Cooperative Multi-UAV Collision Avoidance Based on a Complex Network
Abstract
1. Introduction
2. The Proposed Collision Avoidance System Architecture
3. Core Algorithm Analysis
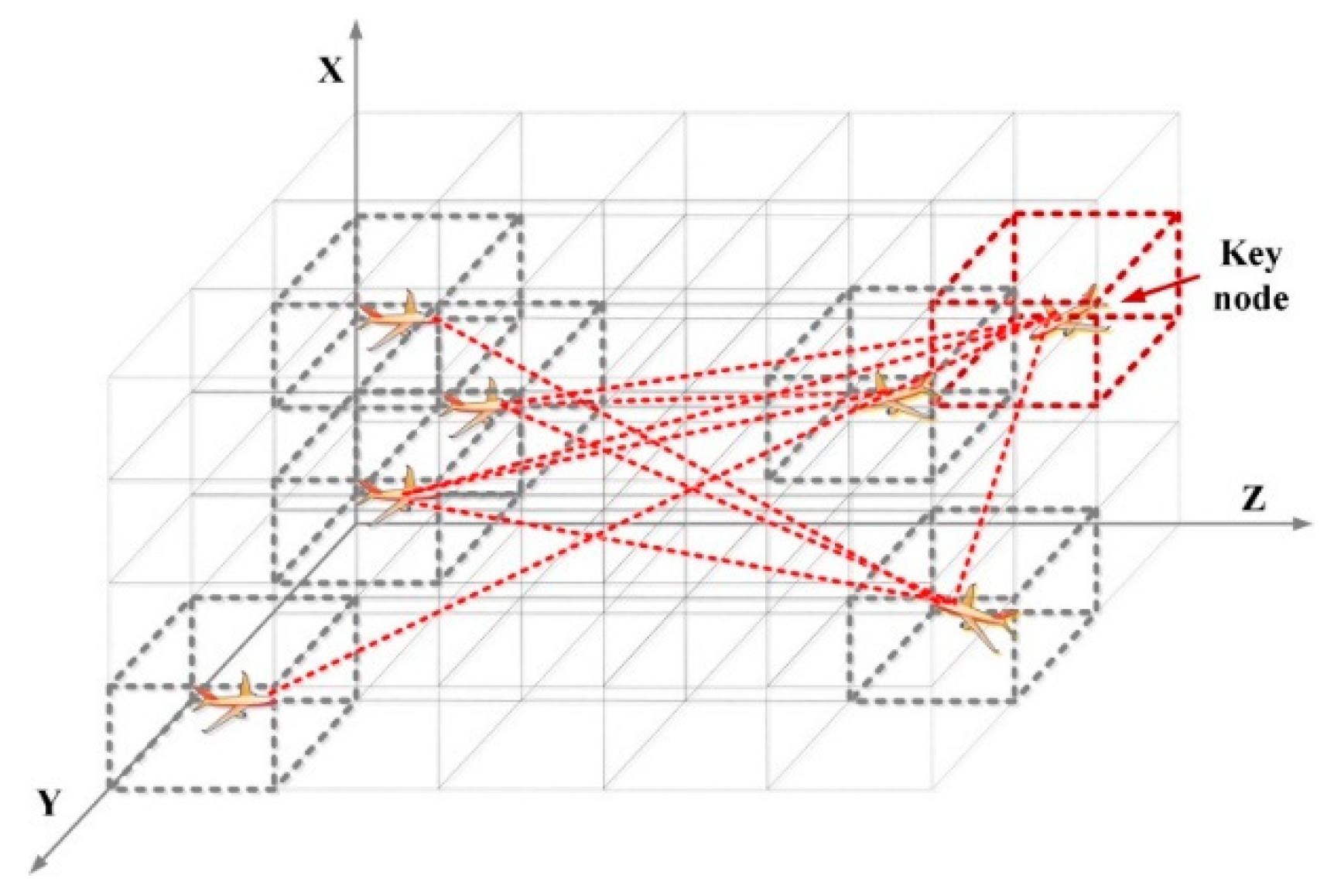
3.1. Representation of Cooperative UAV Flight and Conflict Detection
3.2. Key Node Selection
- sets of node representing UAV flying in the air sector under control.
- , sets of edge implying pairs of UAV that are potentially in conflict.
- , sets of relative velocity between UAVs.
- , graph representing the complex network of the UAV group.
- the threat matrix implying the degree of threat between pairs of UAVs.
- the adjacency matrix of graph G.
- matrix that store the relative distance between UAVs.
- : The average distance of graph G.
- : Node that is chosen to be removed.
- (1)
- If and :
- ①
- If , it is implied that node is on the shortest path between node and node ; then, ;
- ②
- If , it is implied that node is not on the shortest path between node and node ; then .
- (2)
- If only one node exists between node and node , then ;
- (3)
- If , then .
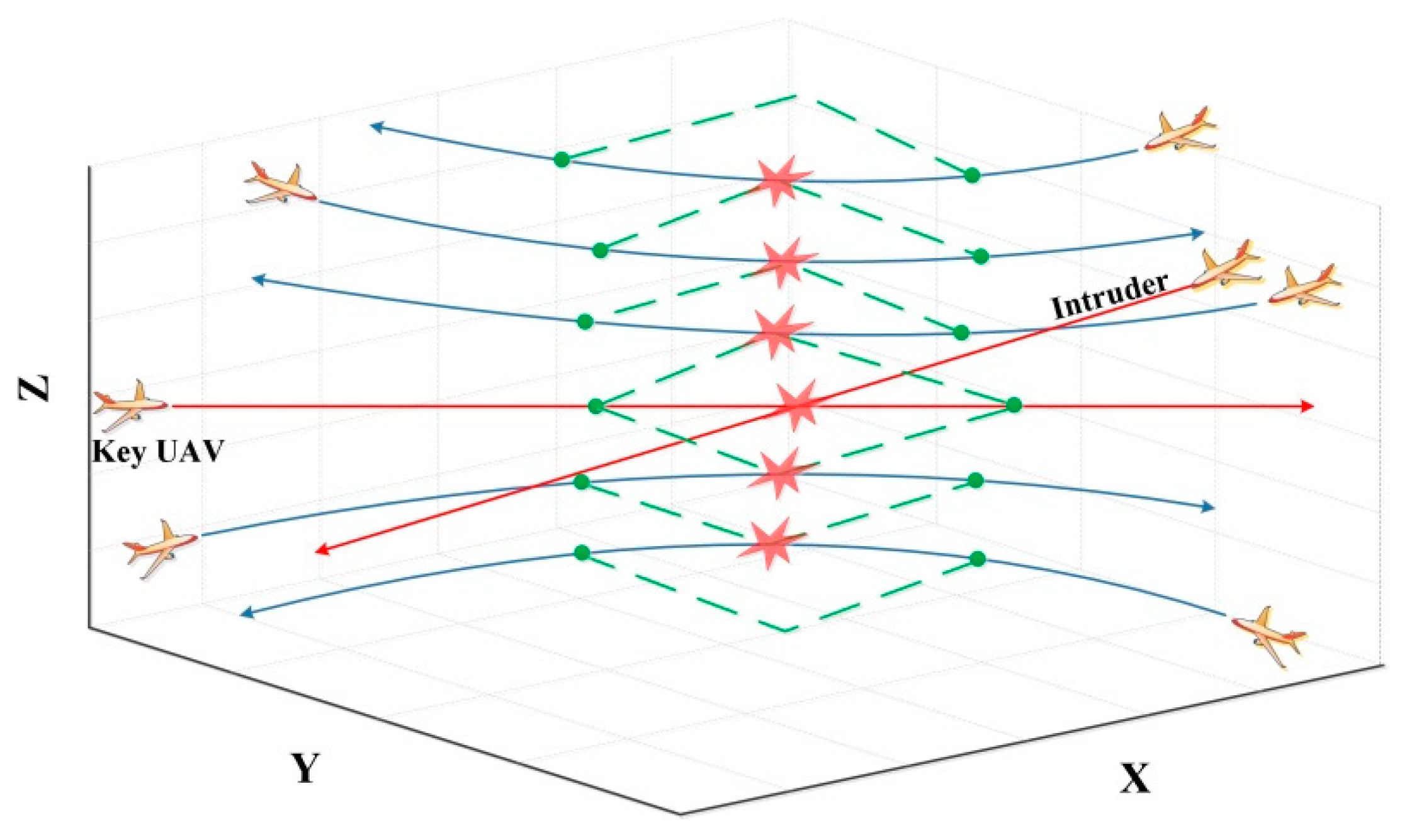
3.3. Direction of Collision Avoidance
| Algorithm 1 Novel Model Based on Key Node Research |
| Input: Initial position, target position, initial velocity of the UAVs, the number of UAVs N, the simulation step length S Output: Trajectories of all the UAVs R for j = 1:S do for i = 1:N do Calculate whether a TA is issued; while TA is issued do Construct the network of the UAVs involved; Calculate the relative distance and relative velocities of all the involved UAVs; Select the key node; Calculate the weight (relevant to the number of intruders, robustness and connected component); Choose the optimal directions for the key node; Update the current direction of the key node; if no collision then break; else R[i][j] = the coordinate of the step j of UAV i; Calculate the state of all the UAVs involved in the scenario; if all the UAVs have reach the safe area then break; return R; |
4. Simulation and Results
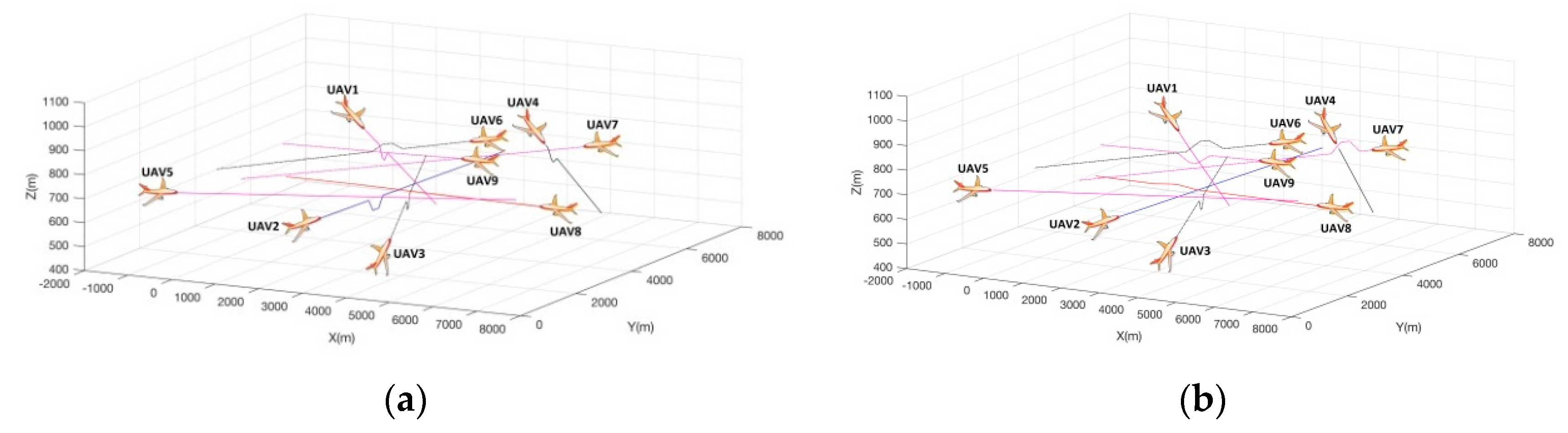
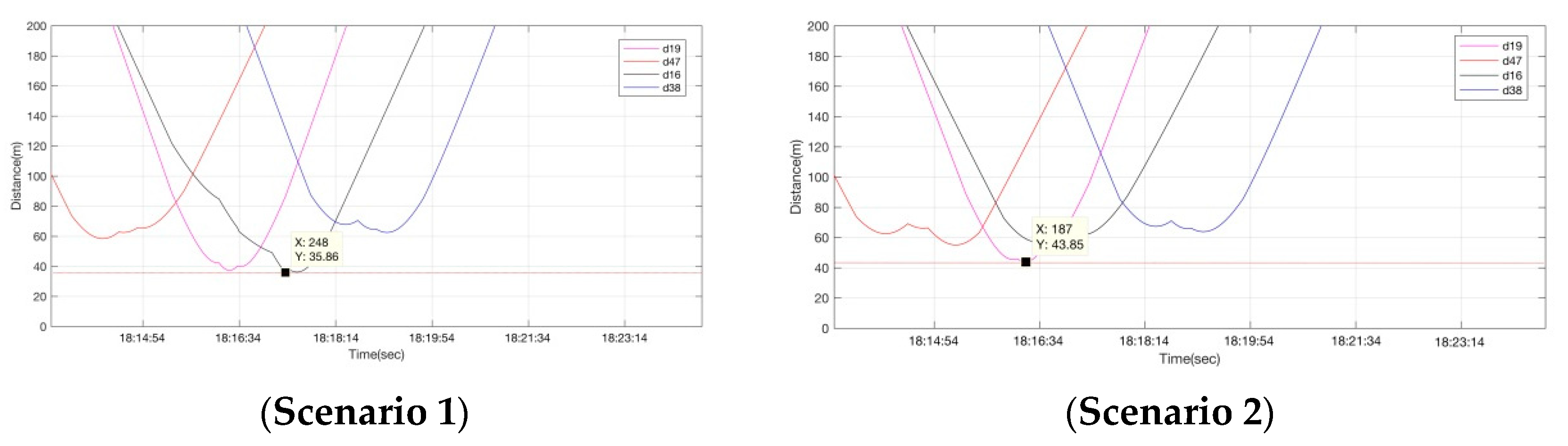
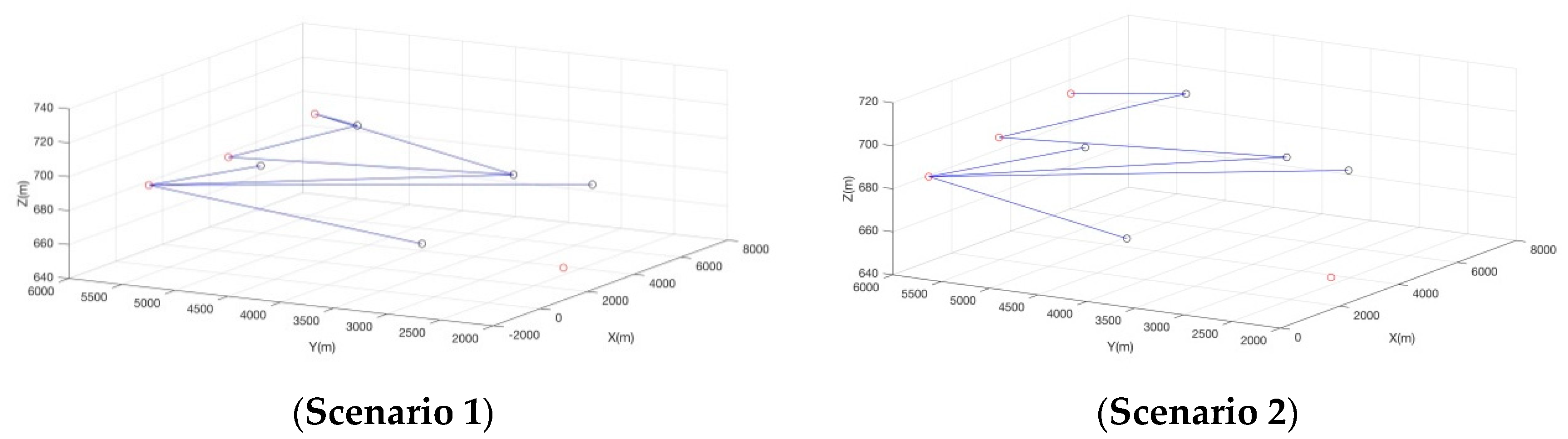
4.1. A Case Scenario
4.2. Further Investigation
5. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Olfati-Saber, R. Flocking for multi-agent dynamic systems: Algorithms and theory. IEEE Trans. Autom. Control 2006, 51, 401–420. [Google Scholar] [CrossRef]
- Rezaee, H.; Abdollahi, F. Mobile robots cooperative control and obstacle avoidance using potential field. In Proceedings of the 2011 IEEE/ASME International, Budapest, Hungary, 3–7 July 2011; pp. 2159–6247. [Google Scholar]
- Rezaee, H.; Abdollahi, F. A decentralized cooperative control scheme with obstacle avoidance for a team of mobile robots. IEEE Trans. Ind. Electron. 2013, 61, 347–354. [Google Scholar] [CrossRef]
- Nguyen, T.; La, H.M.; Le, T.D.; Jafari, M. Formation control and obstacle avoidance of multiple rectangular agents with limited communication ranges. IEEE Trans. Control Netw. Syst. 2016, 4, 680–691. [Google Scholar] [CrossRef]
- Duguleana, M.; Mogan, G. Neural networks based reinforcement learning for mobile robots obstacle avoidance. Expert Syst. Appl. 2016, 62, 104–115. [Google Scholar] [CrossRef]
- Pallottino, L.; Feron, E.M.; Bicchi, A. Conflict resolution problems for air traffic management systems solved with mixed integer programming. IEEE Trans. Intell. Transp. 2002, 3, 3–11. [Google Scholar] [CrossRef]
- Richards, A.; How, J.P. Aircraft Trajectory Planning with Collision Avoidance Using Mixed Integer Linear Programming. In Proceedings of the American Control Conference, Anchorage, AK, USA, 8–10 May 2002; pp. 1936–1941. [Google Scholar]
- Shorrock, S.T.; Kirwan, B. Development and application of a human error identification tool for air traffic control. Appl. Ergon. 2002, 33, 319–336. [Google Scholar] [CrossRef]
- Galster, S.M.; Duley, J.A.; Masalonis, A.J. Air traffic controller performance and workload under mature free flight: Conflict detection and resolution of aircraft self-separation. Int. J. Aviat. Psychol. 2001, 11, 71–93. [Google Scholar] [CrossRef]
- Yu, X.; Zhang, Z. Sense and avoid technologies with applications to unmanned aircraft systems: Review and prospects. Prog. Aerosp. Sci. 2015, 74, 152–166. [Google Scholar] [CrossRef]
- Tang, J. Review: Analysis and Improvement of Traffic Alert and Collision Avoidance System. IEEE Access 2017, 99, 1. [Google Scholar] [CrossRef]
- LaValle, S.M. Planning Algorithms; Cambridge University Press: Cambridge, UK, 2006. [Google Scholar]
- Ha, L.N.N.T.; Bui, D.H.P.; Hong, S.K. Nonlinear Control for Autonomous Trajectory Tracking while Considering Collision Avoidance of UAVs Based on Geometric Relations. Energies 2019, 12, 1551. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, Y.; Yuan, C.; Ciarletta, L.; Theilliol, D. Collision Avoidance and Path Following Control of Unmanned Aerial Vehicle in Hazardous Environment. J. Intell. Robot. Syst. 2018, 95, 193–210. [Google Scholar] [CrossRef]
- Sharma, V.; Jayakody, D.; Kumar, R.; Li, J. Secure and Efficient Context-Aware Localization of Drones in Urban Scenarios. IEEE Commun. Mag. 2018, 56, 120–128. [Google Scholar] [CrossRef]
- Park, J.W.; Oh, H.D.; Tahk, M.J. UAV collision avoidance based on geometric approach. In Proceedings of the SICE Annual Conference, Tokyo, Japan, 20–22 August 2008; pp. 2122–2126. [Google Scholar]
- Chakravarthy, A.; Ghose, D. Generalization of the collision cone approach for motion safety in 3-D environments. Auton. Robot. 2012, 32, 243–266. [Google Scholar] [CrossRef]
- Lin, Y.; Saripalli, S. Sampling-Based Path Planning for UAV Collision Avoidance. IEEE Trans. Intell. Transp. 2017, 99, 1–14. [Google Scholar] [CrossRef]
- Pehlivanoglu, Y.V. A new vibrational generic algorithm enhanced with a Voronoi diagram for path planning of autonomous UAV. Aerosp. Sci. Technol. 2012, 16, 47–55. [Google Scholar] [CrossRef]
- Karimi, J.; Pourtakdoust, S.H. Optimal maneuver-based motion planning over terrain and threats using a dynamic hybrid PSO algorithm. Aerosp. Sci. Technol. 2013, 26, 60–71. [Google Scholar] [CrossRef]
- Xu, C.; Duan, H.B.; Liu, F. Chaotic artifical bee colony approach to uninhabited combat air vehicle (UCAV) path planning. Aerosp. Sci. Technol. 2010, 18, 535–541. [Google Scholar] [CrossRef]
- Campbell, S.E.; Bragg, M.B.; Neogi, N.A. Fuel-optimal trajectory generation for persistent contrail mitigation. AIAA J. Guid. Control Dyn. 2013, 36, 1741–1750. [Google Scholar] [CrossRef]
- Tisdale, J.; Kim, Z.; Hedrick, J.K. Autonomous UAV path planning and estimation. IEEE Robot. Autom. Mag. 2009, 16, 35–42. [Google Scholar] [CrossRef]
- Jorris, T.R.; Cobb, R.G. Multiple method 2-D trajectory optimization satisfying waypoints and no-fly zone constraints. AIAA J. Guid. Control Dyn. 2008, 31, 543–553. [Google Scholar] [CrossRef]
- Grancharova, A.; Grotli, E.I.; Ho, D.T. UAVs trajectory planning by distributed MPC under radio communication path loss constraints. J. Intell. Robot. Syst. 2014, 79, 115–134. [Google Scholar] [CrossRef]
- Sridhar, B.; Ng, H.K.; Chen, N.Y. Aircraft trajectory optimization and contrails avoidance in the presence of winds. AIAA J. Guid. Control Dyn. 2011, 34, 1577–1583. [Google Scholar] [CrossRef]
- Kim, Y.; Gu, D.W.; Postlethwaite, I. Real-time path planning with limited in formation for autonomous unmanned air vehicles. Automatica 2008, 44, 696–712. [Google Scholar] [CrossRef]
- Dai, R.; Cocharan, J. Path planning and state estimation for unmanned aerial vehicles in hostile environment. AIAA J. Guid. Control Dyn. 2010, 33, 595–601. [Google Scholar] [CrossRef]
- Hao, S.; Cheng, S.; Zhang, Y. A multi-aircraft conflict detection and resolution method for 4-dimensional trajectory-based operation. Chin. J. Aeronaut. 2018, 31, 1579–1593. [Google Scholar] [CrossRef]
- Yang, J.; Yin, D.; Shen, L.; Cheng, Q.; Xie, X. Cooperative Deconflicting Heading Maneuvers Applied to Unmanned Aerial Vehicles in Non-Segregated Airspace. J. Intell. Robot. Syst. 2018, 92, 187–201. [Google Scholar] [CrossRef]
- Yang, J.; Yin, D.; Niu, Y.; Shen, L. Distributed Cooperative Onboard Planning for the Conflict Resolution of Unmanned Aerial Vehicles. J. Guid. Control Dyn. 2019, 42, 272–283. [Google Scholar] [CrossRef]
- Radanovic, M.; Eroles, M.A.; Koca, T.; Gonzalez, J.J. Surrounding traffic complexity analysis for efficient and stable conflict resolution. Transp. Res. Part C Emerg. Technol. 2018, 95, 105–124. [Google Scholar] [CrossRef]
- Wu, J.; Tan, S.Y.; Liu, Z. Enhancing structural robustness of scale-free networks by information disturbance. Sci. Rep. 2017, 7, 7559. [Google Scholar] [CrossRef]
- Lu, L.; Chen, D.; Ren, X.L. Vital nodes identification in complex networks. Phys. Rep. 2016, 650, 1–63. [Google Scholar] [CrossRef]
- Morone, F.; Makse, H.A. Influence maximization in complex networks through optimal percolation. Nature 2015, 524, 65–68. [Google Scholar] [CrossRef]
- Ding, J.; Wen, C.; Li, G. Key node selection in minimum-cost control of complex networks. Phys. A Stat. Mech. Appl. 2017, 486, 251–261. [Google Scholar] [CrossRef]
- Tan, Y.J.; Wu, J. Network structure entropy and its application in unscaled networks. Syst. Eng. Theory Pract. 2004, 24, 1–3. [Google Scholar]
- Tang, Y.J.; Wu, J.; Deng, H.Z. Node contraction method for node importance evaluation in complex networks. Syst. Eng. Theory Pract. 2006, 26, 79–83. [Google Scholar]
- Brooker, P. Airborne collision avoidance systems and air traffic management safety. J. Navig. 2005, 58, 1–16. [Google Scholar] [CrossRef]
- Wu, J.; Deng, H.Z.; Tan, Y.J. Spectral Measure of Robustness for Internet Topology. In Proceedings of the IEEE International Conference on Computer Science, Chengdu, China, 9–11 July 2010; pp. 50–54. [Google Scholar]
- Archibald, J.K.; Hill, J.C.; Jepsen, N.A. A Satisficing Approach to Aircraft Conflict Resolution. IEEE Trans. Syst. Man Cybern. Part C 2008, 38, 510–521. [Google Scholar] [CrossRef]
- George, J.; Ghose, D. A reactive inverse PN algorithm for collision avoidance among multiple unmanned aerial vehicles. In Proceedings of the Conference on American Control Conference, St. Louis, MO, USA, 10–12 June 2009; pp. 3890–3895. [Google Scholar]
- Tang, J.; Fan, L.J.; Lao, S.Y. Collision Avoidance for Multi-UAV Based on Geometric Optimization Model in 3D Airspace. Arab. J. Sci. Eng. 2014, 39, 8409–8416. [Google Scholar] [CrossRef]


| Publication | Dimension | Maneuvers | Multiple | Resolution | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 3D | T/V/S/C | Pairwise | Global | Geometric Algorithm | Path Planning Algorithm | |||||
| CPA | CCA | Sampling-Based Path Planning Approaches | Artificial Heuristic Approaches | Numerical Optimization Approaches | Decoupled Path Planning Approaches | |||||
| Park, Oh, and Tahk (2008) | X | C(T,S) | X | X | ||||||
| Chakravarthy, Animesh, and Ghose (2012) | X | C(T,V,S) | X | X | ||||||
| Lin and Saripalli (2017) | X | C(T,V) | X | X | ||||||
| Pehlivanoglu (2012) | X | C(T,V) | X | X | ||||||
| Karimi and Pourtakdoust (2013) | X | C(T,V) | X | X | ||||||
| Xu, Duan and Liu (2010) | C(T,V) | X | X | |||||||
| Campbell, Bragg and Neogi (2013) | X | C(T,V) | X | X | ||||||
| Tisdale, Kim and Hedrick (2009) | V | X | X | |||||||
| Jorris and Cobb (2008) | C(V,S) | X | X | |||||||
| Grancharova et al. (2014) | X | C(T,V,S) | X | X | ||||||
| Sridhar, Ng and Chen (2011) | V | X | X | |||||||
| Kim, Gu and Postlethwaite (2008) | X | V | X | X | ||||||
| Dai and Cocharan (2010) | V | X | X | |||||||
| Hao, Cheng and Zhang (2018) | X | X | ||||||||
| Yang, Yin and Shen. (2018) | X | X | X | |||||||
| Yang et al. (2019) | X | X | ||||||||
| Radanovic et al. (2018) | X | X | X | |||||||
| Scenario 1 | Scenario 2 | |||||||
|---|---|---|---|---|---|---|---|---|
| Time | ID | Amended Trajectory | ID | Amended Trajectory | ||||
| X(m) | Y(m) | Z(m) | X(m) | Y(m) | Z(m) | |||
| 18:15:19 | UAV1 | 876.27 | 6123.72 | 695.67 | UAV9 | 1762.27 | 5756.46 | 688.52 |
| 18:15:23 | UAV1 | 904.54 | 6095.45 | 695.53 | UAV9 | 1722.34 | 5754.09 | 688.48 |
| 18:15:27 | UAV1 | 919.23 | 6080.77 | 692.11 | UAV9 | 1695.73 | 5752.51 | 685.49 |
| 18:15:31 | UAV1 | 933.91 | 6066.08 | 688.69 | UAV9 | 1669.11 | 5750.93 | 682.51 |
| 18:15:35 | UAV1 | 948.60 | 6051.40 | 685.27 | UAV9 | 1642.50 | 5749.35 | 679.53 |
| 18:15:39 | UAV1 | 963.28 | 6036.71 | 681.85 | UAV9 | 1615.89 | 5747.76 | 676.55 |
| 18:15:43 | UAV1 | 977.97 | 6022.03 | 678.43 | UAV9 | 1589.28 | 5746.18 | 673.57 |
| 18:15:47 | UAV1 | 992.65 | 6007.34 | 675.02 | UAV9 | 1562.66 | 5744.60 | 670.58 |
| UAV9 | 1482.76 | 5739.86 | 688.48 | UAV1 | 1074.25 | 5925.74 | 695.53 | |
| 18:15:51 | UAV1 | 1007.33 | 5992.66 | 671.60 | UAV9 | 1536.05 | 5743.02 | 667.60 |
| UAV9 | 1442.83 | 5737.48 | 688.48 | UAV1 | 1102.53 | 5897.46 | 695.53 | |
| 18:15:55 | UAV1 | 1022.02 | 5977.97 | 668.18 | UAV9 | 1509.44 | 5741.44 | 664.62 |
| UAV9 | 1402.90 | 5735.11 | 688.48 | UAV1 | 1130.81 | 5869.18 | 695.53 | |
| 18:15:59 | UAV1 | 1036.70 | 5963.29 | 664.76 | UAV9 | 1482.83 | 5739.86 | 661.64 |
| UAV9 | 1362.97 | 5732.74 | 688.48 | UAV1 | 1159.10 | 5840.89 | 695.53 | |
| 18:16:03 | UAV1 | 1051.39 | 5948.60 | 661.34 | UAV9 | 1456.21 | 5738.28 | 658.66 |
| UAV9 | 1323.04 | 5730.37 | 688.48 | UAV1 | 1187.38 | 5812.61 | 695.53 | |
| 18:16:07 | UAV1 | 1066.07 | 5933.92 | 657.92 | UAV9 | 1429.60 | 5736.70 | 655.67 |
| UAV9 | 1283.11 | 5727.99 | 688.48 | UAV1 | 1215.67 | 5784.32 | 695.53 | |
| 18:16:11 | UAV1 | 1080.76 | 5919.23 | 654.50 | UAV9 | 1402.99 | 5735.12 | 652.69 |
| UAV9 | 1243.18 | 5725.62 | 688.46 | UAV1 | 1243.95 | 5756.04 | 695.53 | |
| 18:16:15 | UAV1 | 1105.63 | 5894.36 | 653.54 | UAV9 | 1366.39 | 5732.94 | 651.91 |
| UAV9 | 1203.25 | 5723.25 | 688.48 | UAV1 | 1272.24 | 5727.75 | 695.53 | |
| 18:16:19 | UAV1 | 1133.90 | 5866.09 | 653.43 | UAV9 | 1326.46 | 5730.57 | 651.86 |
| 18:16:23 | UAV1 | 1162.16 | 5837.83 | 653.27 | UAV9 | 1286.54 | 5728.20 | 651.82 |
| 18:16:27 | UAV1 | 1190.43 | 5809.56 | 653.13 | UAV9 | 1246.61 | 5725.83 | 651.77 |
| 18:16:31 | UAV1 | 1218.70 | 5781.29 | 652.99 | UAV9 | 1206.68 | 5723.45 | 651.72 |
| 18:16:35 | UAV1 | 1233.38 | 5766.61 | 656.41 | UAV9 | 1180.07 | 5721.87 | 654.70 |
| 18:16:39 | UAV1 | 1248.07 | 5751.92 | 659.82 | UAV9 | 1153.46 | 5720.29 | 657.68 |
| 18:16:43 | UAV1 | 1262.75 | 5737.24 | 663.24 | UAV9 | 1126.84 | 5718.71 | 660.67 |
| 18:16:47 | UAV1 | 1277.44 | 5722.55 | 666.66 | UAV9 | 1100.23 | 5717.13 | 663.65 |
| 18:16:51 | UAV1 | 1292.12 | 5707.87 | 670.08 | UAV9 | 1073.62 | 5715.55 | 666.63 |
| 18:16:55 | UAV1 | 1306.81 | 5693.18 | 673.50 | UAV9 | 1047.01 | 5713.97 | 669.61 |
| 18:16:59 | UAV1 | 1321.49 | 5678.50 | 676.92 | UAV9 | 1020.39 | 5712.39 | 672.59 |
| 18:17:03 | UAV1 | 1336.18 | 5663.81 | 680.34 | UAV9 | 993.78 | 5710.80 | 675.58 |
| 18:17:07 | UAV1 | 1350.86 | 5649.13 | 683.75 | UAV9 | 967.17 | 5709.22 | 678.56 |
| 18:17:11 | UAV1 | 1365.55 | 5634.44 | 687.17 | UAV9 | 940.56 | 5707.64 | 681.54 |
| 18:17:15 | UAV1 | 1380.23 | 5619.76 | 690.59 | UAV9 | 913.94 | 5706.06 | 684.52 |
| 18:17:19 | UAV1 | 1394.92 | 5605.07 | 694.01 | UAV9 | 887.33 | 5704.48 | 687.50 |
| 18:17:23 | UAV1 | 1416.39 | 5583.60 | 695.65 | UAV9 | 850.73 | 5702.31 | 688.21 |
| Key Node Selecting Approach | |
|---|---|
| Node selection based on degree | 0.0126 |
| Node contraction method | 0.0093 |
| Number of Aircrafts | Time Taken (s) | ||||
|---|---|---|---|---|---|
| SGTA | RIPNA | GOM | Complex Network Based on Degree | Complex Network Based on Node Contraction | |
| 20 | 673 | 68 | 27 | 3 | 3 |
| 40 | 1711 | 200 | 68 | 9 | 10 |
| 60 | 3009 | 396 | 189 | 20 | 26 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, Y.; Tang, J.; Lao, S. Cooperative Multi-UAV Collision Avoidance Based on a Complex Network. Appl. Sci. 2019, 9, 3943. https://doi.org/10.3390/app9193943
Huang Y, Tang J, Lao S. Cooperative Multi-UAV Collision Avoidance Based on a Complex Network. Applied Sciences. 2019; 9(19):3943. https://doi.org/10.3390/app9193943
Chicago/Turabian StyleHuang, Yang, Jun Tang, and Songyang Lao. 2019. "Cooperative Multi-UAV Collision Avoidance Based on a Complex Network" Applied Sciences 9, no. 19: 3943. https://doi.org/10.3390/app9193943
APA StyleHuang, Y., Tang, J., & Lao, S. (2019). Cooperative Multi-UAV Collision Avoidance Based on a Complex Network. Applied Sciences, 9(19), 3943. https://doi.org/10.3390/app9193943




