Local-Moment-Driven Robust Reversible Data Hiding
Abstract
1. Introduction
- (1)
- The proposed LM-RRDH transforms the host image into two planes: MSB and LSB, and makes use of the image of the MSB plane for embedding the secret information so that the required robustness of the hidden data can be provided.
- (2)
- The image of the MSB plane is divided into sub-blocks, and pixel groups are formed to collect similar-intensity pixels in the same group. Therefore, highly correlated groups are formed to embed secret information.
- (3)
- Further, the dynamic selection of a pairwise embedding strategy based on the number of pixels in the group can help in achieving better quality while maintaining the embedding capacity.
- (4)
- As a result, the proposed LM-RRDH can provide superior quality while providing comparable embedding capacity.
2. Literature Review
2.1. Review of Existing Robust Reversible Data Hiding Schemes
2.2. Detailed Review of Kumar and Jung’s TLE Scheme [30]
3. The Proposed Local-Moment-Driven Robust Reversible Data-Hiding Scheme
3.1. Embedding Method
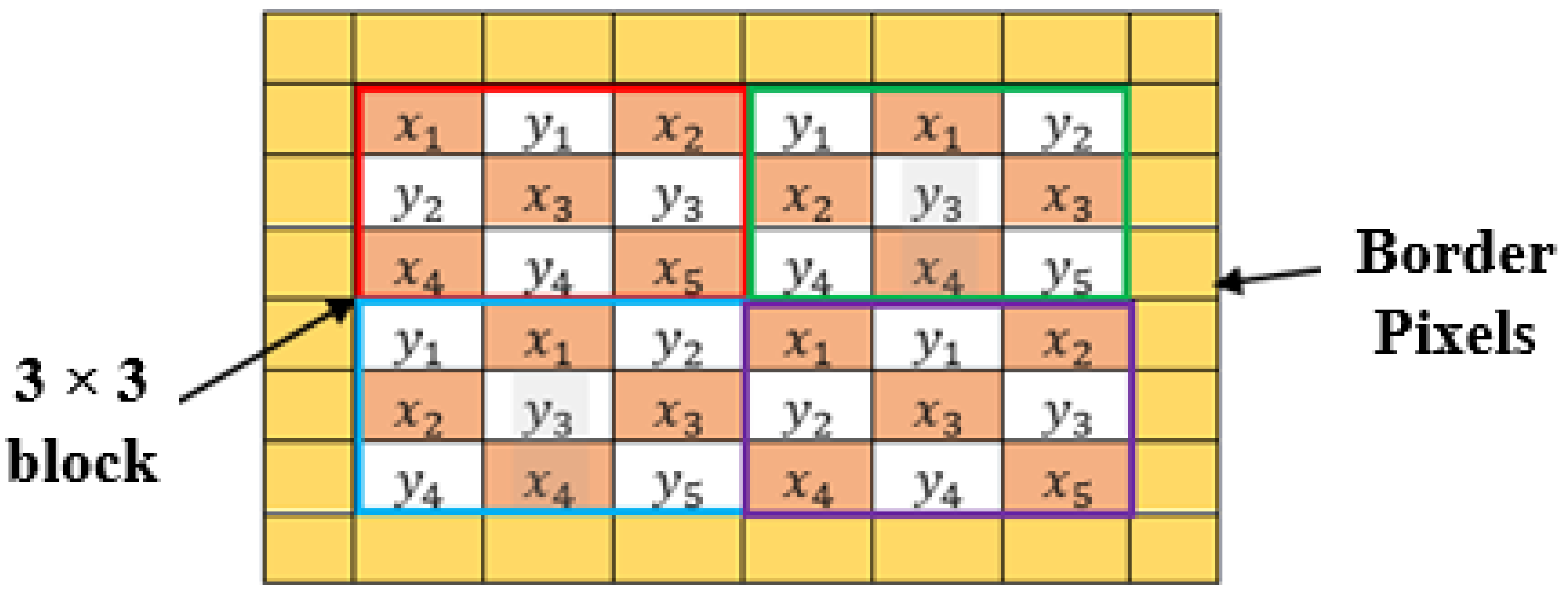
3.1.1. Checkboard Scanning Based Pixel Grouping Using Local Moment
3.1.2. Hiding Method Based on Adaptive Selection of Embedding Strategy
3.1.3. Auxiliary Information for Blind Decoding
- Details of location map: Though the proposed LM-RRDH scheme embeds the secret data in the MSB plane of the image, the problem of overflow (pixel value where or ) and underflow (pixel value ) can still arise due to the pixel modification for embedding the secret information. Therefore, a location map is constructed to avoid such problems, in which all the pixels of the original image that is either equal to ‘0’ or to are marked by ‘1’, otherwise by ‘0’, as given in Equation (21):where is the number of the pixel scanned in the raster-scan order of the image, . Further, the values of ‘0’ and -valued pixels are increased and decreased by ‘1’, respectively, using Equation (22), so that these pixels can also be used for embedding the secret information while avoiding the problem of underflow/overflow.
- Maximum pixel value of: As discussed above, the proposed LM-RRDH scheme first decomposes the cover image () into two images, and cover images (), by segregating a certain number of LSBs from the MSBs of each pixels of the image and then embeds the secret data in . Therefore, the number () of LSBs to generate the must be shared with the receiver so that they can decompose the image and start the extraction process. The value of can be encoded, at a maximum, by 3 bits.
- LSBs of the border pixels: The LM-RRDH scheme embeds some of the information, such as number () of LSBs, to generate the in the LSBs of border pixels of the cover image (), as the border pixels are not used for embedding the secret information. Therefore, the LSBs of the border pixels need to be embedded in the along with the secret data as auxiliary information, so that extraction and recovery can be performed blindly.
3.1.4. Embedding Algorithm
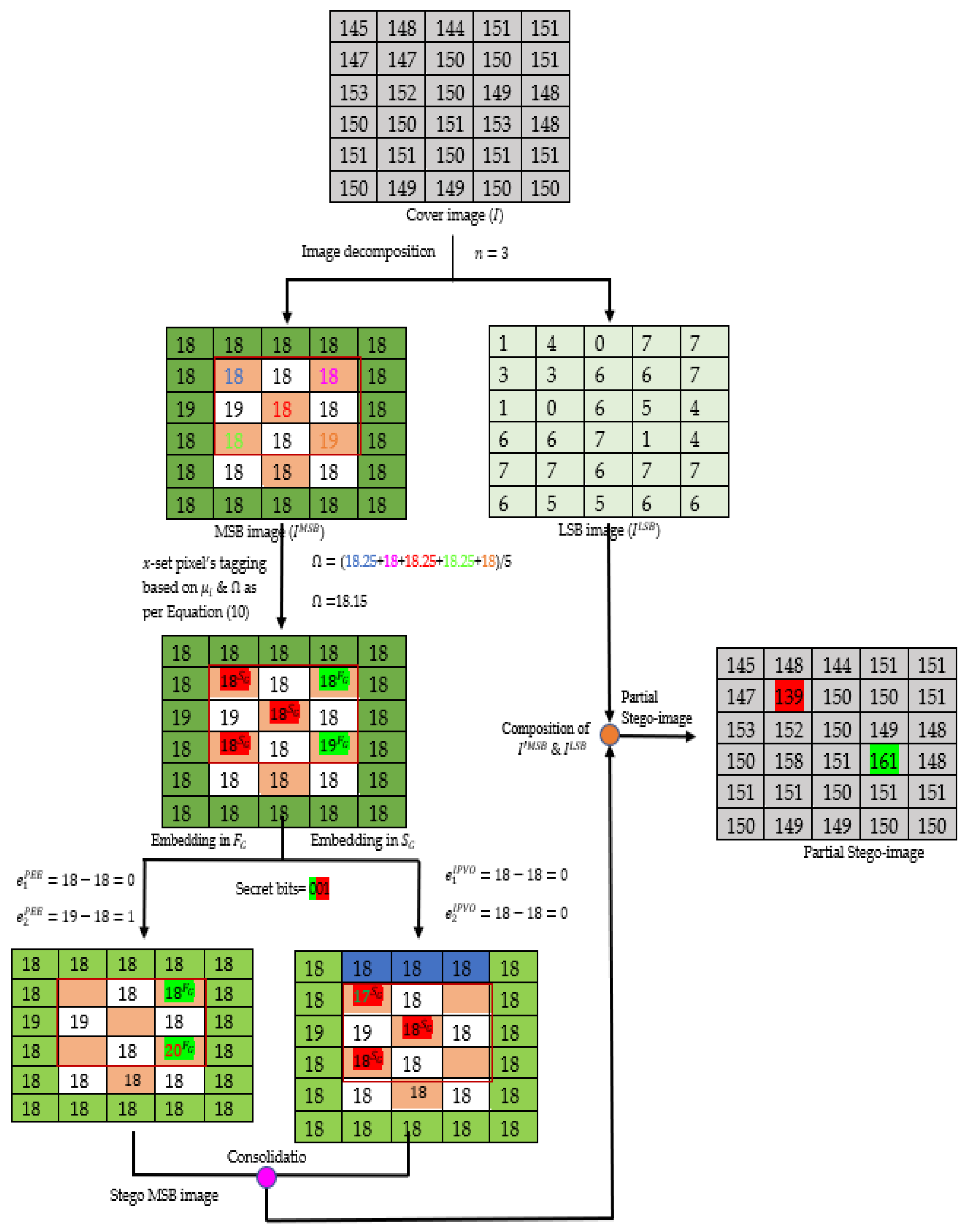
- Step 1: Decompose into and using Equations (2) and (3), respectively. The decomposition is performed by segregating number of LSBs from each pixel of in a pixel-wise manner.
- Step 2: Scan starting from pixel position ( to ( in a raster scan manner and construct using Equation (14) in which all the pixels are marked. Next, compress the using JBEG/arithmetic encoding to obtain a compressed location map (). The length of the is denoted by .
- Step 3: Divide into blocks of 3 × 3 pixels, each starting from pixel position to . Next, group all the pixels into two groups () using Equation (10).
- Step 4: Extract least significant bits (LSBs) of pre-defined border pixels of . Append the extracted bits along with CLM at the end of the secret information.
- Step 5: Embed the secret information in a pixel group as follows:
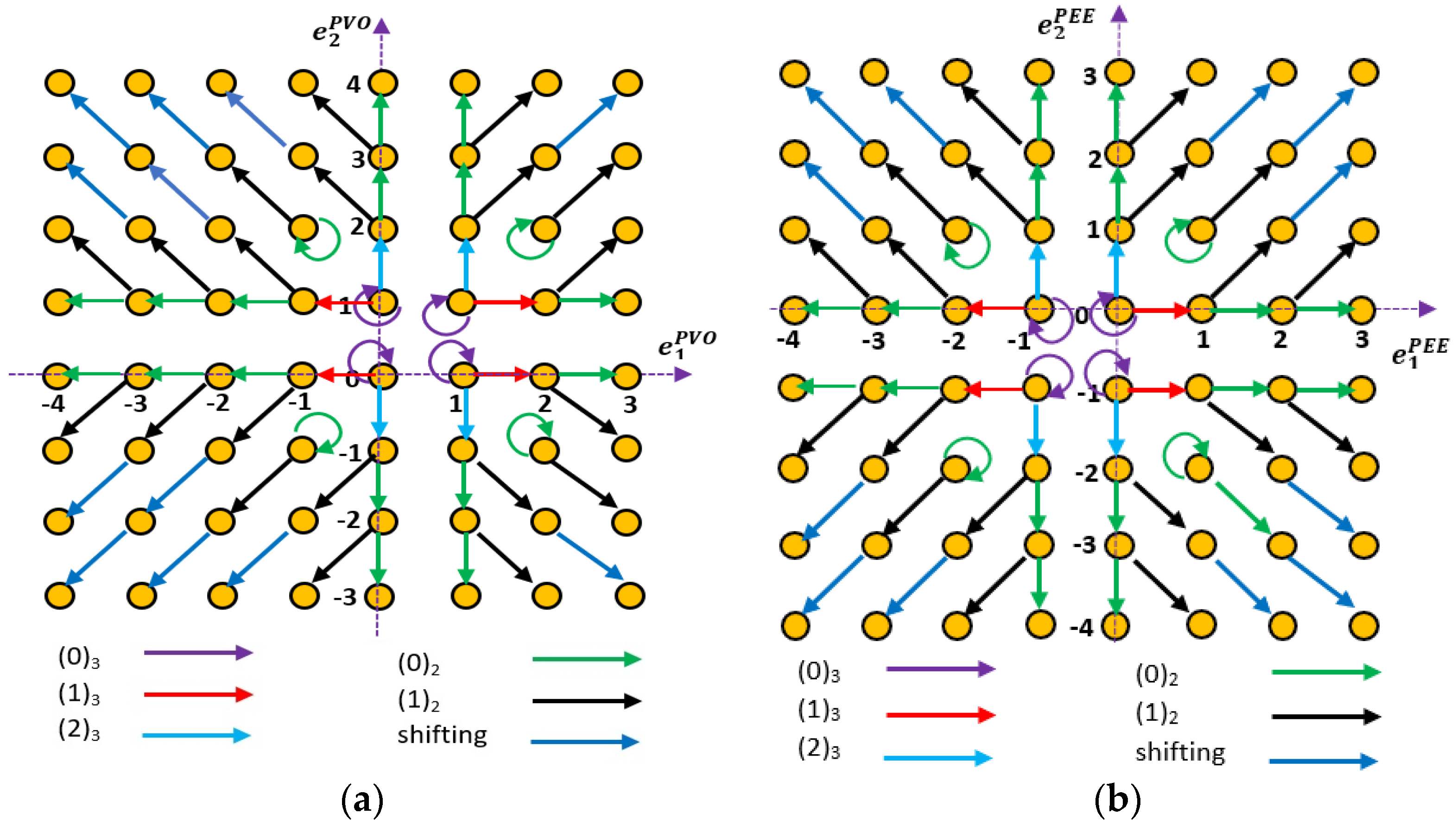
- If cardinality of > 2, then calculate prediction errors and using Equations (12) and (13), respectively, and expand the prediction errors as per the secret data bits as per Figure 2a. Next, modify the minimum and maximum valued pixels using Equations (14) and (15), respectively, to embed the secret data.
- Otherwise, if cardinality of is equal to 2 then calculate prediction errors and using Equations (16) and (17), respectively, and expand the prediction errors as per the secret data bits as in Figure 2b. Next, modify the first and the second pixels of the group using Equations (18) and (19), respectively, to embed the secret data.
- Otherwise, calculate prediction error and embed the secret data in the pixel using Equation (20).
- Step 6: Repeat Step 5 for group .
- Step 7: Repeat Steps 5-6 for pixels. Note the position of last block () in which embedding is carried out.
- Step 8: Compose the and to obtain stego image and replace the LSBs of pre-defined border pixels of from the value of and position of last block () using the LSB substitution method.
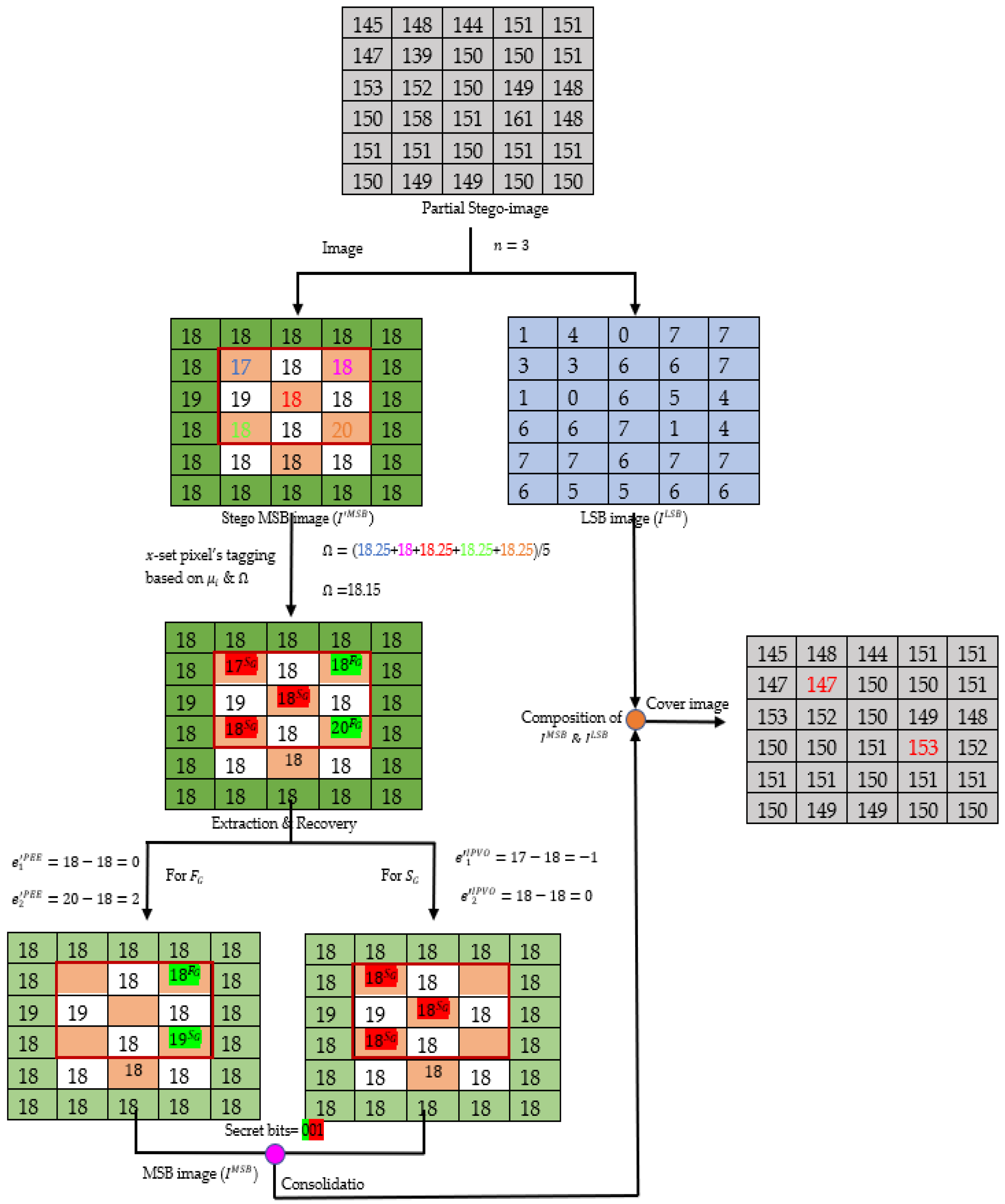
3.2. Secret Information Extraction and the Original Image Recovery Method
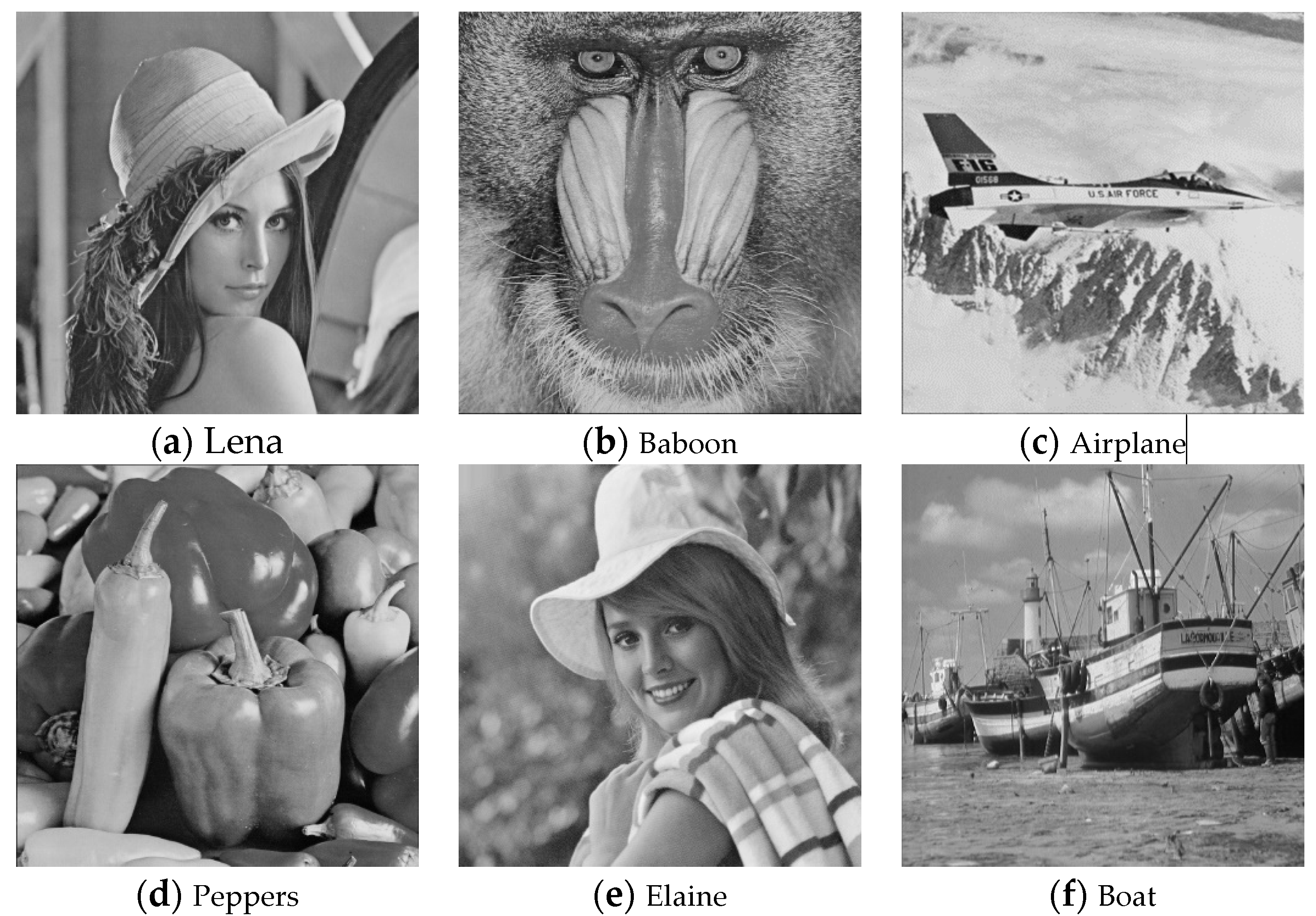
4. Experimental Results and Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kumar, R.; Saini, K.K.; Chand, S. A new steganography technique using snake scan ordering strategy. Int. J. Image 2013, 6, 25–32. [Google Scholar] [CrossRef]
- Kumar, R.; Chand, S.; Singh, S. An Improved Histogram-Shifting-Imitated Reversible Data Hiding based on HVS Characteristics. Multimed. Tools Appl. 2018, 77, 13445–13457. [Google Scholar] [CrossRef]
- Rai, A.K.; Kumar, N.; Kumar, R.; Om, H.; Chand, S.; Jung, K.-H. Intra-Block Correlation Based Reversible Data Hiding in Encrypted Images Using Parametric Binary Tree Labeling. Symmetry 2021, 13, 1072. [Google Scholar] [CrossRef]
- Kumar, R.; Chand, S. A reversible high capacity data hiding scheme using pixel value adjusting feature. Multimed. Tools Appl. 2016, 75, 241–259. [Google Scholar] [CrossRef]
- Malik, A.; Singh, S.; Kumar, R. Recovery based high capacity reversible data hiding scheme using even-odd embedding. Multimed. Tools Appl. 2018, 77, 15803–15827. [Google Scholar] [CrossRef]
- Kumar, R.; Chand, S.; Singh, S. A reversible high capacity data hiding scheme using combinatorial strategy. Int. J. Multimed. Intell. Secur. 2018, 3, 146–161. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Alattar, A. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Proc. 2014, 13, 1147–1156. [Google Scholar] [CrossRef]
- Thodi, D.M.; Rodriguez, J.J. Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 2007, 16, 721–730. [Google Scholar] [CrossRef]
- Sachnev, V.; Kim, H.J.; Nam, J.; Suresh, S.; Shi, Y.Q. Reversible watermarking algorithm using sorting and prediction. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 989–999. [Google Scholar] [CrossRef]
- Fallahpour, M. Reversible image data hiding based on gradient adjusted prediction. IEICE Electron. Exp. 2008, 5, 870–876. [Google Scholar] [CrossRef]
- Runwen, H.; Xiang, S. CNN prediction based reversible data hiding. IEEE Signal Process. Lett. 2021, 28, 464–468. [Google Scholar]
- Kumar, R.; Kim, D.S.; Lim, S.; Jung, K.H. High-Fidelity Reversible Data Hiding Using Block Extension Strategy. In Proceedings of the 34th International Technical Conference Circuits/Systems, Jeju, Korea, 23–26 June 2019; Volume 19, pp. 1–4. [Google Scholar]
- Kumar, R.; Kumar, N.; Jung, K.H. I-PVO based high capacity reversible data hiding using bin reservation strategy. Multimed. Tools Appl. 2020, 79, 22635–22651. [Google Scholar] [CrossRef]
- Ou, B.; Li, X.; Zhao, Y.; Ni, R.; Shi, Y.Q. Pairwise prediction-error expansion for efficient reversible data hiding. IEEE Trans. Image Process. 2013, 22, 5010–5021. [Google Scholar] [CrossRef]
- Kumar, R.; Jung, K.H. Enhanced pairwise IPVO-based reversible data hiding scheme using rhombus context. Inf. Sci. 2020, 536, 101–119. [Google Scholar] [CrossRef]
- Kaur, G.; Singh, S.; Rani, R.; Kumar, R.; Malik, A. High-quality reversible data hiding scheme using sorting and enhanced pairwise PEE. IET Image Process. 2021, 16, 1096–1110. [Google Scholar] [CrossRef]
- Ou, B.; Li, X.; Zhang, W.; Zhao, Y. Improving pairwise PEE via hybrid-dimensional histogram generation and adaptive mapping selection. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 2176–2190. [Google Scholar] [CrossRef]
- Kaur, G.; Singh, S.; Rani, R.; Kumar, R. A comprehensive study of reversible data hiding (RDH) schemes based on pixel value ordering (PVO). Arch. Comput. Methods Eng. 2021, 28, 3517–3568. [Google Scholar] [CrossRef]
- Zhaoxia, Y.; Xiang, Y.; Zhang, X. Reversible data hiding in encrypted images based on multi-MSB prediction and Huffman coding. IEEE Trans. Multimed. 2019, 22, 874–884. [Google Scholar]
- Puyang, Y.; Yin, Z.; Qian, Z. Reversible Data Hiding in Encrypted Images with Two-MSB Prediction. In Proceedings of the IEEE International Workshop on Information Forensics and Security (WIFS), Hong Kong, China, 11–13 December 2018; pp. 1–7. [Google Scholar]
- Puteaux, P.; Ong, S.Y.; KokSheik, W.; Puech, W. A survey of reversible data hiding in encrypted images—The first 12 years. J. Vis. Commun. Image Represent. 2021, 77, 103085. [Google Scholar] [CrossRef]
- Vleeschouwer, C.D.; Delaigle, J.F.; Macq, B. Circular interpretation of bijective transformations in lossless watermarking for media asset management. IEEE Trans. Multimed. 2003, 5, 97–105. [Google Scholar] [CrossRef]
- Ni, Z.C.; Shi, Y.Q.; Ansari, N.; Su, W.; Sun, Q.B.; Lin, X. Robust lossless image data hiding. Multimed. Expo. 2004, 3, 2199–2202. [Google Scholar]
- Ni, Z.C.; Shi, Y.Q.; Ansari, N.; Su, W.; Sun, Q.B.; Lin, X. Robust lossless image data hiding designed for semi-fragile image authentication. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 497–509. [Google Scholar]
- Zeng, X.T. A lossless robust data hiding scheme. Pattern Recognit. 2010, 43, 1656–1667. [Google Scholar] [CrossRef]
- Deng, C.; Gao, X.; Peng, H.; An, L.; Ji, F. Histogram modification based robust image watermarking approach. Int. J. Multimed. Intell. Secur. 2010, 1, 153–168. [Google Scholar] [CrossRef]
- Rajkumar, R.; Vasuki, A. Reversible and robust image watermarking based on histogram shifting. Clust. Comput. 2019, 22, 12313–12323. [Google Scholar] [CrossRef]
- Wang, W.; Ye, J.; Wang, T.; Wang, W. Reversible data hiding scheme based on significant-bit-difference expansion. IET Image Process. 2017, 11, 1002–1014. [Google Scholar] [CrossRef]
- Kumar, R.; Jung, K.H. Robust reversible data hiding scheme based on two-layer embedding strategy. Inf. Sci. 2020, 512, 96–107. [Google Scholar] [CrossRef]
- Zong, T.; Xiang, Y.; Natgunanathan, I.; Guo, S.; Zhou, W.; Beliakov, G. Robust histogram shape-based method for image watermarking. IEEE Trans. Circuits Syst. Video Technol. 2015, 25, 717–729. [Google Scholar] [CrossRef]
- Hu, X.; Wang, D.A. Histogram based algorithm robust to geometric distortions. In Proceedings of the International Conference on Electrical, Computer Engineering and Electronics, Jinan, China, 29–31 May 2015. [Google Scholar]
- Golabi, S.; Helfroush, M.S.; Danyali, H. Non-unit mapped radial moments platform for robust, geometric invariant image watermarking and reversible data hiding. Inf. Sci. 2018, 447, 104–116. [Google Scholar] [CrossRef]
- Bao, Z.; Luo, X.; Zhang, Y.; Yang, C.; Liu, F. A Robust Image Steganography on Resisting JPEG Compression with No Side Information. IETE Tech. Rev. 2018, 35, 4–13. [Google Scholar] [CrossRef]
- Kumar, N.; Kumar, R.; Caldelli, R. Local Moment Driven PVO Based Reversible Data Hiding. IEEE Signal Process. Lett. 2021, 28, 1335–1339. [Google Scholar] [CrossRef]
| 1 | 0 | 1 | >1 | |||
|---|---|---|---|---|---|---|
| - | 0 | 1 | 0 | 1 | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, Y.V.; Khan, S.; Shukla, S.K.; Jung, K.-H. Local-Moment-Driven Robust Reversible Data Hiding. Appl. Sci. 2022, 12, 11826. https://doi.org/10.3390/app122211826
Singh YV, Khan S, Shukla SK, Jung K-H. Local-Moment-Driven Robust Reversible Data Hiding. Applied Sciences. 2022; 12(22):11826. https://doi.org/10.3390/app122211826
Chicago/Turabian StyleSingh, Yash Veer, Shadab Khan, Santosh Kumar Shukla, and Ki-Hyun Jung. 2022. "Local-Moment-Driven Robust Reversible Data Hiding" Applied Sciences 12, no. 22: 11826. https://doi.org/10.3390/app122211826
APA StyleSingh, Y. V., Khan, S., Shukla, S. K., & Jung, K.-H. (2022). Local-Moment-Driven Robust Reversible Data Hiding. Applied Sciences, 12(22), 11826. https://doi.org/10.3390/app122211826








