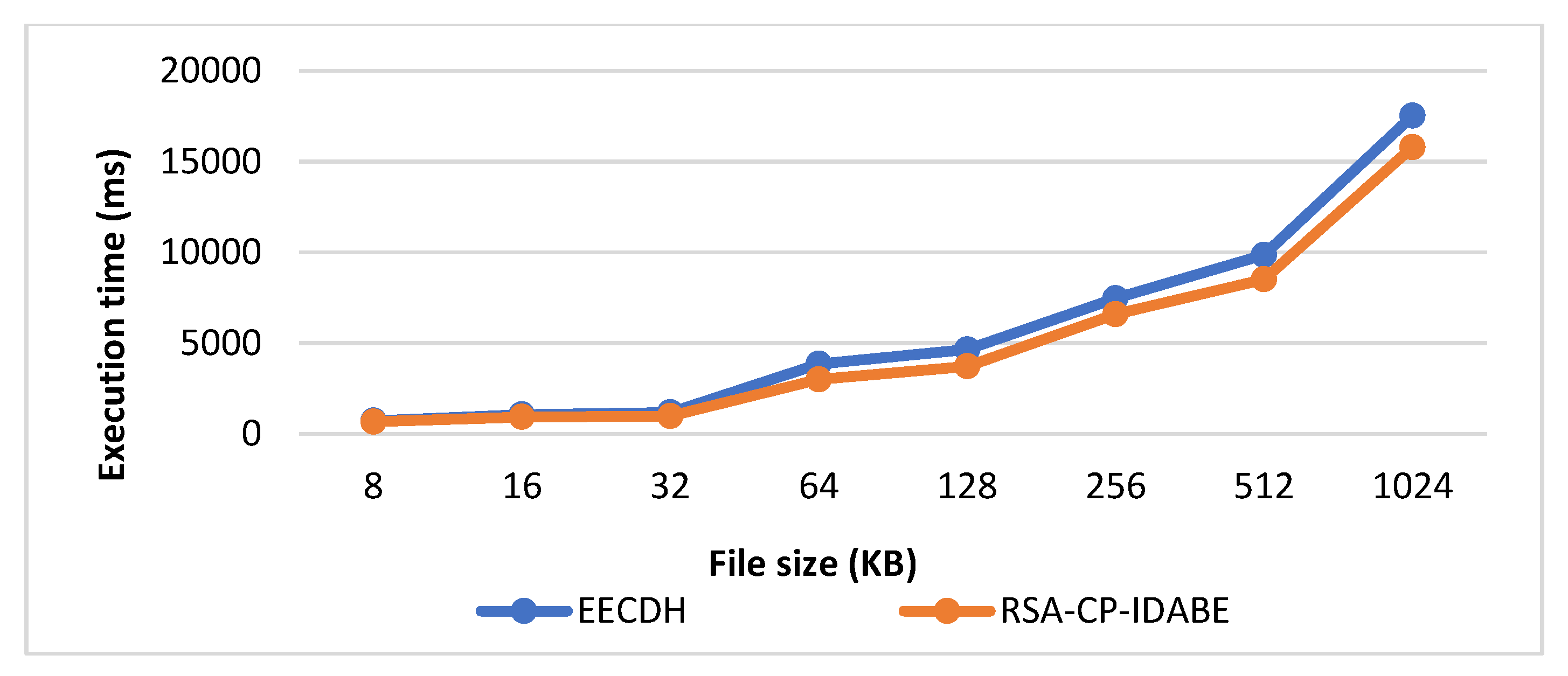
6.3. Execution Time
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Shajina, A.R.; Varalakshmi, P. A novel dual authentication protocol (DAP) for multi-owners in cloud computing. Clust. Comput. 2017, 20, 507–523. [Google Scholar] [CrossRef]
- Zhu, Y.; Hu, H.; Ahn, G.-J.; Yu, M. Cooperative provable data possession for integrity verification in multi-cloud storage. IEE Trans. Parallel Distrib. Syst. 2012, 23, 2231–2242. [Google Scholar] [CrossRef]
- Doelitzscher, F.; Sulistio, A.; Reich, C.; Kuijs, H.; Wolf, D. Private cloud for collaboration and e-Learning services: From IaaS to SaaS. Computing 2011, 91, 23–42. [Google Scholar] [CrossRef]
- Information Resources Management Association. Standards and Standardization: Concepts, Methodologies, Tools and Applications; IGI Global: Hershey, PA, USA, 2015. [Google Scholar]
- Bernsmed, K.; Jaatun, M.G.; Meland, P.H.; Undheim, A. Thunder in the Clouds: Security challenges and solutions for federated Clouds. In Proceedings of the 4th IEEE International Conference on Cloud Computing Technology and Science Proceedings, Taipei, Taiwan, 3–6 December 2012. [Google Scholar]
- Rimal, B.P.; Choi, E.; Lumb, I. A Taxonomy and Survey of Cloud Computing Systems. In Proceedings of the Fifth International Joint Conference on INC, IMS and IDC, Seoul, Korea, 25–27 August 2009. [Google Scholar]
- Ahmat, K. Emerging Cloud Computing Security Threats. arXiv 2015, arXiv:1512.01701. [Google Scholar]
- Liu, X.; Zhang, Y.; Wang, B.; Yan, J. Mona: Secure Multi-Owner Data Sharing for Dynamic Groups in the Cloud. IEEE Trans. Parallel Distrib. Syst. 2012, 24, 1182–1191. [Google Scholar] [CrossRef]
- Chowdary, P.R.; Challa, Y.; Jitendra, M.S.N.V. Identification of MITM Attack by Utilizing Artificial Intelligence Mechanism in Cloud Environments. J. Physics Conf. Ser. 2019, 1228, 012044. [Google Scholar] [CrossRef]
- Amara, N.; Zhiqui, H.; Ali, A. Cloud Computing Security Threats and Attacks with their Mitigation Techniques. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017; pp. 244–251. [Google Scholar]
- Chase, M. Multi-Authority Attribute Based Encryption. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2007; pp. 515–534. [Google Scholar]
- Anand, S.; Perumal, V. EECDH to prevent MITM attack in cloud computing. Digit. Commun. Netw. 2019, 5, 276–287. [Google Scholar] [CrossRef]
- Huang, Q.; Yang, Y.; Yue, W.; He, Y. Secure Data Group Sharing and Conditional Dissemination with Multi-Owner in Cloud Computing. IEEE Trans. Cloud Comput. 2019, 1. [Google Scholar] [CrossRef]
- Miao, Y.; Liu, X.; Choo, K.-K.R.; Deng, R.H.; Li, J.; Li, H.; Ma, J. Privacy-Preserving Attribute-Based Keyword Search in Shared Multi-owner Setting. IEEE Trans. Dependable Secur. Comput. 2019, 1. [Google Scholar] [CrossRef]
- Sangeetha, D.; Vaidehi, V. A secure cloud based Personal Health Record framework for a multi owner environment. Ann. Telecommun. 2016, 72, 95–104. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Liu, X.; Jiang, Q.; Zhang, J.; Shen, L.; Liu, Z. VCKSM: Verifiable conjunctive keyword search over mobile e-health cloud in shared multi-owner settings. Pervasive Mob. Comput. 2017, 40, 205–219. [Google Scholar] [CrossRef]
- Rong, H.; Wang, H.; Liu, J.; Hao, J.; Xian, M. Privacy-Preserving-Means Clustering under Multi owner Setting in Distributed Cloud Environments. Secur. Commun. Netw. 2017, 99, 1–19. [Google Scholar] [CrossRef]
- Aruna, K.B.; LallithaShri, A.; Aravindh; Jayasurya; Jayakumar. Protection for Multi Owner Data Sharing Scheme. Bonfring Int. J. Adv. Image Process. 2017, 7, 1–5. [Google Scholar] [CrossRef]
- Guo, Z.; Zhang, H.; Sun, C.; Wen, Q.; Li, W. Secure multi-keyword ranked search over encrypted cloud data for multiple data owners. J. Syst. Softw. 2018, 137, 380–395. [Google Scholar] [CrossRef]
- Peng, T.; Lin, Y.; Yao, X.; Zhang, W. An Efficient Ranked Multi-Keyword Search for Multiple Data Owners Over Encrypted Cloud Data. IEEE Access 2018, 6, 21924–21933. [Google Scholar] [CrossRef]
- Li, T.; Liu, Z.; Jia, C.; Fu, Z.; Li, J. Key-aggregate searchable encryption under multi-owner setting for group data sharing in the cloud. Int. J. Web Grid Serv. 2018, 14, 21–43. [Google Scholar] [CrossRef]
- Chandel, S.; Yang, G.; Chakravarty, S. AES–CP–IDABE: A Privacy Protection Framework against a DoS Attack in the Cloud Environment with the Access Control Mechanism. Information 2020, 11, 372. [Google Scholar] [CrossRef]
- Kalpana, P.; Singaraju, S. Data security in cloud computing using RSA algorithm. IJRCCT 2012, 1, 2278–5841. [Google Scholar]
- Padmaja, N.; Koduru, P. Providing data security in cloud computing using public key cryptography. Int. J. Eng. Sci. Res. 2013, 4, 1059–1063. [Google Scholar]
- Xue, S.; Ren, C. Security Protection of System Sharing Data with Improved CP-ABE Encryption Algorithm under Cloud Computing Environment. Autom. Control Comput. Sci. 2019, 53, 342–350. [Google Scholar]



| S.no | Notation | Explanation |
|---|---|---|
| 1 | DO | Digital signature of the owner |
| 2 | DU | Digital signature of the user |
| 3 | VMO | Verified message for the owner |
| 4 | VMU | Verified message for the user |
| 5 | IDi | Identity of the owner |
| 6 | IDj | Identity of the user |
| 7 | AO | Attribute of the owner |
| 8 | AU | Attribute of the user |
| 9 | PUK | Public key for CP-IDABE |
| 10 | MAK | Master key for CP-IDABE |
| 11 | PUKR | Public key for RSA |
| 12 | MAKR | Master key for RSA |
| 13 | OSK | Owner’s secret key |
| 14 | USK | User’s secret key |
| 15 | Et | Encryption text after CP-IDABE |
| 16 | A | Attribute policy set |
| 17 | Et’ | Encrypted text after RSA |
| 18 | M | Message for CP-IDABE |
| 19 | M’ | Message for RSA |
| 20 | KR | The secret key for RSA |
| File Size (KB) | EECDH [12] | RSA-CP-IDABE |
|---|---|---|
| 8 | 51 | 40 |
| 16 | 52 | 44 |
| 32 | 55 | 52 |
| 64 | 66 | 62 |
| 128 | 78 | 74 |
| 256 | 110 | 86 |
| 512 | 122 | 100 |
| 1024 | 136 | 124 |
| File Size (KB) | EECDH [12] | RSA-CP-IDABE |
|---|---|---|
| 8 | 54 | 45 |
| 16 | 59 | 48 |
| 32 | 62 | 56 |
| 64 | 67 | 61 |
| 128 | 70 | 65 |
| 256 | 73 | 68 |
| 512 | 78 | 71 |
| 1024 | 80 | 71 |
| File Size (KB) | EECDH [12] | RSA-CP-IDABE |
|---|---|---|
| 8 | 725 | 675 |
| 16 | 1065 | 930 |
| 32 | 1185 | 985 |
| 64 | 3857 | 3000 |
| 128 | 4652 | 3724 |
| 256 | 7474 | 6592 |
| 512 | 9863 | 8520 |
| 1024 | 17,523 | 15,792 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chandel, S.; Yang, G.; Chakravarty, S. RSA-CP-IDABE: A Secure Framework for Multi-User and Multi-Owner Cloud Environment. Information 2020, 11, 382. https://doi.org/10.3390/info11080382
Chandel S, Yang G, Chakravarty S. RSA-CP-IDABE: A Secure Framework for Multi-User and Multi-Owner Cloud Environment. Information. 2020; 11(8):382. https://doi.org/10.3390/info11080382
Chicago/Turabian StyleChandel, Sonali, Geng Yang, and Sumit Chakravarty. 2020. "RSA-CP-IDABE: A Secure Framework for Multi-User and Multi-Owner Cloud Environment" Information 11, no. 8: 382. https://doi.org/10.3390/info11080382
APA StyleChandel, S., Yang, G., & Chakravarty, S. (2020). RSA-CP-IDABE: A Secure Framework for Multi-User and Multi-Owner Cloud Environment. Information, 11(8), 382. https://doi.org/10.3390/info11080382






