Featured Application
Since the proposed scheme can efficiently perform image encryption, it can be applied to real-time communication, such as telemedicine.
Abstract
This paper proposes a novel tweak-cube color image encryption scheme jointly manipulated by chaos and hyper-chaos. One-dimensional (1D) chaotic maps are effortless to operate, but the key space is relatively small. The hyperchaotic system has complex dynamics properties, which are capable of compensating for the defects of 1D chaotic maps. Thus, we first raise an improved 1D chaotic map with an increased key space. Then, we associate it with a four-dimensional (4D) hyperchaotic system to generate the key streams and further rotate and shift the rows and columns of each component of Red (R), Green (G), and Blue (B) for the color image. The permuting mode is to disturb the original position of the pixels by mimicking the way of twisting the Rubik’s cube. Moreover, the key stream updated by the plain images is also utilized for diffusion and scramble at the bit level. As a consequence, our cryptosystem enhances the security without at the expense of increasing time cost.
1. Introduction
Digital image is one of the most popular multimedia forms at present, and it is widely used in politics, economy, national defense, and education. Since images contain a lot of information, we must worry about data being leaked, falsified, and counterfeited. Image encryption is a very effective means of protecting images by processing them into an unrecognizable form. Moreover, image data has its own unique properties: large amount of data, high redundancy, and strong correlation between adjacent pixels [1]. These features make the traditional encryption algorithms such as data encryption standard (DES), advanced encryption standard (AES), and Rivest-Shamir-Adleman (RSA) unsatisfactory. Thus, plenty of new encryption methods have been developed based on various technologies, such as chaos [2,3,4,5], compressed sensing [6,7], wave transmission [8,9], hash function [10,11], deoxyribonucleic acid coding [12,13], genetics [14], gray code [15], elliptical curve [16], and so on. Among them, the chaos-based image encryption schemes have received extensive attention due to the advantages of chaotic systems. They are ergodic, dispersive, and highly sensitive to initial conditions.
In comparison with the methods of encrypting with multidimensional (MD) chaotic maps, the design of cryptosystems with one-dimensional (1D) chaotic maps has the superiorities of simple structures and commodious operations. The most frequently utilized is the Logistic map. At the outset, Pareek et al. employed two Logistic maps to control the tracks of image pixels for encryption [17]. Singh et al. proposed an encryption method that combines the Logistic map and Hartley transform to improve robustness [18]. Then, Wang et al. applied the Logistic map to encrypt the R, G, B components of a color image at the same time and make these components affect each other [19]. Nonetheless, the Logistic map still has several defects: the chaos region is small, the output sequences are uneven, and the dynamic characteristics are not complicated enough. As a consequence, some researchers have ameliorated the Logistic map to design algorithms. Wu et al. presented a cryptosystem with a two-dimensional (2D) Logistic map of complicated basin structures and attractors [20]. Zhou et al. combined the Logistic map with another two existing 1D maps to raise a novel chaotic system for image encryption [21], and Hua et al. also introduced a new 2D Sine Logistic modulation map (2D-SLMM) to change the image pixel positions [22]. Even recently, some scholars yet have been hammering at encryptions with Logistic map transformation. Pak et al. adopted a linear–nonlinear–linear theory to shuffle plain images [23]. Hanis et al. put forward a novel butterfly-like structure algorithm by using the improved Logistic map [24].
Considering that the above techniques have insufficient finite parameter space to resist brute force attacks and are not conducive to real-time communication, the contributions we have made are summarized as follows. (1) We propose a novel 1D chaotic map with larger key space and better chaotic properties. Simultaneously, it is combined with a 4D hyperchaotic map to control the generation of the key streams, which makes the randomness more superior. (2) We excogitate a color image encryption scheme that mimics the Rubik’s cube motion, which can be effectively used for real-time communication and authentication without compromising time cost and safety quality. Moreover, due to our scheme can scramble images by rotating and shifting them at the pixel-level and bit-level promptly, it is suitable as a secure transmission mode in telemedicine systems. The rest of this paper is organized as follows. Section 2 introduces the modified 1D chaotic map and hyperchaotic system. Section 3 presents our cryptosystem. Section 4 gives simulation results. Section 5 evaluates the security performance. And the final section draws a conclusion.
2. Preliminaries
2.1. The Logistic-Fraction Hybrid Chaotic Map
In this section, a new chaotic map called the Logistic-Fraction hybrid chaotic map (LFHCM) is recommended, which is defined as Equation (1). The LFHCM is derived from the classical Logistic map and Fraction map [25], and they can be mathematically represented as Formulas (2) and (3).
where control numbers , and . In addition, the output ranges of the three maps are also different, , , and . Then, the analytical tests can verify that the LFHCM has more complex dynamic characteristics.
2.1.1. Bifurcation Graph
The bifurcation graph can objectively reflect the region and state of the chaotic behavior of a map. Figure 1 exhibits the bifuration graphs of the LFHCM, Logistic map, and Fraction map. It can be found that the Logistic map shows chaotic characteristics only when . Although the Fraction map has more complex dynamic properties than the Logistic map, its chaotic interval length is also less than 1. The interval in which the LFHCM presents chaotic state is . It is obvious that the chaotic region of the new chaotic map is increased, which means that the key space is also improved. Besides, in contrast to the intervals of some 1D chaotic maps in Table 1, the LFHCM has the largest region.
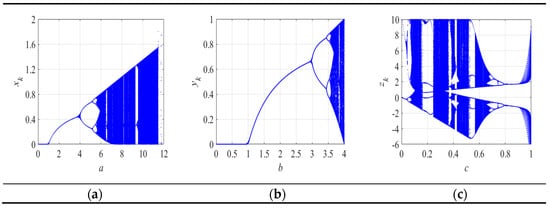
Figure 1.
The bifurcation graphs of the (a) Logistic-Fraction hybrid chaotic map (LFHCM); (b) Logistic map; (c) Fraction map.

Table 1.
Comparison of chaotic intervals between the LFHCM and other one-dimensional (1D) chaotic maps.
2.1.2. Lyapunov Exponent
The Lyapunov exponent is used to characterize the motion of a system. When it is calculated as a positive number, it indicates that a map has chaotic behavior. Not only that, the larger the Lyapunov exponent, the better the chaotic properties of the map. Besides, the definition of the Lyapunov exponent for a 1D chaotic map is as follows:
Since the Lyapunov exponent is independent of the initial value , we arbitrarily chose . Moreover, in order to observe the change between the adjacent iteration points as a whole, the number of iterations should be chosen as large as possible, so we set . Then, calculated the derivatives of the LFHCM, Logistic map, and Fraction map according to Equations (1)–(3), and substituted the results into Equation (4) to get the Lyapunov exponent plots exhibited in Figure 2. It can be seen that the LFHCM has larger Lyapunov exponents than the other two maps, which means that its orbit is rapidly separated in the direction of the positive Lyapunov exponent and it is sensitive to initial values.
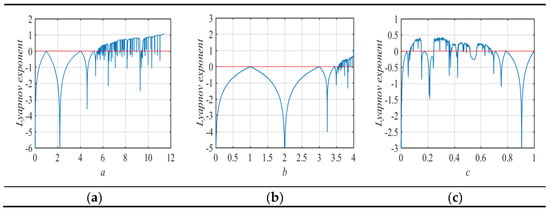
Figure 2.
The Lyapunov exponents of the (a) LFHCM; (b) Logistic map; (c) Fraction map.
2.1.3. Approximate Entropy
Approximate entropy (ApEn) is a nonlinear dynamic parameter used to quantify the regularity and unpredictability of time series fluctuations [27]. It can also measure the complexity of a chaotic map. Moreover, the larger the calculated ApEn value, the more complicated the sequence generated by the chaotic map is. We set the control parameters 11.44, 3.99, and 0.31 for the LFHCM, Logistic map, and Fraction map separately. Then, we calculated the ApEn of the three maps with different thresholds, as shown in Table 2. It can be seen that the proposed LFHCM has larger ApEn values, which proves that it can produce more complex sequences.

Table 2.
Approximate entropy (ApEn) values of 1D chaotic maps.
2.1.4. NIST Test
The NIST (National Institute of Standards and Technology) SP800-22 Revla test consists of 15 sub-items that are used to detect the randomness of the sequences [28]. The method of detection is by comparing the calculated of each sub-item to a prescribed significant level 0.01, and the generated values are all expected to greater than 0.01 to pass the test. We iterated Equation (1) with different initial values to generate 100 binary streams with 1,000,000 bits, then calculated their average values. The results are shown in Table 3. It is obvious that the calculated of each sub-item falls into , that is, the outputs generated by LFHCM can pass all the tests of NIST.

Table 3.
NIST SP800-22 Revla test results of binary streams generated by LFHCM.
2.2. Hyperchaotic System
Since the hyperchaotic system contains more than two positive Lyapunov exponents, its chaotic properties are better, and its trajectory is more unpredictable. When a hyperchaotic system is applied to image encryption, the cryptosystem has a larger key space. The 4D hyperchaotic system utilized in this paper [29] is defined as follows:
where , , , , , , and are control parameters of the system. Only when , , , , , , and , the system exhibits hyperchaotic behavior. Moreover, the phase trajectory of the system is displayed in Figure 3.
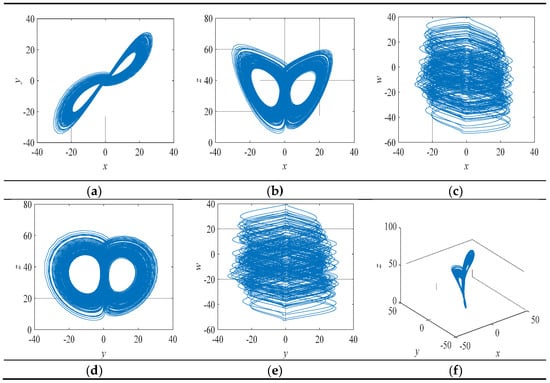
Figure 3.
The phase trajectories of the (a) x, y plane; (b) x, z plane; (c) x, w plane; (d) y, z plane; (e) y, w plane; (f) x, y, z space.
3. The Proposed Image Cryptosystem
3.1. Key Stream Generation
In this subsection, we introduce the key stream generation process of the encryption scheme in this paper. The specific steps are as follows:
Step 1: Decompose the plain image of size into three matrixes, , , and . Set initial values and for the LFHCM and 4D hyperchaotic system, respectively. Then apply the plain image to update the initial values according to Equation (6)
Step 2: Select two control parameters for the LFHCM, and iterate it and times with the initial values . Discard the first 500 elements to form two chaotic sequences, labeled and .
Step 3: Pre-iterate the 4D hyperchaotic system described in the former section 1000 times. Then, iterate another and times to generate two pseudo-random sequences, and , with initial values respectively. They can be defined as follows:
where denotes that the element returns the smallest integer in the infinite direction. Then, arbitrarily intercept and elements corresponding to the sequences and to produce sequences and .
Step 4: Perform the following operations for the four chaotic sequences, and constructed in Step 2 and Step 3:
where represents the function that make the element return the nearest integer towards minus infinity.
Step 5: Further convert these sequences according to Formulas (13) and (14).
The resulting four sequences are treated as key streams that can be expressed as , , and .
3.2. Encryption Scheme
Input: Color plain image of size Output: Color cipher image of the same size.
Step 1: Calculate the initial conditions based on the plain image , and set the control parameters for the LFHCM. After selecting the initial values for the 4D hyperchaotic system, the key streams , , and are generated by the preceding subsection.
Step 2: The color plain image is decomposed into three matrixes of , , and , then each row of the three matrixes is subjected to Equation (15).
When the computed values , the , , and matrixes are respectively cyclically shifted to the left by positions, where Then, when , the cyclic shifts are performed correspondingly to the right positions. As shown in Figure 4, similar to the principle of Rubik’s Cube, the pixels of the image can also be rotated and shifted to the left and right.
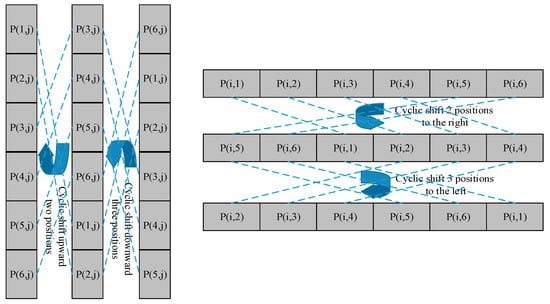
Figure 4.
Schematic diagram of cyclic shifting in all directions.
Step 3: For each column of , , and , the operations are as follows:
When the calculated values , the , , and matrixes are respectively cyclically shifted upward by positions, where . Then, when , the cyclic shifts are performed correspondingly downward to positions. The upward and downward cyclic shift diagram is also displayed in Figure 4, and three scrambled matrixes, and , are obtained.
Step 4: Execute bit-wise diffusion operation on each row of the matrixes , , and according to Equation (17).
Step 5: For the odd rows of the matrixes , , and , they are cyclically shifted to the left by positions, and the even rows are rotated to the right by the same positions. Meanwhile, for the odd columns of the matrixes , , and , they are respectively cycle shifted upward by positions, and the even columns are correspondingly shifted downward by the same positions. Then, three disordered matrixes, , , and , are produced.
Step 6: Finally, a bit-level scrambling is implemented by the following formula:
Merge the three components, , , and , to form the final encrypted image . The flowchart of our encryption scheme is displayed in Figure 5.
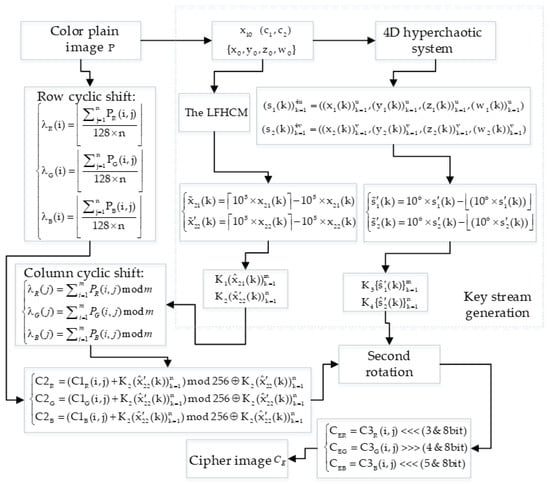
Figure 5.
Flowchart of the encryption scheme.
3.3. Decryption Scheme
The decryption procedure is the inverse process of the encryption scheme, and it can be described briefly as follows:
Step 1: Apply the same initial conditions as encryption to iterate Equations (1) and (9) to generate the key streams , , and .
Step 2: Execute bit shift to the left or right of the components , , and to get the matrixes , , and .
Step 3: Cyclic shift the rows and columns of the matrixes , , and according to the opposite direction of step 5 in the previous subsection, then the matrixes , , and are acquired.
Step 4: Perform bit-wise operations utilizing Formula (19).
Step 5: Implement second reverse circular shifts on the rows and columns of the three matrices, , and , according to Equations (15) and (16).
Step 6: Merge the three obtained matrixes to form the original image .
4. Experimental Results
As exhibited in Figure 6, three color plain images, “Couple”, “House” and “Tree”, were encrypted by python version 3.6 on a PC with an Intel Core i5, 3.4 GHz CPU, 8 GB memory. The noise-like phenomena appear in cipher images, which proves the feasibility of the scheme from the visual perspective
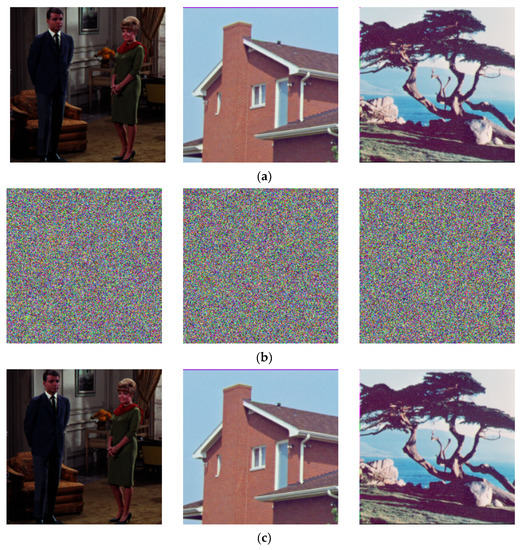
Figure 6.
Encryption results: (a) the original images; (b) the encrypted images; (c) the decrypted images.
The encryption results are based on the following conditions:
5. Performance Analysis
This section describes the performance analysis of our encryption scheme in terms of key space, key sensitivity, histogram analysis, correlation distribution, and information entropy evaluation, and so on.
5.1. Key Space
The key space is a collection of all legitimate keys. Only when it is large enough can it resist a variety of powerful attacks. Here the data range of the LFHCM is , and the approximate intervals about the initial values of the 4D hyperchaotic system are , , , and . In general, the precision of initial values and control numbers can reach . Thus, the size of the key space is able to achieve [24].
5.2. Key Sensitivity Analysis
The key sensitivity analysis is designed to observe the impact of small changes in the keys on cipher images. As for a chaotic map, the nuances of the initial conditions can produce two completely different sequences. Thus, we just changed initial value with , then we re-encrypted the original images in Figure 6a. The cipher images in Figure 7a were obtained. Figure 7b exhibits the pixel-by-pixel difference between Figure 6b and Figure 7a, and it can be discovered that a subtle change to the keys can result in a completely different encryption. Moreover, Table 4 lists the difference rates between two encrypted images with only one of the keys changed, and these data are greater than 99.5%. Therefore, we can conclude that our encryption scheme has strong key sensitivity.
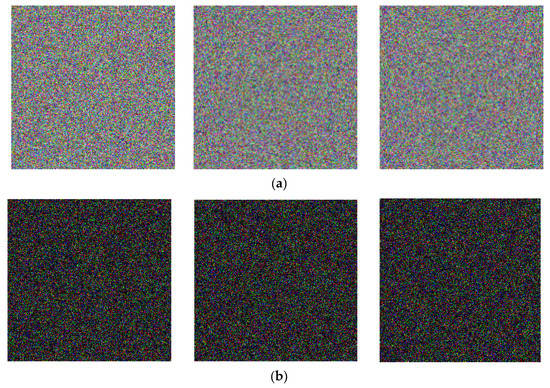
Figure 7.
(a) The cipher images with a small change to initial value x10; (b) the pixel-by-pixel differences between (a) and Figure 6b.

Table 4.
Difference between cipher images with modified keys.
5.3. Histogram Analysis
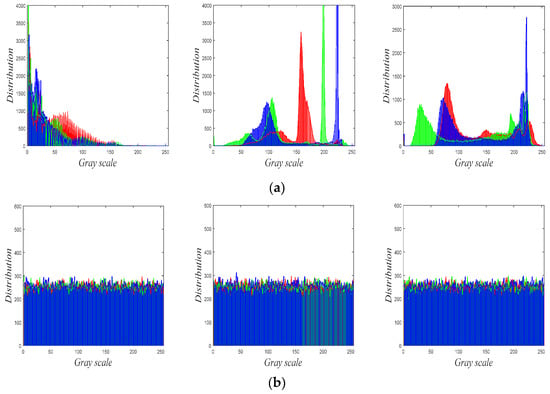
The histogram is an important statistical feature of the image. An outstanding cryptosystem has the capacity to evenly distribute the histogram of the cipher image. In this case, the attacker cannot extract statistical features of the plain image from its cipher. Figure 8 presents the histograms of the plain and cipher images in Figure 7, which demonstrates that encryption makes the histogram information safely obscured.
In order to further verify the encryption effect, we used the statistical magnitude to measure the pixel values distribution of the plain and cipher images, which can be defined as follows:
where denotes occurrence frequency of pixel value , and represents the theoretical frequency of pixel value . As displayed in Table 5, the chi-square test was performed on six images at a significant level of 0.05. Since the values are not only much smaller than the chi-square values of the plain images, but they are also lower than the critical value , they all pass the test. That is, our cryptosystem can effectively resist statistical attack.

Table 5.
Chi-square test of plain and cipher images.
5.4. Correlation Analysis
The correlation of two adjacent pixels can reflect the degree of diffusion about image pixels. Figure 9 and Figure 10 exhibit the correlation distribution of the three channels, R, G and B, in the horizontal, vertical, main-diagonal and back-diagonal directions of the plain Tree image and cipher Tree image, respectively. Furthermore, we randomly chose 3000 pairs of adjacent pixels from a few original images and corresponding encrypted images. Then, we analyzed the correlation coefficients in horizontal, vertical, and main-diagonal directions according to Equation (21).
where and indicate the mean value and standard deviation. The results are shown in Table 6 and Table 7. It can be discovered that the correlation coefficients of the plain images are close to 1, while the results of the cipher images are near to 0. Hence, the encryption effect is satisfactory.
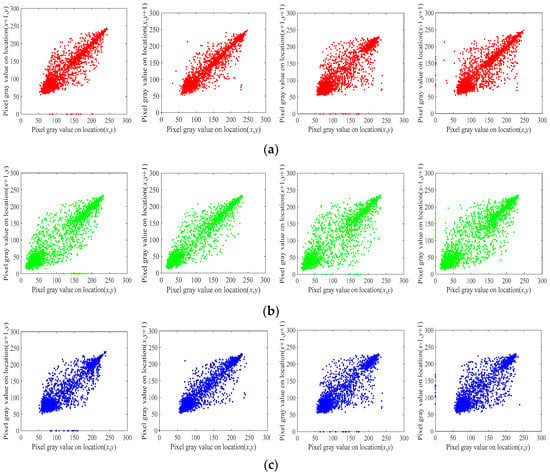
Figure 9.
Correlation coefficients of plain Tree image in each direction: (a) R channel; (b) G channel; (c) B channel.
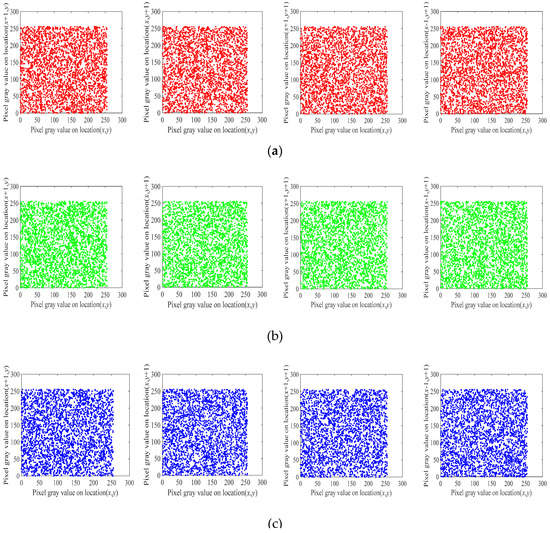
Figure 10.
Correlation coefficients of cipher Tree image in each direction: (a) R channel; (b) G channel; (c) B channel.

Table 6.
Correlation coefficients of plain images.

Table 7.
Correlation coefficients of cipher images.
5.5. Information Entropy Analysis
Information entropy is expressed as the probability of discrete random events, which is used to measure the randomness of a system. It can be defined as follows:
where denotes the probability that the gray value may appear. For a grayscale image with data field of , the maximum value of information entropy is 8. In other words, if the result is close to 8, the algorithm is proved to be quite safe. It can be seen from Table 8 that the entropy values of ciphers are very close to the ideal values, so the possibility of information leakage is quite small.

Table 8.
The results of information entropy.
5.6. Noise Attacks Analysis
When the encrypted image is transmitted through the physical channel, it may be damaged by attackers [38]. Therefore, the cryptosystem should have the ability to resist noise attacks. That is, the cipher image after being attacked can still recover the information conveyed by the original image. In the experiment, we added Gaussian noise, Salt and pepper noise, and Speckle noise to the three cipher images in Figure 6b. As displayed in Figure 11, the decrypted images can still be successfully identified after being assaulted.
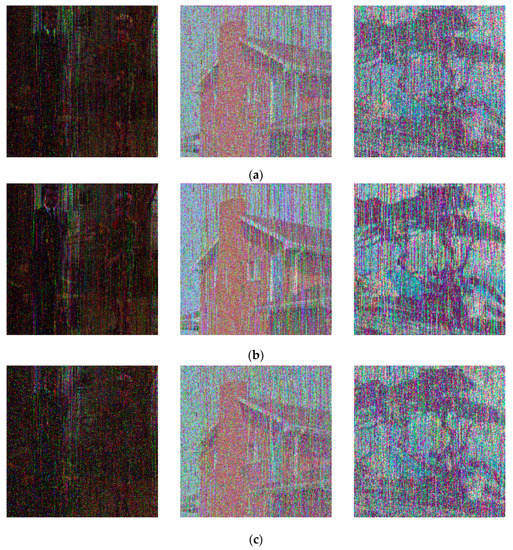
Figure 11.
Decrypted images with (a) Gaussian noise; (b) salt & pepper noise; (c) speckle noise.
5.7. Data Loss Attack
A preeminent cryptosystem should withstand the cost of data loss during transmission and storage [39]. Similar to the test of noise attack, we also verified by decrypting the cipher image after data loss. Figure 12a,c reveals the data loss experiment on the cipher Tree image of different positions and sizes, respectively. It can be found from the corresponding decrypted images in Figure 12b,d that the Tree image after data leakage can still be recognized.
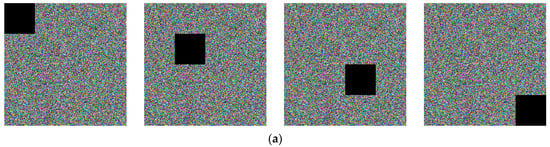

Figure 12.
(a) Cipher images with lost data at different locations; (b) decrypted images of (a); (c) cipher images with different sizes of data loss; (d) decrypted images of (c).
5.8. Differential Attack Analysis
The sensitivity to the plain image determines the ability of an algorithm to resist differential attacks. The measurement methods are the number of pixels change rate (NPCR) and unified average changing intensity (UACI) [40]. The formulas are as follows:
where and are two cipher images whose plain images have only one different pixel. is utilized to determine the distinction between two cipher images, which can be defined as:
In 2011, Wu et al. proposed more stringent standards of NPCR and UACI [41], which clearly demonstrates how high NPCR/UACI is, such that the encryption algorithm indeed has a high security level. The critical value of significance level is calculated by
where is the inverse cumulative density function (CDF) of the standard Normal distribution, and denotes the largest supported pixel value compatible with the ciphertext image format. Assuming that the calculated value is greater than then it can be proved to pass the test. The maximum and minimum of UACI can be computed according to Equation (27).
where , .
If the results of a scheme are between and it can be considered to pass the test. Table 9 reveals the theoretical values of NPCR and UACI at different significance levels for images of size .

Table 9.
The theoretical values of number of pixels change rate (NPCR) and unified average changing intensity (UACI).
In our experiment, we encrypted plain images with the initial keys. Then, we randomly chose one pixel in each original image and changed them slightly. The modified images were encrypted with the same keys. After reckoning the two types of ciphers, it can be found that all the NPCR values in Table 10 are greater than and draw near to the ideal value of 99.6094%. Simultaneously, the UACI results for each image in Table 11 are within the theoretical interval. Thus, the algorithm can effectively resist differential attacks.

Table 10.
The actual values of NPCR for different color images.

Table 11.
The actual values of UACI for different color images.
5.9. Time and Computational Complexity Analysis
Time and speed analysis is also a critical measurement feature for an encryption algorithm. Thus, the security of a scheme cannot be at the expense of increasing time consumption. The time costs of images with different sizes were measured separately, and the results are listed in Table 12. Obviously, the encryption time of our scheme is less than that of some recent encryption algorithms.

Table 12.
The encryption time and speed values for images with different sizes.
Ulteriorly, we will discuss the computational complexity of our scheme. At the outset, the generation process of the key streams made the computational complexity become . Afterwards, the rows and columns of the three components R, G, and B were simultaneously cyclically shifted twice so that the computational complexity changed to . Besides, the bit-level operations do not affect the complexity, hence the computational complexity of this paper is .
6. Conclusions
In this paper, we devise a novel 1D chaotic map LFHCM with increased parameter space. The simulation results exhibit that the LFHCM has better chaotic properties than congeneric chaotic maps. In addition, combining LFHCM with a 4D hyperchaotic system, we also excogitate a color image encryption scheme based on tweak-cube theory. On the one hand, the secondary key streams updated by the plain image guarantee that the image withstands known-plaintext attack and chosen-plaintext attack. On the other hand, fast disorganizing at the bit-level and pixel-level allows our solution to be applied in crucial scenarios for real-time communication, such as telemedicine, authentication, and so forth. Compared with some state-of-arts, our work has achieved excellent encryption effects.
Author Contributions
Conceptualization, L.-L.H. and S.-M.W.; methodology, L.-L.H.; software, S.-M.W.; validation, L.-L.H., S.-M.W. and J.-H.X.; formal analysis, J.-H.X.; investigation, S.-M.W.; resources, L.-L.H.; data curation, L.-L.H.; writing—original draft preparation, S.-M.W.; writing—review and editing, L.-L.H.; visualization, J.-H.X.; supervision, L.-L.H.; project administration, S.-M.W.; funding acquisition, L.-L.H.
Funding
This research was funded by National Natural Science Foundation of China (No. 61203004, 61306142) and Natural Science Foundation of Heilongjiang Province (Grant No. F201220).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wu, X.; Kan, H.; Kurths, J. A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl. Soft Comput. 2015, 37, 24–39. [Google Scholar] [CrossRef]
- Li, C.; Luo, G.; Ke, Q.; Li, C. An image encryption scheme based on chaotic tent map. Nonlinear Dyn. 2017, 87, 127–133. [Google Scholar] [CrossRef]
- Ye, G.; Chen, P.; Huang, X.; Mei, Q. An efficient pixel-level chaotic image encryption algorithm. Nonlinear Dyn. 2018, 94, 1–12. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V. Efficient image encryption method based on improved Lorenz chaotic system. Electron. Lett. 2018, 54, 562–564. [Google Scholar] [CrossRef]
- Wang, X.; Çavuşoğlu, Ü.; Kacar, S.; Akgul, A.; Pham, V.-T.; Jafari, S.; Alsaadi, E.F.; Nguyen, Q.X. S-Box Based Image Encryption Application Using a Chaotic System without Equilibrium. Appl. Sci. 2019, 9, 781. [Google Scholar] [CrossRef]
- Zhou, N.; Li, H.; Di, W.; Pan, S.; Zhou, Z. Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 2015, 343, 10–21. [Google Scholar] [CrossRef]
- Liu, X.; Mei, W.; Du, H. Optical image encryption based on compressive sensing and chaos in the fractional Fourier domain. J. Mod. Opt. 2014, 61, 1570–1577. [Google Scholar] [CrossRef]
- Ye, G. A block image encryption algorithm based on wave transmission and chaotic systems. Nonlinear Dyn. 2014, 75, 417–427. [Google Scholar] [CrossRef]
- Chai, X.L.; Zhu, C.J.; Yang, K.; Gao, Y.L. Block Image Encryption Scheme Based on Wave Transmission and Hyperchaotic Financial System. J. Chin. Comput. Syst. 2016, 37, 1329–1333. [Google Scholar]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn. 2016, 83, 1–14. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. Hash key-based image encryption using crossover operator and chaos. Multimed. Tools Appl. 2016, 75, 4753–4769. [Google Scholar] [CrossRef]
- Yong, Z. The image encryption algorithm based on chaos and DNA computing. Multimed. Tools Appl. 2018, 77, 21589–21615. [Google Scholar]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, H.L. A novel image encryption algorithm based on genetic recombination and hyper-chaotic systems. Nonlinear Dyn. 2016, 83, 333–346. [Google Scholar] [CrossRef]
- Chen, J.X.; Zhu, Z.L.; Chong, F.; Zhang, L.B.; Zhang, Y. An efficient image encryption scheme using lookup table-based confusion and diffusion. Nonlinear Dyn. 2015, 81, 1151–1166. [Google Scholar] [CrossRef]
- Kumar, M.; Iqbal, A.; Kumar, P. A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie-Hellman cryptography. Signal Process. 2016, 125, 187–202. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Singh, N.; Sinha, A. Optical image encryption using Hartley transform and logistic map. Opt. Commun. 2009, 282, 1104–1109. [Google Scholar] [CrossRef]
- Wang, X.; Lin, T.; Xue, Q. A novel colour image encryption algorithm based on chaos. Signal Process. 2012, 92, 1101–1108. [Google Scholar] [CrossRef]
- Yue, W.; Yang, G.; Jin, H.; Noonan, J.P. Image encryption using the two-dimensional logistic chaotic map. J. Electron. Imaging 2012, 21, 3014. [Google Scholar]
- Zhou, Y.; Long, B.; Chen, C.L.P. A new 1D chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M.; Chen, C.L.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Hanis, S.; Amutha, R. A fast double-keyed authenticated image encryption scheme using an improved chaotic map and a butterfly-like structure. Nonlinear Dyn. 2019, 95, 421–432. [Google Scholar] [CrossRef]
- Lu, J.A.; Wu, X.; Lü, J.; Kang, L. A new discrete chaotic system with rational fraction and its dynamical behaviors. Chaos Solitons Fractals 2004, 22, 311–319. [Google Scholar] [CrossRef]
- Zhu, S.; Wang, G.; Zhu, C. A Secure and Fast Image Encryption Scheme Based on Double Chaotic S-Boxes. Entropy 2019, 21, 790. [Google Scholar] [CrossRef]
- Pincus, S. Approximate entropy (ApEn) as a complexity measure. Chaos 1995, 5, 110–117. [Google Scholar] [CrossRef]
- He, J.; Cai, J. Design of a New Chaotic System Based on Van Der Pol Oscillator and Its Encryption Application. Mathematics 2019, 7, 743. [Google Scholar] [CrossRef]
- Guangzhou and China. A new hyperchaotic system and its adaptive tracking control. Acta Phys. Sin. 2012, 61, 273–335. [Google Scholar]
- Wang, X.Y.; Li, P.; Zhang, Y.Q.; Liu, L.Y.; Zhang, H.; Wang, X. A novel color image encryption scheme using DNA permutation based on the Lorenz system. Multimed. Tools Appl. 2018, 77, 6243–6265. [Google Scholar] [CrossRef]
- Sun, S. A novel hyperchaotic image encryption scheme based on DNA encoding, pixel-level scrambling and bit-level scrambling. IEEE Photonics J. 2018, 10. [Google Scholar] [CrossRef]
- Enayatifar, R.; Sadaei, H.J.; Abdullah, A.H.; Lee, M.; Isnin, I.F. A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt. Lasers Eng. 2015, 71, 33–41. [Google Scholar] [CrossRef]
- Xie, Y.; Yu, J.; Guo, S.; Ding, Q.; Wang, E. Image Encryption Scheme with Compressed Sensing Based on New Three-Dimensional Chaotic System. Entropy 2019, 21, 819. [Google Scholar] [CrossRef]
- Cicek, I.; Pusane, A.E.; Dundar, G. A novel design method for discrete time chaos based true random number generators. Integr. VLSI J. 2014, 47, 38–47. [Google Scholar] [CrossRef]
- Liu, H.; Kadir, A.; Sun, X. Chaos-based fast color image encryption scheme with true random number keys from environmental noise. IET Image Process. 2017, 11, 324–332. [Google Scholar] [CrossRef]
- Parvaz, R.; Zarebnia, M. A combination chaotic system and application in color image encryption. Opt. Laser Technol. 2018, 101, 30–41. [Google Scholar] [CrossRef]
- Niyat, A.Y.; Moattar, M.H.; Torshiz, M.N. Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt. Lasers Eng. 2017, 90, 225–237. [Google Scholar] [CrossRef]
- Liu, H.; Kadir, A. Asymmetric color image encryption scheme using 2D discrete-time map. Signal Process. 2015, 113, 104–112. [Google Scholar] [CrossRef]
- Wang, L.; Song, H.; Ping, L. A novel hybrid color image encryption algorithm using two complex chaotic systems. Opt. Lasers Eng. 2016, 77, 118–125. [Google Scholar] [CrossRef]
- Wu, X.; Zhu, B.; Hu, Y.; Ran, Y. A Novel Color Image Encryption Scheme Using Rectangular Transform-Enhanced Chaotic Tent Maps. IEEE Access 2017, 5, 6429–6436. [Google Scholar]
- Wu, Y. NPCR and UACI Randomness Tests for Image Encryption. Cyber J. J. Sel. Areas Telecommun. 2011, 1, 31–38. [Google Scholar]
- Wang, X.; Zhao, Y.; Zhang, H.; Guo, K. A novel color image encryption scheme using alternate chaotic mapping structure. Opt. Lasers Eng. 2016, 82, 79–86. [Google Scholar] [CrossRef]
- Suri, S.; Vijay, R. A synchronous intertwining logistic map-DNA approach for color image encryption. J. Ambient Intell. Humaniz. Comput. 2019, 10, 2277–2290. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).