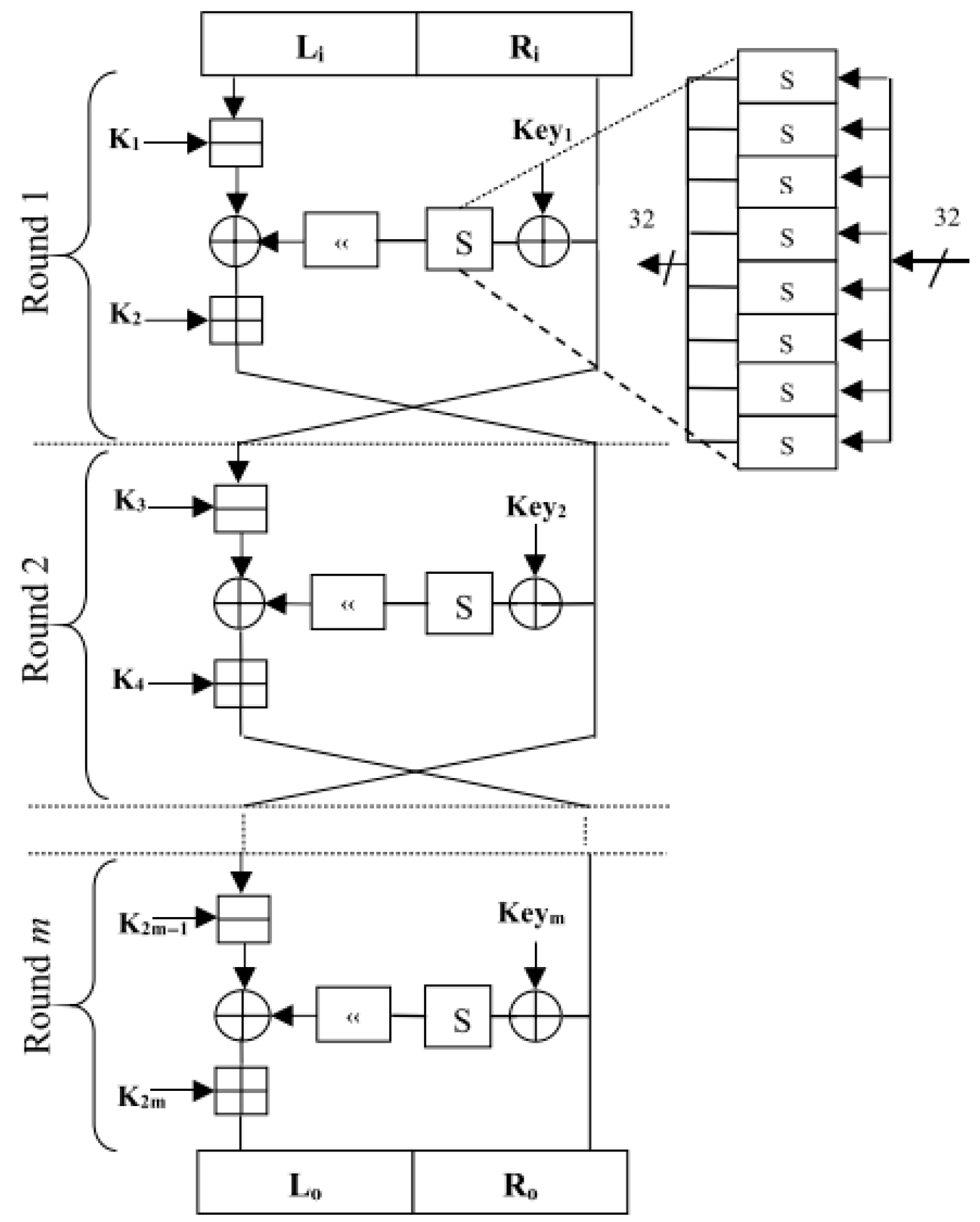
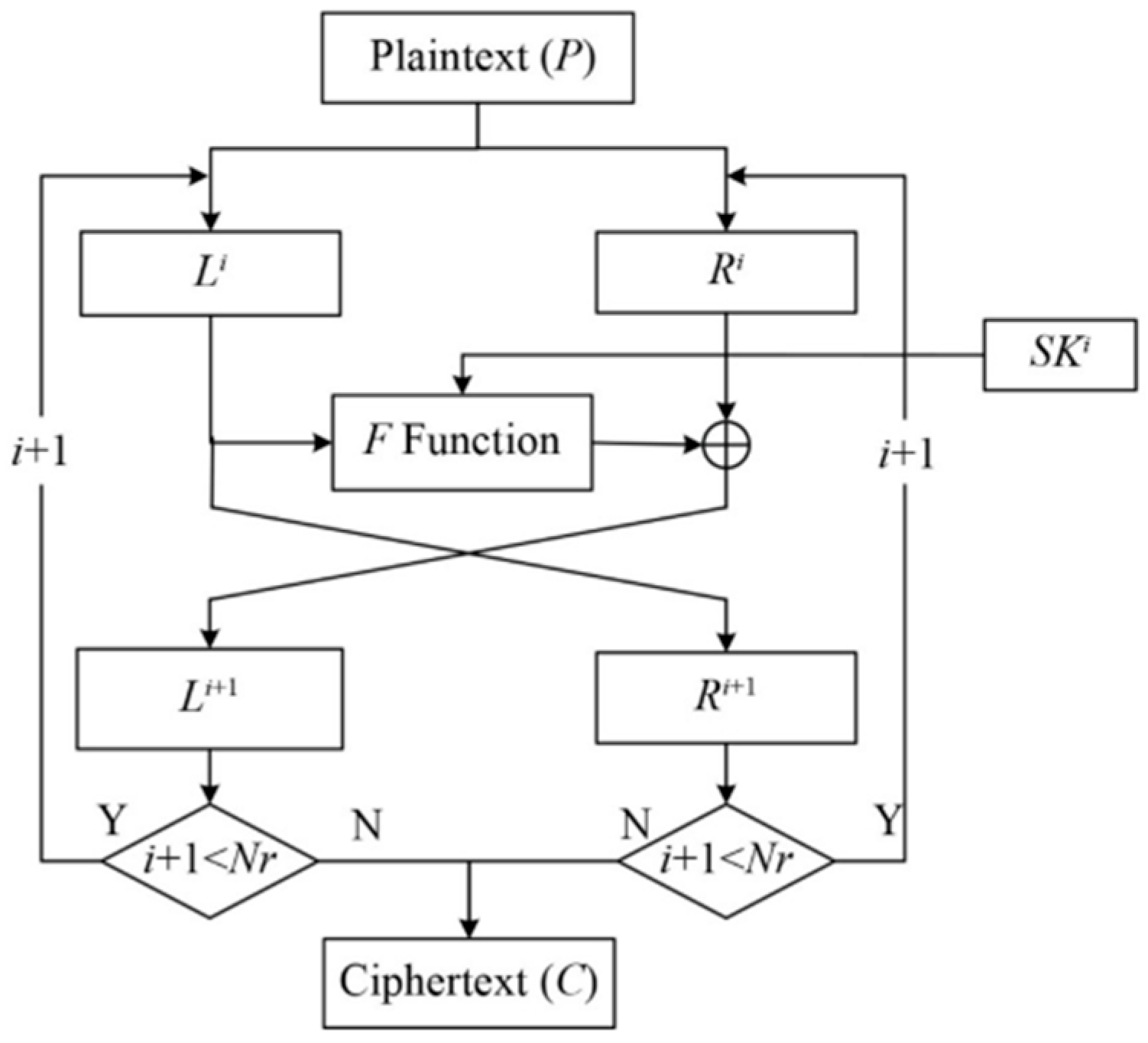
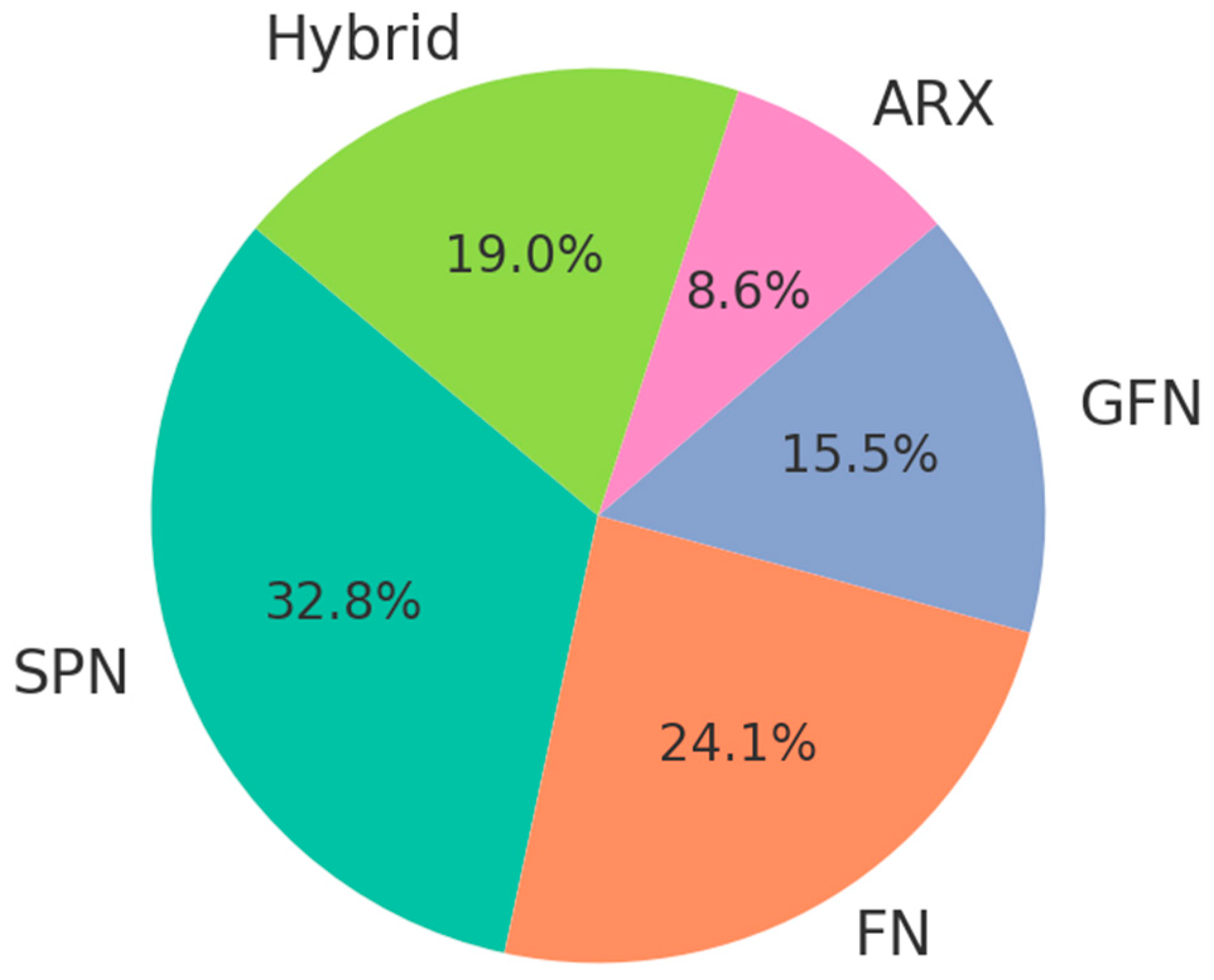
4.1. Substitution-Permutation Network (SPN)
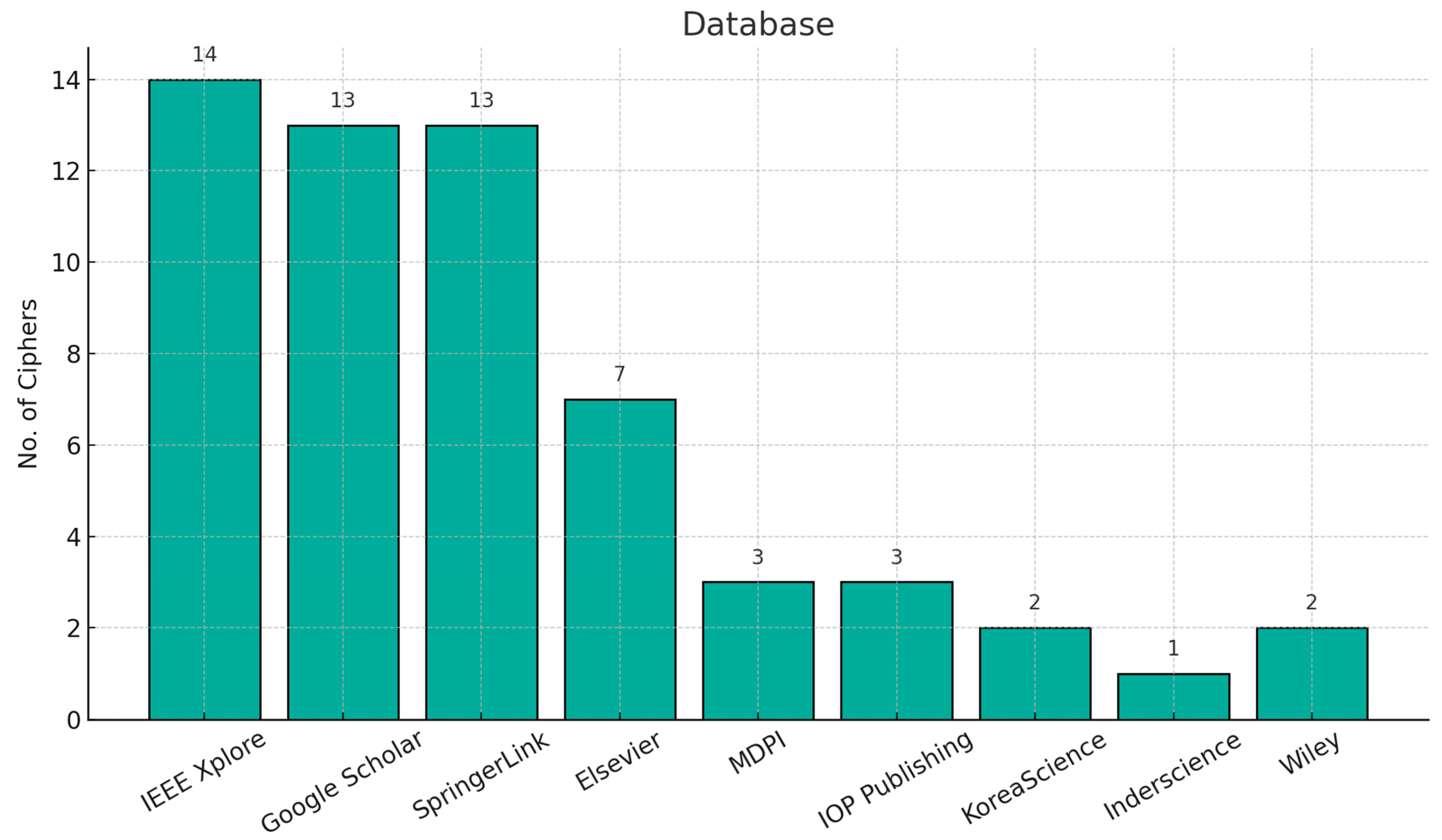
The NVLC [
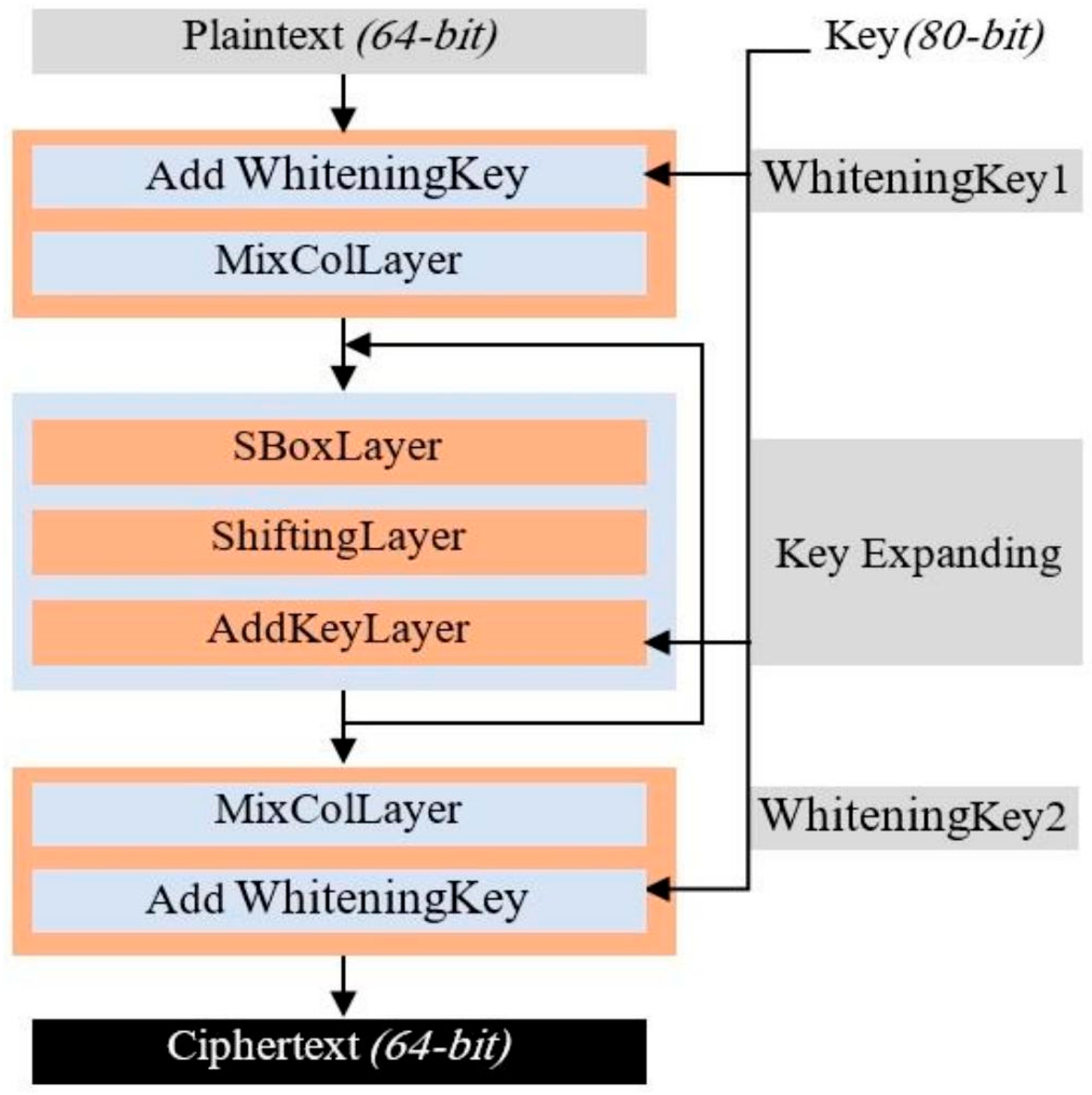
11] (New Variant Lightweight Cryptographic Algorithm) is a symmetric block cipher specifically designed for IoTs applications with constrained resources. It operates on 64-bit blocks with key sizes of either 80 bits or 128 bits. The cipher utilizes six rounds for basic security, although twenty rounds are implemented to increase encryption complexity. The NVLC algorithm incorporates a substitution-permutation network (SPN) structure, combining mathematical and logical operations for efficiency in IoTs environments. The algorithm’s key features include whitening, a mix-column layer, a 4-bit S-box, a key schedule derived from the PRESENT algorithm, and a shifting layer for diffusion as presented in
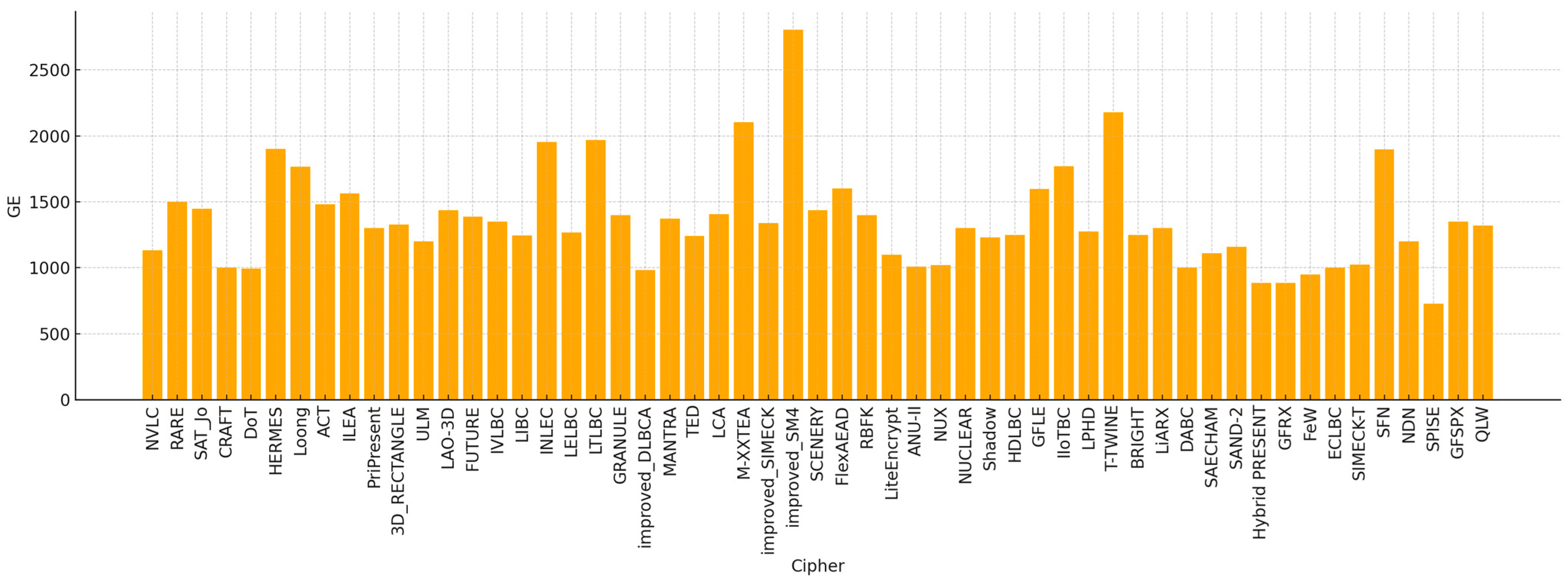
Figure 4. Security evaluations show that NVLC is resilient against various cryptographic attacks, including differential and linear attacks, while achieving a low hardware cost of just 1134 gate equivalents (GEs). This makes it a highly efficient choice for low-cost IoTs applications such as RFID tags and sensors, ensuring both security and performance with minimal resource consumption.
The NVLC algorithm, while optimized for IoTs security, has several limitations. Its increased computational complexity due to 20 encryption rounds may impact processing efficiency in low-power devices. Although designed as a lightweight cipher, its power consumption of 1.83 μW at 100 kHz could still be significant for ultra-low-power IoTs applications. The use of S-Boxes and key expansion may pose memory constraints for devices with limited storage. Additionally, while it claims resistance to attacks, further cryptanalysis is needed to validate its security against advanced cryptographic threats. Lastly, its implementation complexity may make integration into existing IoTs systems more challenging.
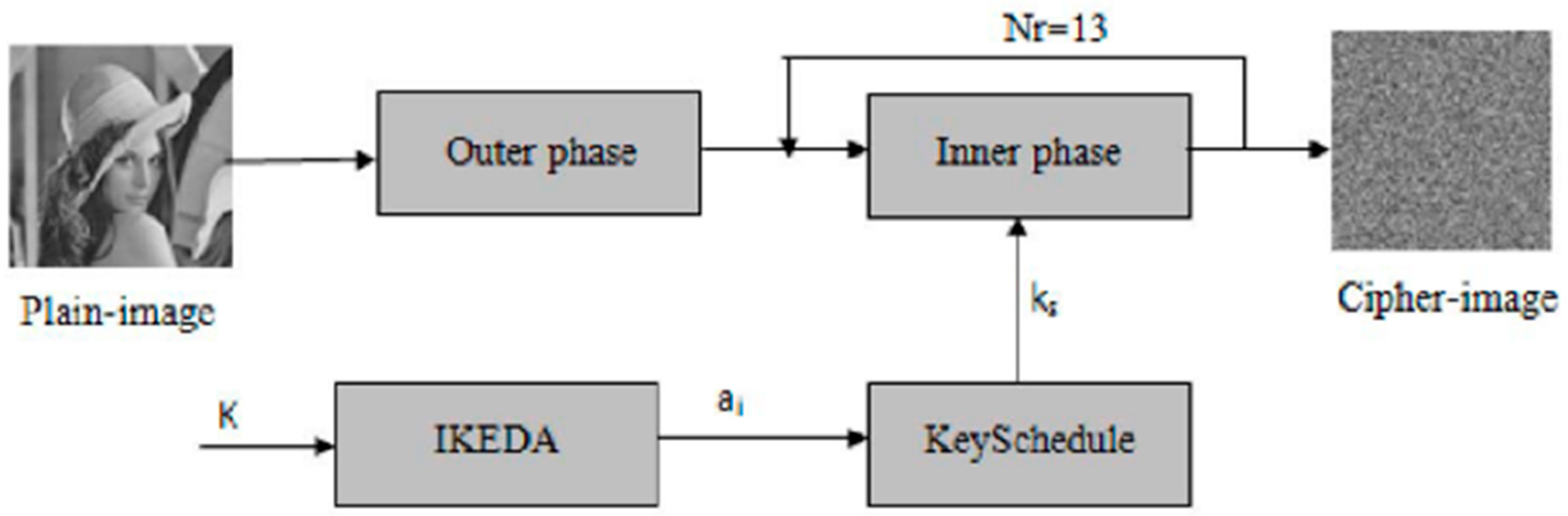
RARE [
12] (Robust Algorithm for Rapid Encryption) is a lightweight cryptosystem designed specifically for image encryption in IoTs applications. The cipher targets the challenges presented by image data, such as high redundancy, correlation, and voluminosity, which can undermine the security of traditional lightweight ciphers. RARE uses an innovative “Outer-Inner” structure, as shown in
Figure 5, where the outer phase applies horizontal and vertical diffusion to reduce image redundancy and correlation, while the inner phase divides the image into sub-blocks and processes them using a block cipher in ECB mode. The system ensures high diffusion and confusion properties, essential for secure image encryption. RARE outperforms existing lightweight ciphers in terms of correlation reduction, entropy increase, and enhanced diffusion. It also shows improved resistance to differential and linear cryptanalysis, demonstrating a lower number of rounds required for secure encryption. Furthermore, RARE is faster and more efficient compared to other ciphers such as PRESENT and RoadRunner, making it highly suitable for IoTs applications that require both security and real-time processing.
The RARE algorithm’s limitations include high computational complexity due to its outer-inner structure, requiring at least 9 rounds for linear cryptanalysis resistance and 13 rounds for differential attacks. Its encryption and decryption speeds are slower than some existing lightweight ciphers, impacting real-time IoTs applications. The chaotic Ikeda-based key scheduling enhances security but adds implementation complexity. While optimized for image encryption, its efficiency for securing text and binary data in IoTs remains uncertain.
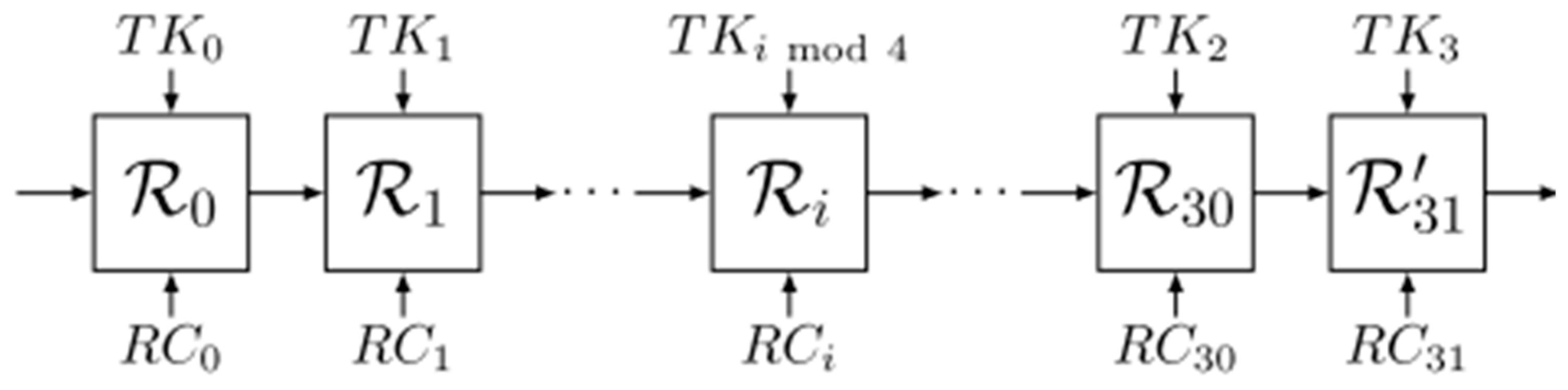
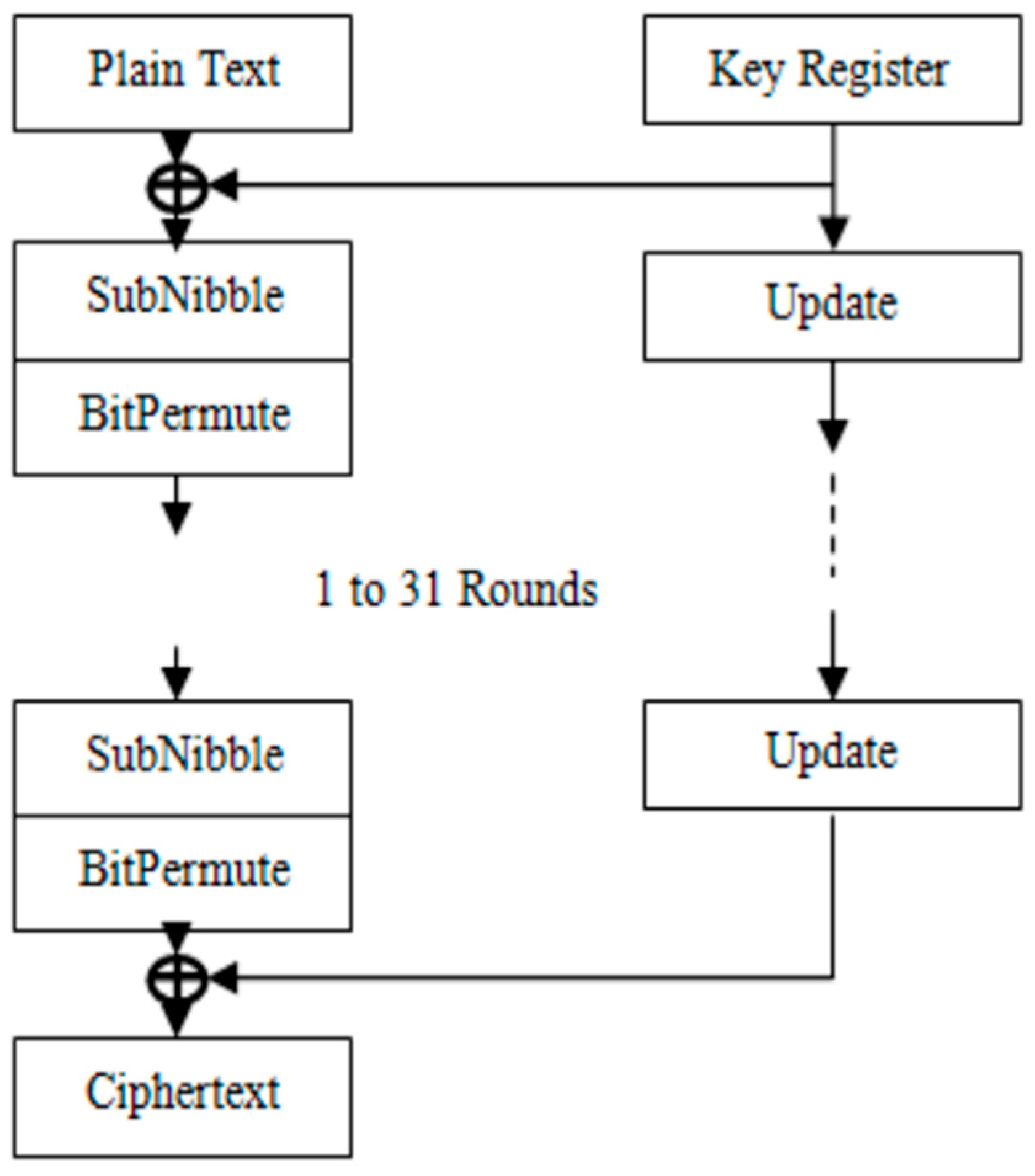
The SAT_Jo [
13] block cipher is designed for secure data encryption in IoTs environments, particularly for tag-based applications with resource-constrained devices. Built on a substitution-permutation network (SPN) structure, SAT_Jo employs a 64-bit block size and 80-bit key, performing 31 rounds of encryption as illustrated in
Figure 6. It features a 4 × 4 S-box derived from the Galois Field (GF(2
4)), providing non-linear transformations to strengthen security. A permutation layer, characterized by bijective mappings, ensures additional diffusion. The cipher uses a novel key scheduling technique based on Fibonacci sequences and includes a post-whitening step to enhance the final output. SAT_Jo is specifically optimized to balance security and efficiency, offering adequate protection against common cryptographic attacks while maintaining low resource usage, making it ideal for IoTs applications where computational power and memory are limited.
The SAT_Jo algorithm has limitations, including high computational overhead due to its 31 encryption rounds, making it resource-intensive. Its energy consumption may be a concern for ultra-low-power IoTs devices, and its memory requirements for the S-Box and key scheduling could challenge constrained systems. While it enhances security with an SPN structure and key whitening, further cryptanalysis is needed to confirm its resistance to advanced attacks. Additionally, its design is mainly suited for tag-based encryption, limiting its broader applicability in IoTs security.
CRAFT [
14] is a lightweight, tweakable block cipher designed with a strong focus on providing efficient protection against Differential Fault Analysis (DFA) attacks. It features a 64-bit block size, 128-bit key, and supports a 64-bit tweak for added security. The cipher utilizes involutory building blocks for encryption and decryption, allowing the same structure for both with minimal area overhead. CRAFT’s design incorporates a mix of substitution, permutation, and key-dependent tweaks across 31 rounds as presented in
Figure 7, with an additional linear round for extra security. The cipher’s main strength lies in its efficient fault-detection capabilities, achieved by integrating error detection codes (EDCs) directly into the cipher structure. Security analysis confirms that CRAFT is resistant to various cryptanalytic attacks, including differential and linear cryptanalysis, and achieves robust fault protection with low implementation costs. It outperforms other lightweight ciphers in terms of area efficiency, making it an ideal candidate for use in resource-constrained environments such as IoTs applications.
The CRAFT algorithm has limitations, including higher computational complexity and increased hardware overhead due to fault detection mechanisms, making it less efficient for ultra-constrained IoTs devices. It remains vulnerable to certain fault attacks such as Ineffective Fault Attacks (IFAs) and Fault Sensitivity Analysis (FSA), requiring additional countermeasures. Its encryption and decryption speed may be slower than other lightweight ciphers, and its tweakable design adds implementation complexity, making integration into existing systems more challenging.
The DoT [
15] cipher is a highly efficient, ultra-LWBC designed for resource-constrained environments such as IoTs and WSN. It uses a 64-bit block size and supports both 80-bit and 128-bit keys. The cipher operates using a substitution-permutation (SP) network and employs a simple but effective design with a single S-box, bit permutations, block shuffling, and circular shifting to enhance security and performance, as demonstrated in
Figure 8. DoT requires only 993 gate equivalents (GEs) for hardware implementation and consumes only 2464 bytes of flash memory, making it highly compact. Its throughput of 53.77 Kbps outperforms many existing ciphers, and it offers strong resistance to linear, differential, and biclique attacks. The key scheduling mechanism is inspired by the PRESENT cipher, ensuring both efficiency and security. Overall, DoT’s design makes it an ideal candidate for low-power and memory-constrained applications, offering high encryption performance with minimal hardware and memory requirements.
The DoT algorithm has limitations, including the need for further validation against advanced cryptanalysis, a high number of rounds (31) that may impact execution speed, and potential inefficiency in ultra-low-power IoTs devices despite its low hardware footprint (993 GEs). Its complex key scheduling and reliance on bit permutation could make integration into existing frameworks challenging. Additionally, while it claims resistance to biclique attacks, its real-world security effectiveness remains uncertain.
HERMES [
16] is an LWBC designed to secure resource-constrained devices such as IoTs devices, microcontrollers, and RFID chips. It operates with 64-bit plaintext blocks and 128-bit keys, making it suitable for environments where memory, processing power, and energy are limited. Hermes features a simple yet effective structure using an 8 × 8 matrix of transformations, including bitwise operations and an S-box for non-linearity as depicted in
Figure 9. With 30 rounds of encryption, it strikes a balance between strong security and minimal resource requirements. The cipher is optimized for low-power consumption, small code size, and efficient memory use. Security analyses show that Hermes is resistant to common cryptographic attacks, including differential, linear, and other advanced attacks, while also providing high diffusion and confusion properties. Hermes’ efficiency in both hardware and software implementations makes it an ideal candidate for deployment in IoTs and similar applications where traditional cryptographic methods may be too resource-intensive.
The HERMES algorithm has limitations, including high computational complexity due to its 30-round structure, which may impact efficiency in low-power devices. Its memory and power consumption could be a concern for ultra-constrained environments, and further cryptanalysis is needed to confirm its resistance to advanced attacks. The key scheduling and substitution mechanisms add implementation complexity, making integration more challenging. Additionally, its real-world performance in terms of speed and execution efficiency remains unverified through practical hardware testing.
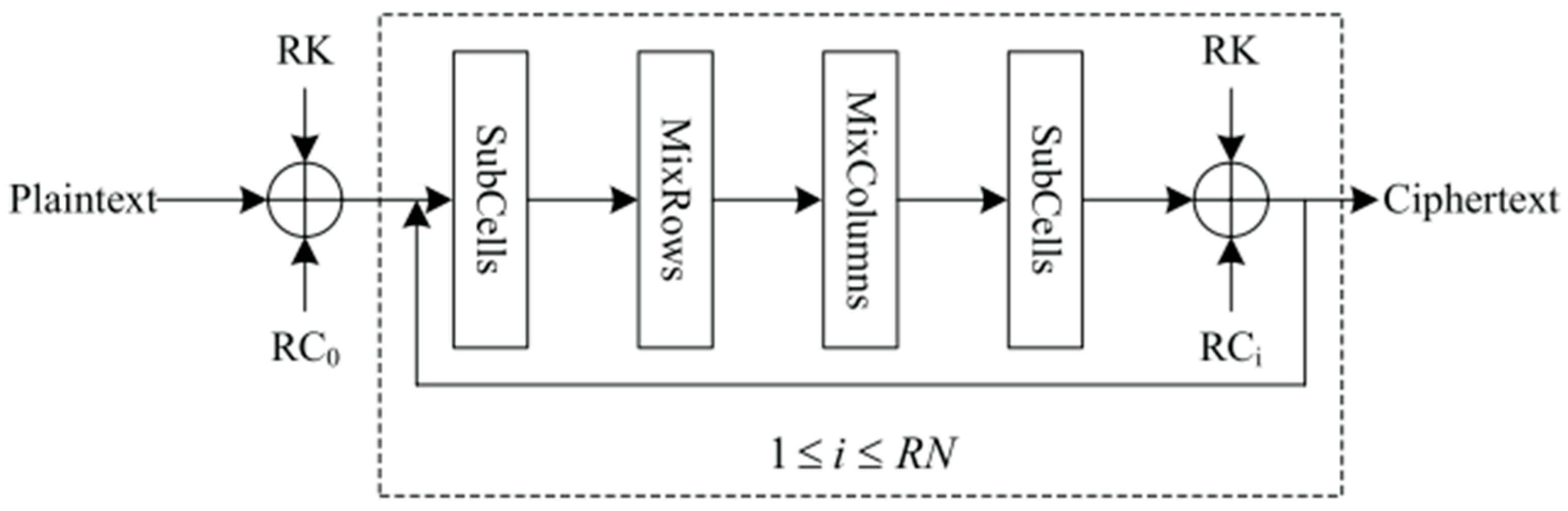
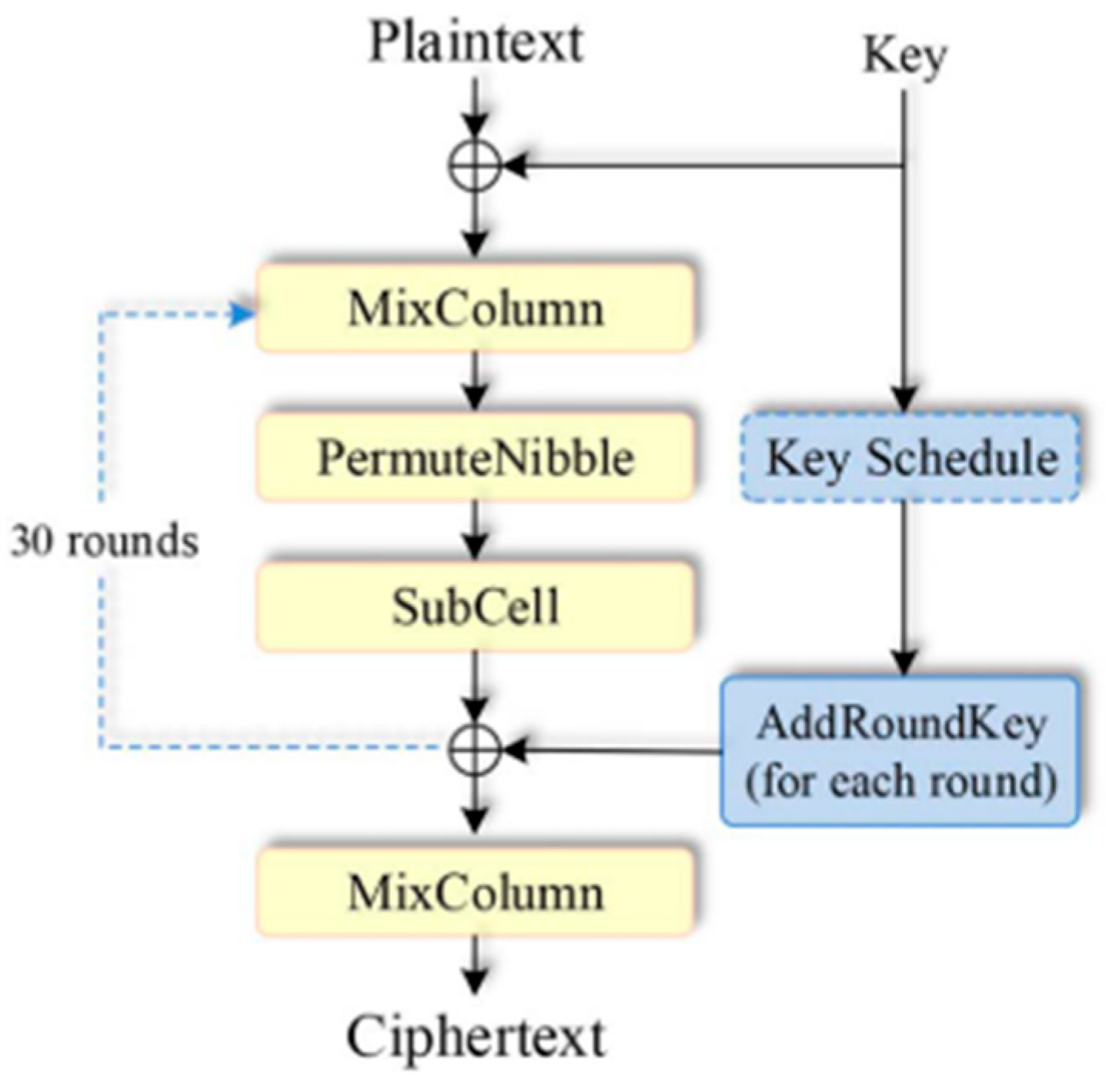
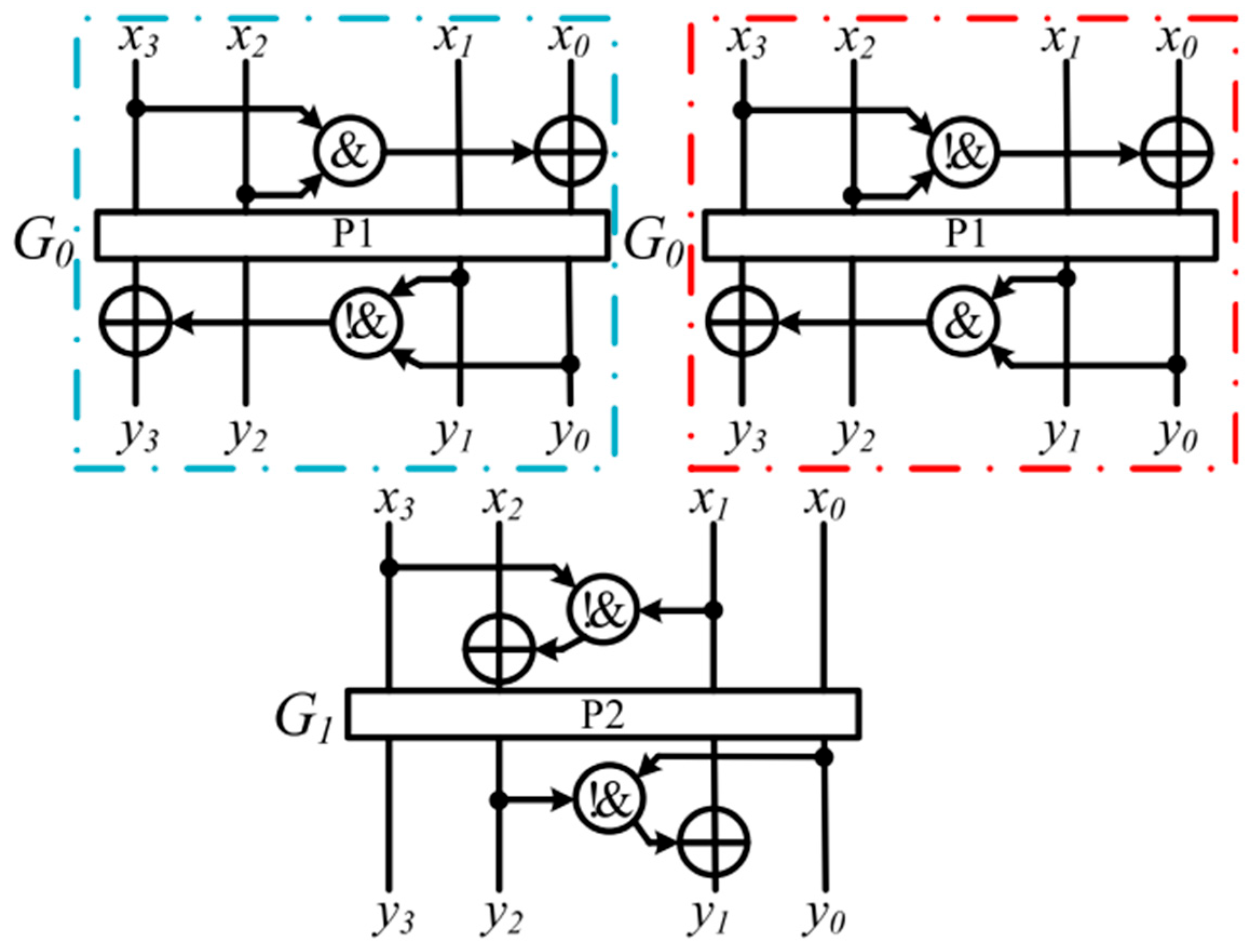
The Loong [
17] cipher is an involutional LWBC based on a novel SPN (substitution-permutation network) structure, designed for efficient use in IoTs devices with resource constraints. Unlike traditional SPN ciphers, Loong ensures that both the encryption and decryption processes are identical, allowing for the same hardware and software implementation for both operations, thus reducing the required resources. It uses a 64-bit block with key sizes of 64, 80, and 128 bits, supporting 16, 20, and 32 rounds, respectively. The round function in Loong, according to
Figure 10, includes AddRoundKey, SubCells (involving a 4-bit S-box), MixRows, and MixColumns, with involutional components that improve security and efficiency. Loong demonstrates strong resistance to differential and linear attacks, with high security derived from its unique round function and the use of a small, low latency S-box. The cipher’s hardware implementation is highly efficient, with area costs lower than comparable ciphers such as PRESENT, and its simplified decryption process contributes to resource savings. Loong is suitable for environments where low memory and fast execution are critical, such as in IoTs applications.
The Loong algorithm has limitations, including higher computational complexity due to dual SubCells operations per round and significant hardware overhead, with Loong-128 consuming 1766 GE, making it less ideal for ultra-low-power IoTs devices. Its matrix multiplications may introduce latency, and while it claims resistance to attacks, its security against emerging threats remains unverified. Additionally, its software implementation is relatively slower, affecting efficiency in speed-critical applications.
ACT [
18] is an ultra-LWBC designed for resource-constrained environments such as IoTs applications. It operates on 64-bit data blocks with an 80-bit key and features a substitution-permutation network (SPN) structure. ACT is designed to achieve low area and power consumption, with a gate count of just 1481 GEs and a dynamic power consumption of 30 mW. The cipher, as evidenced by
Figure 11, employs a 4-bit substitution box (S-box) that minimizes linear and differential cardinalities, providing strong resistance against cryptanalytic attacks such as differential, linear, and biclique attacks. With only three rounds for complete diffusion, ACT offers excellent security performance while maintaining efficiency. Its resistance to algebraic cryptanalysis is also highlighted, with a manageable number of inequalities for its S-box. ACT’s low resource requirements, along with its robust security properties, make it an ideal candidate for lightweight cryptographic applications in IoTs devices.
The ACT algorithm has limitations, including high computational complexity due to its 31-round structure, a gate equivalent count of 1481 that may require further optimization for ultra-low-power devices, and the need for additional cryptanalysis to confirm its resistance to emerging attacks. Its key scheduling adds implementation complexity, and its real-world efficiency in IoTs applications remains unverified, requiring further hardware testing.
The Improved Lightweight Encryption Algorithm (ILEA) [
19] enhances the PRINCE LWBC by adding two Balanced Block Mixing (BBM) layers, one at the input and another at the output, as observed in
Figure 12. This modification improves the diffusion of data, making the cipher more unpredictable and resistant to cryptanalysis. ILEA operates on a 64-bit block with a 128-bit key and is optimized for low-power, low latency applications, making it ideal for IoTs devices. The algorithm performs efficiently in both Python and C++ implementations, with ILEA in C++ showing a processing time of 1.6 μs per round. A comparative study with other lightweight block ciphers demonstrates ILEA’s superior performance in terms of encryption and decryption times. Additionally, ILEA offers enhanced security by increasing the effective key length to 256 bits, making it resistant to brute-force attacks. This makes ILEA suitable for environments requiring both speed and robust security in constrained devices.
The ILEA algorithm’s limitations include a 25% increase in encryption and decryption time, which may affect real-time performance in resource-constrained devices. Its higher computational cost makes it less suitable for ultra-low-power applications, and integration challenges arise due to the complexity of its BBM layers. Additionally, while it claims strong security, its resistance to advanced cryptanalysis remains unverified.
PriPresent [
20] is an LWBC designed for IoTs devices, focusing on providing security services such as confidentiality and integrity while ensuring low resource usage. The cipher, as indicated in
Figure 13, operates with a 64-bit block size and supports both 80-bit and 128-bit keys. It is based on a substitution-permutation network (SPN) and utilizes prime number positions for reordering text blocks before applying encryption. PriPresent ensures data integrity by generating signatures using SHA-256, which are then used to authenticate the sender and verify the message’s authenticity. The algorithm is resistant to common attacks such as replay, fabrication, and man-in-the-middle attacks. Performance tests demonstrate that PriPresent offers better throughput compared to the PRESENT cipher while maintaining similar encryption and decryption times, making it an efficient solution for secure communication in IoTs networks.
The PriPresent algorithm’s limitations include high computational complexity due to its 31-round structure and increased encryption and decryption time from prime number-based block ordering. Its use of SHA-256 for authentication adds computational overhead and memory usage, making it less suitable for ultra-low-power IoTs devices. Additionally, its security against emerging cryptographic attacks remains unverified, requiring further analysis.
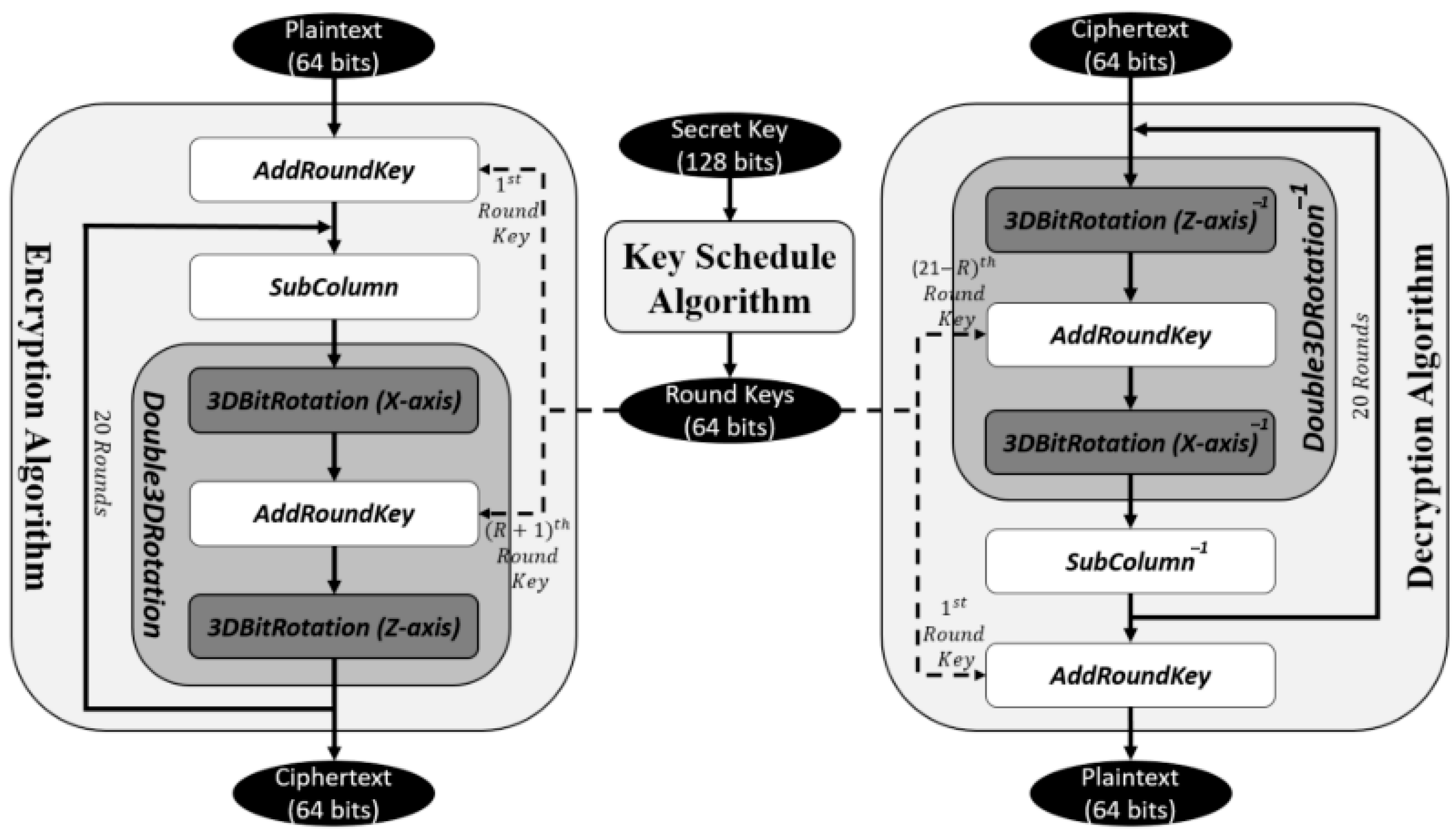
The 3D RECTANGLE [
21] cipher is an enhanced version of the RECTANGLE lightweight block cipher, designed to improve security without increasing block or key sizes. By incorporating a 3D bit rotation technique, it strengthens the cipher’s confusion and diffusion properties. The encryption process involves 4 operations reflected in
Figure 14: 3D bit rotation, AddRoundKey, SubColumn, and ShiftRow, significantly enhancing the algorithm’s resistance to cryptanalysis. Security analyses, including correlation coefficient, bit error, key sensitivity, and randomness tests, show substantial improvements in non-linearity, key sensitivity, and randomness, with the 3D RECTANGLE outperforming the original RECTANGLE cipher. Despite a slight performance trade-off due to the additional 3D bit rotation function, the 3D RECTANGLE maintains competitive encryption speeds and throughput, making it an efficient and secure option for IoTs devices that require lightweight encryption.
The 3D RECTANGLE algorithm’s limitations include higher encryption and decryption times due to added 3D bit rotation, slightly lower efficiency compared to the original RECTANGLE, and a trade-off between security and processing overhead. Additionally, further cryptanalysis is needed to confirm its resistance to emerging attacks.
The Ultra-Lightweight Method (ULM) [
22] is a cryptographic design approach proposed specifically for IoTs environments that require minimal memory usage, high efficiency, and strong security. ULM combines three lightweight cryptographic techniques, as represented in
Figure 15—Bitslice, Wide Trail Strategy (WTS), and involutive operations—to create a design framework that optimizes diffusion, confusion, and execution speed. It uses a 64-bit block size, an 80-bit key, and operates over 15 SPN-based rounds, each including subkey mixing, substitution using a 4 × 4 S-box, and an involutive bit permutation. This structure enables the implementation of block ciphers with low RAM and ROM consumption, fast processing time, and robust resistance to linear and differential attacks. A reference cryptosystem built using ULM demonstrates superior performance compared to existing lightweight methods, making ULM an effective foundation for secure encryption in constrained IoTs devices.
While ULM offers an efficient and compact approach for designing lightweight ciphers, it has some limitations. Its reliance on small 4 × 4 S-boxes and simplified logic operations may result in reduced non-linearity and potential vulnerability to advanced or future cryptanalytic methods. The method is primarily evaluated on 8-bit microcontrollers, which may limit its portability and optimization across more diverse or modern hardware architectures. Furthermore, while ULM shows resilience to linear and differential attacks, it lacks comprehensive evaluation against side-channel or algebraic attacks, which are critical for many IoTs applications.
LAO-3D [
23], or the 3D light algorithm operation, is a lightweight symmetric block cipher designed to enhance the security and efficiency of mobile encryption applications. It employs a 3D permutation structure, incorporating a 3D bit rotation function to strengthen the cipher’s confusion and diffusion properties without increasing block or key sizes, thus maintaining computational efficiency. The cipher operates on a 64-bit block size with a 128-bit key and features 20 rounds, as illustrated in
Figure 16. The encryption process includes key addition, non-linear S-box substitution, and a double 3D bit rotation for enhanced permutation. Security analysis demonstrates LAO-3D’s resistance to differential and linear cryptanalysis, achieving high non-linearity, a 50% bit error rate, and excellent randomness. Performance tests indicate that it has a competitive encryption speed and throughput compared to existing ciphers, making it ideal for mobile and IoTs applications requiring both strong security and efficiency. Additionally, the cipher was successfully implemented in a mobile encryption application, further proving its practical applicability.
The LAO-3D algorithm, despite its advantages in mobile encryption, has several limitations. The 3D permutation design adds computational complexity, which may increase encryption and decryption time, affecting real-time performance in resource-constrained environments. Although it achieves strong security, the trade-off between security and efficiency remains a concern, as stronger diffusion mechanisms can lead to processing overhead. Additionally, while LAO-3D resists differential and linear cryptanalysis, further security analysis is required to confirm its resilience against emerging cryptographic attacks. Finally, its hardware implementation and energy efficiency remain untested, requiring further evaluation for IoTs and ultra-low-power applications.
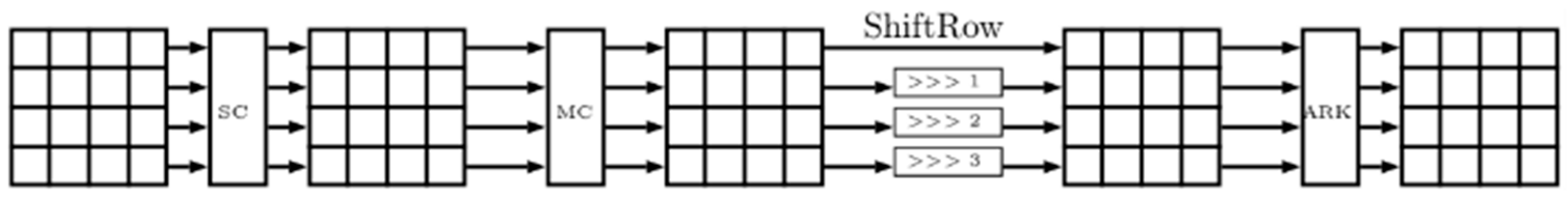
FUTURE [
24] is an LWBC tailored for resource-constrained IoTs devices, utilizing a substitution-permutation network (SPN) structure with 32 rounds. It supports a 64-bit block size and offers key lengths of 64, 96, or 128 bits, making it flexible for varying security requirements. Each encryption round of the FUTURE cipher comprises four sequential transformations: SubCells (SCs), MixColumns (MCs), ShiftRows (SRs), and AddRoundKey (ARK) (see illustration in
Figure 17), which together enhance diffusion and strengthen resistance against linear and differential attacks. The cipher is designed to achieve low memory usage, energy efficiency, and high execution speed, making it well-suited for embedded systems. Its structure and operations are kept simple to reduce computational complexity and facilitate implementation on low-power hardware, providing an effective balance between performance and basic security.
Despite its efficiency, FUTURE has several limitations. It lacks comprehensive cryptanalytic evaluation, such as resistance to differential, linear, or side-channel attacks, which raises concerns about its robustness. The algorithm’s focus on lightweight performance may result in a reduced security margin, particularly in scenarios requiring long-term data protection. Additionally, the key scheduling mechanism is not thoroughly analyzed, potentially exposing it to key-related vulnerabilities.
IVLBC [
25] (Involutive Lightweight Block Cipher) is a compact, energy-efficient block cipher tailored for resource-constrained IoTs devices. It operates on a 64-bit block size with either 64- or 128-bit keys and leverages an involutive design, meaning encryption and decryption use the same structure, reducing hardware complexity. The cipher as depicted in
Figure 18 consists of multiple rounds (64 or 76 depending on key size), each applying a bitwise XOR with the round key, a 4-bit involutive S-box, and a bit permutation layer to ensure confusion and diffusion. Its lightweight key schedule uses a Linear Feedback Shift Register (LFSR) mechanism. By using minimal logic and avoiding complex operations, IVLBC achieves a strong balance between security and implementation efficiency, making it ideal for secure communication in embedded and IoTs systems.
Despite its efficient design, IVLBC has several limitations. Its use of a single small 4-bit S-box, though beneficial for low-cost hardware, may offer lower non-linearity and reduced resistance to algebraic attacks compared to larger or more complex S-boxes. Additionally, its security margin is relatively tight, especially in the 64-bit key variant, which could become vulnerable as cryptanalytic techniques evolve. The bit permutation layer, while simple and hardware-friendly, may not provide the strongest diffusion compared to more advanced methods. Finally, the algorithm is highly hardware-centric, meaning its performance and suitability in software-based or hybrid environments may be limited. These factors suggest that while IVLBC is well-suited for current low resource IoTs systems, its long-term cryptographic strength and adaptability may be constrained.
LIBC [
26] is an LWBC designed to provide efficient cryptographic protection for IoTs devices with limited computational resources. It features a 64-bit block size and 128-bit keys, utilizing a 4-round structure to generate optimized 4-bit S-boxes. The cipher employs an almost MDS (Maximum Distance Separable) matrix for diffusion and optimal involutive nibble-based permutations, as demonstrated by
Figure 19, ensuring full diffusion within minimal rounds while maintaining high security against differential and linear cryptanalysis. The cipher is highly efficient in hardware, requiring only 10.05 gate equivalents (GEs) per bit per round, making it one of the most cost-effective options compared to other lightweight block ciphers such as PRESENT, RECTANGLE, and Midori. The decryption process is nearly identical to encryption, simplifying hardware implementation. Security tests show that LIBC provides robust protection against a variety of cryptographic attacks, including related-key and impossible differential cryptanalysis, with low hardware and energy consumption, making it ideal for resource-constrained IoTs environments.
Despite its efficiency, LIBC has some limitations. Its reliance on 4-bit S-boxes, while beneficial for low-cost hardware implementation, offers weaker cryptographic properties compared to 8-bit S-boxes, potentially making it more susceptible to future attacks. Additionally, its design is heavily optimized for hardware, which may reduce its performance or adaptability in software-based environments. The algorithm also achieves full diffusion in 4 rounds, but with only 31 rounds in total, the security margin—the difference between the number of secure rounds and total rounds—is relatively tight, leaving less room for futureproofing against more advanced cryptanalysis techniques. These factors could limit LIBC’s suitability for applications requiring long-term or high-assurance cryptographic security.
LELBC [
27] is a low energy LWBC designed for IoTs devices in smart agriculture, ensuring secure data transmission while minimizing energy consumption. It has designed a PSP structure as presented in
Figure 20 based on the SPN structure, with highly consistent encryption and decryption, making it ideal for resource-constrained environments. The cipher features a 4-bit involutive S-box generated using a genetic algorithm, reducing energy consumption and latency. Experimental results demonstrate that LELBC reduces energy and area consumption by 24% compared to similar ciphers such as Midori. It also shows robust resistance to differential, linear, and algebraic attacks, making it highly suitable for securing sensor data in smart agriculture applications.
A limitation of LELBC is that, despite its energy efficiency, its reliance on the 4-bit S-box and relatively simplistic structure may not provide the highest level of security in more demanding cryptographic applications. The reduced number of rounds and the simplicity of the diffusion layers could make the cipher more vulnerable to future, more advanced cryptanalysis techniques. Additionally, although LELBC excels in energy and area efficiency, its low complexity might limit its scalability or adaptability to environments that require a higher level of security or more complex cryptographic operations.
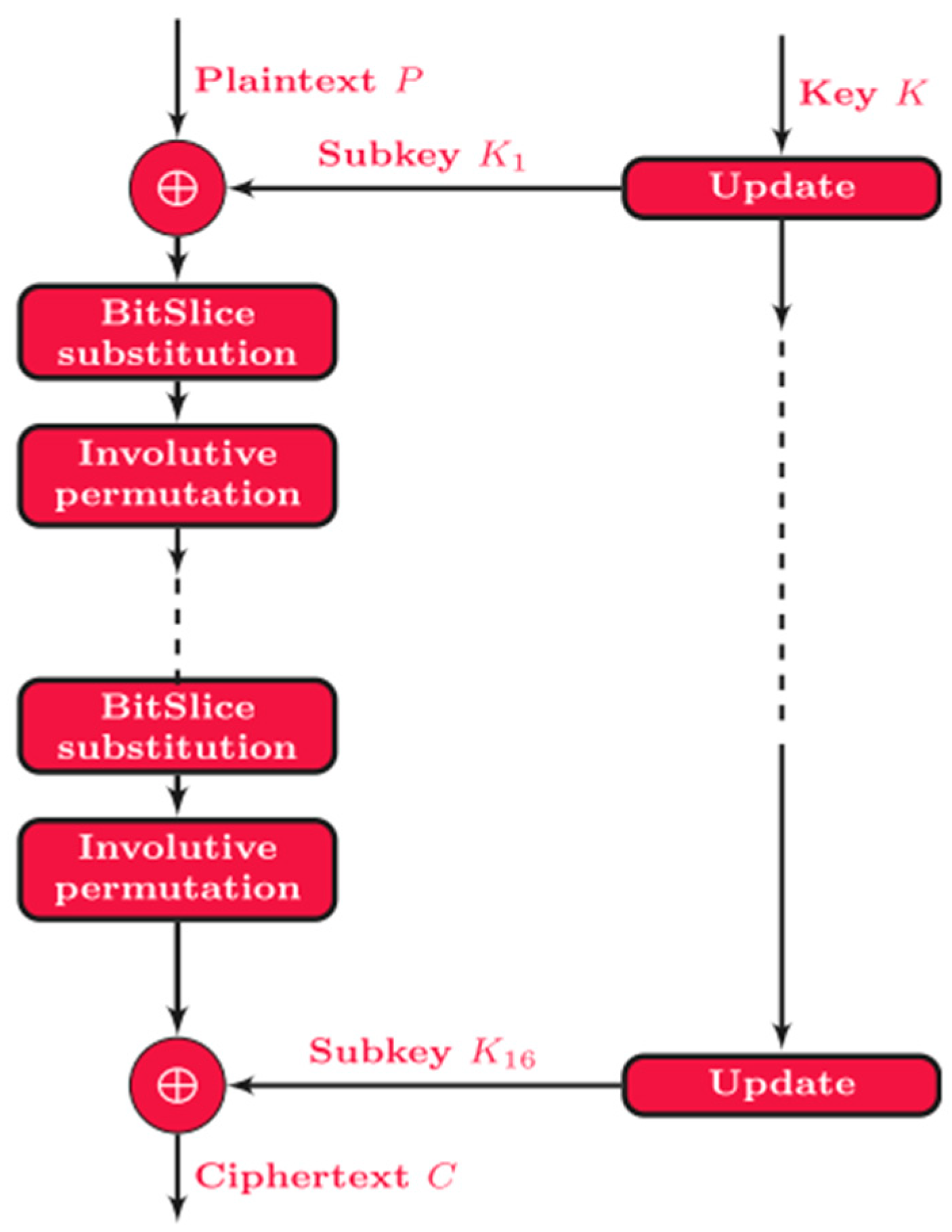
INLEC [
28] is an LWBC designed specifically for energy-constrained IoTs devices, based on a fully involutive substitution-permutation network (SPN) structure. It operates on a 64-bit block size with a 128-bit key over 15 rounds, using two symmetric round functions (F1 and F2) to ensure that encryption and decryption processes share the same circuitry according to
Figure 21, minimizing resource duplication and energy overhead. INLEC introduces a novel design called SCIN (Structure and Components INvolution), featuring an involutive 4 × 4 S-box optimized via genetic programming and a P-box derived from chaotic maps for high diffusion. Its design results in a compact area footprint (1953.91 GEs) and a combined encryption–decryption energy consumption of just 6.88 μJ/bit, making it more efficient than comparable ciphers such as Midori and IVLBC. Security analysis confirms its robustness against differential, linear, algebraic, and impossible differential attacks.
While INLEC achieves impressive energy efficiency and cryptographic strength, it has several limitations. Its design and evaluation are primarily based on theoretical analysis and simulations, with limited validation in real-world, large-scale deployments. Additionally, INLEC’s security has not yet been assessed against quantum threats, and futureproofing against post-quantum cryptography remains an open challenge. The cipher also lacks built-in error detection or correction mechanisms, which are increasingly critical in noisy, real-world IoTs environments.
LTLBC [
29] is a low latency LWBC designed for secure, real-time applications in IoTs environments. It uses a 14-round substitution-permutation network (SPN) structure with a 64-bit block size and 128-bit key. Its core design features a hybrid linear layer combining bit-wise permutation and word-wise involutive mapping, allowing full diffusion after just two rounds. The cipher includes a compact 4 × 4 S-box engineered through a bottom-up gate-level approach, minimizing logic depth and improving delay performance. When implemented in a round-based architecture, LTLBC achieves a latency of 14 ns and a hardware area of just 1967 GE, making it comparable to PRESENT (≈1570 GE) but with higher security margins and better diffusion. For applications requiring even faster response, its fully unrolled version reaches 4.73 ns latency (at 12,540 GE), showcasing scalability across performance profiles.
While LTLBC demonstrates excellent latency and a compact footprint in its round-based form, its fully unrolled implementation incurs a high area cost (12,540 GE), which may not be suitable for ultra-constrained devices such as passive RFID or low-cost smart cards. Furthermore, the cipher’s hybrid linear layer and non-standard word-wise involutive mappings, while effective for diffusion, add architectural complexity that could increase design verification overhead and hinder adoption in minimalistic embedded environments. Additionally, LTLBC operates only on 64-bit blocks, which may pose security or efficiency constraints in modern protocols that prefer 128-bit block sizes. Thus, while highly competitive in low latency and mid-range embedded applications, LTLBC may require tailoring or scaling for deployment in either ultra-lightweight or high throughput contexts.
4.2. Feistel Network (FN)
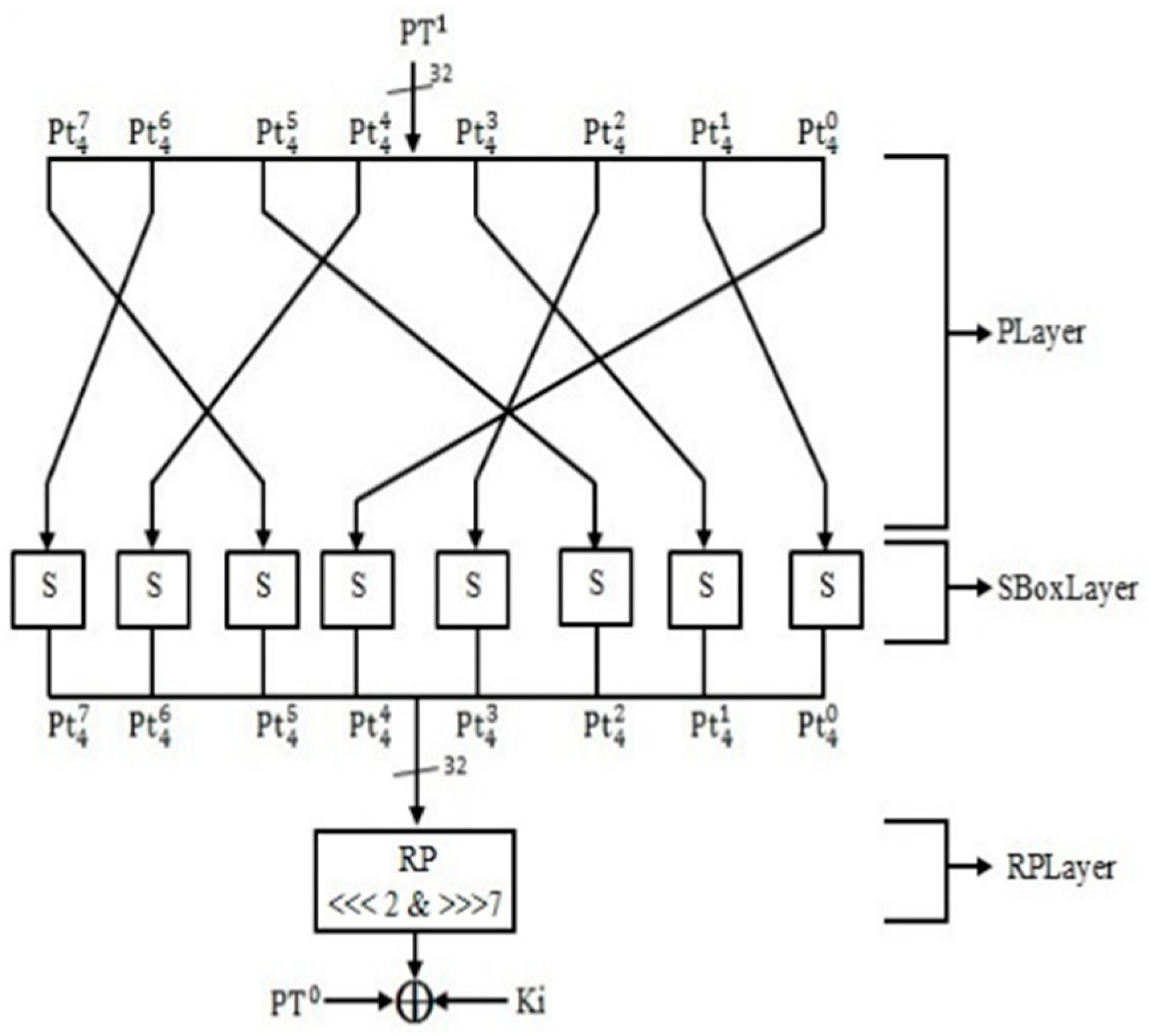
GRANULE [
30] is an ultra-LWBC based on a Feistel network, designed to offer efficient encryption for embedded systems, particularly for IoTs applications. It supports 64-bit blocks with key sizes of 80 or 128 bits and utilizes 32 rounds to ensure strong security against common cryptanalytic attacks, such as differential, linear, biclique, and key collision attacks. The F function of GRANULE, as shown in
Figure 22, incorporates three distinct layers: a permutation layer (PLayer), a substitution layer (SBoxLayer), and a round permutation layer (RPLayer), each contributing to the cipher’s diffusion and non-linearity. The cipher’s design prioritizes minimal memory usage and low-power consumption, with a small footprint in both hardware and software implementations. Its resistance to attacks is enhanced by a robust S-box and an asymmetric permutation layer, which prevent the clustering of linear and differential trails. The cipher is highly efficient, consuming fewer gate equivalents (GEs) than many other lightweight ciphers, making it suitable for resource-constrained environments. Moreover, it shows excellent performance in terms of execution time and throughput, demonstrating its viability for devices with limited computational resources.
The GRANULE algorithm, while robust against many cryptanalytic attacks and optimized for low-power and minimal gate count, has some limitations. Its resistance to advanced cryptanalysis relies on current methods, leaving potential vulnerability to future techniques as computational power and attack strategies evolve. Additionally, its performance trade-offs, such as higher execution time and lower throughput compared to some lightweight ciphers, may limit its applicability in environments requiring faster processing. Furthermore, its efficiency depends heavily on custom hardware designs, making it less optimal for general-purpose processors or legacy systems. Lastly, the need for 32 rounds with a strong S-box and permutation layers, though necessary for security, can demand more resources than simpler lightweight ciphers, posing challenges in resource-constrained environments.
This paper enhances the DLBCA [
31] (Differential LWBC Algorithm) by reducing the number of S-boxes from eight to four, as illustrated in
Figure 23, effectively lowering the cost factor without significantly compromising the algorithm’s security. The optimized cipher, while maintaining 32 rounds of operations similar to the original DLBCA, utilizes fewer S-boxes, which reduces the overall gate equivalents (GEs) needed for its implementation. Security analysis, including differential and boomerang attacks, demonstrates that the proposed algorithm performs similarly to DLBCA in terms of active S-boxes and rounds, with improved cost efficiency. The results show that the new design offers better resistance to the boomerang attack, with a reduced number of rounds for other ciphers such as TWINE, LBlock, and PRESENT. Additionally, the cost comparison reveals that the proposed algorithm is the most cost-efficient among several lightweight block ciphers, making it highly suitable for resource-constrained environments.
The improved DLBCA algorithm reduces the number of S-boxes from 8 to 4 to lower implementation costs, achieving the lowest gate equivalent (GE) compared to similar algorithms. However, this reduction impacts security, particularly against differential cryptanalysis, as the number of active S-boxes is lower than the original DLBCA and some other lightweight ciphers. Additionally, it withstands boomerang attacks for only 3 rounds, similar to the original DLBCA, but falls behind algorithms such as TWINE and LBLOCK, which resist up to 11 rounds. This trade-off between cost efficiency and security may limit its suitability for applications requiring higher resilience against cryptanalysis.
This paper proposes an improved S-box layer for the RoadRunner [
32] lightweight block cipher, aiming to optimize its hardware performance. The new S-box design consists of eight different 4-bit S-boxes as depicted in
Figure 24, each derived from affine transformations and a shared quadratic permutation, reducing area consumption by 51% compared to the traditional lookup table (LUT) approach. The optimized design enhances hardware efficiency by reusing the same quadratic permutation in the construction of each 4-bit S-box, significantly lowering resource overhead. The implementation, synthesized on 0.18 µm CMOS technology, achieves a reduced area of 124 gate equivalents (GEs), while the traditional LUT method requires 251 GE. This optimization makes RoadRunner more suitable for hardware-limited environments, such as smart cards, by allowing more compact and efficient implementations for parallelism and pipelining.
The improved Roadrunner algorithm focuses on hardware optimization, reducing area consumption by 51% through a shared quadratic permutation across multiple S-boxes. However, this optimization introduces increased complexity in S-box composition and limits its efficiency in high-parallelism or software-based applications. Additionally, while security remains comparable to the original, the improvements do not significantly enhance resilience against advanced cryptanalysis.
LWBCLWBC the MANTRA [
33] cipher is an ultra-LWBC designed for resource-constrained applications such as RFID and IoTs. It operates on 64-bit plaintext and supports both 80-bit and 128-bit keys. The cipher uses a Feistel network within a Feistel structure as depicted in
Figure 25, with a strong S-box and permutation layer that provides robust resistance to linear, differential, and zero correlation attacks. With a low footprint, MANTRA requires only 1662 gate equivalents (GEs) for a 128-bit key and 1374 GEs for an 80-bit key. The design minimizes memory and power consumption, making it highly suitable for embedded systems. Security analysis demonstrates that MANTRA performs well against various cryptanalytic attacks, including biclique and key collision attacks, while offering efficient performance in both hardware and software implementations.
MANTRA is optimized for software-based applications but less efficient for hardware implementations. Its computational complexity is high, and while resistant to basic attacks, its security against advanced cryptanalysis remains unverified. The low gate equivalent (GE) count may impact long-term security, and performance on non-ARM architectures and execution speed require further evaluation.
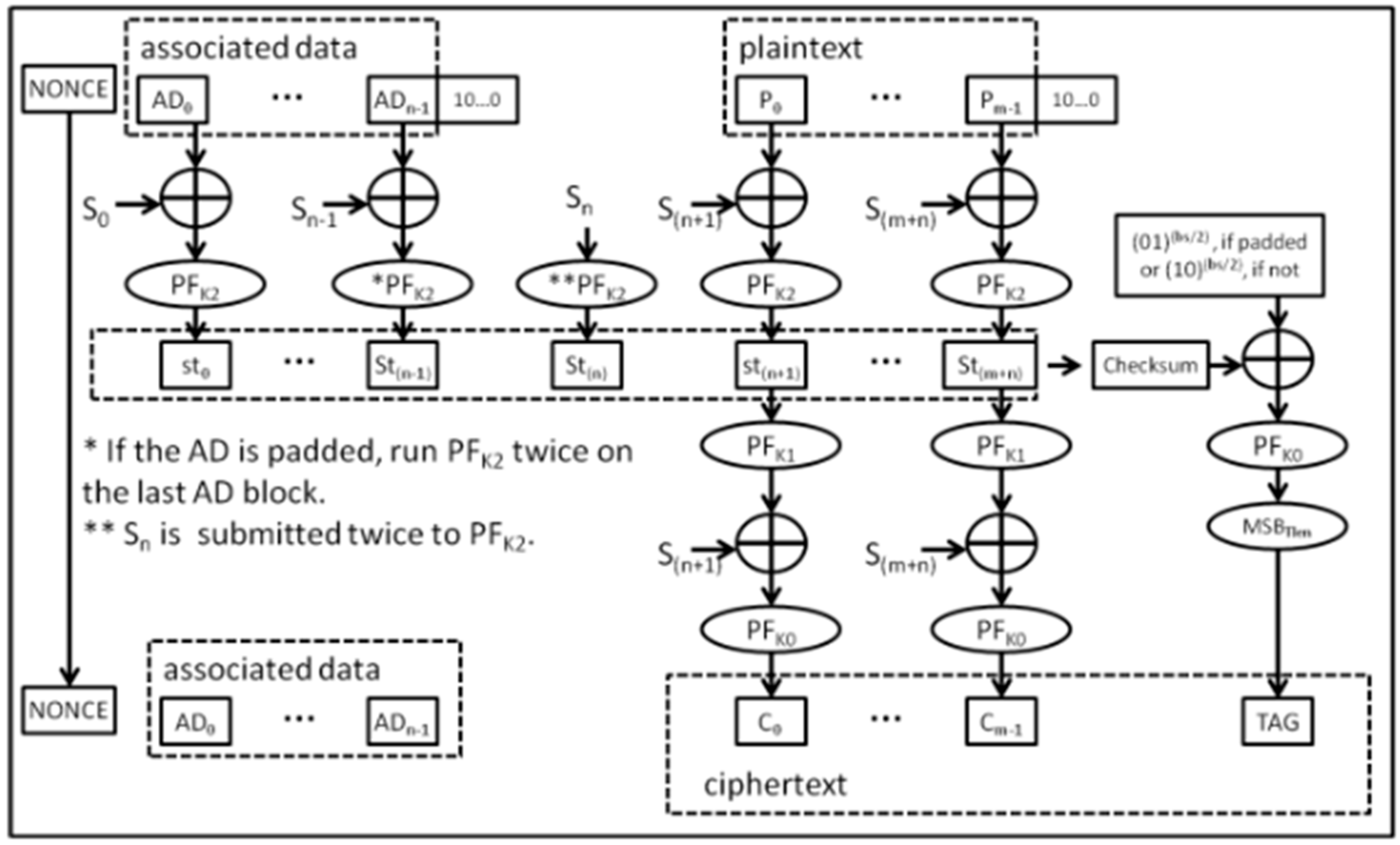
FlexAEAD [
34] is a lightweight authenticated encryption with associated data (AEAD) cipher family designed for efficiency and security in resource-constrained environments. The algorithm integrates both encryption and authentication in a single process, making it more resource-efficient than separate encryption and hashing methods. FlexAEAD v1.1, an improved version, addresses vulnerabilities identified in earlier versions, such as padding attacks and iterated differential attacks. It uses a key-dependent permutation function (PFK) along with multiple rounds involving S-box layers, mix layers, and shuffle operations to ensure strong cryptographic properties, as illustrated in
Figure 26. The cipher supports various block and key sizes, and its performance is optimized for multi-core processing, allowing parallelization. Its security has been evaluated against differential and linear cryptanalysis, demonstrating its resistance to these attacks. FlexAEAD is well-suited for applications requiring lightweight encryption with built-in authentication, making it ideal for IoTs and other embedded systems.
The FlexAEAD algorithm has higher computational overhead due to extra XOR operations and key-dependent permutations. It is not fully optimized for 64-bit processors, impacting performance on some hardware. It consumes more CPU cycles than some lightweight ciphers and requires further cryptanalysis testing for advanced attack resistance. Its complex implementation with multiple S-boxes and shuffle layers makes deployment challenging. Additionally, real-world performance in IoTs environments needs further evaluation.
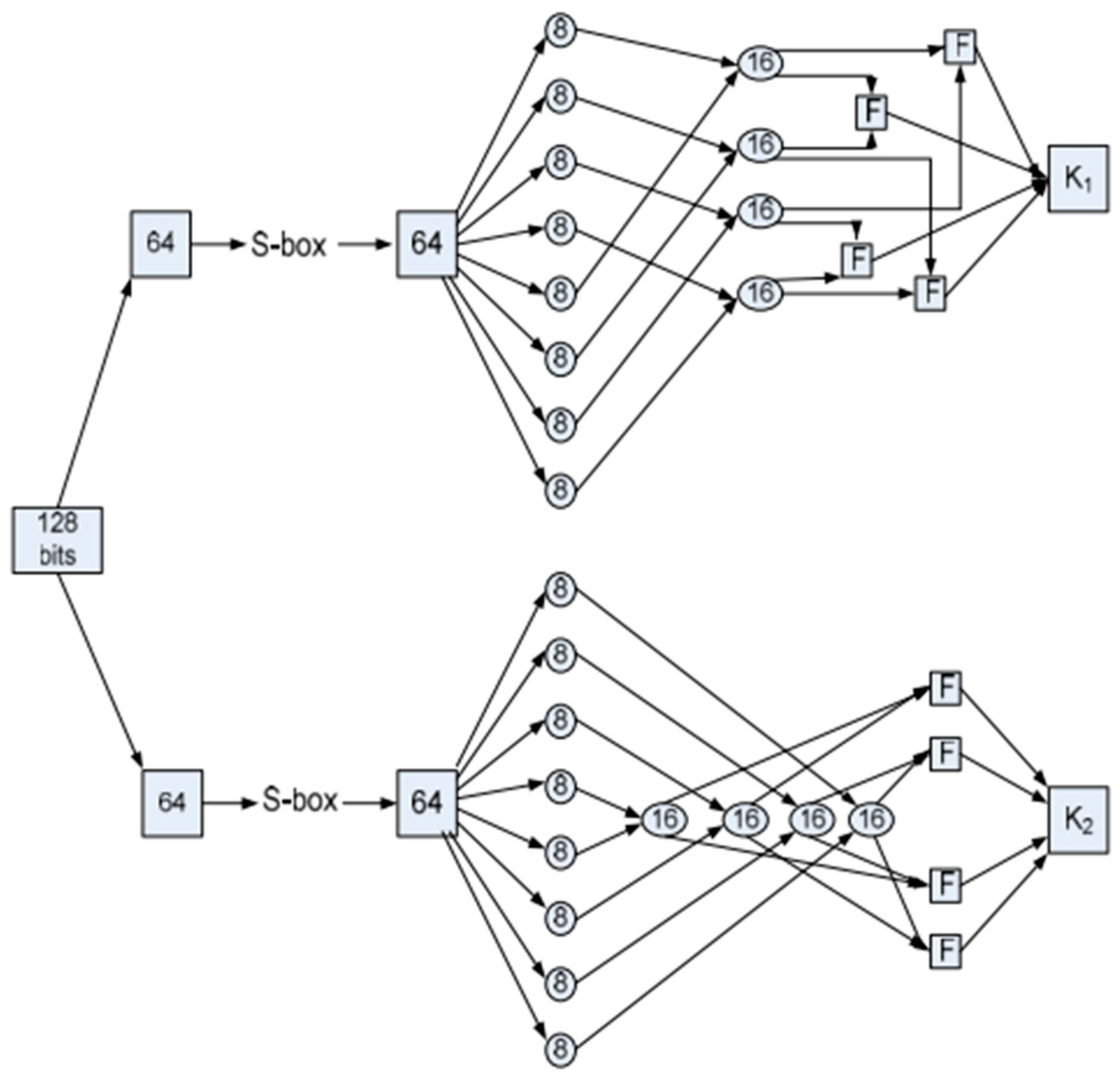
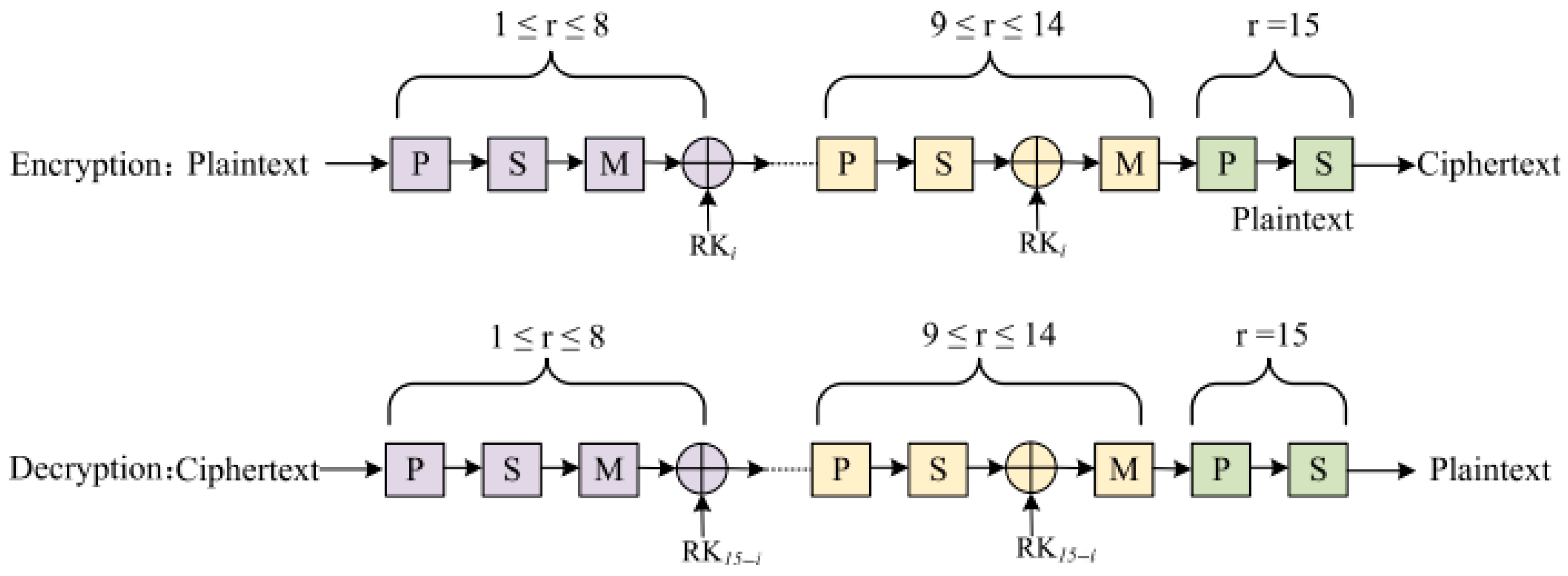
The LCA [
35] (Lightweight Cryptographic Algorithm) is designed to meet the security needs of IoTs and wireless sensor networks with highly constrained resources. It utilizes a Feistel structure, which enables efficient encryption and decryption processes with a 64-bit block size and 256-bit key. LCA incorporates a compact 4-bit S-box with high non-linearity to ensure confusion and a mix of operations such as XOR, addition, and subtraction to ensure diffusion, as depicted in
Figure 27. The algorithm is optimized for both software and hardware implementations, ensuring energy efficiency and fast execution. LCA provides strong resistance to cryptanalytic attacks such as linear and differential attacks, making it suitable for applications in environments where power and computational resources are limited. The design principles of simplicity and low resource usage ensure that it can be deployed effectively in various IoTs applications.
The LCA algorithm has limited cryptanalysis testing, making its resistance to advanced attacks uncertain. Its dual-key structure (256-bit) adds complexity in key management. While the bit-slice implementation improves efficiency, it may not be optimized for all hardware. The multiple algebraic operations per round increase computational overhead, and its scalability for ultra-low-power devices is limited compared to simpler ciphers.
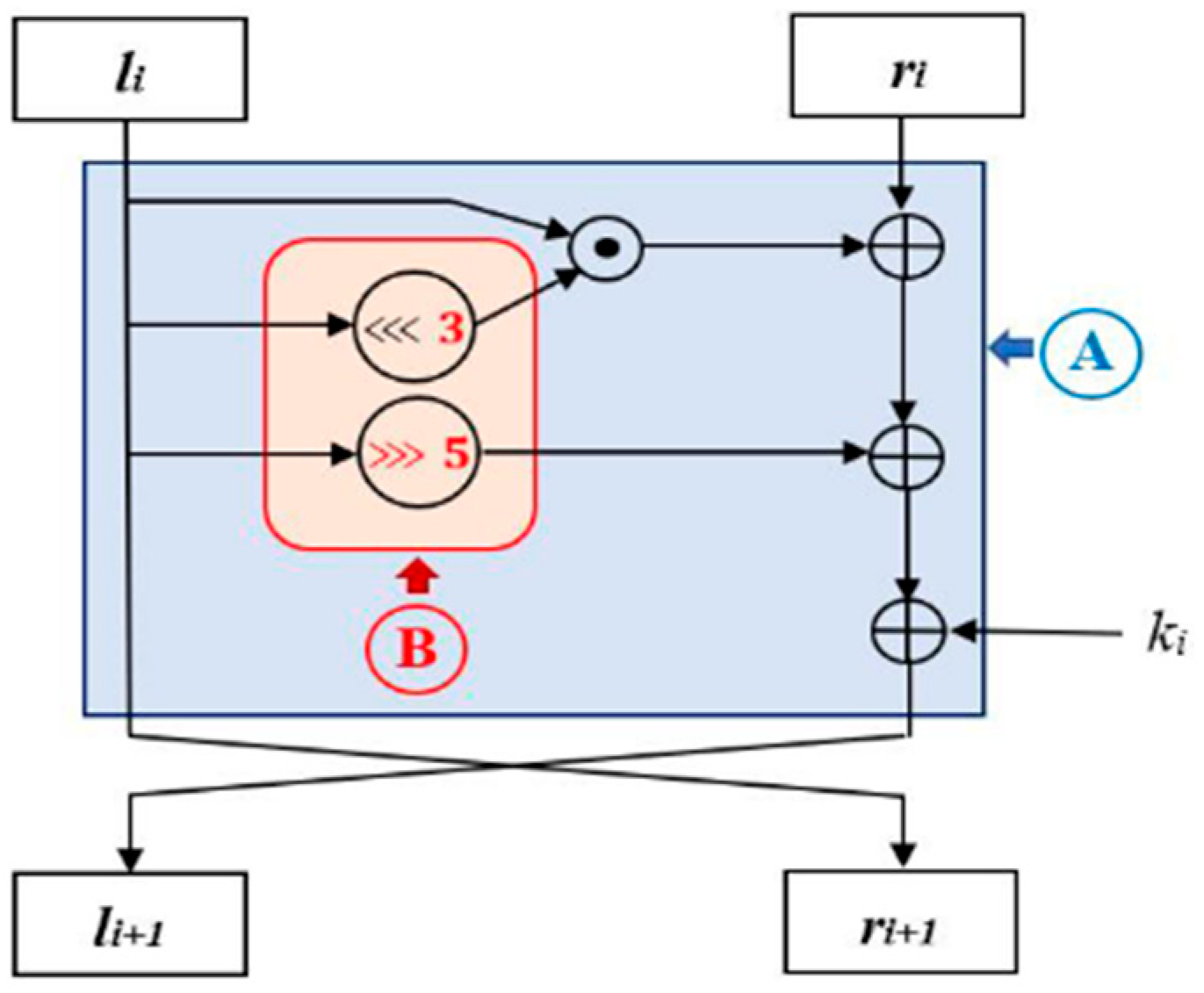
The paper proposes a modification to the SIMECK 32/64 [
36] block cipher’s round function to enhance its security and performance, specifically targeting improvements in the avalanche effect and runtime efficiency. The original round function on the identified area A was modified as represented in
Figure 28 area B by adjusting circular shift constants and altering the shift direction, achieving a significant increase in the avalanche effect (up to 54.67% on average) compared to the original 48.33%. Additionally, the modified algorithm showed improved runtime performance, reducing execution time from 2.44 ms to 1.39 ms. The study also tested the randomness of the modified SIMECK, showing a slightly lower
p-value (0.46931) compared to the original (0.51512), indicating that the modification somewhat affects the algorithm’s randomness. Overall, the study concludes that the modified SIMECK 32/64 is more secure and performs better than the original, making it a promising candidate for use in IoTs applications, where both security and efficiency are critical.
The improved SIMECK algorithm has increased computational complexity and reduced randomness, which may impact security. While it improves the avalanche effect (54.67%), it comes at the cost of slower processing time. Its resistance to cryptanalytic attacks remains unverified, and the key schedule may inherit security weaknesses from SPECK. Further evaluation is needed to confirm its overall security.
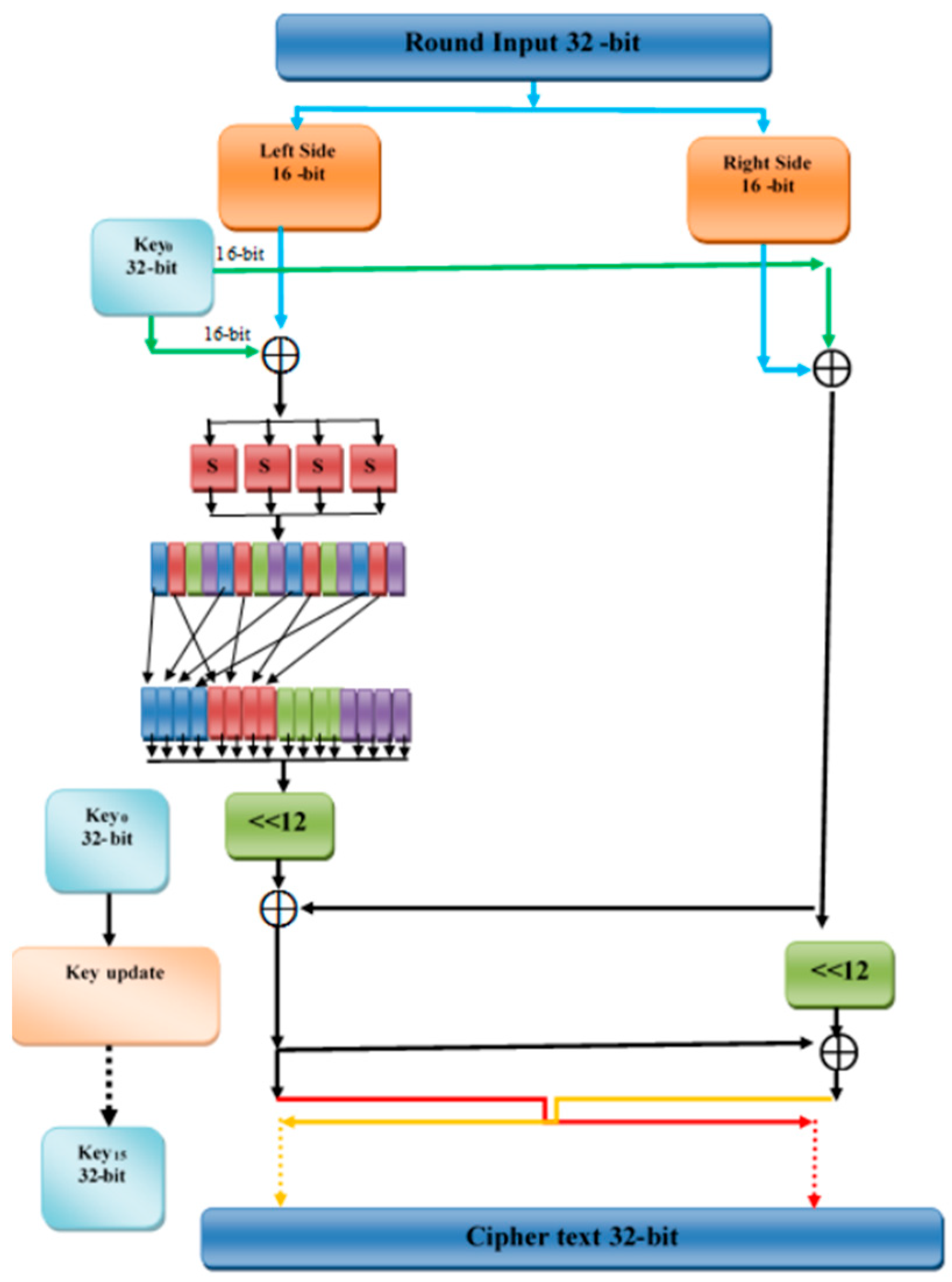
TED [
37] is a LWBC specifically designed for IoTs devices, focusing on security and energy efficiency. The cipher employs a Feistel structure and operates with a 64-bit plaintext block and a 128-bit key across 26 rounds. TED integrates a 4 × 4 bit S-box, modular addition, and bit permutation to enhance security while minimizing memory usage and energy consumption, as demonstrated by
Figure 29. It is optimized to resist side-channel attacks (SCAs) through a bit-slice implementation of the S-box, preventing cache-timing attacks. When evaluated on both software and hardware platforms, TED demonstrated significantly reduced CPU cycles and memory footprint compared to other ciphers such as PRESENT while maintaining robust resistance to differential and linear cryptanalysis. The cipher also performed well in terms of security, with strong resistance to structural attacks and high avalanche effects. Additionally, TED’s energy efficiency was improved by 14.85% through an area-optimized design, making it ideal for resource-constrained IoTs applications.
The TED algorithm has higher computational complexity due to its 26 encryption rounds and increased energy consumption compared to SPECK and SIMON. Its side-channel attack resistance needs further validation, and its complex key scheduling may add processing overhead. The real-time bit permutation calculation reduces memory usage but increases computational cost. Additionally, the bit-sliced S-box implementation may complicate deployment in constrained environments.
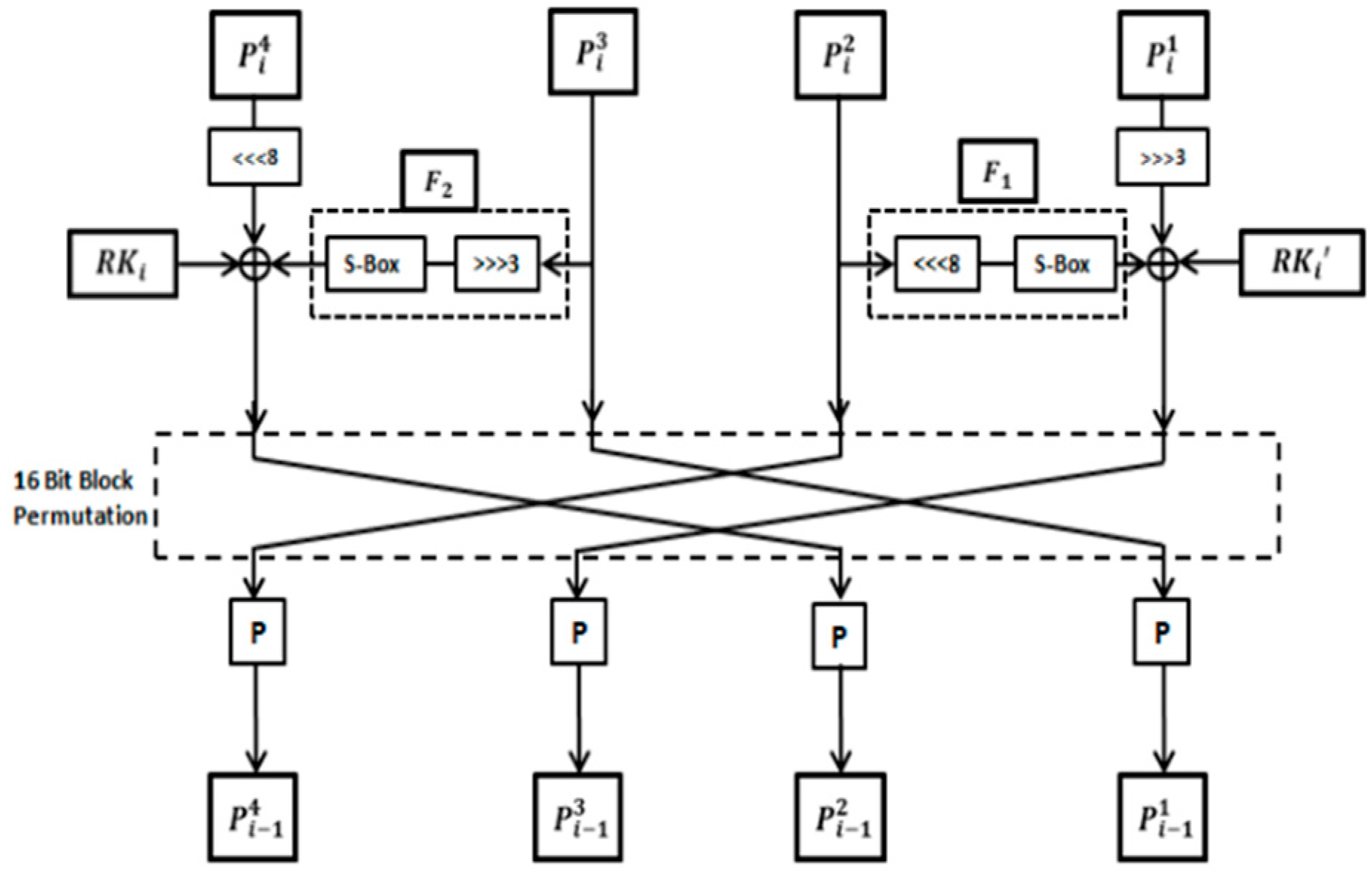
This paper presents a lightweight design of the SM4 [
38] cryptographic algorithm with hardware implementation aimed at improving efficiency in resource-constrained environments. By replacing the original 8-bit S-box with a 4-bit cyclic shift S-box as presented in
Figure 30, the design reduces hardware resource consumption while maintaining the cryptographic properties of the SM4 algorithm. A threshold scheme based on secret sharing is also introduced to enhance resistance against side-channel attacks, particularly first-order and second-order differential power analysis (DPA) attacks. The implementation involves transforming operations from GF(2
4) to GF(2
2) using a multiplier and squarer, further reducing circuit consumption. The system is implemented using FPGA and demonstrates a significant reduction in hardware resource usage, achieving a lightweight cryptographic solution with a total of 2803 logic elements while maintaining robust security.
The improved SM4 algorithm has reduced security due to the 4-bit S-box, making it potentially vulnerable. Its resistance to side-channel attacks still needs further validation. The implementation complexity increases due to composite field transformations and secret sharing. It is hardware-optimized, limiting software efficiency, and software performance remains untested. Despite being lightweight, it still requires 2803 logic elements, which may be a constraint for ultra-low-power devices.
LWBC the paper proposes M-XXTEA [
39], a modified version of the original XXTEA block cipher, designed to enhance the security and performance of lightweight cryptography for IoTs smart devices. M-XXTEA, as evidenced by
Figure 31, builds on the unbalanced Feistel structure of XXTEA and introduces two key improvements: an enhanced S-box (based on AES but modified using Fibonacci numbers and prime factors) to strengthen non-linearity and resistance to cryptanalysis, and a chaotic key generator that dynamically changes the encryption key for each block, emulating a one-time pad. The algorithm supports flexible block sizes (multiples of 32 bits, minimum 64 bits) and uses a 128-bit key. Experimental results show that M-XXTEA achieves significantly better encryption and decryption speed compared to AES (by 60% and 57%, respectively), while maintaining strong avalanche properties and passing all NIST statistical randomness tests. Its design is suitable for real-time data protection in IoTs systems, smart cities, and e-health applications.
Despite its advantages, M-XXTEA has a few limitations. The increased encryption complexity—due to dynamic key generation and non-linear substitutions—adds slight performance overhead compared to the original XXTEA, particularly for large messages or high key sizes (192 or 256 bits). Its reliance on chaotic key generation also introduces challenges in synchronizing sender and receiver seed values in practical deployments. Moreover, while M-XXTEA performs well in simulations, it lacks hardware implementation analysis, leaving its real-world performance on constrained embedded systems unverified. The algorithm’s novel components (such as the improved S-box and key generator) would benefit from further formal cryptanalysis, especially regarding side-channel resistance and algebraic attacks.
SCENERY [
40] is a 64-bit LWBC designed for both hardware and software efficiency, targeting resource-constrained IoTs environments. It uses a balanced Feistel structure as represented in
Figure 32 with 28 rounds and supports an 80-bit key. The round function combines eight 4 × 4 S-boxes with a 32 × 32 binary matrix, enhancing confusion and diffusion. SCENERY employs bit-slice techniques to improve performance and resist side-channel attacks, and its key schedule integrates non-linear operations and dynamic permutation to strengthen security. It achieves balanced performance across platforms, requiring only 1438 GE in hardware and offering competitive encryption speed on 8-bit and 64-bit processors.
While SCENERY offers a strong balance between performance and security, its balanced Feistel structure inherently slows diffusion, requiring more rounds to achieve sufficient confusion compared to SPN-based ciphers. Although the bit-slice and matrix operations improve efficiency, the cipher’s reliance on small 4 × 4 S-boxes may limit its non-linearity and resistance to emerging cryptanalysis. Additionally, its key schedule—though improved—still allows partial backward derivation, making it less robust than designs with fully non-invertible expansion methods.
LiteEncrypt [
41] is a 64-bit LWBC with a 128-bit key based on a Feistel structure. It employs circular shifts, XOR, and modular key addition within a 27-round encryption framework. Subkeys are derived using an LFSR-based key schedule, enhancing diffusion across rounds. Evaluated on several IoTs platforms (e.g., Arduino, ESP32), LiteEncrypt demonstrates a strong avalanche effect and consistent superiority in execution time and energy efficiency compared to CLEFIA, SIT, PRIDE, and GFRX.
LiteEncrypt has not undergone formal cryptanalysis against differential, linear, or algebraic attacks. While its avalanche performance and speed are promising, the lack of GE metrics or side-channel resistance evaluations limits its comparability to standard LWBCs. Additionally, the 27-round structure and reliance on LFSR-based key scheduling need further review for cryptographic strength under active adversarial conditions.
RBFK [
42] is an LWBC with a modified Feistel structure supporting 64-bit blocks and 128-bit keys. It integrates randomized butterfly mixing, dual S-boxes, and a genetic-inspired G-function to boost diffusion and confusion. Its key schedule and encryption rounds provide high avalanche effect and key sensitivity, validated through statistical and image-based tests on FELICS and AVR, confirming suitability for constrained IoTs platforms.
Despite promising results, RBFK lacks formal cryptanalytic bounds (e.g., linear/differential resistance). The PRNG-based key schedule is not fully specified, raising concerns over deterministic entropy. GE is not explicitly reported, but FELICS-based AVR metrics (~1566 bytes of code, ~34B RAM) imply ~2200 GE, aligning it with similar LWBCs in efficiency and area cost.
ANU-II [
43] is an LWBC designed for resource-constrained IoTs environments, offering improvements over its predecessor, ANU. It uses a 64-bit block size and supports 80- or 128-bit keys, operating in a 25-round balanced Feistel structure with minimal cryptographic components: a single 4 × 4 S-box, a few shift operations, and XOR gates. ANU-II eliminates memory-intensive P-layers and employs carefully selected circular shifts to maximize active S-boxes per round, thereby increasing resistance to linear and differential cryptanalysis. It achieves a throughput of 437.31 Kbps with low execution time (146.35 µs) and passes advanced cryptanalytic tests, including biclique and avalanche analysis. Importantly, ANU-II is highly efficient in hardware, requiring only 1010 gate equivalents (GEs)—significantly lower than PRESENT (2756 bytes of flash and higher GE) and other standard ciphers.
Despite its compactness and security, ANU-II has certain limitations. While it removes complex diffusion layers such as P-layer to save memory, this simplification may reduce flexibility in adapting the cipher to newer threat models or future applications requiring stronger diffusion mechanisms. Additionally, its architecture is highly tailored for 64-bit data blocks, which may not scale efficiently to larger block sizes needed in modern secure communication systems. Moreover, although ANU-II uses a single S-box for efficiency, the lack of variety in non-linear operations could be a potential vulnerability if future attacks exploit S-box-specific weaknesses. Hence, while ANU-II is an excellent fit for low-end IoTs devices, its design choices may limit broader applicability and long-term cryptanalytic robustness.
4.3. Generalized Feistel Network (GFN)
The NUX [
44] cipher is an ultra-LWBC designed for resource-constrained applications such as IoTs and wireless sensor networks. It employs a generalized Feistel network with 31 rounds and supports 128-bit or 80-bit key lengths, offering significant security while maintaining a minimal hardware footprint. The cipher, as displayed in
Figure 33 uses a 16-bit permutation and a compact 4 × 4 S-box to reduce gate equivalents (GEs), achieving only 1022 GEs for the 128-bit key version, making it one of the smallest ciphers in its class. NUX is resistant to linear and differential cryptanalysis and advanced attacks such as biclique attacks. Its design features high diffusion and confusion properties, contributing to strong security with low memory and power requirements. The cipher is particularly suitable for IoTs and pervasive computing environments where both security and efficiency are critical.
NUX has high computational overhead due to 31 encryption rounds, and while resistant to basic attacks, its resistance to advanced attacks is unverified. The bit permutation layer adds complexity, and reducing gate equivalents (GEs) may impact long-term security. Additionally, its performance on non-ARM platforms and large-scale deployments needs further testing.
The NUCLEAR [
45] cipher is a lightweight encryption scheme designed to replace AES-128/256 in the 6LoWPAN protocol stack for IoTs applications, optimizing the system’s performance in resource-constrained environments. Using a generalized Feistel structure (GFS), NUCLEAR, according to
Figure 34, is highly efficient in terms of power consumption, memory requirements, and footprint area, making it suitable for wireless sensor networks. It operates on 64-bit blocks, with 25 rounds, and features an optimized S-box and circular shift operators for maximum active S-boxes. Compared to other lightweight ciphers, NUCLEAR demonstrates superior performance, requiring fewer gate equivalents (GEs) and memory while providing higher throughput and lower power dissipation. Security analyses confirm its resilience against common attacks like differential, linear, and biclique attacks, as well as its strong avalanche effect. The such as design makes it a promising candidate for implementing lightweight encryption in IoTs systems, reducing overhead while maintaining robust security.
The NUCLEAR algorithm has limited cryptanalysis testing, making its resistance to advanced attacks uncertain. Its S-box and shift parameters may pose potential security risks over time. The higher number of rounds (25) increases processing time, and there is a trade-off between security and efficiency. Additionally, its real-world deployment and integration in diverse IoTs environments require further evaluation.
The Shadow [
46] cipher is an LWBC designed specifically for resource-constrained IoTs environments. It is structured using a generalized Feistel network with four branches as illustrated in
Figure 35, deliberately avoiding the substitution-permutation network (SPN) model. Shadow supports two configurations: a 32-bit block size with a 64-bit key using 16 rounds and a 64-bit block size with a 128-bit key using 32 rounds. Its design prioritizes efficiency and low computational overhead while maintaining cryptographic strength suitable for IoTs applications.
The Shadow cipher, while efficient for IoTs applications, has several limitations. Its early rounds exhibit a low algebraic degree, making it more vulnerable to algebraic and higher-order differential attacks in reduced-round versions. The theoretical degree growth bounds are not tight, leading to potential underestimations of its security margin. Additionally, distinguishers have been found for reduced rounds (e.g., 4-round versions), suggesting limited resistance when fewer rounds are used. Although no full round attack is currently practical, its reliance on lightweight structures and compact design may come at the cost of a smaller security margin compared to more robust lightweight ciphers.
HDLBC [
47] (High Diffusion Lightweight Block Cipher) is a NAND-RX-based LWBC optimized for IoTs devices, offering a strong balance between high diffusion and low area consumption. It adopts a 4-branch generalized Feistel structure (GFS) with only two F-functions (RA1 and RA2), as depicted in
Figure 36, built using NAND operations, minimizing hardware footprint while improving diffusion. HDLBC supports 64-bit plaintext and 64-/128-bit keys, running for 25 or 32 rounds, depending on key size. Its hardware implementation is highly efficient, requiring only 1248 GEs on 0.18 μm CMOS and achieving 256 Kbps throughput at 100 KHz. HDLBC passes stringent avalanche, differential, linear, integral, and zero correlation cryptanalysis tests, showing strong resistance to a wide range of attacks. With its compact design and strong security properties, HDLBC is well-suited for resource-constrained environments such as RFID and IoTs systems.
Despite its strengths, HDLBC has a few limitations. Its design focuses heavily on hardware efficiency, which may limit its performance or applicability in software-based or hybrid platforms. While it achieves full diffusion in just 3 rounds, this also means its security margin is relatively tight, with 25 rounds total—leaving less buffer against future cryptanalytic advancements. Additionally, its use of simple NAND-based F-functions, though cost-effective, may offer less flexibility or adaptability compared to more complex non-linear components used in other ciphers. These trade-offs make HDLBC ideal for specific constrained environments but less suitable for broader or evolving cryptographic needs.
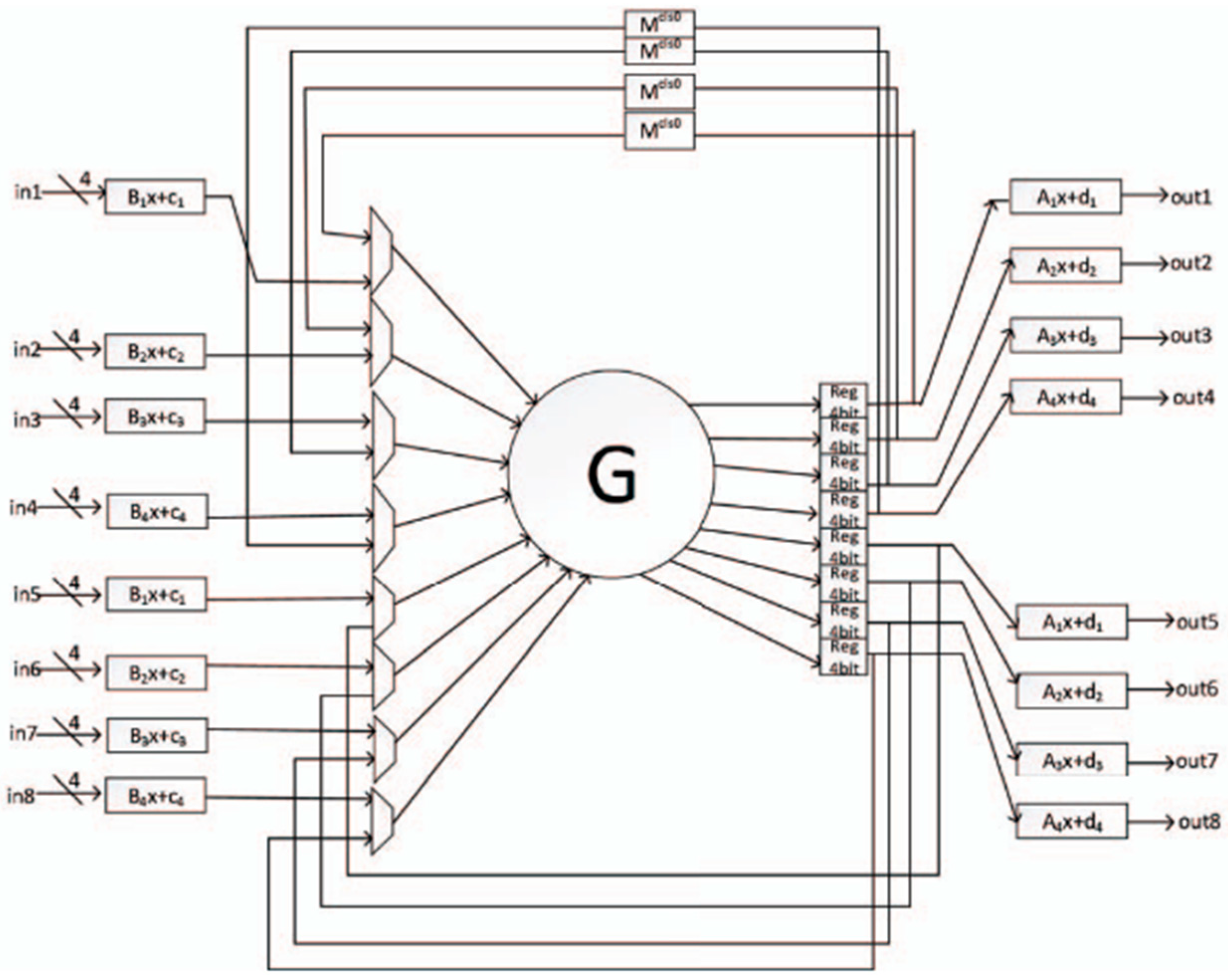
GFLE [
48] is a low energy LWBC designed for IoTs applications, aiming to minimize energy consumption while maintaining high security. Based on a variant of the generalized Feistel structure (GFS) with 4 branches, as confirmed by
Figure 37, GFLE incorporates a simplified Lai-Massey structure to enhance diffusion efficiency, achieving full diffusion in just 3 rounds. The cipher uses a low energy, gate-level S-box optimized through a depth-first strategy for improved hardware performance. GFLE consumes only 1596 gate equivalents (GEs) in its ASIC implementation and reduces energy consumption by 61.59% compared to SKINNY, making it highly efficient for resource-constrained devices. It provides strong resistance against cryptographic attacks such as differential, linear, and impossible differential attacks, making it well-suited for environments such as RFID tags and wireless sensor nodes.
Despite its low energy consumption and strong cryptographic properties, GFLE’s reliance on a smaller number of branches in the GFS structure, while beneficial for energy efficiency, may limit its security under future cryptanalysis techniques. The reduced number of rounds required for full diffusion could potentially expose the cipher to attacks that exploit this faster diffusion process. Additionally, while the cipher’s S-box design and permutation layers are optimized for low energy, the complexity of implementing and optimizing these components for specific hardware could be a challenge in more diverse environments.
IIoTBC [
49] is a 64-bit LWBC with a 128-bit key, built on a flexible generalized Feistel structure that supports 8- or 4-branch modes to match 8- or 16-bit MCUs. It features a lightweight 4 × 4 S-box with excellent cryptographic properties (DU = 4, NL = 4, AD = 3) and alternates involutive/non-involutive permutations for rapid diffusion. The cipher achieved strong avalanche performance and was implemented in ASIC using 0.13 μm tech, with GE ~1769 for System A and ~2338 for System B. Throughput reached 200 Kbps at 100 MHz, and IIoTBC was practically deployed on a temperature-monitoring platform.
IIoTBC demonstrates strong avalanche, algebraic, and impossible differential resistance but lacks independent third-party cryptanalysis or open-source implementations for broader validation. While the flexible dual-system design improves adaptability, it adds structural complexity. Side-channel protection is considered only in System B via bit-slicing, leaving System A potentially vulnerable. Moreover, the 32-round count, while securing full diffusion, may increase latency and power cost in ultra-constrained nodes.
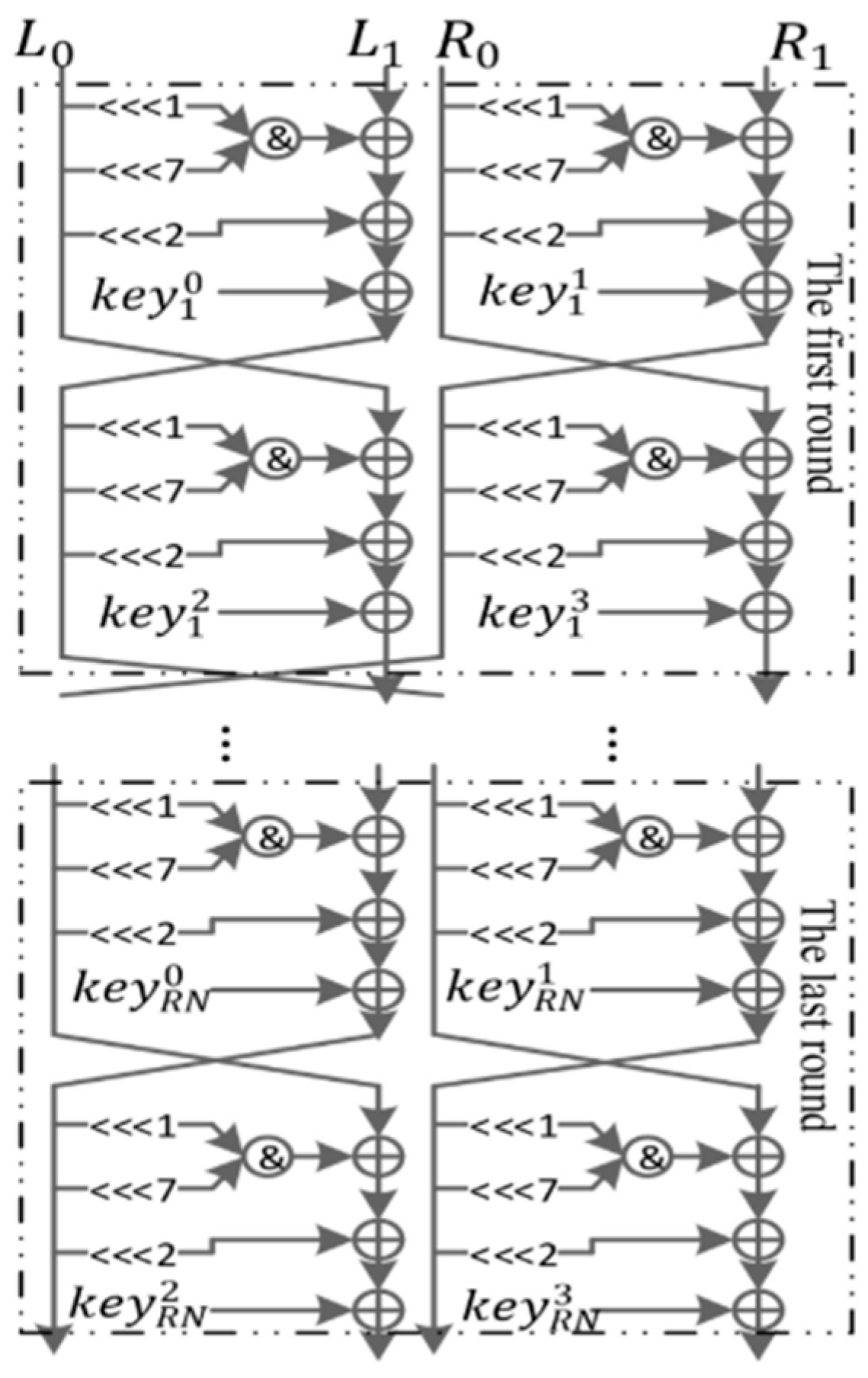
µ2 [
50] is a 64-bit LWBC with an 80-bit key, built on a Type-II generalized Feistel structure using a 16-bit ultra-lightweight SPN-based F-function. It applies PRESENT’s s-box and a novel permutation layer within the F-function and follows a modified PRESENT-like key schedule. Designed for constrained devices, µ2 achieves high security margins against known attacks, including differential, linear, integral, and algebraic cryptanalysis, while maintaining simplicity and strong pseudorandomness as validated by NIST STS.
While µ2 shows strong theoretical resistance, its security relies heavily on design intuition and has yet to undergo extensive third-party cryptanalysis. The performance comparison is limited to software benchmarks on x86 CPUs, with no hardware GE or FPGA synthesis results provided. Further studies are required to confirm µ2’s robustness in side-channel scenarios and its efficiency in constrained hardware environments.
LPHD [
51] is a 64-bit LWBC with a 128-bit key, based on an 8-branch generalized Feistel structure (Type-2 GFS). It integrates a low-power 4-bit S-box, optimized bit permutation, and a two-stage permutation layer (TP) for rapid diffusion. The cipher achieves full diffusion in just 4 rounds and employs a non-linear key schedule that reuses the encryption core, enhancing security while reducing hardware cost. LPHD achieves only 1276 GEs and 1.914 μW of power consumption on UMC 0.18 μm, outperforming SKINNY, PRESENT, and BORON in both area and energy efficiency. It has been practically implemented in a smart door lock platform, encrypting identity-recognition data on STM32-based hardware.
Although LPHD achieves excellent hardware efficiency and demonstrates strong resistance to differential, linear, and impossible differential attacks, it has not been subjected to third-party or open-source cryptanalysis. Its security relies heavily on internally defined parameters (e.g., chaotic constant generation and round permutation), and while its S-box and F-function are carefully optimized, the lack of independent validation may limit its adoption in high-assurance environments. Furthermore, its resistance to side-channel and fault attacks remains untested, and its practical application is limited to specific platforms.
Tweakable TWINE (T-TWINE) [
52] is a dedicated tweakable block cipher (TBC) based on the lightweight cipher TWINE, designed to support secure encryption with an additional 64-bit public input called a tweak. Built upon a generalized Feistel structure (GFS), T-TWINE maintains TWINE’s original 64-bit block size and key options (80-bit or 128-bit) while introducing a lightweight permutation-based tweak schedule. This tweak mechanism is independent of the key schedule and efficiently reuses TWINE’s components, preserving the 36-round structure. Security evaluations show strong resistance to differential, linear, integral, and impossible differential attacks, especially in chosen tweak scenarios. In hardware, the area overhead is minimal, requiring only ~2180 gate equivalents (GEs) for T-TWINE-80, compared to ~1627 GE for the original TWINE-80. This modest increase makes it one of the most efficient tweakable ciphers built on a GFS framework.
While T-TWINE offers solid security and area-efficient tweakable encryption, it comes with certain limitations. Most notably, its GE count (2180), although small, is higher than some other modern TBCs, such as SKINNY-64-128 (1696 GE) and CRAFT-128 (1193 GE), which were designed from scratch with minimal tweak cost in mind. Additionally, T-TWINE inherits the limitations of TWINE’s 64-bit block size, which may not be sufficient for applications requiring larger security margins or higher throughput. The cipher also does not claim security in the chosen tweak and related-key setting, a scenario increasingly relevant in certain side-channel and protocol-driven environments. Therefore, while T-TWINE is excellent for systems needing minimal modification to existing Feistel-based designs, it may not be the best candidate for use cases demanding ultra-low GE or broader adversarial security guarantees.
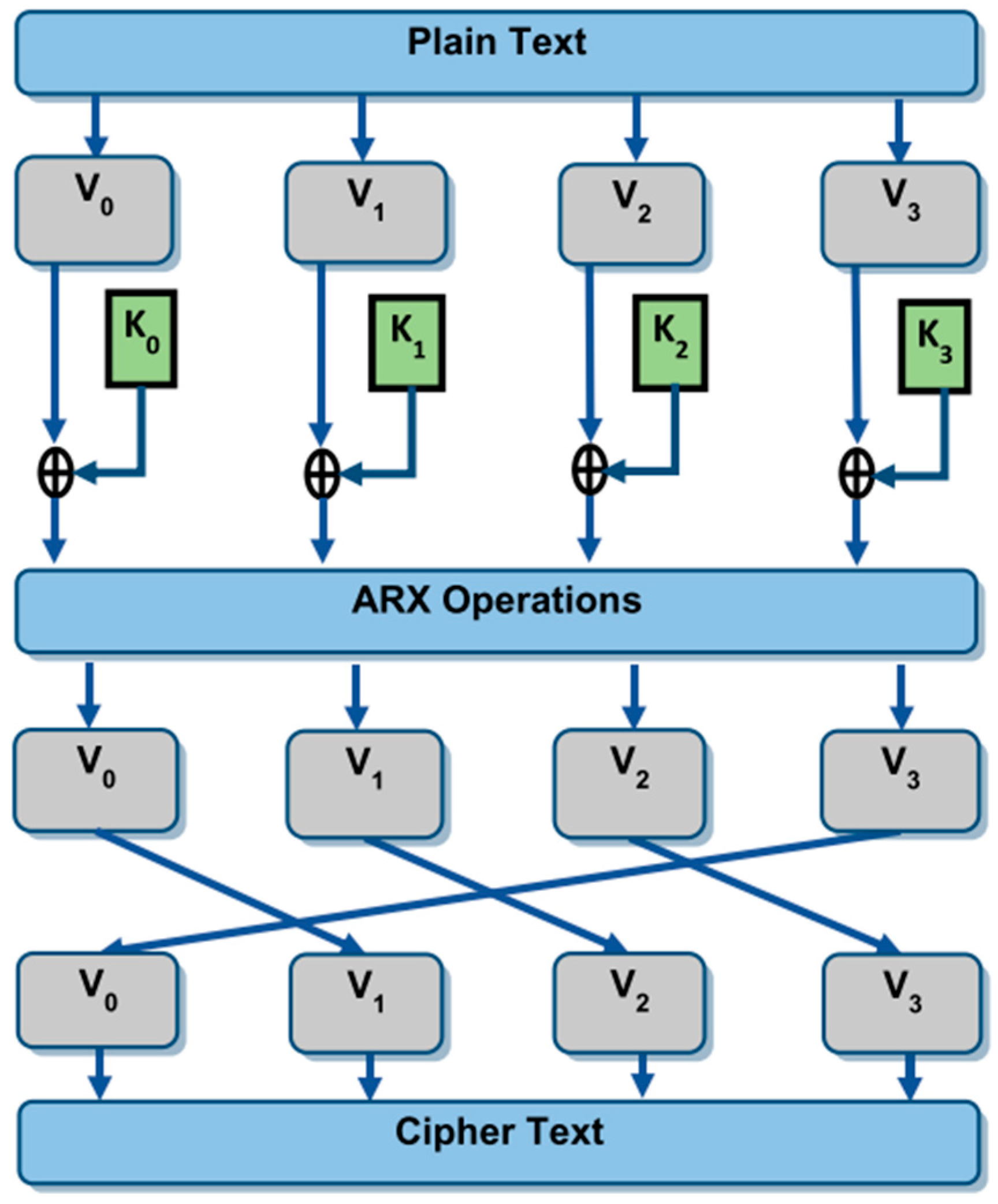
4.4. Addition-Rotation-XOR (ARX)
The BRIGHT [
53] cipher is an LWBC family designed specifically for 32-bit processors, optimized for IoTs and resource-constrained environments. It employs an ARX (addition-rotation-XOR) structure, providing high diffusion and fast execution speed, making it ideal for applications with strict memory and computational limitations. The BRIGHT family includes six variants with different block and key sizes as presented in
Figure 38, supporting 64-bit and 128-bit blocks. Its design incorporates key whitening, ARX operations, and round permutation, offering resistance against weak key attacks and efficient parallel implementation. Performance evaluations show that BRIGHT variants meet the Strict Avalanche Criteria (SAC), exhibit strong key sensitivity, and achieve superior performance in terms of speed, memory usage, and execution time compared to existing lightweight ciphers such as SPECK and RoadRunner. The cipher’s efficiency and compact size make it highly suitable for IoTs devices, where low-power consumption and memory constraints are critical.
BRIGHT is optimized for 32-bit software-based applications, making it less suitable for hardware implementations. Its computational complexity and memory usage vary across variants, and while secure against known attacks, its resistance to emerging cryptanalysis techniques remains unverified. Additionally, key whitening plays a crucial role in security, and performance on lower-bit architectures needs further evaluation.
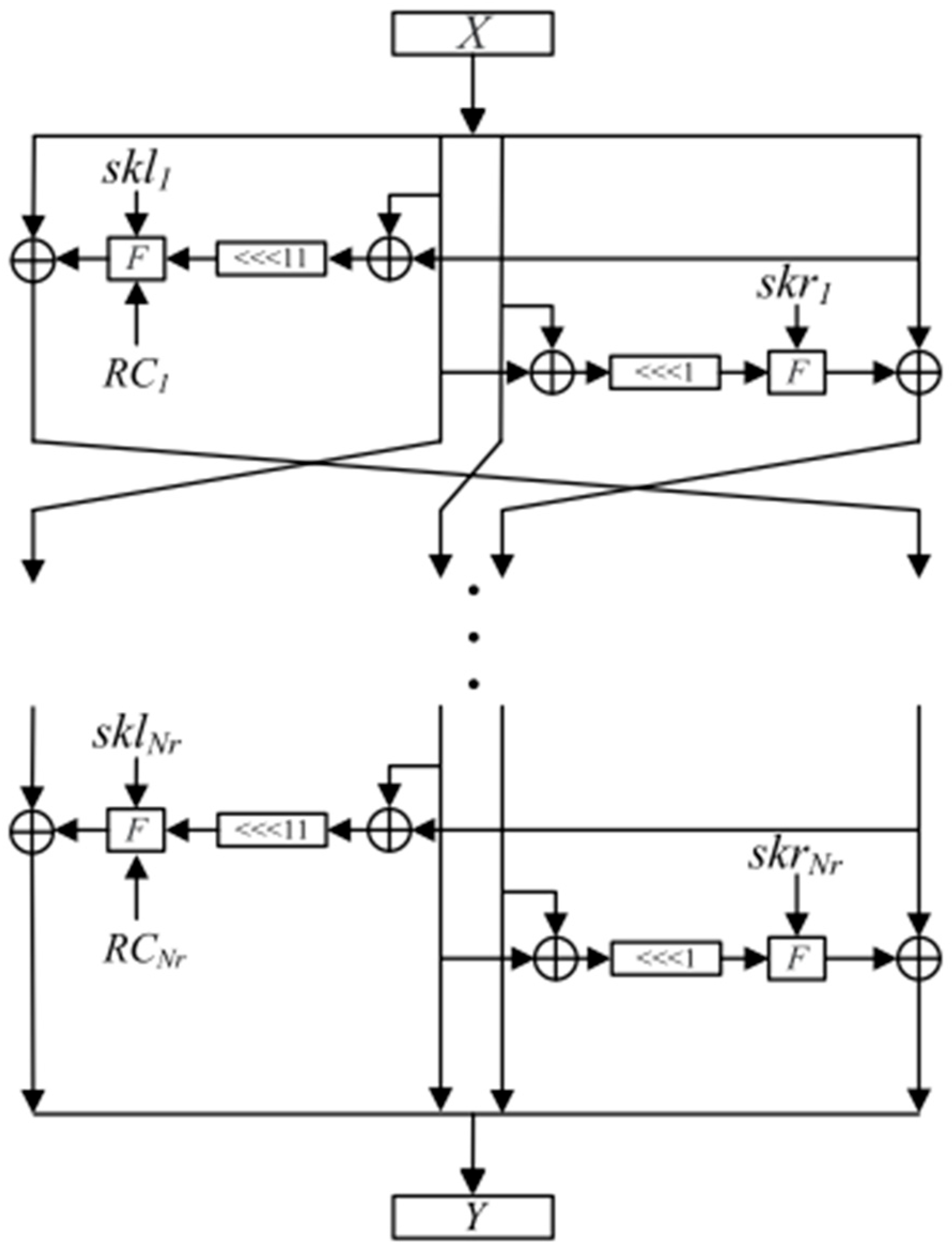
The paper introduces LiARX [
54], an LWBC designed using the ARX architecture and the Long Trail Strategy (LTS), suitable for resource-constrained devices such as RFID tags and sensors. It discusses the fundamental characteristics of lightweight cryptography, emphasizing small block sizes and simple round functions to optimize performance and reduce resource usage. The ARX-based LiARX cipher aims to provide both efficiency and security against cryptographic attacks. The cipher design incorporates MARX-2 as the ARX box, a linear mixing layer as indicated in
Figure 39, and a key schedule inspired by the generalized Feistel structure. Empirical results demonstrate LiARX’s competitive performance, surpassing existing ciphers such as LED in efficiency and closely matching SPECK in terms of resource consumption, making it a promising candidate for low-power IoTs applications.
One limitation of the LiARX cipher lies in its reliance on the ARX architecture, which, while efficient and resistant to certain side-channel attacks, still faces challenges against differential and linear cryptanalysis, particularly in the absence of traditional S-boxes. The use of ARX-based design strategies, while minimizing look-up tables and reducing memory requirements, limits its ability to provide robust non-linearity, making it potentially vulnerable to sophisticated attacks that exploit weak points in the ARX transformations. Furthermore, the cipher’s security relies heavily on the effective design of the ARX boxes and the linear layers, which can be difficult to optimize without increasing complexity or compromising performance.
DABC [
55] (Dynamic ARX-based Lightweight Block Cipher) is designed to address several weaknesses in traditional ARX-based ciphers, particularly their poor diffusion and static structures. By combining ARX operations with a dynamic permutation layer based on the generalized two-dimensional cat map, DABC enhances the diffusion effect and improves resistance to attacks. The cipher alternates between NAND and AND gates in its round functions, as evidenced by
Figure 40, to further increase security without excessive hardware resource consumption. It features a round-based architecture that supports both 96-bit and 128-bit keys, and its implementation on FPGA and ASIC platforms demonstrates high throughput and low resource usage. DABC’s performance is competitive, particularly in terms of hardware efficiency and security, making it suitable for resource-constrained IoTs devices.
A limitation of DABC is its reliance on the ARX-based structure, which, although efficient, may still be vulnerable to certain advanced cryptanalytic techniques such as differential and linear attacks, despite its improved diffusion and dynamic components. While the dynamic permutation layer enhances the cipher’s security by introducing greater uncertainty, it also adds complexity to its analysis. Furthermore, the cipher’s performance in resource-constrained environments could be impacted as the number of rounds increases or when adapting it to higher security requirements, potentially leading to greater hardware resource consumption.
SAECHAM [
56] is a variant of the ARX-based block cipher CHAM64, designed to improve both encryption speed and security. By altering the order of operations and adjusting the rotation amounts in CHAM64, SAECHAM reduces the number of operations, resulting in faster encryption on platforms such as AVR, MSP430, ARM Cortex-M3, and Cortex-M4. The cipher supports a 64-bit block size and a 128-bit key, with 88 rounds of encryption. SAECHAM outperforms CHAM64 in speed, demonstrating up to 14.7% faster performance on MSP430 and up to 33.2% faster on ARM Cortex-M4. Additionally, it shows improved resistance to both differential and linear cryptanalysis. The cipher is particularly suited for resource-constrained environments such as IoTs devices while maintaining strong security.
A limitation of SAECHAM is its reliance on the ARX structure, which, while efficient, may still be vulnerable to certain cryptanalysis techniques, particularly as cipher complexity increases. The reduction in operations achieved by adjusting rotation amounts, although improving speed, might result in potential trade-offs in security under advanced attacks. While SAECHAM improves CHAM64’s performance and security, the design may still face challenges when scaled to larger block sizes, such as in CHAM128/*, where finding the optimal differential or linear trail remains an open problem.
SAND-2 [
57] is an optimized version of the ARX-based LWBCSAND, designed to address performance issues such as slow diffusion and ineffective rounds in certain conditions. The improvements include replacing AND operations with NAND operations and introducing dynamic round functions. The cipher also benefits from linear permutations P1 and P2 in the round functions, as shown in
Figure 41, enhancing the diffusion rate. As a result, SAND-2 achieves full diffusion in just 4 rounds, significantly faster than SAND, which requires 11 rounds. The new architecture also improves throughput by 10% and requires fewer hardware resources, making it well-suited for resource-constrained environments such as IoTs devices. Security analysis confirms that SAND-2 resists differential attacks more effectively, achieving higher security than its predecessor.
While SAND-2 improves upon SAND in terms of performance and security, its reliance on dynamic round function calls and the introduction of additional permutations can make the cipher more complex to analyze and implement, potentially increasing the overhead in specific applications. Furthermore, despite improvements in diffusion, SAND-2 may still face challenges under certain cryptographic attacks, especially as it is optimized for hardware efficiency. The increased complexity in the round functions, although enhancing security, could also pose implementation difficulties for low resource environments when compared to simpler cipher designs.
4.5. Hybrid
This paper presents a hybrid [
58] cryptographic algorithm combining the PRESENT block cipher and Salsa20 stream cipher as represented in
Figure 42, enhanced by a chaotic system to generate pseudo-random keys. The algorithm is designed for lightweight applications, particularly in constrained devices such as IoTs, where efficiency and security are critical. The hybrid approach aims to balance the computational speed and security of both cryptographic systems by reducing the number of rounds in the PRESENT cipher while leveraging Salsa20 for fast key stream generation. Additionally, the chaotic system increases the complexity of the generated keys, making them less predictable and enhancing the algorithm’s robustness against attacks. The proposed algorithm was evaluated using the NIST statistical test suite, showing a higher degree of randomness compared to the standard PRESENT cipher. The experimental results demonstrate that the hybrid algorithm performs efficiently with reduced execution times, offering a secure solution suitable for resource-limited devices.
The Hybrid PRESENT and Salsa20 algorithm has limitations, including a trade-off between security and speed, increased implementation complexity, and potential security weaknesses due to reducing PRESENT rounds from 31 to 20. While the chaotic system enhances key generation, its effectiveness against advanced attacks remains unverified. Additionally, the algorithm’s hardware efficiency and power consumption require further evaluation for ultra-low-power IoTs applications.
FeW [
59] is an LWBC designed for efficient encryption in software-based environments, with a 64-bit block size and 80/128-bit key lengths. It combines a Feistel and generalized Feistel structure, referred to as Feistel-M, to enhance security against cryptanalytic attacks, such as differential, linear, impossible differential, and zero correlation attacks. The cipher operates in 32 rounds and utilizes a round function with two weight functions (WF1 and WF2) to improve the cipher’s resistance to cryptanalysis. FeW employs a key schedule similar to the PRESENT cipher, ensuring strong security for both 80-bit and 128-bit keys. Its efficiency is enhanced by the use of a 4x4 S-box and cyclic shifts, with the decryption algorithm using the same round function as encryption but in reverse. Security analysis shows that FeW is resistant to multiple attacks, including differential and linear cryptanalysis, and achieves high resistance with a lower probability of successful attacks as rounds increase.
FeW has high computational and key schedule complexity, potentially leading to higher energy consumption. While resistant to known attacks, its security against advanced attacks is unverified. Additionally, real-world performance data in constrained environments is limited.
ECLBC [
60] is an LWBC designed for IoMTs (Internet of Medical Things) applications that prioritizes both security and reliability, addressing the challenges posed by channel interference in resource-constrained environments. The cipher incorporates error detection and correction mechanisms, ensuring the integrity of transmitted ciphertext. ECLBC transitions from a Feistel structure to a substitution-permutation network (SPN) and integrates the AND-rotation-XOR (AND-RX) operation to strengthen security while optimizing resource usage. The cipher supports error detection and correction through linear block codes, ensuring that data corruption due to interference can be identified and corrected. Performance analyses, including ASIC hardware implementation, show that ECLBC provides robust security with a high avalanche effect and resistance to cryptanalytic attacks, including differential, linear, and related-key differential cryptanalysis. Additionally, ECLBC achieves a balanced trade-off between security and resource efficiency, making it an effective solution for IoMT devices that require secure and reliable data transmission.
The primary limitation of ECLBC is its lack of dynamic responsiveness, meaning it cannot adapt in real time to changing security threats or environmental conditions. This constraint stems from its design focus on ultra-low resource environments such as IoMT, where dynamic adaptability would require extra computation, memory, and communication resources that such devices typically cannot afford. As a result, while ECLBC achieves a strong balance between security and reliability, it may require additional external mechanisms to handle evolving threat landscapes or perform real-time adjustments.
SFN [
61] is an LWBC that integrates both the SP network structure and the Feistel network structure to enhance encryption efficiency and security. By using a 96-bit key and a 64-bit block size, SFN employs a novel encryption method that leverages both network structures for key expansion and encryption or decryption. The control signal from a 32-bit key allows for 232 different operation modes, improving the cipher’s resistance to attacks such as differential, linear, meet-in-the-middle, impossible differential, and integral attacks. SFN’s round function includes components such as AddRoundKey, S-box layers, MixColumns, MixRows, and MixXors, which collectively improve the security and efficiency of the cipher. It is shown to be compact in hardware (1876.04 GE) and efficient in software, making it suitable for constrained environments such as IoT.
One limitation of SFN is the complexity introduced by using both SP and Feistel network structures, which, while enhancing security, could lead to higher resource usage in certain hardware environments compared to simpler designs. Although SFN performs well in terms of security against multiple types of cryptographic attacks, its performance might suffer in highly resource-constrained settings that require faster encryption or lower power consumption. The hybrid nature of SFN also increases the implementation complexity, which could make it harder to optimize for specific applications or adapt to evolving security requirements without significant modifications.
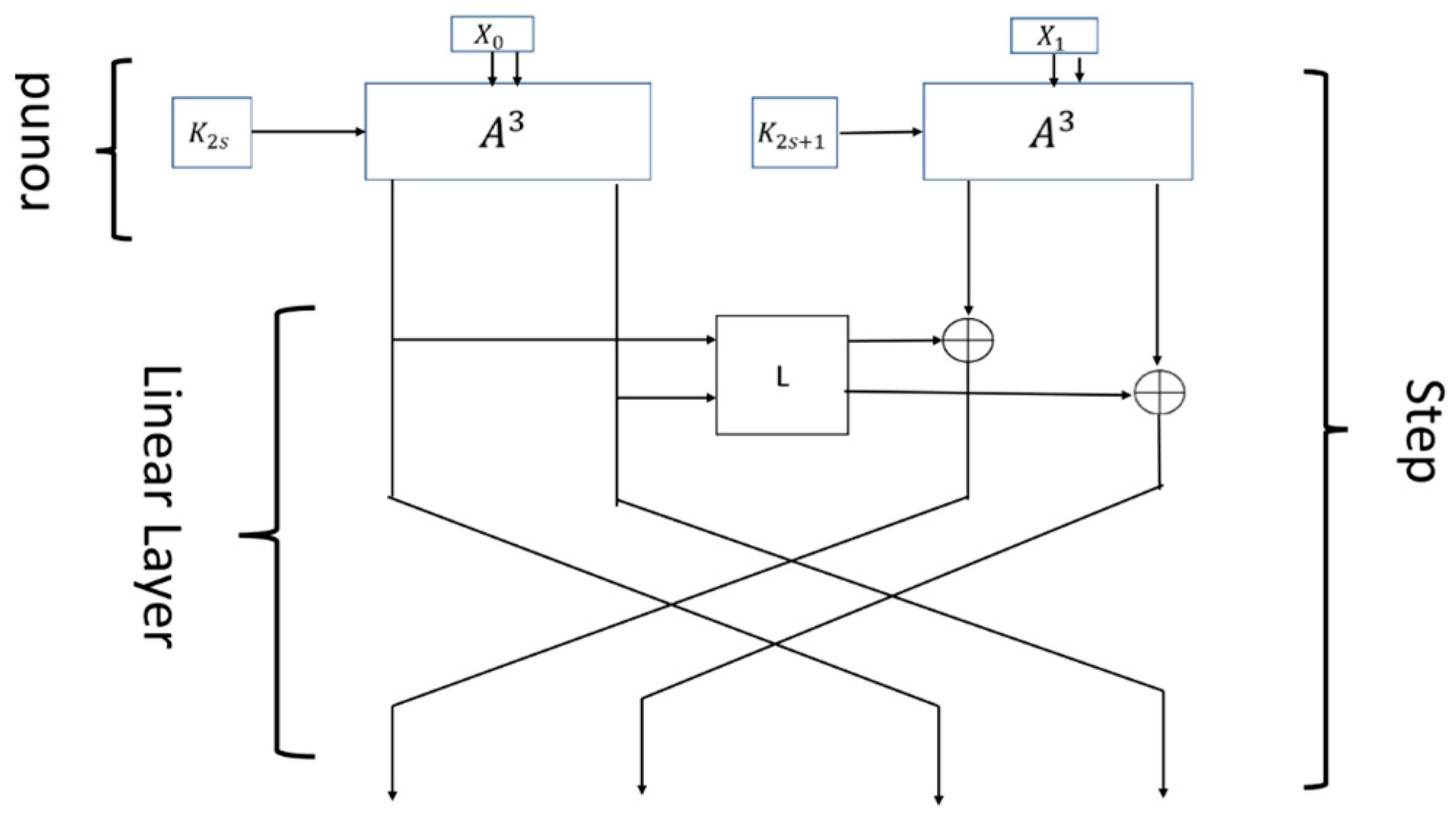
GFRX [
62] is an LWBC designed for resource-constrained IoTs devices, combining a generalized Feistel structure with ARX (addition or AND, rotation, XOR) operations to enhance diffusion and hardware efficiency. Unlike traditional Feistel structures, which process only half the data per round, GFRX uses four branches and alternates between two ARX-based functions (FAN and FAD) to achieve strong diffusion in fewer rounds. It supports various block/key size combinations (e.g., 64/128 bits) and achieves the avalanche effect within 6 rounds, indicating fast diffusion. GFRX reuses its encryption structure for decryption and key expansion, reducing hardware cost. Hardware evaluations show excellent performance, requiring as little as 886 GE in fully serialized ASIC implementations and outperforming many existing lightweight ciphers such as PRESENT and SIMON in both area and efficiency. Its security is validated up to 19-round differential and 13-round linear attacks, offering a good balance of security, performance, and flexibility for IoTs environments.
Despite its efficiency and strong diffusion, the GFRX algorithm has a few notable limitations. Its use of ARX-based round functions introduces lower throughput due to the serial generation of round keys, which can slow down performance in high-speed environments. Additionally, while the design simplifies hardware implementation, its security margin is relatively narrow, with effective differential and linear attacks reaching up to 19 and 13 rounds, respectively, leaving less buffer against future cryptanalytic advances. Furthermore, the structure is highly hardware-oriented, potentially reducing performance and flexibility in software or mixed platforms. These factors may limit GFRX’s applicability in use cases demanding high-speed, scalability, or long-term cryptographic strength.
SIMECK-T [
63] is an ultra-LWBC tailored for software-oriented, resource-constrained environments such as IoTs and embedded systems. It is a hybrid design combining the efficient ARX (addition, rotation, XOR) structure of SIMECK and TEA ciphers. The core innovation lies in embedding multiple TEA rounds within SIMECK rounds, effectively enhancing randomness and cryptographic strength while minimizing reliance on substitution boxes. This approach allows SIMECK-T to maintain strong resistance to various cryptanalytic attacks—validated by NIST SP800-22, AIS.31, and the Law of Iterated Logarithm (LIL)—and achieve excellent performance on low-power devices such as the Raspberry Pi Pico. The cipher also supports secure key derivation and initialization vector (IV) generation using PBKDF2, making it suitable for secure file encryption. Its design avoids the use of lookup tables, reducing vulnerability to side-channel attacks and memory overhead, thereby offering a fast, compact, and secure solution for modern lightweight encryption needs.
While SIMECK-T is highly optimized for lightweight, software-based encryption, it has several limitations. First, its security relies on a relatively small number of rounds (e.g., 3 SIMECK rounds with 5 embedded TEA rounds), which—though empirically sufficient—may offer a narrower security margin compared to more conservative cipher designs. Second, its performance is optimized specifically for 64-bit microcontrollers, potentially limiting efficiency on systems with different architectures. Third, although it avoids substitution boxes to minimize memory usage, this lack of dynamic substitution layers could reduce confusion compared to S-box-based designs. Lastly, while SIMECK-T passes standard randomness tests, its resilience to future cryptanalysis remains to be thoroughly validated over time, especially as it depends on ARX structures that could be vulnerable to emerging attack methods.
NDN [
64] is a hybrid LWBC combining SPN and Feistel structures, supporting 64-bit blocks with 80- and 128-bit keys over 12 and 18 rounds, respectively. It incorporates dynamic round functions, a high diffusion key schedule, and 4 × 4 S-boxes, ensuring strong non-linearity and resistance to known cryptanalytic attacks. Its innovative DFFT-based permutations and primitive polynomial transformations enhance key diffusion and scalability. Hardware implementation on 0.13 μm ASIC shows GE of ~1068 (NDN-80) and ~1272 (NDN-128), while software benchmarks on AVR microcontrollers confirm low memory footprint and fast execution, making NDN well-suited for both low-power and high security IoTs environments.
While NDN offers strong theoretical security and efficient performance, its evaluation primarily relies on internal analysis without independent third-party cryptanalysis. The absence of public cryptanalytic challenges or open-source implementations limits reproducibility and peer validation. Moreover, although the cipher demonstrates competitive GE and speed, there is limited discussion on side-channel resistance or fault attack tolerance. The dual-round structure, while efficient, may also introduce complexity in hardware pipeline optimization. Future studies are needed to assess its resilience in real-world adversarial settings and broader platform adaptability.
RAZOR [
65] is a newly proposed LWBC designed specifically for software-oriented IoTs applications. It combines the Feistel structure and substitution-permutation network (SPN) in a hybrid round function and utilizes 4-bit S-boxes along with a diffusion function based on rotation and XOR operations. This design achieves strong resistance to differential, linear, impossible differential, and related-key attacks. RAZOR demonstrates improved security compared to other lightweight ciphers such as PRESENT, Rectangle, LBlock, GIFT, and SCENERY, notably achieving the highest number of active S-boxes in a 5-round differential analysis (21 S-boxes). The cipher offers an average software throughput of 1.47 MB/s and passes standard statistical and avalanche tests, proving its randomness and effectiveness for securing resource-constrained IoTs devices.
Despite its strong security and efficiency in software environments, RAZOR has limitations in hardware implementations. The use of rotation and XOR operations in its diffusion layer, although optimized for software, is less efficient in hardware compared to simpler bit-permutation techniques commonly used in other lightweight ciphers. This could restrict RAZOR’s suitability for ultra-low resource or hardware-constrained environments. Additionally, while its security is validated against several attacks up to a specific number of rounds, its resilience beyond 10–15 rounds in the presence of advanced cryptanalytic techniques remains theoretical and would benefit from further empirical validation.
SPISE [
66] is an LWBC designed specifically for ultra-constrained environments such as RFID tags and wireless sensor networks. It employs a hybrid structure combining generalized Feistel network (GFN) and SPN-like fast diffusion, which enhances its security and efficiency. Supporting a 256-bit data block and a 258-bit key (including 2 control bits for subkey selection), SPISE replaces traditional S-boxes with bit-jumbling and permutation techniques, achieving confusion and diffusion with minimal logic. Its gateless key schedule is compact and efficient, modeled on Rubik’s Cube-style operations. Notably, SPISE achieves just 728 gate equivalents (GEs)—one of the lowest recorded for such high data and key lengths—along with a fast delay of 1.364 ns and low-power consumption of 32.16 µW, making it highly suitable for secure low-power embedded systems.
While SPISE boasts excellent hardware efficiency and strong resistance to major cryptanalytic attacks, it does carry certain practical limitations. Its use of a non-conventional S-box-free design—relying entirely on bit-jumbling and control-based key scheduling—may pose challenges for integration with cryptographic systems that expect more traditional SPN or Feistel structures with well-analyzed components. Additionally, its large block and key sizes (256 bits), while advantageous for future-proof security, may not align well with the needs of ultra-low latency or bandwidth-sensitive IoTs applications where 64- or 128-bit configurations are more common. Hence, while SPISE offers strong security and compactness, its high parameter sizes and unconventional operation flow might limit adoption in certain scenarios without further adaptation or standardization.
GFSPX [
67] is a 64-bit LWBC with a 128-bit key, designed for resource-constrained IoTs nodes. It uses a hybrid structure combining generalized Feistel network (GFN) and SPN architecture to overcome the diffusion limitations of classical Feistel ciphers. GFSPX introduces a dual-round function: F1 uses ARX (addition, rotation, XOR) operations for simplicity and efficiency, while F2 employs compact 4 × 4 S-boxes and a P-layer for strong diffusion. The cipher achieves strong avalanche properties in just 6 rounds and demonstrates robust resistance to differential, linear, algebraic, structural, and key schedule attacks. Its hardware implementation cost is only 1715 gate equivalents (GEs) on a 0.13 μm process, making it more efficient than PRESENT (1886 GE) and many SPN-based ciphers. GFSPX also performs well in software, reaching an encryption speed of 12.31 Mb/s, showing suitability for both hardware and software applications in lightweight environments.
Despite its strong performance and low area cost, GFSPX has some limitations. While its hybrid GFN–SPN structure enhances diffusion and reduces round count, this added architectural complexity increases design and verification overhead compared to simpler Feistel or pure ARX designs. The key schedule, involving circular shifts, S-box substitutions, and round-dependent constants, is more intricate, which may challenge implementation on ultra-constrained microcontrollers with very limited code space. Additionally, although GFSPX strikes a balance between security and efficiency, its GE count (1715), while lower than many SPN ciphers, is still slightly higher than ARX-based or simplified GFN ciphers such as GFRX (1496 GE) or SPNRX (1357 GE), which may matter in ultra-minimalist chip designs. Thus, while GFSPX is highly optimized, there’s still room for further simplification or specialization in extreme low-power IoTs contexts.
QLW [
68] is a 64-bit LWBC with a 128-bit key, designed to achieve high diffusion using a hybrid structure that combines a type-III generalized Feistel structure (GFS) with Lai–Massey elements. Its round function incorporates a double half-round mechanism, dynamic round constants, and a genetic algorithm-optimized 4 × 4 S-box with an area of only 15.01 GE. The entire cipher achieves full diffusion in just two rounds, enhancing resistance to differential and linear attacks. Hardware implementation on the SMIC 0.18 μm process shows that QLW requires 1655.26 GE and consumes only 7.37 μJ/bit, making it more area- and energy-efficient than similar ciphers such as PRINCE, CRAFT, and SKINNY.
Despite its strong security margins and hardware efficiency, QLW’s evaluation lacks independent third-party cryptanalysis or open-source implementations. The complexity introduced by the dynamic round constant and non-linear key schedule, while enhancing diffusion and unpredictability, may increase implementation difficulty in constrained environments. Additionally, no detailed analysis is provided for side-channel or fault attack resistance, which may limit adoption in high-assurance or critical IoTs applications.