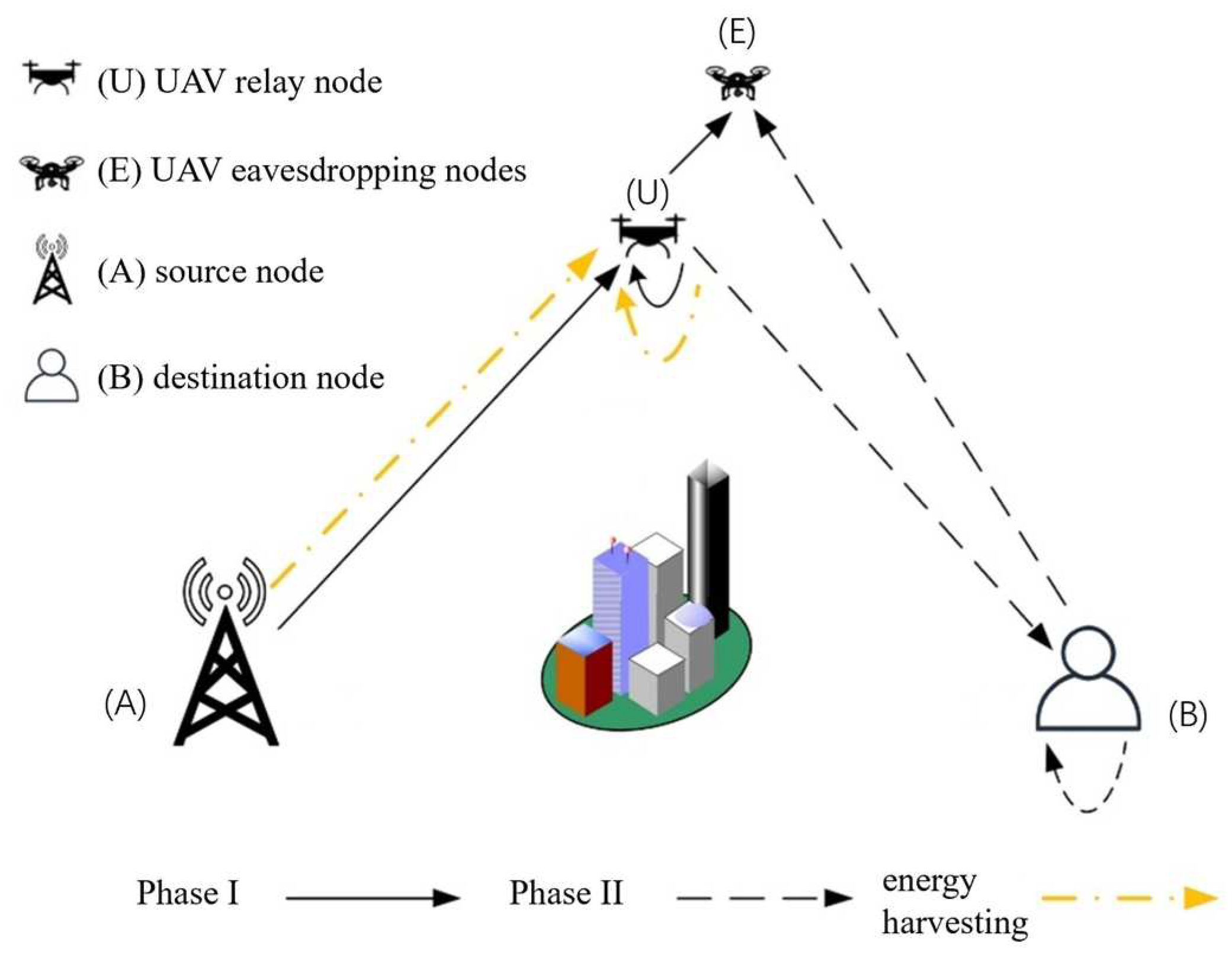
1. Introduction
In recent years, UAVs have been widely used in the military, agriculture, monitoring and prediction, transportation and logistics, and disaster rescue [
1,
2,
3,
4,
5] because of their advantages, such as high mobility and low-cost networking. UAV signal transmission has line-of-sight link transmission and broadcasting characteristics, which will make the UAV communication system easier to eavesdrop on, therefore, how to guarantee the security of signal transmission has gradually become a hot issue in the study of UAV communication [
6]. Compared to traditional network layer encryption techniques, physical layer security techniques have attracted a lot of attention in the field of wireless communications because they reduce the high complexity of the system and solve the problem of limited resources [
7].
The combination of UAV communication and physical layer security techniques has led to a wider field of research, while UAUs play more roles in the application process. In literature [
8], UAU acts as a receiver to receive signals in the presence of randomly distributed eavesdropper scenarios. In the literature [
9], the UAV is used as a transmitter, and the proposed algorithm shows better convergence speed as well as good throughput by optimizing the UAV trajectory design scheme. In literature [
10], the UAV acts as a jammer, moves along with the eavesdropper, and transmits a jamming signal to the eavesdropper when it reaches the optimal position, ensuring the reachable security rate of the system by reducing the eavesdropping channel capacity.
It is also possible to combine multiple uses of UAVs in the design of communication systems. For example, in the literature [
11], the UAV acts as both a jammer and a transmitter, sending signals to the base station while sending jamming to the eavesdropper, maximizing the Expected Sum Rate (ESR) by optimizing the position and target rate of the UAV. When the UAV works in full-duplex mode, it can act as a transmitter and a receiver at the same time [
12,
13,
14], which can effectively improve the spectral efficiency of the communication system. In the literature [
12], the authors combine the full-duplex technique with Reconfigurable Intelligent Surface (RIS) technique and propose a joint optimization algorithm, which improves the overall secrecy rate of the UAV system. Literature [
13] introduces Non-Orthogonal Multiple Access (NOMA) technique and Idle Energy Access Point (EAP) and constructs a full duplex UAV relay system. The proposed model and strategy outperform the traditional maximum-minimum relay selection scheme in terms of throughput gain. The literature [
14] considers Artificial Noise (AN)-enhanced covert wireless communication in UAV networks. In the article, the UAV uses a full duplex mode of operation and sends interference to the monitor while receiving signals, and the results show that the proposed scheme significantly enhances the covert transmission performance of the system compared to the interference-free scheme.
Since the small size of the UAV leads to less energy storage, the energy limitation problem of the UAV has also attracted extensive attention from scholars. SWIPT technology was first proposed by Varshney in 2008 [
15], which is a combination of signaling and energy harvesting technologies to draw energy from the received radio frequency (RF) signals. This technique is widely used in communication systems [
16] and has been applied in UAV communication systems to alleviate the energy constraints of UAVs. Based on SWIPT technology and noise interference technology in the literature [
17], the authors propose a new UAV-assisted relay security transmission protocol, and compared with the traditional terrestrial relay transmission protocol, the proposed protocol enhances the security performance of the system. Aiming at the scenario of a relay UAV with limited energy and active attack by full-duplex eavesdroppers, in the literature [
18], the authors propose a model of UAV wireless power supply technology based on SWIPT technology and analyze the impact of factors such as the base station’s transmit power, the energy harvesting time factor, and the environment on the security performance of the UAV communication system. In the existing literature, the physical layer security research of UAV relay systems by combining SWIPT technology and full-duplex technology is limited, and the research for the airborne UAV eavesdropping scenario still needs to be explored. Therefore, to address the above problems, firstly, this paper establishes a UAV downlink communication system model under an airborne eavesdropping scenario; then, it proposes a secure transmission protocol for a full-duplex UAV relay system based on SWIPT technology; then, it analyzes and derives the connection probability and secrecy outage probability of the downlink transmission; and finally, it explores the influence of system parameters such as environmental parameters, UAV altitude, energy allocation efficiency, power allocation factor, and other system parameters on the safety performance of the UAV system.
3. Performance Analysis
It is assumed that the channel coefficients remain constant for all nodes during each communication frame. For computational simplicity, the connection probability (CP) and secrecy outage probability (SOP) of the UAV-assisted relay system are derived for the airborne eavesdropping scenario, assuming that the system operates under medium- to high-SINR conditions. For simplicity of calculation, it is assumed that
in Equations (13) and (15), and this assumption is valid for medium- to high-SINR conditions. According to the Shannon channel formula, the channel capacity of the legitimate channel in the system is defined as
and the channel capacity of the eavesdropping channel about the drone eavesdropping node E is defined as
, where
and
are the signal-to-interference plus noise ratios at node B and at node E in the communication system. Based on the first type of Marcu-Q and Bessel functions [
22,
23] and the literature [
24], a series of complex calculations and simplifications are performed to finally derive closed expressions for the system’s probability of connectivity and the probability of safety interruption.
3.1. Connection Probability
For a full-duplex UAV-assisted relay system, the message in the legal channel undergoes two stages of transmission: . is the instantaneous information transmission rate when the condition is satisfied: The entire communication system is in a connected state when the channel capacity is . If , the system is in a disconnected state. Therefore, the connection probability (PC) is defined as . Assuming that under the constraint of the threshold , the following theorem is obtained:
Theorem 1. Throughout the link transmission of , the UAV relay node U adopts the relaying method of Amplify-and-Forward, at this time, the connection probability closure expression of the legal channel is:where, ,, D and R are integers used to control the precision,is the gamma function. With the proposed system transmission protocol and the calculated SINR, after a series of complex calculations, we can derive a closed expression for the connectivity probability, as shown in Equation (16).
3.2. Probability of Safety Interruption
The secrecy capacity of the system is defined as the difference between the legitimate channel capacity and the eavesdropping channel capacity of the system, , and is the threshold of the secrecy transmission rate for the whole information transmission process. When , it indicates that the system is securely connected and the signal can be securely transmitted; when , it indicates that the secure transmission is interrupted. is the instantaneous capacity of the eavesdropping link, , defined as . When greater than the rate difference , the message is intercepted and the node E has access to the transmitted confidential information, again indicating an interruption of the secure transmission.
Theorem 2. Assuming as the threshold for secrecy transmission, let , the lower bound of the system’s secrecy outage probability in an aerial drone eavesdropping scenario is denoted by:where , , .
where
,
,
.
Since , a lower bound on the secrecy outage probability can be derived after a series of complex calculations as shown in Equations (17)–(19). Where are integers of definite precision, is the gamma function, and and are given by Equations (14) and (15).
4. Experimentation and Simulation
In this section, the impact of the established model and the proposed new transmission protocol on the security and reliability of the system is verified through simulation experiments, and the applicability of the communication system in the airborne UAV eavesdropping scenario in real scenarios is explored by analyzing the simulation results of the proposed scheme in this paper. If not specified later, the experimental parameters were set as shown in
Table 2. In order not to lose the generality of the experiment, the Cartesian 3D coordinate system parameters are all normalized distances, where
(CP* denotes the value taken in the calculation of CP, and SOP* denotes the value taken in the calculation of SOP).
Figure 2 shows the variation of CP versus total transmit power
for UAV relay node U under different self-interference channel gain conditions. It can be seen that when the total transmit power increases, the connection probability CP shows a trend of increasing and then stabilizing. This is because when the power allocation factor
and the power splitting ratio
are certain, the total transmit power increases, so the power
used for transmitting information in the first stage increases, and the channel capacity for effective information transmission increases; therefore, the connection probability shows an upward trend. When the total transmit power continues to increase, the channel capacity for effective information transmission tends to be close to the maximum transmission capacity, so the connection probability value of CP tends to stabilize. When the total transmit power
is certain, the CP increases as the self-interference channel gain of the UAV relay node U decreases. Because
smaller means smaller path loss, the SINR at the destination node B increases, and the channel capacity for effective information transmission increases, so the connection probability increases and the system connectivity performance is enhanced.
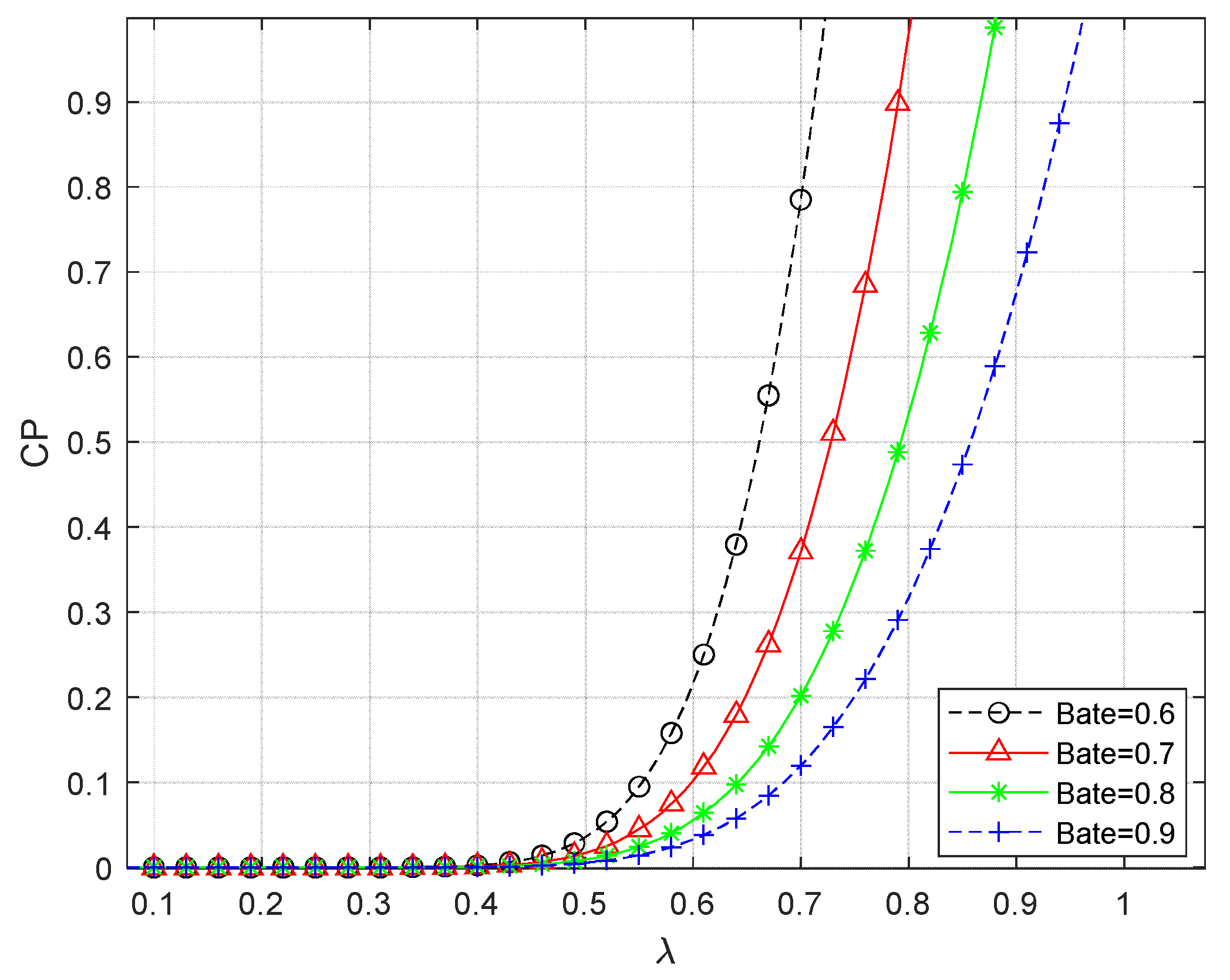
Figure 3 gives the variation of CP with respect to the power allocation factor
for different power splitting ratios
. As can be seen from the figure, CP tends to be close to 0 when the power allocation factor
is small, and CP increases as
increases. An increase in
means that the more power
is used to transmit information in the first stage, therefore, the channel capacity for effective information transmission increases, which confirms the correctness of the conclusions of
Figure 2. When the power splitting ratio
is certain, there exists a system connection initiation value
. When
, the power allocated to the signal transmission is not enough to transmit a valid signal, at this time the system is in the unconnected state; when
, the system can only be in the connected state. From the figure, it can be seen that when the other condition parameters are certain, the larger the value of power splitting ratio
is taken, the larger the value of system connection initiation
is. When the power splitting ratio
decreases from 0.9 to 0.6 at a certain value of
, the power used for energy harvesting decreases while the power used for the first stage of signal processing increases, and therefore the connection probability is enhanced.
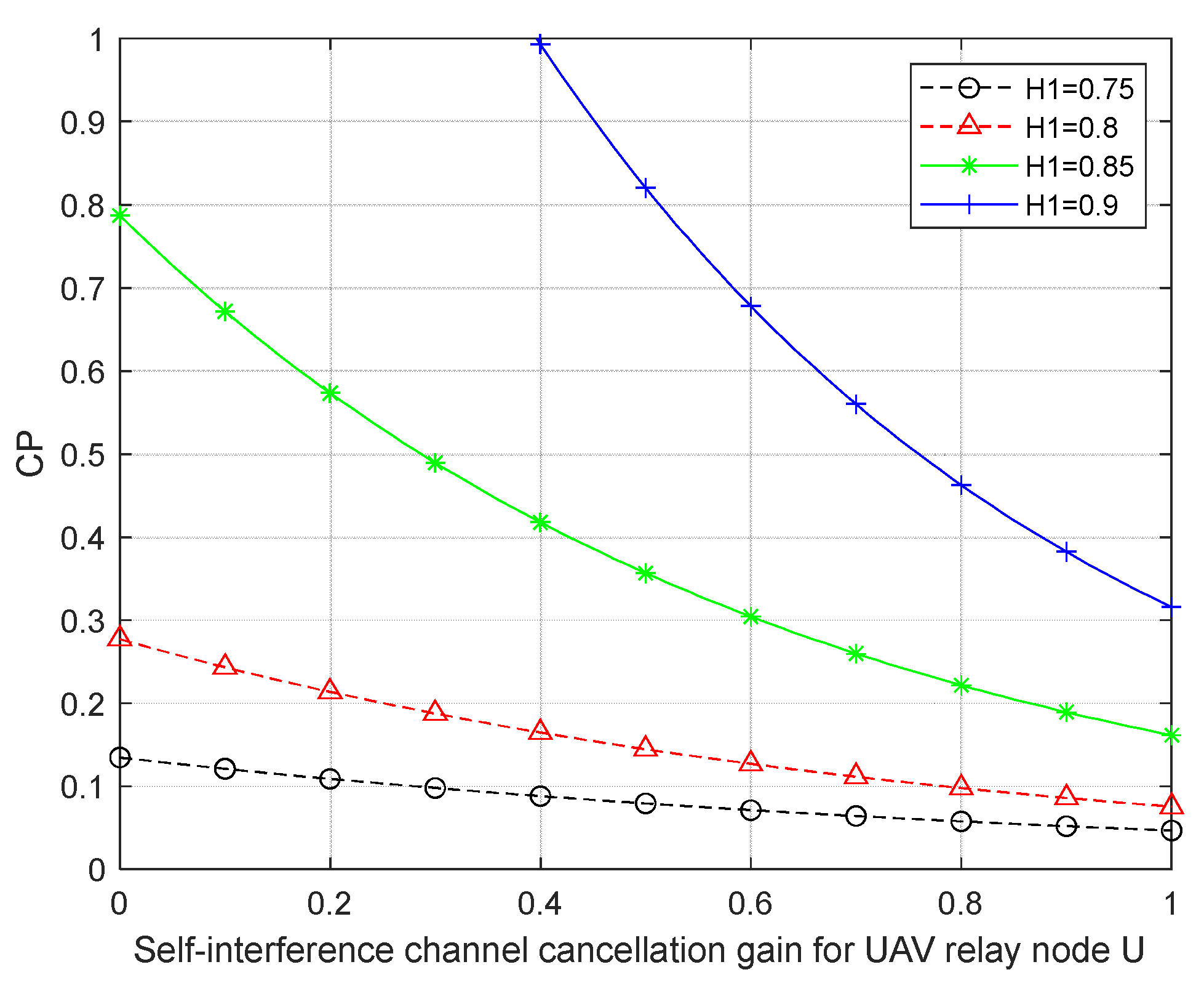
Figure 4 investigates the variation relationship between connection probability CP and UAV self-interference gain
under different flight altitudes of UAV relay node U. From the figure, it can be seen that when
increasing, CP decreases, and the higher the height
of UAV relay node U, the greater the decreasing trend of CP; when
is certain, the higher the normalized height of UAV relay node U, the greater the CP. When
increasing from 0.75 to 0.9, the line-of-sight channel link for effective information transmission is enhanced and the probability of transmission of LOS increases, and therefore, the probability of connectivity CP increases.
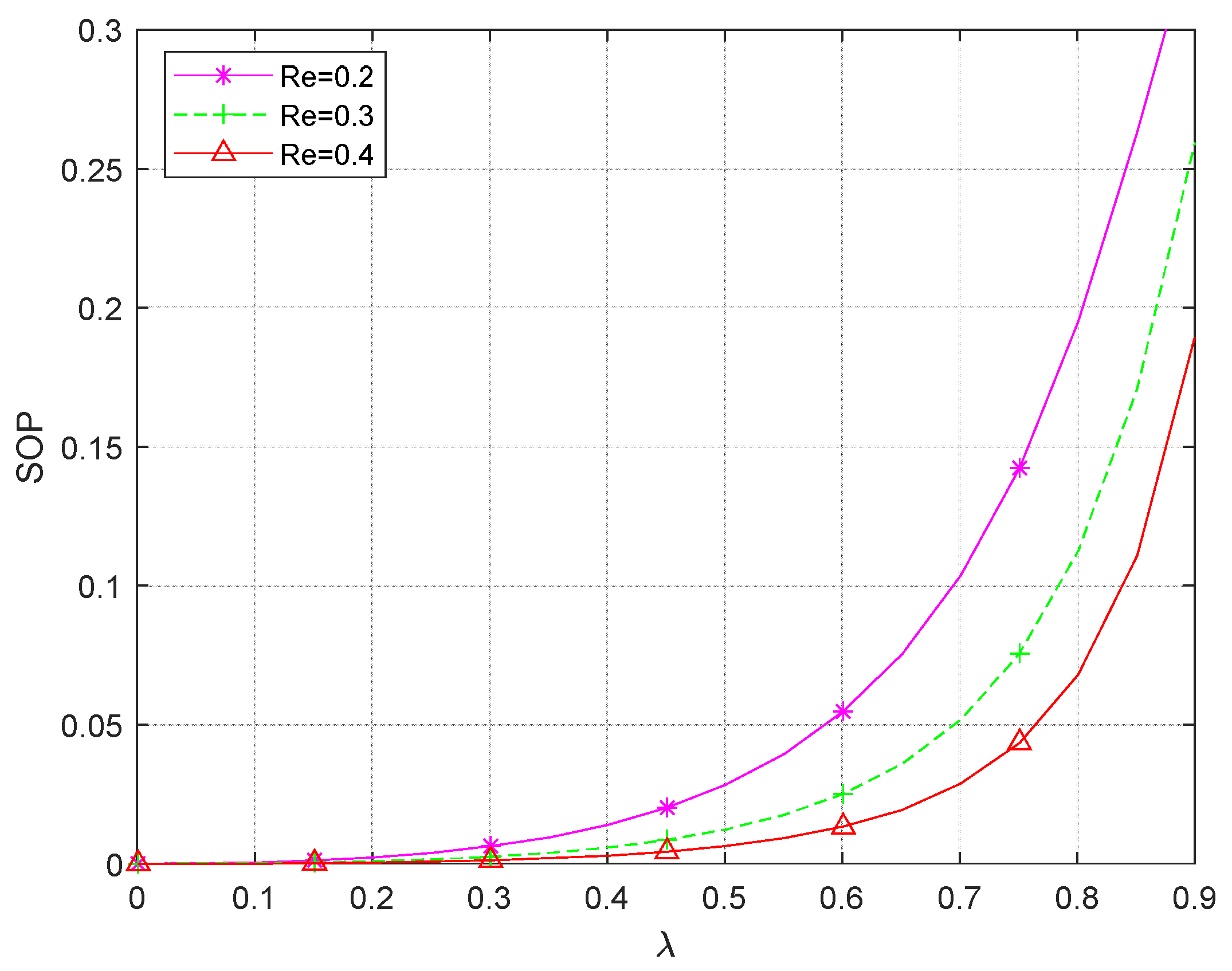
Figure 5 reveals the relationship between SOP and power allocation factor λ under different eavesdropping rate thresholds
. As can be seen from the figure, when the total transmit power
is certain, the SOP increases with the increase of
. This is because an increase in λ for a certain
leads to an increase in
and a decrease in the power
used to send the jamming signal to the UAV eavesdropping node E. This causes the channel capacity of the eavesdropping link to become larger, at which point the information is more likely to be eavesdropped and the secrecy outage probability SOP increases. The smaller the power allocation factor
is, the better the secure transmission of the system is, but the security of the system is limited by the system connectivity. From the conclusion of
Figure 1, it can be seen that the system can only be connected when
, and the larger the
is, the better the connectivity is, so there is a trade-off between the system’s connectivity and security. In addition, when
is certain, the SOP decreases as the eavesdropping rate threshold
increases, and the smaller the threshold
the greater the change in the value of the power allocation factor
is required when raising the same value of the security interruption probability. This suggests that when security needs are high, increasing security by an equal margin comes at a greater cost in terms of eavesdropping interference.
Plot (a) in
Figure 6 compares the effect of different environmental parameters on the secrecy outage probability SOP. The (b) plot in
Figure 6 is a localized enlargement of the (a) plot, where A takes values from 0.58 to 0.62. When the environmental parameters
,
, it corresponds to a suburban environment; when the environmental parameters
,
, the environment is urban; when the environment is a dense urban area, the environmental parameters
,
; when the environment is a high-rise building, the environmental parameters
,
. From the (b) graph in
Figure 6, it can be seen that the system’s secrecy outage probability is minimized in the environment of a high-rise city. This is because in the environment of high-rise buildings, the fading of the system will increase, but at this time, the interference signal sent by the UAV relay node U to the UAV eavesdropping node E belongs to the high-altitude transmission, which is less affected, so the eavesdropping channel capacity will become smaller, the SOP of the system decreases, and the security of the system is enhanced.
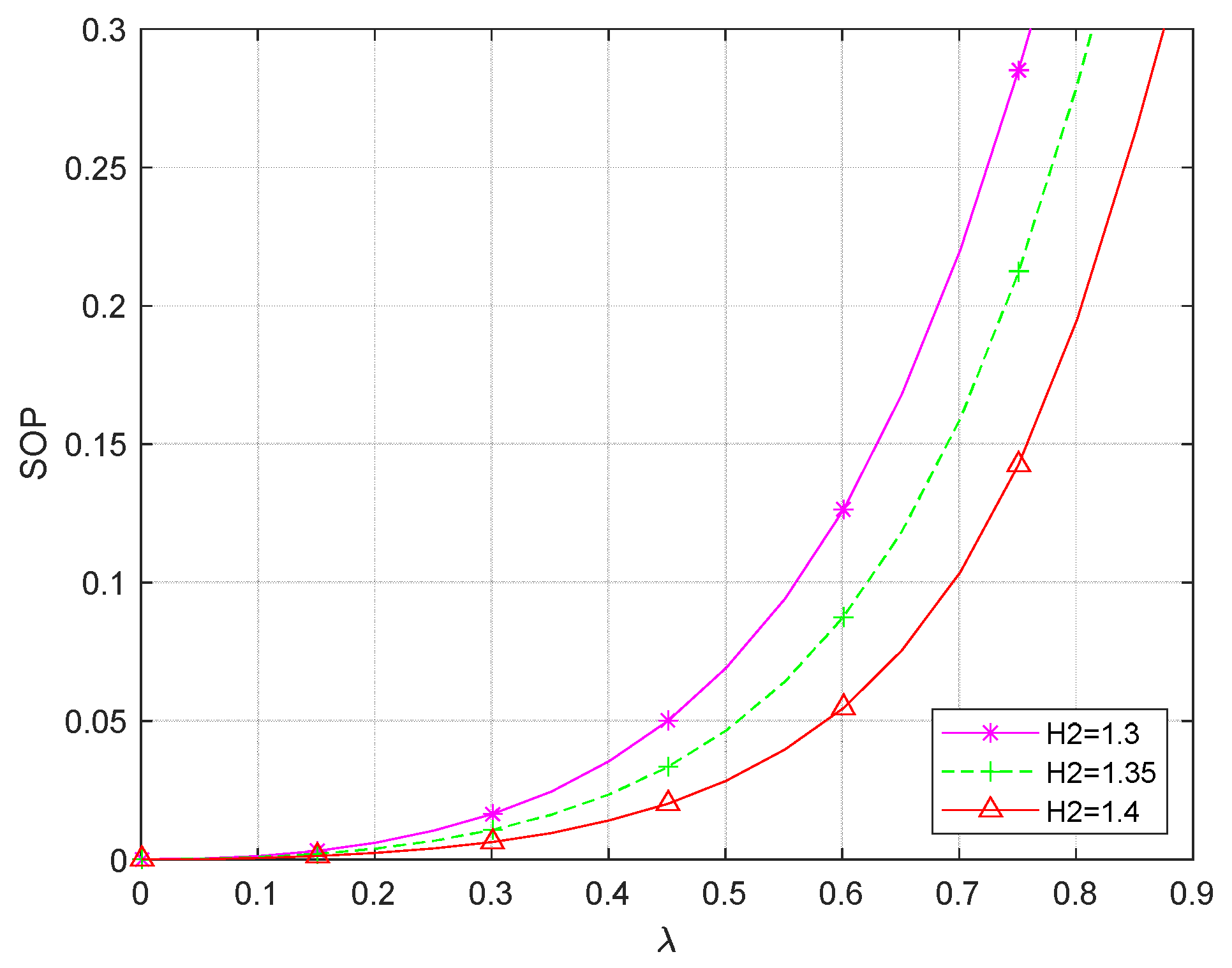
From
Figure 7, it can be seen that when the
normalized height is 1, the SOP of the system decreases as the height of the eavesdropping UAV increases from 1.3 to 1.4, causing an increase in the security performance of the system. This is because when the eavesdropping UAV height
increases, the probability of line-of-sight propagation of the eavesdropping signal transmission increases, and at the same time, the eavesdropping interference decreases, which reduces the security performance of the system. But if it continues to increase
, it will lead to a higher path loss, which will cause a reduction in the channel capacity of the system’s eavesdropping channel link, and the security performance of the system will be enhanced.
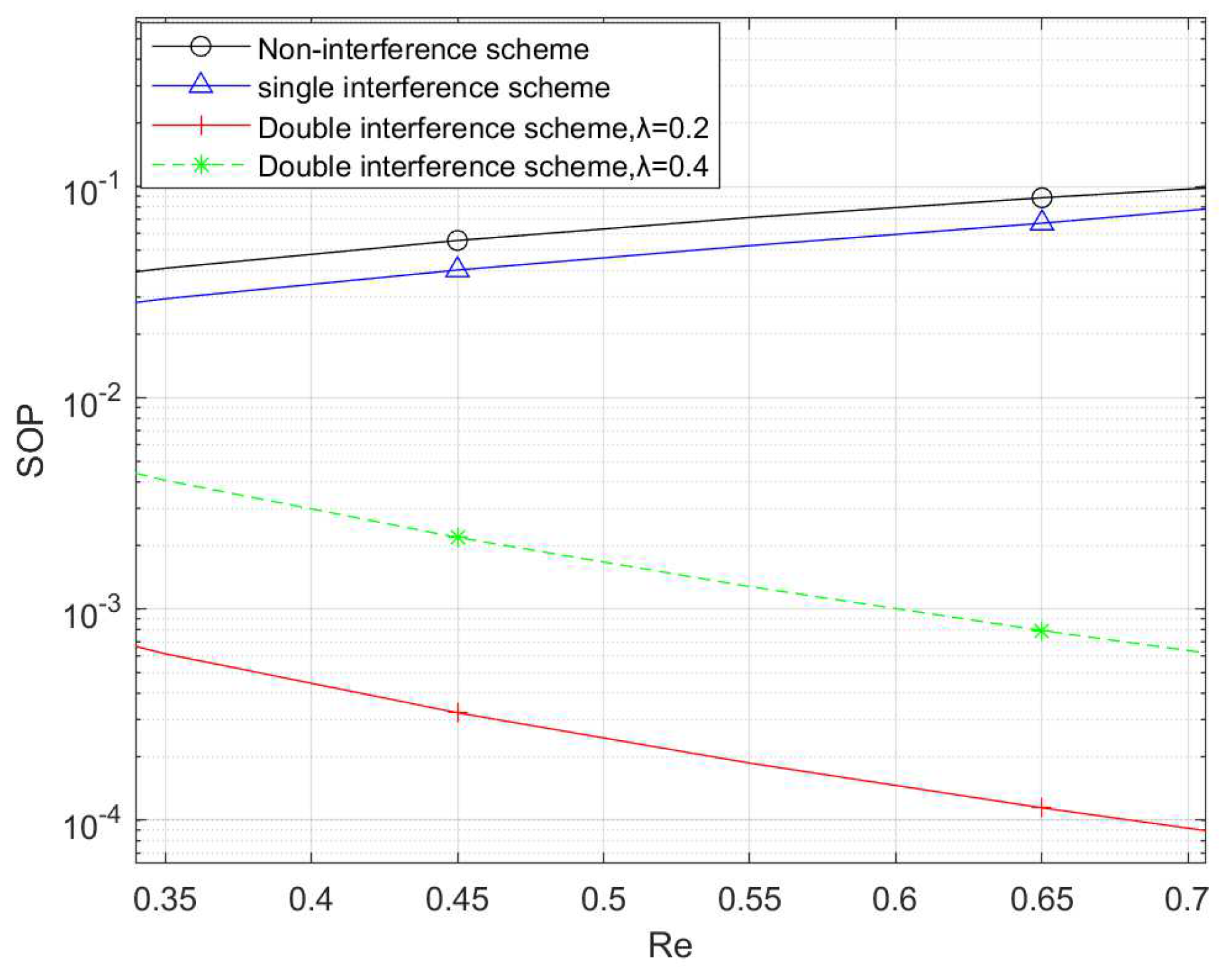
Figure 8 compares the variation of SOP with the eavesdropping rate threshold
for different eavesdropping interference schemes. Scenario 1 is a no interference scenario, where there is no interference signal in the first and second phases of the whole communication system; Scenario 2 is a single interference scenario, where only the destination node sends interference in the second phase; and Scenario 3 is the double interference scenario proposed in this paper, where the relay UAV U is in full-duplex mode and there are eavesdropping interferences in both the first and second phases of the relay communication link. From the figure, it can be seen that the size relationship of secrecy outage probability under different eavesdropping interference schemes is: double interference scheme < single interference scheme < no interference scheme, so the relationship of system security performance is double interference scheme > single interference scheme > no interference scheme. For the dual interference scheme proposed in this paper, as
decreases, for example, A changes from 0.4 to 0.2, the SOP decreases. This is because when the total transmit power is certain, the decrease in
implies that the jamming signals acting on the eavesdropping node increase; therefore, the SOP of the whole communication link decreases, and the security performance of the system is enhanced, which verifies the relationship between the SOP and
once again. The results show that the proposed scheme in this paper outperforms the half-duplex UAV scheme as well as the non-interference scheme in terms of security performance.