A Geographic Information System (GIS)-Based Investigation of Spatiotemporal Characteristics of Pirate Attacks in the Maritime Industry
Abstract
:1. Introduction
2. Literature Review
2.1. Research on Piracy
2.2. Applications of GIS
3. Research Methods and Data
3.1. Data Source
3.2. Research Methods
3.2.1. Kernel Density Analysis
3.2.2. Hot Spot Analysis
3.2.3. Spatiotemporal Hot Spot Analysis
4. Result Analysis
4.1. Spatial Distribution of Pirate Attacks
4.2. Hot Spot Analysis of Pirate Attacks
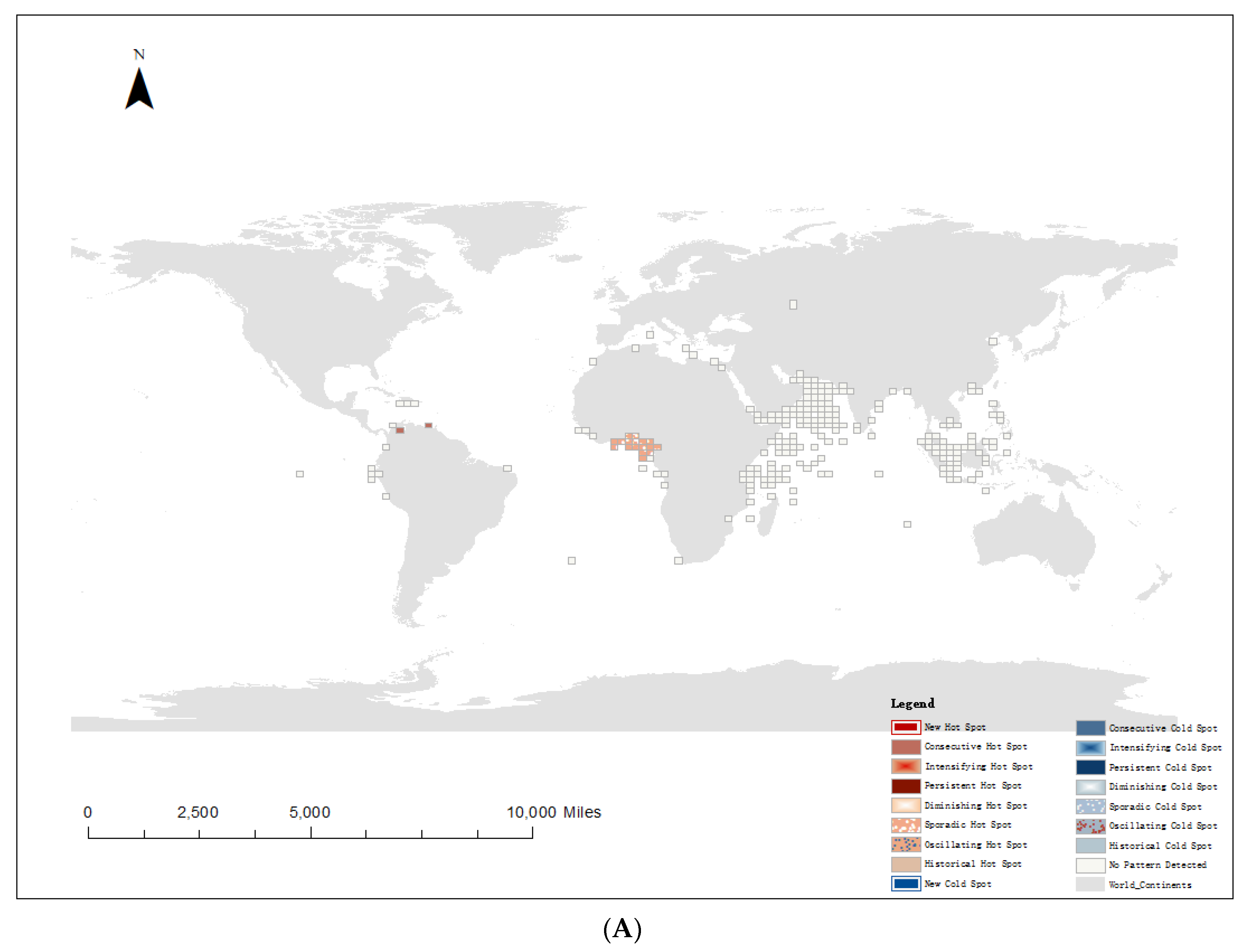
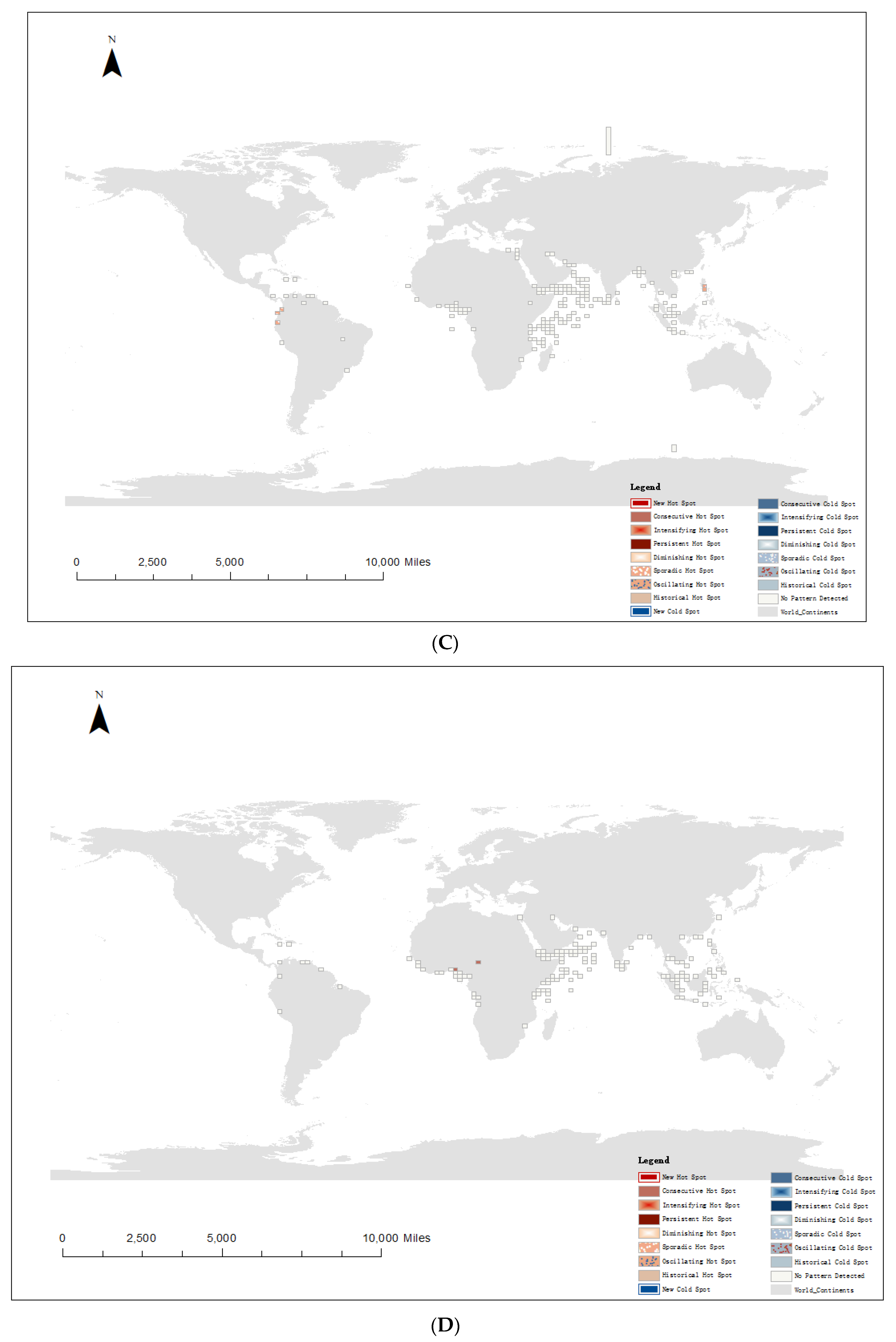
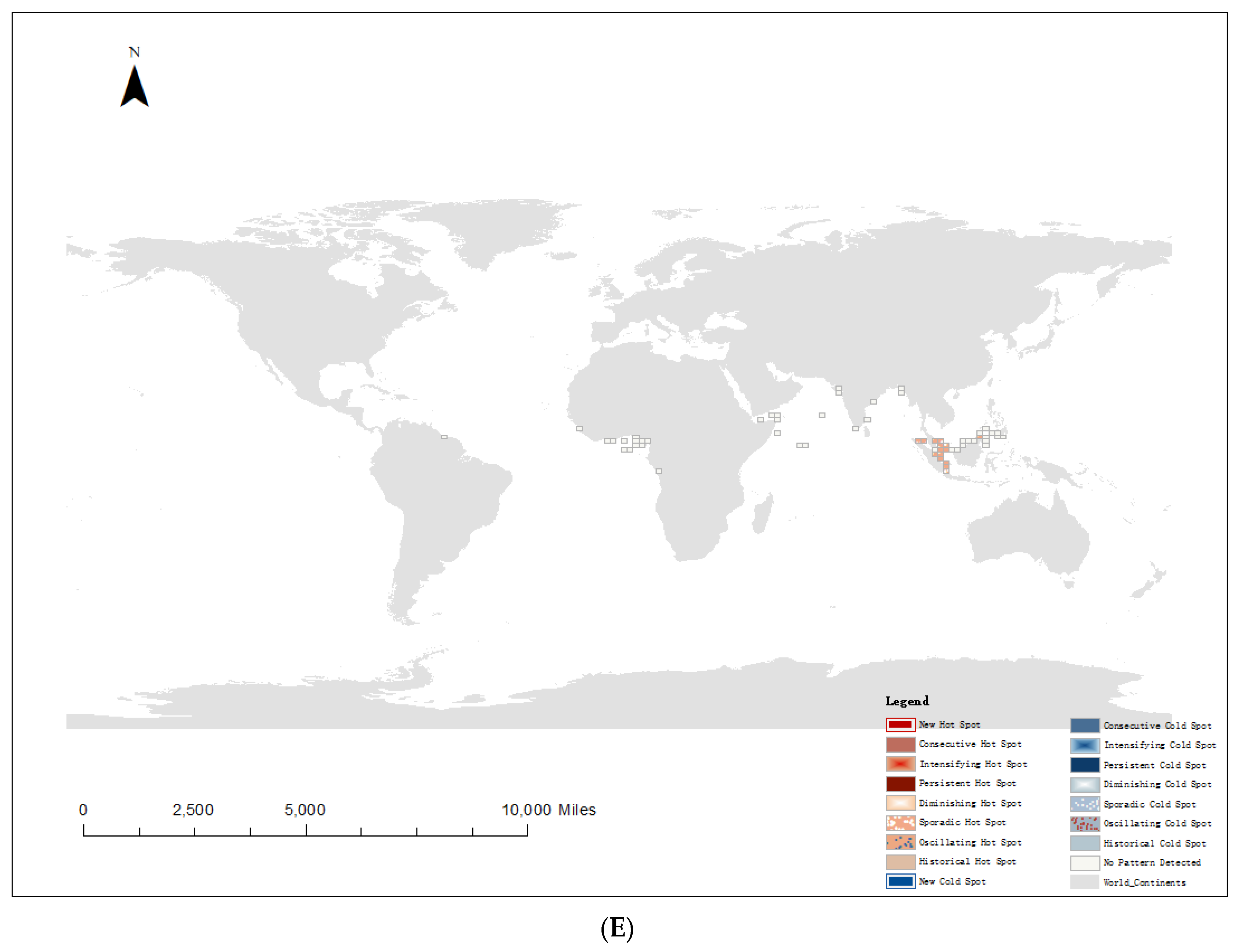
4.3. Spatiotemporal Hot Spot Analysis of Pirate Attacks
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ahmad, M. Maritime piracy operations: Some legal issues. J. Int. Marit. Saf. Environ. Aff. Shipp. 2020, 4, 62–69. [Google Scholar] [CrossRef]
- Hastings, J.V. The Return of Sophisticated Maritime Piracy to Southeast Asia. Pac. Aff. 2020, 93, 5–29. [Google Scholar] [CrossRef]
- Elmi, Z.; Singh, P.; Meriga, V.K.; Goniewicz, K.; Borowska-Stefańska, M.; Wiśniewski, S.; Dulebenets, M.A. Uncertainties in Liner Shipping and Ship Schedule Recovery: A State-of-the-Art Review. J. Mar. Sci. Eng. 2022, 10, 563. [Google Scholar] [CrossRef]
- Lau, Y.-y.; Ducruet, C.; Ng, A.K.Y.; Fu, X. Across the waves: A bibliometric analysis of container shipping research since the 1960s. Marit. Policy Manag. 2017, 44, 667–684. [Google Scholar] [CrossRef]
- Wang, L.; Zhu, Y.; Ducruet, C.; Bunel, M.; Lau, Y.-Y. From hierarchy to networking: The evolution of the “twenty-first-century Maritime Silk Road” container shipping system. Transp. Rev. 2018, 38, 416–435. [Google Scholar] [CrossRef]
- Bueger, C. Learning from piracy: Future challenges of maritime security governance. Glob. Aff. 2015, 1, 33–42. [Google Scholar] [CrossRef]
- Gong, X.; Jiang, H.; Yang, D. Maritime piracy risk assessment and policy implications: A two-step approach. Mar. Policy 2023, 150, 105547. [Google Scholar] [CrossRef]
- UNCTAD. United Nations Conference on Trade and Development, 2014, Part I: An Overview of Trends, Costs and Tradetrelated Implications. 2014. Available online: https://unctad.org/system/files/official-document/dtltlb2013d1_en.pdf (accessed on 1 October 2023).
- Jin, M.; Shi, W.; Lin, K.C.; Li, K.X. Marine piracy prediction and prevention: Policy implications. Mar. Policy 2019, 108, 103528. [Google Scholar] [CrossRef]
- Jiang, M.; Lu, J. The analysis of maritime piracy occurred in Southeast Asia by using Bayesian network. Transp. Res. Part E Logist. Transp. Rev. 2020, 139, 101965. [Google Scholar] [CrossRef]
- Liu, K.; Yang, L.; Li, M. Application of Cloud Model and Bayesian Network to Piracy Risk Assessment. Math. Probl. Eng. 2021. 2021, 2021, 6610339. [Google Scholar] [CrossRef]
- Nwokedi, T.C.; Anyanwu, J.; Eko-Rapheaels, M.; Obasi, C.; Akpufu, I.D.; Ogola, D.B. Probability Theory Analysis of Maritime Piracy and the Implications for Maritime Security Governance. J. ETA Marit. Sci. 2022, 10, 133–143. [Google Scholar] [CrossRef]
- Marchione, E.; Johnson, S.D. Spatial, Temporal and Spatio-Temporal Patterns of Maritime Piracy. J. Res. Crime Delinq. 2013, 50, 504–524. [Google Scholar] [CrossRef] [PubMed]
- Denton, G.L.; Harris, J.R. Maritime Piracy, Military Capacity, and Institutions in the Gulf of Guinea. Terror. Political Violence 2022, 34, 1–27. [Google Scholar] [CrossRef]
- Phayal, A.; Gold, A.; Prins, B. Interstate hostility and maritime crime: Evidence from South East Asia. Mar. Policy 2022, 143, 105134. [Google Scholar] [CrossRef]
- Fan, H.; Lu, J.; Chang, Z. A risk-based game theory model of navy and pirate behaviors. Ocean. Coast. Manag. 2022, 225, 106200. [Google Scholar] [CrossRef]
- Sandkamp, A.; Stamer, V.; Yang, S. Where has the rum gone? The impact of maritime piracy on trade and transport. Rev. World Econ. 2022, 158, 751–778. [Google Scholar] [CrossRef]
- Divine Caesar, L.; Cahoon, S.; Fei, J.; Sallah, C.A. Exploring the antecedents of high mobility among ship officers: Empirical evidence from Australia. Marit. Policy Manag. 2021, 48, 109–128. [Google Scholar] [CrossRef]
- Rosnani, R.; Heryadi, D.; Yani, Y.M.; Sinaga, O. ASEAN Maritime Security Cooperation. TransNav. Int. J. Mar. Navig. Saf. Sea Transp. 2022, 16, 413–417. [Google Scholar]
- Dong, B.; Morrison, C.N.; Branas, C.C.; Richmond, T.S.; Wiebe, D.J. As Violence Unfolds: A Space-Time Study of Situational Triggers of Violent Victimization among Urban Youth. J. Quant. Criminol. 2020, 36, 119–152. [Google Scholar] [CrossRef]
- Martins Filho, T.R.; Melo, S.N. School performance and violence: Intra-urban evaluation of an Amazonian metropolis. Cities 2023, 132, 104074. [Google Scholar] [CrossRef]
- Rosa, A.G.F.; Mota, C.M.D.M.; Figueiredo, C.J.J.D. A spatial multi-criteria decision analysis framework to reveal vulnerabilities of areas to incidences of street robberies. Appl. Geogr. 2023, 151, 102840. [Google Scholar] [CrossRef]
- Silva, C.; Melo, S.; Santos, A.; Junior, P.A.; Sato, S.; Santiago, K.; Sá, L. Spatial Modeling for Homicide Rates Estimation in Pernambuco State-Brazil. ISPRS Int. J. Geo-Inf. 2020, 9, 740. [Google Scholar] [CrossRef]
- Stassen, R.; Ceccato, V. Environmental and Wildlife Crime in Sweden from 2000 to 2017. J. Contemp. Crim. Justice 2020, 36, 403–427. [Google Scholar] [CrossRef]
- Sukhija, K.; Singh, S.N.; Kumar, M.; Mehrotra, D. Spatial and temporal trends reveal: Hotspot identification of crimes using machine learning approach. Int. J. Comput. Sci. Eng. 2022, 25, 174–185. [Google Scholar] [CrossRef]
- Li, G.; Wang, H.; Tan, R.; Fu, Y. Spatiotemporal characteristics and formation mechanism of child trafficking in China based on “successful cases”. Geogr. Res. 2017, 36, 2505–2520. [Google Scholar]
- ArcGIS Pro. 2023. Available online: https://pro.arcgis.com/zh-cn/pro-app/latest/tool-reference/spatial-analyst/an-overview-of-the-density-tools.htm (accessed on 1 October 2023).
- Kloog, I.; Haim, A.; Portnov, B.A. Using kernel density function as an urban analysis tool: Investigating the association between nightlight exposure and the incidence of breast cancer in Haifa, Israel. Comput. Environ. Urban Syst. 2009, 33, 55–63. [Google Scholar] [CrossRef]
- Alam, M.S.; Tabassum, N.J. Spatial pattern identification and crash severity analysis of road traffic crash hot spots in Ohio. Heliyon 2023, 9, e16303. [Google Scholar] [CrossRef]
- Fu, X.; Ng, A.K.Y.; Lau, Y.-Y. The impacts of maritime piracy on global economic development: The case of Somalia. Marit. Policy Manag. 2010, 37, 677–697. [Google Scholar] [CrossRef]
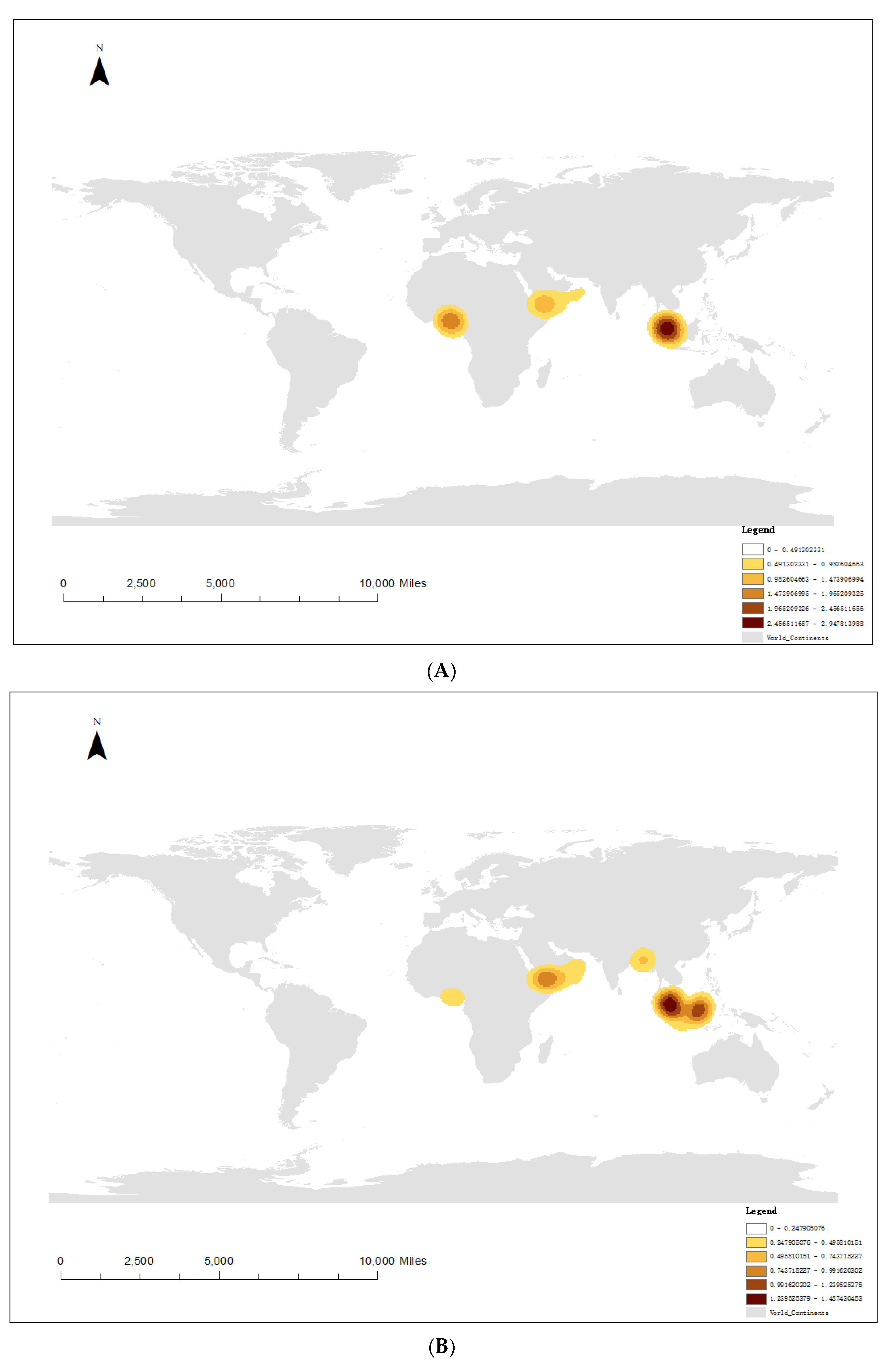

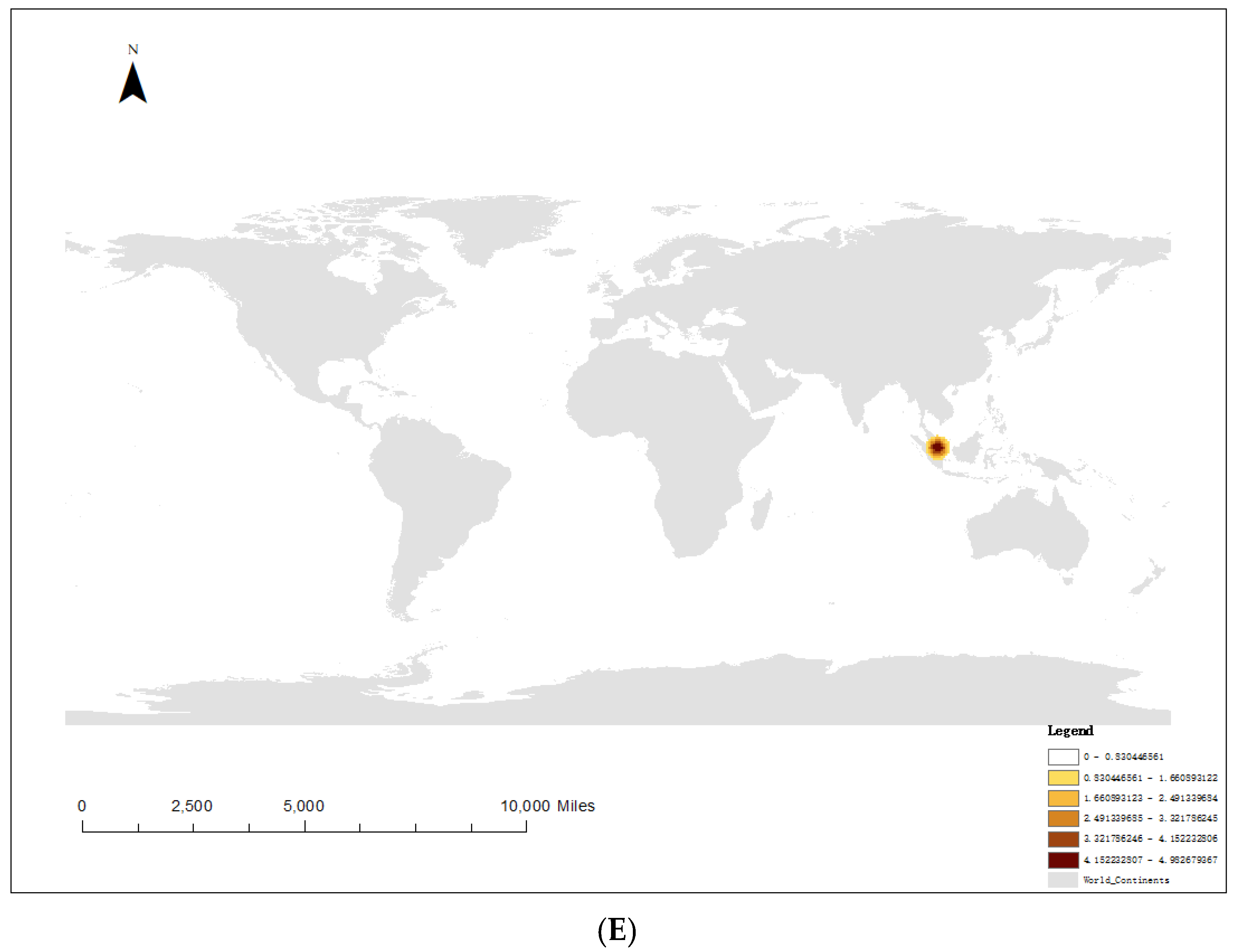
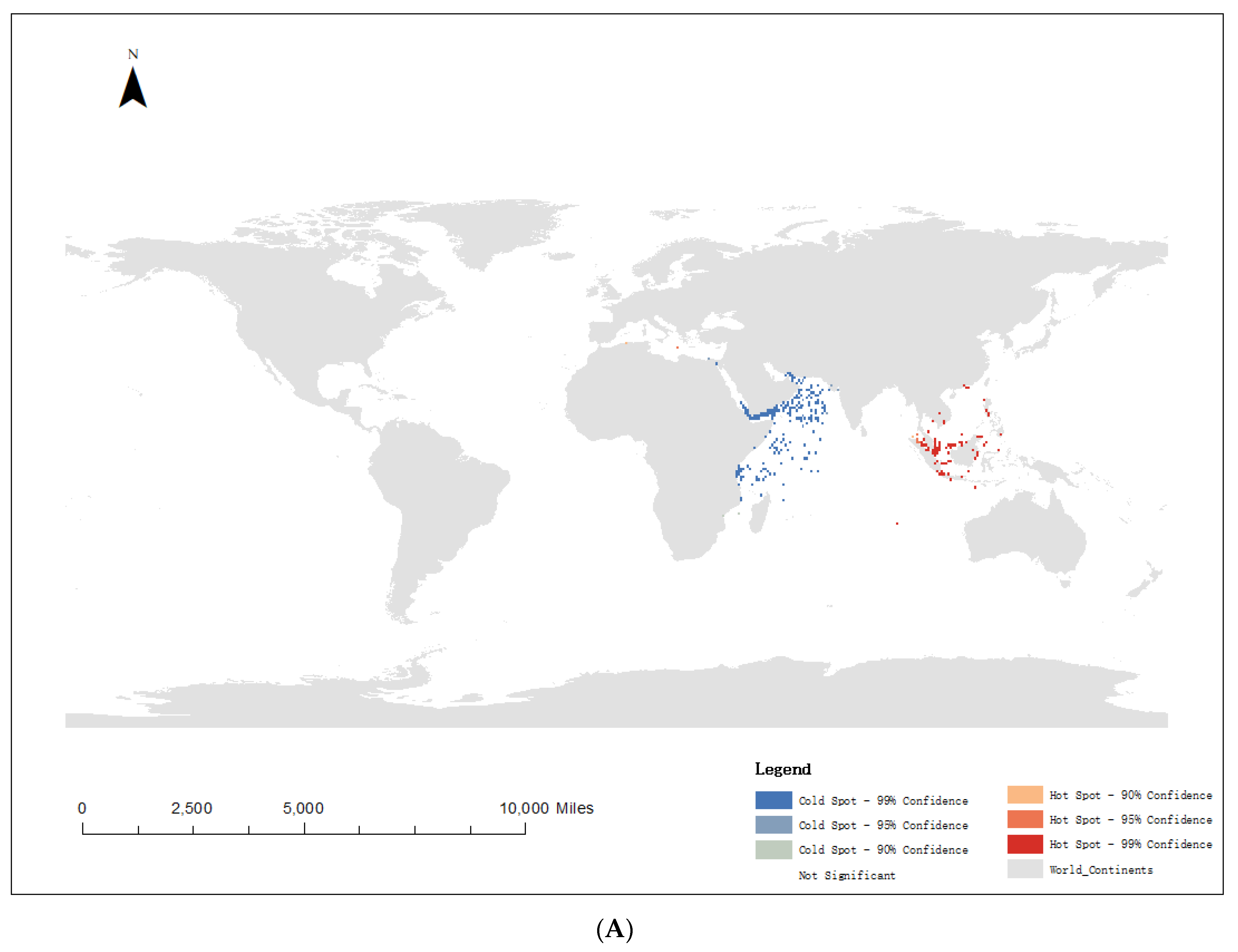



| Ship Type | Number of Pirate Attacks |
|---|---|
| Tanker | 1411 |
| Bulk carrier | 863 |
| Container vessel | 516 |
| General cargo vessel | 328 |
| Tug | 217 |
| Z-Score (Standard Deviation) | p-Value (Probability) | Confidence Degree |
|---|---|---|
| <−1.65 or >+1.65 | <0.10 | 90% |
| <−1.96 or >+1.96 | <0.05 | 95% |
| <−2.58 or >+2.58 | <0.01 | 99% |
| Pattern Name | Definition |
|---|---|
| No pattern detected | It does not belong to any of the cold or hot spot patterns explained below. |
| New cold spots (or hot spots) | This position is a statistically remarkable cold (or hot) spot for the last time step and has absolutely not been a cold (or hot) spot of statistical significance before. |
| Continuous cold spots (or hot spots) | This position has a sole continuous operation of statistically significant cold (or hot) bins in the last time step interval. It is most certaintly not a statistically remarkable cold (or hot) spot until the last hot spot runs, and at most 90% of every bin is a statistically remarkable cold (or hot) spot. |
| Strengthening cold spots (or hot spots) | This position has been a statistically remarkable cold (or hot) spot for 90% of the time step intervals, pertaining to the last. Moreover, the clustering intensity of the larger (or smaller) number of every time step rises in general, and the rise is statistically notable. |
| Persistent cold spots (or hot spots) | This position is already a statistically remarkable cold (or hot) spot at 90%-time step intervals, and there is no obvious direction indicating that the clustering intensity increases or decreases over time. |
| Gradually decreasing cold spots (or hot spots) | This position has been a statistically remarkable cold (or hot) spot for 90% of the time step intervals, containing the last time step. Additionally, the intensity of a smaller number of clusters in every time step decreases generally, and the reduction is statistically notable. |
| Scattered cold spots (or hot spots) | This position is a period cold spot (or hot spot). Up to 90% of the time step intervals are already statistically remarkable cold (or hot) spots, and no time step intervals are statistically significant hot (or cold) spots. |
| Oscillating cold spots (or hot spots) | A statistically remarkable cold spot (or hot spot) at the last time step interval has a record of being a statistically remarkable hot spot (or cold spot) in the previous time step. At up to 90% of the time-step intervals, it is already a statistically remarkable cold (or hot) spot. |
| Historical hot and cold spots | Recnetly, almost the position is not a cold (or hot) spot, but it is already a cold (or hot) spot with statistical remarkable in at least 90% of the intervals. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Q.; Zhang, H.; Lau, Y.-y.; Liu, K.; Ng, A.K.Y.; Chen, W.; Liao, Q.; Dulebenets, M.A. A Geographic Information System (GIS)-Based Investigation of Spatiotemporal Characteristics of Pirate Attacks in the Maritime Industry. J. Mar. Sci. Eng. 2023, 11, 2295. https://doi.org/10.3390/jmse11122295
Chen Q, Zhang H, Lau Y-y, Liu K, Ng AKY, Chen W, Liao Q, Dulebenets MA. A Geographic Information System (GIS)-Based Investigation of Spatiotemporal Characteristics of Pirate Attacks in the Maritime Industry. Journal of Marine Science and Engineering. 2023; 11(12):2295. https://doi.org/10.3390/jmse11122295
Chicago/Turabian StyleChen, Qiong, Hongyu Zhang, Yui-yip Lau, Kaiyuan Liu, Adolf K. Y. Ng, Weijie Chen, Qingmei Liao, and Maxim A. Dulebenets. 2023. "A Geographic Information System (GIS)-Based Investigation of Spatiotemporal Characteristics of Pirate Attacks in the Maritime Industry" Journal of Marine Science and Engineering 11, no. 12: 2295. https://doi.org/10.3390/jmse11122295
APA StyleChen, Q., Zhang, H., Lau, Y.-y., Liu, K., Ng, A. K. Y., Chen, W., Liao, Q., & Dulebenets, M. A. (2023). A Geographic Information System (GIS)-Based Investigation of Spatiotemporal Characteristics of Pirate Attacks in the Maritime Industry. Journal of Marine Science and Engineering, 11(12), 2295. https://doi.org/10.3390/jmse11122295








