We Are Not Equipped to Identify the First Signs of Cyber–Physical Attacks: Emotional Reactions to Cybersecurity Breaches on Domestic Internet of Things Devices
Abstract
1. Introduction
1.1. Cybersecurity Breach
1.2. Emotion Processes Resulting from Cybersecurity Breaches/Component Process Model
1.3. Research Aims and Hypothesis
1.3.1. Research Question and Hypothesis 1
1.3.2. Research Question and Hypothesis 2
1.3.3. Research Question and Hypothesis 3
2. Study Design
3. Study 1
3.1. Materials and Methods
3.1.1. Participants
3.1.2. Procedure
3.1.3. Instrument
3.2. Results
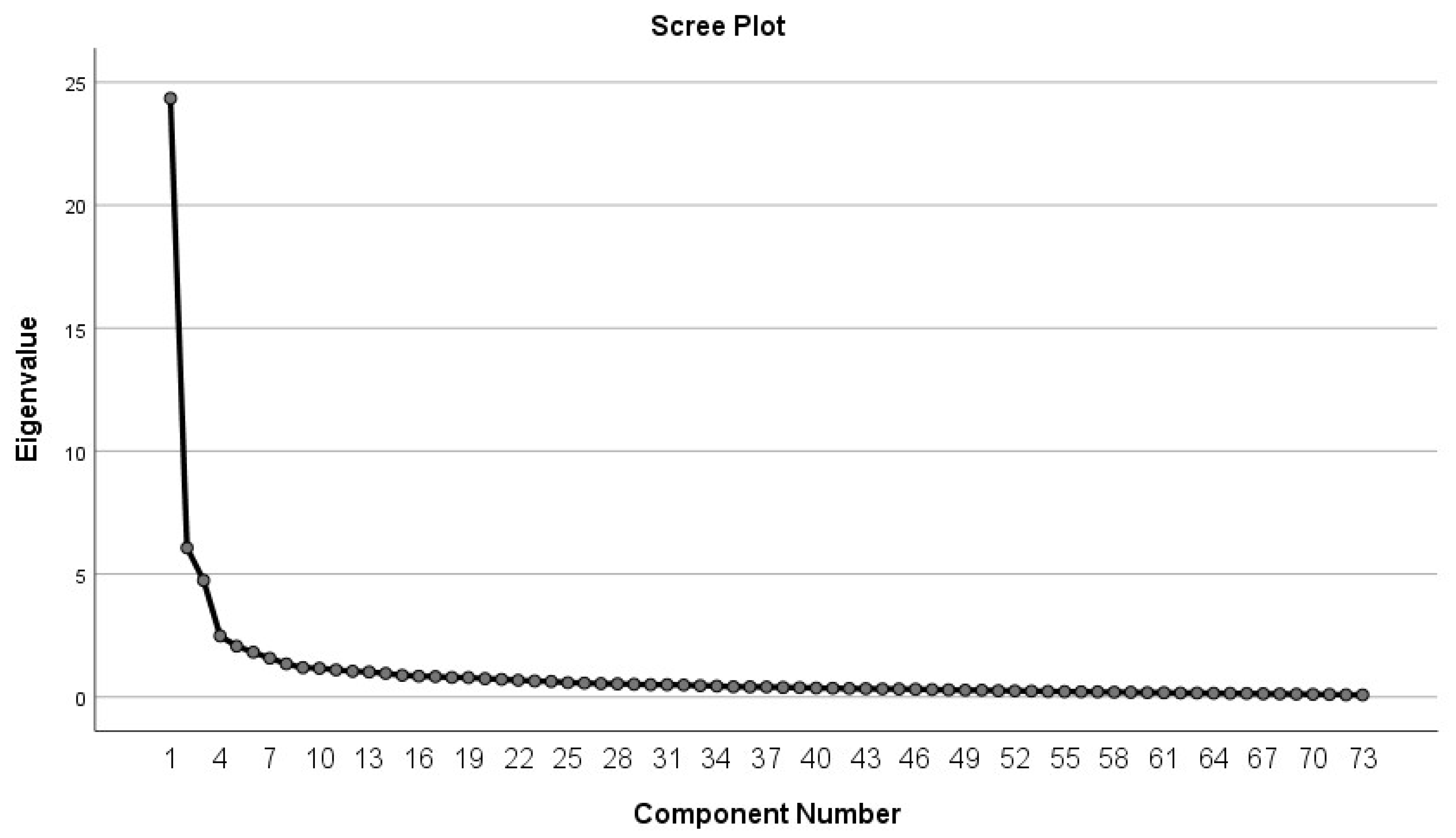
3.2.1. Underlying Structure of the Interindividual Differences in Emotion Processes in the Situation of Cybersecurity Breaches of Domestic IoT Devices
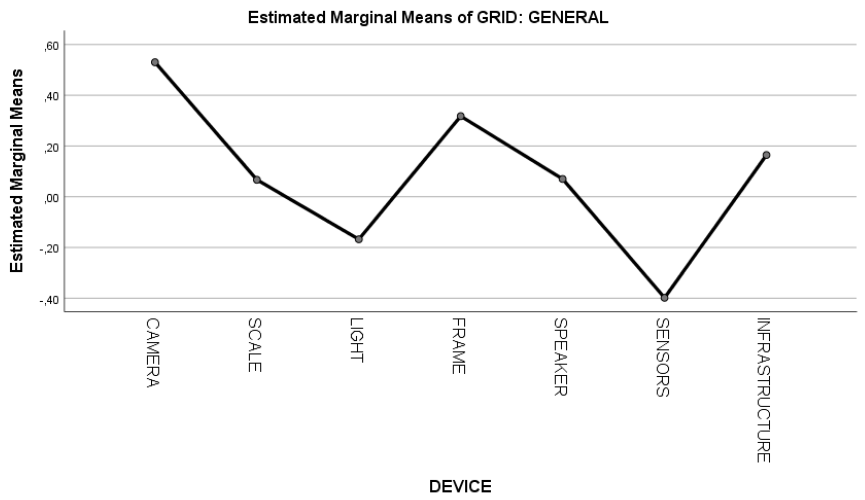
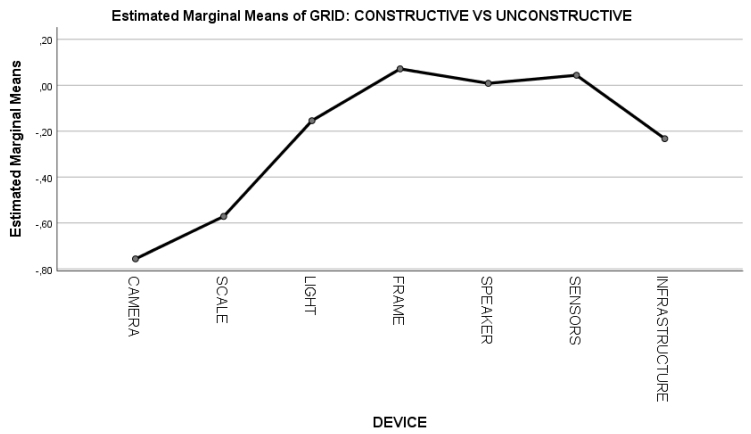
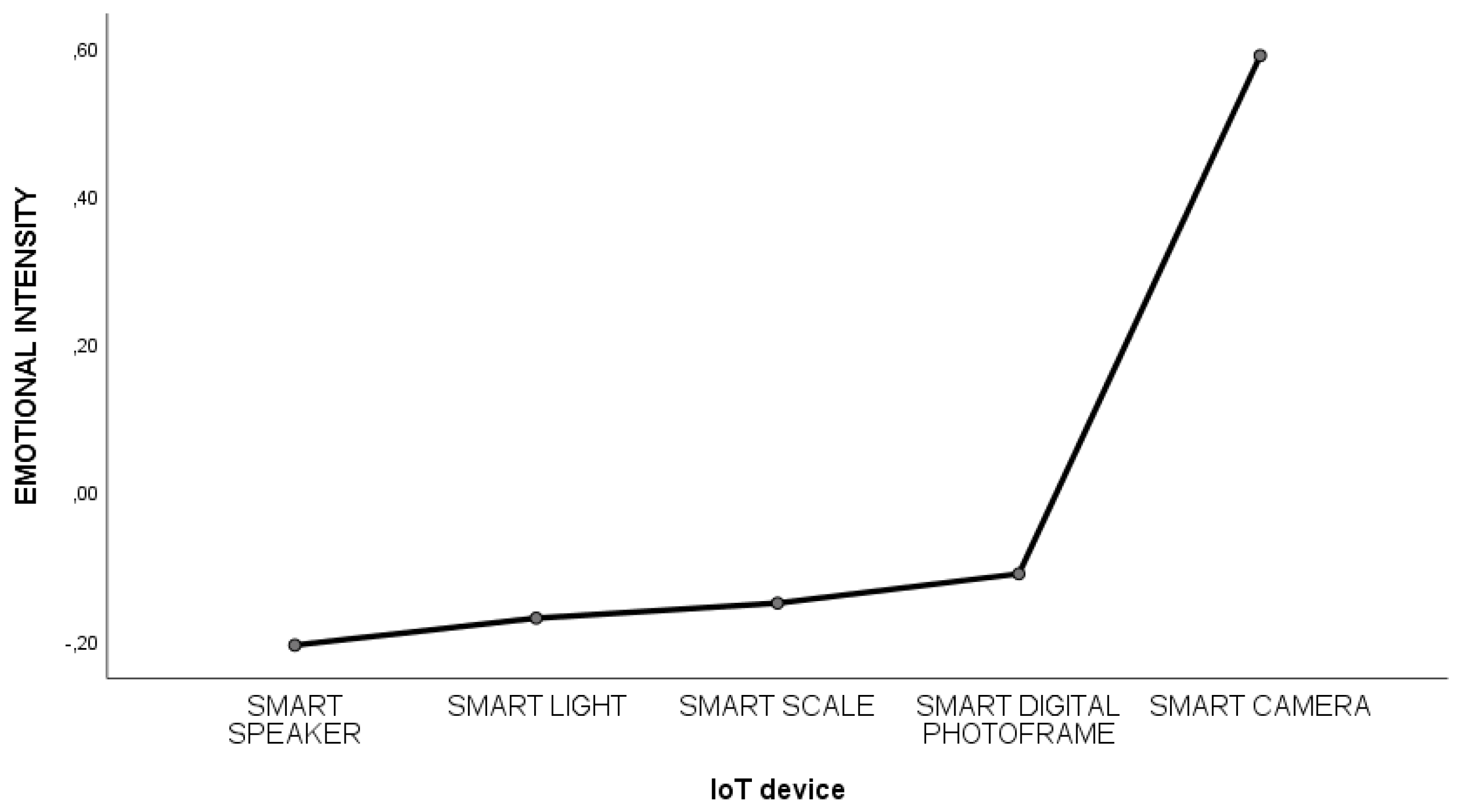
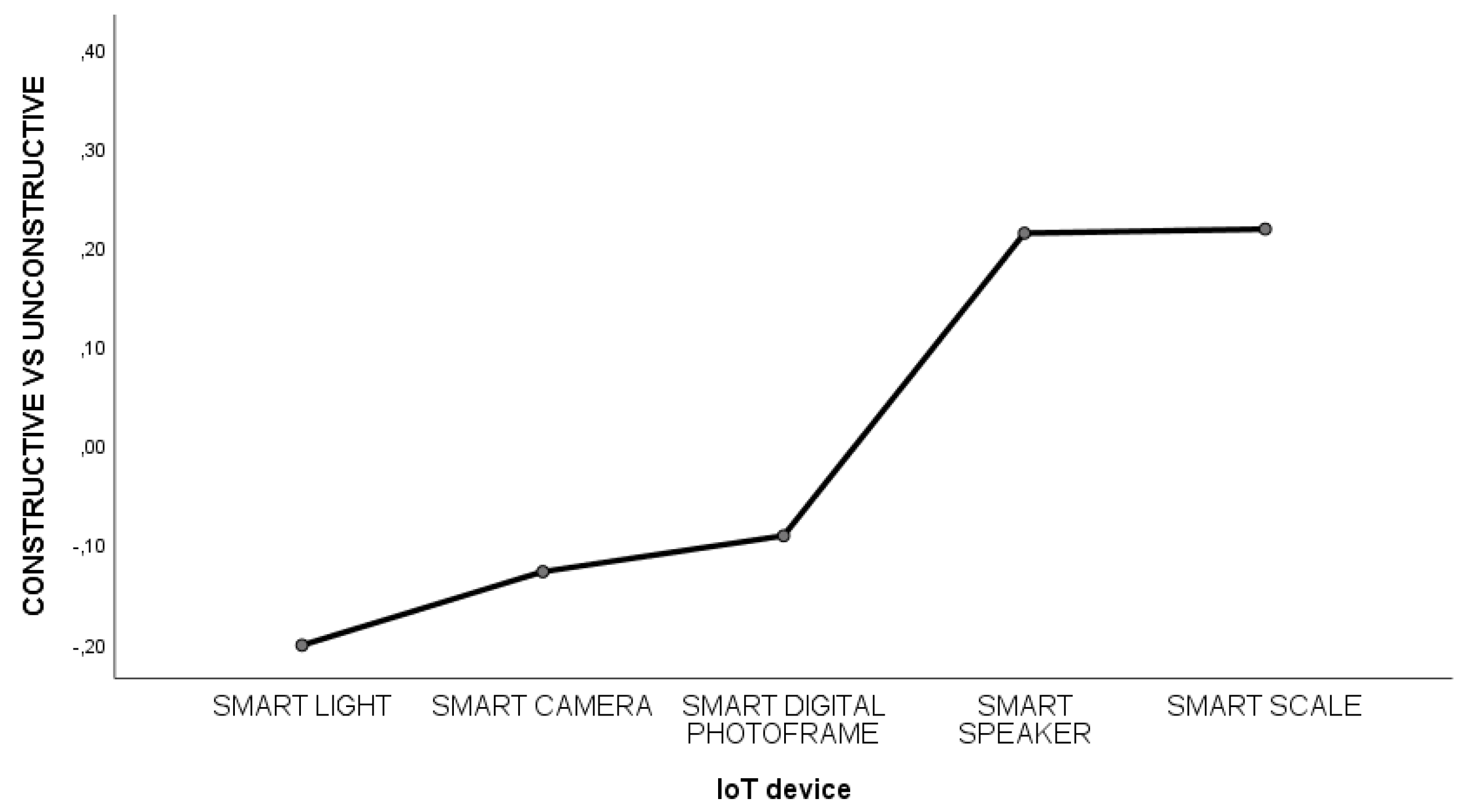
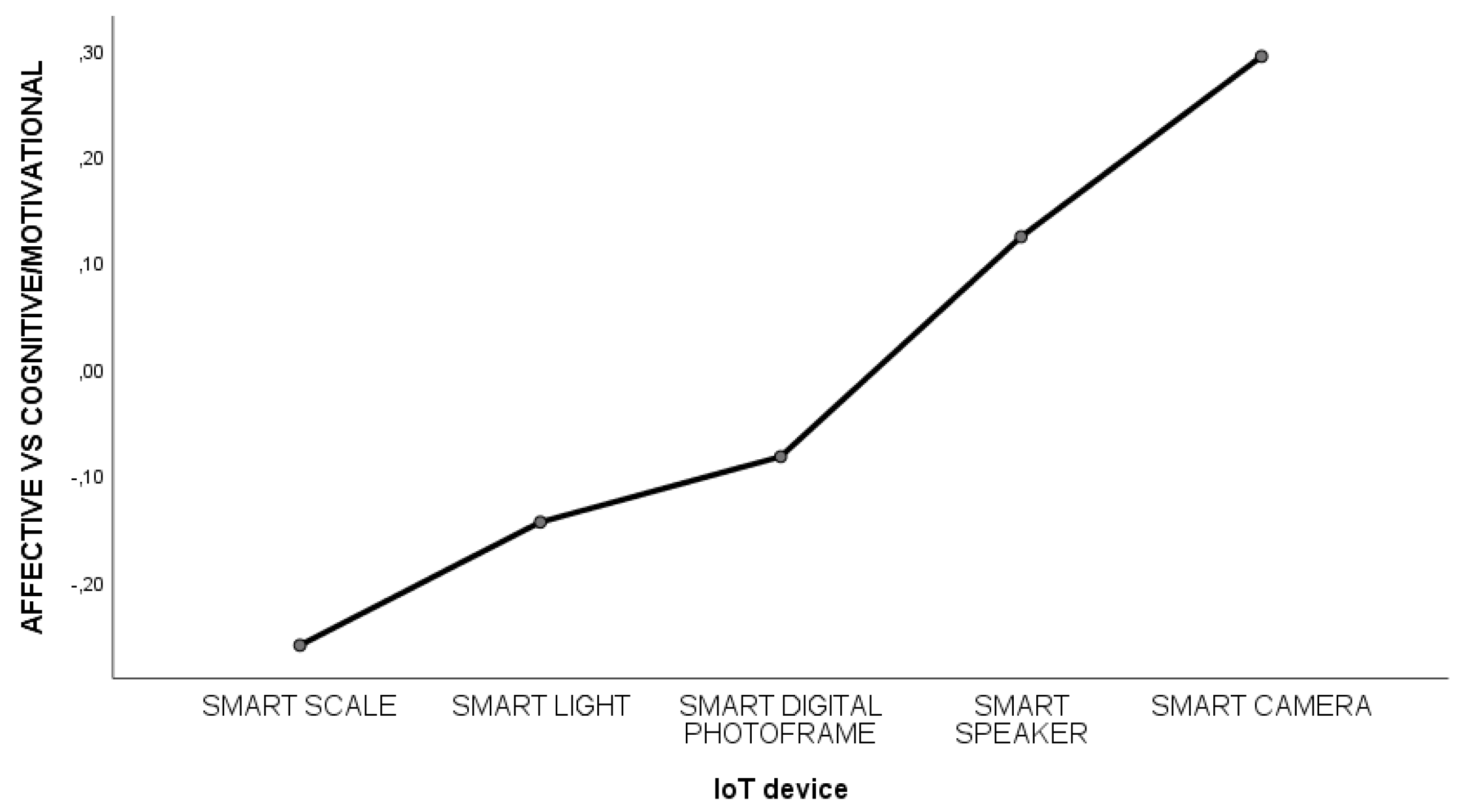
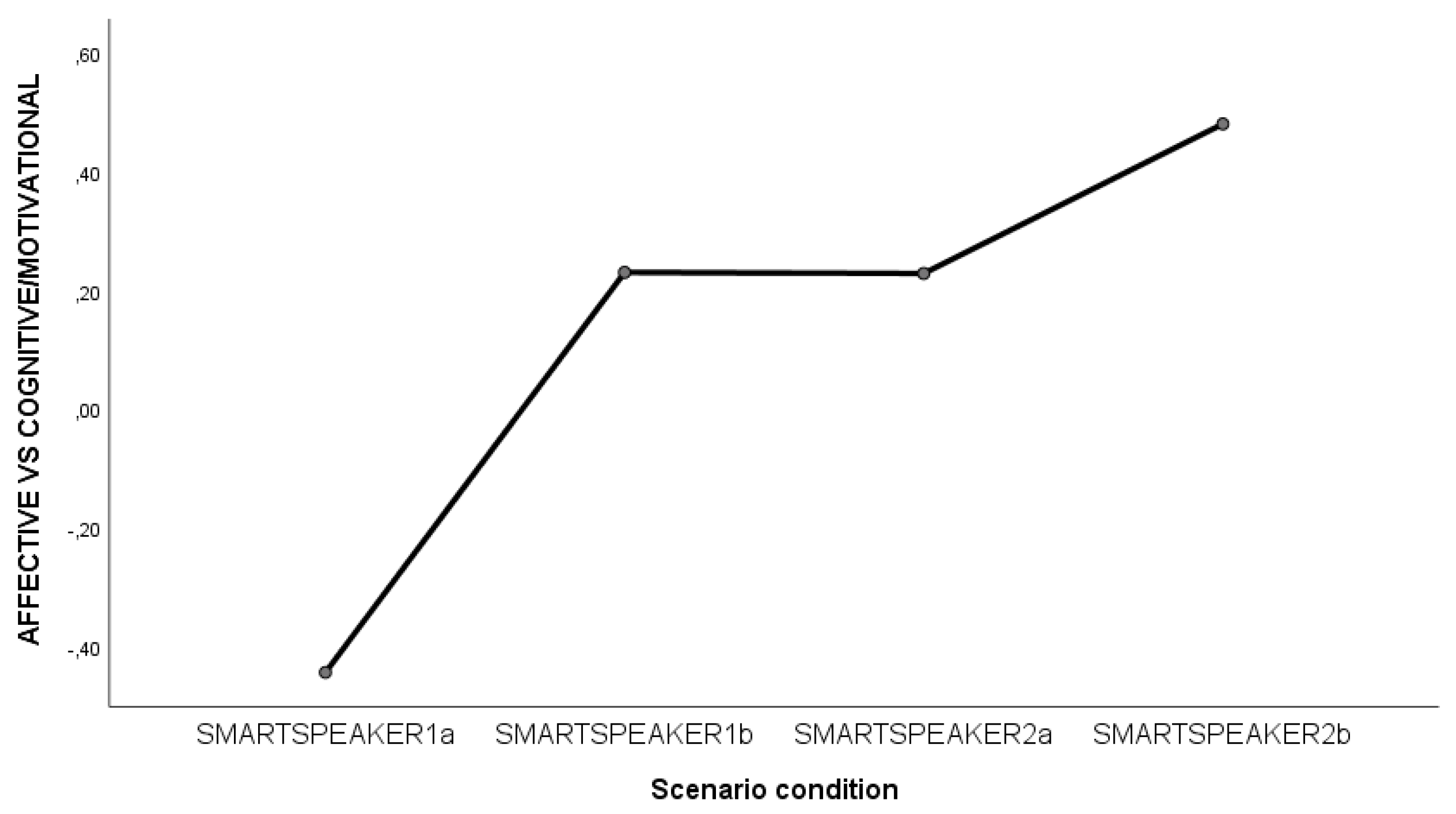
3.2.2. Differences Across Five IoT Devices in Households
3.2.3. Comparison Across Different Conditions/Intensities Across Five IoT Devices
4. Study 2
4.1. Materials and Methods
4.1.1. Participants
4.1.2. Design
4.1.3. Procedure
4.1.4. Instrument
4.2. Results
4.2.1. Underlying Structure of the Inter-Individual Differences in Emotion Processes in the Situation of Cybersecurity Breaches of IoT Devices in the Household
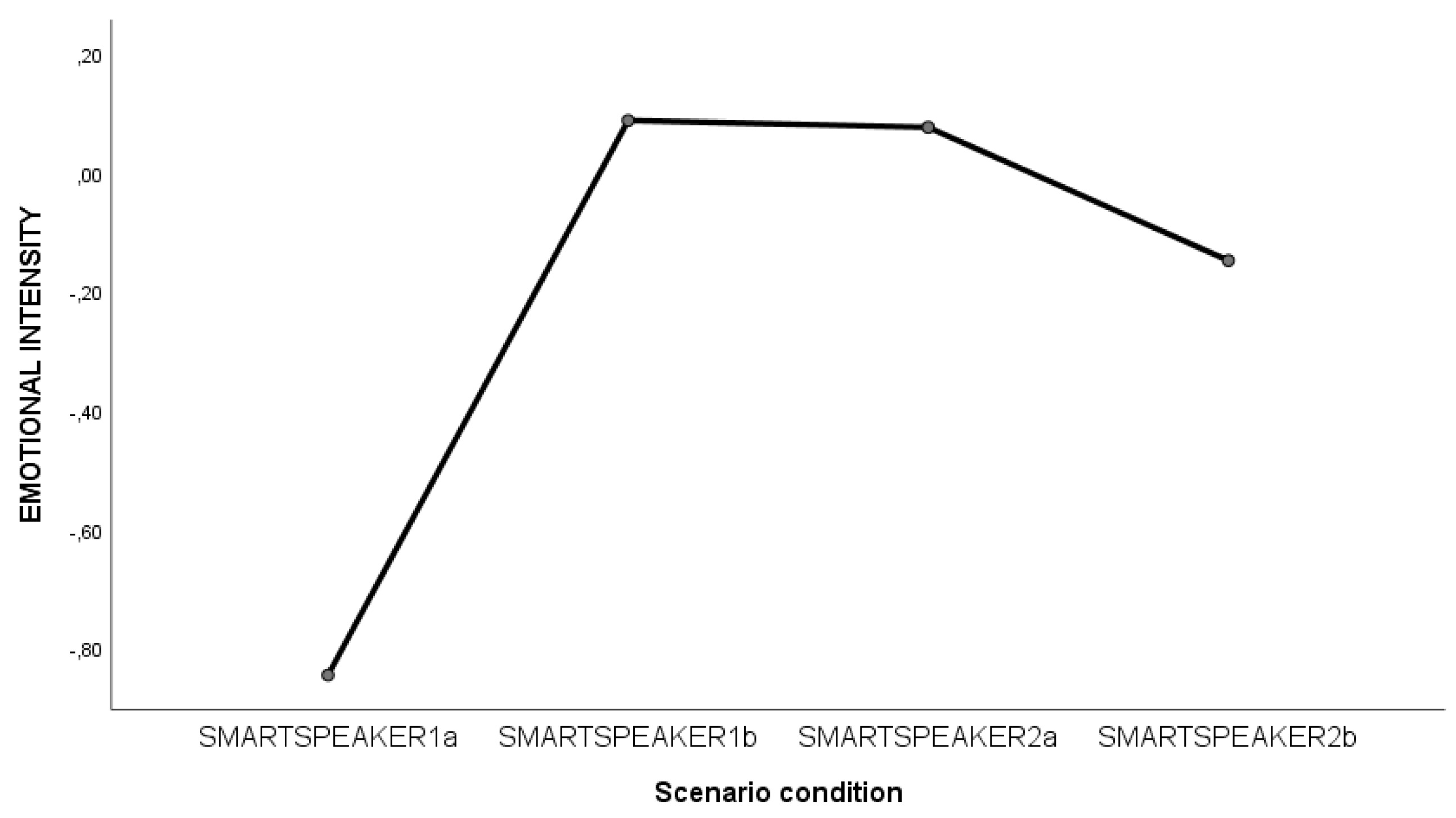
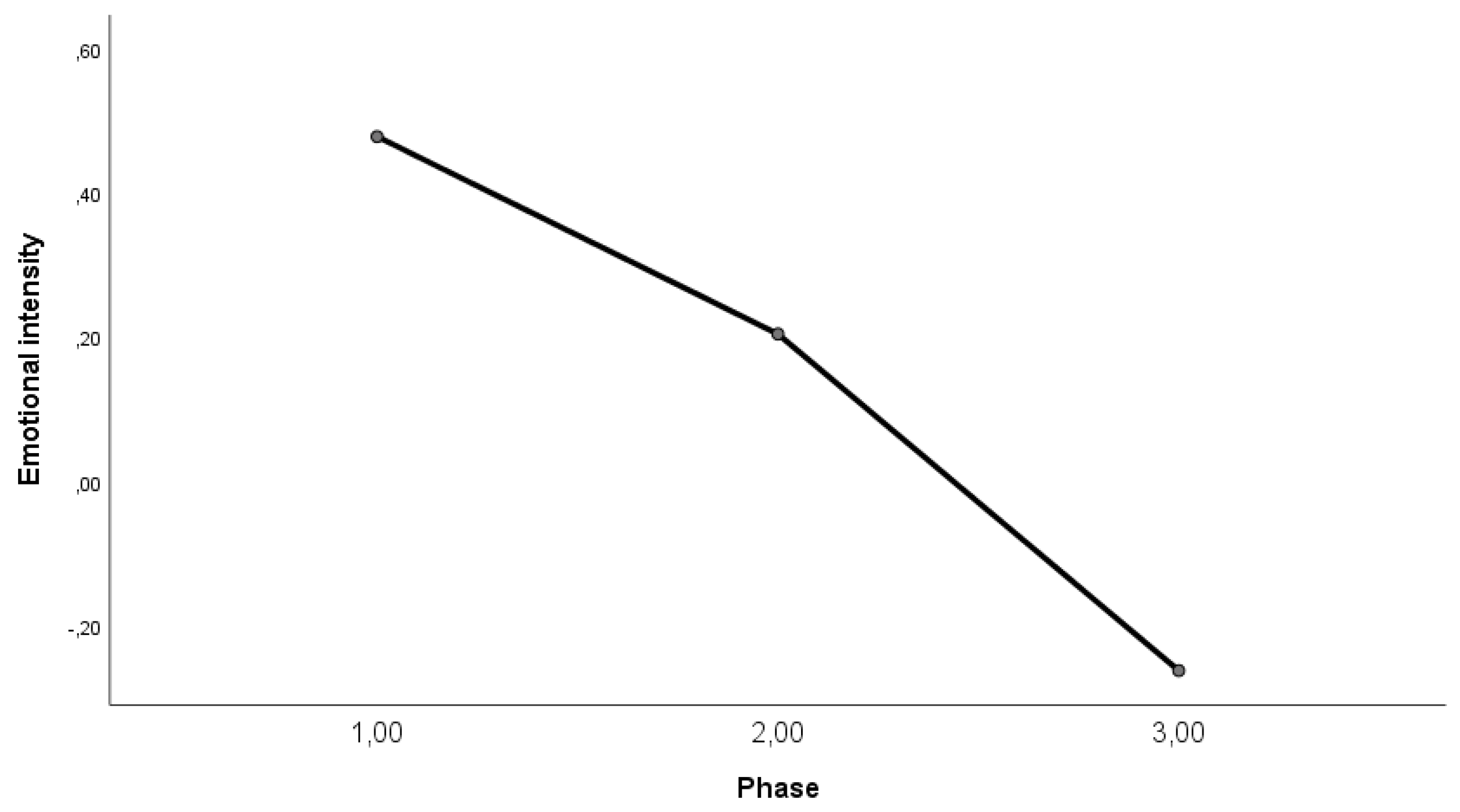
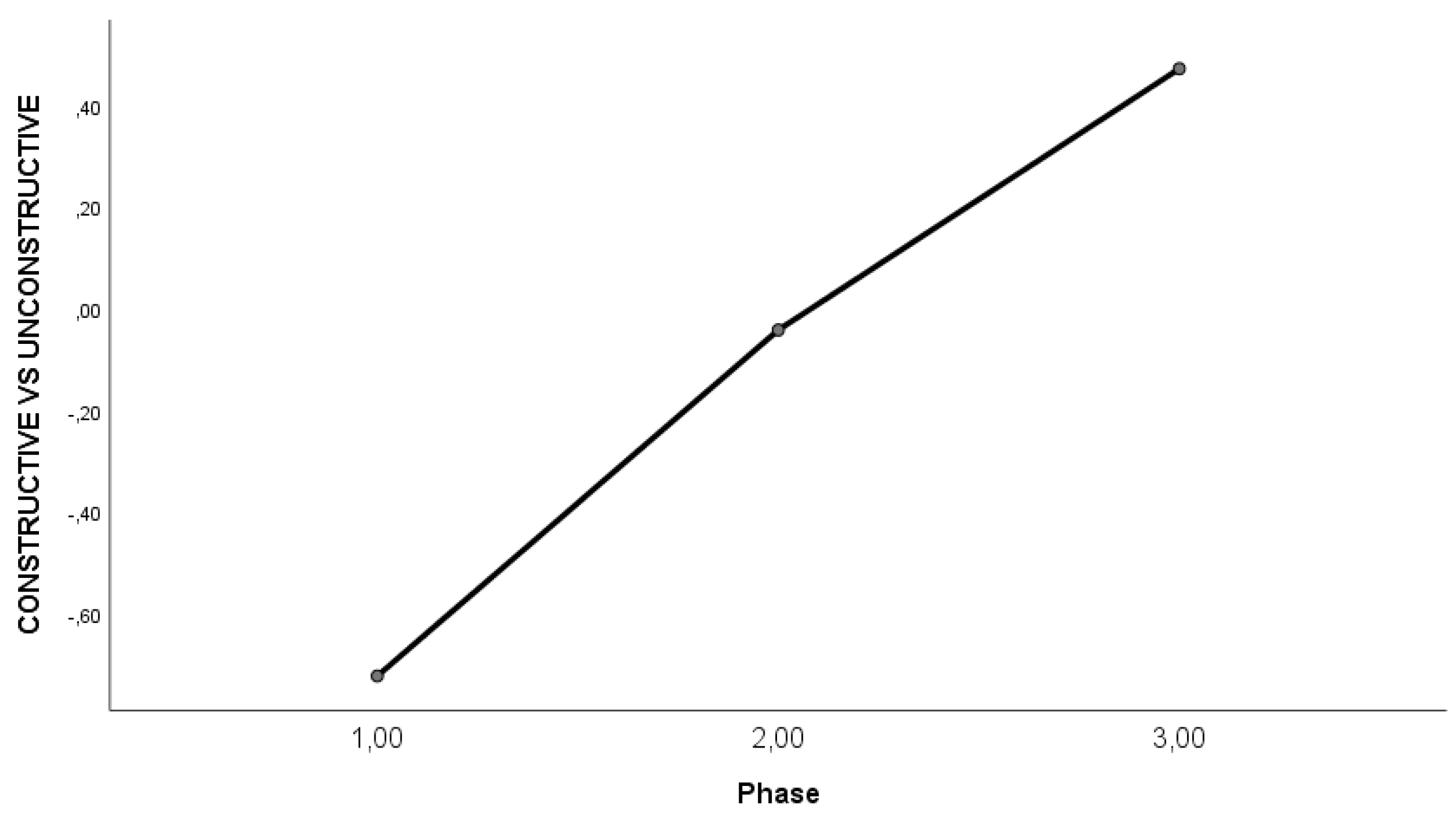
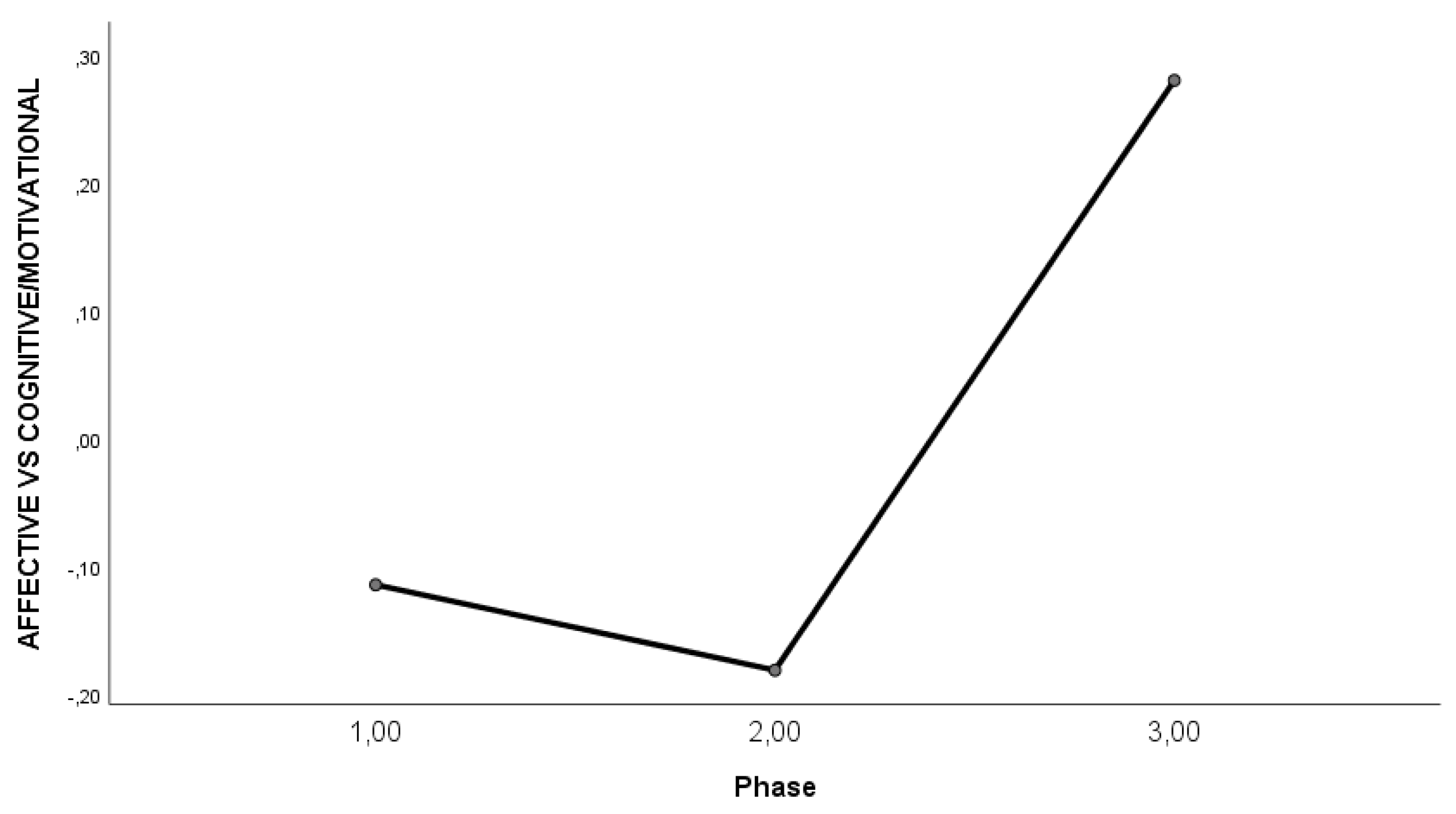
4.2.2. Differences in the Dimensions Across the Three Phases of the Field Experiment
5. Discussion
6. Limitations and Future Perspectives
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Detailed Scenarios and Emotional Response Measures for Study 1 and Study 2
| Device | Level 1 | Level 2 | Level 3 |
|---|---|---|---|
| Smart camera | Close and open with 20 s in between | Close, open, close, open, close, open, with 20 s in between | Close and open shutter in morse code: 4 times close and open (20 s in between), then a break of 40 s and then 2 times close and open |
| Smart weight scales | Delete the last existing weight from online account. | Modify last weighing point into a 3.1 kilo higher weight. | Add one false weight (latest weight +8.9 kg) to online account |
| Smart light | Toggle once (turn on when off, turn off when on) | Toggle 3 times, with appr. 20 s in between | Toggle smart light in morse code: 4 times toggle, then a break of 40 s and then 2 times toggle (with 20 s in between each off and on) |
| Smart socket | Toggle once | Toggle 3 times, with appr. 20 s in between | Toggle smart socket (and thus photo frame) in morse code: 4 times toggle, then a break of 40 s and then 2 times toggle (with 20 s in between each off and on) |
| Smart speaker | Let smart speaker say: “radio is unavailable” 1. If radio was on, this will make it stop playing. | If radio is playing then reduce volume by 50%, if radio is off, put it on and put on 20% (plus or minus 5% because it is not precise). |
| Intensity Level | SECURITY CAMERA | SCALE | LIGHT | DIGITAL PHOTOFRAME | SPEAKER |
|---|---|---|---|---|---|
| 1 | Imagine that you bought a smart security camera for your home. After some time, you notice that the shutter on your smart security camera opens without your instruction, and then closes after twenty seconds | Imagine that you bought smart scales for your home. After some time, you notice that your last measurement on the smart scales has been deleted, and you cannot retrieve it anymore. | 1a Imagine that you bought a smart light for your home. After some time, you notice that your smart light turns on without your instruction. 1b Imagine that you bought a smart light for your home. After some time, you notice that your smart light turns off without your instruction. | 1a Imagine that you bought a smart socket to which you plug a digital photo frame for your home. After some time, you notice that your digital photo frame, which is connected to the smart socket, turns itself on without your instruction. 1b Imagine that you bought a smart socket to which you plug a digital photo frame for your home. After some time, you notice that your digital photo frame, which is connected to the smart socket, turns itself off without your instruction. | 1a Imagine that you bought a smart speaker for your home. After some time, you are at home listening to the radio through your smart speaker when you notice that your smart speaker says: “Radio is unavailable” and it turns off the radio that was playing without your instruction. 1b Imagine that you bought a smart speaker for your home. After some time, you are at home when you notice that your smart speaker starts to play radio at a low volume without your instruction. |
| 2 | Imagine that you bought a smart security camera for your home. After some time, you notice that the shutter on your smart security camera starts opening and closing without your instruction, several times for a few minutes. | Imagine that you bought smart scales for your home. After some time, you notice that your last measurement on the smart scales is around 3 kg higher than you remember it, and you cannot change it. | Imagine that you bought a smart light for your home. After some time, you notice that your smart light is turning on and off without your instruction, several times in a period of one minute and then it stops. | Imagine that you bought a smart socket to which you plug a digital photo frame for your home. After some time, you notice that your digital photo frame, which is connected to the smart socket, is turning itself on and off without your instruction, several times for a period of a minute. | 2a Imagine that you bought a smart speaker for your home. After some time, you are at home listening to the radio through your smart speaker when you notice that the volume decreases without your instruction. 2b Imagine that you bought a smart speaker for your home. After some time, you are at home not listening to the radio through your smart speaker when you notice that your radio starts playing without your instruction. |
| 3 | Imagine that you bought a smart security camera for your home. After some time, you notice that the shutter on your smart security camera starts opening and closing without your instruction, several times for a few minutes, then it stops for a minute and starts again opening and closing several times and then it stops. | Imagine that you bought smart scales for your home. After some time, you notice that your last measurement on the smart scales is around 9 kg higher than you remember it, and you cannot change it. | Imagine that you bought a smart light for your home. After some time, you notice that your smart light is turning on and off without your instruction, several times over a few minutes, then it stops for a minute and starts again flickering several times, and then it stops. | Imagine that you bought a smart socket and a digital photo frame for your home. After some time, you notice that your digital photo frame, which is connected to the smart socket is turning on and off without your instruction, several times for a few minutes, then it stops for a minute and starts flickering again, several times and then it stops. |
| Emotion Feature | Emotional Intensity | Constructive vs. Unconstructive | Cognitive−Motivational vs. Affective |
|---|---|---|---|
| A1 I thought/I would think “I do not know what is happening”. | 0.38 | −0.29 | 0.01 |
| A2 I thought/I would think “I wonder whether something is wrong with the device/account”. | 0.27 | −0.55 | 0.00 |
| A3 I thought/I would think “I am confused”. | 0.39 | −0.12 | −0.05 |
| A4 I thought/I would think “My data are not available anymore” | 0.27 | 0.07 | 0.19 |
| A5 I thought/I would think “I cannot use the device or service anymore”. | 0.39 | 0.01 | 0.24 |
| A6 I thought/I would think “I cannot do much about that situation”. | 0.16 | 0.28 | 0.16 |
| A7 I thought/I would think “My trust is betrayed”. | 0.57 | 0.18 | 0.29 |
| A8 I thought/I would think “My security could be jeopardized”. | 0.64 | −0.02 | 0.55 |
| A9 I thought/I would think “The security of people close to me could be jeopardized”. | 0.64 | 0.06 | 0.51 |
| A10 I thought/I would think “It is happening because I did something wrong”. | 0.22 | 0.07 | −0.07 |
| A14 I thought/I would think “I could lose personal information, data and documents”. | 0.60 | 0.07 | 0.52 |
| A15 I thought/I would think “Someone may have access to my private information”. | 0.66 | 0.06 | 0.57 |
| A16 I thought/I would think “Someone could destroy my data”. | 0.65 | 0.12 | 0.57 |
| A17 I thought/I would think “Someone could use my data to harm me”. | 0.69 | 0.11 | 0.52 |
| A18 I thought/I would think “Similar situations might happen again in the future”. | 0.42 | −0.33 | 0.18 |
| A19 I thought/I would think “It is not safe that this device is connected to the Internet”. | 0.63 | 0.03 | 0.50 |
| AT1 I wanted to/would want to stop what was happening. | 0.47 | −0.50 | 0.03 |
| AT2 I wanted to/would want to regain control over the device/account. | 0.46 | −0.53 | 0.00 |
| AT3 I wanted to/would want to protect myself. | 0.64 | −0.19 | 0.25 |
| AT4 I wanted to/would want to stop using devices that are connected to the Internet. | 0.55 | 0.25 | 0.42 |
| AT5 I wanted to/would want to isolate myself physically. | 0.50 | 0.52 | 0.19 |
| AT6 I wanted to/would want to isolate myself in the virtual world (e.g., close my online accounts) | 0.53 | 0.41 | 0.33 |
| AT7 I wanted to/would want to change my privacy settings. | 0.63 | 0.02 | 0.35 |
| AT8 I wanted to/would want to save my data. | 0.52 | −0.11 | 0.25 |
| AT9 I wanted to/would want to find a solution and fix the problem. | 0.28 | −0.60 | −0.14 |
| AT10 I wanted to/would want to report the situation (e.g., to the police or to the internet provider). | 0.46 | −0.30 | 0.08 |
| AT11 I wanted to/would want to reset my device. | 0.33 | −0.47 | −0.07 |
| AT12 I wanted to/would want to protect my device. | 0.57 | −0.30 | 0.10 |
| AT13 I wanted to/would want to swear and curse. | 0.41 | −0.03 | −0.21 |
| AT14 I wanted to/would want to destroy whatever was close. | 0.37 | 0.53 | 0.07 |
| AT15 I wanted to/would want to take revenge. | 0.40 | 0.52 | 0.09 |
| AT16 I wanted to/would want to find and punish the attacker. | 0.49 | 0.37 | 0.14 |
| BR1 I had/would have stomach discomfort. | 0.61 | 0.43 | −0.22 |
| BR2 I was/would be dizzy. | 0.58 | 0.54 | −0.14 |
| BR3 I was/would be shaking. | 0.64 | 0.46 | −0.18 |
| BR4 I had/would have pain in the chest. | 0.56 | 0.55 | −0.14 |
| BR5 I sweated/would sweat (whole body). | 0.61 | 0.43 | −0.22 |
| BR6 My heartbeat was/would be faster. | 0.66 | 0.25 | −0.34 |
| BR7 My breathing was/would be faster. | 0.66 | 0.29 | −0.35 |
| BR8 My muscles were/would be tense. | 0.67 | 0.28 | −0.34 |
| BR9 I had/would have goosebumps. | 0.62 | 0.41 | −0.17 |
| BR10 I had/would have a dry mouth. | 0.62 | 0.46 | −0.21 |
| BR11 My body became/would become hot (puff of heat, cheeks or chest). | 0.65 | 0.38 | −0.28 |
| E1 I frowned/would frown. | 0.32 | −0.36 | −0.21 |
| E2 I had/would have tears in my eyes. | 0.55 | 0.45 | −0.18 |
| E3 I spoke/would speak louder. | 0.45 | 0.13 | −0.36 |
| E4 I had/would have a trembling voice. | 0.66 | 0.42 | −0.28 |
| E5 I slouched/ would slouch (shoulders down, head down, hands down). | 0.44 | 0.26 | −0.39 |
| E6 I covered/would cover my face with my hands. | 0.46 | 0.30 | −0.34 |
| E7 I was/would be restless (touching face, hair, biting nails, nervously kicking with legs). | 0.64 | 0.22 | −0.40 |
| E8 I was/ would be walking around nervously. | 0.67 | 0.29 | −0.34 |
| SF1 I was/would be in an intense emotional state. | 0.68 | 0.37 | −0.29 |
| SF2 I experienced/ I would experience the emotional state for a long time. | 0.65 | 0.41 | −0.27 |
| SF3 I felt/I would feel anxious. | 0.75 | 0.10 | −0.25 |
| SF4 I felt/I would feel afraid. | 0.76 | 0.27 | −0.20 |
| SF5 I felt/I would feel panic. | 0.73 | 0.23 | −0.31 |
| SF6 I felt/I would feel upset. | 0.71 | 0.07 | −0.26 |
| SF7 I felt/I would feel worried. | 0.79 | 0.02 | −0.18 |
| SF8 I felt/I would feel powerless. | 0.65 | 0.14 | −0.27 |
| SF9 I felt/I would feel sad. | 0.56 | 0.15 | −0.36 |
| SF10 I felt/I would feel ashamed. | 0.49 | 0.53 | −0.13 |
| SF11 I felt/I would feel angry. | 0.64 | 0.02 | −0.29 |
| SF12 I felt/I would feel frustrated. | 0.56 | −0.21 | −0.36 |
| SF13 I felt/I would feel surprised. | 0.29 | −0.09 | −0.23 |
| SF14 I felt/I would feel uncomfortable. | 0.72 | 0.07 | −0.16 |
| ER1 I wanted to ask others to help me in solving the problem. | 0.43 | −0.31 | −0.09 |
| ER2 I wanted people to comfort me. | 0.63 | 0.25 | −0.18 |
| ER3 I tried to calm myself down (e.g., by breathing deeply) | 0.62 | 0.09 | −0.18 |
| ER4 I tried to suppress my feelings and control myself. | 0.57 | −0.08 | −0.16 |
| ER5 I tried to make the best out of the situation. | 0.08 | −0.32 | −0.06 |
| ER6 I tried to see the positive side of the situation | 0.01 | −0.17 | −0.03 |
| ER7 I could not stop thinking and analyzing the situation. | 0.50 | 0.03 | −0.22 |
| ER8 I had trouble concentrating. | 0.65 | 0.20 | −0.35 |


| Emotion Feature | Emotional Intensity | Constructive vs. Unconstructive | Cognitive−Motivational vs. Affective | Sympathetic Arousal vs. Distress Symptoms |
|---|---|---|---|---|
| A1 I thought/I would think “I do not know what is happening.” | 0.33 | −0.43 | 0.00 | −0.13 |
| A2 I thought/I would think “I wonder whether something is wrong with the device/account.” | 0.40 | −0.54 | 0.03 | 0.17 |
| A3 I thought/I would think “I am confused.” | 0.47 | −0.19 | −0.26 | 0.29 |
| A4 I thought/I would think “My data are not available anymore.” | 0.64 | −0.02 | 0.19 | −0.08 |
| A5 I thought/I would think “I cannot use the device or service anymore.” | 0.48 | −0.40 | 0.16 | 0.11 |
| A6 I thought/I would think “I cannot do much about that situation.” | 0.28 | −0.40 | 0.08 | −0.13 |
| A7 I thought/I would think “My trust is betrayed.” | 0.50 | −0.19 | 0.23 | 0.04 |
| A8 I thought/I would think “My security could be jeopardized.” | 0.64 | 0.26 | 0.34 | 0.14 |
| A9 I thought/I would think “The security of people close to me could be jeopardized.” | 0.64 | 0.33 | 0.25 | 0.17 |
| A10 I thought/I would think “It is happening because I did something wrong.” | 0.31 | −0.09 | −0.33 | −0.38 |
| A14 I thought/I would think “I could lose personal information0. data and documents.” | 0.59 | 0.23 | 0.15 | −0.14 |
| A15 I thought/I would think “Someone may have access to my private information.” | 0.57 | 0.23 | 0.38 | −0.13 |
| A16 I thought/I would think “Someone could destroy my data.” | 0.69 | 0.37 | 0.39 | 0.10 |
| A17 I thought/I would think “Someone could use my data to harm me.” | 0.66 | 0.39 | 0.38 | 0.05 |
| A18 I thought/I would think “Similar situations might happen again in the future.” | 0.39 | −0.45 | −0.08 | 0.00 |
| A19 I thought/I would think “It is not safe that this device is connected to the Internet.” | 0.47 | 0.02 | 0.47 | −0.12 |
| AT1 I wanted to/would want to stop what was happening. | 0.41 | −0.34 | −0.21 | 0.07 |
| AT2 I wanted to/would want to regain control over the device/account. | 0.34 | −0.56 | −0.08 | 0.04 |
| AT3 I wanted to/would want to protect myself. | 0.66 | 0.14 | 0.12 | −0.04 |
| AT4 I wanted to/would want to stop using devices that are connected to the Internet. | 0.48 | 0.14 | 0.11 | 0.06 |
| AT5 I wanted to/would want to isolate myself physically. | 0.73 | 0.45 | 0.07 | 0.03 |
| AT6 I wanted to/would want to isolate myself in the virtual world (e.g., close my online accounts) | 0.69 | 0.39 | 0.13 | 0.02 |
| AT7 I wanted to/would want to change my privacy settings. | 0.66 | 0.39 | 0.24 | 0.03 |
| AT8 I wanted to/would want to save my data. | 0.64 | 0.26 | 0.08 | 0.07 |
| AT9 I wanted to/would want to find a solution and fix the problem. | 0.44 | −0.55 | −0.18 | 0.04 |
| AT10 I wanted to/would want to report the situation (e.g., to the police or to the internet provider). | 0.41 | −0.44 | 0.19 | −0.14 |
| AT11 I wanted to/would want to reset my device. | 0.59 | −0.29 | 0.04 | 0.39 |
| AT12 I wanted to/would want to protect my device. | 0.68 | 0.06 | 0.17 | 0.03 |
| AT13 I wanted to/would want to swear and curse. | 0.58 | 0.00 | −0.25 | 0.30 |
| AT14 I wanted to/would want to destroy whatever was close. | 0.66 | 0.45 | 0.10 | 0.12 |
| BR1 I had/would have stomach discomfort. | 0.58 | 0.07 | −0.15 | −0.52 |
| BR2 I was/would be dizzy. | 0.74 | 0.54 | 0.09 | 0.11 |
| BR3 I was/would be shaking. | 0.76 | 0.55 | 0.06 | 0.08 |
| BR4 I had/would have pain in the chest. | 0.73 | 0.57 | 0.04 | 0.11 |
| BR5 I sweated/would sweat (whole body). | 0.73 | 0.57 | 0.04 | 0.11 |
| BR6 My heartbeat was/would be faster. | 0.58 | 0.23 | −0.35 | 0.30 |
| BR7 My breathing was/would be faster. | 0.63 | 0.28 | −0.30 | 0.24 |
| BR8 My muscles were/would be tense. | 0.70 | 0.39 | −0.19 | 0.21 |
| BR9 I had/would have goosebumps. | 0.76 | 0.54 | −0.02 | 0.10 |
| BR10 I had/would have a dry mouth. | 0.71 | 0.54 | −0.03 | 0.08 |
| BR11 My body became/would become hot (puff of heat. cheeks or chest). | 0.73 | 0.49 | −0.10 | 0.11 |
| E1 I frowned/would frown. | 0.33 | −0.29 | −0.37 | −0.02 |
| E2 I had/would have tears in my eyes. | 0.69 | 0.49 | 0.00 | 0.08 |
| E3 I spoke/would speak louder. | 0.48 | −0.02 | −0.28 | 0.21 |
| E4 I had/would have a trembling voice. | 0.73 | 0.49 | −0.07 | 0.05 |
| E5 I slouched/would slouch (shoulders down. head down. hands down). | 0.68 | 0.09 | −0.31 | 0.03 |
| E6 I covered/would cover my face with my hands. | 0.63 | 0.24 | −0.23 | 0.17 |
| E7 I was/would be restless (touching face. hair. biting nails. nervously kicking with legs). | 0.70 | 0.27 | −0.24 | 0.05 |
| E8 I was/would be walking around nervously. | 0.65 | 0.25 | −0.27 | −0.02 |
| SF1 I was/would be in an intense emotional state. | 0.63 | 0.32 | −0.24 | 0.27 |
| SF2 I experienced/I would experience the emotional state for a long time. | 0.74 | 0.39 | −0.17 | 0.02 |
| SF3 I felt/I would feel anxious. | 0.60 | −0.02 | −0.24 | −0.48 |
| SF4 I felt/I would feel afraid. | 0.74 | 0.39 | −0.10 | −0.11 |
| SF5 I felt/I would feel panic. | 0.67 | 0.44 | −0.17 | 0.00 |
| SF6 I felt/I would feel upset. | 0.63 | 0.03 | −0.42 | 0.06 |
| SF7 I felt/I would feel worried. | 0.57 | 0.01 | −0.15 | −0.55 |
| SF8 I felt/I would feel powerless. | 0.55 | −0.31 | −0.27 | −0.23 |
| SF9 I felt/I would feel sad. | 0.65 | 0.02 | −0.30 | −0.23 |
| SF10 I felt/I would feel ashamed. | 0.48 | 0.24 | −0.30 | −0.48 |
| SF11 I felt/I would feel angry. | 0.57 | −0.13 | −0.43 | 0.07 |
| SF12 I felt/I would feel frustrated. | 0.49 | −0.34 | −0.46 | 0.15 |
| SF13 I felt/I would feel surprised. | 0.28 | −0.15 | 0.20 | −0.13 |
| SF14 I felt/I would feel uncomfortable. | 0.57 | −0.08 | −0.14 | −0.53 |
| ER1 I wanted to ask others to help me in solving the problem. | 0.56 | −0.42 | −0.11 | −0.11 |
| ER2 I wanted people to comfort me. | 0.72 | 0.37 | −0.15 | 0.06 |
| ER3 I tried to calm myself down (e.g., by breathing deeply) | 0.69 | 0.25 | −0.32 | 0.16 |
| ER4 I tried to suppress my feelings and control myself. | 0.70 | 0.09 | −0.35 | 0.10 |
| ER5 I tried to make the best out of the situation. | 0.30 | −0.31 | 0.07 | −0.27 |
| ER6 I tried to see the positive side of the situation | 0.30 | −0.11 | 0.11 | −0.34 |
| ER7 I could not stop thinking and analysing the situation. | 0.60 | −0.10 | −0.28 | −0.09 |
| ER8 I had trouble concentrating. | 0.68 | 0.18 | −0.15 | −0.13 |
Appendix B. Statistical Analysis of Device-Specific Emotional Responses in Study 2
| Between-Subjects Factors | |||
| Value Label | N | ||
| DEVICE | 1.00 | CAMERA | 8 |
| 2.00 | SCALE | 13 | |
| 3.00 | LIGHT | 28 | |
| 4.00 | FRAME | 12 | |
| 5.00 | SPEAKER | 40 | |
| 6.00 | SENSORS | 14 | |
| 7.00 | INFRASTRUCTURE | 21 | |
| Tests of Between-Subjects Effects | ||||||
| Dependent Variable: GRID: GENERAL | ||||||
| Source | Type III Sum of Squares | df | Mean Square | F | Sig. | Partial Eta Squared |
| Corrected Model | 7.115 a | 6 | 1.186 | 1.354 | 0.238 | 0.059 |
| Intercept | 0.731 | 1 | 0.731 | 0.835 | 0.363 | 0.006 |
| DEVICE | 7.115 | 6 | 1.186 | 1.354 | 0.238 | 0.059 |
| Error | 112.938 | 129 | 0.875 | |||
| Total | 120.229 | 136 | ||||
| Corrected Total | 120.053 | 135 | ||||
| a. R Squared = 0.059 (Adjusted R Squared = 0.016). | ||||||
| DEVICE | ||||
| Dependent Variable: GRID: GENERAL | ||||
| DEVICE | Mean | Std. Error | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||
| CAMERA | 0.530 | 0.331 | −0.124 | 1.185 |
| SCALE | 0.067 | 0.260 | −0.447 | 0.580 |
| LIGHT | −0.168 | 0.177 | −0.518 | 0.182 |
| FRAME | 0.318 | 0.270 | −0.217 | 0.852 |
| SPEAKER | 0.070 | 0.148 | −0.223 | 0.363 |
| SENSORS | −0.398 | 0.250 | −0.893 | 0.096 |
| INFRASTRUCTURE | 0.164 | 0.204 | −0.240 | 0.568 |
| Multiple Comparisons | ||||||
| Dependent Variable: GRID: GENERAL | ||||||
| Tukey HSD | ||||||
| (I) DEVICE | (J) DEVICE | Mean Difference (I−J) | Std. Error | Sig. | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||||
| CAMERA | SCALE | 0.4634 | 0.42045 | 0.926 | −0.7961 | 1.7228 |
| LIGHT | 0.6979 | 0.37510 | 0.510 | −0.4257 | 1.8215 | |
| FRAME | 0.2125 | 0.42708 | 0.999 | −1.0668 | 1.4917 | |
| SPEAKER | 0.4603 | 0.36239 | 0.864 | −0.6252 | 1.5458 | |
| SENSORS | 0.9286 | 0.41469 | 0.282 | −0.3135 | 2.1708 | |
| INFRASTRUCTURE | 0.3660 | 0.38875 | 0.965 | −0.7985 | 1.5304 | |
| SCALE | CAMERA | −0.4634 | 0.42045 | 0.926 | −1.7228 | 0.7961 |
| LIGHT | 0.2345 | 0.31403 | 0.989 | −0.7061 | 1.1752 | |
| FRAME | −0.2509 | 0.37457 | 0.994 | −1.3729 | 0.8711 | |
| SPEAKER | −0.0031 | 0.29872 | 1.000 | −0.8979 | 0.8917 | |
| SENSORS | 0.4653 | 0.36039 | 0.855 | −0.6142 | 1.5448 | |
| INFRASTRUCTURE | −0.0974 | 0.33020 | 1.000 | −1.0865 | 0.8917 | |
| LIGHT | CAMERA | −0.6979 | 0.37510 | 0.510 | −1.8215 | 0.4257 |
| SCALE | −0.2345 | 0.31403 | 0.989 | −1.1752 | 0.7061 | |
| FRAME | −0.4854 | 0.32284 | 0.742 | −1.4525 | 0.4816 | |
| SPEAKER | −0.2377 | 0.23055 | 0.946 | −0.9283 | 0.4529 | |
| SENSORS | 0.2307 | 0.30627 | 0.989 | −0.6867 | 1.1481 | |
| INFRASTRUCTURE | −0.3320 | 0.27011 | 0.882 | −1.1410 | 0.4771 | |
| FRAME | CAMERA | −0.2125 | 0.42708 | 0.999 | −1.4917 | 1.0668 |
| SCALE | 0.2509 | 0.37457 | 0.994 | −0.8711 | 1.3729 | |
| LIGHT | 0.4854 | 0.32284 | 0.742 | −0.4816 | 1.4525 | |
| SPEAKER | 0.2478 | 0.30797 | 0.984 | −0.6747 | 1.1703 | |
| SENSORS | 0.7162 | 0.36809 | 0.454 | −0.3864 | 1.8188 | |
| INFRASTRUCTURE | 0.1535 | 0.33860 | 0.999 | −0.8607 | 1.1677 | |
| SPEAKER | CAMERA | −0.4603 | 0.36239 | 0.864 | −1.5458 | 0.6252 |
| SCALE | 0.0031 | 0.29872 | 1.000 | −0.8917 | 0.8979 | |
| LIGHT | 0.2377 | 0.23055 | 0.946 | −0.4529 | 0.9283 | |
| FRAME | −0.2478 | 0.30797 | 0.984 | −1.1703 | 0.6747 | |
| SENSORS | 0.4684 | 0.29055 | 0.675 | −0.4019 | 1.3387 | |
| INFRASTRUCTURE | −0.0943 | 0.25215 | 1.000 | −0.8496 | 0.6610 | |
| SENSORS | CAMERA | −0.9286 | 0.41469 | 0.282 | −2.1708 | 0.3135 |
| SCALE | −0.4653 | 0.36039 | 0.855 | −1.5448 | 0.6142 | |
| LIGHT | −0.2307 | 0.30627 | 0.989 | −1.1481 | 0.6867 | |
| FRAME | −0.7162 | 0.36809 | 0.454 | −1.8188 | 0.3864 | |
| SPEAKER | −0.4684 | 0.29055 | 0.675 | −1.3387 | 0.4019 | |
| INFRASTRUCTURE | −0.5627 | 0.32284 | 0.589 | −1.5297 | 0.4044 | |
| INFRASTRUCTURE | CAMERA | −0.3660 | 0.38875 | 0.965 | −1.5304 | 0.7985 |
| SCALE | 0.0974 | 0.33020 | 1.000 | −0.8917 | 1.0865 | |
| LIGHT | 0.3320 | 0.27011 | 0.882 | −0.4771 | 1.1410 | |
| FRAME | −0.1535 | 0.33860 | 0.999 | −1.1677 | 0.8607 | |
| SPEAKER | 0.0943 | 0.25215 | 1.000 | −0.6610 | 0.8496 | |
| SENSORS | 0.5627 | 0.32284 | 0.589 | −0.4044 | 1.5297 | |
| Based on observed means. The error term is Mean Square(Error) = 0.875. | ||||||
| GRID: GENERAL | ||
| Tukey HSD a,b,c | ||
| DEVICE | N | Subset |
| 1 | ||
| SENSORS | 14 | −0.3984 |
| LIGHT | 28 | −0.1677 |
| SCALE | 13 | 0.0669 |
| SPEAKER | 40 | 0.0700 |
| INFRASTRUCTURE | 21 | 0.1643 |
| FRAME | 12 | 0.3178 |
| CAMERA | 8 | 0.5302 |
| Sig. | 0.101 | |
| Means for groups in homogeneous subsets are displayed. Based on observed means. The error term is Mean Square(Error) = 0.875. | ||
| a. Uses Harmonic Mean Sample Size = 15.053. | ||
| b. The group sizes are unequal. The harmonic mean of the group sizes is used. Type I error levels are not guaranteed. | ||
| c. Alpha = 0.05. | ||
| Between-Subjects Factors | |||
| Value Label | N | ||
| DEVICE | 1.00 | CAMERA | 8 |
| 2.00 | SCALE | 13 | |
| 3.00 | LIGHT | 28 | |
| 4.00 | FRAME | 12 | |
| 5.00 | SPEAKER | 40 | |
| 6.00 | SENSORS | 14 | |
| 7.00 | INFRASTRUCTURE | 21 | |
| Tests of Between-Subjects Effects | ||||||
| Dependent Variable: GRID: CONSTRUCTIVE VS UNCONSTRUCTIVE | ||||||
| Source | Type III Sum of Squares | df | Mean Square | F | Sig. | Partial Eta Squared |
| Corrected Model | 7.508 a | 6 | 1.251 | 1.454 | 0.199 | 0.063 |
| Intercept | 5.447 | 1 | 5.447 | 6.328 | 0.013 | 0.047 |
| DEVICE | 7.508 | 6 | 1.251 | 1.454 | 0.199 | 0.063 |
| Error | 111.049 | 129 | 0.861 | |||
| Total | 121.767 | 136 | ||||
| Corrected Total | 118.558 | 135 | ||||
| a. R Squared = 0.063 (Adjusted R Squared = 0.020) | ||||||
| DEVICE | ||||
| Dependent Variable: GRID: CONSTRUCTIVE VS UNCONSTRUCTIVE | ||||
| DEVICE | Mean | Std. Error | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||
| CAMERA | −0.756 | 0.328 | −1.405 | −0.107 |
| SCALE | −0.571 | 0.257 | −1.081 | −0.062 |
| LIGHT | −0.155 | 0.175 | −0.502 | 0.192 |
| FRAME | 0.071 | 0.268 | −0.458 | 0.601 |
| SPEAKER | 0.008 | 0.147 | −0.282 | 0.299 |
| SENSORS | 0.044 | 0.248 | −0.447 | 0.534 |
| INFRASTRUCTURE | −0.233 | 0.202 | −0.633 | 0.168 |
| Multiple Comparisons | ||||||
| Dependent Variable: GRID: CONSTRUCTIVE VS UNCONSTRUCTIVE | ||||||
| Tukey HSD | ||||||
| (I) DEVICE | (J) DEVICE | Mean Difference (I−J) | Std. Error | Sig. | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||||
| CAMERA | SCALE | −0.1848 | 0.41692 | 0.999 | −1.4336 | 1.0641 |
| LIGHT | −0.6016 | 0.37195 | 0.671 | −1.7158 | 0.5125 | |
| FRAME | −0.8277 | 0.42349 | 0.449 | −2.0963 | 0.4408 | |
| SPEAKER | −0.7646 | 0.35934 | 0.343 | −1.8410 | 0.3118 | |
| SENSORS | −0.7999 | 0.41121 | 0.455 | −2.0316 | 0.4318 | |
| INFRASTRUCTURE | −0.5237 | 0.38548 | 0.823 | −1.6783 | 0.6310 | |
| SCALE | CAMERA | 0.1848 | 0.41692 | 0.999 | −1.0641 | 1.4336 |
| LIGHT | −0.4169 | 0.31139 | 0.832 | −1.3496 | 0.5159 | |
| FRAME | −0.6429 | 0.37142 | 0.597 | −1.7555 | 0.4696 | |
| SPEAKER | −0.5798 | 0.29621 | 0.447 | −1.4671 | 0.3074 | |
| SENSORS | −0.6151 | 0.35736 | 0.603 | −1.6856 | 0.4553 | |
| INFRASTRUCTURE | −0.3389 | 0.32743 | 0.945 | −1.3197 | 0.6419 | |
| LIGHT | CAMERA | 0.6016 | 0.37195 | 0.671 | −0.5125 | 1.7158 |
| SCALE | 0.4169 | 0.31139 | 0.832 | −0.5159 | 1.3496 | |
| FRAME | −0.2261 | 0.32013 | 0.992 | −1.1850 | 0.7328 | |
| SPEAKER | −0.1630 | 0.22862 | 0.992 | −0.8478 | 0.5218 | |
| SENSORS | −0.1983 | 0.30370 | 0.995 | −1.1080 | 0.7114 | |
| INFRASTRUCTURE | 0.0780 | 0.26784 | 1.000 | −0.7243 | 0.8803 | |
| FRAME | CAMERA | 0.8277 | 0.42349 | 0.449 | −0.4408 | 2.0963 |
| SCALE | 0.6429 | 0.37142 | 0.597 | −0.4696 | 1.7555 | |
| LIGHT | 0.2261 | 0.32013 | 0.992 | −0.7328 | 1.1850 | |
| SPEAKER | 0.0631 | 0.30538 | 1.000 | −0.8516 | 0.9779 | |
| SENSORS | 0.0278 | 0.36500 | 1.000 | −1.0655 | 1.1212 | |
| INFRASTRUCTURE | 0.3041 | 0.33575 | 0.971 | −0.7016 | 1.3098 | |
| SPEAKER | CAMERA | 0.7646 | 0.35934 | 0.343 | −0.3118 | 1.8410 |
| SCALE | 0.5798 | 0.29621 | 0.447 | −0.3074 | 1.4671 | |
| LIGHT | 0.1630 | 0.22862 | 0.992 | −0.5218 | 0.8478 | |
| FRAME | −0.0631 | 0.30538 | 1.000 | −0.9779 | 0.8516 | |
| SENSORS | −0.0353 | 0.28812 | 1.000 | −0.8983 | 0.8277 | |
| INFRASTRUCTURE | 0.2410 | 0.25003 | 0.961 | −0.5080 | 0.9899 | |
| SENSORS | CAMERA | 0.7999 | 0.41121 | 0.455 | −0.4318 | 2.0316 |
| SCALE | 0.6151 | 0.35736 | 0.603 | −0.4553 | 1.6856 | |
| LIGHT | 0.1983 | 0.30370 | 0.995 | −0.7114 | 1.1080 | |
| FRAME | −0.0278 | 0.36500 | 1.000 | −1.1212 | 1.0655 | |
| SPEAKER | 0.0353 | 0.28812 | 1.000 | −0.8277 | 0.8983 | |
| INFRASTRUCTURE | 0.2762 | 0.32013 | 0.977 | −0.6827 | 1.2352 | |
| INFRASTRUCTURE | CAMERA | 0.5237 | 0.38548 | 0.823 | −0.6310 | 1.6783 |
| SCALE | 0.3389 | 0.32743 | 0.945 | −0.6419 | 1.3197 | |
| LIGHT | −0.0780 | 0.26784 | 1.000 | −0.8803 | 0.7243 | |
| FRAME | −0.3041 | 0.33575 | 0.971 | −1.3098 | 0.7016 | |
| SPEAKER | −0.2410 | 0.25003 | 0.961 | −0.9899 | 0.5080 | |
| SENSORS | −0.2762 | 0.32013 | 0.977 | −1.2352 | 0.6827 | |
| Based on observed means 0. The error term is Mean Square(Error) = 0.861. | ||||||
| GRID: CONSTRUCTIVE VS UNCONSTRUCTIVE | ||
| Tukey HSD a,b,c | ||
| DEVICE | N | Subset |
| 1 | ||
| CAMERA | 8 | −0.7563 |
| SCALE | 13 | −0.5715 |
| INFRASTRUCTURE | 21 | −0.2326 |
| LIGHT | 28 | −0.1546 |
| SPEAKER | 40 | 0.0083 |
| SENSORS | 14 | 0.0436 |
| FRAME | 12 | 0.0715 |
| Sig. | 0.188 | |
| Means for groups in homogeneous subsets are displayed. Based on observed means. The error term is Mean Square(Error) = 0.861. | ||
| a. Uses Harmonic Mean Sample Size = 15.053. | ||
| b. The group sizes are unequal. The harmonic mean of the group sizes is used. Type I error levels are not guaranteed. | ||
| c. Alpha = 0.05. | ||
| Between-Subjects Factors | |||
| Value Label | N | ||
| DEVICE | 1.00 | CAMERA | 8 |
| 2.00 | SCALE | 13 | |
| 3.00 | LIGHT | 28 | |
| 4.00 | FRAME | 12 | |
| 5.00 | SPEAKER | 40 | |
| 6.00 | SENSORS | 14 | |
| 7.00 | INFRASTRUCTURE | 21 | |
| Tests of Between-Subjects Effects | ||||||
| Dependent Variable: GRID: AFFECTIVE VS COGNITIVE/MOTIVATIONAL | ||||||
| Source | Type III Sum of Squares | df | Mean Square | F | Sig. | Partial Eta Squared |
| Corrected Model | 9.482 a | 6 | 1.580 | 1.689 | 0.129 | 0.073 |
| Intercept | 2.524 | 1 | 2.524 | 2.698 | 0.103 | 0.020 |
| DEVICE | 9.482 | 6 | 1.580 | 1.689 | 0.129 | 0.073 |
| Error | 120.707 | 129 | 0.936 | |||
| Total | 134.124 | 136 | ||||
| Corrected Total | 130.189 | 135 | ||||
| a. R Squared = 0.073 (Adjusted R Squared = 0.030) | ||||||
| DEVICE | ||||
| Dependent Variable: GRID: AFFECTIVE VS COGNITIVE/MOTIVATIONAL | ||||
| DEVICE | Mean | Std. Error | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||
| CAMERA | 0.115 | 0.342 | −0.562 | 0.791 |
| SCALE | −0.405 | 0.268 | −0.935 | 0.126 |
| LIGHT | 0.254 | 0.183 | −0.108 | 0.615 |
| FRAME | −0.316 | 0.279 | −0.869 | 0.236 |
| SPEAKER | −0.430 | 0.153 | −0.733 | −0.128 |
| SENSORS | −0.204 | 0.259 | −0.715 | 0.308 |
| INFRASTRUCTURE | −0.097 | 0.211 | −0.515 | 0.320 |
| Multiple Comparisons | ||||||
| Dependent Variable: GRID: AFFECTIVE VS COGNITIVE/MOTIVATIONAL | ||||||
| Tukey HSD | ||||||
| (I) DEVICE | (J) DEVICE | Mean Difference (I−J) | Std. Error | Sig. | 95% Confidence Interval | |
| Lower Bound | Upper Bound | |||||
| CAMERA | SCALE | 0.5193 | 0.43468 | 0.895 | −0.7828 | 1.8213 |
| LIGHT | −0.1390 | 0.38779 | 1.000 | −1.3006 | 1.0226 | |
| FRAME | 0.4310 | 0.44152 | 0.958 | −0.8916 | 1.7535 | |
| SPEAKER | 0.5449 | 0.37464 | 0.771 | −0.5773 | 1.6671 | |
| SENSORS | 0.3186 | 0.42872 | 0.990 | −0.9656 | 1.6028 | |
| INFRASTRUCTURE | 0.2119 | 0.40190 | 0.998 | −0.9920 | 1.4157 | |
| SCALE | CAMERA | −0.5193 | 0.43468 | 0.895 | −1.8213 | 0.7828 |
| LIGHT | −0.6582 | 0.32465 | 0.403 | −1.6307 | 0.3142 | |
| FRAME | −0.0883 | 0.38724 | 1.000 | −1.2482 | 1.0716 | |
| SPEAKER | 0.0256 | 0.30882 | 1.000 | −0.8994 | 0.9507 | |
| SENSORS | −0.2007 | 0.37258 | 0.998 | −1.3167 | 0.9153 | |
| INFRASTRUCTURE | −0.3074 | 0.34137 | 0.972 | −1.3299 | 0.7152 | |
| LIGHT | CAMERA | 0.1390 | 0.38779 | 1.000 | −1.0226 | 1.3006 |
| SCALE | 0.6582 | 0.32465 | 0.403 | −0.3142 | 1.6307 | |
| FRAME | 0.5700 | 0.33376 | 0.612 | −0.4298 | 1.5697 | |
| SPEAKER | 0.6839 | 0.23835 | 0.070 | −0.0301 | 1.3978 | |
| SENSORS | 0.4576 | 0.31663 | 0.776 | −0.4909 | 1.4060 | |
| INFRASTRUCTURE | 0.3509 | 0.27924 | 0.870 | −0.4856 | 1.1873 | |
| FRAME | CAMERA | −0.4310 | 0.44152 | 0.958 | −1.7535 | 0.8916 |
| SCALE | 0.0883 | 0.38724 | 1.000 | −1.0716 | 1.2482 | |
| LIGHT | −0.5700 | 0.33376 | 0.612 | −1.5697 | 0.4298 | |
| SPEAKER | 0.1139 | 0.31839 | 1.000 | −0.8398 | 1.0676 | |
| SENSORS | −0.1124 | 0.38054 | 1.000 | −1.2523 | 1.0275 | |
| INFRASTRUCTURE | −0.2191 | 0.35005 | 0.996 | −1.2676 | 0.8295 | |
| SPEAKER | CAMERA | −0.5449 | 0.37464 | 0.771 | −1.6671 | 0.5773 |
| SCALE | −0.0256 | 0.30882 | 1.000 | −0.9507 | 0.8994 | |
| LIGHT | −0.6839 | 0.23835 | 0.070 | −1.3978 | 0.0301 | |
| FRAME | −0.1139 | 0.31839 | 1.000 | −1.0676 | 0.8398 | |
| SENSORS | −0.2263 | 0.30038 | 0.989 | −1.1261 | 0.6735 | |
| INFRASTRUCTURE | −0.3330 | 0.26067 | 0.861 | −1.1138 | 0.4478 | |
| SENSORS | CAMERA | −0.3186 | 0.42872 | 0.990 | −1.6028 | 0.9656 |
| SCALE | 0.2007 | 0.37258 | 0.998 | −0.9153 | 1.3167 | |
| LIGHT | −0.4576 | 0.31663 | 0.776 | −1.4060 | 0.4909 | |
| FRAME | 0.1124 | 0.38054 | 1.000 | −1.0275 | 1.2523 | |
| SPEAKER | 0.2263 | 0.30038 | 0.989 | −0.6735 | 1.1261 | |
| INFRASTRUCTURE | −0.1067 | 0.33376 | 1.000 | −1.1064 | 0.8931 | |
| INFRASTRUCTURE | CAMERA | −0.2119 | 0.40190 | 0.998 | −1.4157 | 0.9920 |
| SCALE | 0.3074 | 0.34137 | 0.972 | −0.7152 | 1.3299 | |
| LIGHT | −0.3509 | 0.27924 | 0.870 | −1.1873 | 0.4856 | |
| FRAME | 0.2191 | 0.35005 | 0.996 | −0.8295 | 1.2676 | |
| SPEAKER | 0.3330 | 0.26067 | 0.861 | −0.4478 | 1.1138 | |
| SENSORS | 0.1067 | 0.33376 | 1.000 | −0.8931 | 1.1064 | |
| Based on observed means. The error term is Mean Square(Error) = 0.936. | ||||||
| GRID: AFFECTIVE VS COGNITIVE/MOTIVATIONAL | ||
| Tukey HSD a,b,c | ||
| DEVICE | N | Subset |
| 1 | ||
| SPEAKER | 40 | −0.4301 |
| SCALE | 13 | −0.4045 |
| FRAME | 12 | −0.3162 |
| SENSORS | 14 | −0.2038 |
| INFRASTRUCTURE | 21 | −0.0972 |
| CAMERA | 8 | 0.1147 |
| LIGHT | 28 | 0.2537 |
| Sig0. | 0.458 | |
| Means for groups in homogeneous subsets are displayed. Based on observed means. The error term is Mean Square(Error) = 0.936. | ||
| a. Uses Harmonic Mean Sample Size = 15.053. | ||
| b. The group sizes are unequal. The harmonic mean of the group sizes is used. Type I error levels are not guaranteed. | ||
| c. Alpha = 0.05. | ||

References
- IoTAnalytics Connected IoT Device Market Update—Summer. 2024. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 12 December 2024).
- Statista Number of Internet of Things (IoT) Connections Worldwide from 2022 to 2023, with Forecasts from 2024 to 2033. Available online: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/ (accessed on 12 December 2024).
- ISO 25000. Software and Data Quality. Available online: https://iso25000.com/index.php/en/iso-25000-standards/iso-25010 (accessed on 12 December 2024).
- Systems and Software Engineering—Systems and Software Quality Requirements and Evaluation (SQuaRE)—Product Quality Model. Available online: https://www.iso.org/obp/ui/#iso:std:iso-iec:25010:ed-2:v1:en (accessed on 12 December 2024).
- ISO/IEC 27000. Family Information Security Management. Available online: https://www.iso.org/standard/iso-iec-27000-family (accessed on 12 December 2024).
- Vardakis, G.; Hatzivasilis, G.; Koutsaki, E.; Papadakis, N. Review of Smart-Home Security Using the Internet of Things. Electronics 2024, 13, 3343. [Google Scholar] [CrossRef]
- Marton, A. IoT Malware Attacks up by 37% in the First Half of 2023. Available online: https://iotac.eu/iot-malware-attacks-up-by-37-in-the-first-half-of-2023/ (accessed on 12 December 2024).
- Kaspersky Unveils an Overview of IoT-Related Threats in 2023. Available online: https://www.kaspersky.com/about/press-releases/kaspersky-unveils-an-overview-of-iot-related-threats-in-2023 (accessed on 12 December 2024).
- Heartfield, R.; Loukas, G.; Budimir, S.; Bezemskij, A.; Fontaine, J.R.J.; Filippoupolitis, A.; Roesch, E. A Taxonomy of Cyber-Physical Threats and Impact in the Smart Home. Comput. Secur. 2018, 78, 398–428. [Google Scholar] [CrossRef]
- Bitdefender The 2023 IOT Security Landscape Report 2023. Available online: https://www.bitdefender.com/files/News/CaseStudies/study/429/2023-IoT-Security-Landscape-Report.pdf (accessed on 12 December 2024).
- Loukas, G. Cyber-Physical Attacks: A Growing Invisible Threat; Butterworth-Heinemann: Oxford, UK, 2015; ISBN 978-0-12-801463-9. [Google Scholar]
- Parsons, E.K.; Panaousis, E.; Loukas, G.; Sakellari, G. A Survey on Cyber Risk Management for the Internet of Things. Appl. Sci. 2023, 13, 9032. [Google Scholar] [CrossRef]
- Baraniuk, C. Ashley Madison: ‘Suicides’ over Website Hack. Available online: https://www.bbc.com/news/technology-34044506 (accessed on 10 December 2019).
- Watson, D.; Clark, L.A.; Tellegen, A. Development and Validation of Brief Measures of Positive and Negative Affect: The PANAS Scales. J. Personal. Soc. Psychol. 1988, 8, 1063. [Google Scholar] [CrossRef]
- Scherer, K.R. Appraisal Considered as a Process of Multilevel Sequential Checking. In Appraisal Processes in Emotion: Theory, Methods, Research; Series in Affective Science; Oxford University Press: New York, NY, USA, 2001; pp. 92–120. ISBN 978-0-19-513007-2. [Google Scholar]
- Gross, M.L.; Canetti, D.; Vashdi, D.R. Cyberterrorism: Its Effects on Psychological Well-Being, Public Confidence and Political Attitudes. J. Cybersecur. 2017, 3, 49–58. [Google Scholar] [CrossRef]
- Gross, M.L.; Canetti, D.; Vashdi, D.R. The Psychological Effects of Cyber Terrorism. Bull. At. Sci. 2016, 72, 284–291. [Google Scholar] [CrossRef]
- Kopecký, K.; Szotkowski, R. Cyberbullying, Cyber Aggression and Their Impact on the Victim—The Teacher. Telemat. Inform. 2017, 34, 506–517. [Google Scholar] [CrossRef]
- Budimir, S.; Fontaine, J.R.J.; Roesch, E.B. Emotional Experiences of Cybersecurity Breach Victims. Cyberpsychology Behav. Soc. Netw. 2021, 24, 612–616. [Google Scholar] [CrossRef] [PubMed]
- Budimir, S.; Fontaine, J.R.J.; Huijts, N.M.A.; Haans, A.; Loukas, G.; Roesch, E.B. Emotional Reactions to Cybersecurity Breach Situations: Scenario-Based Survey Study. J. Med. Internet Res. 2021, 23, e24879. [Google Scholar] [CrossRef] [PubMed]
- Qualtrics, P.U. Qualtrics 2019. Provo, UT, USA. Available online: https://www.qualtrics.com (accessed on 12 December 2024).
- Huijts, N.M.A.; Haans, A.; Budimir, S.; Fontaine, J.R.J.; Loukas, G.; Bezemskij, A.; Oostveen, A.; Filippoupolitis, A.; Ras, I.; IJsselsteijn, W.A.; et al. User Experiences with Simulated Cyber-Physical Attacks on Smart Home IoT. Pers. Ubiquitous Comput. 2023, 27, 2243–2266. [Google Scholar] [CrossRef]
- Achenbach, T.M. The Achenbach System of Empirically Based Assessemnt (ASEBA): Development, Findings, Theory, and Applications; University of Vermont Research Center for Children, Youth, & Families: Burlington, VT, USA, 1966. [Google Scholar]
- Fontaine, J.R.J.; Scherer, K.R.; Soriano, C. (Eds.) Components of Emotional Meaning: A Sourcebook; Oxford University Press: Oxford, UK, 2013; ISBN 978-0-19-959274-6. [Google Scholar]
- Frijda, N.H. The Emotions; Cambridge University Press: Cambridge, UK, 1986; ISBN 978-0-521-31600-2. [Google Scholar]
- Riquelme, H.E.; Alqallaf, A. Anticipated Emotions and Their Effects on Risk and Opportunity Evaluations. J. Int. Entrep. 2020, 18, 312–335. [Google Scholar] [CrossRef]
- Kaplan, S.; Winslow, C.; Craig, L.; Lei, X.; Wong, C.; Bradley-Geist, J.; Biskup, M.; Ruark, G. “Worse than I Anticipated” or “This Isn’t so Bad”?: The Impact of Affective Forecasting Accuracy on Self-Reported Task Performance. PLoS ONE 2020, 15, e0235973. [Google Scholar] [CrossRef] [PubMed]
- Kutt, K.; Nalepa, G.J. Emotion Prediction in Real-Life Scenarios: On the Way to the BIRAFFE3 Dataset. In Artificial Intelligence for Neuroscience and Emotional Systems; Ferrández Vicente, J.M., Val Calvo, M., Adeli, H., Eds.; Lecture Notes in Computer Science; Springer Nature: Cham, Switzerland, 2024; Volume 14674, pp. 465–475. ISBN 978-3-031-61139-1. [Google Scholar]
- Beaton, A.; Cook, M.; Kavanagh, M.; Herrington, C. The Psychological Impact of Burglary. Psychol. Crime Law 2000, 6, 33–43. [Google Scholar] [CrossRef]
- Chung, M.C.; Stedmon, J.; Hall, R.; Marks, Z.; Thornhill, K.; Mehrshahi, R. Posttraumatic Stress Reactions Following Burglary: The Role of Coping and Personality. Traumatol. Int. J. 2014, 20, 65–74. [Google Scholar] [CrossRef]

| Conditions | Camera | Scale | Light | Photo Frame | Speaker | |
|---|---|---|---|---|---|---|
| 1 | A | 35 | 34 | 26 | 26 | 22 |
| B | 24 | 26 | 28 | |||
| 2 | A | 36 | 37 | 27 | 26 | 27 |
| B | 26 | |||||
| 3 | 37 | 30 | 26 | 26 | ||
| Total | 108 | 101 | 103 | 104 | 103 | |
| Dimension Loading | |||
|---|---|---|---|
| Emotion Feature Item | D1 | D2 | D3 |
| General Emotion Dimension | |||
| SF7 I felt/I would feel worried. | 0.79 | 0.02 | −0.18 |
| SF4 I felt/I would feel afraid. | 0.76 | 0.27 | −0.20 |
| SF3 I felt/I would feel anxious. | 0.75 | 0.10 | −0.25 |
| SF5 I felt/I would feel panic. | 0.73 | 0.23 | −0.31 |
| SF14 I felt/I would feel uncomfortable. | 0.72 | 0.07 | −0.16 |
| SF6 I felt/I would feel upset. | 0.71 | 0.07 | −0.26 |
| A17 I thought/I would think “Someone could use my data to harm me”. | 0.69 | 0.11 | 0.52 |
| SF1 I was/would be in an intense emotional state. | 0.68 | 0.37 | −0.29 |
| BR8 My muscles were/would be tense. | 0.67 | 0.28 | −0.34 |
| E8 I was/would be walking around nervously. | 0.67 | 0.29 | −0.34 |
| Constructive | |||
| AT9 I wanted to/would want to find a solution and fix the problem. | 0.28 | −0.60 | −0.14 |
| A2 I thought/I would think “I wonder whether something is wrong with the device/account”. | 0.27 | −0.55 | 0.00 |
| AT2 I wanted to/would want to regain control over the device/account. | 0.46 | −0.53 | 0.00 |
| AT1 I wanted to/would want to stop what was happening. | 0.47 | −0.50 | 0.03 |
| AT11 I wanted to/would want to reset my device. | 0.33 | −0.47 | −0.07 |
| Unconstructive | |||
| BR4 I had/would have pain in the chest. | 0.56 | 0.55 | −0.14 |
| BR2 I was/would be dizzy. | 0.58 | 0.54 | −0.14 |
| AT14 I wanted to/would want to destroy whatever was close. | 0.37 | 0.53 | 0.07 |
| SF10 I felt/I would feel ashamed. | 0.49 | 0.53 | −0.13 |
| AT5 I wanted to/would want to isolate myself physically. | 0.50 | 0.52 | 0.19 |
| Cognitive–Motivational | |||
| A16 I thought/I would think “Someone could destroy my data”. | 0.65 | 0.12 | 0.57 |
| A15 I thought/I would think “Someone may have access to my private information”. | 0.66 | 0.06 | 0.57 |
| A8 I thought/I would think “My security could be jeopardized”. | 0.64 | −0.02 | 0.55 |
| A17 I thought/I would think “Someone could use my data to harm me”. | 0.69 | 0.11 | 0.52 |
| A14 I thought/I would think “I could lose personal information, data and documents”. | 0.60 | 0.07 | 0.52 |
| Affective | |||
| E7 I was/would be restless (touching face, hair, biting nails, nervously kicking with legs). | 0.64 | 0.22 | −0.40 |
| E5 I slouched/would slouch (shoulders down, head down, hands down). | 0.44 | 0.26 | −0.39 |
| E3 I spoke/would speak louder. | 0.45 | 0.13 | −0.36 |
| SF9 I felt/I would feel sad. | 0.56 | 0.15 | −0.36 |
| SF12 I felt/I would feel frustrated. | 0.56 | −0.21 | −0.36 |
| Emotion Feature Items | Dimension Loading | |||
|---|---|---|---|---|
| D1 | D2 | D3 | D4 | |
| Emotional Intensity | ||||
| BR3 I was/would be shaking. | 0.76 | 0.55 | 0.06 | 0.08 |
| BR9 I had/would have goosebumps. | 0.76 | 0.54 | −0.02 | 0.10 |
| BR2 I was/would be dizzy. | 0.74 | 0.54 | 0.09 | 0.11 |
| SF2 I experienced/I would experience the emotional state for a long time. | 0.74 | 0.39 | −0.17 | 0.02 |
| SF4 I felt/I would feel afraid. | 0.74 | 0.39 | −0.10 | −0.11 |
| AT5 I wanted to/would want to isolate myself physically. | 0.73 | 0.45 | 0.07 | 0.03 |
| BR4 I had/would have pain in the chest. | 0.73 | 0.57 | 0.04 | 0.11 |
| BR5 I sweated/would sweat (whole body). | 0.73 | 0.57 | 0.04 | 0.11 |
| BR11 My body became/would become hot (puff of heat. cheeks or chest). | 0.73 | 0.49 | −0.10 | 0.11 |
| E4 I had/would have a trembling voice. | 0.73 | 0.49 | −0.07 | 0.05 |
| Constructive | ||||
| AT2 I wanted to/would want to regain control over the device/account. | 0.34 | −0.56 | −0.08 | 0.04 |
| AT9 I wanted to/would want to find a solution and fix the problem. | 0.44 | −0.55 | −0.18 | 0.04 |
| A2 I thought/I would think “I wonder whether something is wrong with the device/account”. | 0.40 | −0.54 | 0.03 | 0.17 |
| A18 I thought/I would think “Similar situations might happen again in the future”. | 0.39 | −0.45 | −0.08 | 0.00 |
| AT10 I wanted to/would want to report the situation (e.g., to the police or to the internet provider). | 0.41 | −0.44 | 0.19 | −0.14 |
| Unconstructive | ||||
| BR4 I had/would have pain in the chest. | 0.73 | 0.57 | 0.04 | 0.11 |
| BR5 I sweated/would sweat (whole body). | 0.73 | 0.57 | 0.04 | 0.11 |
| BR3 I was/would be shaking. | 0.76 | 0.55 | 0.06 | 0.08 |
| BR2 I was/would be dizzy. | 0.74 | 0.54 | 0.09 | 0.11 |
| BR10 I had/would have a dry mouth. | 0.71 | 0.54 | −0.03 | 0.08 |
| Cognitive–motivational | ||||
| A19 I thought/I would think “It is not safe that this device is connected to the Internet”. | 0.47 | 0.02 | 0.47 | −0.12 |
| A16 I thought/I would think “Someone could destroy my data”. | 0.69 | 0.37 | 0.39 | 0.10 |
| A15 I thought/I would think “Someone may have access to my private information”. | 0.57 | 0.23 | 0.38 | −0.13 |
| A17 I thought/I would think “Someone could use my data to harm me”. | 0.66 | 0.39 | 0.38 | 0.05 |
| A8 I thought/I would think “My security could be jeopardized”. | 0.64 | 0.26 | 0.34 | 0.14 |
| Affective | ||||
| SF12 I felt/I would feel frustrated. | 0.49 | −0.34 | −0.46 | 0.15 |
| SF11 I felt/I would feel angry. | 0.57 | −0.13 | −0.43 | 0.07 |
| SF6 I felt/I would feel upset. | 0.63 | 0.03 | −0.42 | 0.06 |
| E1 I frowned/would frown. | 0.33 | −0.29 | −0.37 | −0.02 |
| BR6 My heartbeat was/would be faster. | 0.58 | 0.23 | −0.35 | 0.30 |
| Distress symptoms | ||||
| SF7 I felt/I would feel worried. | 0.57 | 0.01 | −0.15 | −0.55 |
| SF14 I felt/I would feel uncomfortable. | 0.57 | −0.08 | −0.14 | −0.53 |
| BR1 I had/would have stomach discomfort. | 0.58 | 0.07 | −0.15 | −0.52 |
| SF10 I felt/I would feel ashamed. | 0.48 | 0.24 | −0.30 | −0.48 |
| SF3 I felt/I would feel anxious. | 0.60 | −0.02 | −0.24 | −0.48 |
| Oppositional tendencies | ||||
| AT11 I wanted to/would want to reset my device. | 0.59 | −0.29 | 0.04 | 0.39 |
| AT13 I wanted to/would want to swear and curse. | 0.58 | 0.00 | −0.25 | 0.30 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Budimir, S.; Fontaine, J.R.J.; Huijts, N.M.A.; Haans, A.; IJsselsteijn, W.A.; Oostveen, A.-M.; Stahl, F.; Heartfield, R.; Loukas, G.; Bezemskij, A.; et al. We Are Not Equipped to Identify the First Signs of Cyber–Physical Attacks: Emotional Reactions to Cybersecurity Breaches on Domestic Internet of Things Devices. Appl. Sci. 2024, 14, 11855. https://doi.org/10.3390/app142411855
Budimir S, Fontaine JRJ, Huijts NMA, Haans A, IJsselsteijn WA, Oostveen A-M, Stahl F, Heartfield R, Loukas G, Bezemskij A, et al. We Are Not Equipped to Identify the First Signs of Cyber–Physical Attacks: Emotional Reactions to Cybersecurity Breaches on Domestic Internet of Things Devices. Applied Sciences. 2024; 14(24):11855. https://doi.org/10.3390/app142411855
Chicago/Turabian StyleBudimir, Sanja, Johnny R. J. Fontaine, Nicole M. A. Huijts, Antal Haans, Wijnand A. IJsselsteijn, Anne-Marie Oostveen, Frederic Stahl, Ryan Heartfield, George Loukas, Anatolij Bezemskij, and et al. 2024. "We Are Not Equipped to Identify the First Signs of Cyber–Physical Attacks: Emotional Reactions to Cybersecurity Breaches on Domestic Internet of Things Devices" Applied Sciences 14, no. 24: 11855. https://doi.org/10.3390/app142411855
APA StyleBudimir, S., Fontaine, J. R. J., Huijts, N. M. A., Haans, A., IJsselsteijn, W. A., Oostveen, A.-M., Stahl, F., Heartfield, R., Loukas, G., Bezemskij, A., Filippoupolitis, A., Ras, I., & Roesch, E. B. (2024). We Are Not Equipped to Identify the First Signs of Cyber–Physical Attacks: Emotional Reactions to Cybersecurity Breaches on Domestic Internet of Things Devices. Applied Sciences, 14(24), 11855. https://doi.org/10.3390/app142411855






