1. Introduction
In recent years, Internet of Things (IoT) technology has flourished, which has led to the development of many peripheral and emerging markets. The IoT is a physical object which contains embedded wireless devices and sensors, and sends its data to the processing platform through internet communication technologies. Therefore, IoT has a wide range of applications in various fields. For resource-constrained devices in IoT, Message Queuing Telemetry Transport (MQTT) is a lightweight publish/subscribe communication protocol, and is quite prevalent and easy to use. For example, the MQTT protocol has been applied in a structural monitoring scenario [
1] and a long-term energy monitoring system [
2]. In the IoT application, each information processing platform can be connected to another one to form a huge network. Obviously, most IoT data is opened and stored on the Internet or in IoT devices, so many new security and privacy issues have been derived [
3]. Taking smart meters, for example, the hacker can know when you will be at home and what devices you have used. Therefore, for these resource-constrained devices, the absence of security or weak security mechanisms will cause an unpredictable crisis, and the use of these devices will then be limited in some aspects. However, considering the limited computational abilities of resource-constrained devices, they cannot use too powerful or complicated cryptographic algorithms to ensure the security of data. To solve this problem, we have studied and discussed the security mechanism of MQTT protocol commonly used in IoT [
4,
5,
6,
7]. To solve the data security of resource-constrained devices, cryptography is generally used to protect the data, so that clearly visible information can be transformed into seemingly messy ciphertext to protect them from malicious people. It is usually not a complex process to encrypt data when using the MQTT protocol. In this way, the data will be vulnerable to eavesdroppers. To encrypt the data, the available encryption schemes on the Internet fall into two categories: symmetric encryption and asymmetric encryption. Both of these have to repeatedly encrypt the data by the key and decrypt the data by the same or another key data-by-data. The traditional encryption technique is not suitable for publish/subscribe communication protocol such as MQTT. To solve this problem, Sahai and Waters proposed a new cryptographic technique called attribute-based encryption (ABE) [
8]. A data owner (or publisher) can specify access to the data as a Boolean formula related to a set of attributes and the data will be encrypted in relation to this. Then, the data user (or subscriber) can only decrypt the ciphertext if they possess the attributes satisfying the Boolean formula ascribed to the ciphertext. ABE has two types: Ciphertext-Policy ABE (CP-ABE) [
9] and Key-Policy ABE (KP-ABE) [
10]. However, the disadvantage of these is their complex computation, which is not suitable for resource-constrained devices.
Therefore, in this direction, some approaches have been proposed [
6,
11,
12]. The common way to reduce computation is to use an elliptic curve in a bilinear map [
6,
11]. A pre-computation method was proposed to store a set of pairs and to simply put and exchange the memory for the encryption time [
12]. Since we aimed to design an encryption algorithm suitable for resource-constrained devices, the computing ability and memory requirements had to be reduced enough. A widespread consensus is that the computation overhead of bilinear pairing is excessive in the practical application of ABE, especially for devices with limited computational resources. Therefore, the authors [
13] proposed a scheme called Pairing-Free CP-ABE (PF-CP-ABE) [
13], replacing bilinear pairing with simple scalar multiplication on elliptic curves, in order to reduce the overall computational overhead. It substantially works like CP-ABE, and the elliptic curve is difficult to compute, so it is still safe enough. However, since data keeps transmitting between resource-constrained devices, and the authority (MQTT broker) needs to identify users and send certification results to them each time, the schemes mentioned above cannot provide effective data communication.
In the last two decades, chaos systems have been widely applied in secure communication. Chaos systems have characteristics such as a butterfly effect sensitive dependence on the initial conditions, so that eavesdroppers cannot easily deal with them. Motivated by the aforesaid discussion, in this paper, we propose a new Chaos Synchronization Attribution-Based Encryption Scheme (CS-ABE) utilizing the random property of the chaos signal and integrating chaos synchronization with PF-CP-ABE. We take the secret number of PF-CP-ABE generated by a chaos random number. Before chaos synchronization, the system we propose, combining PF-CP-ABE with chaos synchronization, works like PF-CP-ABE. After chaos synchronization, the state variables of both chaos systems are synchronized, and the system can just obtain the secret number from itself. Therefore, the performance and security of PF-CP-ABE can be improved.
The remainder of this paper is structured as follows. The algorithms we apply are described in
Section 2, such as elliptic curve cryptography (ECC), ABE, and chaos synchronization. Our proposed scheme is proposed in
Section 3. The performance and security are discussed in
Section 4. Finally, the conclusion is given in
Section 5.
3. Chaos Synchronization Attribution-Based Encryption Scheme
In this section, we give the detailed algorithm of our brand-new system, which combines PF-CP-ABE with chaos synchronization. The synchronization characteristic in PF-CP-ABE is utilized to give another approach to get the secret number. Although PF-CP-ABE greatly reduces the complexity and computation of CP-ABE, if there are a lot of data and they keep being sent, the users should also employ the algorithm every time when receiving the data. This is quite ineffective, so we applied another algorithm to improve it. Due to it combining the concept of ABE with synchronization characteristics of the chaos system, we have given it the name Chaos Synchronization Attribute-Based Encryption (CS-ABE), which can be divided into four parts, as shown below. Set up.
An elliptic curve over a finite field of order with generator is agreed upon. The point generates a cyclic subgroup in . In addition, a hash function is defined to map every user’s to , and every user’s is unique, which means .
The trust authority, which can be a broker, randomly selects an integer as the authority’s main private key and then computes to be the main public key. At the same time, the authority randomly selects an integer for every attribute and computes to be its public key.
The data owner and user hold a chaos master and slave system, respectively, and select satisfying ; satisfying ; and initial conditions such as , , , , , and .
The master data owner hold system is as below:
The slave data user hold system is as below:
(1) Key generation
A private key of each attribute (topic name)
is generated for each user
, and the authority computes the formulas below to get their corresponding private keys and record them.
(2) Encryption
The plain text is first mapped to a point
on the elliptic curve
. State variables of the chaos system are selected to generate an integer
called a secret number, and then compute
The encryption algorithm is associated with an access structure and does not need any polynomials. The data owner defines the access structure and transforms it to an
LSSS matrix, and then randomly selects a vector
with
as its first entry and lets
denote
, where
is row
of
. They also randomly select a vector
with 0 as its first entry and let
denote
. The ciphertext would be
(3) Decryption
The user transmits their
and
to the authority, and lets the authority verify its identity. If the authority confirms that the user is valid, it secretly sends back a result according to each
. The result is computed as below:
With the above result, the user can then compute
Then, an integer
is selected such that
and computes
as
and
.
The secret number is generated from the state variable of the chaos master system, and compared with the state variable of the chaos slave system, such as , , or . If the chaos system does not achieve synchronization, the ciphertext is processed by the above, and the synchronization controller still works. Then, if the chaos system does synchronize, the ciphertext will no longer require the above algorithm, and it can be done by itself, using the same state variable to generate .
Finally, the user can compute the formula below to get point
and map it back to the plain text on the same elliptic curve.
4. Implementation Results
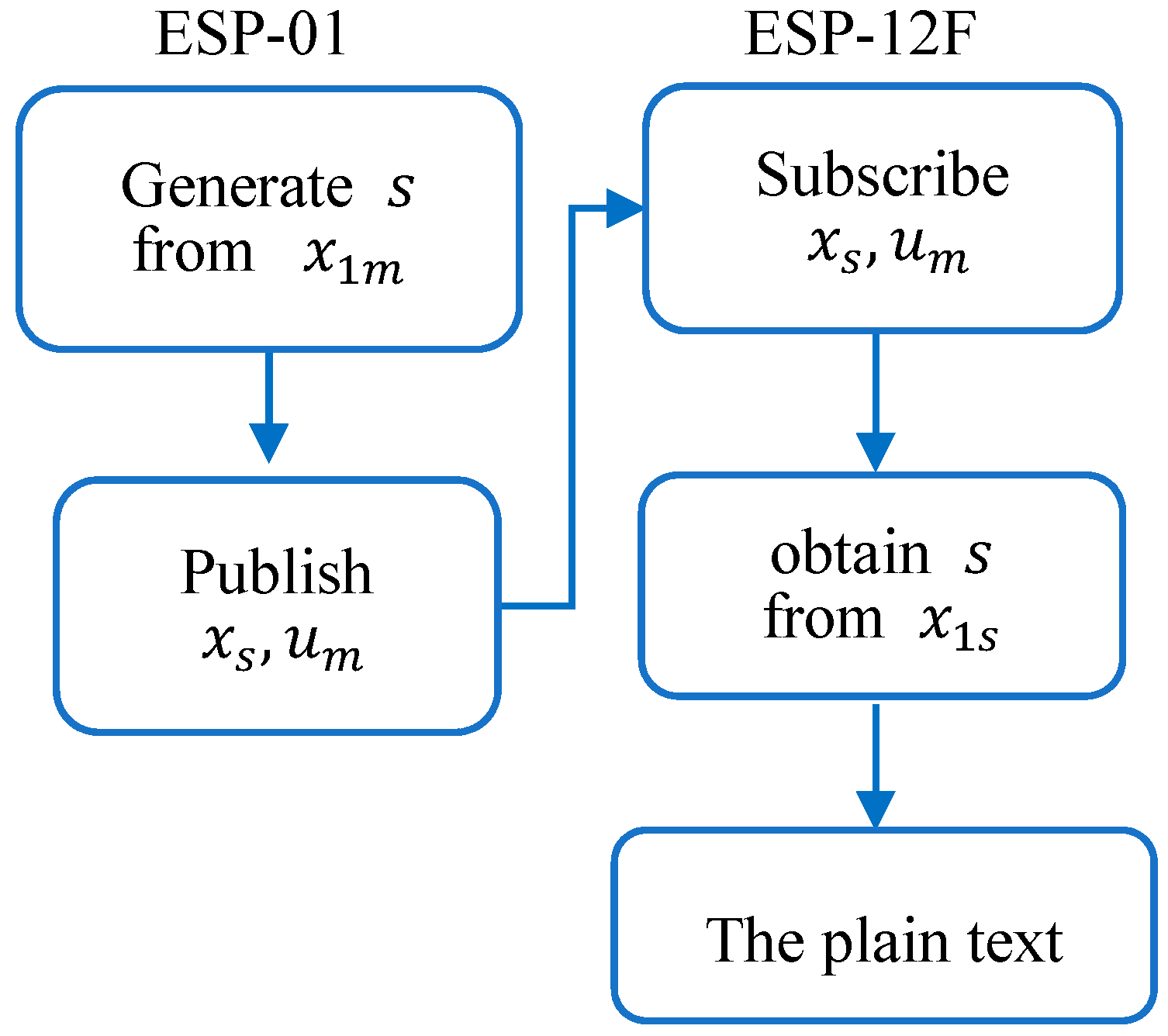
There are four elements in MQTT message transmission, which are the publisher, subscriber, broker, and topic. To simulate resource-constrained devices, we used ESP8266 (ESP-01 and ESP-12F) to act as a publisher and subscriber, respectively, as shown in
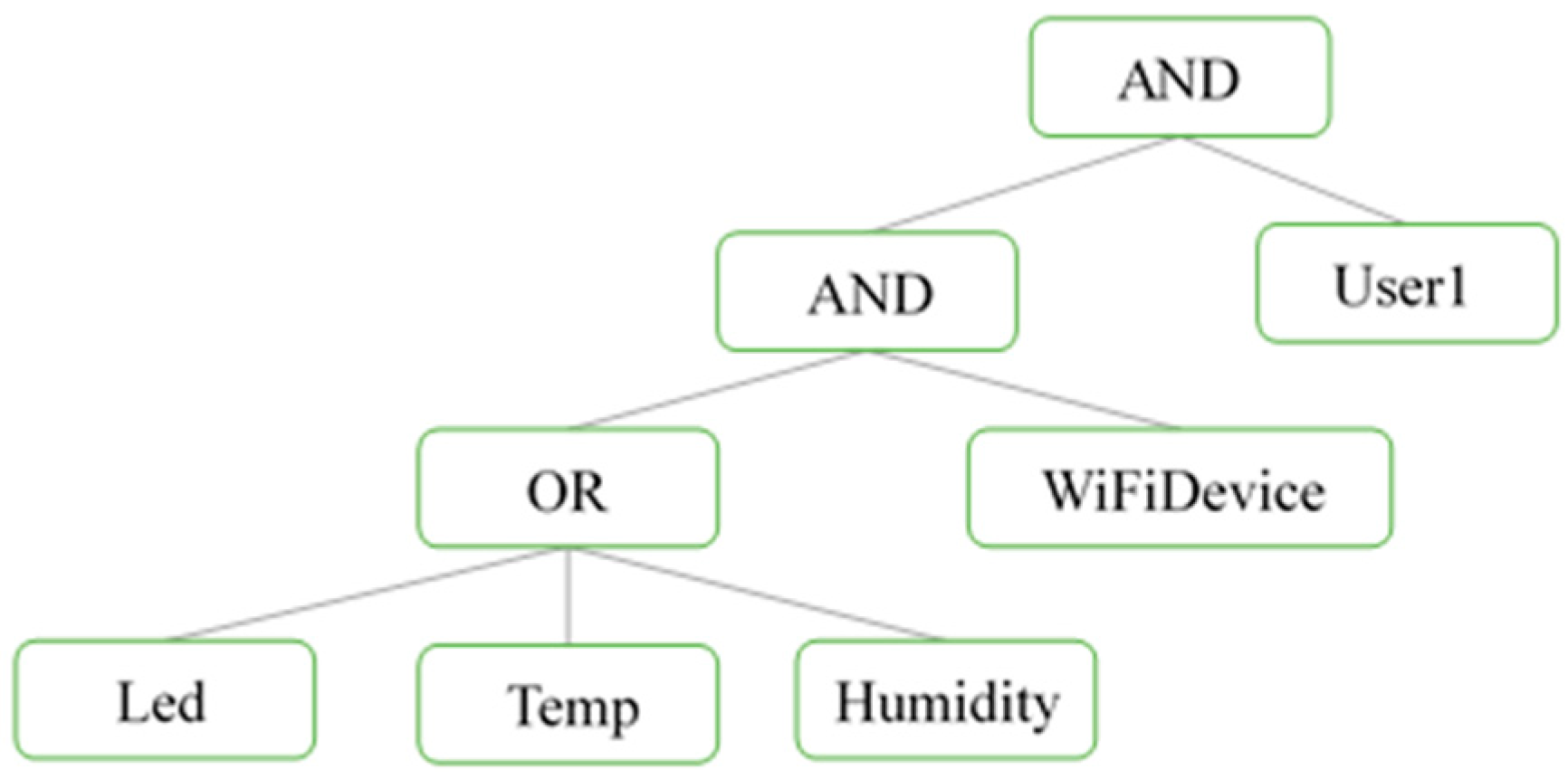
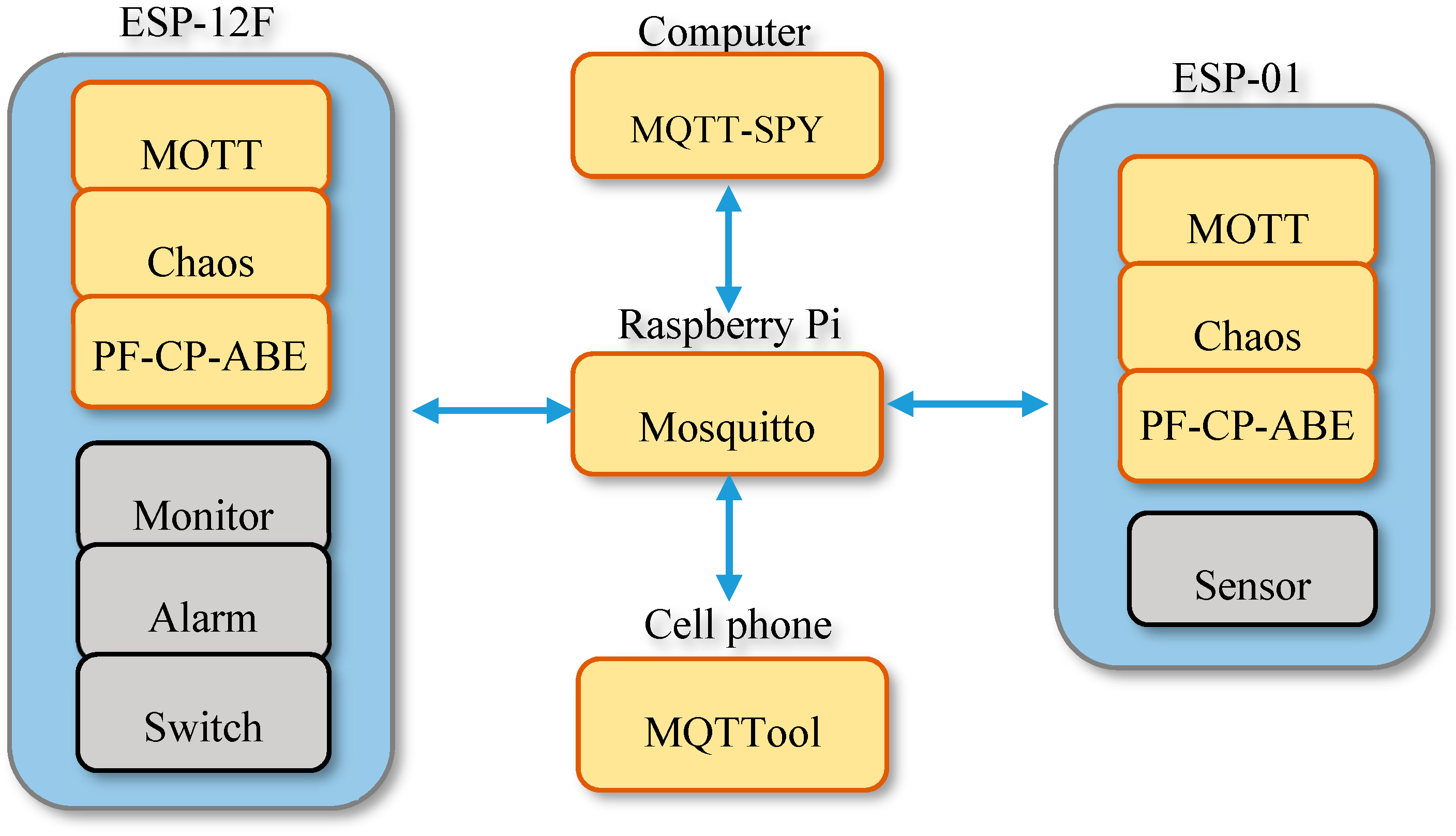
Figure 4, and raspberry pi 3 to act as the broker, which can also be the authority too. The entire system architecture is shown in
Figure 5. ESP-12F and ESP-01 are two wireless IoT devices, and both are equipped with MQTT protocol, a chaos system, and PF-CP-ABE. All the messages are transmitted in an MQTT format, and are passed through the network to everyone. ESP-01 is the data owner (publisher), and it possesses a chaos master system. It needs to transmit all the parameters of chaos synchronization and attributes them to ESP-12F, which possesses a chaos slave system. ESP-01 with a temperature sensor will keep publishing ciphertext of the temperature, and ESP-12F will subscribe, decrypt, and show it on the displayer. There are some simulation situations where, if the temperature is too high, the alarm led will be lit up, and the switch on ESP-12F will act as a remote controller. All the values and states of devices will be published, and will be analyzed by an open source utility MQTT-SPY, monitoring software on a computer, and the MQTT tool, an IOS application on a cell phone.
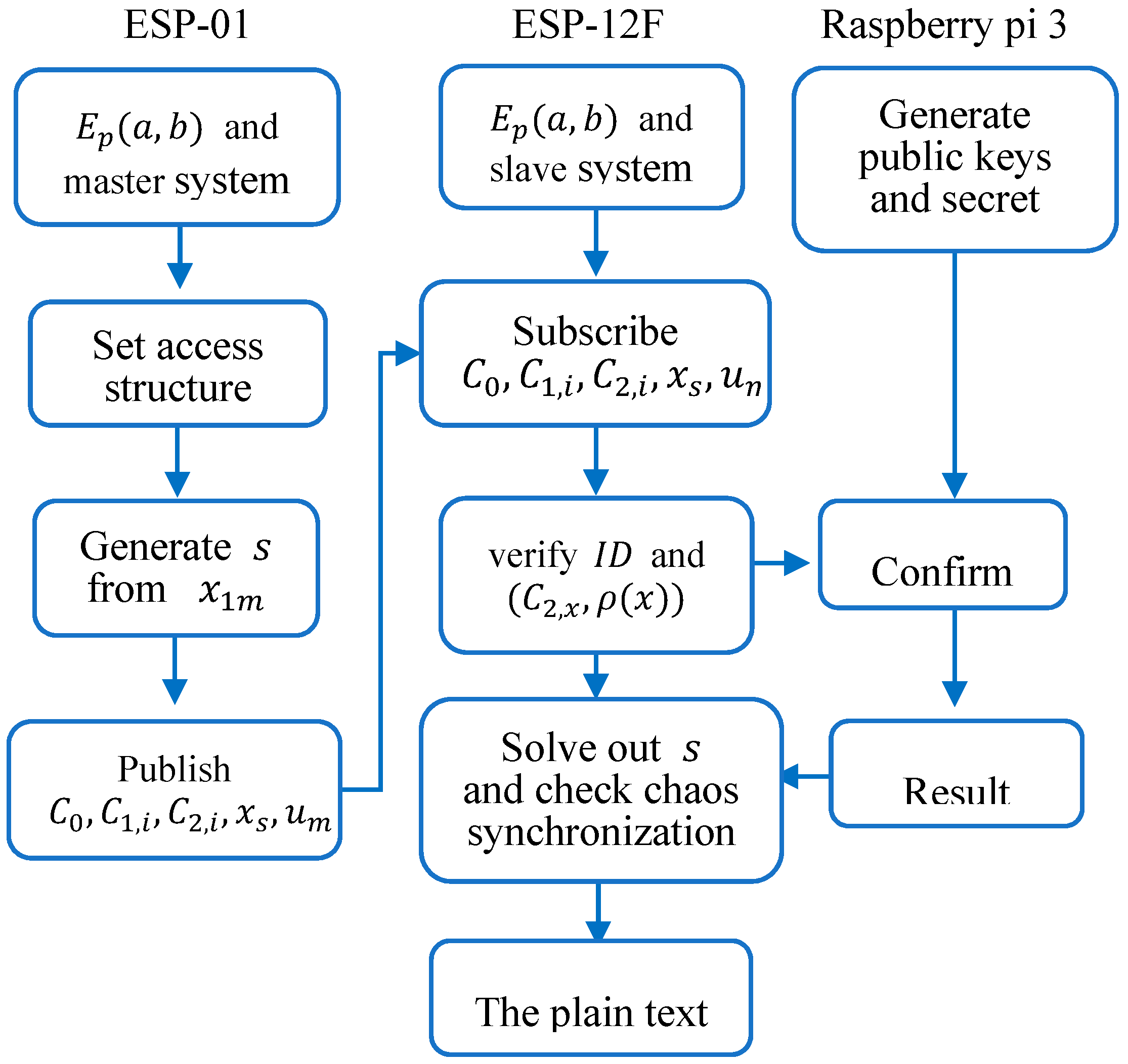
The encryption and decryption of the CS-ABE flow chart are shown in
Figure 6 and
Figure 7, respectively, where the state variable of the master system also encrypted like
,
, and
is one of the parameters of the synchronization controller. At first, before chaos synchronization, both ESP-01 and ESP-12F establish the same elliptic curve and chaos system. The data owner, ESP-01, sets an access structure and generates
from its master system, and then publishes all parameters of attributes and synchronization. On the other side, ESP-12F subscribes it and sends its identity to the authority to request a valid result. After the identity is validated and the result is received, ESP-12F can calculate all the values to get the plain text of the temperature, and the synchronization controller still works. After both master and slave systems are synchronized, ESP-01 will stop publishing the parameters of attributes and only publish those of chaos synchronization, as shown in
Figure 8. When ESP-12F receives them, it can generate
from its slave system to decrypt the ciphertext.
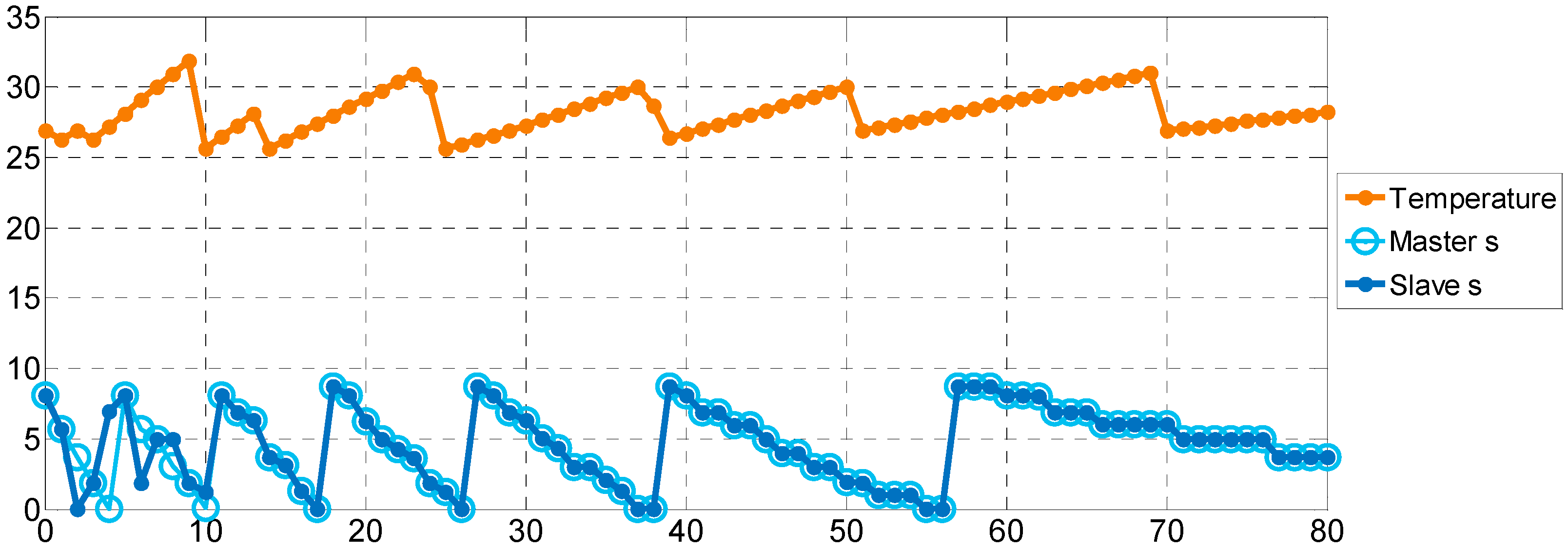
From the analysis of MQTT-SPY, we recorded 80 data for the original temperature and the secret number
in the master and slave system, respectively. Then, we used the plot tool in Matlab to produce a graph, shown in
Figure 8. The upper line is the temperature sensed on ESP-01, and the lower two lines are the secret number
of both the master and slave system used to check that they are the same. From this, we can find out that the secret number is different at the beginning, because chaos systems are not synchronized, and the secret number is solved by the PF-CP-ABE algorithm. After synchronization, the two randomly secret numbers become consistent, which means that the CS-ABE we proposed does work.