Cyberattack Path Generation and Prioritisation for Securing Healthcare Systems
Abstract
:1. Introduction
2. Related Work
3. The Proposed Attack Path Discovery
3.1. Assumptions
- The assets within the healthcare ecosystem are dependent upon each other for the healthcare service delivery;
- Each asset may link with single or multiple confirmed vulnerabilities published by the National Vulnerability Database (NVD) or CVE, which are required to be considered for the attack path generation. CVE contains a huge list of published vulnerabilities that assist in determining vulnerabilities related to specific healthcare assets;
- The threat actor needs a certain profile in terms of attacker capability (knowledge and skill) and access vector (local, adjacent, network, and physical) to exploit a vulnerability and discover an attack path;
- Each user within the healthcare system performs certain functionalities based on the roles and responsibilities. Threat actors could take advantage of target user profiles to execute an attack;
- Each attack path includes several variables, such as entry point asset, intermediate point (if any), target point asset, dependencies among the assets, and underlying characteristics of the vulnerability within the assets;
- The methodology follows the CVSS for attack path generation and vulnerability estimation. It mainly considers the base score metric values for generating the attack path.
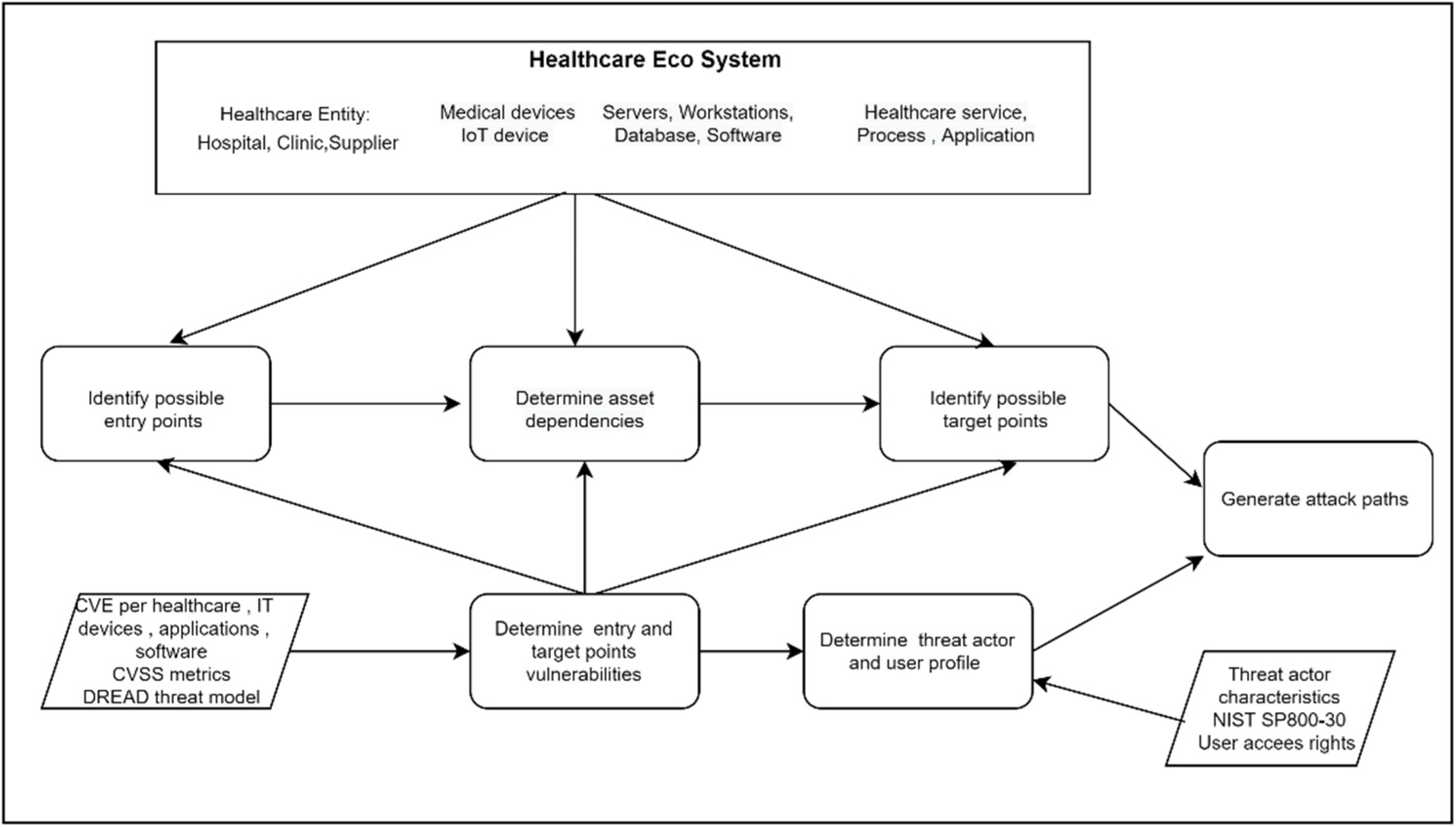
3.2. Cyberattack Path Generation and Analysis Process
4. Attack Path Generation Rules
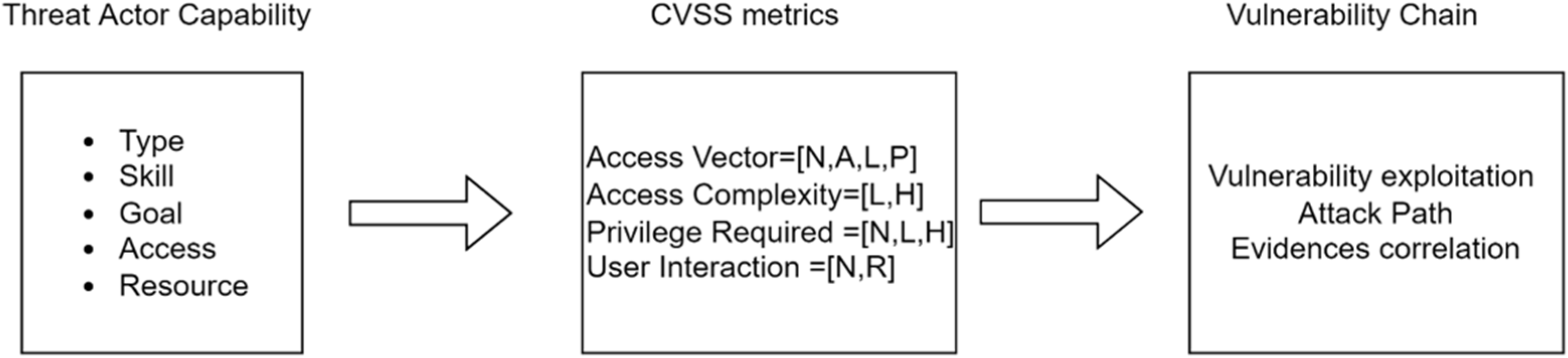
4.1. Variables
- Threat actor capability: Defines the attackers’ necessary skill, goals supplication, resources required to execute an attack. It includes five given scales (very low, low, moderate, high, and very high);
- Attack access vector: Define the necessary access path for an attack campaign. There are four different access vectors for executing an attack: Local—A vulnerability is exploitable with only local access; Adjacent—A vulnerability is exploitable with adjacent network access; Network—A vulnerability is exploitable with network access; Physical—A vulnerability is exploitable with physical access.
4.2. Knowledge Base
- Vul denotes Vulnerability which links with an asset;
- Asset denotes specific assets of the overall healthcare ecosystem and possible cyber dependencies with other assets including Hosting, ExchangingData, Storing, Controlling, Processing, Accessing, Installing, Trusted, Inclusion, Interaction, and Connected;
- TA and TAP denotes Threat Actor and Threat Actor Profile, respectively with capability VeryHigh, High, Moderate, Low, and VeryLow, threat require for an attack;
- AV denotes Access Vector with Local Network, Adjacent Network, Local and Physical;
- Vuln_PR denotes Privileged Required as a level of privileges, i.e., None, Low, and High, before successfully exploiting a vulnerability by a Threat Actor;
- Vuln_AC denotes Attack complexity in terms of certain conditions, i.e., Low and High, beyond the attacker’s control that must exist in order to exploit the attack;
- Vuln_UI denotes the user interaction, i.e., None and Required, excluding the threat actors for an attack;
- TUP denotes the Target User Profile, i.e., High, Medium, and Low, that assists an attacker to execute an attack;
- Vuln_Exp denotes vulnerability exploitability level, i.e., High, Medium, and Low, based on the exploitability properties;
- Vul_Exp_Fea denotes specific exploitability features of the vulnerability.
- ∀asset1,asset2 ExchangingData(asset1,asset2) ∨ Storing(asset1,asset2) ∨ Configuring(asset1,asset2) ∨ Updating(asset1,asset2) ∨ Accessing(asset1,asset2) ∨ Installing (asset1,asset2 ⇒ Connected (asset1,asset2) ∧ Connected(asset2,asset1)
- ∀vuln1,vuln2,asset1,asset2 Connected(vuln1,asset1, vuln2,asset2) ⇒ Connected (vuln2,asset2, vuln1,asset1)
- ∀vuln, asset,TA vuln_AV() ∧ TAP() ⇒ Accessible(vuln,asset,TA)
- ∀vuln,asset,TA Accessible(vuln,asset,TA) ∧ (vul_UI() ∨ vul_PR() ∨ vul_AC()) ∧ TAP() ⇒ Exploitable(vuln,asset,TA)
- ∀vuln,asset,TA Accessible(vuln,asset,TA) ∧ Exploitable(vuln,asset,TA) ⇒ Attacked(vuln,asset,TA)
4.3. Attack Path Generation
4.3.1. Rules Using Access Vector
- If AV is ‘Network’ (i.e., remotely exploitable), this means both asset and TA are connected to the same network (Internet).
- ∀vuln, asset,TA, locNetwork(TA,loc) ∧ ConnectsTo(asset,loc) ∧ Vulnerability(vuln,asset) ∧ Network(vuln) ⇒ Accessible(vuln,asset,TA).
- ∀vuln,asset,TA,loc AdjacentNetwork(TA,loc) ∧ ConnectsTo(asset,loc).
- ∧Vulnerability(vuln,asset) ∧ (AdjacentNetwork(vuln) ∨ Network(vuln)) ⇒ Accessible(vuln,asset,TA).
4.3.2. Rules Using Base Metrics
4.3.3. Access Vector and Privileges Required
- ∀vuln1,asset1,vuln2,asset2, TA(vuln1_AV(N) ∧ vuln1_PR(L)) ∧ (vuln2_AV(N) vuln2_PR(L)) ⇒ Accessible(vuln2,asset2,TA).
4.3.4. Target User Profile and User Interaction
- ∀vuln,asset,TA Vuln_UI(R) ∧ Vuln_TUP(L) ∧ TA_AC(VH or H) ⇒ Exploitable(vuln,asset,TA).
4.3.5. Threat Actor Profile and Attack Complexity
- ∀vuln,asset, TA Vuln_AC(H) ∧ Vuln_TAP(VH ∨ H) ⇒ Exploitable(vuln,asset,TA).
4.3.6. Rules Using Vulnerability Exploitability
4.3.7. Exploitability Level and Threat Actor Profile
- ∀vuln,asset,TA Accessible(vuln,asset,TA) ∧ Vuln_Exp(H) ∧ Vuln_TAP(VH ∨ H VM ∨ L ∨ VL) ⇒ Attacked(vuln,asset,TA).
4.3.8. Proof of Concept Exploit, Weaponized Exploit, Arbitrary Code Execution
- ∀vuln,asset, TA Vuln_Exp_Fea(PoC ExploitCode) ∧ Vuln_Exp_Fea(weaponized exploits) ∨ Vuln_Exp_Fea(arbitrary code execution) ⇒ Exploitable(vuln,asset,TA).
5. Evaluation: A Healthcare Scenario
5.1. Healthcare Use Case Scenario
5.2. Implementation of the Attack Path Generation
5.2.1. Identify Entry, Target Point Assets, and Possible Dependencies
- Infusion Pump (A1): Braun’s Infusion System 871305U aims to deliver fluid such as nutrients and medications into the patient’s body. Trained healthcare practitioners should program the rate and duration for the medication. The pump stores patient drug information;
- Insulin pump (A2): Medtronic MiniMed 508 is one of the most widely used pumps for delivering a specific amount of insulin to the diabetic patient’s body. The device is programmed to inject a specific amount of insulin set by the doctor into the patient body. The pump stores patient sensitive insulin information;
- Insulin management system (A3): Omnipod DASH Insulin Management System 19191 is a tubeless and wireless system that allows continuous insulin delivery for 3 days. It consists of a pod that is worn directly on the patient’s body and a personal diabetic manager which programs and controls the delivery;
- IoT devices (A4): There are several IoT devices that are relevant to the scenario. A heartrate monitor (Maxim’s 700-MAXREFDES117) can be used to monitor the heart rate (wearable device). Additionally, a smart light system (Philips) is also considered for the healthcare service delivery;
- Information and communication network (A5): This includes multiple devices, such as routers, WiFi, switches, wireless interface cards, and others that are responsible for the connection from the device to the network;
- Computer system (A6): Windows-based workstation and servers connected to the medical devices, patient interfaces and servers;
- Rugged tablets (A7): These tablets are commonly used for patient care applications such as medication alerts and tracking, Electronic Health Records (EHR) support, blood pressure monitoring, and connecting to barcode readers and can directly interface to the other medical equipment. Healthcare practitioners can directly use these tablets for patient treatment.
5.2.2. Information and Software
- Hospital information management system (A8): Care 2X software is a patient medical record and staff management system. It supports web-based platforms and a simple user interface. The patient medical record includes patients’ identifiable and treatment information;
- SpaceCom and SpaceStation (A9): This is the software that operates the infusion pump and resides either on the pump or the space station. Generally, the pump is attached to the space station. We have considered Braun’s Infusion System 871305U, which is linked with the SpaceCom 012U000050. SpaceCom is responsible to update two critical functions, i.e., drug library and pump configuration. Drug libraries can prevent incorrect dosing of drugs;
- Device usage information: This includes the amount of time used by the patient from the device and the relevant programme data.
5.2.3. Possible Asset Dependencies
5.2.4. Entry and Target Point Vulnerabilities
- two vulnerabilities are identified on asset A1;
- one vulnerability is identified on asset A2;
- one vulnerability is identified on asset A3;
- one vulnerability is identified on asset A4;
- three vulnerabilities are identified on asset A5;
- three vulnerabilities are identified on asset A6;
- one vulnerability is identified on asset A7;
- one vulnerability is identified on asset A8;
- two vulnerabilities are identified on asset A9.
5.2.5. Threat Actor and User Profile
- Infusion Pump: TA should have knowledge regarding the access to the local network, CAN bus data structure, escalation of privilege from user access to admin access and the pump configuration;
- Medtronic Insulin Pumps: Knowledge regarding how to access the network and intercept radio frequency and the pump configuration;
- Smart bulb: Knowledge of smart bulb operation and access point to overtake the bulb control.
5.3. Results: Attack Path Generation
- A5,V1 → A9,V1 → A1,V1
- A9,V2 → A1,V2
- A8,V1 → A9,V1 → A1,V2
- A4,V1 → A9,V1 → A1,V1
- A5,V3 → A3,V1 → A2,V1
- A3,V1 → A2,V1
- A4,V1 → A3,V1 → A2,V1
- A5,V3 → A6,V1 → A8,V1
- A5,V3 → A6,V2 → A8,V1
- A7,V1 → A6,V3 → A8,V1
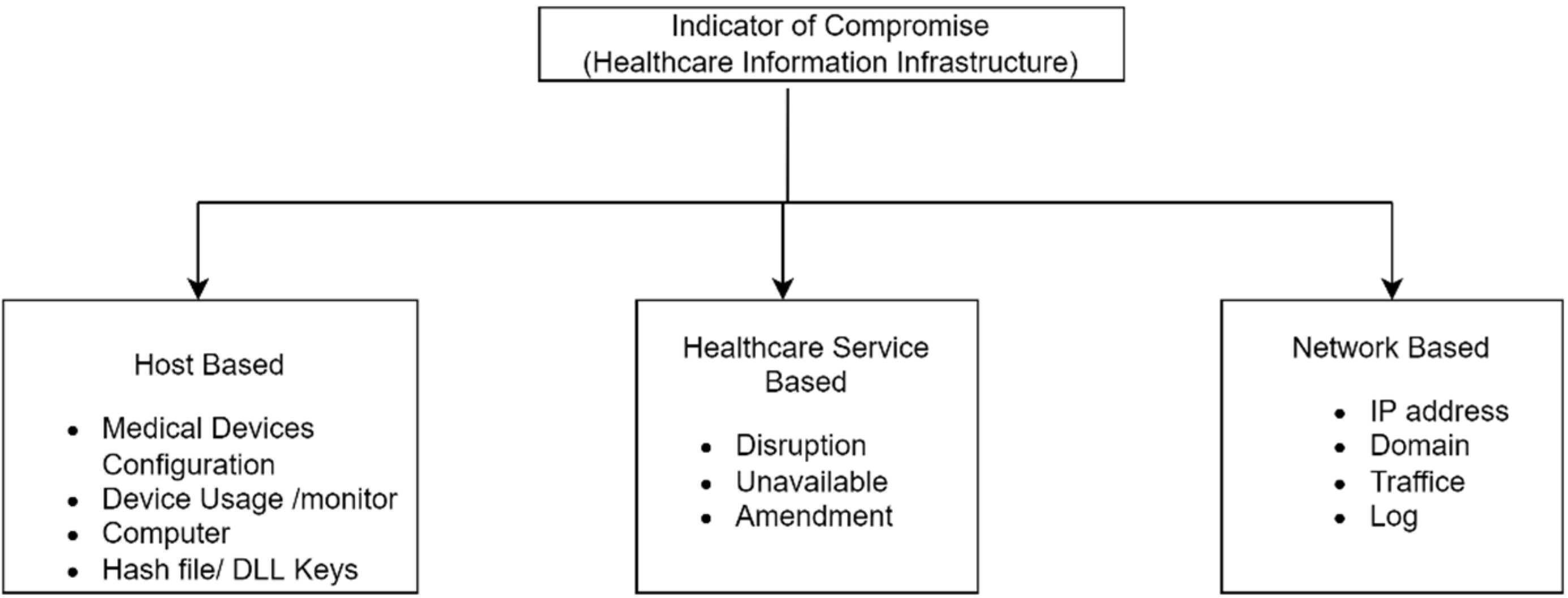
5.4. Generate and Prioritise Evidence-Based Vulnerability Chain
6. Discussion
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Williams, A.H.P.; Woodward, J.A. Cybersecurity vulnerabilities in medical devices: A complex environment and multifaceted problem. Med. Devices Evid. Res. 2015, 12, 305–316. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Forbes. Available online: https://www.forbes.com/sites/forbestechcouncil/2021/06/07/increased-cyberattacks-on-healthcare-institutions-shows-the-need-for-greater-cybersecurity/?sh=7b228d895650 (accessed on 5 January 2022).
- McKee, D.; Laulheret, P. McAfee Enterprise ATR Uncovers Vulnerabilities in Globally Used B. Braun Infusion Pump. Available online: https://www.mcafee.com/blogs/enterprise/mcafee-enterprise-atr/mcafee-enterprise-atr-uncovers-vulnerabilities-in-globally-used-b-braun-infusion-pump/#_Toc76469513 (accessed on 5 January 2022).
- Hanemann, A.; Patricia, M. Algorithm design and application of service-oriented event correlation. In Proceedings of the 3rd IEEE/IFIP International Workshop on Business-Driven IT Management, Salvador, Brazil, 7 April 2008. [Google Scholar]
- Kathleen, J.A.; DuBois, D.A.; Stallings, C.A. An Expert System Application for Network Intrusion Detection; No. LA-UR-91-558; CONF-911059-1; Los Alamos National Lab.: Santa Fe, NM, USA, 1991.
- Chochliouros, I.; Spiliopoulou, A.; Chochliouros, S. Methods for Dependability and Security Analysis of Large Networks. In Encyclopedia of Multimedia Technology and Networking; Pagani, M., Ed.; IGI Global: Milan, Italy, 2009; pp. 921–929. [Google Scholar]
- Bodeau, D.J.; McCollum, C.D.; Fox, D.B. Cyber Threat Modeling: Survey, Assessment, and Representative Framework. The Homeland Security Systems Engineering and Development Institute (HSSEDI) & MITRE Cooperation. 2018. Available online: https://www.mitre.org/sites/default/files/publications/pr_18-1174-ngci-cyber-threat-modeling.pdf (accessed on 25 January 2022).
- Frigault, M.; Wang, L. Measuring Network Security Using Bayesian Network-Based Attack Graphs. In Proceedings of the 3rd IEEE International Workshop on Security, Trist and Privacy for Software Applications, Turku, Finland, 28 July–1 August 2008. [Google Scholar]
- Kriaa, S.; Bouissou, M.; Piètre-Cambacédès, L. Modeling the Stuxnet attack with BDMP: Towards more formal risk assessments. In Proceedings of the 2012 7th International Conference on Risks and Security of Internet and Systems (CRiSIS), Cork, Ireland, 10–12 October 2012. [Google Scholar]
- Jha, S.; Sheyner, O.; Wing, J. Two formal analyses of attack graphs. In Proceedings of the 15th IEEE Computer Security Foundations Workshop. CSFW-15, Cape Breton, NS, Canada, 24–26 June 2002. [Google Scholar]
- Al-Mohannadi, H.; Awan, I.; Al Hamar, J. Analysis of adversary activities using cloud-based web services to enhance cyber threat intelligence. Serv. Oriented Comput. Appl. 2020, 14, 175–187. [Google Scholar] [CrossRef] [Green Version]
- Kim, K.; Shin, Y.; Lee, J.; Lee, K. Automatically Attributing Mobile Threat Actors by Vectorized ATT&CK Matrix and Paired Indicator. Sensors 2021, 21, 6522. [Google Scholar] [CrossRef] [PubMed]
- Somak, B.; Ghosh, S.K. An attack graph-based risk management approach of an enterprise. J. Inf. Assur. Secur. 2008, 2, 119–127. [Google Scholar]
- Polatidis, N.; Pavlidis, M.; Mouratidis, H. Cyber-attack path discovery in a dynamic supply chain maritime risk management system. Comput. Stand. Interfaces 2017, 56, 74–82. [Google Scholar] [CrossRef] [Green Version]
- Polatidis, N.; Pimenidis, E.; Pavlidis, M.; Papastergiou, S.; Mouratidis, H. From product recommendation to cyber-attack prediction: Generating attack graphs and predicting future attacks. Evol. Syst. 2020, 11, 479–490. [Google Scholar] [CrossRef] [Green Version]
- Yeboah-Ofori, A.; Islam, S. Cyber security threat modeling for supply chain organizational environments. Future Internet 2019, 11, 63. [Google Scholar] [CrossRef] [Green Version]
- Kure, H.I.; Islam, S.; Mouratidis, H. An integrated cyber security risk management framework and risk predication for the critical infrastructure protection. Neural Comput. Appl. 2022, 1, 1–31. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Grigoriadis, C. Assessing IoT enabled cyber-physical attack paths against critical systems. Comput. Secur. 2021, 107, 102316. [Google Scholar] [CrossRef]
- Cheung, K.; Bell, M.; Bhattacharjya, J. Cybersecurity in logistics and supply chain management: An overview and future research directions. Transp. Res. 2021, 146, 102217. [Google Scholar] [CrossRef]
- Kioskli, K.; Polemi, N. Psychosocial approach to cyber threat intelligence. Int. J. Chaotic Comput. 2020, 7, 159–165. [Google Scholar] [CrossRef]
- Common Vulnerabilities and Exposures (MITRE). Available online: https://cve.mitre.org/ (accessed on 10 February 2022).
- CVSS v.2 (FIRST). 2007. Available online: https://www.first.org/cvss/v2/guide (accessed on 15 February 2022).
- NIST SP 800-30. 2020. Available online: https://www.nist.gov/privacy-framework/nist-sp-800-30 (accessed on 5 February 2022).
- A Dynamic and Self-Organized Artificial Swarm Intelligence Solution for Security and Privacy Threats in Healthcare ICT Infrastructures. Available online: https://cordis.europa.eu/project/id/883273 (accessed on 5 February 2022).
- Digital Health Living Lab. Available online: https://www.brighton.ac.uk/research/enterprise/enterprise-projects/brighton-and-hove-digital-health-living-lab.aspx (accessed on 15 February 2022).
- Kioskli, K.; Fotis, T.; Mouratidis, H. The landscape of cybersecurity vulnerabilities and challenges in healthcare: Security standards and paradigm shift recommendations. In Proceedings of the 16th International Conference on Availability, Reliability and Security, the 1st SecHealth Workshop, Vienna, Austria, 17–20 August 2021; Digital Conference. ACM ICPS: New York, NY, USA, 2021; Volume 136, pp. 1–9. [Google Scholar]
| Vulnerability Scale | Description of Vulnerability Level | |
|---|---|---|
| Vulnerability Occurrence | Value Range (%) | Description of Successful Exploitation of the Vulnerability |
| Very High (5) | 80–100 | >80% |
| High (4) | 60–80 | 60–80% |
| Medium (3) | 40–60 | 40–60% |
| Low (2) | 20–40 | 20–40% |
| Very low (1) | 1–20 | <20% |
| Threat Actor Capability Scale | Description of Scale | |||
|---|---|---|---|---|
| Qualitative Values | Semi-Quantitative Values | Description | Exploitability Features | Metrics |
| Very High | 80–100 | TA has a very sophisticated level of expertise and is well-resourced for the required access vector and attack complexity. TA can generate opportunities to support multiple successful, continuous, and coordinated attacks. | Availability of all features = PoC and Weaponized Exploit, arbitrary code execution | PR = required level Entry point asset AV = required level |
| High | 60–80 | TA has a sophisticated level of expertise, with significant resources for the required access vector and attack complexity. TA has opportunities to support multiple successful coordinated attacks. | Availability of all features = PoC and Weaponized Exploit, arbitrary code execution | PR = required level Entry point asset AV = required level |
| Medium | 40–60 | TA has moderate resources, expertise, and opportunities for the required access vector and attack complexity to support multiple successful attacks. | Availability of some features = PoC and Weaponized Exploit, arbitrary code execution | PR = required level Entry point asset AV = required level |
| Low | 20–40 | TA has limited resources, expertise, and opportunities for the required access vector and attack complexity to support a successful attack. | Availability of some features = PoC and Weaponized Exploit, arbitrary code execution | PR = not required level Entry point asset AV = not required level |
| Very Low | 0–20 | TA has very limited resources, expertise, and opportunities for the required access vector and attack complexity to support a successful attack. | No Availability = PoC and Weaponized Exploit, arbitrary code execution | PR = not required level Entry point asset AV = not required level |
| Threat Actor’s Exploitation Capability IVL | Very Low | Low | Medium | High | Very High |
|---|---|---|---|---|---|
| Very Low | VL | VL | L | L | M |
| Low | VL | L | L | M | H |
| Medium | L | L | M | H | H |
| High | L | M | H | H | VH |
| Very High | M | H | H | VH | VH |
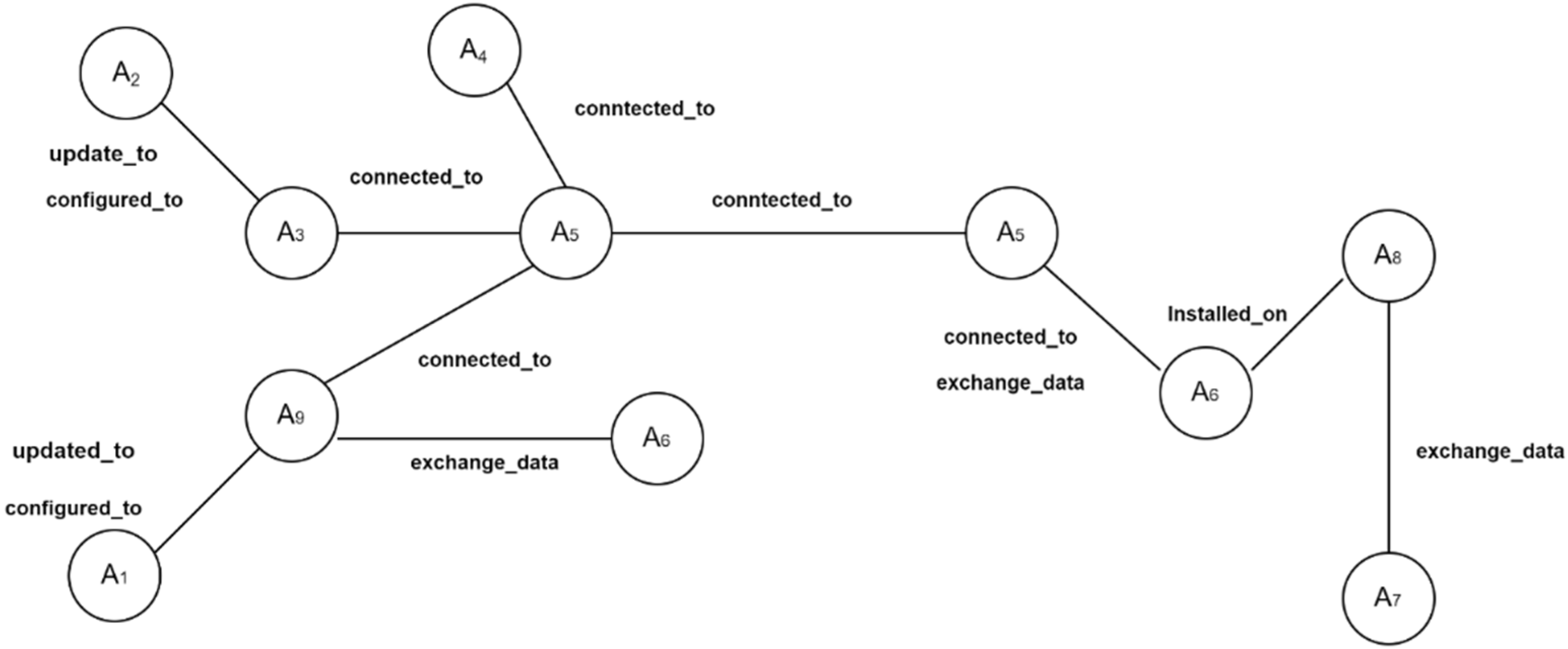
| Entry Point Asset and Type | Target Point Asset and Type | Dependency Type |
|---|---|---|
| A9 (SpaceCom Software) | A1 (Infusion Pump) | Configured_to, Updated_to |
| A3 (Insulin Management System) | A2 (Insulin Pump) | Configured_to, Updated_to |
| A8 (Care2X-Hospital Management System) | A6 (Windows System) | Installed_on, Updated_by |
| A5 (Router) | A6 (Windows System) | Connected_to, Exchange_data |
| A4 (IoT Device) | A5 (Router) | Connected_to, Exchange_data |
| A7 (Tablet) | A8 (Care2X-Hospital Management System) | Exchange_data |
| A9 (SpaceCom Software) | A1 (Infusion Pump) | Configured_to, Updated_to |
| Asset | Vulnerabilities & Exploitability |
|---|---|
| A1 = Braun’s Infusion Pump | A1,V1 = Lack of input validation provides command line access and privilege escalation. TA requires in the same network as device CVE-2021-33886, A1.V3 = VH(8.8) AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| A1,V2 = Unrestricted file upload that can overwritten critical files due to privilege escalation CVE-2021-33884, A1.V4 = VH(9.1) CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H | |
| A2 = Medtronic MiniMed 508 insulin pump | A2,V1 = lack of security (authentication and authorization) in RF communication protocol with other devices such as blood glucose meter and glucose sensor transmitters. TA requires in the same network as device can inject or intercept data and change pump settings CVE-2019-10964, A2.V1 = VH(8.8) CVSS:3.0/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| A3 = Insulin Management System | A3,V1 = improper access control in the wireless RF communication protocol allows local TA to intercept or modify insulin data and change pump settings. CVE-2020-10627 A3.V1 = VH(8.1) CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N |
| A4 = IoT device Philips Hue light bulb | A4,V1 = communication protocol can be abused to remotely installed malicious firmware in the light bulb as remote code execution through buffer overflow and spread to other IoT devices that use Zigbee communication protocol. CVE-2020-6007 A4.V1 = H(7.8) CVSS:3.1/AV:A/AC:H/PR:N/UI:R/S:C/C:H/I:H/A:H |
| A5 = Router (Buffalo, Cisco RV Series—Netgear) | A5,V1 (Buffalo routers) = Bypass authentication procedures on the affected routers though files which do not need authentication and gain root level access. It enables telnet service to connect other devices’ control such as IoT Devices. CVE-2021-20090 A5.V1 = VH(9.8) CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| A5,V2 (Cisco RV series) = Remote TA with administrative privileges inject arbitrary commands into operating system due to lack of input level validation through web-based interface. CVE-2021-4012 A5.V2 = H(7.2) CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H | |
| A5,V3 (Netgear router) = unauthenticated TA can affect the device through buffer overflow attack. CVE-2018-21224 A5.V3 = VH(8.8) CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | |
| A6 = System (Windows Compatible) | A6,V1 = A remote code execution vulnerability allows TA to execute arbitrary code and gain same right as current user. This allows to install program modify files based on the existing user rights. CVE-2019-1236 A6.V1 = H(7.5) CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H |
| A6,V2 = A remote code execution vulnerability allows TA to execute arbitrary code and gain same right as current user. TA needs control of a server to execute this vulnerability and tricks the user for the to connect the server. CVE-2019-1333 A6.V2 = H(7.5) CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H | |
| A6,V3 = A remote code execution vulnerability allows TA to run arbitrary code with system privilege. TA could install program, amend files, and create new users with full rights. CVE-2021-36958 A6.V3 = H(7.8) CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H | |
| A7 = Rugged Tablet (Dell) | A7,V1 = A local TA without the necessity of authentication can exploit this vulnerability and execute arbitrary code in system management mode. CVE-2020-5348 A8.V1 = H(7.8) CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H |
| A8 = web-based hospital management system (Care2X) | A8,V1 = A cross site scripting vulnerability exploited during patient registration. TA can send the XSS payload to this vulnerable parameter and take control of another register user. TA needs victim user interaction Exploitability features = PoC and Weaponized Exploit, CVE-2021-36352 A9.V1 = M(5.4) CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N |
| A9 = SpaceCom | A9,V1 = Lack of authentication for critical space com function allows connection to the pump Exploitability features = PoC and Weaponized Exploit, arbitrary code execution CVE-2021-33882, A1.V1 = VH(8.6) AV:N/AC:L/PR:N/UI:N/S:C/C:N/I:H/A:N |
| A9,V2 = Clear text transmission allows TA to snoop network traffic. Exploitability features = PoC and Weaponized Exploit, arbitrary code execution CVE-2021-33883, A1.V2 = H(7.5) AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
| Security Incident | Attack Path | Evidence Chain |
|---|---|---|
| Amendment of drug level and pump configuration | A5,V1 → A9,V1 → A1,V1 A9,V2 → A1,V2 A8,V1 → A9,V1 → A1,V2 A4,V1 → A9,V1 → A1,V1 | A5,V1 → A9, IoC1 → A1, IoC2 A9, IoC4 → A1, IoC3 A8,V1 → A9, IoC1 → A1, IoC2 A4,V1 → A9, IoC1 → A1, IoC2 |
| Patient data leak | A5,V3 → A6,V1 → A8,V1 A5,V3 → A6,V2 → A8,V1 A7,V1 → A6,V3 → A8,V1 | A5,V3 → A6, IoC5 → A8, IoC6 A5,V3 → A6, IoC7 → A8, IoC6 A7,V1 → A6,V3 → A8, IoC6 |
| Vulnerability | Asset | Individual Vulnerability Level (IVL) | Threat Actor’s Exploitability Level | ||||
|---|---|---|---|---|---|---|---|
| Capability = Very Low (VL) | Capability = Low (L) | Capability = Moderate (M) | Capability = High (H) | Capability = Very High (VH) | |||
| V1 | A1 | IVL(A1,V1) = VH | M | H | H | VH | VH |
| V2 | A1 | IVL(A1,V2) = VH | M | H | H | VH | VH |
| V1 | A9 | IVL(A9,V1) = VH | M | H | H | VH | VH |
| V2 | A2 | IVL(A9,A2) = H | L | M | H | H | VH |
| V1 | A6 | IVL(A6,V1) = H | L | L | H | H | VH |
| V2 | A6 | IVL(A6,V2) = H | L | L | H | H | VH |
| V1 | A8 | IVL(A8,V1) = VH | M | H | H | VH | VH |
| AP No. | Attack Paths | Evidence Chains | Exploitation Level Chain (ELC) | Exploitation Probability | APEL |
|---|---|---|---|---|---|
| 1 | A5,V1 → A9,V1 → A1,V1 | V1 → IoC1 → IoC2 | H → IoC1 → IoC2 | 0.75 × 1 × 1 = 0.75 | H |
| 2 | A9,V2 → A1,V2 | IoC4 → IoC3 | IoC4 → IoC3 | 1 × 1 = 1 | VH |
| 3 | A8,V1 → A9,V1 → A1,V2 | V1 → IoC1 → IoC2 | M → IoC1 → IoC2 | 0.5 × 1 × 1 = 0.5 | M |
| 4 | A4,V1 → A9,V1 → A1,V1 | A4,V1 → A9, IoC1 → A1, IoC2 | M → IoC1 → IoC2 | 0.5 × 1 × 1 = 0.5 | M |
| 5 | A5,V3 → A6,V1 → A8,V1 | A5,V3 → IoC5 → IoC6 | H → IoC5 → IoC6 | 0.75 × 1 × 1 = 0.75 | H |
| 6 | A5,V3 → A6,V2 → A8,V1 | A5,V3 → A6, IoC7 → A8, IoC6 | H → IoC7 → IoC6 | 0.75 × 1 × 1 = 0.75 | H |
| 7 | A7,V1 → A6,V3 → A8,V1 | A7,V1 → A6,V3 → A8, IoC6 | H → H → IoC6 | 0.75 × 0.75 × 1 = 0.56 | M |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Islam, S.; Papastergiou, S.; Kalogeraki, E.-M.; Kioskli, K. Cyberattack Path Generation and Prioritisation for Securing Healthcare Systems. Appl. Sci. 2022, 12, 4443. https://doi.org/10.3390/app12094443
Islam S, Papastergiou S, Kalogeraki E-M, Kioskli K. Cyberattack Path Generation and Prioritisation for Securing Healthcare Systems. Applied Sciences. 2022; 12(9):4443. https://doi.org/10.3390/app12094443
Chicago/Turabian StyleIslam, Shareeful, Spyridon Papastergiou, Eleni-Maria Kalogeraki, and Kitty Kioskli. 2022. "Cyberattack Path Generation and Prioritisation for Securing Healthcare Systems" Applied Sciences 12, no. 9: 4443. https://doi.org/10.3390/app12094443
APA StyleIslam, S., Papastergiou, S., Kalogeraki, E.-M., & Kioskli, K. (2022). Cyberattack Path Generation and Prioritisation for Securing Healthcare Systems. Applied Sciences, 12(9), 4443. https://doi.org/10.3390/app12094443







