A Secure Communication Method Based on Message Hash Chain
Abstract
:1. Introduction
Contributions
- 1.
- The MHC method adopts a new chain transmission method to ensure the non-tampering, non-repudiation, and higher reliability requirements of multiple messages. The main idea is to iteratively hash the digest of the transmitted message to form a hash chain about the message sequence. The two communicating parties can ensure the integrity, immutability, and synchronization of the message sequence through the hash chain, thereby effectively guaranteeing the security of message transmission.
- 2.
- When performing data signature and authentication, both parties only need to perform signature authentication on messages at certain intervals and do not need to complete it on each message. In this way, the authenticity and non-repudiation of all previously transmitted messages can be ensured, the overhead of signature authentication is reduced, and the efficiency of secure message transmission is greatly improved.
- 3.
- Using the sequence number and node value of the message hash chain of the MHC method can provide anti-protection against replays and ensure reliability.
2. Related Works
3. Chain Communication Model
3.1. Notation and Meaning
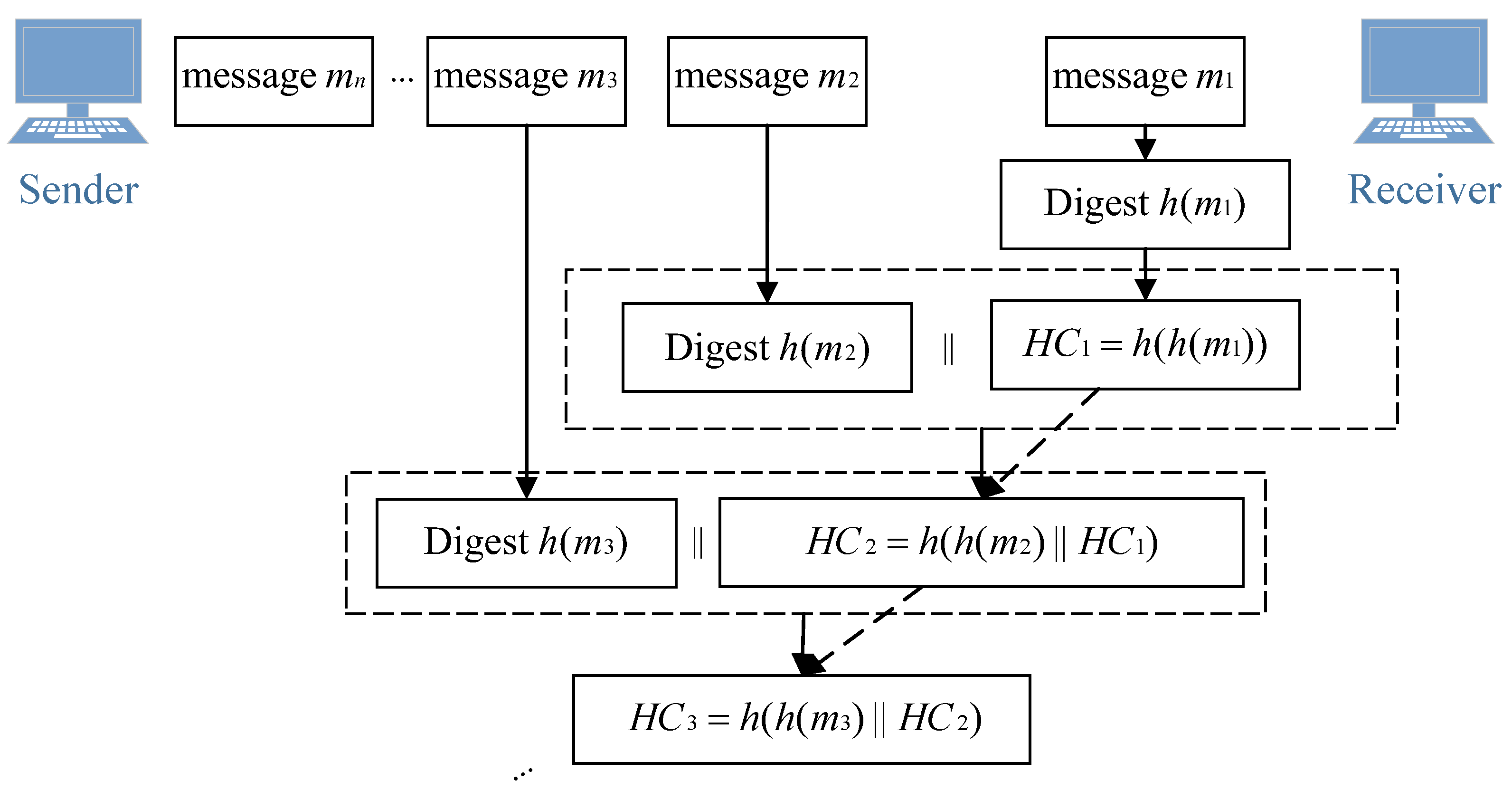
3.2. Message Hash Chain Communication Model
- The sender first determines the (source address), (destination address), and (other fields of the header) of the sent message, and then the header information can be obtained. The expression of the message that the sender needs to send in the MHC method iswhere is the payload of . The sender needs to obtain the message hash chain from to locally and record the message hash chain as . According to the and the tail node of the message hash chain, the latest node of the message hash chain is constructed, i.e., the node value of message hash chain corresponding to the message . At the same time, is updated to the intermediate node of this message hash chain, and is updated to the tail node of the chain of this message hash chain. The sender sends the message to the receiver according to , where is the sequence.
- After receiving the , the receiver verifies the node value of the message hash chain. Record the receiver’s message hash chain as . The receiver calculates a node value to be verified in the message hash chain between and through the construction method of the message hash chain, where is the tail node of the message hash chain constructed by the receiver. Next, the receiver verifies whether holds. If so, the The receiver’s verification of ends successfully and updates to the intermediate node of the message hash chain and to the tail node of the message hash chain. Otherwise, the receiver’s verification of is unsuccessful and must to discard the and report an error.
3.3. Message Structure
4. Construction Method of Message Hash Chain
- : The role of the function is to obtain the source and destination addresses from the message header.
- : Match the message hash chain between two addresses.
| Algorithm 1HC_Iteration |
Input: Header content, payload, node value of the message hash chain. Output: A new node value of the chain.
|
| Algorithm 2 The construction process of the message hash chain |
|
5. Chain Synchronization
5.1. Sequence Number
5.2. Chain Synchronization Mechanism
5.2.1. General Chain Synchronization Mechanism
5.2.2. Chain Synchronization Mechanism Based on Signature Confirmation
6. Chain Signature
6.1. Chain Signature Process
- : Current signature interval.
- : A signature is required when the sender’s signature interval reaches .
- : The function that encapsulates parameters as header of message hash chain.
- : The signature function described in Section 7.
- : Sender’s private key.
| Algorithm 3 Message Hash Chain Encapsulates Messages Header |
Input: Header content, signature interval, payload. Output: Encapsulated MHC datagram.
|
6.2. Chain Authentication Process
- : Sequence number counter.
- : Sender’s public key.
- : Message hash chain node value used for verification.
| Algorithm 4 The Receiver Verifying The Received Messages |
Input: Messages. Output: Verification status.
|
7. Safety Analysis
- represents the asymmetric key generation algorithm. For the key pair , is the private key of the signature, and is the public key of the signature.
- is the signature algorithm of the digital signature scheme. For the communication transmission sequence , there is on a certain segment of data transmitted, where q is a positive integer, and come from .
- is the verification algorithm of the digital signature scheme. For the digital signature of a certain segment of data and the generated by , there is always .
- is the construction algorithm of the message hash chain. For the transmission sequence , there is = , where come from , respectively.
- After receiving the sequence and the encapsulated in it, the receiver also constructs a message hash chain node = for the received sequence through , and there is , , .
- . Obviously if , where h is a non-collision hash function, then is obtained. Next, algorithm can output the message hash chain sequenceand finally get . If there should be , but , it means that algorithm can forge digital signature scheme. However, it obviously contradicts the assumption that is a secure digital signature scheme.
- . Knowing that , there must be that can recursively get . For the message hash chains and digital signatures at both sides of the transmission corresponding to , they satisfy the relational expressions and . If , then the receiver can use the message hash chain to verify the authenticity and non-repudiation of , and then use the message hash chain to verify the authenticity and non-repudiation of in a recursive way, which contradicts the null hypothesis.
8. Reliability Analysis
8.1. Packet Loss Retransmission
- At least, there is a possibility that it is greater than , and the P received by B arrives in order, then the message hash chain constructed by B through P satisfies .
- At least, there is a possibility that it is greater than , and the data stream received by B may arrive out of sequence or lose packets. Assume that at a certain time , the sequence number corresponding to the sender’s tail node is , and the sequence number corresponding to the tail node used by the receiver for verification is , . At this time, if the sender sends a new message to reach B, and its corresponding sequence number , then set the message retention time for . Subsequently, at time , where , if the message hash chain of the has not been successfully verified, the will be discarded, and the sender will request the following message corresponding to the sequence number of the current tail node of the chain. In contrast, if the chain of the can be successfully verified and the corresponding message hash chain is constructed at the receiver, the verification of the message corresponding to the last sequence number is continued.
8.2. Error Detection and Correction
9. Efficiency Analysis
9.1. Experimental Environment
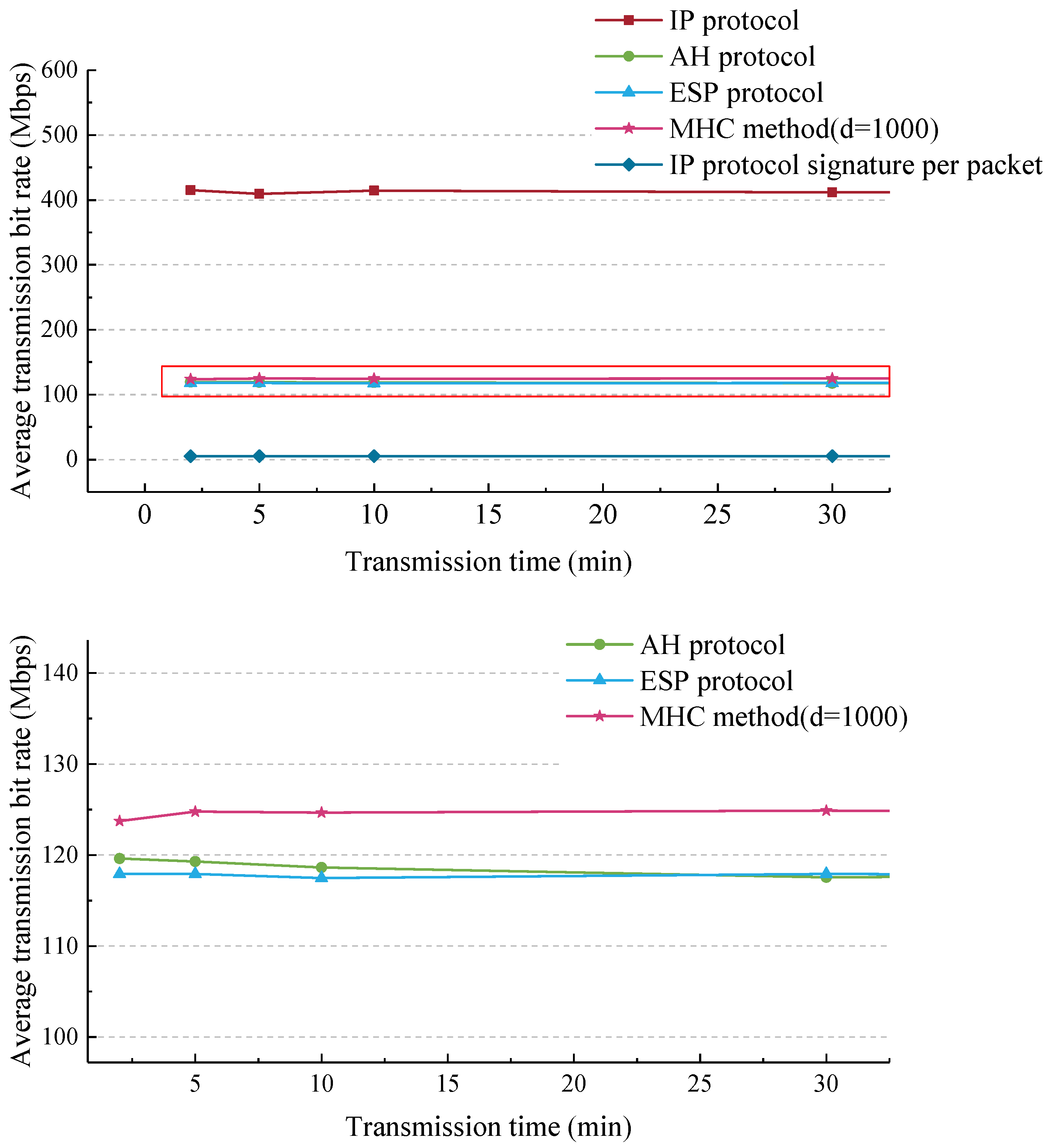
9.2. Efficiency Comparison of Several Communication Methods
9.3. Comparison and Analysis of Security Properties of Several Existing Schemes
10. Conclusions
Author Contributions
Funding
Funding
Data Availability Statement
Conflicts of Interest
References
- IP Security (IPsec) and Internet Key Exchange (IKE). Available online: https://www.rfc-editor.org/rfc/rfc6071 (accessed on 1 January 2020).
- Dennis, F.; Martin, G.; Jörg, S.; Adam, C.; Marcin, S. The Dangers of Key Reuse: Practical Attacks on IPsec IKE. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 567–583. [Google Scholar]
- Kenneth, G.P. A Cryptographic Tour of the IPsec Standards. Inf. Secur. Tech. Rep. 2006, 10, 72–81. [Google Scholar]
- Zhao, E.; Xiong, G. Reflective Denial-of-Service based on IKEv2 Protocol. Commun. Technol. 2019, 52, 144–148. [Google Scholar]
- IP Authentication Header. Available online: https://www.rfc-editor.org/rfc/rfc4302 (accessed on 1 January 2020).
- IP Encapsulating Security Payload (ESP). Available online: https://www.rfc-editor.org/rfc/rfc4303 (accessed on 1 January 2020).
- Geetanjali, R.; Ashutosh, S.; Rajiv, K.; Farhan, A.; Razi, I. A trust management scheme to secure mobile information centric networks. Comput. Commun. 2020, 151, 66–75. [Google Scholar]
- Adnan, M.; Quan, Z.S.; Sarah, A.S.; Subhash, S.; Wei, E.Z.; Hajime, S.; Wei, N. When Trust Meets the Internet of Vehicles: Opportunities, Challenges, and Future Prospects. In Proceedings of the IEEE 7th International Conference on Collaboration and Internet Computing, Atlanta, GA, USA, 13–15 December 2021; pp. 60–67. [Google Scholar]
- Adnan, M.; Sarah, A.S.; Quan, Z.S.; Wei, E.Z.; Hajime, S.; Wei, N. Trust on wheels: Towards secure and resource efficient IoV networks. Computing 2022, 1–22. [Google Scholar] [CrossRef]
- Lamport, L. Password Authentication with Insecure Communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Chung, K.W.; Lam, S.S. Digital signatures for flows and multicasts. IEEE/ACM Trans. Netw. 1999, 7, 502–513. [Google Scholar] [CrossRef]
- Golle, P.; Modadugu, N. Authenticating Streamed Data in the Presence of Random Packet Loss. In Proceedings of the NDSS Symposium, San Diego, CA, USA, 8–9 February 2001. [Google Scholar]
- Liu, C. Research on Streaming Data Signature and Verification Based on Hash Chain. Ph.D. Thesis, Hunan University, Hunan, China, 2004. [Google Scholar]
- Zhang, Z.; Sun, Q.; Wong, L. A proposal of butterfly-graph based stream authentication over lossy networks. In Proceedings of the 2005 IEEE International Conference on Multimedia and Expo, Amsterdam, The Netherlans, 6–8 July 2005; p. 4. [Google Scholar]
- Miller, D. A Hash-Chain Based Method for Full or Partial Authentication of Communication in a Real-Time Wireless Environment. Master’s Thesis, University of Waterloo, Waterloo, ON, Canada, 2010. [Google Scholar]
- Liu, F. Security authentication protocol of Modbus/TCP based on hash chain and synchronization mechanism. Appl. Res. Comput. 2018, 35, 1169–1173, 1186. [Google Scholar]
- Huang, Q.; Huang, H.; Wang, W.; Li, Q.; Wu, Y. An Authentication Scheme Based on Novel Construction of Hash Chains for Smart Mobile Devices. Wirel. Commun. Mob. Comput. 2020, 2020, 8888679. [Google Scholar] [CrossRef]
- Zhang, H.; Zhu, Y. A Self-Updating Hash Chain Mechanism. Wuhan Univ. (Nat. Sci. Ed.) 2006, 52, 4–8. [Google Scholar]
- Li, B.; Hou, Y.; Zhao, Y. An Optimized Scheme for Multicast Packet Authentication. Comput. Eng. 2006, 32, 3. [Google Scholar]
- Hakeem, S.; El-Gawad, M.; Kim, H. Comparative Experiments of V2X Security Protocol Based on Hash Chain Cryptography. Sensors 2020, 20, 5719. [Google Scholar] [CrossRef] [PubMed]
- Hakeem, S.; El-Kader, S.; Kim, H. A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks. Sensors 2021, 21, 5838. [Google Scholar] [CrossRef] [PubMed]
- Huang, N.; Zhu, J.; Guo, C.; Cheng, S.; Li, X. A Novel Hash Chain-Based Data Availability Monitoring Method for Off-site Disaster Recovery Architecture. J. Circuits Syst. Comput. 2021, 6, 2150294. [Google Scholar] [CrossRef]
- Kim, D.; Seo, S.; Kim, H.; Lim, W.; Lee, Y. A Study on the Concept of Using Efficient Lightweight Hash Chain to Improve Authentication in VMF Military Standard. Appl. Sci. 2020, 24, 8999. [Google Scholar] [CrossRef]
- Luo, G.; Shi, M.; Zhao, C.; Shi, Z. Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs. Appl. Sci. 2020, 12, 4206. [Google Scholar] [CrossRef]
- Han, M.; Jiang, W.; Guo, Y. Signature and authentication method based on message hash chain. Appl. Res. Comput. 2021, 39, 1183–1189. [Google Scholar]


| Notation | Meaning |
|---|---|
| Cryptographic hash functions, . | |
| Concatenate string A with string B. | |
| The ith message of message transmission sequence. | |
| The ith node value of the message hash chain constructed by the sender is sent to the communication peer together with the payload and needs to be verified. | |
| The ith node value of the message hash chain constructed by the receiver is used to compare with the received message hash chain. | |
| The content of the ith message sent by the sender. | |
| The digital signature of . | |
| Key pair in the asymmetric digital signature. | |
| Based on its , the sender uses an asymmetric encryption algorithm to calculate the signature of . | |
| The receiver verifies the signature against the sender’s . If the value is 1, it means that the verification can be successful; otherwise, it means that the verification cannot be passed. |
| Serial Number | Transport Layer Protocol | Communication Mode | Payload Length of Each Message |
|---|---|---|---|
| 1 | TCP protocol | IP protocol | 1460 B |
| 2 | TCP protocol | Packet by packet signed IP protocol | 1372 B |
| 3 | TCP protocol | AH protocol | MTU-TCPH-IPH-AHH = 1436 B |
| 4 | TCP protocol | ESP protocol | MTU-TCPH-IPH-ESPH = 1436 B |
| 5 | TCP protocol | MHC method (signature interval 1000) | About 1420B without signature and about 1332 B with signature |
| Network Layer Communication Method | 2 min | 5 min | 10 min | 30 min | 60 min | |
|---|---|---|---|---|---|---|
| IP protocol | Million packets | 4.26 | 10.52 | 21.28 | 63.47 | 128.51 |
| Amount of data transmitted/Mb | 49,809.46 | 122,837.52 | 248,540.61 | 741,347.66 | 1,501,003.01 | |
| Throughout capacity/Mbps | 415.08 | 409.46 | 414.23 | 411.86 | 416.95 | |
| IP Packet signature | Million packets | 0.06 | 0.14 | 0.29 | 0.87 | 1.72 |
| Amount of data transmitted/Mb | 641.96 | 1579.89 | 3217.72 | 9574.15 | 18,903.31 | |
| Throughout capacity/Mbps | 5.35 | 5.27 | 5.36 | 5.32 | 5.25 | |
| AH protocol | Million packets | 1.25 | 3.12 | 6.2 | 18.42 | 36.98 |
| Amount of data transmitted/Mb | 14,354.48 | 35,786.94 | 71,181.33 | 211,615.71 | 424,800.51 | |
| Throughout capacity/Mbps | 119.62 | 119.29 | 118.64 | 117.56 | 118 | |
| ESP protocol | Million packets | 1.23 | 3.08 | 6.14 | 18.48 | 36.89 |
| Amount of data transmitted/Mb | 14,151.8 | 35,376.74 | 70,483.29 | 212,260.47 | 423,755.83 | |
| Throughout capacity/Mbps | 117.93 | 117.92 | 117.47 | 117.92 | 117.71 | |
| MHC method | Million packets | 1.31 | 3.3 | 6.58 | 19.79 | 39.45 |
| Amount of data transmitted/Mb | 14,849.35 | 37,430.08 | 74,798.15 | 224,780.88 | 448,085.5 | |
| Throughout capacity/Mbps | 123.74 | 124.77 | 124.66 | 124.88 | 124.47 | |
| Schemes and Configurations | Length of Transmitted Data | |||
|---|---|---|---|---|
| 1 GB | 5 GB | 10 GB | 50 GB | |
| The MHC method/signature interval is 1000 | 68.76 s | 337.47 s | 678.31 s | 3374.16 s |
| AH protocol/SA phase II life cycle is 2 min | 70.68 s | 358.53 s | 712.34 s | 3568.89 s |
| AH protocol/SA phase II life cycle is 5 min | 70.75 s | 353.60 s | 704.51 s | 3530.46 s |
| AH protocol/SA phase II life cycle is 10 min | 70.03 s | 351.51 s | 701.97 s | 3514.27 s |
| AH protocol/SA phase II life cycle is 60 min | 70.00 s | 351.58 s | 698.37 s | 3510.16 s |
| Scheme | Immutable | Integrity | Nonrepudiation | Reliability | Traceability | Synchronicity | Confidentiality | Efficiency |
|---|---|---|---|---|---|---|---|---|
| IP protocol | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | Highest |
| IP protocol with signature 1 | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | Lowest |
| AH protocol | ✓ | ✓ | ✗ | Higher | ✗ | ✗ | ✗ | Higher |
| ESP protocol | ✓ | ✓ | ✗ | Higher | ✗ | ✗ | ✓ | Higher |
| [11] | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | Medium |
| [12] | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | Higher |
| [13] | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | Medium |
| [15] | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | Lower |
| [16] | ✓ | ✓ | ✓ | Higher | ✗ | ✓ | ✓ | Low |
| MHC | ✓ | ✓ | ✓ | High | ✓ | ✓ | ✓ | Higher |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, M.; Jiang, W. A Secure Communication Method Based on Message Hash Chain. Appl. Sci. 2022, 12, 4505. https://doi.org/10.3390/app12094505
Han M, Jiang W. A Secure Communication Method Based on Message Hash Chain. Applied Sciences. 2022; 12(9):4505. https://doi.org/10.3390/app12094505
Chicago/Turabian StyleHan, Mingxuan, and Wenbao Jiang. 2022. "A Secure Communication Method Based on Message Hash Chain" Applied Sciences 12, no. 9: 4505. https://doi.org/10.3390/app12094505
APA StyleHan, M., & Jiang, W. (2022). A Secure Communication Method Based on Message Hash Chain. Applied Sciences, 12(9), 4505. https://doi.org/10.3390/app12094505






