Abstract
Currently, we are facing an increasing trend in the use of unmanned aerial vehicles (UAV) in various activities, both civilian and military. The application of UAVs in the battlefield has received extensive attention amid a global new military revolution. A UAV cluster is a large and complex real-time feedback system that integrates a communication and sensor network, control system, calculation, and physical process. The heterogeneous UAVs conduct complex behaviors, which requires a comprehensive description and analysis of UAV cluster modeling. The integrated modeling of the heterogeneous UAV cluster is of great significance and value to test and verify the new combat mode. In this paper, we present a novel representation framework based on the Petri nets. We used a spatial-temporal hybrid Petri net to illustrate the discrete state and continuous process of a heterogeneous UAV cluster system, and effectively achieved the fusion of a physical and computational process and interaction event modeling in the cluster system. Finally, the formal verification of UAV cluster attack mission modeling was carried out by UPPAAL, suggesting the proposed modeling method is feasible and effective.
1. Introduction
The increasing application of the new generation of artificial intelligence technology and autonomous technology rapidly in the battlefield will give birth to a new type of combat force and overturn the traditional mode of war [1,2,3,4,5]. The future war will be intelligent war. The application of a UAV cluster in a battlefield is an important part of intelligent warfare. The UAV cluster is a kind of large and complex real-time feedback system that integrates the calculation process, the communication network, the physical process, sensor network, and control system. We need a comprehensive description and analysis on the model of the UAV cluster due to the various forms of complex behavior between heterogeneous UAVs. Using the modeling and simulation method to study the relevant issues of UAV cluster combat can provide theoretical support for the development and application of this new combat style, which has important practical significance [6,7,8]. Cao Ruimin [9] proposed the hybrid stochastic timed Petri net (HSTPN) modeling method for hybrid systems featuring discrete, continuous, conflicting, time-delay, and stochastic characteristics simultaneously. Song Xiangjun [10] used an extended Petri net to model the obstacle avoidance system of the unmanned vehicle, and such models were converted into corresponding Simulink models. The dynamic behaviors and attributes of the obstacle avoidance system was analyzed through the simulation of MATLAB T. In Thacker’s [11] proposal, they labeled a hybrid Petri net model and proposed an automatic extraction technique that could simplify the model handling the state space explosion problem, which can be used for CPS modeling and verification. Hu Haiyang [12] proposed a compression algorithm to convert OGSPN into a generalized stochastic Petri net (GSPN), through which the CPS was abstracted into several types of objects and its logical structure and working process was visually described. Considering the uncertainty of CPS, Hu used a fuzzy mathematics-based method to process the compressed model of GSPN to improve the accuracy of the performance analysis. A variety of CPN (colored Petri net) models were established to represent fleet maintenance activities and maintenance management, taking into consideration the factors that have a significant impact on fleet maintenance including fleet operation, aircraft failure logic, and component failure processes [13]. Peng Shitong [14] built a transition timed Petri net using the heuristic A* algorithm to deal with the scheduling in remanufacturing scheduling. Jianchao Luo [15] developed a Petri net model that can well deal with all AMS characteristics, and proposed a Banker’s algorithm, like deadlock avoidance policy. Zhang Jing [16] used hybrid Petri nets to model and analyze the operating mechanism of adaptive cruise control system and verified the feasibility of the proposed model. Song Zhenhua [17] proposed a CPS model based on AOP spatial-temporal Petri net, which was successfully applied in the fault detection and repair of a robot system. Tan [18] proposed a CPS real-time event model based on spatial-temporal hybrid Petri nets and analyzed the reliability of the method by modeling a medical control system. Wang [19] used spatial-temporal hybrid Petri nets to build and verify a CPS model. Based on formal modeling methods, Guo [20] analyzed and detected the logic flaw of poor synchronization. To avoid this kind of logic flaw, Guo presented a novel optimized modeling solution based on the synchronization theory of Petri nets and further improved the calculation method of the synchronic distance.
Petri net is a formal graphical model, which can intuitively reveal the essence of the system operation process with a suitable modeling scheme [21,22,23]. Heterogeneous UAV cluster modeling is characterized by deep integration of the discrete process and continuous process, physical process, and computational process. However, most of the current UAV modeling research has only studied a single physical object. There is a lack of studies regarding the characteristics of UAV clusters, and a lack of research work on the formal verification of the practical application of scenario modeling. With the popularization of UAV deployment, the cooperation of multiple UAVs in the cluster has become a prominent problem, which makes it necessary to investigate an integrated modeling method. In order to study the characteristics of the UAV cluster, based on the requirements of intelligent war, this paper studied the model construction method of a heterogeneous UAV cluster, represented by the maneuvering behavior using spatial-temporal Petri nets, and defined the interaction events to solve the integrated modeling problem. The UPPALL tool was used to verify the modeling method. The contributions of this paper are two-fold, as follows.
- (1)
- A modeling method based on spatial-temporal hybrid Petri nets was proposed. Its high expressiveness allows one to effectively model the complex behavior of the UAV cluster.
- (2)
- By introducing the labeling mechanism, an external event can be specified to enrich the expressiveness of the model.
2. The Modeling Method of UAV Cluster
The variation in the UAV flight state can be expressed as [24]:
where from left to right, the first three attributes are the coordinates, pitch angle, roll angle, yaw angle, roll angular velocity, pitch angular velocity, yaw angular velocity, velocity vector (also divided into three axis velocity components u, v, w), angle of attack, sideslip angle, and mass.
2.1. The Modeling Method of Interaction Event
The UAV cluster can be regarded as a typical cyber physical system including physical space and information space. The interaction of a UAV mission between information and physics can be viewed as the interaction between the perception events and control events. Perception events include the perception of key attributes such as speed, altitude, pitch angle, and roll angle. Control events include maneuvers such as flat flight, acceleration and deceleration, dives, jumps, and combat turns.
2.1.1. Definition of the Perception Event Model
A meta perception event refers to sensors perceiving the key attributes of the UAV. Whether this event occurs is determined only by the numeric value of a key attribute.
Definition 1.
Formal model of a meta perception event:
where is a class of a meta perception event; is the name of the event;is the name of related attributes; is the trigger rule.
Definition 2.
Trigger rules of a meta perception event:
where is the operator of the attributes; is a real number; is the trigger rule of a perception event. For example, a UAV performs horizontal acceleration and deceleration maneuvers, , where is the name of the maneuver, and a is the key attribute. When the value ofis greater than , the horizontal acceleration event of will be triggered, then the UAV immediately performs a horizontal acceleration maneuver. Since the execution process of the UAV task has temporal and spatial attributes, a perception event model at a certain time and place can be expressed as:
where and represent the temporal and spatial attributes of the perception event, respectively.
The triggering of most maneuvers of an UAV is controlled by multiple key attributes and multiple meta perception events. Based on Definition 1, represents the attribute name related to the combination perception event, andis the set of trigger rules.
The integrated perception event model is defined based on Definition 2.
Definition 3.
Formal model of an integrated perception event:
2.1.2. Definition of the Interaction Event Model
Each maneuver of UAVs is driven by events.
Definition 4.
Formal model of an interaction event:
where is the perception event in the interaction event; is the receiver of the perception event; is the responder of the perception event or the producer of the control event; andis the control event in the interaction event. The control event can be defined as:
is a set containing multiple key attributes, and is the set of values of the key attribute.
2.2. The Modeling Method of Heterogeneous UAV Cluster System Behavior
A heterogeneous UAV cluster system is a hybrid system with discrete behavior and continuous behavior. There are two kinds of modeling methods for hybrid system. The non-formal method is incomplete because it cannot detect all possible states of the system exhaustively. Formal modeling methods include hybrid automata, hybrid behavior systems, hybrid communication sequence processes, and hybrid Petri nets. Compared with other methods, the hybrid Petri net has the advantages of finite state description, description simplification, and widening application range. Therefore, spatial-temporal factors are introduced into the spatial-temporal hybrid Petri net as a new model to describe the behavior of a heterogeneous UAV cluster system.
Definition 5.
Formal model of heterogeneous UAV cluster system behavior:
whereis the finite set of places represented by circular nodes; is the finite set of transitions represented by square nodes; is the set of flow relations represented by directed arcs;is the weight function; is the initial identification vector; is a hybrid function; is the set of conditions; is the excitation velocity of continuous transition; represents the time function; is the spatial position.
Definition 6.
There is a one-to-one correspondence between events and discrete transitions. The excitation of discrete transitions indicates the occurrence of corresponding events.
There are both discrete state nodes and continuous state nodes in a spatial-temporal hybrid Petri net, and their interactions are represented by directed arcs. The excitation of transitions indicates the occurrence of corresponding events.
3. UAV Cluster Modeling and Formal Verification
We took the heterogeneous UAV cluster collaborative combat scenario as the object for modeling and used the UPPAAL tool based on time automata to verify the availability, reliability, and real-time capability of the built model to evaluate the feasibility of the modeling method.
3.1. Modeling Instance
We used a heterogeneous UAV cluster combat scenario to verify the modeling method. Suppose that the red side is a heterogeneous UAV cluster system consisting of two reconnaissance UAVS, three attack UAVs and a control center, and the blue side consists of two UAVs. The red side conducts reconnaissance and attack missions against the blue side. The scenario of the attack mission is complex. There will be many situations in the actual attack mission such as weather, equipment, and surrounding environment. This paper assumes that all external factors are ideal, and the whole process of the attack mission can be regarded as a sequence of events.
We will show a modeling instance for an attack mission of a heterogeneous UAV cluster. The attack mission has the following primitive behaviors:
- Search target
The UAV cluster searches the blue side through the event of reconnaissance carried out by reconnaissance UAVs.
- Assign tasks
The control center assigns specific tasks to each UAV.
- Approach target
With the assistance of reconnaissance UAVs, attack UAVs approach the target.
- Target acquired
With the assistance of reconnaissance UAVs, the targets are acquired by attack UAVs.
- Mission complete
UAV cluster complete attack mission.
The heterogeneous UAV cluster system includes reconnaissance UAVs, attack UAVs, and reconnaissance/attack UAVs as well as sensors. The formal expression is shown in Formulas (9) and (10):
where is the dynamic attributes; is the kinematic attributes; is the reconnaissance behavior; is the attack behavior; Z is the coordinate of UAV; is a point or an interval; indicates the change of sensor data; indicates that the sensor data remain unchanged.
- Acceleration sensor
- Gyroscope sensor
- Reconnaissance UAV
- Attack UAV
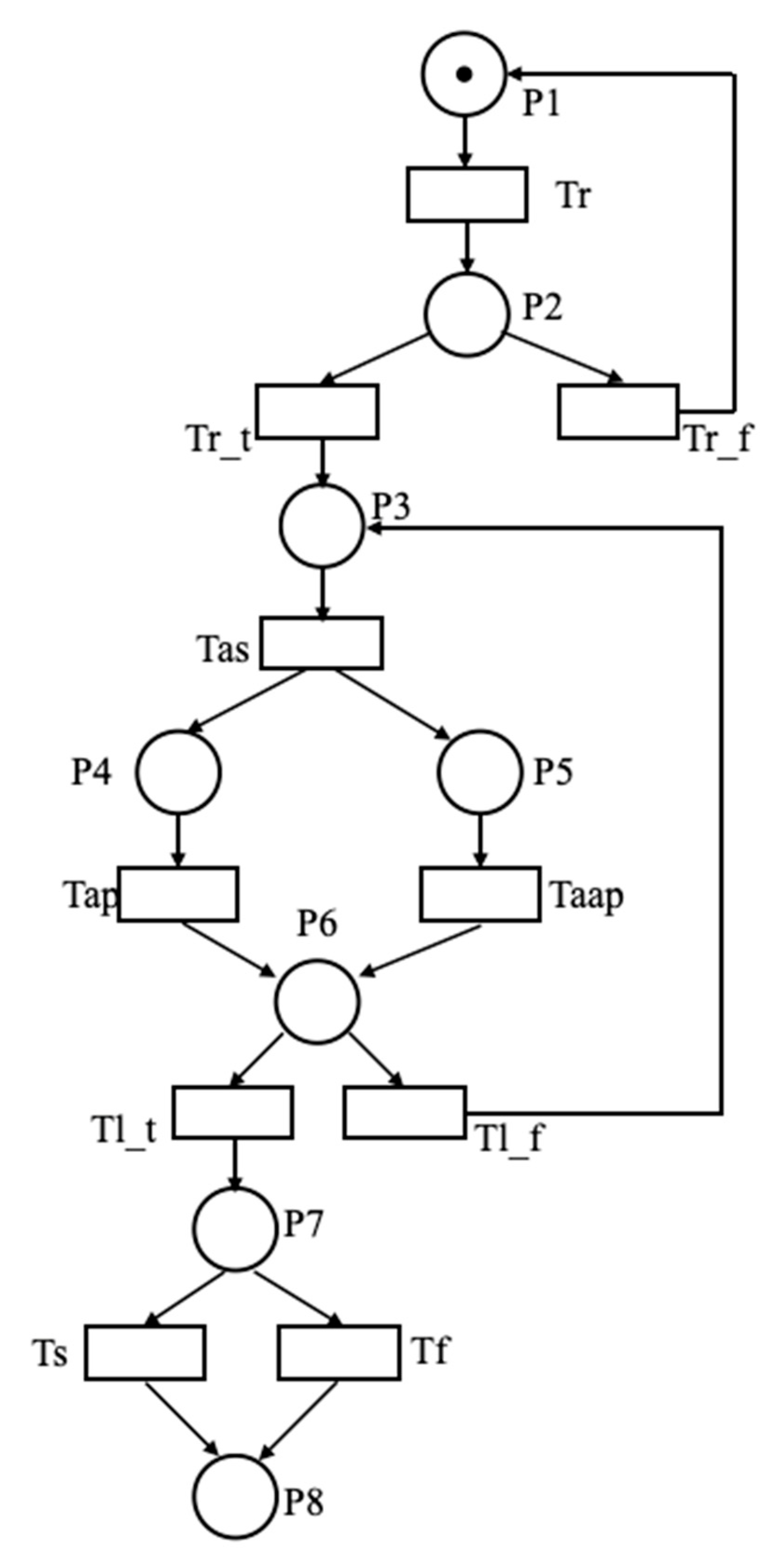
Modeling high level behaviors for a UAV cluster executing complex attack mission in dynamic, partially observable, and environments requires a powerful modeling method. The attack mission of a heterogeneous UAV cluster can be described as a Petri net, as shown in Figure 1. The process of the attack mission begins with a reconnaissance event. When the targets are detected, the control center will carry out task assignment. Then, with the assistance of reconnaissance UAVs, the attack UAVs approach the targets. When the targets are acquired by the attack UAVs, an attack action will be carried out. Finally, the process of the attack mission is ended whether the targets are destroyed or not.
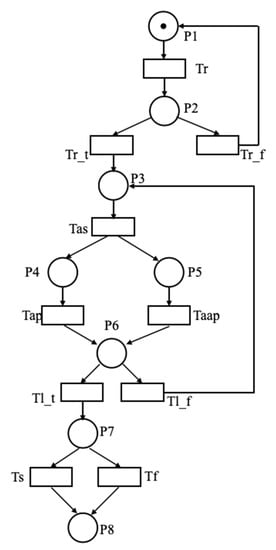
Figure 1.
The Petri net of the attack mission of a heterogeneous UAV cluster.
The formal model of the attack mission of a heterogeneous UAV cluster can be expressed as Formula (14). , places represent the execution phases of the attack mission. , transitions represent events (i.e., is the reconnaissance event; is the mission complete event. Here, we introduced a labeling mechanism for transitions in the Petri net to specify external events. All transitions may be labeled with conditions that must be verified in order to be fired when enabled. A condition on the transition is denoted with . If no condition is specified for a transition, we will assume that it is True. . , , for each . is the initial marking representing a description of the initial state of the attack mission. . is a hybrid function (i.e., the maneuvers of UAV). E is the set of conditions (i.e., ). V is the firing velocity of continuous transition; I represents the time function; A is the spatial position. The explanation of places and transitions is shown in Table 1.

Table 1.
The explanation of transitions.
The state of the attack mission during the execution of the Petri net is given by its marking. Transitions between two states are modeled by transitions in the Petri net (i.e., by evolution of its markings). During the execution of the Petri net of the attack mission, we assumed that UAVs were provided with a set of functions that can evaluate its internal state. These functions were used to evaluate the conditions labelling the transitions of the Petri net and thus determine when and how it is possible to perform such transitions.
Given two markings , , a transition from to is enabled if , so that
- (i)
- , , then ;
- (ii)
- for each ;
- (iii)
- for each .
An enabled transition from to is denoted by .
Given two markings , , and a situation at time , firing a transition from to in situation , if , a transition from to is enabled and the event condition labelling the transition t ( is verified in situation .
There exists a finite sequence of markings such that is the initial markings, and is the goal marking, which shows that the Petri net of the attack mission is executable.
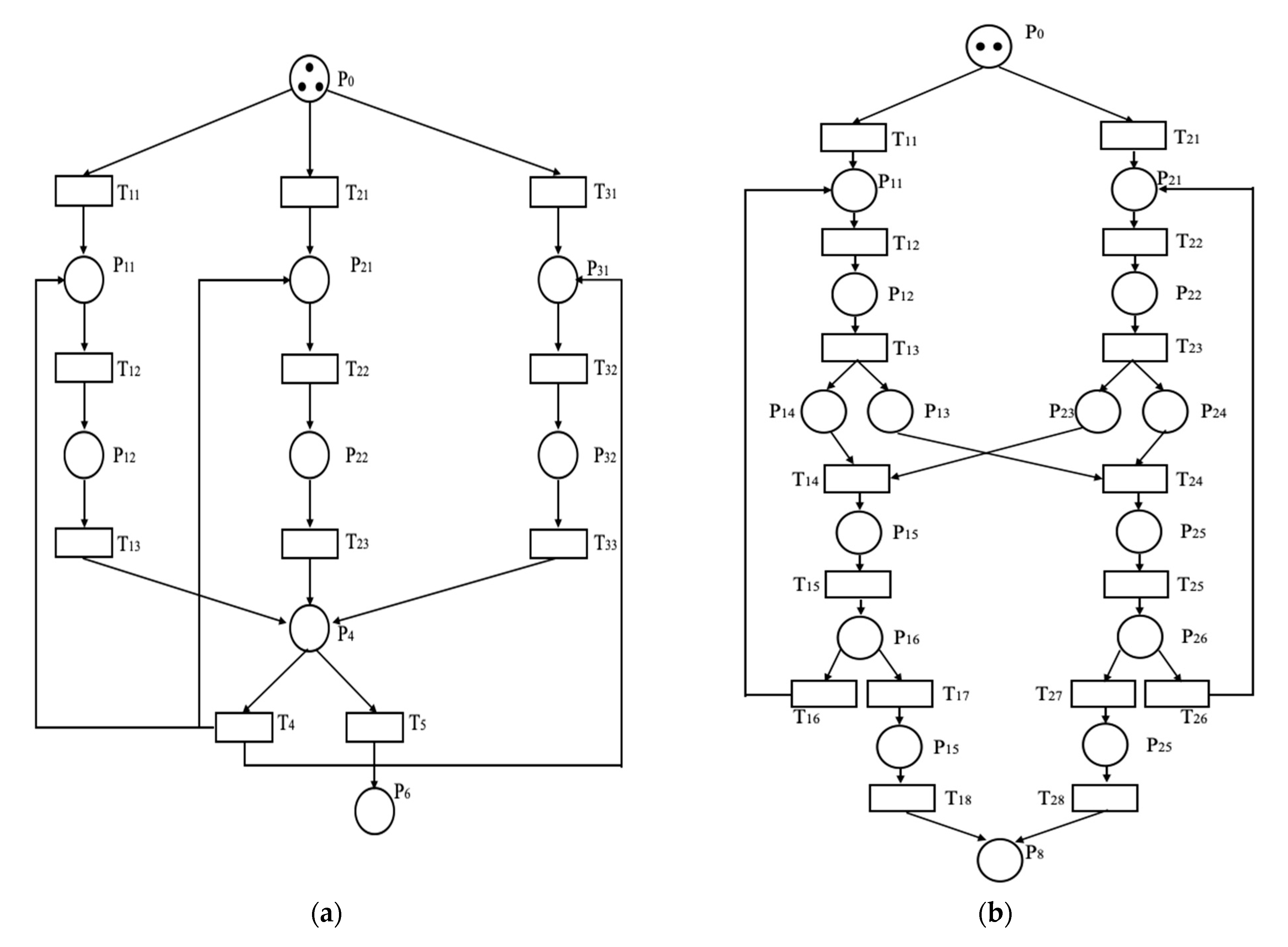
We used Petri net to simulate the process of the coordinated combat of the heterogeneous UAV cluster. The attack UAVs will execute the attack mission when all the attack UAVs reach the specified position. The collaborative attack/reconnaissance process of the UAVs was mapped in Petri net, as shown in Figure 2.
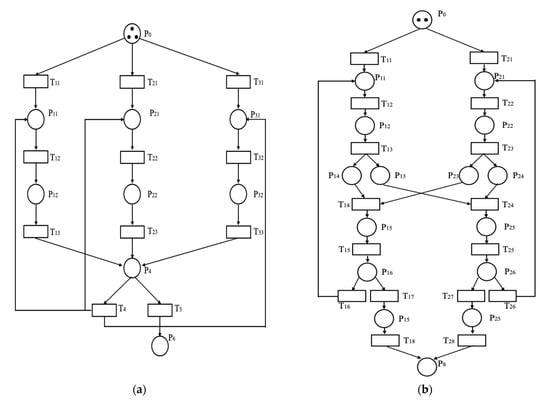
Figure 2.
The Petri net of the attack/reconnaissance process. (a) Petri net of the coordinated attack process. (b) Petri net of the coordinated reconnaissance process.
Figure 2a shows the model of the coordinated attack process; represents that the attack UAVs arrive at the specified area; represents the state of each UAV, ; is used to identify different attack UAVs. When j = 1, the UAVs will carry out coordinated attack. When j = 2, each of the UAVs will notify the control center of the completion of its own task. shows that the control center receives the message about the completion of the coordinated attack task. represents the end of the coordinated attack mission. represents the state changes of the attack UAVs, represents a coordinated attack task that is assigned, represents a coordinated attack task that is carried out, j = 3 represents that the attack UAVs sends the information of completion of the attack mission to the control center. represents that the control center has received the message that the attack mission has not been completed, indicating that some targets are left undestroyed. shows that all two targets were destroyed. The initial marking .
Figure 2b shows the model of the coordinated reconnaissance process, shows that the reconnaissance UAVs arrive at the specified area; represents the state of each UAV, ; is used to identify different reconnaissance UAVs; is used to represent the different states of reconnaissance task, . When , reconnaissance UAVs carry out the reconnaissance task, represents the exchange of information between two reconnaissance UAVs, determines whether the current reconnaissance information is fully obtained, shows that the reconnaissance task is complete. The initial marking is .
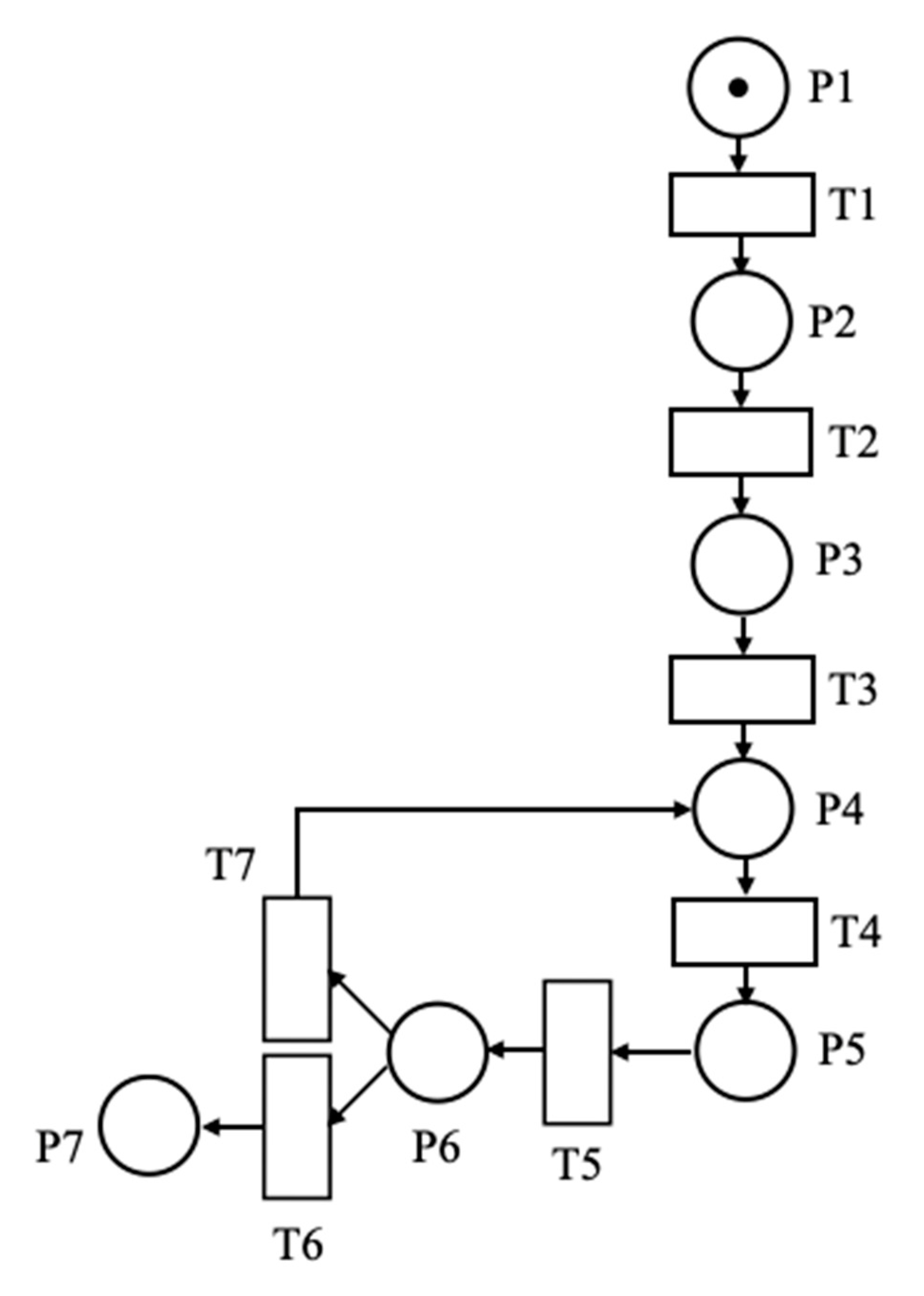
We used spatial-temporal hybrid Petri nets to simulate the behavior of the individual UAV, as shown in Figure 3.
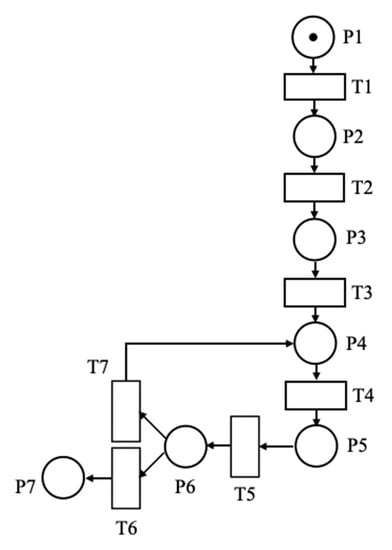
Figure 3.
A spatial-temporal hybrid Petri net model of a UAV attack process.
The UAV completes an attack mission through the following procedures.
- Reaches the specified position through horizontal acceleration maneuver;
- Performs a dive maneuver to reach directly above the first target;
- Performs a horizontal deceleration maneuver to approach the target;
- Performs a chandelle maneuver;
- Performs a zooming maneuver and finishes the attack mission.
The places and transitions in the spatial-temporal hybrid Petri net include discrete and continuous attributes. Place represents the state of different maneuvers of the attack UAVs. Transition shows when the maneuver changes. , 1 represents the token in ; represents the continuous attributes of UAV shown in Formula (1).
represents the level accelerating, where the speed of the UAV rises from 200 m/s to 300 m/s, and key attributes such as velocity and tangential overload are changed. The velocity of the UAV at time in represents the differential equation for the change in velocity, as defined in Equation (16).
indicates that the horizontal acceleration maneuver has been completed. represents the dive maneuver. The differential equation for the change in the angle of attack is as defined in Equation (17).
indicates that the dive maneuver has been completed. represents the horizontal deceleration maneuver, which is like the horizontal acceleration maneuver. indicates that the horizontal deceleration maneuver has been completed. represents the chandelle maneuver. The differential equation for the change in height is as defined in Equation (18).
The differential equation for the change in the roll angle is as defined in Equation (19).
represents that the chandelle maneuver has been completed. represents a jump maneuver. represents that the jump maneuver has been completed. represents that the current attack job has been completed. represents the return to as several targets are left unattacked. represents that the individual UAV have completed all of its attacks. represents the end of the attack mission.
The key attributes in the of interaction events include velocity , height , air flow angle of attack , and roll angle . Different attribute values represent different events. The modeling of perception events, control events, and interaction events is as follows:
- Model of perception events
- Model of control events
- Model of interaction events
3.2. Formal Verification of the Modeling
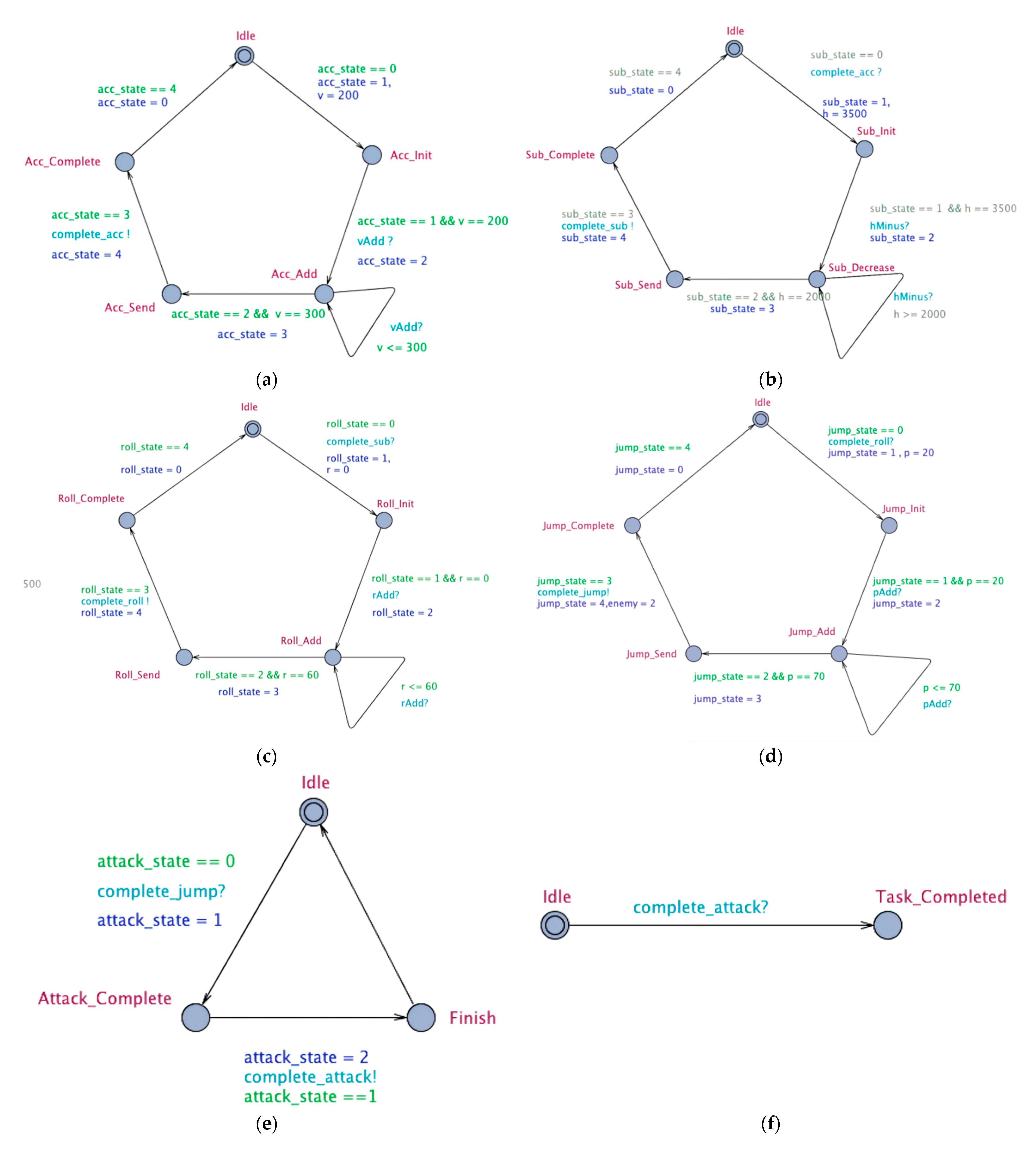
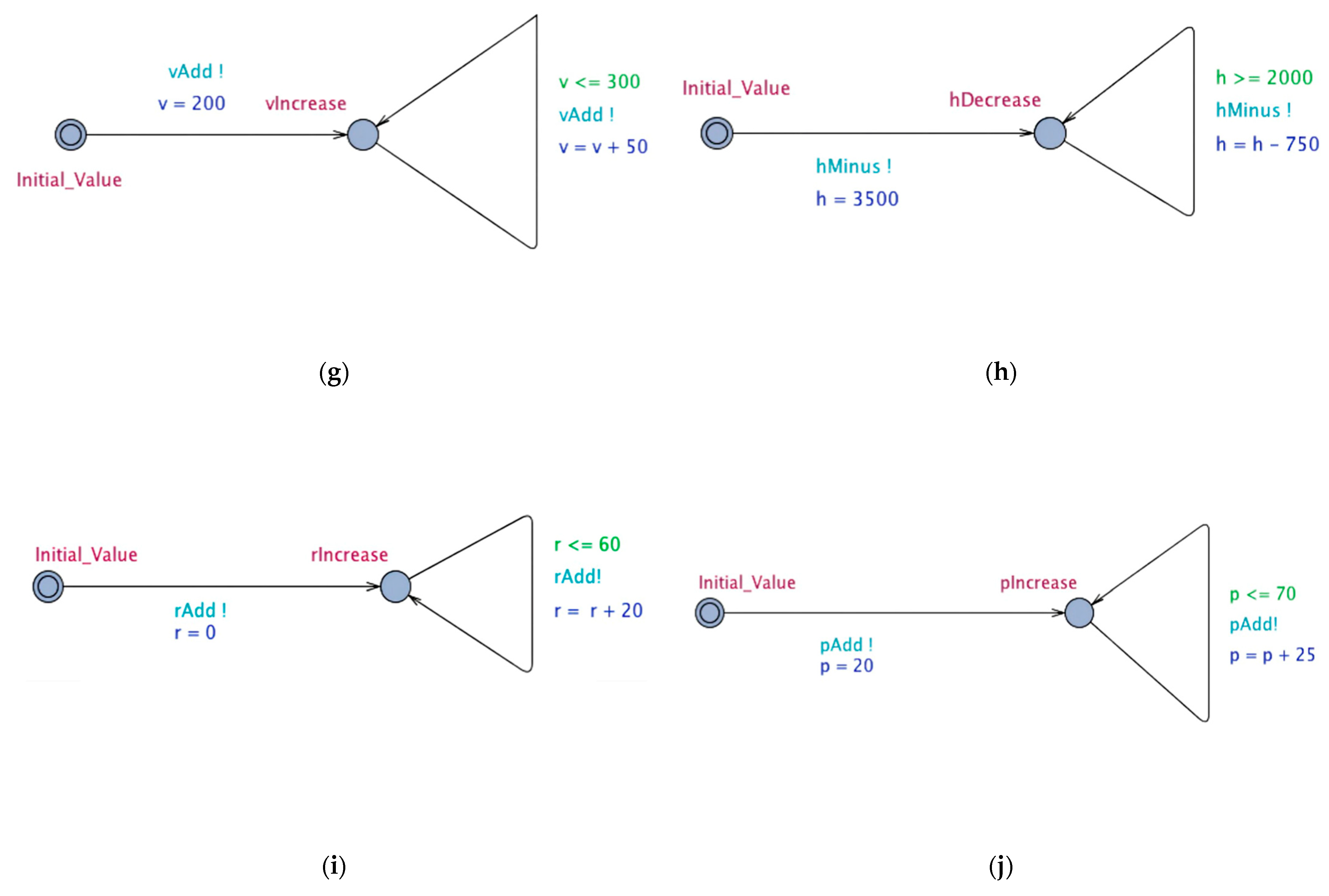
In addition to six discrete maneuver action modules including Acc_Action, Sub_Action, Turn_Action, Jump_Action, Attack_Action, Finished_Action, which respectively represent horizontal acceleration maneuver, dive maneuver, chandelle maneuver, jump maneuver, attack maneuver and mission accomplished, there are four continuous attribute modules including Velocity, Height, Roll, Pitch. These modules communicate with each other through synchronous channels. These ten modules are mapped into timed automata templates, where each process in the module corresponds to a location of the template, and each maneuver action corresponds to a synchronous channel of the template. The timed automata is shown in Figure 4.
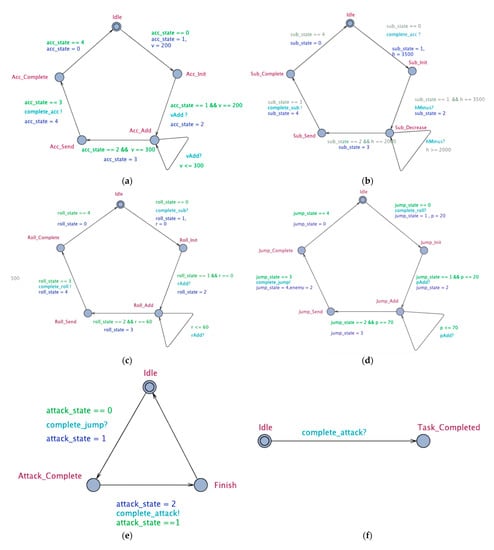
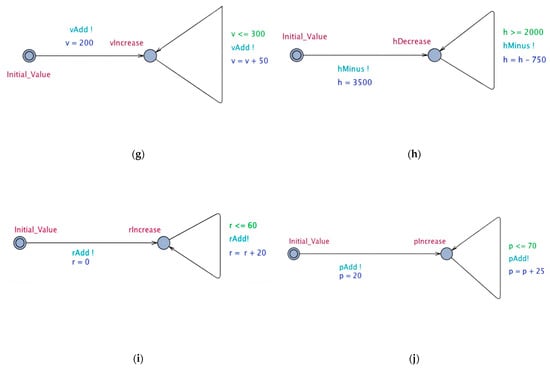
Figure 4.
Timed automata of ten modules. (a) TA of Acc_Action. (b) TA of Sub_Action. (c) TA of Turn_Action. (d) TA of Jump_Action. (e) TA of Attack_Action. (f) TA of Finished_Action. (g) TA of Velocity. (h) TA of Height. (i) TA of Roll. (j) TA of Pitch.
As shown in Figure 4, circles represent various states of the system, where directed segments with arrows represent transitions of different states in the system, red circles represent the current state, dark blue data are the update of the current state, green data are the conditions for state transition, and light blue data represent the synchronous channel of transmission of the current state.
4. Discussion
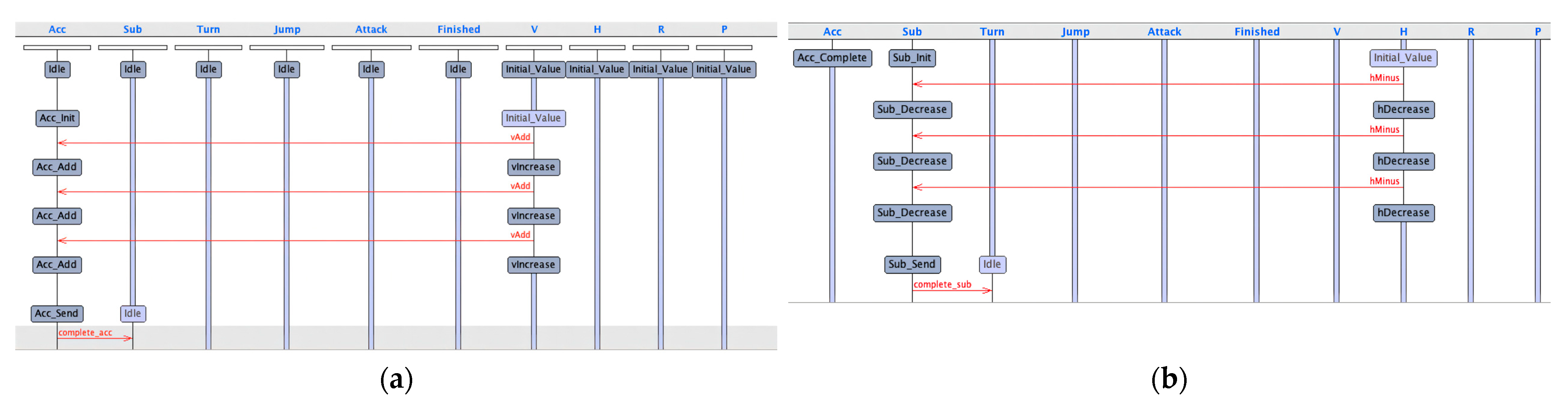
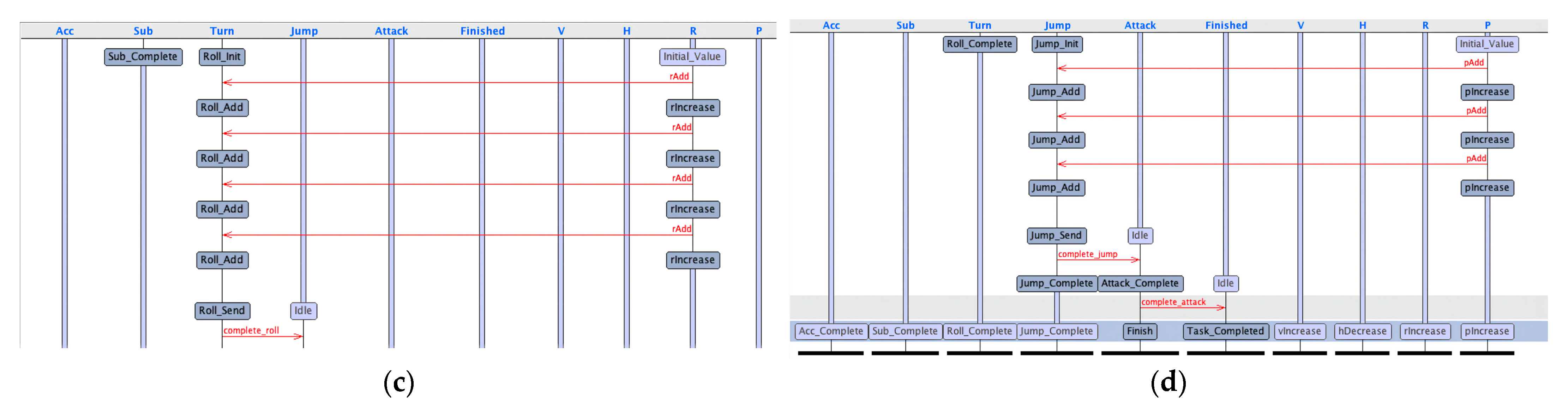
We used the UPPAAL tool [25,26] for automatic analysis. The flowchart of instances of the attack mission is shown in Figure 5.
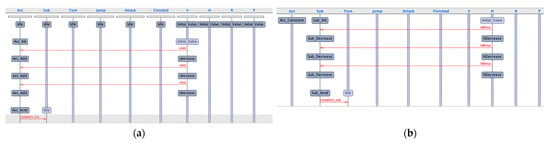
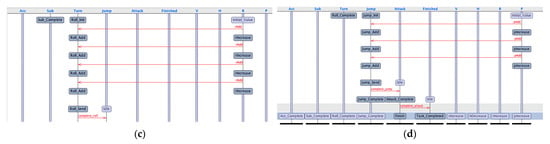
Figure 5.
Flowchart of the attack mission. (a) Flowchart of Acc_Action. (b) Flowchart of Sub_Action. (c) Flowchart of Turn_Action. (d) Flowchart of Jump_Action, Attack_Action and Finished_Action.
Based on the timed automata template, the key attributes in the process of the heterogeneous UAV cluster attack mission were verified with the help of an UPPAAL tool.
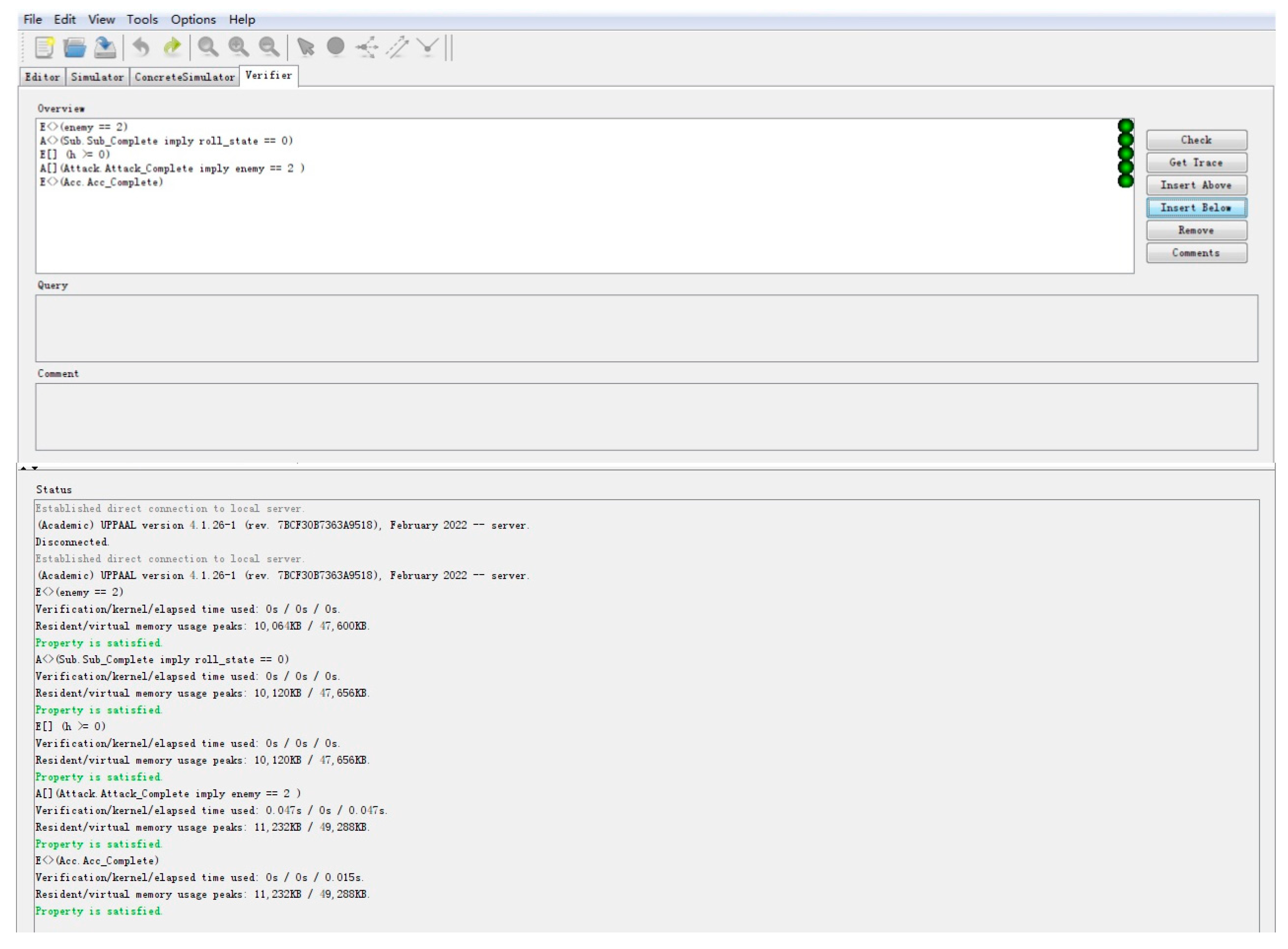
illustrates that there is at least one path in the process of completing the attack mission, and two blue targets are destroyed in the end, which verifies the reachability of the model.
illustrates that the chandelle maneuver followed the dive maneuver, which verified the real-time of the model.
illustrates that the height attribute in the procedure will never be a negative value.
illustrates that all two blue targets are destroyed if the attack mission is complete.
illustrates the existence of a complete state of horizontal acceleration maneuver.
The attributes verified above can represent a certain class of attributes of the events. The verification results are shown in Figure 6. The results show that the model could well represent the process, and all attributes were verified. The model meets the requirements of reliability, accessibility, effectiveness, and real-time performance.
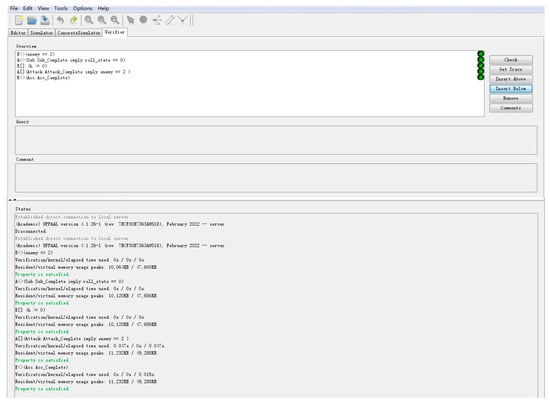
Figure 6.
The validation result of the attributes of the example.
The occurrence of any failure will inhibit the normal mission performance in the physical simulation. This fact leads to the need to consider the security analysis to determine which system has failed and what is the UAV mission phase. Whenever there is a failure in the flight controllers or in the communication, or a combination of failures of these systems, the normal execution of the UAV mission will be interrupted. Such cases were not considered in this article. For future research, this interruption may be represented by a dashed arc (inhibiting arc) in the Petri net. In this situation, the UAV will perform security analysis to identify the flight phase in which the failure occurred.
5. Conclusions
The experience in using a spatial-temporal hybrid Petri net for modeling the attack mission of a UAV cluster has been very effective, providing many advantages over other methods as well as some difficulties that we have dealt with.
This paper focused on representing the heterogeneous UAV cluster combat mission through spatial-temporal hybrid Petri net modeling. First, the modeling and verification of the heterogeneous UAV cluster combat mission was performed, then the dynamic and kinematic equation of the change in key attributes of the heterogeneous UAV cluster were represented, and the formal modeling of the perceptive events, control events, and their interaction event was achieved, extending the single object modeling to various objects modeling for UAVs. This modeling method can effectively represent the fusion of the physical and computational process and information exchange and coordination between each UAV node in the UAV cluster system. Throughout verification, the UPPAAL tool provides an effective framework and environment to demonstrate the reliability, accessibility, effectiveness, and real-time of the aforementioned modeling method.
The main advantage of the spatial-temporal hybrid Petri net is the clear definition of the modeling language and of its semantics in terms of Petri nets. Using such a modeling method guarantees the possibility of using standard tools to evaluate the properties of the model such as liveness and reachability of the goal states. High expressiveness of the spatial-temporal hybrid Petri net allows for effectively capturing and dealing with most of the situations encountered in the research of a UAV cluster.
Although we proposed a modeling method to describe the scenario of the attack mission of a UAV cluster, in order to have a clear specification of the behavior of the UAV cluster, it may still be very difficult to design a model when more and more factors are considered and the dependency across each other becomes more complex. There is no automatic tool to support the conversion between the behavior model proposed in this paper and the simulation verification model, and further research is needed to simplify the connection process between the formal characterization model and the simulation model.
Author Contributions
Methodology, X.W. and N.L.; Validation, N.L. and P.H.; Writing—original draft preparation, X.W. and N.L.; Writing—review and editing, Y.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research has been supported the Project of National Defense Basic Research Program, the National Defense Science and Technology Key Laboratory Fund Under Grant No. 6142219200205, the Open Fund of CETC Key Laboratory of Data Link Technology Under Grant No. CLDL-20202208_2, the Fundamental Research Funds for the Central Universities (G2022KY0603) and the National Natural Science Foundation of China under grant No.62203361.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zohreh, H.; Arash, M.; Jamshid, A.; Ming, H. Joint Transmission Scheme and Coded Content Placement in Cluster-Centric UAV-Aided Cellular Networks. IEEE Internet Things J. 2022, 9, 11098–11114. [Google Scholar]
- Zhou, L.; Leng, S.; Liu, Q.; Wang, Q. Intelligent UAV Swarm Cooperation for Multiple Targets Tracking. IEEE Internet Things J. 2022, 9, 743–754. [Google Scholar] [CrossRef]
- Dui, H.; Zhang, C.; Bai, G.; Chen, L. Mission Reliability Modeling of Uav Swarm and Its Structure Optimization Based on Importance Measure. Reliab. Eng. Syst. Saf. 2021, 215, 107879. [Google Scholar] [CrossRef]
- Fabra, F.; Zamora, W.; Masanet, J.; Calafate, C.T.; Cano, J.-C.; Manzoni, P. Automatic system supporting multicopter swarms with manual guidance. Comput. Electr. Eng. 2019, 74, 413–428. [Google Scholar] [CrossRef]
- Yang, J.; You, X.; Wu, G.; Hassan, M.M.; Almogren, A.; Guna, J. Application of reinforcement learning in UAV cluster task scheduling. Future Gener. Comput. Syst. 2019, 95, 140–148. [Google Scholar] [CrossRef]
- Ouyang, M. Review on modeling and simulation of interdependent critical infrastructure systems. Reliab. Eng. Syst. Saf. 2014, 121, 43–60. [Google Scholar] [CrossRef]
- Macal, C.M.; North, J. Agent-Based Modeling and Simulation. AI Mag. 2012, 33, 29–40. [Google Scholar]
- Zhang, X.; Chan, F.K. Tejaswin Parthasarathy, and Mattia Gazzola. Modeling and simulation of complex dynamic musculoskeletal architectures. Nat. Commun. 2019, 10, 4825. [Google Scholar] [CrossRef]
- Ruimin, C.; Lina, H.; Fengli, W.; Qiang, G. Modelling and Analysis of Hybrid Stochastic Timed Petri Net. J. Control Decis. 2019, 6, 90–110. [Google Scholar]
- Song, X.; Zhang, G. Modeling and analysis of CPS unmanned vehicle systems based on extended hybrid Petri net. Comput. Sci. 2017, 44, 21–24. [Google Scholar]
- Thacker, R.A.; Jones, K.R.; Myers, C.J.; Zheng, H. Automatic abstraction for verification of cyber-physical systems. In Proceedings of the ACM/IEEE 1st International Conference on Cyber-Physical Systems, Stockholm, Sweden, 13 April 2010. [Google Scholar]
- Haiyang, H.; Jiawei, Y.; Zhongjin, L.; Jie, C.; Hua, H. Modeling and Analysis of Cyber–Physical System Based on Object-Oriente Generalized Stochastic Petri Net. IEEE Trans. Reliab. 2021, 70, 1271–1285. [Google Scholar]
- Sheng, J.; Darren, P. A coloured Petri net framework for modelling aircraft fleet maintenance. Reliab. Eng. Syst. Saf. 2019, 189, 67–88. [Google Scholar] [CrossRef]
- Shitong, P.; Shitong, P.; Tao, L.; Jiali, Z.; Yanchun, G.; Shengping, L.; George, Z.T.; Hongchao, Z.; Hongchao, Z. Petri net-based scheduling strategy and energy modeling for the cylinder block remanufacturing under uncertainty. Robot. Comput. Integr. Manuf. 2019, 58, 208–219. [Google Scholar]
- Luo, J.; Liu, Z.; Zhou, M. A Petri Net Based Deadlock Avoidance Policy for Flexible Manufacturing Systems with Assembly Operations and Multiple Resource Acquisition. IEEE Trans. Ind. Inform. 2019, 15, 3379–3387. [Google Scholar] [CrossRef]
- Zhang, J.; Yuan, Z. Modeling of CPS events based on augmented hybrid Petri nets. Comput. Eng. Sci. 2020, 303, 173–179. [Google Scholar]
- Song, Z.; Zhang, G. Modeling of CPS based on aspect-oriented spatial-temporal petri net. Comput. Sci. 2017, 44, 38–41. [Google Scholar]
- Tan, P.; Wang, Y.; Zhu, M. Real-time event CPS model based on hybrid spatial-temporal Petri nets. Transducer Microsyst. Technol. 2016, 35, 32–35. [Google Scholar]
- Wang, Y. Modeling and Verification Based on Hybrid Spatial-Temporal Petri Net for Cyber Physical System. Master’s Dissertation, Nanchang Hangkong University, Nanchang, China, 2006. [Google Scholar]
- Guo, Q.; Yu, W.; Hao, F.; Zhou, Y.; Liu, Y. Modelling and Analysis of Adaptive Cruise Control System Based on Synchronization Theory of Petri Nets. Electronic 2022, 11, 3632. [Google Scholar] [CrossRef]
- Li, J.; Yu, X.; Zhou, M. Analysis of Unbounded Petri Net with Lean Reachability Trees. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 2007–2016. [Google Scholar] [CrossRef]
- Rodríguez, R.J.; Bernardi, S.; Zimmermann, A. An Evaluation Framework for Comparative Analysis of Generalized Stochastic Petri Net Simulation Techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 2834–2844. [Google Scholar] [CrossRef]
- Kim, C.; Yu, T.S.; Lee, T.E. Reachability Tree-Based Optimization Algorithm for Cyclic Scheduling of Timed Petri Nets. IEEE Trans. Autom. Sci. Eng. 2021, 18, 1441–1452. [Google Scholar] [CrossRef]
- Wang, F. Research on the Flight Movement Modeling and Autonomous Control Technology of Unmanned Aerial Vehicle. Master’s Dissertation, Nanjing University of Aeronautics and Astronautics, Nanjing, China, 2009. [Google Scholar]
- Bengtsson, J.; Larsson, F. UPPAAL-a tool for automatic verification of real⁃time systems. In Proceedings of the DIMACS/SYCON Workshop on Hybrid Systems III: Verification and Control, New Brunswick, NJ, USA, 1 July 1996. [Google Scholar]
- Epettersson, K. Glarsen UPPAAL2K: SmallTutorial. Bull. Eur. Assoc. Theor. Comput. Sci. 2000, 70, 40–44. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).