In this work, we implemented the proposed control algorithm and compared schemes using MATLAB-based discrete-time event simulation toolboxes: WLAN toolbox, Communication toolbox, DSP System toolbox, and Signal Processing toolbox [
16]. We assumed a low-power mobile terminal based WLAN adhoc networks. The nodes used the IEEE 802.11 radio and MAC model. Each source sent data packets at a constant rate of 4 packets/s. Each packet size was 512 bytes. This simulation modeled a network of uniformly deployed mobile hosts within a given area. We executed each simulation using 15 sessions with randomly selected sources and destinations for 1000 s. The simulation parameters are summarized in
Table 1.
In this simulation, the parameters related to the wireless channel and mobility were used according to the standard specification documents of the wireless communication and networking system. However, the parameters related to the proposed control algorithm did not have a standard model: hub mobility threshold (), relative mobility speed threshold (), relative mobility angle threshold (), DCT, probability condition (), maximum redundancy (), maximal path length (m), and delay proportional coefficient (w). In fact, these may be set differently according to a service to be actually applied. In this work, we did not assume any specific application services. Instead, we set the parameters heuristically to fully reflect the characteristics of the proposed algorithm. In this section, we compare the following schemes.
These schemes were evaluated in the same environment to ensure a fair comparison. In fact, the methods in [
17,
18] are well-known controls, and we implemented important functions: route request and establishment, route failure management, cluster-header selection, and cluster-header switching.
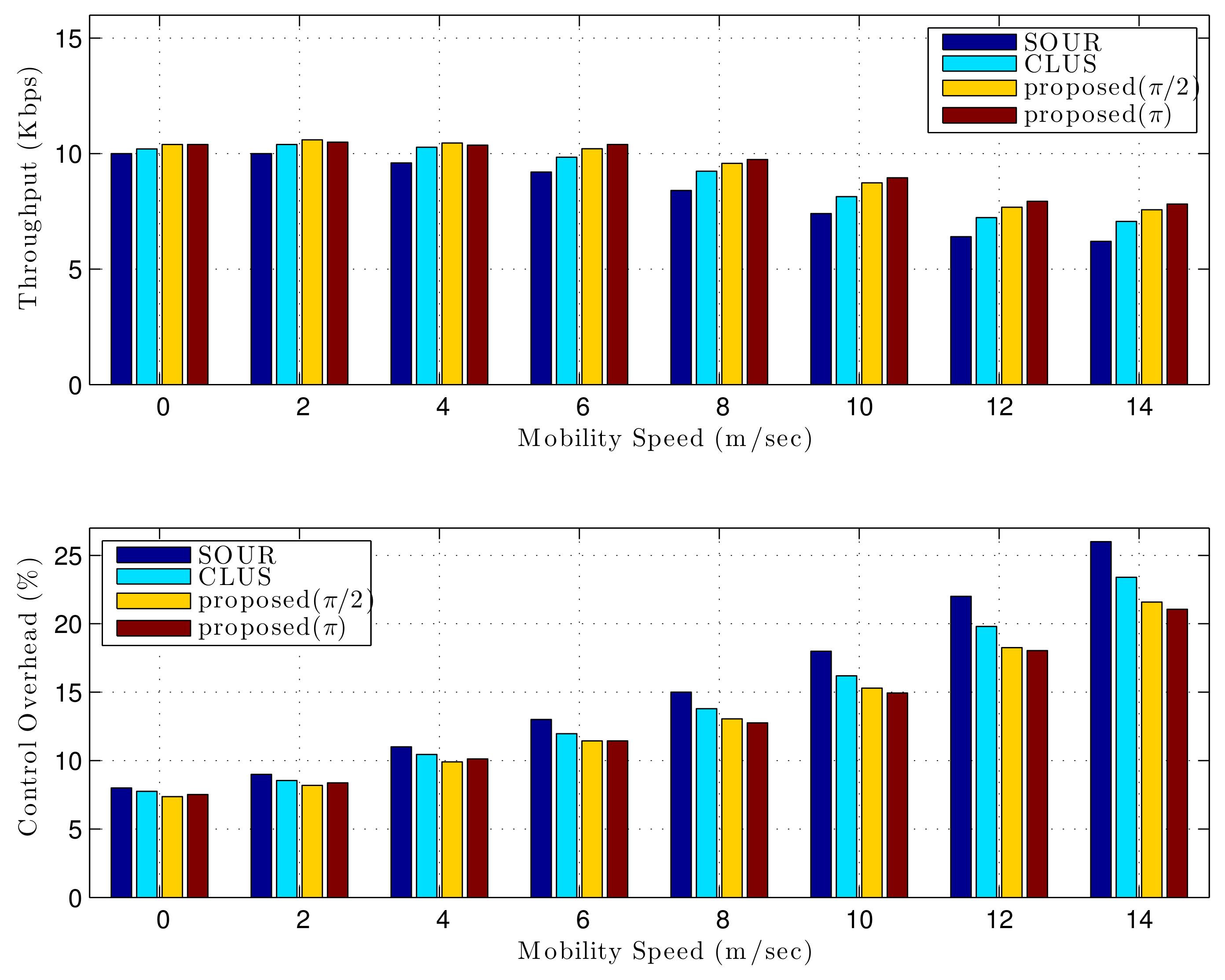
Figure 6 shows the performance when the network size was 1 km × 1 km.
Figure 6 compares the throughput, showing how many data packets could be sent successfully from the source to the destination. The proposed control exploits redundant paths as backup links or relayed cooperative links. Backup links increase the throughput by reducing the time for link recovery, and relayed cooperative links can increase throughput by sending the same information at the same time to enhance the signal-to-noise ratio. In contrast, in SOUR and CLUS, information is sent along a single path based on a noncooperative mode. Comparing SOUR and CLUS, the proposed control provided
and
enhanced throughput.
Figure 6 also compares the control packet overhead to successfully deliver data traffic from the source to the destination. Control packet overhead is strongly related to transmission-path management tasks such as finding new routes and recovering from link failures. The proposed approach reduced the control packets using predetermined stable hub paths and redundant local paths, minimizing frequent route discovery processes. It also used simpler maintenance messages—i.e., HelloHub and ByeHub messages. In contrast, in SOUR, the intermediate node started the source routing whenever there was a link failure. Frequent route-retrieval processes that rely on network-wide flooding mechanisms increase control overhead. The CLUS had higher overhead because of its complex cluster and gateway selection mechanism and various cluster head and gateway messages. Comparing SOUR and CLUS, the proposed control gave
and
lower overhead. On the other hand, in a low mobility environment, the proposed (
) gave a higher performance than the proposed (
). However, as the movement speed increased, the proposed (
) gave a better performance than the proposed (
), because the number of synchronized nodes is more important than the synchronization strength in the slow movement, and the synchronization strength is more important than the number of synchronized nodes in the fast movement. The larger is
, the greater is the number of synchronized nodes, but the weaker is the synchronization.
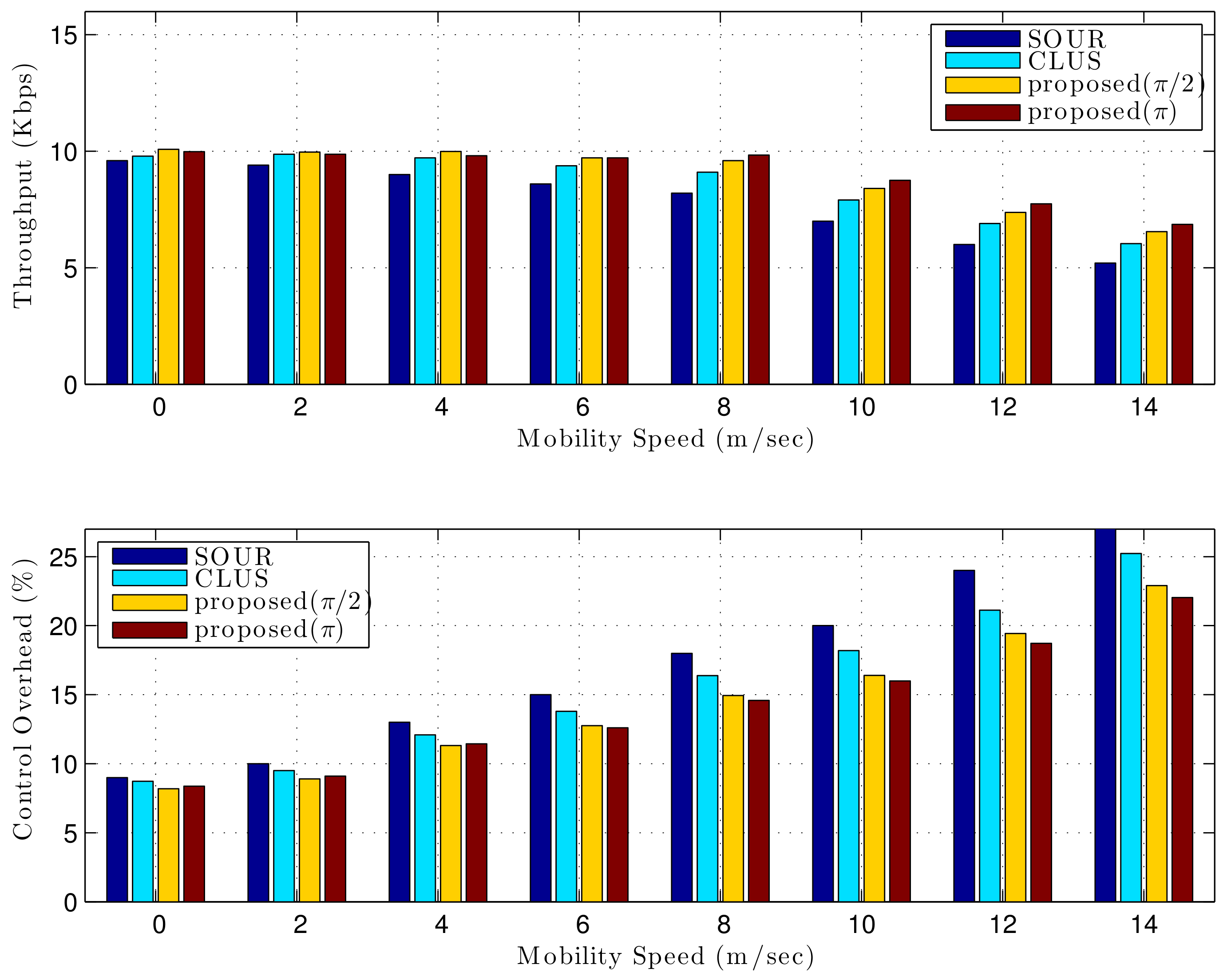
Figure 7 shows the performance when the network size was 2 km × 2 km. Comparing SOUR and CLUS, the proposed control gave
and
enhanced throughput, and
and
reduced overhead. From these simulations, we can see that the performance gain increased as the network size grew larger.