A Lightweight Image Cryptosystem for Cloud-Assisted Internet of Things
Abstract
1. Introduction
1.1. Motivation
1.2. Contribution
- i.
- The use of an S-box and bit permutation techniques to achieve the confusion and diffusion properties of the cryptography algorithm was replaced with the use of the XOR function and bit permutation.
- ii.
- A hash algorithm was introduced to make the cryptosystem sensitive to both changes in the key and plain image bits.
- iii.
- The innovations (i) and (ii) were applied to design a new lightweight image cryptosystem.
2. Literature Review
3. Materials and Methods
3.1. Proposed Lightweight Image Cryptography Algorithm
- i.
- Bit grouping layer: The bits in A are grouped into two equal parts, L and R, each of size (n/2) bits.
- ii.
- XOR operation layer: A bitwise XOR operation is carried out on L and R, according to Equation (3), to form an array of xorbit and the bits in R is concatenated to xorbit to form xorbitR, which has n bits. The symbol represents concatenation in Equation (4).
- iii.
- Bit permutation: This layer takes the permutation key, permkey, and xorbitR as inputs. Permkey contains an array of random integers with size n. The value of integers in permkey ranges between 0 and n − 1. Each bit of xorbitR is rewritten according to Equation (5).
| Algorithm 1: Encryption module (block, permkey) |
Output: encblock
|
| Algorithm 2: encreshufflement (blockbits, permkey) |
Output: rblockbit
|
- Random key generation: An array of random integer, PERMkey, is generated using the key. Given an image A with dimension , the image A is converted into a grayscale image, grayA, of dimension . If a > b, the size of PERMkey will be a; otherwise, the size of PERMkey will be b.
- ii.
- Random image generation: the bytes of grayA and that of the key are combined together to form Cbyte. Cbyte is made to pass through SHA−256. The first k bits of the output of SHA−256, where k is the block size, is selected as the shavalue. The shavalue is encrypted using the encryption module and the output is used as the seed to generate the pixels of a random image, Randimage. The size of Randimage is equal to the size of grayA. A bitwise XOR operation is carried out between Randimage and grayA to form interimage.
- iii.
- Cipher image generation: The generation of cipherimage is carried according to Equations (6) and (7), where nrows and ncols represent the quantity of rows and columns in the interimage, respectively. Equations (6) and (7) outline the description of how the bits of interimage are manipulated along the rows and columns of the image, respectively, to form an encrypted image.
| Algorithm 3: Encryption process (pimage, K) |
Output: encimage
|
| Algorithm 4: Decryption module (encblock, permkey) |
Output: decblock
|
| Algorithm 5: Decryption process (cimage, hasvalue, key) |
Output: decimage
|
| Algorithm 6: Decreshufflement (blockbits, permkey) |
Output: im
|
| Algorithm 7: Generate random seed (key) |
Output: randomseed
|
3.2. Metrics and Methods of Analysis of the Proposed Lightweight Image Cryptosystem
3.2.1. Metrics Used for the Analysis of the Proposed Algorithm
- Encryption quality (EQ): Given the plain image P and its equivalent cipher image C each with the equal size M × N, the gray values of pixel P(I,j) and C(i,j) in P and C range from 0…255. If and represent the occurrence of each gray value, L, in P and C, respectively, then, Equation (8) gives the encryption quality of the cryptosystem. The higher the value of EQ, the better the |EQ of the cryptosystem.
- Mean square error (MSE): This metric measures the distance between the input P and the output C, where P and C represent the plain and cipher images of size MN, respectively. A cryptosystem with a high value of MSE indicates a better encryption quality. Mathematically, the MSE of images P and C with pixels and at grid location is outlined by the formula in Equation (9). When the MSE is used as a metric for measuring the quality of the decrypted image, the image C in Equation (9) is replaced with the decrypted image D. In this scenario, the value of the MSE should be low for a good decryption algorithm.
- Peak signal-to-noise ratio (PSNR): The PSNR is a standard way of measuring image fidelity. It compares the quality of the cipher image C with that of the plain image P. Mathematically, PSNR is defined by Equation (10), where represents the highest image pixel value. A secure cryptosystem is expected to produce low values of the PSNR; the low value indicates a great difference between P and C. In the case of comparing P and a decrypted image, the value of PSNR is expected to be infinity for a good cipher.
- Structural similarity index measure (SSIM): SSIM values range from −1 to +1. A value of +1 signifies a similarity between two images, whereas a value of −1 implies a dissimilarity of the two images. The SSIM compares the two images based on their luminance, , which represents the average of all the pixel values. In contrast, , which represents the standard deviation of all the pixel values, can be implemented to uncover the structural characteristics of the images, which are obtained by applying the following formula: where P is the input image. The SSIM between images P and C can be found by applying the formula in Equation (11), where and are constant to steady division with the feeble denominator.
- v.
- Normalized cross-correlation (NCC): NCC is a widely accepted metric for measuring similarity between the two images P and C. The value of NCC ranges from −1 to 1. The value −1 implies that there is strong correlation between P and C, while the value 1 indicates that there is no strong correlation between P and C. NCC is also used in measuring image quality in image processing. Pixels of plain image P and that of the cipher image C should lack a correlation. Hence, it is expected that the NCC between P and C should be close to 1 for a good cipher. There should be a strong correlation between the pixels of P and that of the decrypted image D obtained from the decryption of C. Hence, the NCC value obtained when P and D are used as the inputs should be close to −1. Equation (12) details the mathematical description of NCC:
- vi.
- Mean absolute error (MAE): The MAE can be used in the determination of an image’s quality and the resistance of an image cryptosystem to differential attacks. An image cryptosystem is considered secure if the value of MAE is greater than 75; otherwise, the cryptosystem is said to be insecure. When comparing cryptosystems, a cryptosystem that has a higher value of MAE is said to be more secure. When considering the quality of the plain image and decrypted image obtained from the decryption of the cipher image, a cryptosystem that has the lower value of MAE is said to produce a higher quality image than the one with a higher value of MAE. Equation (13) represents the formula for determining the MAE of a cryptosystem:
- vii.
- Normalized absolute error (NAE): NAE is a metric that can be used to compare the quality of an image with that of a reference image. If the value of NAE is high, it means that the image quality is low. A low value of NAE implies a higher quality of the image. Equation (14) represents the formula for calculating the NAE between the reference image P and image C.
- viii.
- Maximum difference (MD): The MD is determined by obtaining the maximum value when corresponding pixels at grid location (i,j) of plain image P and the cipher image C are subtracted from each other, as shown in Equation (15). A higher value of the MD indicates a significant difference between P and C. Hence, a cryptosystem with a higher value of MD is said to be more secure than the one with a lower value. In the case of consideration of P and the decrypted image D obtained from the decryption of C, a lower value of the MD is desirable. A cryptosystem with a lower value of the MD between the plain image and the decrypted image is said to be better, as a lower value indicates that there is no substantial alteration between the two images. The formula for finding the MD is outlined by Equation (15).
- ix.
- Average difference (AD): A higher value of the AD, that can be obtained when the plain image P and the cipher image C are used for the computation, signifies that the image cryptosystem is secure, while a low value implies a less secure cryptosystem. In the case of the computation of the AD between P and the decrypted image D, which can be obtained when C undergoes the decryption process, a lower value of AD implies a better quality of the decrypted image, while a high value indicates that the decryption process cannot obtain an image that is similar to P from C. Equation (16) represents the formula for determining the AD between the two images P and C, where and represent the pixels at grid location (i,j) of P and C, respectively.
- x.
- Structural content (SC): SC is another metric that can be used to measure the image quality. The image quality of a processed image, Pm, is a measure of the degradation of pm when compared to an ideal image, P. Achieving a value of 1 for the SC indicates a high quality of Pm, while a higher value indicates a low quality of Pm. For a good cryptosystem, when the cipher image Pm is compared with the original image P, it is expected that the value of SC should be high for the cipher to be regarded as secure. When the decrypted image D is compared to P, it is expected that a good cryptosystem should provide a SC of 1 in order for the cipher to be rated as being able to retrieve the exact copy of P from the cipher image Pm. Equation (17) represents the formula for calculating the SC between the original image P and the processed image (cipher/decrypted) Pm.
- xi.
- Two-dimensional correlation coefficient (2DCC): The 2DCC can be used to calculate the similarity or difference between two images. If the value of the 2DCC is small (or zero), the two images are said to be different. A large value of the 2DCC implies that the two images are similar. Equation (18) represents the formular for finding the 2DCC between two images P and C.
- xii.
- Differential cryptanalysis: The net pixel change rate (NPCR) [51] and the unified average change intensity (UACI) [52] are the commonly used metrics for measuring the resistance of a cipher to cryptanalysis attack between two images P and C. The ideal values of the NPCR and UACI, according to the authors of [53], are 99.6093% and 33.4635%, respectively, for the differential cryptanalysis-resistant cipher. The formulae for determining the NPCR and UACI are given in Equations (19) and (20), respectively:
- xiii.
- Histograms are graphical representations of the distribution of gray levels in the pixels of images [54]. Ciphertext images always have a uniform distribution of pixels; in the case of a plaintext image, these pixels are jerky. A uniform histogram of a cipher image therefore indicates a secure encryption scheme [55]. A Chi-square test was carried out to validate the histogram’s uniformity. The formula for calculating the uniformity of histograms is given by Equation (21):
- xiv.
- Adjacent pixels correlation coefficient: The correlation coefficient of adjacent pixels in an image can be calculated by applying Equation (22) [56]:
- xv.
- The statistical measure that was used to test the entropy of the proposed image cryptosystem is given by the formula in Equation (23):
3.2.2. Methods of Analysis
- i.
- Procedure for simulation analysis: ‘airplane.tiff’,’baboon.tiff’,’boat.tiff’,’lena.tiff’, and ‘pepper.tiff’ were retrieved from the USC-SIPI image database (http://sipi.usc.edu/database/) for simulation purposes. Each of the images was converted into a grayscale image. Each of the grayscale images was made to pass through an encryption algorithm of the proposed image cryptosystem to obtain a cipher image. Each of the obtained cipher images was also made to pass through the decryption algorithm of the proposed image cryptosystem to ascertain whether or not the decryption process is able to recover the original image from the cipher image.
- ii.
- Procedure for encryption/decryption quality analysis: In order to justify the claim as per the quality of the images produced by the encryption and decryption processes and the security of the proposed cryptosystem, metrics 1–10 were used. For EQ, the images produced by the encryption process were compared with the original images. For DQ, the images produced by the decryption process were compared with the original images.
- iii.
- Procedure for system sensitivity analysis: Key sensitivity and plain image sensitivity were used to test the system’s sensitivity via the following statistical procedures:
- a.
- Key sensitivity: A key, K, was randomly generated. A single bit at a random location within the bits of K was flipped to obtain another key, K1. The keys K and K1 were used in turns to encrypt the image P to obtain the cipher images C and C1, respectively. Metrics 3–11 were used to compare C and C1. This procedure was repeated for each of the test images.
- b.
- Plain image sensitivity: A key, K, was randomly generated. A single bit within the bits of an image P at a random location was flipped to obtain another image, P1. Both the P and P1 images were encrypted using key K to obtain the cipher images C and C1, respectively. Metrics 3–11 were used to compare C and C1. This procedure was repeated for each of the test images.
- c.
- Cipher image sensitivity: A key, K, was randomly generated. A plain image, P, was encrypted using the proposed image encryption algorithm to form the cipher image, C. A single bit within the bits of image C was flipped at a randomly selected location within the bits of image C to obtain another cipher image, C1. Both C and C1 were decrypted using the decryption algorithm of the proposed image cryptosystem and key K to obtain the decrypted images D and D1, respectively. Metrics 3–11 were used to compare D and D1. This procedure was repeated for each of the test images.
- iv.
- Statistical analysis procedure: The purpose of statistical analysis is to test the algorithm in order to ascertain its resistance to statistical attacks. Histograms, the adjacent pixel correlation coefficient, and entropy analysis were employed in this case as follows:
- a.
- Histogram analysis procedure: For each of the test images, histograms of the plain image and that of the cipher image were taken and the Chi-square test was used to verify the uniformity of each histogram.
- b.
- The adjacent pixel correlation coefficient: A thousand randomly selected pixels along the horizontal, vertical, and diagonal directions of each of the test images were plotted on scatter graphs for each direction. The same was conducted for each of the cipher images obtained from each test image. The correlation coefficient, in each case, was also calculated to verify the resistance of the cryptosystem against correlation coefficient attacks.
- c.
- Entropy analysis: Each of the test images were encrypted using the proposed encryption scheme. Entropy analysis, as specified by Equation (23), of both the plain and cipher images were measured.
4. Results and Discussions
| Processor | AMD E1−1200 APU with Radeon(tm) HD Graphics 1.40 GHz |
| Installed RAM | 4.00 GB (3.59 GB usable) |
| Device ID | E4C0446D−57F5−4475−8A60-F1D4A41F6048 |
| Product ID | 00331−10000−00001-AA508 |
| System type | 64-bit operating system, x64-based processor |
4.1. Discussion of Experimental Results
- i.
- Simulation results: Figure 3 shows the simulation results. The input images are shown in Figure 3a–e. The outputs of these images following their conversion into grayscale images are shown in Figure 3f–j. The resulting images when the images in Figure 3f–j are subjected to the encryption process are shown in Figure 3k–o, and Figure 3p–t represent the images recovered from the decryption of the images in Figure 3k–o. By visual inspection, the images in Figure 3k–o are very different from the images in Figure 3f–j. Comparing the images through visual inspection also shows that Figure 3f–j and Figure 3p–t are identical. These results reveal that HXP is capable of securing images and that the recovered images from the cipher images are of a high quality, such that mere visual inspection cannot detect any difference between the original image and the decrypted images.
- ii.
- Encryption quality of the HXP algorithm: The encryption quality of HXP was analyzed using the metrics one to eleven. Each cipher image C, in Figure 3k–o, was compared with their corresponding original image P, in Figure 3f–j, based on these metrics. Table 3 shows the results that were obtained. The high values of EQ, MSE, MAE, NAE, MD, and AD indicate that C is very different from P. Furthermore, the low values of the metrics PSNR, SSIM, NCC, and DCC establish the fact that C is very different from P. The inability of the algorithm to produce a value of one for the metric SC is also an indication that C is different from P. Overall, these results showed that the quality of C produced by the HXP algorithm is not of the same quality as that of P. This is an indication of a secure image encryption algorithm.
- iii.
- Decryption quality of HXP: Metrics two to ten were used to measure the decryption quality of HXP. The values of these metrics were compared with the ideal values of these metrics in order to ascertain the quality of the decrypted images. Table 4 shows the results of the evaluation. The first row shows the ideal value of each metric in the heading of the table, while the subsequent rows show the obtained value for each metric in the headings of the columns of the table when the images in Figure 3p–t were compared with the images in Figure 3f–j. From the results in Table 4, it is clear that the obtained values for all the tests images are just the same as the ideal value. These results show that the recovered images from the encrypted images have the same quality as the original images. Hence, the HXP algorithm has an excellent decryption quality.
- iv.
- System Sensitivity Analysis Results
- i.
- Key Sensitivity Analysis ResultsThe results of the key sensitivity analysis are shown in Table 5. As shown in Table 5, the values of PSNR, SSIM, NCC, and DCC were greatly reduced when compared to the ideal values when two images that were of the same quality were compared. These results show that the obtained cipher images are different and are not of the same quality. The high values of MSE, MAE, MD, and AD are indicators that the cipher images are very different. The values of the NPCR and UACI were very close to the ideal values expected of a cryptosystem that is resistant to differential cryptanalysis. These results show that a small change in the key causes an enormous change in the cipher images. Hence, HXP is key sensitive.Table 5. Results of key sensitivity analysis.
Image PSNR SC SSIM NCC DCC MSE MAE NAE MD AD NPCR UACI airplane.tiff 7.7493 1.0012 0.0055 0.0001 0.0001 10,918.08 85.2896 0.6693 255 42.6 99.6078 33.4469 baboon.tiff 7.7494 0.9982 0.0068 0.0013 0.0013 10,917.94 85.3712 0.6698 255 42.7691 99.6178 33.4789 boat.tiff 7.7504 1.0028 0.0073 0.0021 0.0021 10,915.36 85.3001 0.669 255 42.7253 99.6208 33.451 lena.tiff 7.7413 0.9995 0.0045 −0.001 −0.001 10,938.39 85.4321 0.6715 255 42.5178 99.6143 33.5028 pepper.tiff 7.7512 1.0012 0.0063 0.0013 0.0013 10,913.51 85.3219 0.6696 255 42.6955 99.6426 33.4596 - ii.
- Plaintext Sensitivity analysis and Results and ResultsThe results shown in Table 6 are the obtained results when the proposed cryptosystem was subjected to plaintext sensitivity analysis. As can be seen, the obtained results resembles the results that were obtained during the key sensitivity analysis. These results reveal that HXP is very sensitive to a slight change in the plain image.Table 6. Plain image sensitivity analysis results.
Image PSNR SC SSIM NCC DCC MSE MAE NAE MD AD NPCR UACI airplane.tiff 7.7561 0.9993 0.0075 0.0019 0.0019 10,901.08 85.2592 0.6679 255 42.6426 99.6025 33.435 baboon.tiff 7.7637 1.0024 0.0081 0.0028 0.0028 10,882.12 85.1354 0.667 255 42.6557 99.593 33.3864 boat.tiff 7.7586 0.9979 0.0078 0.0024 0.0024 10,894.76 85.1562 0.668 255 42.5446 99.5953 33.3946 lena.tiff 7.7697 0.9987 0.0094 0.0041 0.0041 10,867.12 84.9817 0.6671 255 42.4845 99.6162 33.3262 pepper.tiff 7.7388 1 0.0037 −0.0016 −0.0016 10,944.68 85.4524 0.6706 255 42.6269 99.6231 33.5107 - iii.
- Cipher Image Sensitivity AnalysisFrom the results shown in Table 7, it is obvious that HXP has a poor cipher image sensitivity. This is revealed from the values of PSNR, SC, SSIM, NCC, DCC MSE, MAE, NAE, MD, and AD, that were very close to the ideal values when two images of a similar quality were compared. These results revealed that there was no significant difference between the cipher image and the altered cipher image. This means that the two cipher images are of a similar quality. The obtained results for the NPCR and UACI were very far from the ideal values for the images that were different. Hence, HXP has a poor cipher image sensitivity. However, this poor cipher image sensitivity should not be seen as a weakness, as cipher image sensitivity and a chosen cipher image attack are not related. On the contrary, a cryptosystem that has a poor cipher image sensitivity is capable of resisting against certain noise interference. Hence, it can be said by these results that the proposed lightweight cryptosystem is resistant to some noise interference.Table 7. Cipher image sensitivity analysis results.
Image PSNR SC SSIM NCC DCC MSE MAE NAE MD AD NPCR UACI airplane.tiff inf 1 1 1 1 0 0 0 0 0 0.0004 0 baboon.tiff inf 1 1 1 1 0 0 0 0 0 0.0004 0 boat.tiff inf 1 1 1 1 0 0 0 0 0 0.0008 0 lena.tiff inf 1 1 1 1 0 0 0 0 0 0.0008 0 pepper.tiff inf 1 1 1 1 0 0 0 0 0 0.0004 0
- v.
- Statistical Analysis and Results
- i.
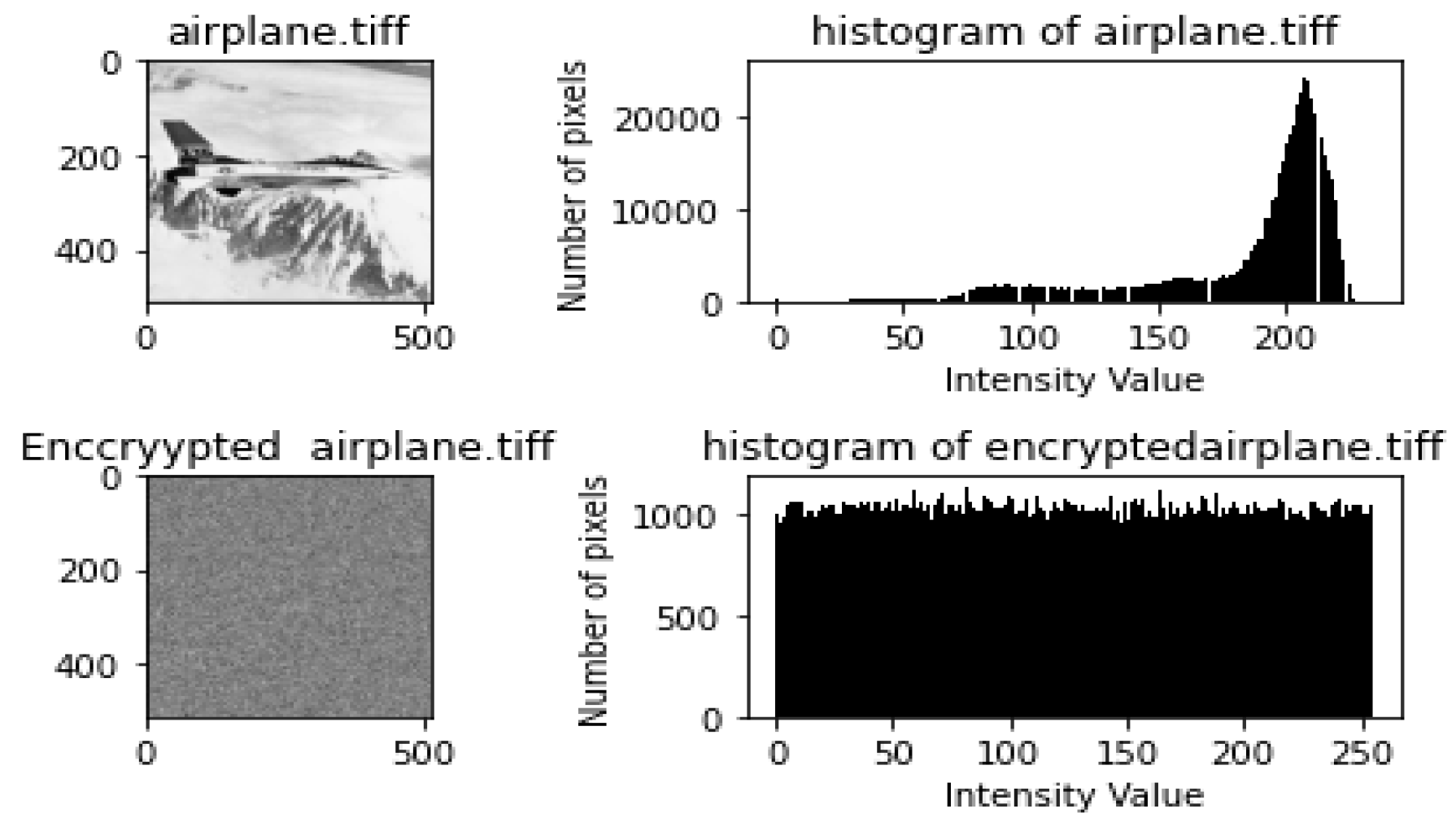
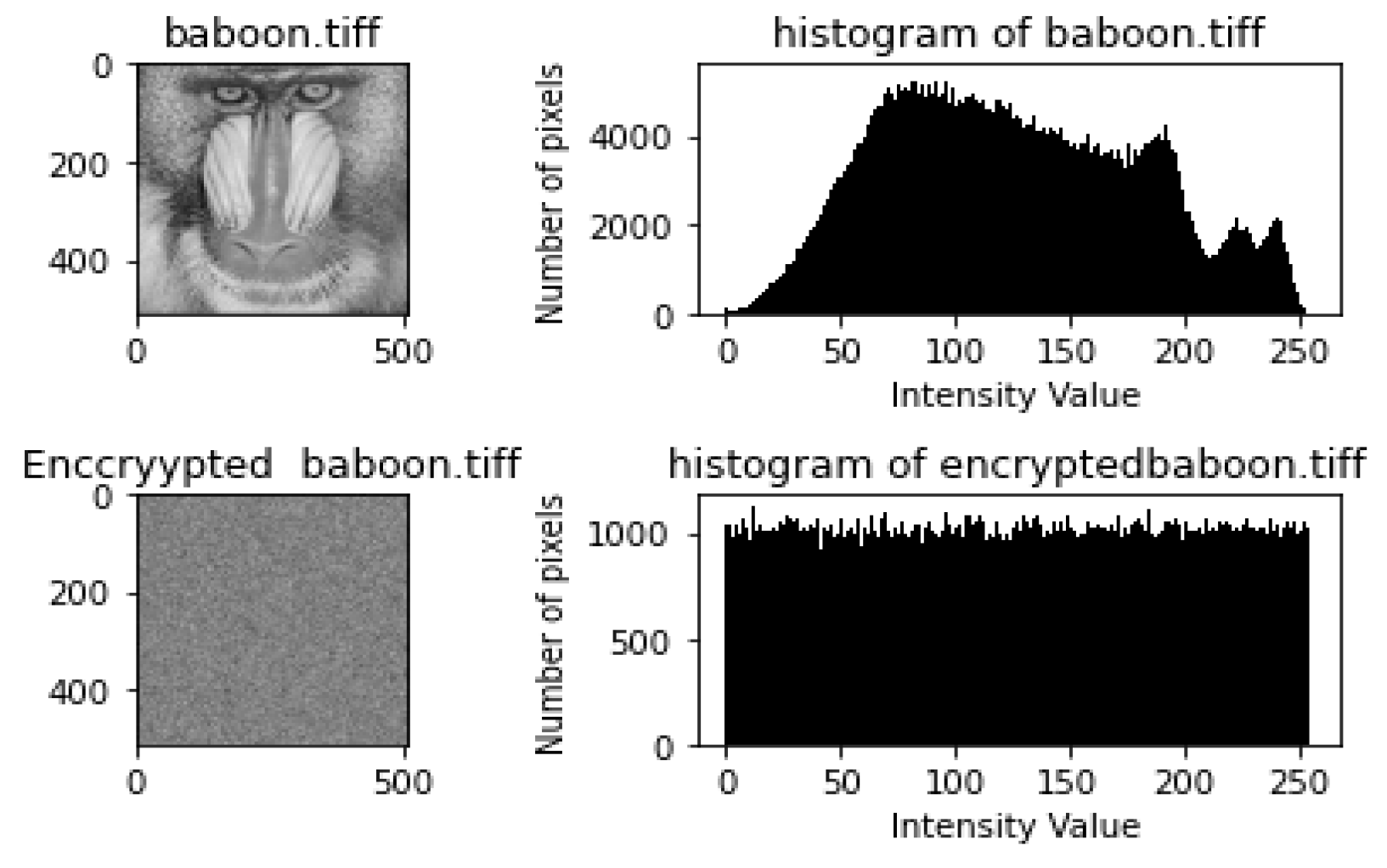
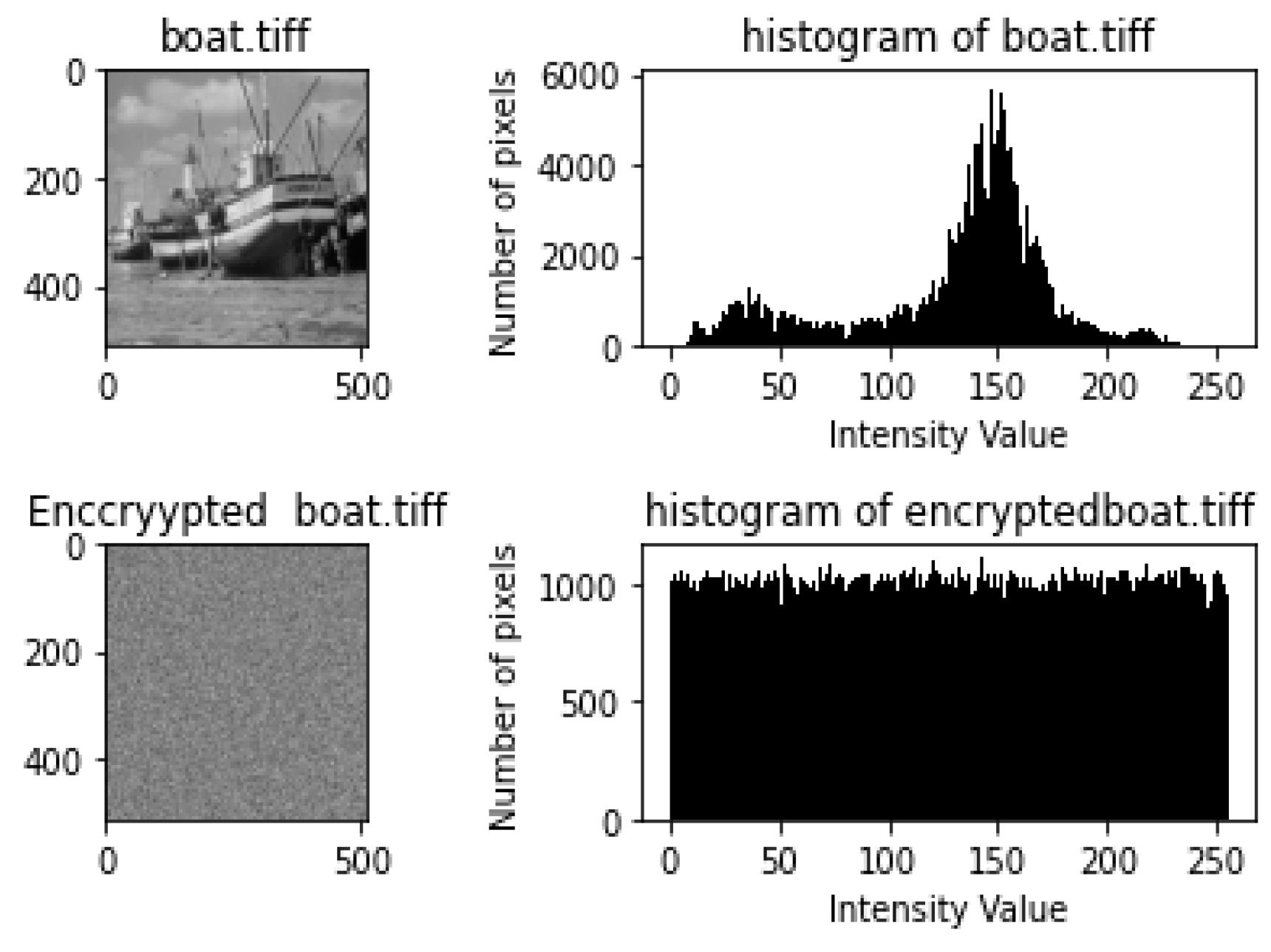
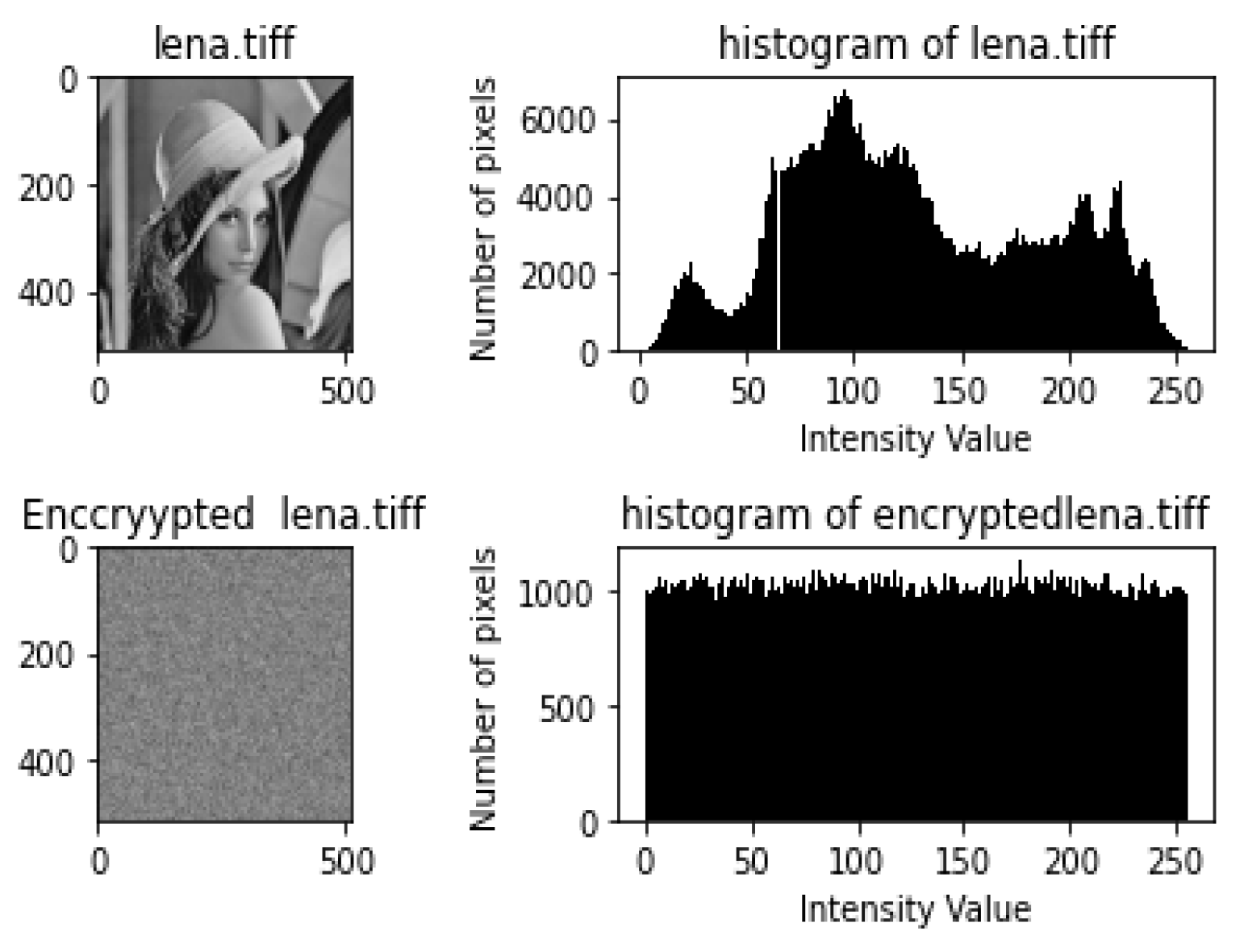
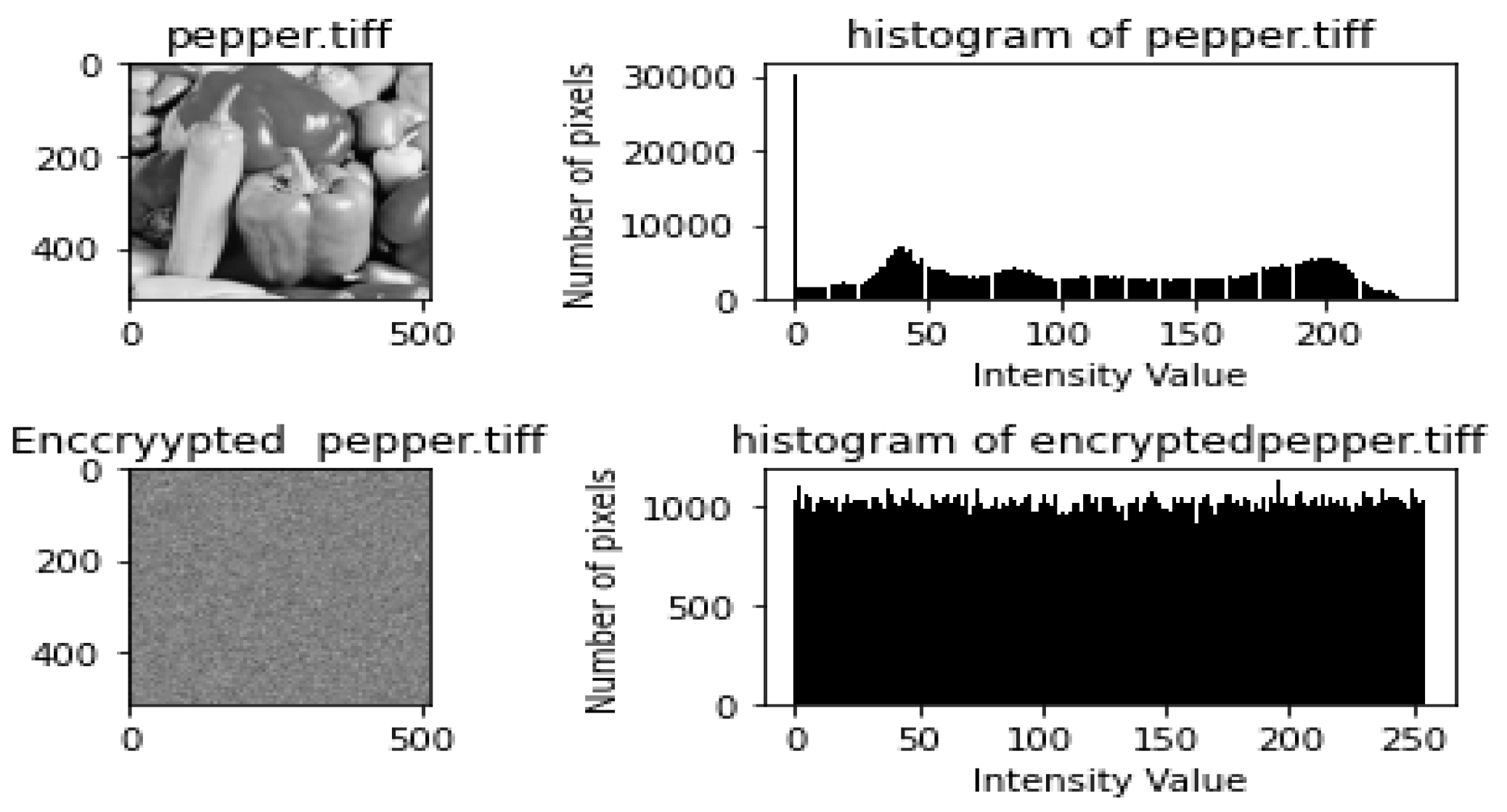
- Histogram and Chi-Square Analysis ResultsEach of the figures in Figure 4, Figure 5, Figure 6, Figure 7 and Figure 8 shows the plain image, histogram of the plain image, the cipher image, and histogram of the cipher image, respectively. By visual inspection, the histograms of the plain images are not uniform, while those of the encrypted images appear uniform. The results from the chi-square tests carried out on the histograms are shown in Table 8. As shown in Table 8, the chi-square values for the plain images were very high, while the chi-square values of the encrypted images were very low. The lower the value of chi-square, the more uniform the histogram.All the p-values of the plain images were found to be less than the significance value; hence, their histogram is not uniform. In contrast, all the p-values of the encrypted images were greater than the significance value of 0.05; hence, they are uniform. These results prove that HXP is resistant to histogram analysis.
- ii.
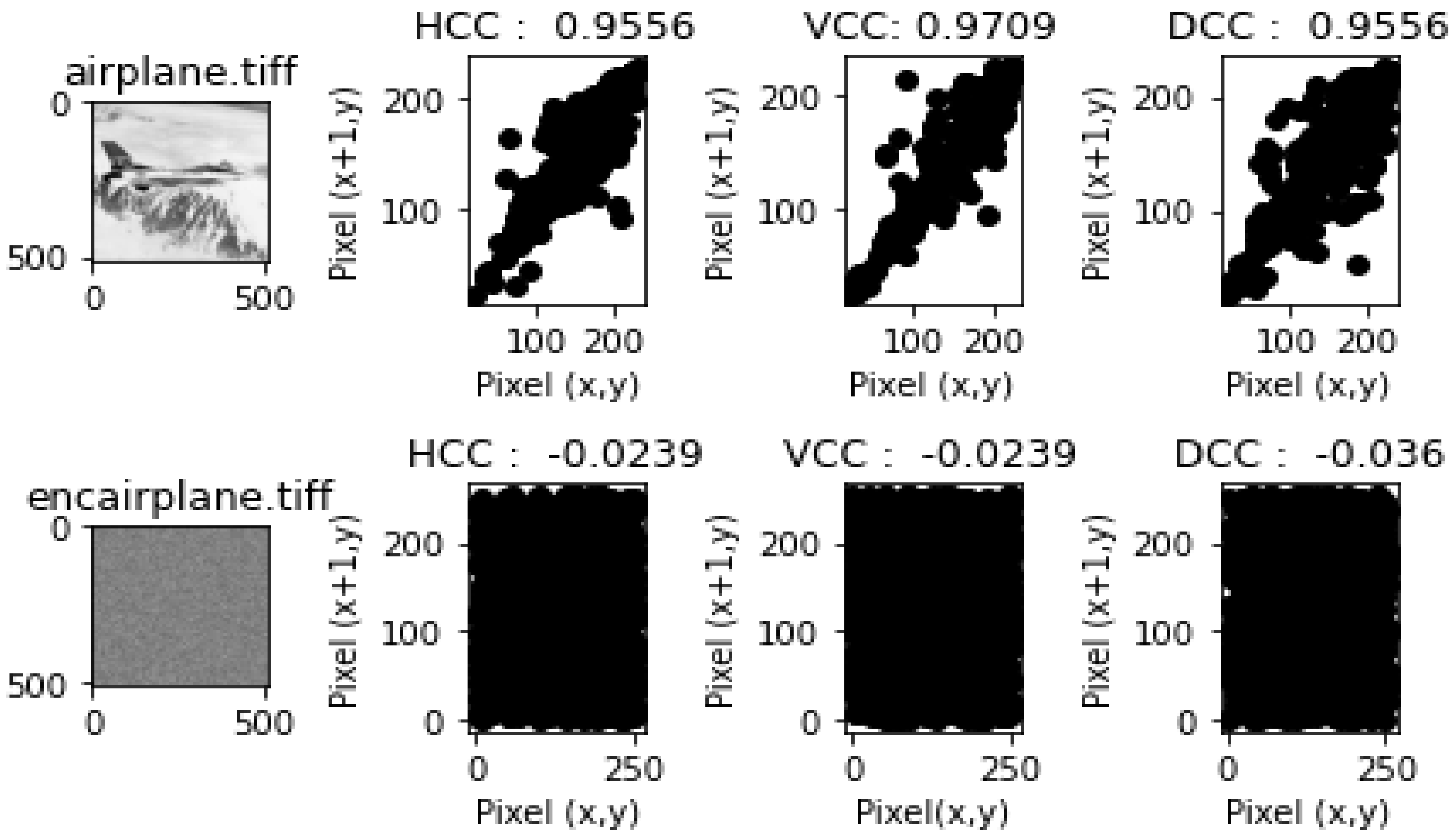
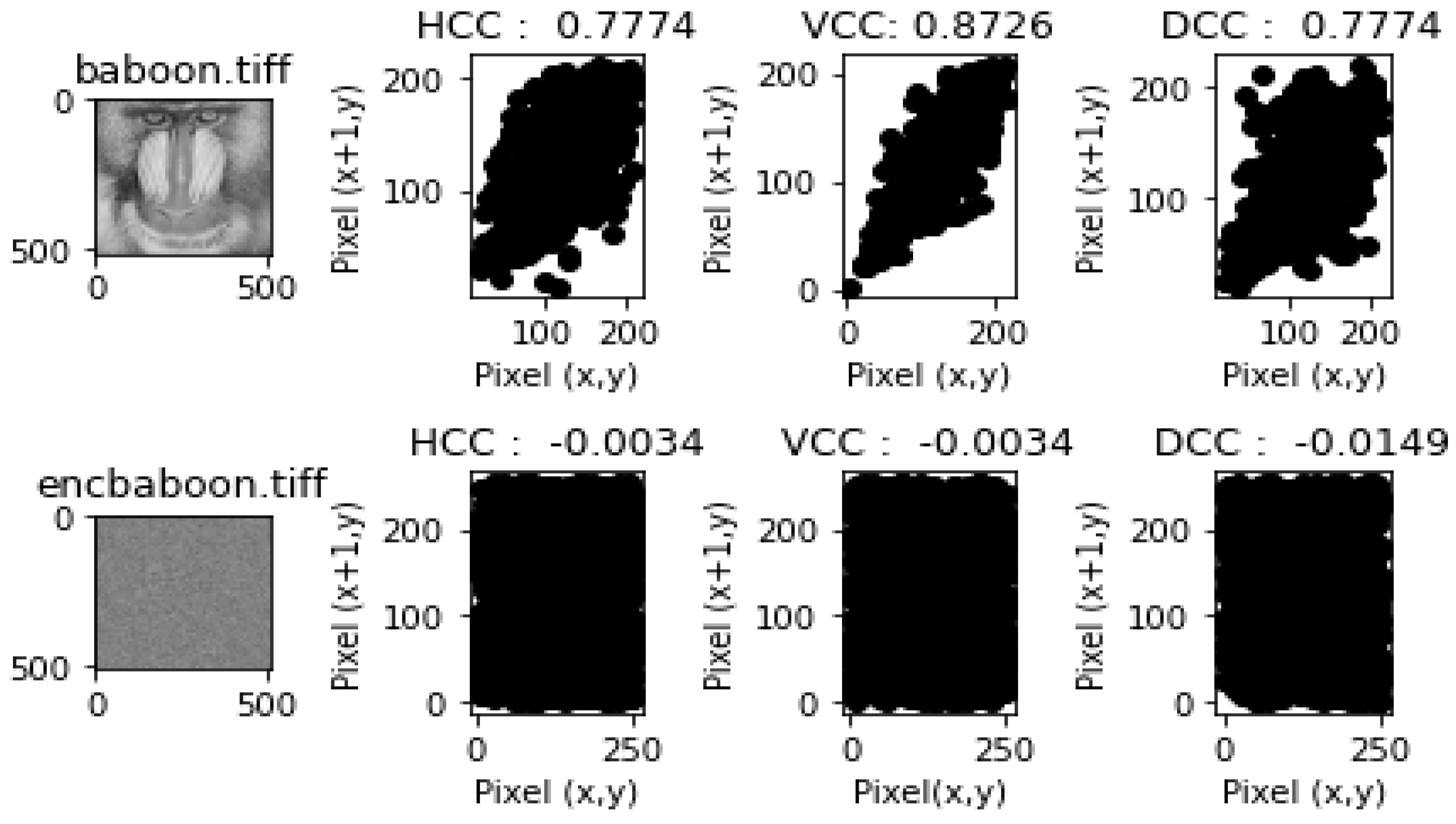
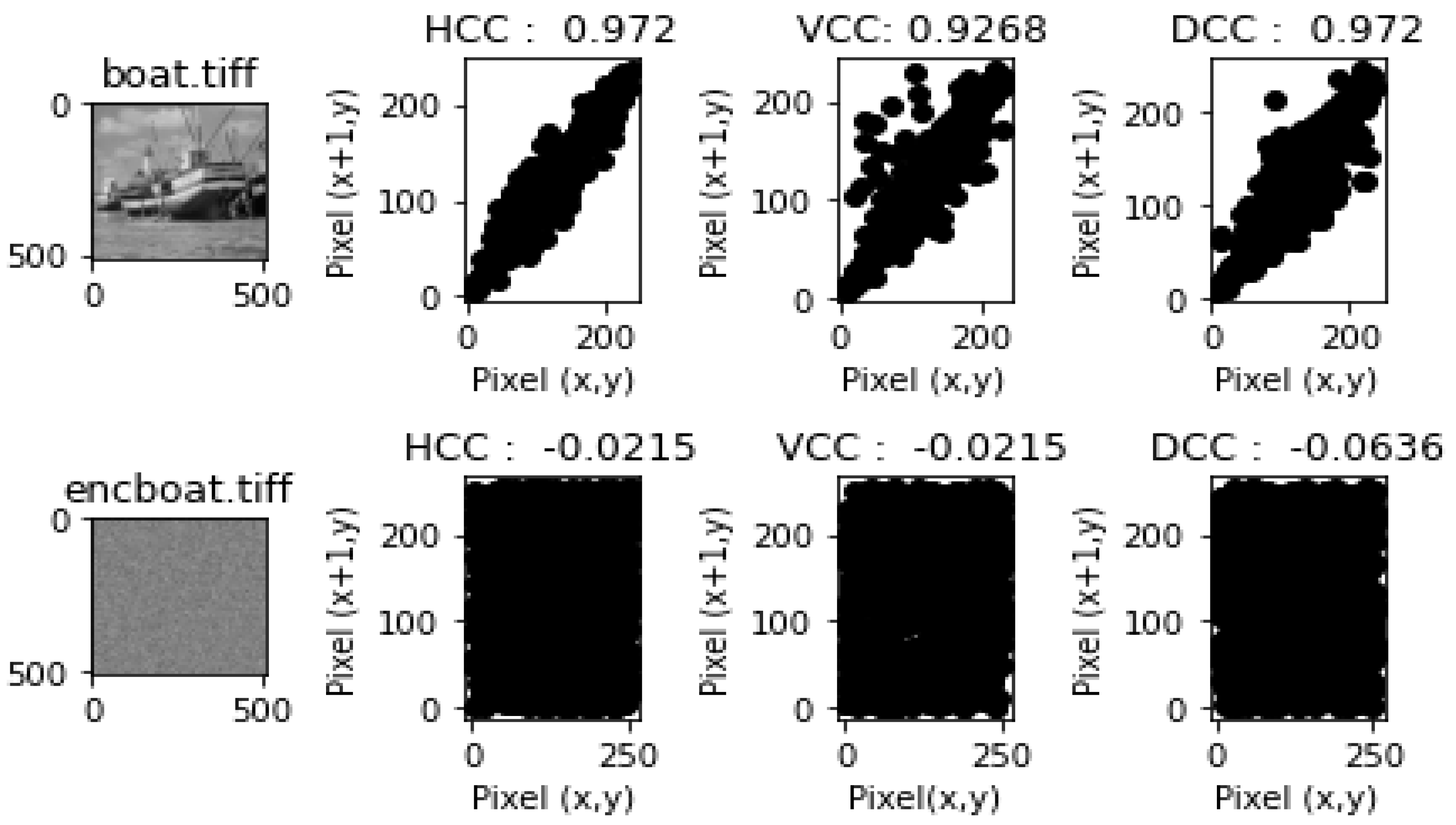
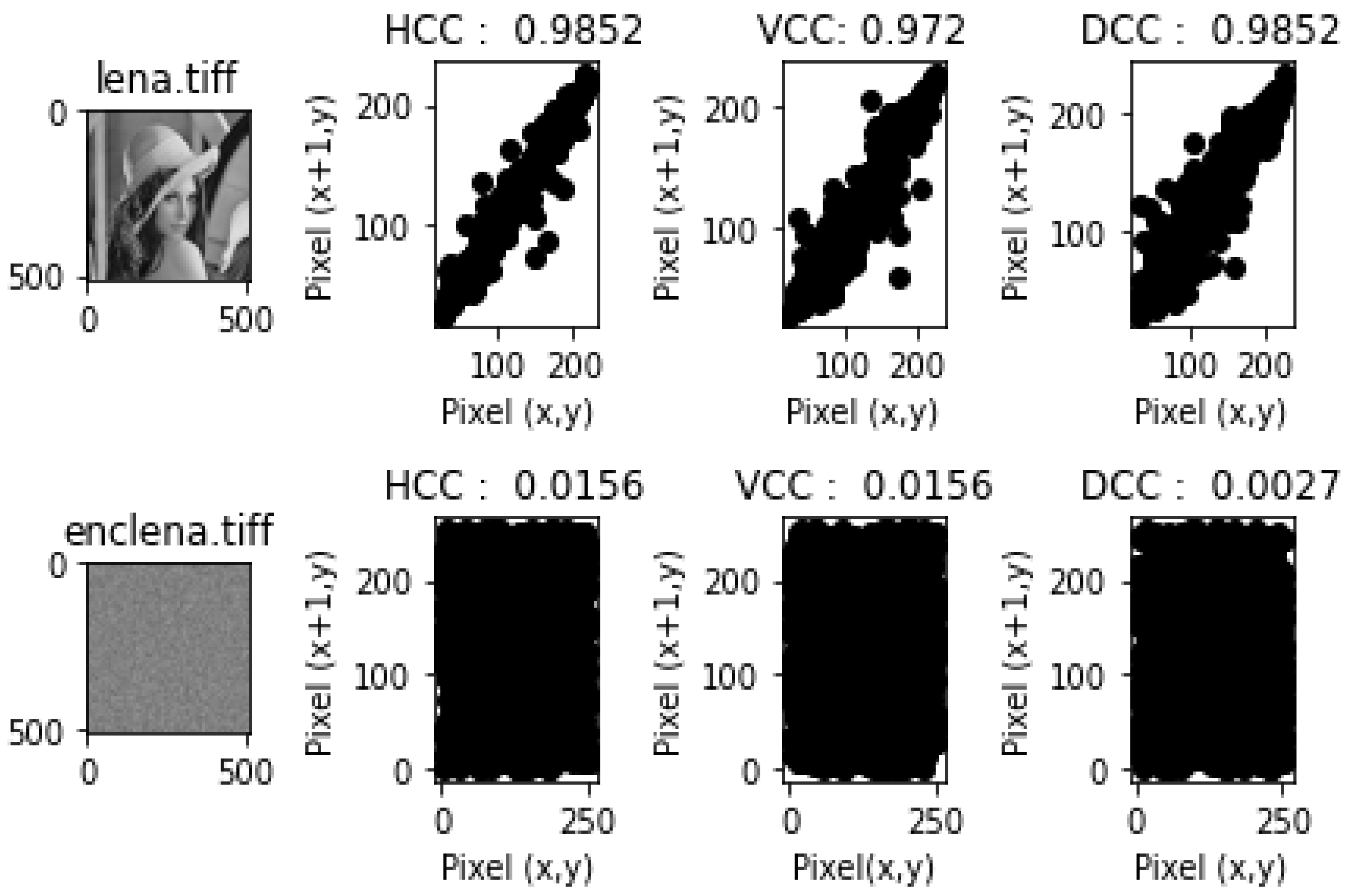
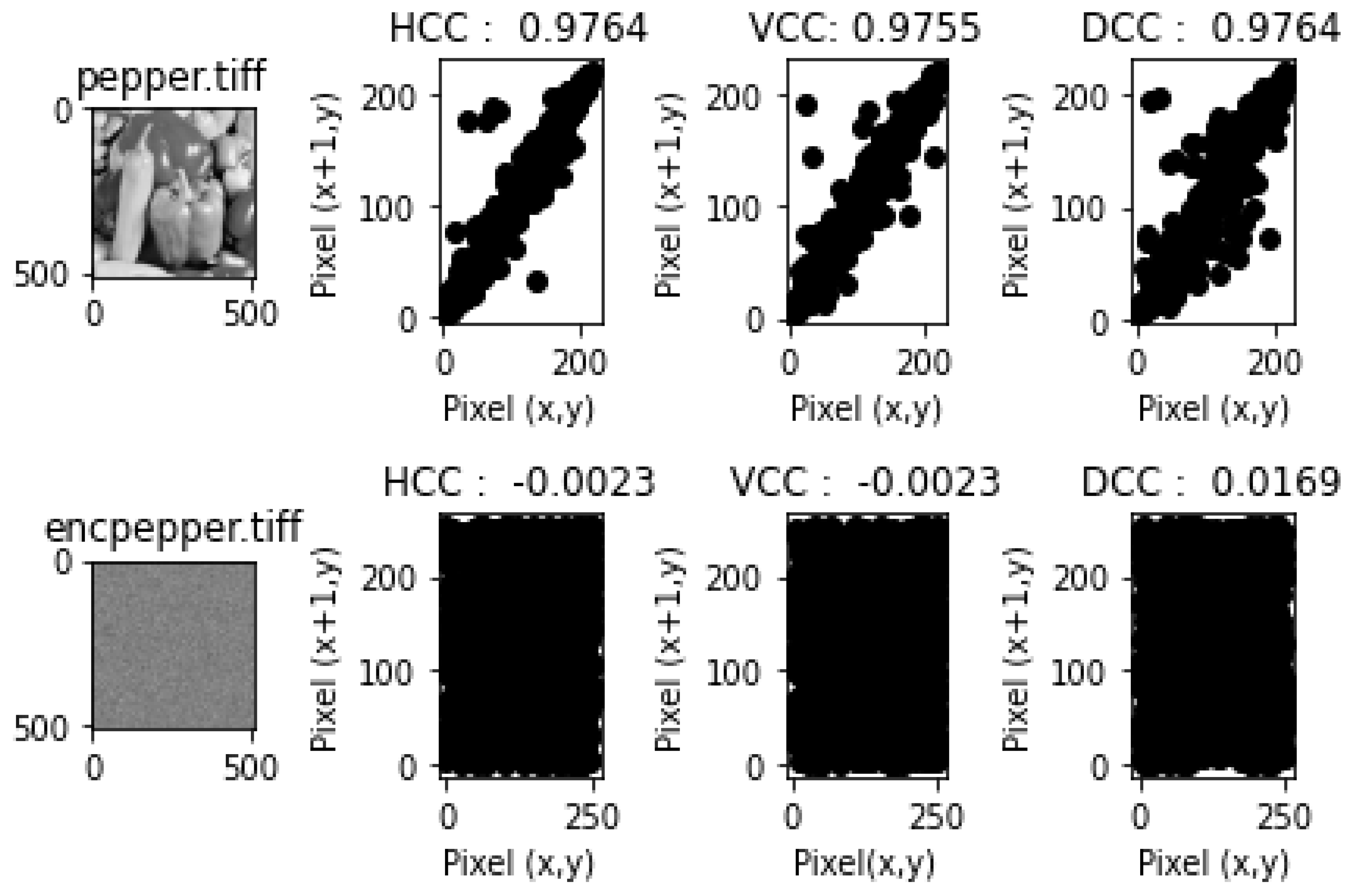
- Correlation Coefficient Analysis and ResultsEach of the figures in Figure 9, Figure 10, Figure 11, Figure 12 and Figure 13 show the plain image, the graphs of the horizontal correlation coefficient (HCC), the vertical correlation coefficient (VCC), and the diagonal correlation coefficient of the adjacent pixels of the plain image in the first row, and the encrypted image, the graphs of the HCC, VCC, and DCC of the encrypted image in the second row, respectively. Table 9 shows the HCC, VCC, and DCC of the plain and encrypted images in Figure 9, Figure 10, Figure 11, Figure 12 and Figure 13. As shown in Figure 9, Figure 10, Figure 11, Figure 12 and Figure 13, the correlation between the adjacent pixels of the plain images was very high for the HCC, VCC, and DCC, while those of the encrypted images appeared to be very low. These results reveal that the proposed lightweight image encryption system can successfully destroy the correlation between the adjacent pixels of the images. Hence, HXP is resistant to correlation coefficient analysis.
- iii.
- Entropy Analysis ResultsTable 10 shows the information entropies of the plain and encrypted images in Figure 3f–j and Figure 3k–o, respectively. The entropies of the plain images were low (meaning not close to the expected value of eight), while the entropies of the encrypted images were high (close to eight). These results show that HXP introduces enough confusion into the encrypted image; therefore, the encryption system is immune to entropy analysis.
Analysis of Memory Utilization during the Encryption and Decryption Processes of the HXP
4.2. Comparative Security Analysis of HXP with the Existing Cryptosystems
5. Justification of The Suitability of HXP on Resource-Staved IOT Devices
6. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ambika, N. A Reliable Cloud Assisted IoT Application in Smart Cities. In Data-Driven Mining, Learning and Analytics for Secured Smart Cities; Chakraborty, C., Lin, J.C.-W., Alazab, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 71–88. [Google Scholar]
- Sundaram, B.V.; Ramnath, M.; Prasanth, M.; Sundaram, J.V. Encryption and Hash based Security in Internet of Things. In Proceedings of the ICSCN 2015, Chennai, India, 26–28 March 2015; pp. 1–6. [Google Scholar]
- Sallam, S.; Beheshti, B.D. A survey on lightweight cryptographic algorithms. In Proceedings of the IEEE Region Conference, Austin, TX, USA, 6–8 April 2018; pp. 1784–1789. [Google Scholar]
- Ram, R.S.; Kumar, M.V.; Ramamoorthy, S.; Balaji, B.S.; Kumar, T.R. An Efficient Hybrid Computing Environment to Develop a Confidential and Authenticated IoT Service Model. In Wireless Personal Communications; Springer: Cham, Switzerland, 2020; pp. 1–25. [Google Scholar]
- Zolfaghari, B.; Yazdinejad, A.; Dehghantanha, A.; Krzciok, J.; Bibak, K. The Dichotomy of Cloud and IoT: Cloud-Assisted IoT from a Security Perspective; Spring: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Ahmed, M.S.K.S.; Hossain, M.F.; Mahmud, M.B.T.N.M.; Chakraborty, C. Artificial Intelligence and Machine Learning for Ensuring Security in Smart Cities. In Data-Driven Mining, Learning and Analytics for Secured Smart Cities; Chakraborty, C., Lin, J.C.-W., Alazab, M., Eds.; Spring: Berlin/Heidelberg, Germany, 2021; pp. 23–47. [Google Scholar]
- França, R.A.R.P.; Monteiro, A.C.B.; Iano, Y. Smart Cities Ecosystem in the Modern Digital Age: An Introduction. In Data-Driven Mining, Learning and Analytics for Secured Smart Cities; Chakraborty, C., Lin, J.C.-W., Alazab, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 49–70. [Google Scholar] [CrossRef]
- França, R.P.; Lano, Y.; Montriro, A.C.B.; Arthur, R. Lower memory consumption for data transmission in smart cloud environments with CBEDE methodology. In Smart Systems Design, Applications, and Challenges; IGI Global: Hershey, PN, USA, 2020; pp. 216–237. [Google Scholar]
- Hatzivasilis, G.; Fysarakis, K.; Papaefstathiou, I.; Manifavas, C. A review of lightweight block ciphers. J. Cryptogr. Eng. 2018, 8, 141–184. [Google Scholar] [CrossRef]
- El-Hajj, M.; Mousawi, H.; Fadlallah, A. Analysis of Lightweight Cryptographic Algorithms on IoT Hardware Platform. Futur. Internet 2023, 15, 54. [Google Scholar] [CrossRef]
- AlJabri, Z.S.; Abawajy, J.H.; Huda, S. Lightweight Authenticated Encryption for Cloud-assisted IoT Applications. In Trends in Wireless Communication and Information Security Proceedings of EWCIS 2020; Jha, R.K., Balas, V.E., Sur, S.N., Kandar, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 295–299. [Google Scholar]
- Botta, A.; De Donato, W.; Persico, V.; Pescape, A. On the integration of cloud computing and internet of things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud, FiCloud, Barcelona, Spain, 27–29 August 2014; pp. 23–30. [Google Scholar] [CrossRef]
- Ghanavati, S.; Abawajy, J.; Izadi, D.; Alelaiwi, A. Cloud-assisted IoT-based health status monitoring framework. Clust. Comput. 2017, 20, 1843–1853. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Dehghantanha, A.; Parizi, R.M.; Hammoudeh, M.; Karimipour, H.; Srivastava, G. Block Hunter: Federated Learning for Cyber Threat Hunting in Blockchain-Based IIoT Networks. IEEE Trans. Ind. Inform. 2022, 18, 8356–8366. [Google Scholar] [CrossRef]
- Ranger, S. What is cloud computing? Everything you need to know about cloud explained. Zdnet. 2018. Available online: https://www.zdnet.com/article/ (accessed on 20 March 2022).
- Sultangazin, A.; Tabuada, P. Symmetries and isomorphisms for privacy in control over the cloud. IEEE Trans. Autom. Control 2021, 66, 538–549. [Google Scholar] [CrossRef]
- Nakhodchi, S.; Zolfaghari, B.; Yazdinejad, A.; Dehghan Tanha, A. Steeleye: An application-layer attack detection and at_tribution model in industrial control systems using semi-deep learning. In Proceedings of the 2021 18th International Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 13–15 December 2021; IEEE: New York, NY, USA; pp. 1–8. [Google Scholar]
- Pasupuleti, S.K.; Varma, D. Lightweight Ciphertext-Policy Attribute-Based Encryption Scheme for Data Privacy and Security in Cloud-assisted IoT in Real-Time Data Analytics for Large Scale Sensor Data; Elsevier: Amsterdam, The Netherlands, 2020; pp. 97–114. [Google Scholar]
- Oladipupo, E.T.; Abikoye, O.C.; Imoize, A.L.; Awotunde, J.B.; Chang, T.-Y.; Lee, C.-C.; Do, D.-T. An Efficient Authenticated Elliptic Curve Cryptography Scheme for Multicore Wireless Sensor Networks. IEEE Access 2023, 11, 1306–1323. [Google Scholar] [CrossRef]
- Ibrahim, A.A.A.; Nisar, K.; Hzou, Y.K.; Welch, I. Review and Analyzing RFID Technology Tags and Applications. In Proceedings of the 2019 IEEE 13th International Conference on Application of Information and Communication Technologies (AICT), Baku, Azerbaijan, 23–25 October 2019; pp. 1–4. [Google Scholar]
- Hu, S.; Chen, Y.; Zheng, Y.; Xing, B.; Li, Y.; Zhang, L.; Chen, L. Provably Secure ECC-Based Authentication and Key Agreement Scheme for Advanced Metering Infrastructure in the Smart Grid. IEEE Trans. Ind. Inform. 2022, 19, 5985–5994. [Google Scholar] [CrossRef]
- Aljaedi, A.; Jamal, S.S.; Rashid, M.; Alharbi, A.R.; Alotaibi, M.; Alanazi, D.J. Area-Efficient Realization of Binary Elliptic Curve Point Multiplication Processor for Cryptographic Applications. Appl. Sci. 2023, 13, 7018. [Google Scholar] [CrossRef]
- Eisenbarth, T.; Gong, Z.; Güneysu, T.; Heyse, S.; Indesteege, S.; Kerckhof, S.; Koeune, F.; Nad, T.; Plos, T.; Regazzoni, F.; et al. Cryptology: Compact Implementation and Performance Evaluation of Block Ciphers in ATtiny Devices. In Progress in AFRICACRYPT 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 172–187. [Google Scholar]
- Zhu, B.; Sun, J.; Qin, J.; Ma, J. A Secure Data Sharing Scheme with Designated Server. Secur. Commun. Networks 2019, 2019, 4268731. [Google Scholar] [CrossRef]
- Omrani, T.; Rhouma, R.; Becheikh, R. LICID: A lightweight image cryptosystem for IoT devices. Cryptologia 2019, 43, 313–343. [Google Scholar] [CrossRef]
- Sadikin, M.A.; Susanti, B.H. Design of AL-13 Block Cipher Algorithm Based On Extended Feistel Network. J. Phys. Conf. Ser. 2019, 1127, 012027. [Google Scholar] [CrossRef]
- Oladipupo, E.T.; Abikoye, O.C. Modified Playfair cryptosystem for improved data security. Comput. Sci. Inf. Technol. 2022, 3, 51–64. [Google Scholar] [CrossRef]
- Piret, G.; Roche, T.; Carlet, C. Picaro—A block cipher allowing efficient higher-order side-channel resistance. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2012; pp. 311–328. [Google Scholar]
- Vergili, I.; Yücel, M.D. Avalanche and Bit Independence Properties for the Ensembles of Randomly Chosen n × n S-Boxes. Turk J. Electr. Eng. 2001, 9, 137–145. [Google Scholar]
- Thakor, V.A.; Razzaque, M.A.; Khandaker, M.R.A. Lightweight Cryptography Algorithms for Resource-Constrained IoT Devices: A Review, Comparison and Research Opportunities. IEEE Access 2021, 9, 28177–28193. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Cheng, N.; Shen, X. Secure Password-Protected Encryption Key for Deduplicated Cloud Storage Systems. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2789–2806. [Google Scholar] [CrossRef]
- Samaila, M.G.; Neto, M.; Fernandes, D.A.B.; Freire, M.M.; Inácio, P.R.M. Security Challenges of the Internet of Things. In Beyond the Internet of Things, Internet of Things; Batalla, J.M., Ed.; Springer International Publishing: Berlin/Heidelberg, Germany, 2017; pp. 53–82. [Google Scholar] [CrossRef]
- Mohd, B.J.; Hayajneh, T. Lightweight Block Ciphers for IoT: Energy Optimization and Survivability Techniques. IEEE Access 2018, 6, 35966–35978. [Google Scholar] [CrossRef]
- Din, I.U.; Guizani, M.; Kim, B.S.; Hassan, S.; Khan, M.K. Trust management techniques for the internet of things: A survey. IEEE Access 2018, 7, 29763–29787. [Google Scholar] [CrossRef]
- Robertson, J.; Riley, M. The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies. 2018. Available online: https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies#xj4y7vzkg (accessed on 16 June 2023).
- Li, S.Z.S.; Xu, L.D. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Dinu, D.; Biryukov, A.; Großschädl, J. FELICS—Fair evaluation of lightweight cryptographic systems. In NIST Workshop on Lightweight Cryptography 2015; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2015. [Google Scholar]
- Zhang, X.; Tang, S.; Li, T.; Li, X.; Wang, C. GFRX: A New Lightweight Block Cipher for Resource-Constrained IoT Nodes. Electronics 2022, 12, 405. [Google Scholar] [CrossRef]
- Guo, Y.; Li, L.; Liu, B. Shadow: A Lightweight Block Cipher for IoT Nodes. IEEE Internet Things J. 2021, 8, 13014–13023. [Google Scholar] [CrossRef]
- Alizadeh, M.; Salleh, M.; Zamani, M.; Shayan, J.; Karamizadeh, S. Security and Performance Evaluation of Lightweight Cryptographic Algorithms in RFID. In Recent Researches in Communications and Computers Security; Kos Island, Greece, 2012; pp. 45–50. [Google Scholar]
- Suzaki, T.; Minematsu, K.; Morioka, S.; Kobayashi, E. TWINE: A lightweight block cipher for multiple platforms. In Selected Areas in Cryptography, vol. 7707 of Lecture Notes in Computer Science; Knudsen, L., Ed.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 339–354. [Google Scholar]
- Zhang, W.; Bao, Z.; Lin, D.; Rijmen, V.; Yang, B.; Verbauwhede, I. Rectangle: A Bit-Slice Ultra-Lightweight Block Cipher Suitable for Multiple Platforms. 2014. Available online: http://eprint.iacr.org/ (accessed on 15 September 2022).
- Liu, H.; Zhao, B.; Zou, J.; Huang, L.; Liu, Y. A Lightweight Image Encryption Algorithm Based on Message Passing and Chaotic Map. Secur. Commun. Networks 2020, 2020, 12. [Google Scholar] [CrossRef]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A. PRESENT: An Ultra-Lightweight Block Cipher; Spring: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Daemen, J.; Peeters, M.; Van Assche, G.; Rijmen, V. The Noekeon Block Cipher. In The NESSIE Proposal, 2000. First Open NESSIE Workshop; 2016; Available online: http://gro.noekeon.org (accessed on 15 September 2022).
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. PRINCE—A low-latency block cipher for pervasive computing applications. In Proceedings of the ASIACRYPT, Beijing, China, 2–6 December 2012; Springer: Berlin/Heidelberg, Germany,, 2012; pp. 208–225. [Google Scholar]
- Gong, Z.; Nikova, S.; Law, Y.W. KLEIN: A New Family of Lightweight Block Ciphers. In RFIDSec 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 1–18. [Google Scholar]
- Leander, G.; Paar, C.; Poschmann, A.; Schramm, K. New Lightweight DES Variants. In FSE 2007; Springer: Berlin/Heidelberg Germany, 2007; pp. 196–210. [Google Scholar]
- Lim, C.H.; Korkishko, T.; Song, J.; Kwon, T.; Yung, M. mCrypton—A Lightweight Block Cipher for Security of Low-Cost RFID Tags and Sensors. In ISA 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 243–258. [Google Scholar]
- Borislav, S.; Krasimir, K. Image encryption using chebyshev map and rotation equation. Entropy 2015, 17, 2117–2139. [Google Scholar]
- Chen, G.; Mao, Y.; Chui, C.K. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Rhouma, R.; Meherzi, S.; Belghith, S. OCML-based color image encryption. Chaos Solitons Fractals 2009, 40, 309–318. [Google Scholar] [CrossRef]
- Liu, H.; Zhao, B.; Huang, L. Quantum Image Encryption Scheme Using Arnold Transform and S-box Scrambling. Entropy 2019, 21, 343. [Google Scholar] [CrossRef]
- Kaur, J.; Jindal, N. A secure image encryption algorithm based on fractional transforms and scrambling in combination with multimodal biometric keys. Multimed. Tools Appl. 2019, 78, 11585–11606. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Chai, X.; Bi, J.; Gan, Z.; Liu, X.; Zhang, Y.; Chen, Y. Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process 2020, 176, 107684. [Google Scholar] [CrossRef]
- Norouzi, B.; Seyedzadeh, S.M.; Mirzakuchaki, S.; Mosavi, M.R. A novel image encryption based on row-column, masking and main diffusion processes with hyper chaos. Multimed. Tools Appl. 2013, 74, 781–811. [Google Scholar] [CrossRef]
- Zhu, C. A novel image encryption scheme based on improved hyperchaotic sequences. J. Opt. Commun. 2012, 285, 29–37. [Google Scholar] [CrossRef]
- Wang, X.; Li, Y.; Jin, J. A new one-dimensional chaotic system with applications in image encryption. Chaos Solitons Fractals 2020, 139, 110102. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S.; Seyedzadeh, S.M.; Mosavi, M.R. A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed. Tools Appl. 2014, 71, 1469–1497. [Google Scholar] [CrossRef]
- Borujeni, S.E.; Eshghi, M. Chaotic image encryption system using phase-magnitude transformation and pixel substitution. Telecommun. Syst. 2011, 52, 525–537. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; Xu, D.; Liu, C. Image encryption scheme using chaos and simulated annealing algorithm. Nonlinear Dyn. 2016, 84, 1417–1429. [Google Scholar] [CrossRef]
- Zhang, Y. The fast image encryption algorithm based on lifting scheme and chaos. Inf. Sci. 2020, 520, 177–194. [Google Scholar] [CrossRef]
- Bertoni, G.; Daemen, J.; Peeters, M.; Assche, G.V. On the Indifferentiability of the Sponge Construction. In EUROCRYPT. Lecture Notes in Computer Science; Ismart, N.P., Ed.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 181–197. [Google Scholar]
- Watson, K. Network security. Netw. Secur. 2002, 4965, 1–34. [Google Scholar]


| Author | Title | Algorithm used | Strength | Weakness |
|---|---|---|---|---|
| [41] | Lightweight cryptography Algorithm for Multiple platforms | Generalized Feistel structure (GFS) | Less resources-intensive. The same program code can be used for encryption and decryption | It is vulnerable to related key attacks |
| [44] | An Ultra-Lightweight Block Cipher | Feistel structure | Conserves memory | Susceptible to related key attacks, and requires more rounds to ensure security |
| [45] | The Noekeon Block Cipher | SPN structure | Consumes less power and has better performance than the software on legacy sensors | It is resource-intensive |
| [46] | PRINCE—A low-latency block cipher for pervasive computing applications | Feistel structure | It conserves computational resources | It is susceptible to key-related attacks and requires more rounds to ensure security |
| [47] | A New Family of Lightweight Block Ciphers | SPN structure | Consumes low power and exhibits high diffusion | Hardware implementation is resource-intensive |
| [48] | New Lightweight DES Variants | Feistel structure | It uses only one S-Box | S-Box consumes memory and requires more rounds to ensure security |
| [49] | mCrypton—A Lightweight Block Cipher for the Security of Low-Cost RFID Tags and Sensors | Crypton architecture [50] (SPN structure) | Compact implementation in both hardware and software | Hardware implementation is resource-intensive |
| Symbol | Description |
|---|---|
| XOR | Exclusive-or |
| HXP | Hash, XOR, and bit permutation |
| Concatenation operator | |
| XOR operator | |
| SHA−256 | Secure Hash Algorithm 256 |
| Input image | |
| C | Cipher image |
| Contrast of P/standard deviation of pixels in P | |
| Luminance of P/mean of pixel in P | |
| Contrast of C/standard deviation of pixels in C | |
| Luminance of C/mean of pixel in C | |
| Variance of P | |
| Variance of C |
| Image | EQ | PSNR | SC | SSIM | NCC | DCC | MSE | MAE | NAE | MD | AD |
|---|---|---|---|---|---|---|---|---|---|---|---|
| airplane.tiff | 2,869,083 | 8.0041 | 1.1062 | 0.0095 | −0.0016 | −0.0016 | 10,296.2 | 82.9506 | 0.4629 | 227 | 67.3335 |
| baboon.tiff | 750,867.4 | 9.5204 | 0.9773 | 0.0087 | 0 | 0 | 7261.71 | 71.0481 | 0.5481 | 221 | 36.4318 |
| boat.tiff | 1,533,181 | 9.2952 | 1.0287 | 0.009 | 0.0009 | 0.0009 | 7648.14 | 72.5083 | 0.559 | 248 | 37.4054 |
| lena.tiff | 623,642.2 | 9.2399 | 1.0012 | 0.0096 | 0.0022 | 0.0022 | 7746.15 | 72.895 | 0.5876 | 235 | 34.6345 |
| pepper.tiff | 2,610,186 | 8.8704 | 1.0452 | 0.0097 | −0.002 | −0.002 | 8434.09 | 75.6136 | 0.629 | 222 | 34.1703 |
| Image | PSNR | SC | SSIM | NCC | DCC | MSE | MAE | NAE | MD | AD |
|---|---|---|---|---|---|---|---|---|---|---|
| Ideal values | Inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| airplane.tiff | inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| baboon.tiff | inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| boat.tiff | inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| lena.tiff | inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| pepper.tiff | inf | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 |
| Plain image | Encrypted image | |||||
|---|---|---|---|---|---|---|
| Image | Chi-square | p-Value | Remark | Chi-square | p-Value | Remark |
| airplane.tiff | 564,672.6 | 0 | not uniform | 216.5977 | 0.961 | Uniform |
| baboon.tiff | 134,688.4 | 0 | not uniform | 225.127 | 0.911 | Uniform |
| boat.tiff | 381,445.8 | 0 | not uniform | 280.6582 | 0.129 | Uniform |
| lena.tiff | 91,011.39 | 0 | not uniform | 209.1113 | 0.984 | Uniform |
| pepper.tiff | 79,851.4 | 0 | not uniform | 289.3418 | 0.069 | Uniform |
| Plain image | Encrypted image | |||||
|---|---|---|---|---|---|---|
| Image | Horizontal | Vertical | Diagonal | Horizontal | Vertical | Diagonal |
| airplane.tiff | 0.9556 | 0.9709 | 0.9556 | −0.0239 | −0.0239 | −0.036 |
| baboon.tiff | 0.7774 | 0.8726 | 0.7774 | −0.0034 | −0.0034 | −0.0149 |
| boat.tiff | 0.972 | 0.9268 | 0.972 | −0.0215 | −0.0215 | −0.0636 |
| lena.tiff | 0.9852 | 0.972 | 0.9852 | 0.0156 | 0.0156 | 0.0027 |
| pepper.tiff | 0.9764 | 0.9755 | 0.9764 | −0.0023 | −0.0023 | 0.0169 |
| Image | Plain image | Encrypted image |
|---|---|---|
| airplane.tiff | 6.66391 | 7.99934 |
| baboon.tiff | 7.76244 | 7.99941 |
| boat.tiff | 7.19137 | 7.99932 |
| lena.tiff | 7.7502 | 7.99941 |
| pepper.tiff | 7.66983 | 7.99927 |
| Line # | Mem usage | Increment | Occurrences | Line contents |
|---|---|---|---|---|
| 92 | 168.8 MiB | 168.8 MiB | 1 | @ profile |
| 93 | def bitmodification(encseed, encryptedtext, bsize): | |||
| 94 | 168.8 MiB | 0.0 MiB | 1 | encryptedtext = bytestobinary(encryptedtext) |
| 95 | 168.8 MiB | 0.0 MiB | 1 | confusionkey = randgen(encseed,len(encryptedtext)) |
| 96 | 168.8 MiB | 0.0 MiB | 1 | lnibble = encryptedtext [0: len(encryptedtext)//2] |
| 97 | 168.8 MiB | 0.0MiB | 1 | rnibble = encryptedtext[len(encryptedtext)//2: len(encryptedtext)] |
| 98 | 168.8 MiB | 0.0 MiB | 2051 | xornibble = [str(int(lnibble[i])^int(rnibble[i])) for i in range(len(lnibble))] |
| 99 | 168.8 MiB | Xornibble = ‘‘.join(xornibble) | ||
| 100 | 168.8 MiB | 0.0MiB | 1 | fullbyte = ‘‘.join([xornibble, rnibble]) |
| 101 | 168.8 MiB | 0.0MiB | 1 | fullbyte = reshuffleforencryption(confusionkey,fullbyte) |
| 102 | 168.8 MiB | 0.0MiB | 1 | encryptedtext = ‘‘.join(fullbyte) |
| 103 | #encryptedtext = ‘‘.join(reshuffleforencryption(confusionkey,fullbyte)) | |||
| 104 | #encryptedtext = binarytobytes(encryptedtext) | |||
| 105 | 168.8 MiB | 0.0MiB | 1 | encryptedtext = list(binarytobytes(encryptedtext)) |
| 106 | 168.8 MiB | 0.0MiB | 1 | return encryptedtext |
| Line # | Mem usage | Increment | Occurrences | Line contents |
|---|---|---|---|---|
| 107 | 55.0 MiB | 55.0 MiB | 1 | @ profile |
| 108 | def reversebitmodification(encseed, ciphertext, bsize): | |||
| 109 | 55.0 MiB | 0.0 MiB | 1 | reversebinX = bytestobinary(ciphertext) |
| 110 | 55.0 MiB | 0.0 MiB | 1 | confusionkey = randgen(encseed,len(reversebinX)) |
| 111 | 55.0 MiB | 0.0 MiB | 1 | reversebinX = reshufflefordecryption(confusionkey, reversebinX) |
| 112 | 55.0 MiB | 0.0 MiB | 1 | lnibble = reversebinX [0: len(reversebinX)//2] |
| 113 | 55.0 MiB | 0.0 MiB | 1 | rnibble = reversebinX[len(reversebinX)//2: len(reversebinX)] |
| 114 | 55.0 MiB | 0.0 MiB | 2051 | Xornibble = [str(int(lnibble[j])^int(rnibble[j])) for j in range(len(lnibble))] |
| 115 | 55.0 MiB | 0.0 MiB | 1 | Xornibble = ‘‘.join(xornibble) |
| 116 | 55.0 MiB | 0.0 MiB | 1 | rnibble = ‘‘.join(rnibble) |
| 117 | 55.0 MiB | 0.0 MiB | 1 | reversebinX = xornibble + rnibble |
| 118 | 55.0 MiB | 0.0 MiB | 1 | revtext = list (binarytobytes(reversebinX)) |
| 119 | 55.0 MiB | 0.0 MiB | 1 | return revtext |
| Metrics | Algorithm | airplane.tiff | baboon.tiff | boat.tiff | lena.tiff | pepper.tiff |
|---|---|---|---|---|---|---|
| PSNR | HXP | 8.0041 | 9.5204 | 9.2952 | 9.2399 | 8.8704 |
| [57] | 7.9804 | 9.4722 | - | 8.55 | 8.8807 | |
| [58] | 9.5466 | 9.2322 | 8.9914 | |||
| [59] | - | 9.400680 | 9.312557 | 9.287804 | - | |
| [60] | - | 9.4474 | 9.2653 | 8.5731 | 8.9603 | |
| NCC | HXP | −0.0016 | 0 | 0.0009 | 0.0022 | −0.002 |
| [57] | −0.000004 | 0.00257 | - | −0.0023 | −0.011567 | |
| [58] | −0.006632 | 0.002851 | −0.001650 | |||
| [60] | - | −0.00070284 | −0.00302940 | 0.003389097 | 0.002385462 | |
| MSE | HXP | 10,296.1584 | 7261.712 | 7648.1358 | 7746.154 | 8434.092 |
| [57] | 10352 | 7343 | - | 9080 | 8414 | |
| [60] | - | 7385 | 7701 | 9032 | 8261 | |
| [61] | 9980 | 6583 | - | 7510 | 8298 | |
| HXP | 216.5977 | 225.127 | 280.6582 | 209.1113 | 289.3418 | |
| [57] | 246 | 259 | - | 184 | 270 | |
| [59] | - | 274.7051 | 216.3223 | 254.5176 | - | |
| [61] | 265 | 266 | - | 263 | 274 | |
| [62] | 244.65 | - | 256.31 | 284.81 | 281.41 | |
| Entropy | HXP | 7.99934 | 7.99941 | 7.99932 | 7.99941 | 7.99927 |
| [57] | 7.9973 | 7.9972 | - | 7.9980 | 7.9970 | |
| [58] | - | 7.9970 | - | 7.9977 | 7.9973 | |
| [59] | - | 7.99924 | 7.99940 | 7.99930 | - | |
| [63] | - | 7.997436 | - | 7.997466 | 7.997355 | |
| EQ | HXP | 2,869,083.01 | 750,867.4 | 1,533,181.18 | 623,642.2 | 261,0186 |
| [57] | 259.17 | 189.78 | - | 147.20 | 155.67 | |
| [60] | - | 190.76 | 209.95 | 146.84 | 153.52 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oladipupo, E.T.; Abikoye, O.C.; Awotunde, J.B. A Lightweight Image Cryptosystem for Cloud-Assisted Internet of Things. Appl. Sci. 2024, 14, 2808. https://doi.org/10.3390/app14072808
Oladipupo ET, Abikoye OC, Awotunde JB. A Lightweight Image Cryptosystem for Cloud-Assisted Internet of Things. Applied Sciences. 2024; 14(7):2808. https://doi.org/10.3390/app14072808
Chicago/Turabian StyleOladipupo, Esau Taiwo, Oluwakemi Christiana Abikoye, and Joseph Bamidele Awotunde. 2024. "A Lightweight Image Cryptosystem for Cloud-Assisted Internet of Things" Applied Sciences 14, no. 7: 2808. https://doi.org/10.3390/app14072808
APA StyleOladipupo, E. T., Abikoye, O. C., & Awotunde, J. B. (2024). A Lightweight Image Cryptosystem for Cloud-Assisted Internet of Things. Applied Sciences, 14(7), 2808. https://doi.org/10.3390/app14072808








