Hybrid Services Collaborative Resource Scheduling Strategy towards Artificial Intelligence of Things
Abstract
:1. Introduction
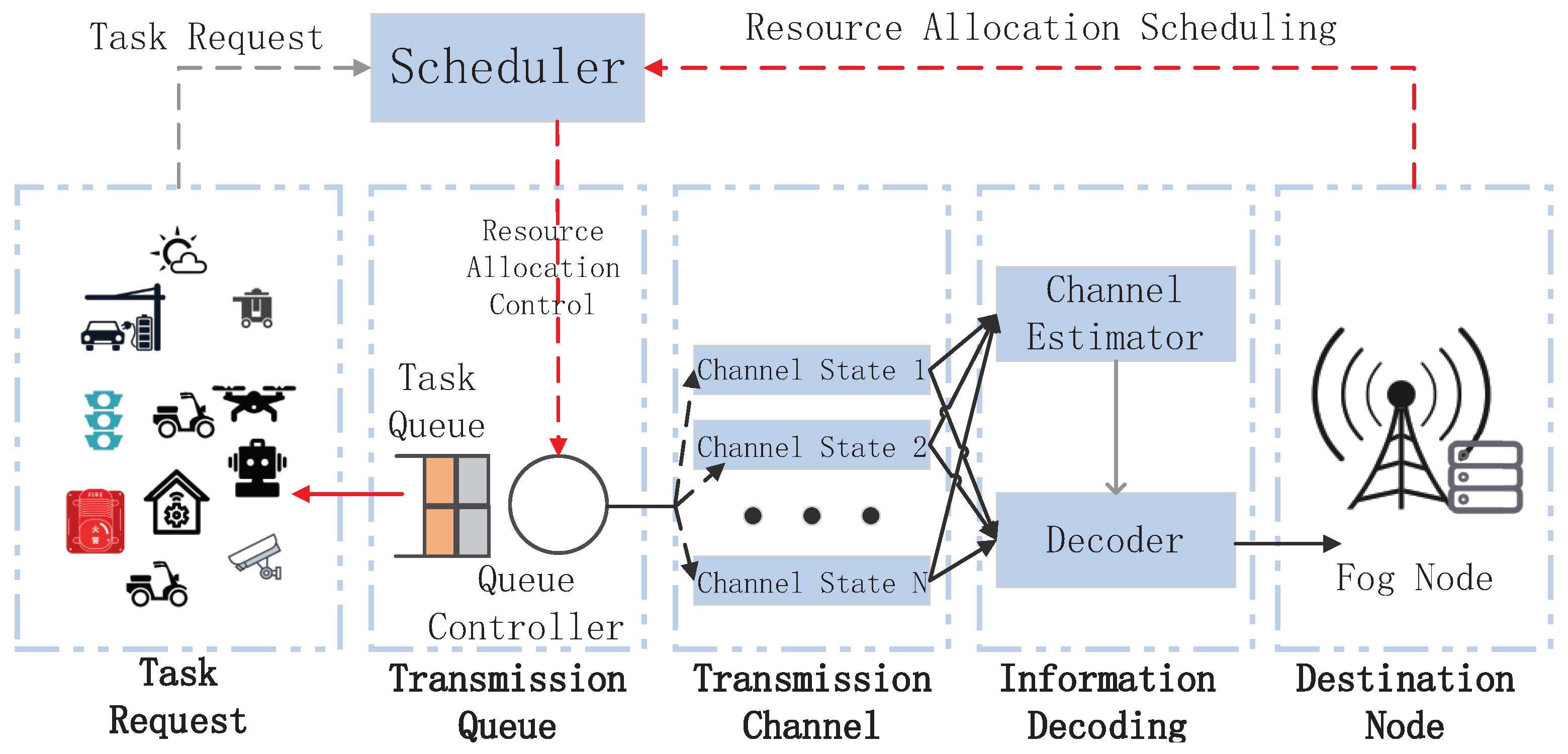
- A multi-layer collaborative resource scheduling framework for the AIoT hybrid services is designed based on the F-RAN, and resource scheduling is performed based on the QoS requirements of different IoT service types.
- A throughput weighting model for hybrid services is constructed to analyze the throughput characteristics of the mMTC service and URLLC service in the AIoT.
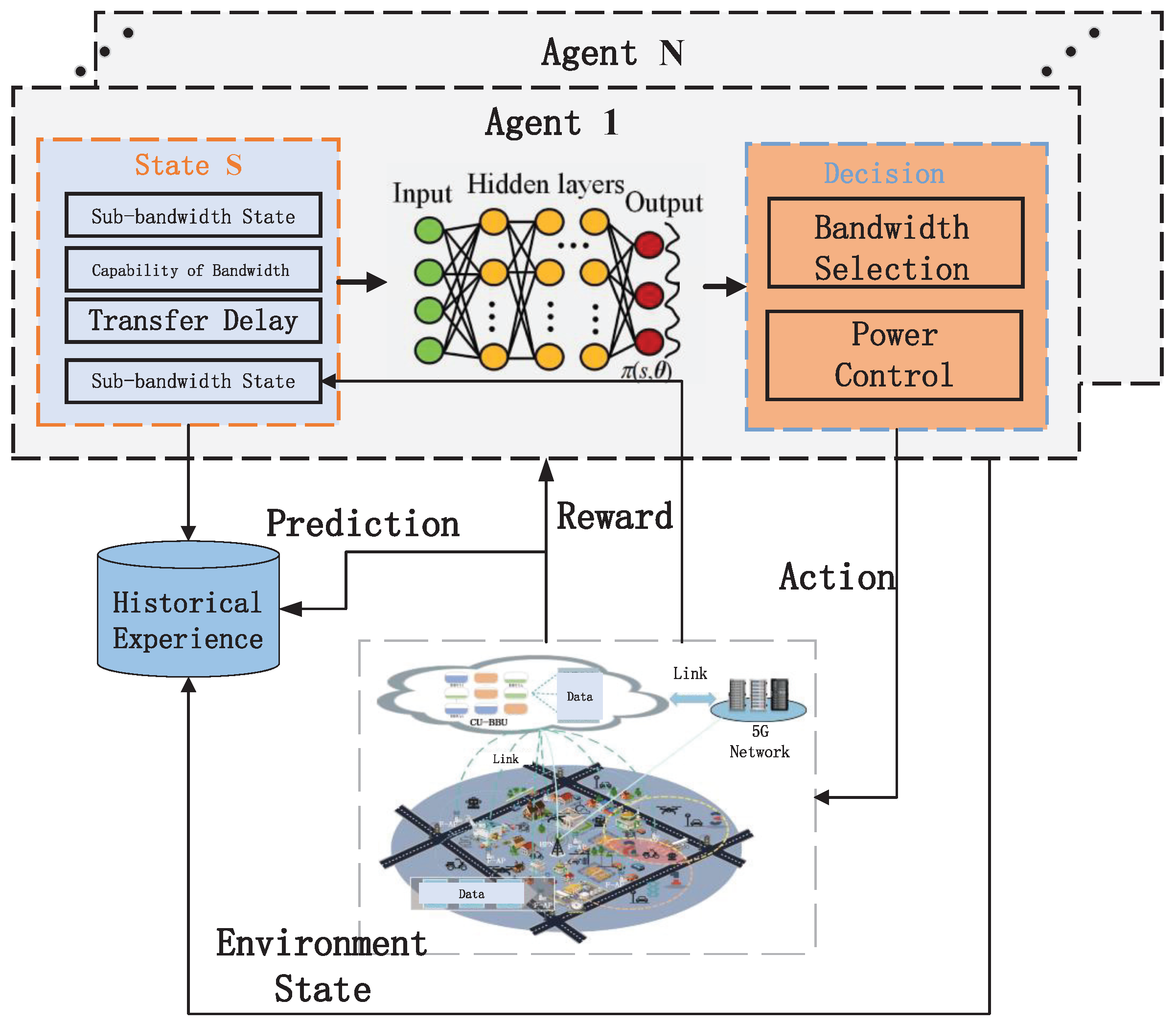
- A sub-channel allocation and power control method is designed to solve the better resource scheduling strategy of AIoT hybrid services in complex environments. At the same time, a multi-agent model is constructed to improve the network throughput in a mixed service scenario.
2. Related Works
2.1. Throughput Optimization Strategy Based on Traditional Fog Architecture
2.2. Throughput Optimization Strategy Based on New Fog Architecture
3. Hybrid Business System Model
3.1. Analysis for System SNR
3.2. Analysis for Throughput in Mixed Services
3.3. Throughput Modeling
4. Throughput Optimization Strategy of Hybrid Service
4.1. Multi-Agent Modeling in Hybrid Service
4.2. Throughput Optimization Algorithm for Hybrid Service
| Algorithm 1 HSCRS. |
|
5. Experiment
5.1. Settings
5.2. Main Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nkenyereye, L.; Hwang, J.; Pham, Q.V.; Jaeseung, S. Virtual IoT service slice functions for multiaccess edge computing platform. IEEE Internet Things J. 2021, 8, 11233–11248. [Google Scholar] [CrossRef]
- Zarca, A.M.; Bernabe, J.B.; Skarmeta, A.; Alcaraz Calero, J.M. Virtual IoT HoneyNets to mitigate cyberattacks in SDN/NFV-enabled IoT networks. IEEE J. Sel. Areas Commun. 2020, 38, 1262–1277. [Google Scholar] [CrossRef]
- Hazra, A.; Adhikari, M.; Amgoth, T.; Srirama, S.N. Stackelberg game for service deployment of IoT-enabled applications in 6G-aware fog networks. IEEE Internet Things J. 2020, 7, 5185–5193. [Google Scholar] [CrossRef]
- Malik, A.W.; Qayyum, T.; Rahman, A.U.; Khan, M.A.; Khalid, O.; Khan, S.U. XFogSim: A distributed fog resource management framework for sustainable IoT services. IEEE Trans. Sustain. Comput. 2020, 6, 691–702. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Toward massive machine type communications in ultra-dense cellular IoT networks: Current issues and machine learning-assisted solutions. IEEE Commun. Surv. Tutorials 2019, 22, 691–702. [Google Scholar] [CrossRef] [Green Version]
- Hu, Y.; Li, Y.; Gursoy, M.C.; Schmeink, A. Throughput analysis of low-latency IoT systems with QoS constraints and finite blocklength codes. IEEE Trans. Veh. Technol. 2020, 69, 3093–3104. [Google Scholar] [CrossRef]
- Li, Y.; Zhao, X.; Liang, H. Throughput maximization by deep reinforcement learning with energy cooperation for renewable ultradense IoT networks. IEEE Internet Things J. 2020, 7, 9091–9102. [Google Scholar] [CrossRef]
- Huang, R.; Wong, V.W.S.; Schober, R. Throughput optimization for grant-free multiple access with multiagent deep reinforcement learning. IEEE Trans. Wirel. Commun. 2020, 20, 228–242. [Google Scholar] [CrossRef]
- Mankar, P.D.; Chen, Z.; Abd-Elmagid, M.A.; Pappas, N.; Dhillon, H.S. Throughput and age of information in a cellular-based IoT network. IEEE Trans. Wirel. Commun. 2021, 20, 8248–8263. [Google Scholar] [CrossRef]
- Xu, Y.; Zhang, H.; Ji, H.; Yang, L.; Li, X.; Leung, V.C.M. Transaction throughput optimization for integrated blockchain and MEC system in IoT. IEEE Trans. Wirel. Commun. 2022, 21, 1022–1036. [Google Scholar] [CrossRef]
- Deb, P.K.; Roy, C.; Roy, A.; Misra, S. DEFT: Decentralized multiuser computation offloading in a fog-enabled IoV environment. IEEE Trans. Veh. Technol. 2020, 69, 15978–15987. [Google Scholar] [CrossRef]
- Ren, C.; Lyu, X.; Ni, W.; Tian, H.; Liu, R.P. Distributed online learning of fog computing under nonuniform device cardinality. IEEE Internet Things J. 2018, 6, 1147–1159. [Google Scholar] [CrossRef]
- Kharel, B.; Lýpez, O.L.A.; Mahmood, N.H.; Alves, H.; Latva-Aho, M. Fog-RAN enabled multi-connectivity and multi-cell scheduling framework for ultra-reliable low latency communication. IEEE Access 2022, 10, 7059–7072. [Google Scholar] [CrossRef]
- Zhao, S.; Yang, Y.; Shao, Z.; Yang, X.; Qian, H.; Wang, C.-X. FEMOS: Fog-enabled multitier operations scheduling in dynamic wireless networks. IEEE Internet Things J. 2018, 5, 1169–1183. [Google Scholar] [CrossRef]
- Wadhwa, H.; Aron, R. Optimized task scheduling and preemption for distributed resource management in fog-assisted IoT environment. J. Supercomput. 2023, 79, 2212–2250. [Google Scholar] [CrossRef]
- Cheng, B.; Solmaz, G.; Cirillo, F.; Kovacs, E.; Terasawa, K.; Kitazawa, A. FogFlow: Easy programming of IoT services over cloud and edges for smart cities. IEEE Internet Things J. 2017, 5, 696–707. [Google Scholar] [CrossRef]
- Carnero, A.; Martín, C.; Torres, D.R.; Garrido, D.; Díaz, M.; Rubio, B. Managing and deploying distributed and deep neural models through Kafka-ML in the cloud-to-things continuum. IEEE Access 2021, 9, 125478–125495. [Google Scholar] [CrossRef]
- Nguyen, N.D.; Phan, L.A.; Park, D.H.; Kim, S.; Kim, T. ElasticFog: Elastic resource provisioning in container-based fog computing. IEEE Access 2020, 8, 183879–183890. [Google Scholar] [CrossRef]
- Zhou, Z.; Chen, X.; Liao, H.; Gan, Z.; Xiao, F.; Tu, Q.; Sun, W. Collaborative learning-based network resource scheduling and route management for multi-mode green iot. IEEE Trans. Green Commun. Netw. 2022, 7, 928–939. [Google Scholar] [CrossRef]
- Lin, K.; Gao, J.; Han, G.; Wang, H.; Li, C. Intelligent blockchain-enabled adaptive collaborative resource scheduling in large-scale industrial internet of things. IEEE Trans. Ind. Inform. 2022, 18, 9196–9205. [Google Scholar] [CrossRef]
- Zhang, Q.; Meng, H.; Feng, Z.; Han, Z. Resource Scheduling of Time-Sensitive Services for B5G/6G Connected Automated Vehicles. IEEE Internet Things J. 2022, 2022, 3224927. [Google Scholar] [CrossRef]
- Polyanskiy, Y.; Poor, H.V.; Verdú, S. Channel coding rate in the finite blocklength regime. IEEE Trans. Inf. Theory 2010, 56, 2307–2359. [Google Scholar] [CrossRef]
- Liang, L.; Ye, H.; Li, G.Y. Spectrum sharing in vehicular networks based on multi-agent reinforcement learning. IEEE J. Sel. Areas Commun. 2019, 37, 2282–2292. [Google Scholar] [CrossRef] [Green Version]




| Parameter | Value |
|---|---|
| Number of URLLC links | 4 |
| Number of mMTC links | 4 |
| Carrier frequency | 2 GHz |
| Bandwidth | 4 MHz |
| F-AP antenna gain | 8 dBi |
| F-AP receiver noise coefficient | 3 dB |
| AIoT devices antenna gain | 1 dBi |
| AIoT devices receiver noise coefficient | 5 dB |
| mMTC link power | [50, 100, 150, 200] mW |
| URLLC link power | 200 mW |
| Noise power | −114 dBm |
| mMTC business volume | 1024 bytes |
| mMTC limitation of service transmission delay | 100 ms |
| URLLC limitation of service transmission delay | 1 ms [b] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, S.; Yan, Y.; Ji, Y.; Peng, W.; Wan, L.; Zhang, P. Hybrid Services Collaborative Resource Scheduling Strategy towards Artificial Intelligence of Things. Appl. Sci. 2023, 13, 7956. https://doi.org/10.3390/app13137956
Li S, Yan Y, Ji Y, Peng W, Wan L, Zhang P. Hybrid Services Collaborative Resource Scheduling Strategy towards Artificial Intelligence of Things. Applied Sciences. 2023; 13(13):7956. https://doi.org/10.3390/app13137956
Chicago/Turabian StyleLi, Songnong, Yao Yan, Yongliang Ji, Wenxin Peng, Lingyun Wan, and Puning Zhang. 2023. "Hybrid Services Collaborative Resource Scheduling Strategy towards Artificial Intelligence of Things" Applied Sciences 13, no. 13: 7956. https://doi.org/10.3390/app13137956
APA StyleLi, S., Yan, Y., Ji, Y., Peng, W., Wan, L., & Zhang, P. (2023). Hybrid Services Collaborative Resource Scheduling Strategy towards Artificial Intelligence of Things. Applied Sciences, 13(13), 7956. https://doi.org/10.3390/app13137956





