Built Environment Cybersecurity: Development and Validation of a Semantically Defined Access Management Framework on a University Case Study
Abstract
:1. Introduction
2. Background and Related Work
- (1)
- Extend BIM specifications to satisfy IoT requirements.
- (2)
- Improve BIM standards so as to promote the provision of effective cybersecurity.
- (3)
- Ensure that effective support for cybersecurity and the IoT is incorporated into digital twin and future city standards.
- (4)
- Thoroughly combine cybersecurity concepts with the prevailing built environment data standards.
3. Methodology
- (1)
- Define the concept of an access management framework for the built environment. It is our view that semantics must be utilised here to provide the formalised management of access management concepts for the built environment which can then, in turn, enable the wide range of tools and standards utilised in the built environment to be applied in an interoperable manner, thereby making it possible to make use of the defines access management concepts (see Section 4).
- (2)
- Eliciting the formal specification of the framework using the NeOn methodology (Section 5).
- (3)
- Development of the semantic access management framework in smart cities using both new and existing ontological resources (Section 5.2).
- (4)
- Validation of the framework whereby the ontology is applied in a use case via the CUSP platform [2]. This entailed the integration of the ontology and access management framework on the available platform so that a range of case studies could be applied to validate the framework. The results confirmed the ability of the ontology to function as intended in a digital twin setting, offering single sign-on and suitable access control [20] (see Section 6). The decision was taken to apply the NeOn approach for the second step owing to the fact that the supporting documentation was available, it offered a scenario-based approach and because of the available knowledge [21]. Consequently, digital twin access management for a built environment ontology was achieved using the NeOn approach [21,22]. More specifically, this entails the application of a four-phases process:
- Phase 2 (Re-use phase): The second phase involves analysing the available ontological resources to establish the ways in which they can be redeployed in the ontology that is devised. As part of this process, the semantic resources currently available in the access management and built environment domains will be factored in (see Section 5.2). In addition, there is an assessment of the resources that are non-ontological, enabling them to be formalised and re-engineered in a way that brings them into line with the ontological resources that are already in place. This second phase was undertaken for both case studies utilised to establish the requirements Section 5.3). The main purpose of this investigation is to establish the concepts and terminologies which will contribute to the ontology.
- Phase 3 (Design): The third phase involves developing the final ontology with reference to the specified requirements as well as the re-engineering of the non-ontological and ontological resources (described in Section 6).
- Phase 4 (Implementation): The developed ontology will be implemented and validated on a digital twin case study within the university buildings (described in Section 6.2).
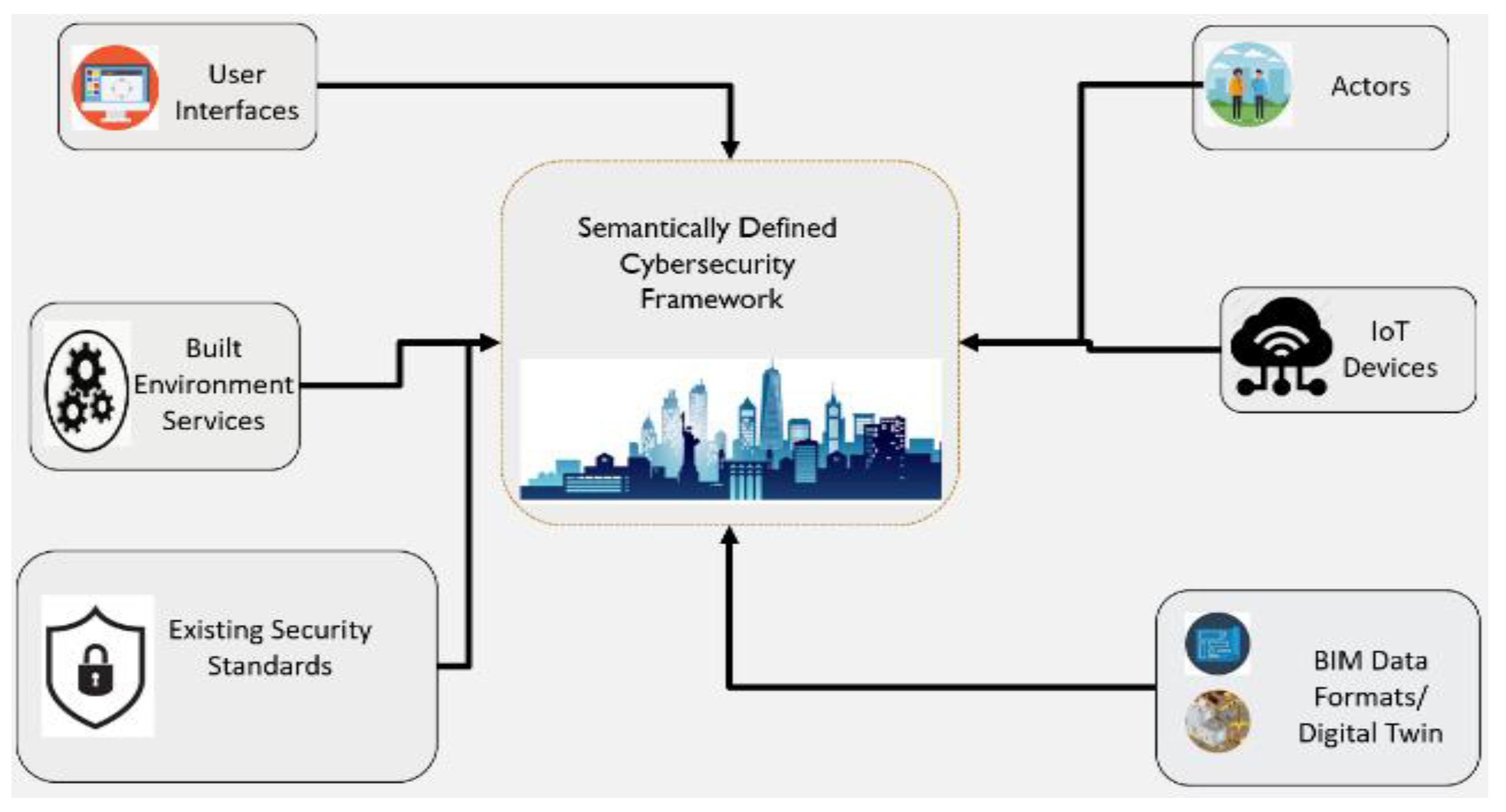
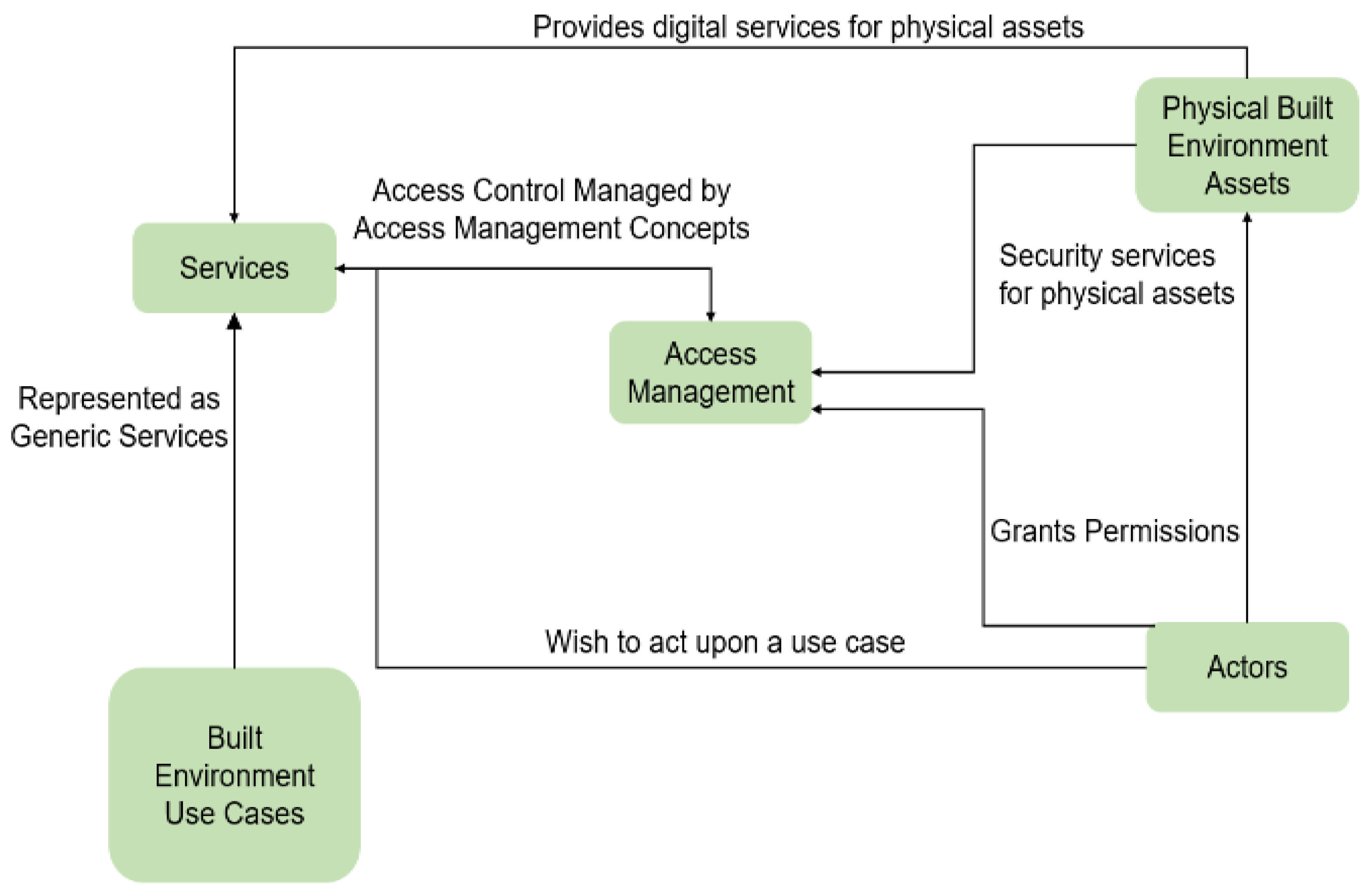
4. Semantically Defined Access Management Framework in Smart Cities
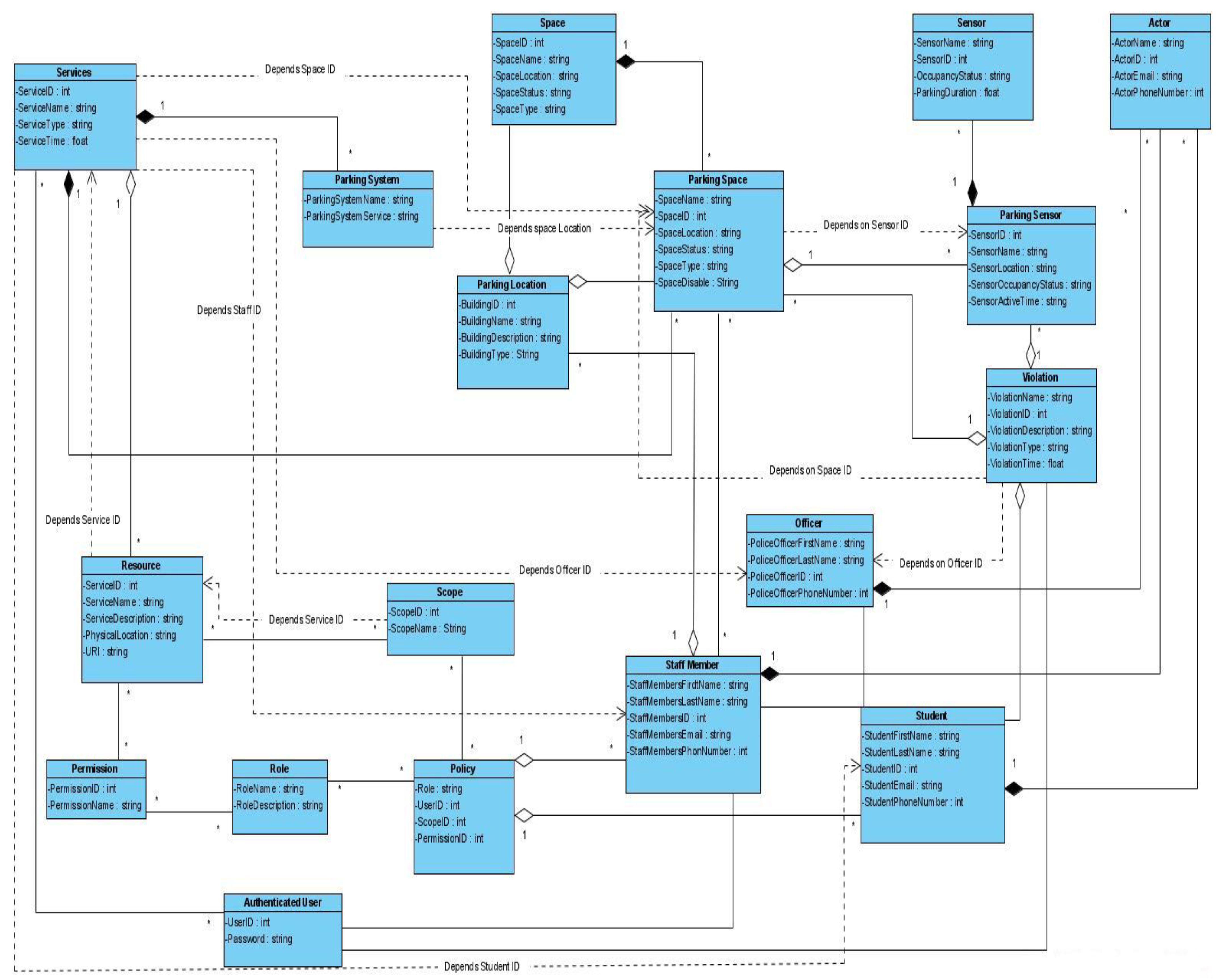
5. Ontology Access Management Framework Development
5.1. Re-Engineering of Built Environment Non-Ontological Resources
5.2. Analysis of Existing Ontological Resources
5.3. Existing Built Environment Ontological Resources
5.4. Sensing Resources
5.5. Urban Object Resources
5.6. Existing Security-Focused Resources
6. Validating an Access Management Ontology for Built Environment Cyber Physical System
6.1. Competency Questions
- IoT devices group questions contain six questions;
- Built environment data format questions contain nine questions;
- Actors’ questions contain seven questions;
- Built environment services questions contain eight questions;
- Security standards questions contain twelve questions.
6.2. Validation on a University Building
- An ontology of the set of surrounding buildings was generated from Open Street Map.
- Ontologies of the university buildings were generated by converting existing IFC models into ifcOWL using commonly available tools.
- Additional data were added manually (extracted from paper-based records) to represent cyber security related information and other metadata that were not present in the BIM datasets.
- (1)
- The ontology will, indeed, be validated to ensure that it sufficiently represents the security needs of the use case chosen.
- (2)
- The ontology will be validated to ensure that it accurately assigns and provides access rights to built-environment services.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Darif, A.; Chaibi, H.; Saadane, R. Energy optimization of SWIMAC for WSN based on IR-UWB in smart cities by using network coding. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–5. [Google Scholar]
- Kuster, C.; Hippolyte, J.-L.; Rezgui, Y. The UDSA ontology: An ontology to support real time urban sustainability assessment. Adv. Eng. Softw. 2020, 140, 102731. [Google Scholar]
- Howell, S.; Rezgui, Y. Beyond BIM: Knowledge Management for a Smarter Future; BRE Electronic Publications: London, UK, 2018. [Google Scholar]
- Hashem, I.A.T.; Chang, V.; Anuar, N.B.; Adewole, K.; Yaqoob, I.; Gani, A.; Ahmed, E.; Chiroma, H. The role of big data in smart city. Int. J. Inf. Man. 2016, 36, 748–758. [Google Scholar]
- Contreras, F.R.; Pastor, J.Á.; Losilla, F. A Domain Specific Language for Smart Cities. Proceedings 2018, 2, 148. [Google Scholar]
- Rawat, D.B.; Bajracharya, C. Cyber security for smart grid systems: Status, challenges and perspectives. In Proceedings of the SoutheastCon 2015, Fort Lauderdale, FL, USA, 9–12 April 2015. [Google Scholar]
- Demertzis, K.; Iliadis, L.S.; Anezakis, V.-D. An innovative soft computing system for smart energy grids cybersecurity. Adv. Build. Energy Res. 2018, 12, 3–24. [Google Scholar] [CrossRef]
- Alshammari, K. Access Management for Digital Twins in the Built Environment. Ph.D. Dissertation, School of Engineering. Cardiff University, Cardiff, UK, 2022. [Google Scholar]
- Alshammari, K.; Beach, T.; Rezgui, Y. Cybersecurity for digital twins in the built environment: Current research and future directions. J. Inf. Technol. Constr. 2021, 26, 159–173. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad. Hoc. Netw. 2012, 10, 1497–1516. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Alelwani, R.; Ahmad, M.; Rezgui, Y.; Kwan, A. Rawshan: Environmental Impact of a Vernacular Shading Building Element in Hot Humid Climates. In Proceedings of the 2019 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Valbonne, France, 17–19 June 2019; pp. 1–6. [Google Scholar]
- Ahmad, M.W.; Mourshed, M.; Yuce, B.; Rezgui, Y. Computational intelligence techniques for HVAC systems: A review. In Building Simulation; Springer: Berlin/Heidelberg, Germany, 2016; pp. 359–398. [Google Scholar]
- Rezgui, Y.; Miles, J. Exploring the potential of SME alliances in the construction sector. J. Constr. Eng. Manag. 2010, 136, 558–567. [Google Scholar] [CrossRef]
- Shin, D.-H. Ubiquitous city: Urban technologies, urban infrastructure and urban informatics. J. Inf. Sci. 2009, 35, 515–526. [Google Scholar]
- Steinmetz, C.; Rettberg, A.; Ribeiro, F.G.C.; Schroeder, G.; Pereira, C.E. Internet of things ontology for digital twin in cyber physical systems. In Proceedings of the 2018 VIII Brazilian Symposium on Computing Systems Engineering (SBESC), Salvador, Brazil, 6–9 November 2018; pp. 154–159. [Google Scholar]
- Eckhart, M.; Ekelhart, A. Towards security-aware virtual environments for digital twins. In Proceedings of the 4th ACM Workshop on Cyber-Physical System Security, Incheon, Republic of Korea, 4–8 June 2018; pp. 61–72. [Google Scholar]
- Lezzi, M.; Lazoi, M.; Corallo, A. Cybersecurity for Industry 4.0 in the current literature: A reference framework. Comput. Ind. 2018, 103, 97–110. [Google Scholar] [CrossRef]
- Corallo, A.; Lazoi, M.; Lezzi, M. Cybersecurity in the context of industry 4.0: A structured classification of critical assets and business impacts. Comput. Ind. 2020, 114, 103165. [Google Scholar] [CrossRef]
- Vajpayee, A.; Ramachandran, K. Reconnoitring artificial intelligence in knowledge management. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 114–117. [Google Scholar]
- Suárez-Figueroa, M.; Gómez-Pérez, A.; Fernández-López, M. The NeOn methodology framework: A scenario-based methodology for ontology development. Appl. Ontol. 2015, 10, 107–145. [Google Scholar] [CrossRef]
- Hou, S. An Ontology-Based Holistic Approach for Multi-Objective Sustainable Structural Design; Cardiff University: Cardiff, UK, 2015. [Google Scholar]
- Alshammari, K.; Beach, T.; Rezgui, Y. Industry engagement for identification of cybersecurity needs practices for digital twins. In Proceedings of the 2021 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Cardiff, UK, 21–23 June 2021; pp. 1–7. [Google Scholar]
- Howell, S.; Beach, T.; Rezgui, Y. Robust requirements gathering for ontologies in smart water systems. Requir. Eng. 2021, 26, 97–114. [Google Scholar] [CrossRef]
- Tapia-Leon, M.; Santana-Perez, I.; Poveda-Villalón, M.; Espinoza-Arias, P.; Chicaiza, J.; Corcho, O. Extension of the BiDO ontology to represent scientific production. In Proceedings of the 2019 8th International Conference on Educational and Information Technology, Yantai, China, 10–11 August 2019; pp. 166–172. [Google Scholar]
- Hippolyte, J.-L.; Rezgui, Y.; Li, H.; Jayan, B.; Howell, S. Ontology-driven development of web services to support district energy applications. Autom. Constr. 2018, 86, 210–225. [Google Scholar] [CrossRef] [Green Version]
- Chun, S.; Jung, J.; Jin, X.; Seo, S.; Lee, K.-H. Designing an integrated knowledge graph for smart energy services. J. Supercomput. 2020, 76, 8058–8085. [Google Scholar] [CrossRef]
- Beetham, I.F.; Enoch, M.P.; Tuuli, M.M.; Davison, L.J. Stakeholder perspectives on the value of car parking. Urban Plan. Transp. Res. 2014, 2, 195–214. [Google Scholar] [CrossRef] [Green Version]
- Gray, J.A.; Zimmerman, J.L.; Rimmer, J.H. Built environment instruments for walkability, bikeability, and recreation: Disability and universal design relevant? Disabil. Health J. 2012, 5, 87–101. [Google Scholar] [CrossRef]
- Anumba, C.J.; Roofigari-Esfahan, N. Cyber-Physical Systems in the Built Environment; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Górka, M. Cybersecurity Politics-Conceptualization of the Idea. Polish Pol. Sci. YB 2021, 50, 71. [Google Scholar] [CrossRef]
- Rivadeneira, W.F.B.; Gómez, O.S. Cybersecurity Ontologies: A Systematic Literature Review, ReCIBE. Revista electrónica de Computación. Inf. Biomédica Y Electrónica 2020, 9, 1–18. [Google Scholar]
- Jiang, L.; Kuhn, W.; Yue, P. An interoperable approach for Sensor Web provenance. In Proceedings of the 2017 6th International Conference on Agro-Geoinformatics, Fairfax, VA, USA, 7–10 August 2017; pp. 1–6. [Google Scholar]
- Cox, S.J. Ontology for observations and sampling features, with alignments to existing models. Semant. Web 2017, 8, 453–470. [Google Scholar] [CrossRef]
- Pal, S.; Mishra, S.K.; Rath, C.K.; Debnath, N.C.; Sarkar, A. Enrichment of Semantic Sensor Network Ontology: Description Logics based approach. In Proceedings of the 2020 IEEE International Conference on Industrial Technology (ICIT), Buenos Aires, Argentina, 26–28 February 2020; pp. 995–1000. [Google Scholar]
- de Roode, M.; Fernández-Izquierdo, A.; Daniele, L.; Poveda-Villalón, M.; García-Castro, R. SAREF4INMA: A SAREF extension for the industry and manufacturing domain. Semant. Web 2020, 11, 911–926. [Google Scholar] [CrossRef]
- Haller, A.; Janowicz, K.; Cox, S.; Lefrançois, M.; Taylor, K.; Le Phuoc, D.; Stadler, C. The SOSA/SSN ontology: A joint WeC and OGC standard specifying the semantics of sensors observations actuation and sampling. Semant. Web 2018, 1, 1–19. [Google Scholar]
- Petrova-Antonova, D.; Ilieva, S. Digital twin modeling of smart cities. In Proceedings of the International Conference on Human Interaction and Emerging Technologies, Virtual, 27–29 August 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 384–390. [Google Scholar]
- Pauwels, P.; Krijnen, T.; Terkaj, W.; Beetz, J. Enhancing the ifcOWL ontology with an alternative representation for geometric data. Autom. Constr. 2017, 80, 77–94. [Google Scholar] [CrossRef] [Green Version]
- Pauwels, P.; Roxin, A. SimpleBIM: From full ifcOWL graphs to simplified building graphs. In eWork and eBusiness in Architecture, Engineering and Construction; CRC Press: Boca Raton, FL, USA, 2017; pp. 11–18. [Google Scholar]
- Pauwels, P.; Zhang, S.; Lee, Y.-C. Semanticweb technologies in AEC industry: A literature overview. Autom. Constr. 2017, 73, 145–165. [Google Scholar] [CrossRef]
- Tarasov, V.; Seigerroth, U.; Sandkuhl, K. Ontology development strategies in industrial contexts. In International Conference on Business Information Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 156–167. [Google Scholar]
- Burov, Y.; Mykich, K.; Karpov, I. Intelligent systems based on ontology representation transformations. In Conference on Computer Science and Information Technologies; Springer: Berlin/Heidelberg, Germany, 2021; pp. 263–275. [Google Scholar]
| City | District | Street | Building |
|---|---|---|---|
|
|
|
|
| Case study 1: Smart Parking System Access Control | |
| Data Description | Notes |
| The number of parking floors available | The system administrator can configure the number of parking floors. The location’s space determines the spot number, and the system administration adds entrance/exit time data based on the organization’s operating hours. For instance, there are two parking levels, each with 12 spaces. From 8:00 a.m. to 8:00 p.m., parking spaces are accessible. On each floor, the user can locate a parking space that is open and pay for it hourly. The system administration will change the parking system to make those spaces appear to users as unavailable parking spots when the floor or parking spots are undergoing maintenance work. |
| Case study 2: Attendance Management System Access Control | |
| information about the students (who is available in the system) | A new student may be added by the system administrator based on the student’s schedule. |
| User | Roles Given to User |
|---|---|
| Ahmed (CU Staffmember) | Displaying University Parking Violation |
| Reserve University Parking | |
| Displaying University Parking Violation | |
| Attendance Recording | |
| Reserve University Parking | |
| Sara (CU Student) | Reserve University Parking |
| Displaying University Parking Violation | |
| Khaled (CU Campus Police Officer) | Record and Display University Parking Violations |
| Alan (General User) | Not allowed to use digital twin services |
| Rayan (General User) | Not allowed to use digital twin services |
| Policy Content | Policies | Permissions Assigned | Relevant Service |
|---|---|---|---|
| Allow Staff to Reserve University Parking | Allow if Role = “StaffMember” | Make reservation | Reserve Parking Space |
| Allow Police Officer to Record and Display University Parking Violations | Allow if Role = “Campus Police Officer” | Record Violation | Record Violation |
| Allow Staff to Displaying University Parking Violation | Allow if Role = “StaffMember” | Display Violation | Display Violation |
| Allow Student Attendance Recording | Allow if Role = “Student” | Attendance Management | Attendance Management |
| Users | Reserve Parking Space | Record Parking Violation | Display Parking Violation | Attendance Recorded |
|---|---|---|---|---|
| Ahmed | Yes, user is granted access | No, user isn’t granted access | Yes, user is granted access | No, user isn’t granted access |
| Sara | Yes, user is granted access | No, user isn’t granted access | Yes, user is granted access | Yes, user is granted access |
| Khaled | No, user isn’t granted access | Yes, user is granted access | Yes, user is granted access | No, user isn’t granted access |
| Alan | No, user isn’t granted access | No, user isn’t granted access | No, user isn’t granted access | No, user isn’t granted access |
| Rayan | No, user isn’t granted access | No, user isn’t granted access | No, user isn’t granted access | No, user isn’t granted access |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alshammari, K.; Beach, T.; Rezgui, Y.; Alelwani, R. Built Environment Cybersecurity: Development and Validation of a Semantically Defined Access Management Framework on a University Case Study. Appl. Sci. 2023, 13, 7518. https://doi.org/10.3390/app13137518
Alshammari K, Beach T, Rezgui Y, Alelwani R. Built Environment Cybersecurity: Development and Validation of a Semantically Defined Access Management Framework on a University Case Study. Applied Sciences. 2023; 13(13):7518. https://doi.org/10.3390/app13137518
Chicago/Turabian StyleAlshammari, Kaznah, Thomas Beach, Yacine Rezgui, and Raed Alelwani. 2023. "Built Environment Cybersecurity: Development and Validation of a Semantically Defined Access Management Framework on a University Case Study" Applied Sciences 13, no. 13: 7518. https://doi.org/10.3390/app13137518
APA StyleAlshammari, K., Beach, T., Rezgui, Y., & Alelwani, R. (2023). Built Environment Cybersecurity: Development and Validation of a Semantically Defined Access Management Framework on a University Case Study. Applied Sciences, 13(13), 7518. https://doi.org/10.3390/app13137518







