1. Introduction
Underground metal detection technology has been widely used in military fields [
1] and also plays an important role in archeology [
2], prospecting [
3], medical positioning [
4], underground metal pipeline modeling [
5] and other fields. Electromagnetic induction (EMI) detection technology is an underground metal detection method that uses secondary field information generated by a changing magnetic field acting on the metal target to detect the state of a target [
6]. In the EMI model, the secondary field is related to nine parameters of a target, which are grouped into the target’s position
, polarizability
, and posture
[
7].
,
,
are the yaw angle, pitch angle and roll angle of the target, respectively. Compared with other underground metal detection technologies, such as infrared imaging and seismic wave technology, EMI detection technology has the advantages of having a strong penetration capability and being nondestructive [
8], so it is widely used in the underground metal detection field. EMI technology includes time domain electromagnetic (TDEM) induction [
9,
10] and frequency domain electromagnetic (FDEM) induction [
11]. In the TDEM method, a pulse signal is transmitted. Then, the position and polarizability of the target are obtained by analyzing the attenuation characteristics of the secondary field signal. Unlike the TDEM method, the FDEM method transmits harmonic signals with multiple frequencies. Through analyzing the amplitude and phase information of the secondary field signal, the position, polarizability and posture of the target can be obtained. Both TDEM induction and FDEM induction are based on the same fundamental physical principles, but the types of information obtained from secondary fields are different. The FDEM method measures the phase and amplitude of the secondary fields, which is different from the primary fields, mainly due to the subsurface properties [
12]. We focus on the FDEM method in this paper.
Inversion algorithms are used to calculate the target’s physical parameters from the observed data. It includes recursive inversion algorithms [
8,
13] and nonrecursive inversion algorithms [
1,
14]. For example, filter methods are classified as recursive inversion algorithms, and gradient methods are classified as nonrecursive inversion algorithms. The filter method uses the system’s dynamic state space model (DSSM) to solve the target detection problems and offers good real-time performance. Filter algorithms mainly include particle filters (PFs) and Kalman filters (KFs). When PFs are in the face of high-dimensional problems such as dipole tracking, the number of required particles increases exponentially, which results in the “curse of dimensionality”. When the noise satisfies the Gaussian distribution, the KFs have the best performance, and this assumption is also reasonable in practical applications. Consequently, we focus on KFs in this paper. Although nonrecursive inversion algorithms have higher accuracy than recursive algorithms, their computational efficiency is lower than that of filter algorithms. We focus on improving the accuracy of KF algorithm in underground target detection.
Filter methods have long been used to solve underground metal detection problems. For example, Grzegorczyk et al. used a KF and an extended Kalman filter (EKF) to solve the problem of underground unexploded ordnance detection [
8]. However, in the traditional EMI model, the secondary field of the target has a nonlinear relationship with six parameters that relate to the position and posture and has a linear relationship with the three parameters of polarizability. The high nonlinearity of the model results in poor performance of the filter algorithm. Dekdouk et al. used the concept of the magnetic polarizability tensor to reduce the number of nonlinear parameters from six to three in the traditional model [
15]. Ambruš et al. used a linearized model to solve the problem of underground metal detection [
16]. However, one problem that cannot be avoided in the current research is that the performance of filter algorithms is extremely sensitive to the initial value of the filter. In the case of a large initial value error, the precision is low, and the results sometimes are divergent. In [
17], Chan et al. used a least squares estimator to yield an estimation of the acceleration input vector for maneuvering targets. In [
18], Koopman used maximum likelihood estimation to solve the initialization problem of the KF. Based on their research, the least squares method and two image processing algorithms are combined to obtain initial values for the filter algorithm in underground metal detection. Early research in the underground metal detection is mostly based on the assumption of Gaussian noise distribution. Tomasz et al. investigate KF and EKF for the inversion of unexploded ordnance (UXO) polarizabilities and positions under the dipole model approximation and the assumption of Gaussian noise distribution, respectively [
19]. There are also some researchers studied the application of detection algorithm in non-Gaussian noise. Tantum et al. studied the effects of assuming i.i.d. white Gaussian noise on the performance of likelihood ratio detectors and maximum likelihood classifiers implemented in a non-Gaussian noise environment. In addition, they had illustrated the effects of mismatch between the assumed and actual noise distributions on detection and classification performance for likelihood ratio processors derived under several assumptions regarding the noise distribution [
20]. Gordon et al. had proposed the bootstrap filter for implementing recursive Bayesian filters [
21]. In addition, the method is not restricted by assumptions of linearity or Gaussian noise. In [
22], Jay et al. derived a theoretical expression of the optimum non-Gaussian radar detector. The researchers above had made certain research about non-Gaussian noise. In this paper, we focus on the improvement of the filter algorithm’s performance in the environment of non-Gaussian noise.
In this paper, we propose an initial value estimation method for the KF and the EKF (IVE-KF) for underground metal detection. In IVE-KF, the horizontal position of the target is estimated by the first-order central moments of the map that are composed of secondary field data, the depth of the target is estimated by the full width at half maximum (FWHM), and the initial states of the other six linear parameters are estimated by the least square method combined with Tikhonov regularization. Finally, these initial states are used as the initial values of the filter algorithm, and the parameters of the metal target are solved simultaneously by combining the KF and the EKF algorithms. To evaluate the performance of IVE-KF, a simulation platform for EMI detection is built in this paper. The simulation results show that the convergence of IVE-KF is better than that of the filter algorithm with random initial values in the application of underground metal detection, and the detection accuracy is close to that of the Levenberg–Marquardt (LM) algorithm of inversion when the signal-to-noise ratio (SNR) is greater than 30 dB; in addition, the computational complexity of IVE-KF is lower than that of the LM algorithm.
The detailed content of this paper is arranged as follows:
Section 2 introduces the system model.
Section 3 introduces the IVE-KF algorithm, which includes the initial value estimation algorithm and the filter algorithm.
Section 4 introduces the simulation system and evaluates the performance of the IVE-KF algorithm.
Section 5 concludes the paper.
2. System Model
Notation: In this paper, bold letters denote vectors and matrices; omega denotes the angular frequency of electric current in the transmitter; w denotes the number of sets of secondary field data we collected in the process of detection; , and respectively denote the values of the primary field magnetic field intensity, primary field magnetic induction and secondary field magnetic induction, which contain x, y, and z components; denotes the collected secondary field data generated by the simulation system; , , and denote the pitch angle, roll angle and yaw angle for a vertically placed cylinder target, respectively; and j denotes the imaginary unit.
In the detection system, the metal target is located at a certain position in the underground space. When the primary field (generated by the transmitter) acts on the metal target, a secondary field is generated by the eddy current of the metal target. The secondary field data are collected by a detector sequentially placed in different positions on the detection plane (the detector includes a transmitter and a receiver; in this paper, we assume that these two components are coincident). Estimation of the target’s parameters can be obtained from these secondary field data. As shown in
Figure 1, in EMI detection, the commonly used data collection scheme is 2D scanning [
14,
23,
24]. The detector is placed on the scanning line to collect data successively. On each scanning line, the distance between two adjacent sampling points is called the point interval
, and the distance between the scanning lines is called the line interval
. The plane where the scanning line is located is called the detection plane. Assuming that there are
scanning lines,
sets of data are collected on each scanning line, ultimately producing
sets of data collected on the detection plane. Each set of data are represented by
. Based on these collected data, the initial value estimation algorithm can be used to obtain the approximate estimation of the target state, and, by using these initial values, an accurate estimation of the metal target’s parameters can be obtained quickly by the KF and EKF algorithms. In
Figure 1, the target position vector is
, the posture is
,
,
, and the polarizability is
. To obtain an estimation of the target’s parameters from secondary field data, it is necessary to characterize the EMI response with a suitable forward model.
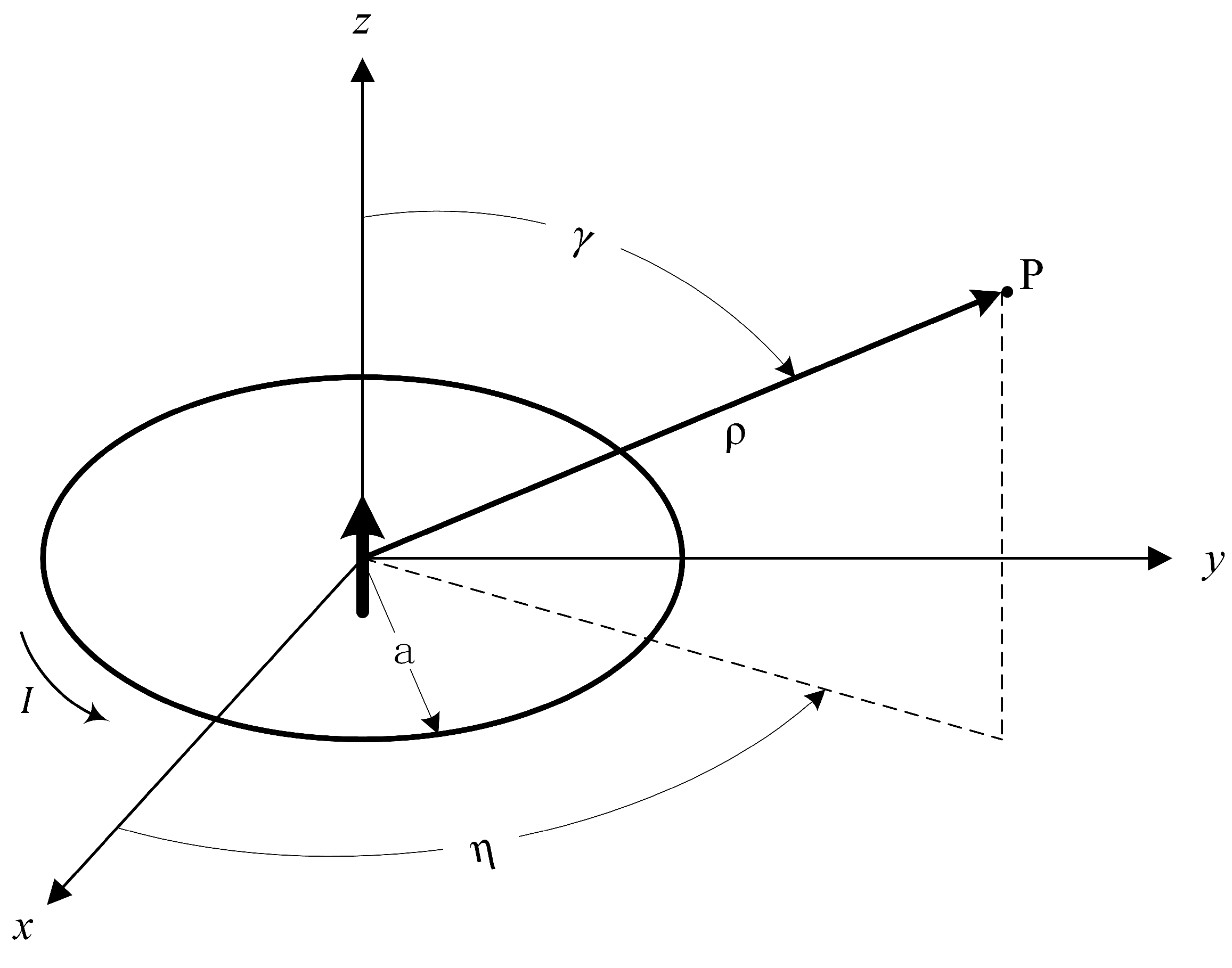
A spherical coordinate system is used in the primary field calculation because calculating the primary field in this coordinate system is simpler than that in a Cartesian coordinate system. As shown in
Figure 2, there is a circular coil with a radius of
a in the space, and a harmonic current
with an angular frequency of
is applied to the coil. In the spherical coordinate system, the center of the toroidal coil lies at the origin.
are the radial distance, polar angle and azimuthal angle, respectively. The inducted field strength at any position
in space is [
25]:
where
is the vacuum permeability,
is the wave number of electromagnetic waves in the propagation medium,
is the wavelength of the electromagnetic waves, and
v is the wave velocity in the medium. Then, the spherical coordinates can be converted to rectangular coordinates according to Formula (
4):
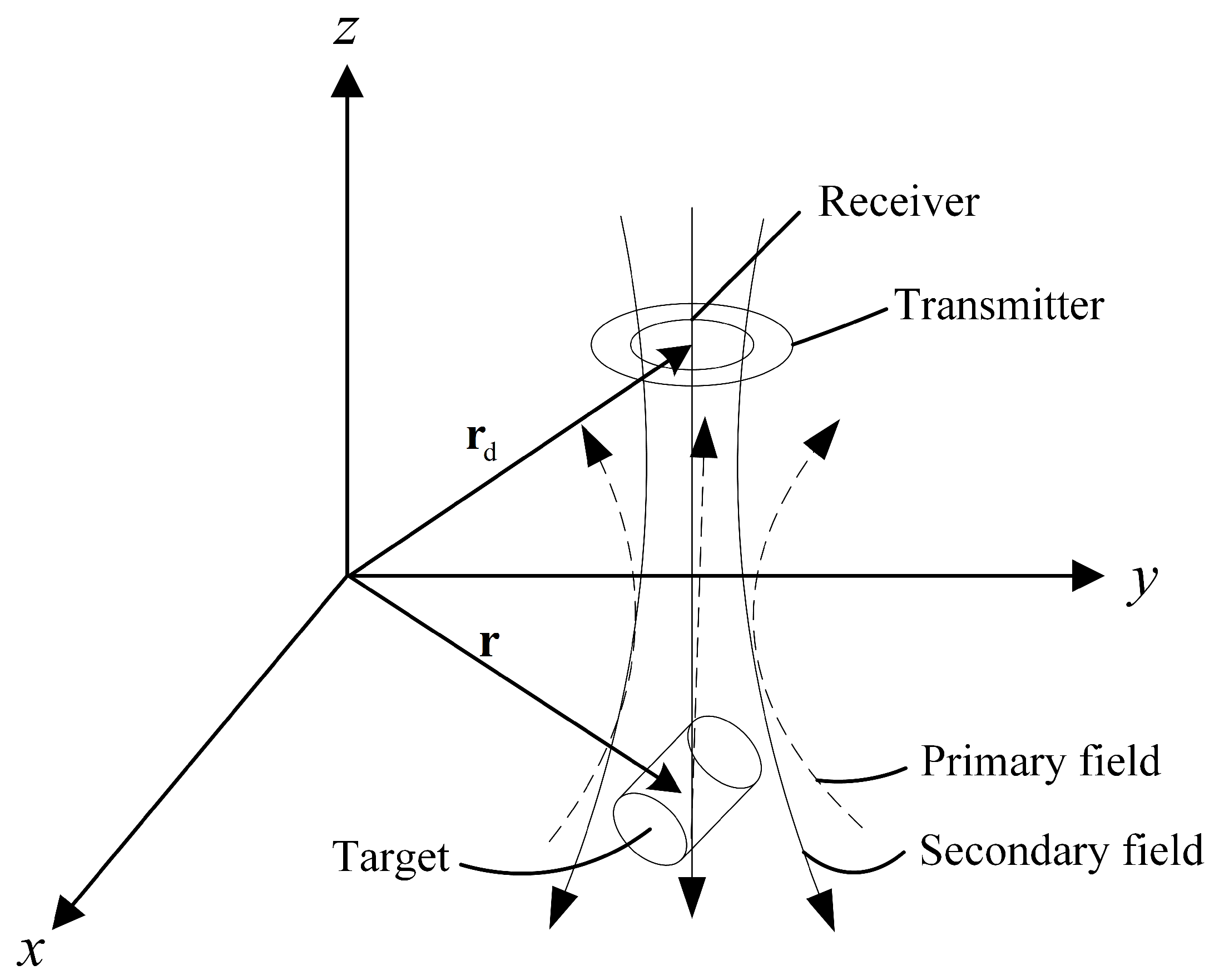
The principle of electromagnetic induction in underground metal detection is illustrated by
Figure 3, the detector position is
, and the target position is
. When the length of the detected target is much shorter than the distance between the detector and the detected target, the detected target can be idealized as a magnetic dipole, which satisfies the requirements of engineering applications. When the primary field acts on the metal target, an eddy current is generated inside the metal. The magnetic field sensor can be used to obtain the secondary field
generated by the eddy current [
26]:
where
is the induced dipole moment at the metal target position,
is the permeability of vacuum,
r is the distance from the detector center to the metal target center, and
is the vector of the metal target center pointing to the detector center. The value of the induced dipole moment is related to the detected target’s posture and polarizability and the primary field strength [
26]:
where
represents the transpose of the matrix
and
is the transformation matrix between the observation coordinate system and the metal target coordinate system, also known as the Euler rotation matrix [
27].
is the primary field strength calculated according to Formulas (
1)–(
3) at the detected target position.
, the polarizability of the metal target, is an intrinsic feature of the target and is independent of the position and posture:
Formulas (
5) and (
6) imply that the secondary field has a nonlinear relationship with the position and posture angle of the detected target and scales linearly with the polarizability. Therefore, a nonlinear equation needs to be solved to obtain the position and posture angle, which is a relatively complicated undertaking. In [
15], Formula (
6) is written as follows:
where
is a
magnetic polarizability tensor, which is related to the polarizability and posture of the metal target.
fully reflects the dipole response of the metal target and it can be proven that
is a
symmetric matrix [
28]; thus, there are only six different elements in
.
can be expressed as follows:
Magnetic polarizability tensor
is related only to the posture and the polarizability of the target; therefore, it is constant during the detection process.
can be directly obtained from the secondary field data without obtaining the target’s polarizability and three posture angles. Because the secondary field strength and
are linearly related, the use of
reduces the number of nonlinear parameters in the EMI model and greatly improves the computational efficiency in the calculation process. Once the six parameters in
are obtained, the polarizability
and the three posture angles can be obtained directly. Eigendecomposition is performed on
to obtain:
where ∑ is a diagonal matrix, each element on the diagonal line is the eigenvalue of
, and
are the elements on the diagonal line of ∑. Since
is a symmetric matrix,
, and the corresponding posture angles can be obtained:
Finally, the secondary field is represented as (with the constant being omitted for conciseness):
where
and
are the position vectors of the detected target and detector, respectively.
,
, and
are the posture angles of the target,
is the target’s polarizability,
is the permeability of vacuum,
is Green function, which is related only to the position vector
,
is the magnetic polarization tensor,
is the primary field magnetic induction at the detected target and
, and
is the permeability of vacuum.
The Formula (
14) can be further abstracted as:
where
is a nine-dimensional vector and
x,
y and
z are the positions of the target object in the coordinate system.
4. Simulation Platform and Algorithm Performance
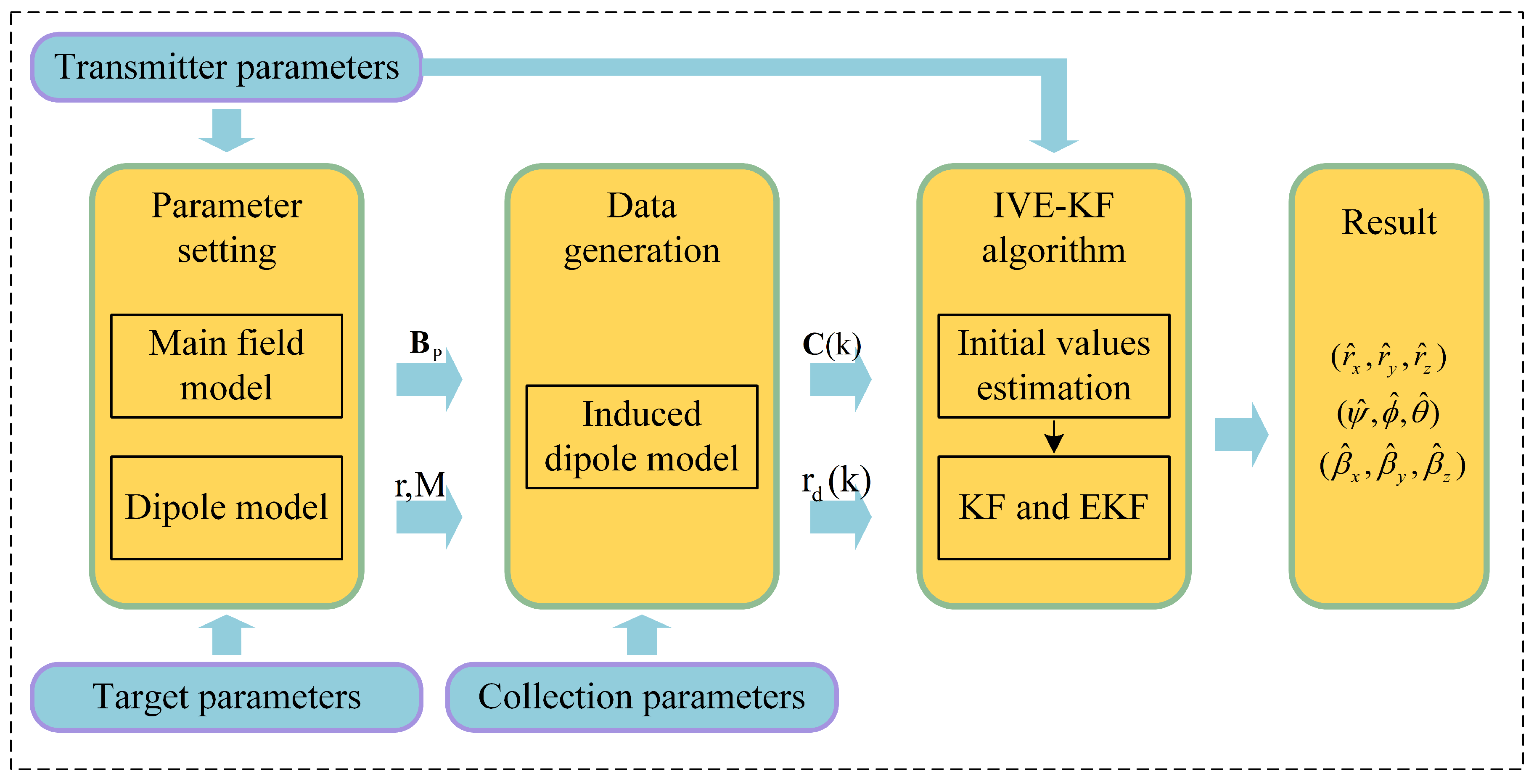
To verify the performance of the IVE-KF algorithm, an EMI detection simulation platform is built in this paper.
Figure 5 is the diagram of the simulation system. The transmitter parameters, target parameters and collection parameters can be set in the simulation system. According to the primary field model, the primary field
at the detected target’s position can be obtained. Then, the target’s induced dipole moment and secondary field data
at the detector position
can be obtained according to the induced dipole model. Finally, the generated data are processed by using the IVE-KF algorithm, and the parameters, including the position, posture and polarizability of the detected target are calculated. In
Figure 5, the primary field model, the induced dipole model, and the IVE-KF algorithm are given as determined in
Section 2 and
Section 3. For irregular shaped targets, the calculation of the polarizability is very difficult, but, for spherical and cylindrical (axisymmetric) targets with uniform material, the process is relatively easy. The detected targets in the actual scene are mostly axisymmetric targets. Therefore, this paper selects a cylindrical object as the detected target to verify the feasibility and performance of the IVE-KF algorithm.
For a cylindrical target with radius
and length
L, let the length direction be the
z-axis and radial direction be the
x- and
y-axis. The polarizability of the cylinder is [
34]:
where
j is the imaginary unit
and
is the conductivity of the target.
and
are the magnetic permeability and relative permeability of the target, respectively.
is the time constant,
, with
. The parameters to be set in the stimulation system are shown in
Table 2,
Table 3 and
Table 4. In the subsequent simulation experiments, the simulation parameters are set as the values in these tables.
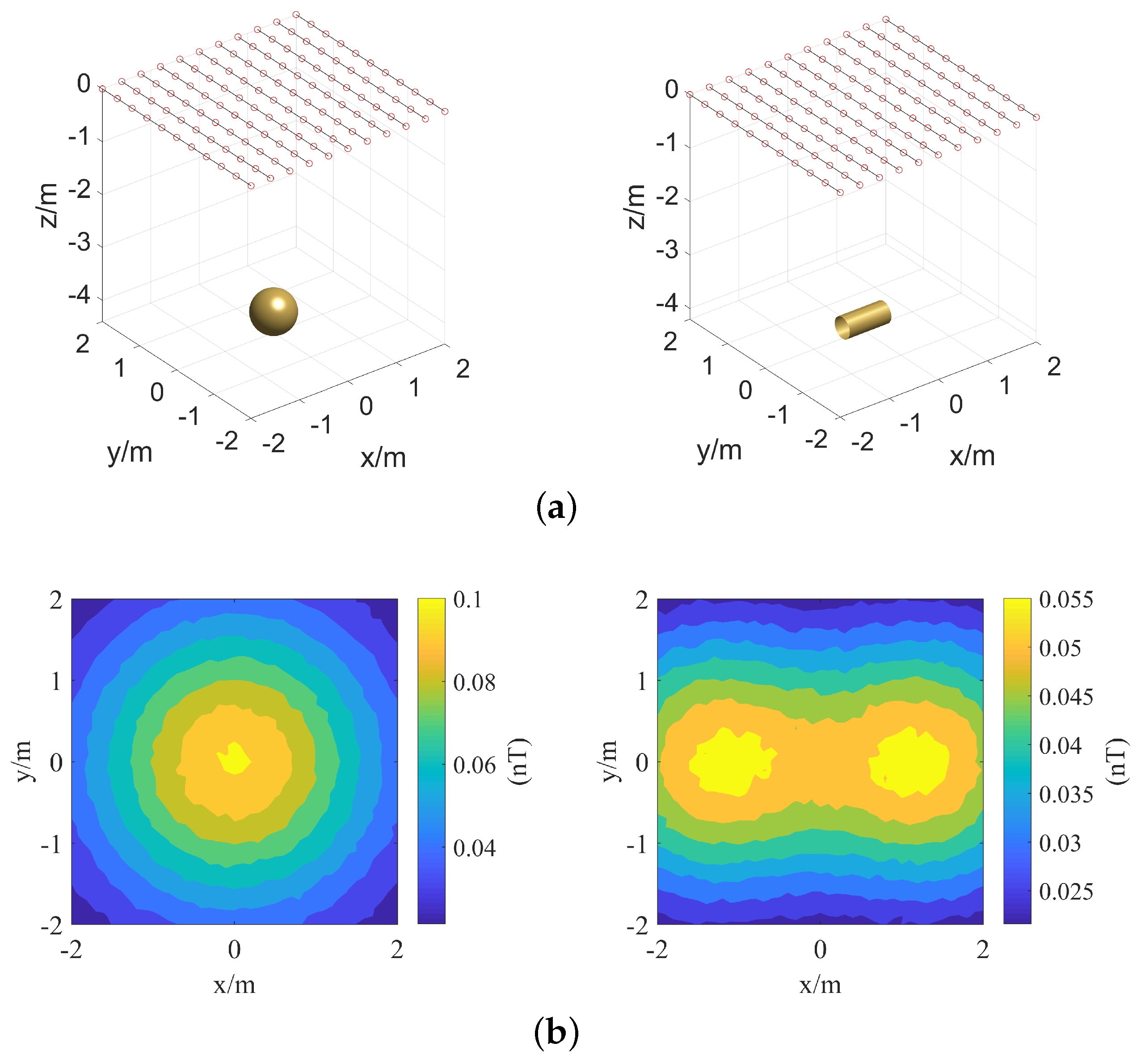
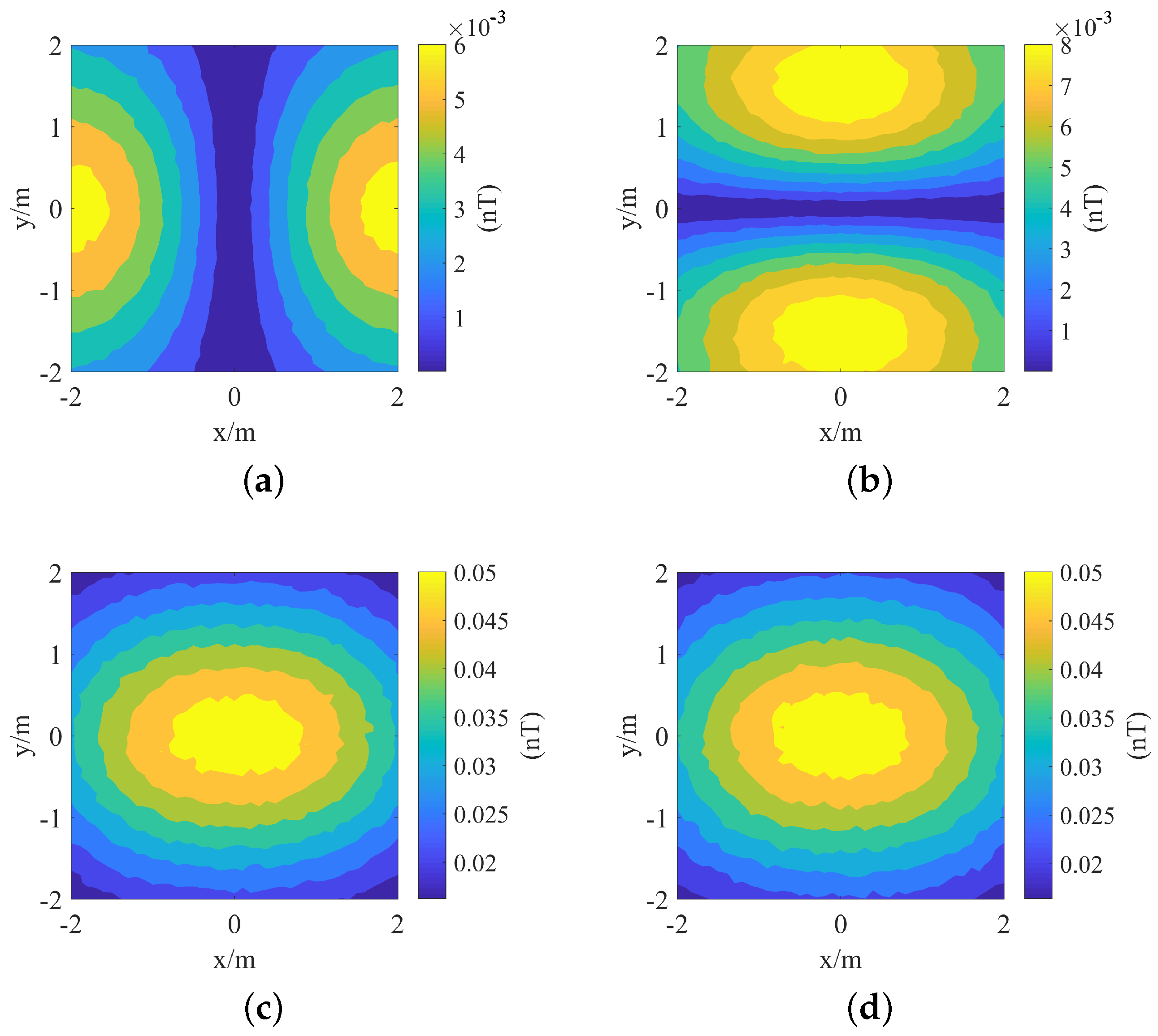
The secondary field strength map for the case in which a cylindrical target is parallel to the
x-axis (that is,
, as shown in
Figure 6) is shown in
Figure 7.
The maps of and are symmetric about the lines and , respectively. Considering that the response is consistent with the response but the amplitude of the is larger than the , is used in the following analysis.
4.1. Initial Value Estimation Performance
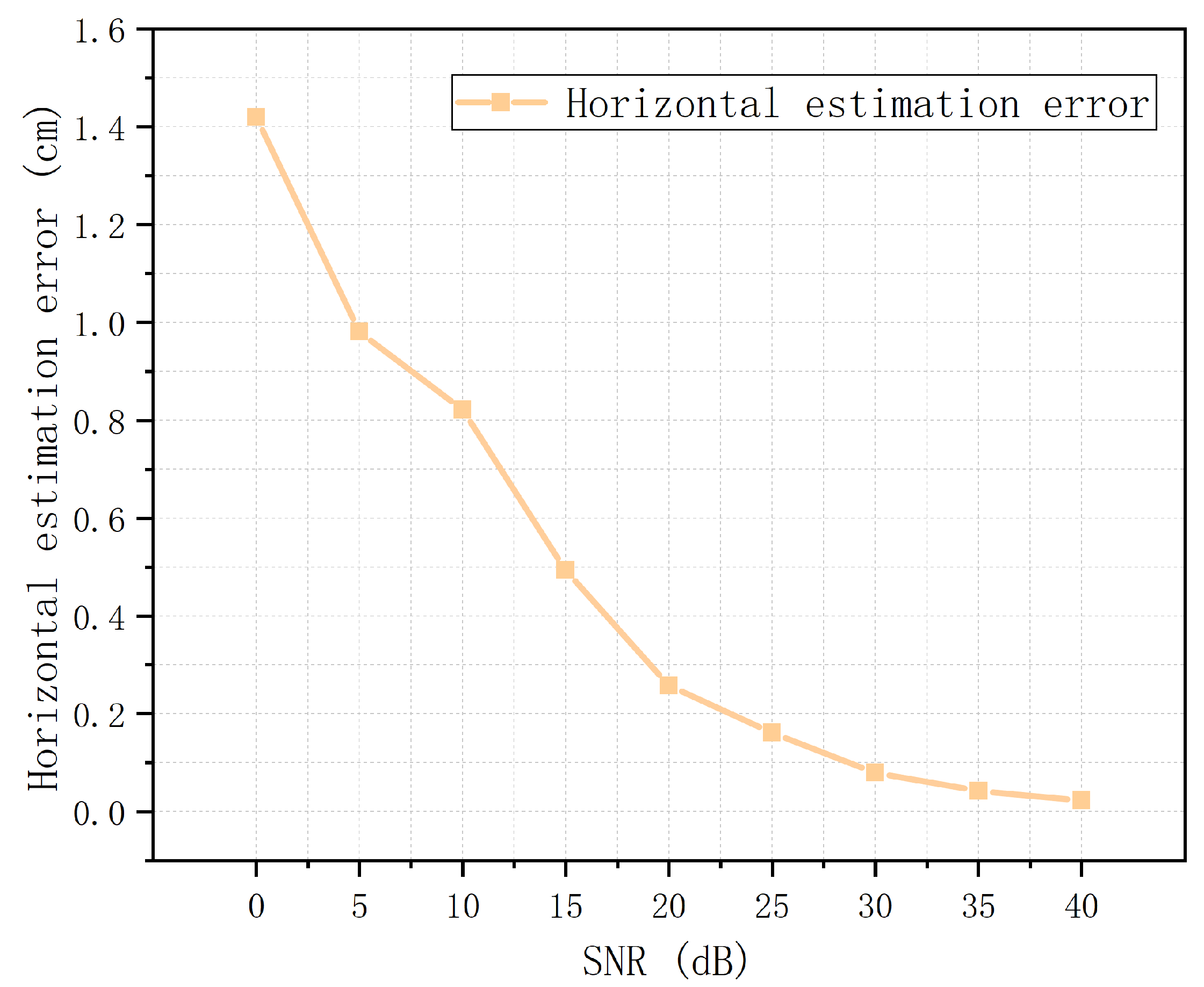
The performance of the initial value estimation algorithm is discussed from three aspects: horizontal position estimation performance, depth estimation performance, and magnetic polarizability tensor estimation performance. To objectively evaluate the horizontal position estimation performance, the horizontal position estimation errors at different simulation conditions are compared in this paper. The horizontal position estimation error
at each simulation condition is the average value obtained from 100 Monte Carlo experiments, which is:
where
is the horizontal position estimation obtained by the
ith Monte Carlo experiment, and
is the true position of the detected target. The results of the horizontal position estimation error for the cylindrical target at different
are shown in
Figure 8. As
increases, the error gradually decreases. When
10 dB, the error is less than 1 cm. The horizontal position estimation exhibits an excellent performance.
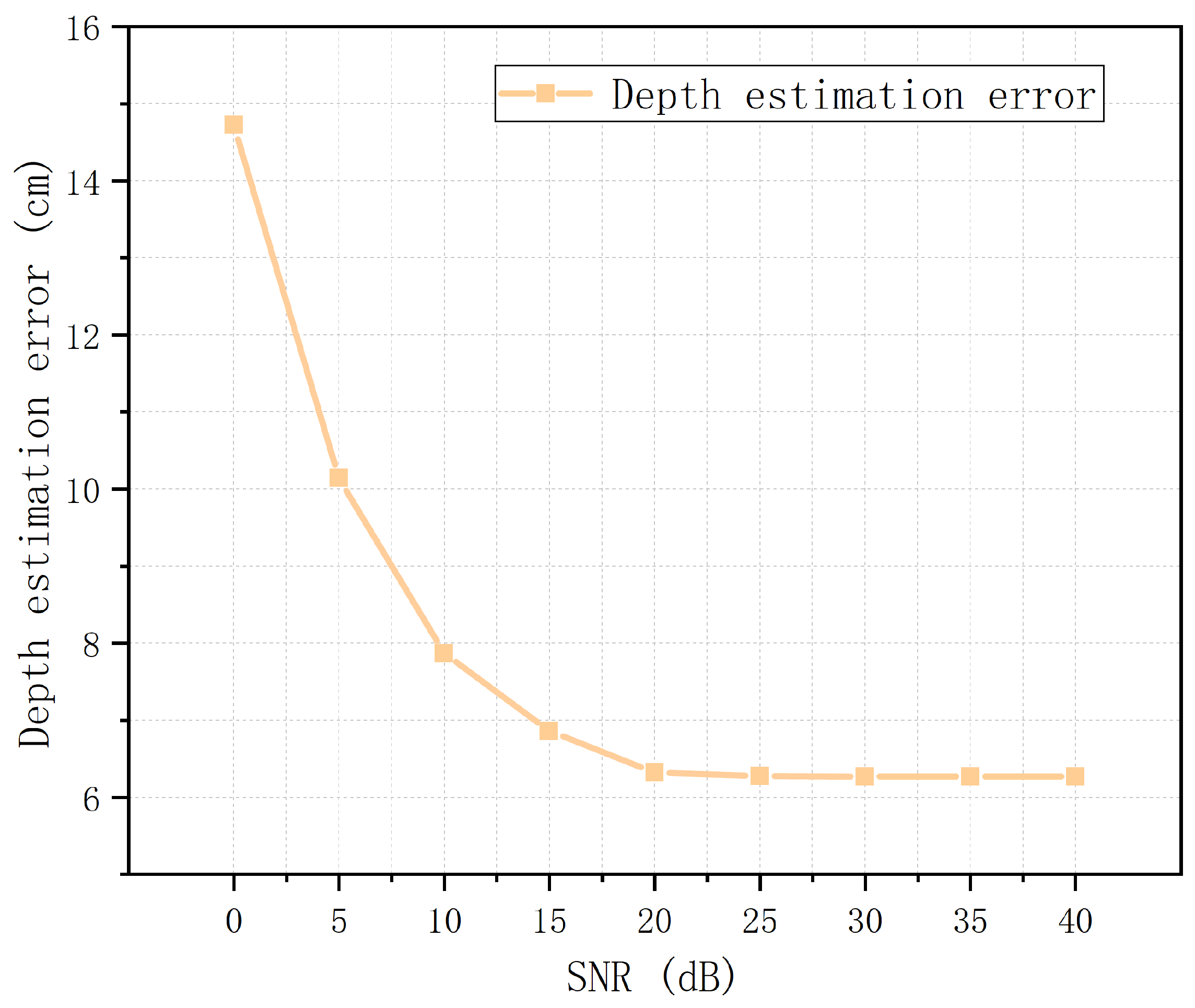
To evaluate the depth estimation performance, the depth estimation errors at different simulation conditions are compared in this paper. The depth estimation error
at each simulation condition is the average value obtained from 100 Monte Carlo experiments:
where
is the depth obtained by the
ith Monte Carlo experiment and
is the true depth of the target. The depth estimation errors of cylindrical targets at different
are compared in
Figure 9. It can be seen from the figure that, as
increases, the depth estimate error gradually decreases. After
reaches a certain threshold, the error gradually stabilizes to approximately 6 cm. The FWHM method can obtain only an approximate estimation of the target depth. Even in the case of no noise, there are errors in depth estimation. The depth estimation errors of cylindrical targets with depths in the range of 35–105 cm are compared in
Figure 10. The error increases with increasing depth but remains within 8 cm. In summary, the FWHM method provides a method for depth estimation with acceptable performance.
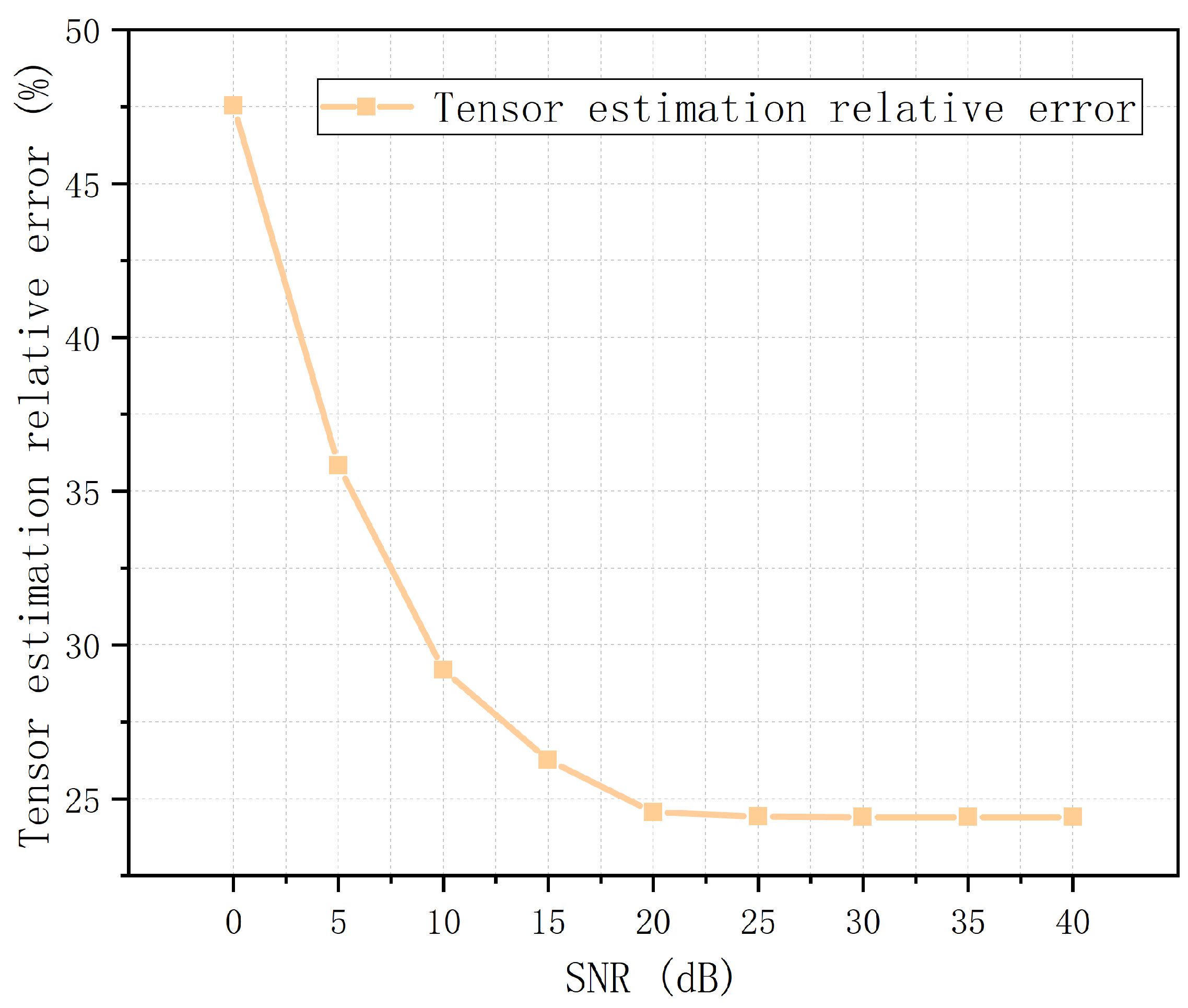
To evaluate the estimation performance of the magnetic polarizability tensor
, the relative error of
under different simulation conditions is compared in this paper. The relative error
for each simulation condition is the average value obtained from 100 Monte Carlo experiments:
where
is the estimation of
obtained by using the least squares method in the
ith Monte Carlo experiment. The changes in the relative error
at different
are shown in
Figure 11. The changes in
are the same as those in
in
Figure 9, which indicate that
is related mainly to the depth estimation performance. This result occurs because the horizontal estimation error is much less than the depth estimation error. However, the depth estimation can be kept within an order of magnitude from the true parameter, which is accurate enough for subsequent filter algorithms.
4.2. Target Parameter Estimation Performance
To evaluate the performance of the IVE-KF algorithm, the position estimation error
, the polarizability estimation error
, and the posture angle estimation errors
,
at different simulation conditions are discussed.
, the values of
,
and
for each simulation condition are the average values obtained from 100 Monte Carlo experiments:
where
,
,
,
are respectively the position estimation, polarizability estimation, pitch angle estimation and roll angle estimation obtained by the IVE-KF algorithm at the
ith Monte Carlo experiment.
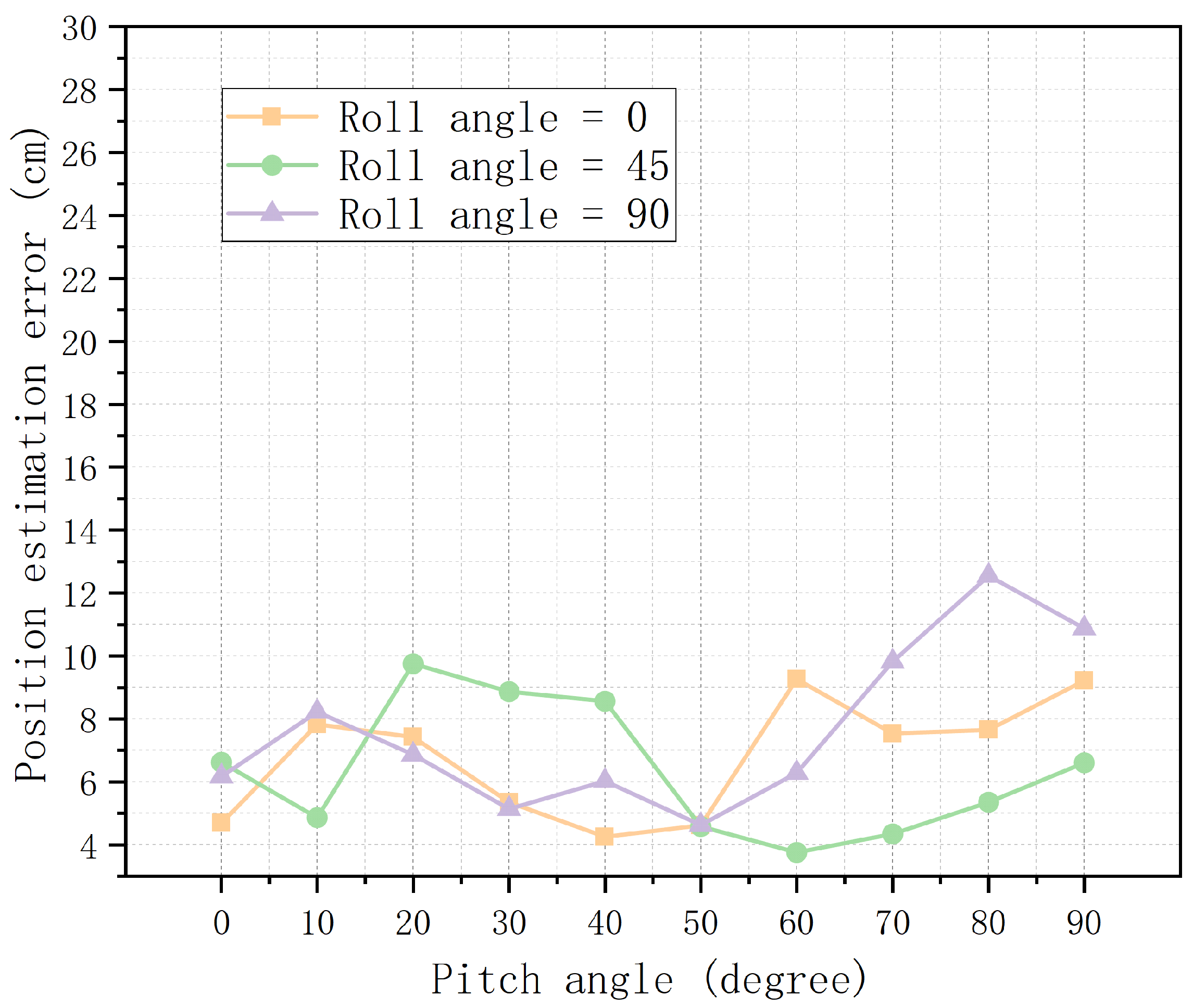
,
,
and
of a cylinder at different postures are shown in
Figure 12,
Figure 13 and
Figure 14. The errors fluctuate as the posture changes, but the position errors are always within 13 cm, the polarization relative errors are within
, and the angle errors are within
. When
, the phenomenon of gimbal lock [
35] occurs, so the angle simulation is performaed only up to
.
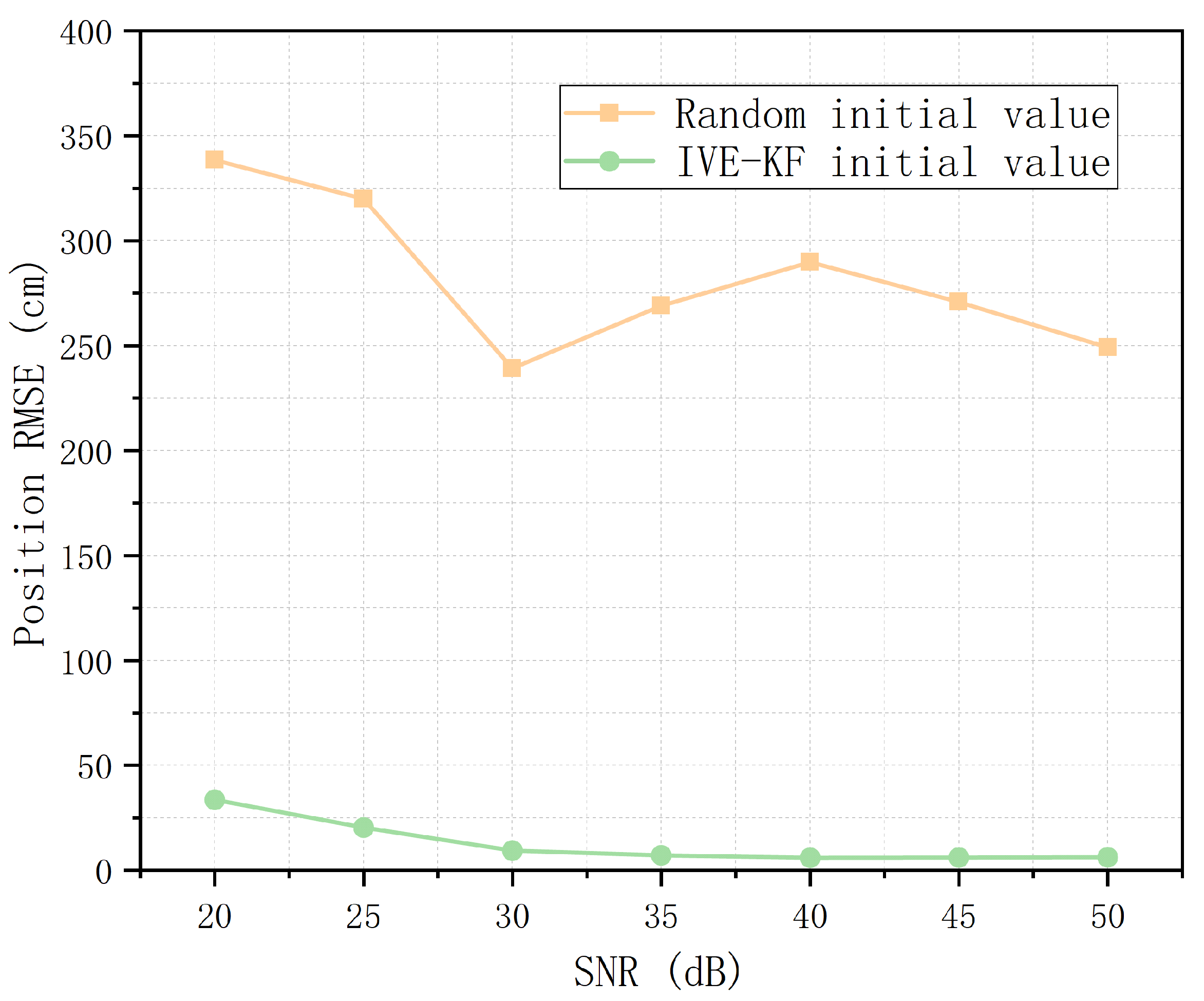
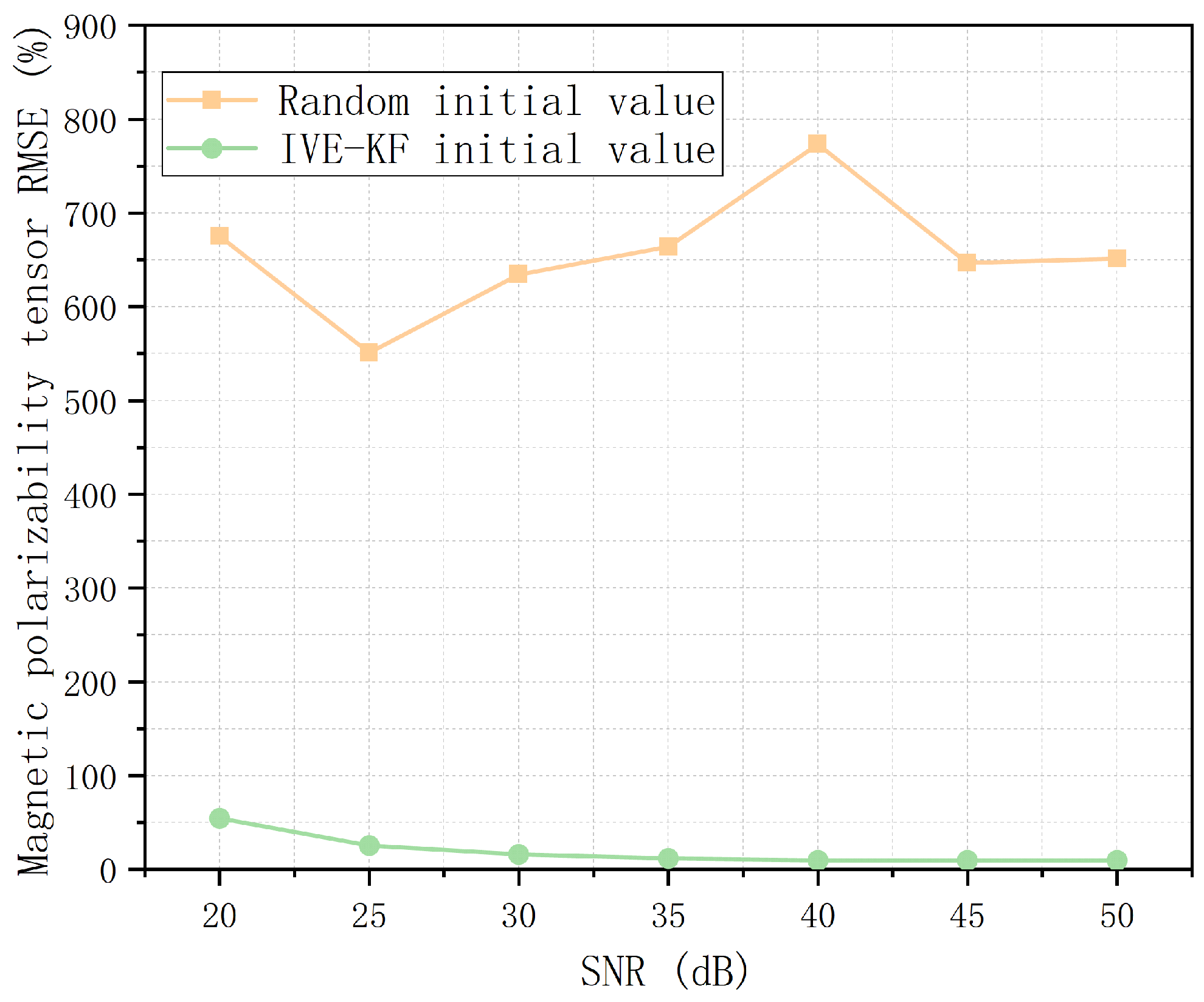
The convergence performances of the IVE-KF algorithm and the filter algorithm with a random initial value are compared in this paper. The convergence results of the algorithm are evaluated using the root mean square error (RMSE) of position and magnetic polarizability tensor.
Figure 15 and
Figure 16 show that the filter algorithm with a random initial value cannot converge to the true value at all. Our initial value estimation algorithm provides a relatively accurate initial value for the KF and EKF and improves the convergence and accuracy of the filter algorithm.
The computational complexities of the inversion algorithm and IVE-KF algorithm in this project are also compared. We use the number of floating point operations (FLOPs) to measure the computational complexity of an algorithm. A FLOP is defined as one operation of addition, subtraction, multiplication, or division of two floating point numbers. The FLOPs of the basic algebraic operations are defined in
Table 5 [
36]:
According to the processes listed in
Table 1 and the corresponding Formulas, and assuming that
w sets data are collected in the process of detection, the FLOPs of IVE-KF algorithm can be obtained and are shown in
Table 6.
The LM algorithm can be analyzed using the same method. The computational complexity of the LM algorithm per iteration is
FLOPs. The FLOPs comparison of the IVE-KF algorithm and LM algorithm is shown in
Table 7:
In
Table 7,
is the iteration times of the LM algorithm. The computational complexity of iterating the LM algorithm twice is equal to the computational complexity of the IVE-KF algorithm. However, the LM algorithm generally iterates 5–8 times in our experiments.
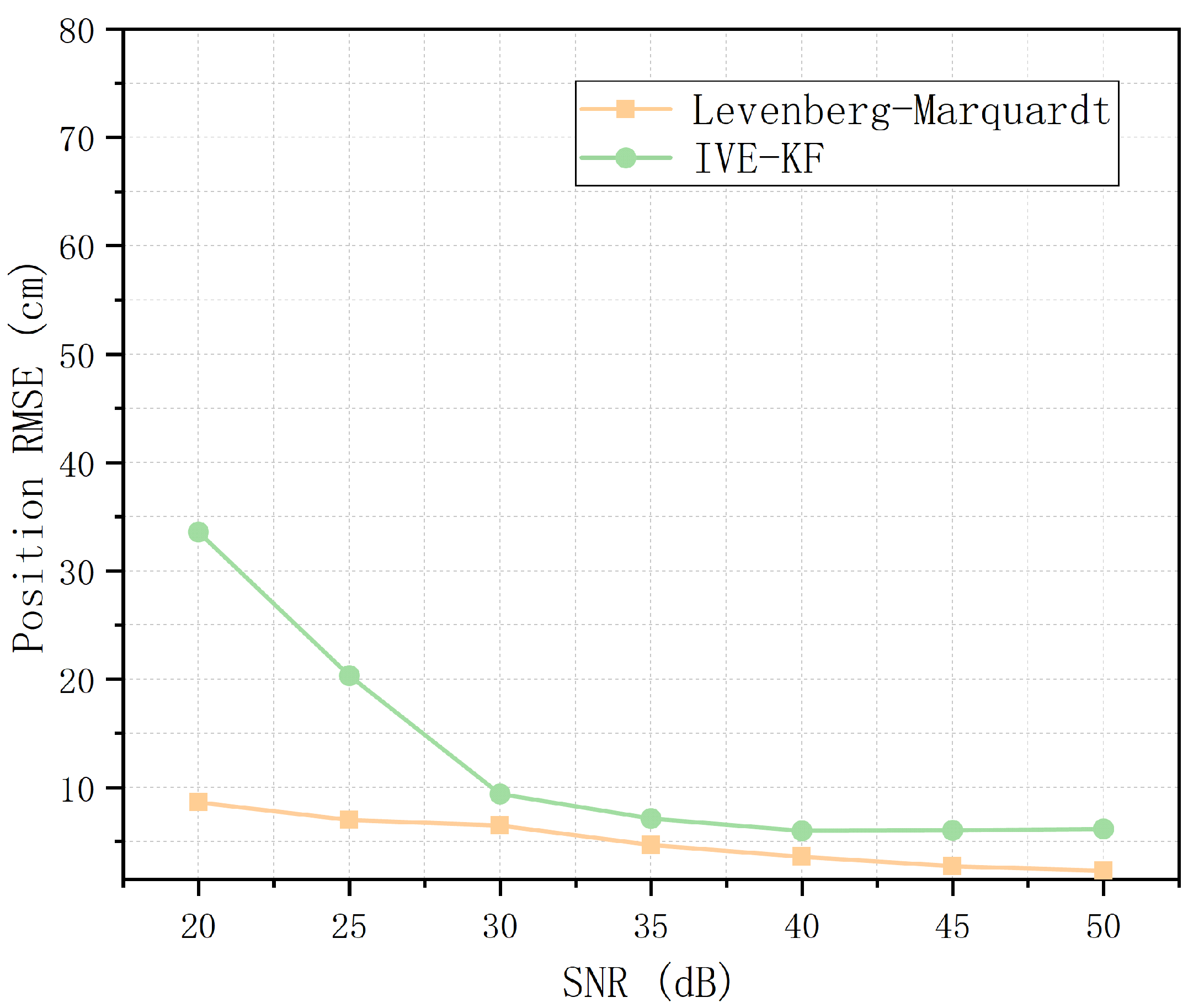
The accuracy performances of the LM algorithm and IVE-KF algorithm are also discussed in terms of the RMSE of the position and magnetic polarizability tensor.
Figure 17 and
Figure 18 show that the results of the IVE-KF algorithm are not as good as those of the LM algorithm, but the accuracies are very similar when the SNR exceeds 30 dB. This result occurs because of the characteristics of the filter algorithm and inversion algorithm. However, the computational complexity of the LM algorithm is much higher than that of the IVE-KF algorithm. Therefore, future research should focus on the accuracy of the filtering algorithm.