HORSIC+: An Efficient Post-Quantum Few-Time Signature Scheme
Abstract
:1. Introduction
2. Preliminaries and Related Works
2.1. Preliminaries
- takes as input a security parameter and outputs a signature key X and a verification key Y;
- outputs a signature σ under the signature key X for message ;
- outputs 1 iff σ is a valid signature on M under the verification key Y;
2.2. Winternitz One-Time Signature Scheme (W-OTS)
2.2.1. W-OTS
2.2.2. W-OTS
2.2.3. W-OTS
2.3. HORSIC
| Algorithm 1: Key generation of HORSIC () |
| System Parameters: Parameters n, t, k, z, and w Output: Signature key X and verification key Y 1: Choose 2: Compute 3: return |
| Algorithm 2: Signing of HORSIC () |
| System Parameters: Parameters n, t, k, z, and w Input: Signature key X and message M Output: Signature 1: Compute 2: Compute 3: Set 4: Compute 5: Split h into k pieces of length bits each 6: Interpret each as an integer for all 7: if there exist p and q with such that and then 8: and go to Step 4 9: Compute for all 10: return |
| Algorithm 3: Verification of HORSIC () |
| System Parameters: Parameters n, t, k, z, and w Input: Verification key Y, message M, and signature Output: “accept” or “reject” 1: Compute 2: Compute 3: Compute 4: Split h into k pieces of length bits each 5: Interpret each as an integer for all 6: if there exist p and q with such that and then 7: return “reject” 8: if there exist such that then 9: return “reject” 10: return “accept” |
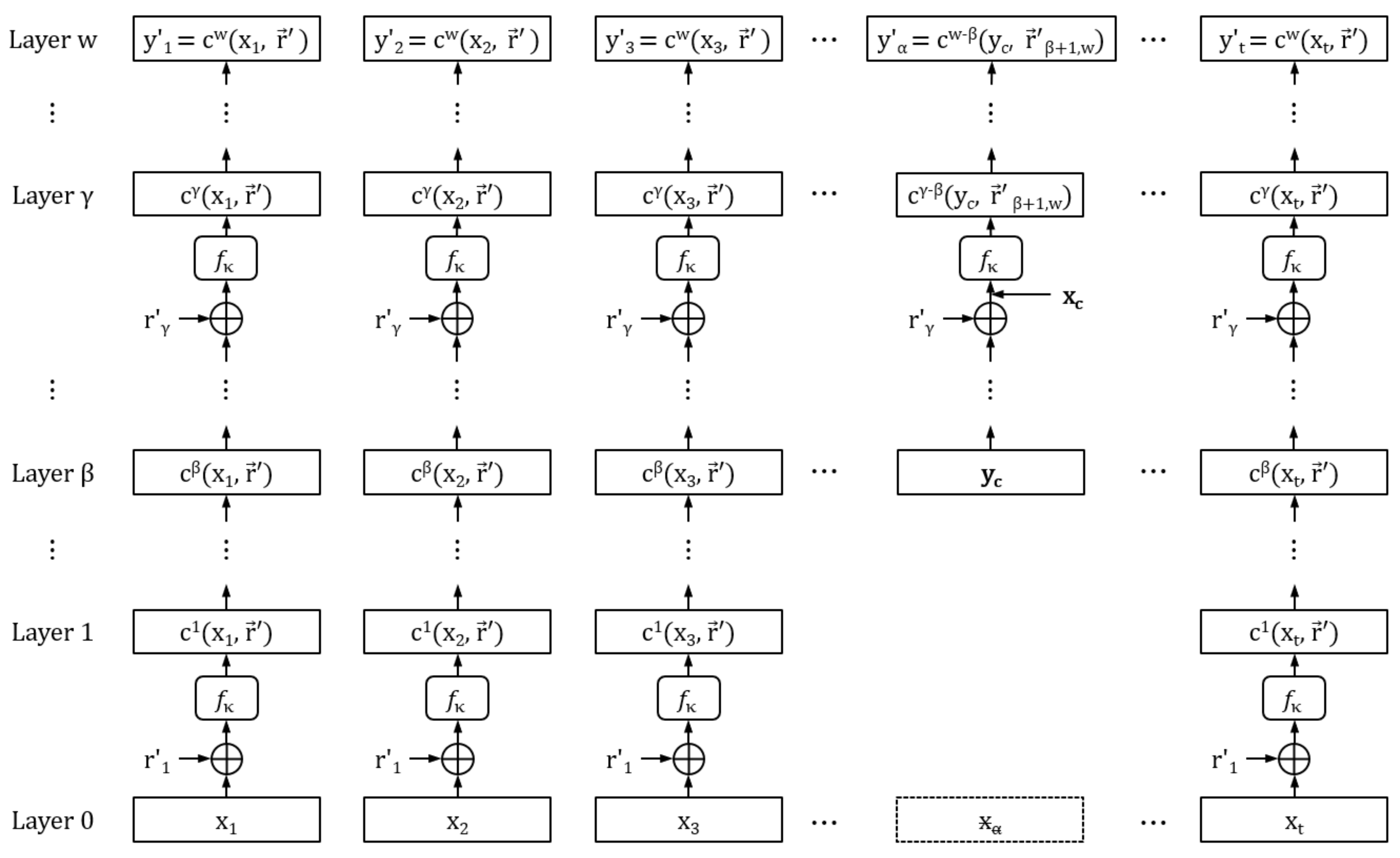
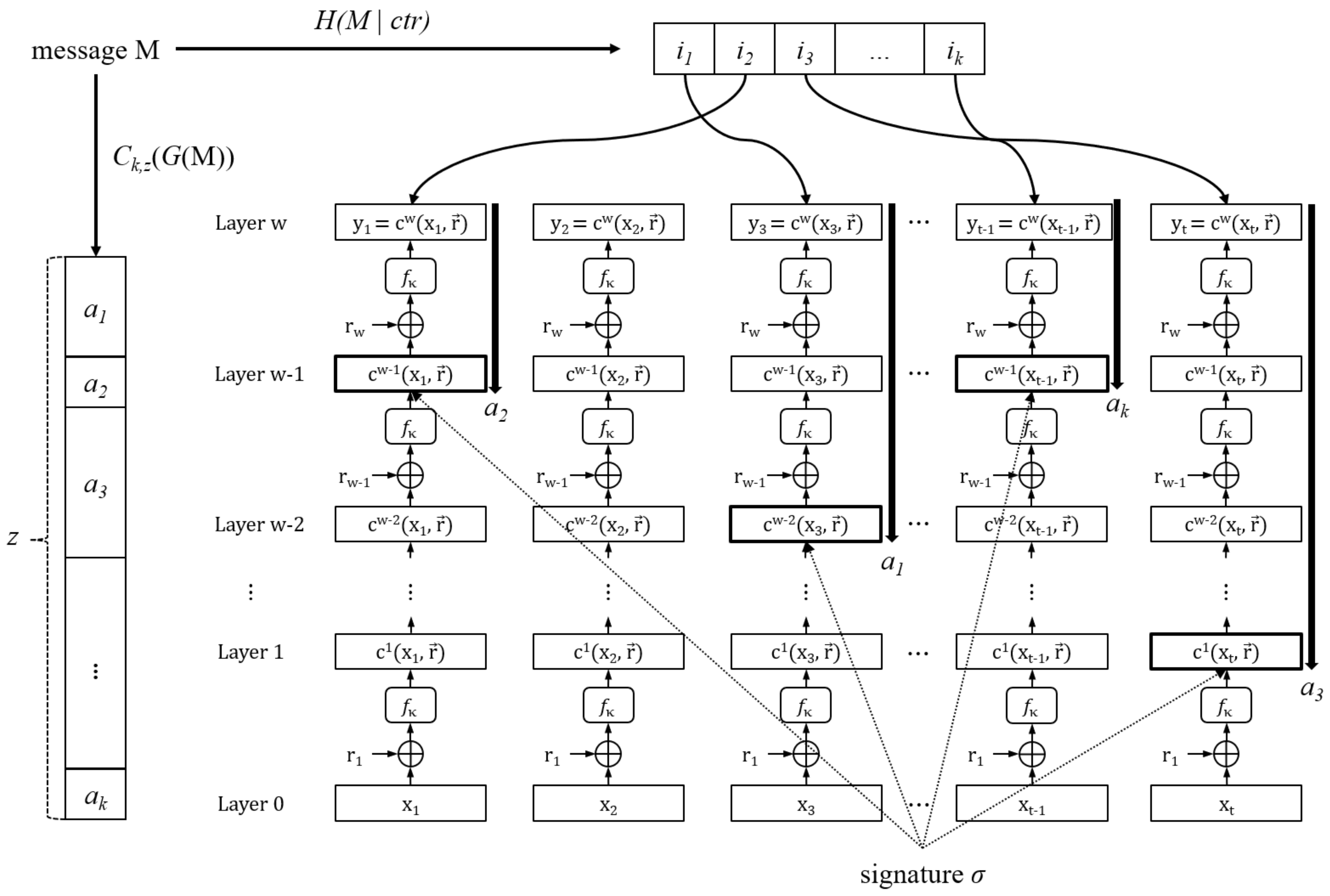
3. The HORSIC+ Signature Scheme
| Algorithm 4: Implementation of the function |
| System Parameters: Parameters k and z where Input: g where Output: 1: , 2: for to do 3: for to do 4: ifthen 5: , , 6: break 7: 8: , |
| Algorithm 5: Key generation of HORSIC+ () |
| System Parameters: Parameters n, t, k, z, and w Output: Signature key X and verification key Y 1: Choose 2: Choose 3: Choose 4: Compute 5: return |
| Algorithm 6: Signing of HORSIC+ () |
| System Parameters: Parameters n, t, k, z, and w Input: Signature key X, message M, function key , and bitmasks Output: Signature 1: Compute 2: Compute 3: Set 4: Compute 5: Split h into k pieces of length bits each 6: Interpret each as an integer for all 7: if there exist p and q with such that and then 8: and go to Step 4 9: Compute for all 10: return |
| Algorithm 7: Verification of HORSIC+ () |
| System Parameters: Parameters n, t, k, z, and w Input: Verification key Y, message M, and signature Output: “accept” or “reject” 1: Compute 2: Compute 3: Compute 4: Split h into k pieces of length bits each 5: Interpret each as an integer for all 6: if there exist p and q with such that and then 7: return “reject” 8: if there exist such that then 9: return “reject” 10: return “accept” |
4. Analysis
4.1. Security Analysis
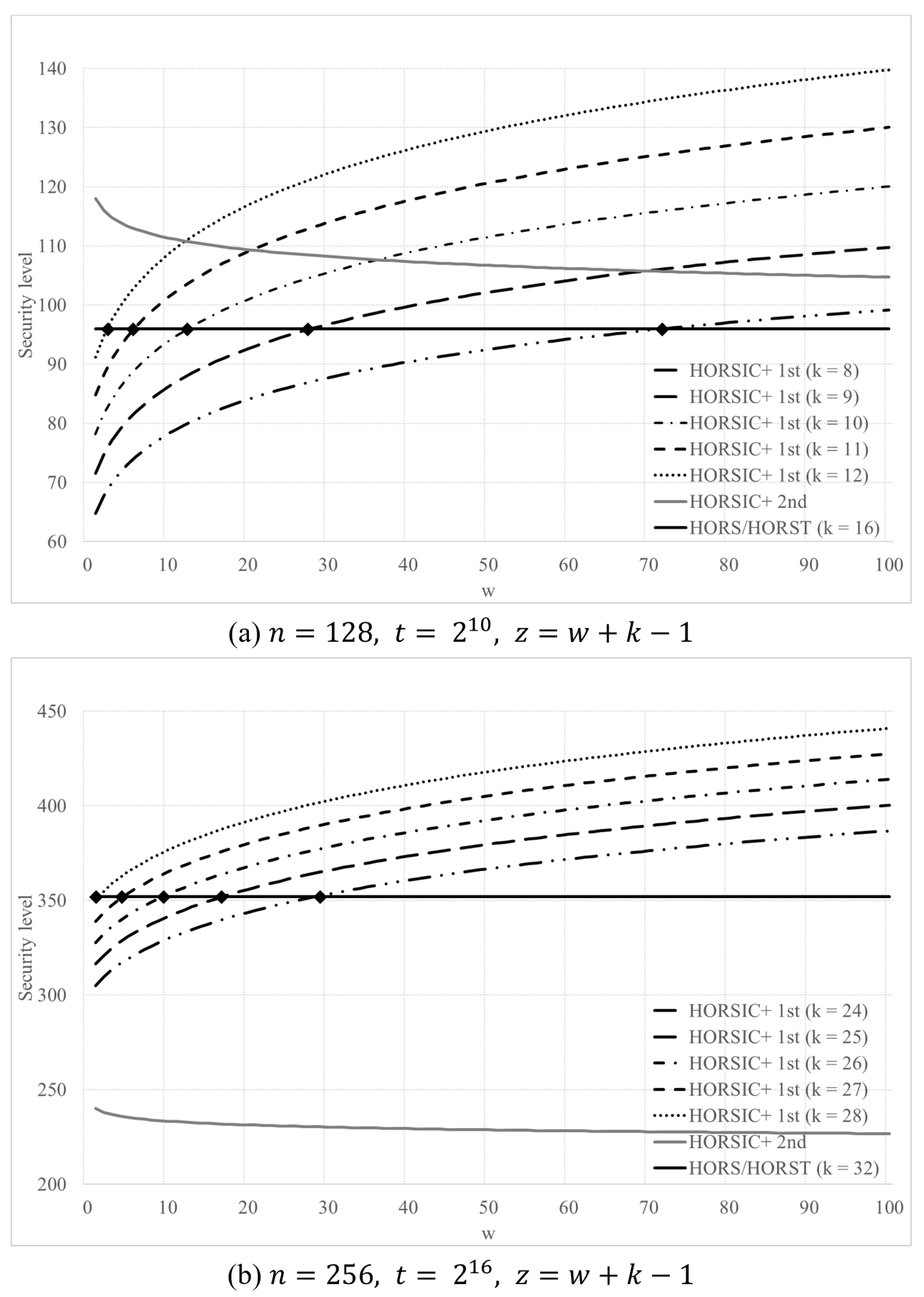
4.2. Security Level
4.3. Comparison with HORS and HORST
4.3.1. Security Parameters for HORSIC+
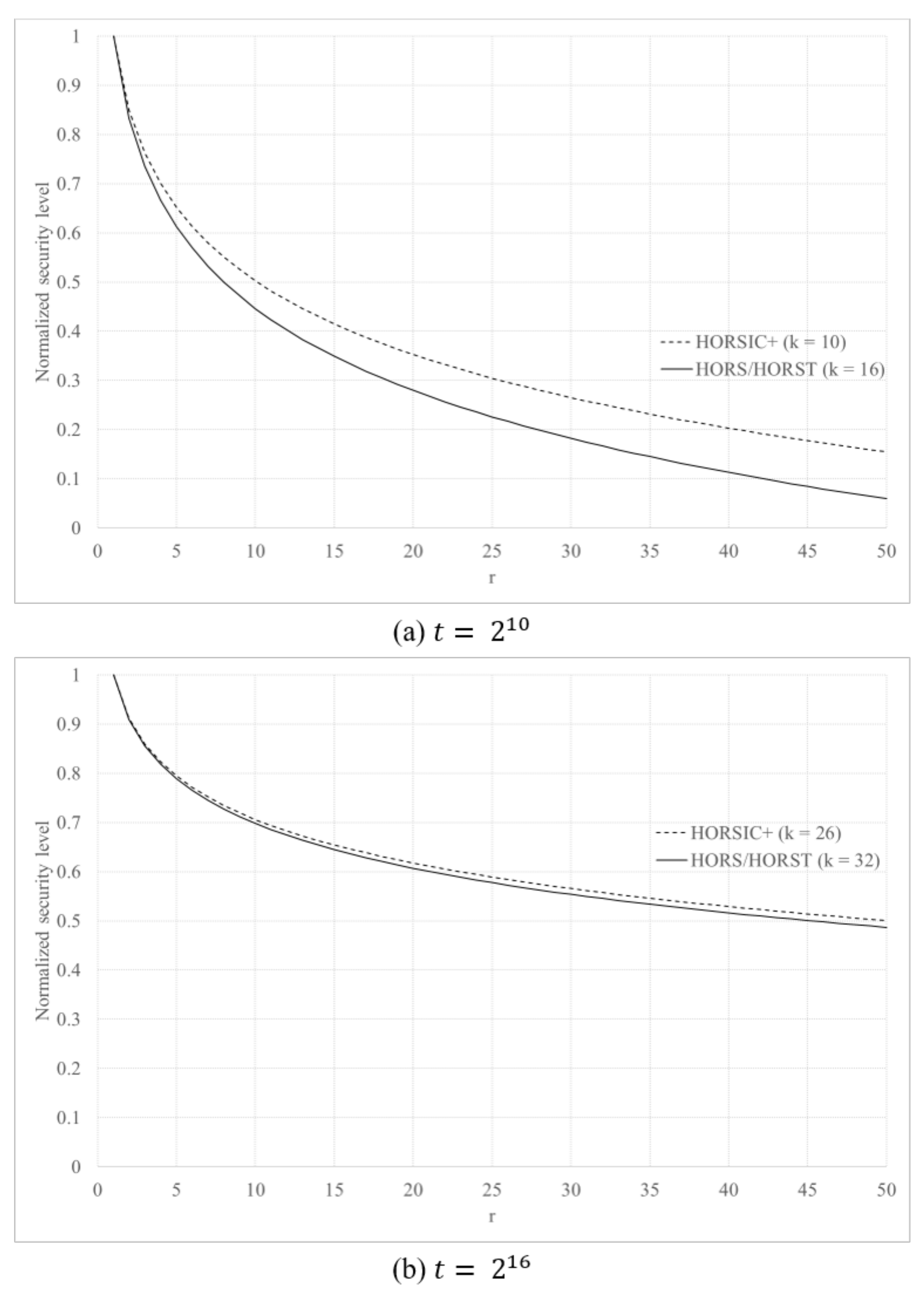
4.3.2. Security for Multiple Messages
4.3.3. Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Algorithm A1: |
| Input: Parameters n, t, k, z, w, one-way challenge , and second preimage resistance challenge Output: A value x that is either a preimage of or a second preimage for under or “fail” 1: Generate HORSIC+ key pair : 2: Choose indices and uniformly at random 3: if then 4: Set 5: else 6: Choose index uniformly at random 7: Obtain by setting for all and 8: Obtain by setting , for all , and 9: Run 10: if queries with message M then 11: Compute , , and which corresponds to M 12: if there exist such that and then 13: return “fail” 14: Generate signature of M:
15: Reply to the query string 16: if returns valid then 17: Compute , , and which corresponds to 18: if is a permutation of then 19: return “fail” 20: else if there exists no such that and then 21: return “fail” 22: else if then 23: return preimage 24: else if then 25: return preimage 26: else if and then 27: return second preimage 28: return “fail” |
References
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Cambou, B.; Gowanlock, M.; Yildiz, B.; Ghanaimiandoab, D.; Lee, K.; Nelson, S.; Philabaum, C.; Stenberg, A.; Wright, J. Post Quantum Cryptographic Keys Generated with Physical Unclonable Functions. Appl. Sci. 2021, 11, 2801. [Google Scholar] [CrossRef]
- Ghosh, S.; Zaman, M.; Sakauye, G.; Sampalli, S. An Intrusion Resistant SCADA Framework Based on Quantum and Post-Quantum Scheme. Appl. Sci. 2021, 11, 2082. [Google Scholar] [CrossRef]
- Hoffstein, J.; Howgrave-Graham, N.; Pipher, J.; Silverman, J.H.; Whyte, W. NTRUSign: Digital signatures using the NTRU lattice. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 13–17 April 2003; Volume 2612, pp. 122–140. [Google Scholar] [CrossRef]
- Porras, J.; Baena, J.; Ding, J. ZHFE, a new multivariate public key encryption scheme. In Proceedings of the International Workshop on Post-Quantum Cryptography, Waterloo, ON, Canada, 1–3 October 2014; Volume 8772, pp. 229–245. [Google Scholar] [CrossRef]
- McEliece, R.J. A Public-Key Cryptosystem Based On Algebraic Coding Theory. Coding THV 1978, 4244, 114–116. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; Association for Computing Machinery: New York, NY, USA, 1996; pp. 212–219. Available online: https://arxiv.org/pdf/quant-ph/9605043.pdf (accessed on 10 August 2021).
- Palmieri, P. Hash-based signatures for the internet of things: Position paper. In Proceedings of the 15th ACM International Conference on Computing Frontiers, Ischia, Italy, 8–10 May 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 332–335. [Google Scholar] [CrossRef]
- Suhail, S.; Hussain, R.; Khan, A.; Hong, C.S. On the Role of Hash-Based Signatures in Quantum-Safe Internet of Things: Current Solutions and Future Directions. IEEE Internet Things J. 2021, 8, 1–17. [Google Scholar] [CrossRef]
- Buchmann, J.; Dahmen, E.; Hülsing, A. XMSS—A practical forward secure signature scheme based on minimal security assumptions. In Proceedings of the International Workshop on Post-Quantum Cryptography, Taipei, Taiwan, 29 November–2 December 2011; Volume 7071, pp. 117–129. [Google Scholar] [CrossRef] [Green Version]
- Bernstein, D.J.; Hopwood, D.; Hülsing, A.; Lange, T.; Niederhagen, R.; Papachristodoulou, L.; Schneider, M.; Schwabe, P.; Wilcox-O’hearn, Z. SPHINCS: Practical stateless hash-based signatures. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Volume 9056, pp. 368–397. [Google Scholar] [CrossRef] [Green Version]
- Reyzin, L.; Reyzin, N. Better than BiBa: Short one-time signatures with fast signing and verifying. In Proceedings of the Australasian Conference on Information Security and Privacy, Perth, WA, Australia, 3–5 July 2002; Volume 2384, pp. 144–153. [Google Scholar] [CrossRef]
- Lee, J.; Kim, S.; Cho, Y.; Chung, Y.; Park, Y. HORSIC: An efficient one-time signature scheme for wireless sensor networks. Inf. Process. Lett. 2012, 112, 783–787. [Google Scholar] [CrossRef]
- Hülsing, A. W-OTS+—Shorter signatures for hash-based signature schemes. In Proceedings of the International Conference on Cryptology in Africa, Cairo, Egypt, 22–24 June 2013; Volume 7918, pp. 173–188. [Google Scholar] [CrossRef]
- Merkle, R.C. A certified digital signature. In Advances in Cryptology—CRYPTO’ 89 Proceedings; Brassard, G., Ed.; Springer: New York, NY, USA, 1989; pp. 218–238. [Google Scholar]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography, 3rd ed.; Chapman & Hall/CRC: London, UK, 2020. [Google Scholar]
- Kudinov, M.A.; Kiktenko, E.O.; Fedorov, A.K. Security analysis of the W-OTS+ signature scheme: Updating security bounds. arXiv 2020, arXiv:2002.07419. [Google Scholar]
- Dods, C.; Smart, N.P.; Stam, M. Hash based digital signature schemes. In Cryptography and Coding; Smart, N.P., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 96–115. [Google Scholar]
- Dahmen, E.; Okeya, K.; Takagi, T.; Vuillaume, C. Digital signatures out of second-preimage resistant hash functions. In Proceedings of the 2nd International Workshop on Post-Quantum Cryptography, Cincinnati, OH, USA, 17–19 October 2020; Springer: Berlin/Heidelberg, Germany, 2008; pp. 109–123. [Google Scholar] [CrossRef]
- Brassard, G.; HØyer, P.; Tapp, A. Quantum cryptanalysis of hash and claw-free functions. In Latin American Symposium on Theoretical Informatics; Springer: Berlin/Heidelberg, Germany, 1998; pp. 163–169. [Google Scholar] [CrossRef] [Green Version]
- Lamport, L. Constructing Digital Signatures from a One Way Function; Technical Report CSL-98; SRI International Computer Science Laboratory: Menlo Park, CA, USA, 1979. [Google Scholar]
- Buchmann, J.; Dahmen, E.; Ereth, S.; Hülsing, A.; Rückert, M. On the security of the Winternitz one-time signature scheme. Int. J. Appl. Cryptogr. 2013, 3, 84–96. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Collision-resistant hashing: Towards making UOWHFs practical. In Advances in Cryptology—CRYPTO ’97; Kaliski, B.S., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; pp. 470–484. [Google Scholar]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; Association for Computing Machinery: New York, NY, USA, 1993; pp. 62–73. [Google Scholar] [CrossRef]
- Andrews, G.E. The Theory of Partitions; Encyclopedia of Mathematics and Its Applications, Cambridge University Press: Cambridge, UK, 1984. [Google Scholar] [CrossRef]
- Asharov, G.; Segev, G. On constructing one-way permutations from indistinguishability obfuscation. In TCC (A2); Springer: Berlin/Heidelberg, Germany, 2016; pp. 512–541. [Google Scholar] [CrossRef]
- Lenstra, A.K. Key Length. Contribution to The Handbook of Information Security. 2004. Available online: https://infoscience.epfl.ch/record/164539/files/NPDF-32.pdf (accessed on 10 August 2021).
- FIPS Publication 180-1, Secure Hash Standard. 1995. National Institute of Standards and Technology (NIST). Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/FIPS/fipspub180-1.pdf (accessed on 10 August 2021).
- Dobbertin, H.; Bosselaers, A.; Preneel, B. RIPEMD-160: A strengthened version of RIPEMD. In Fast Software Encryption; Gollmann, D., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; pp. 71–82. [Google Scholar]
- Aumasson, J.P.; Endignoux, G. Clarifying the Subset-Resilience Problem; Report 2017/909; Cryptology ePrint Archive: Lyon, France, 2017. [Google Scholar]
- Perrig, A. The BiBa one-time signature and broadcast authentication protocol. In Proceedings of the 8th ACM Conference on Computer and Communications Security—CCS ’01, Philadelphia, PA, USA, 5–8 November 2001; Association for Computing Machinery (ACM): New York, NY, USA, 2001; p. 28. [Google Scholar] [CrossRef]
- Crypto++ 5.6.0 Benchmarks. Available online: https://www.cryptopp.com/benchmarks.html (accessed on 6 August 2021).
| OW | SPR | CR | |
|---|---|---|---|
| Classical | |||
| Quantum |
| Scheme | Key Gen. | Signing | Verification | Sig. Size | V. K. Size | Security Level |
|---|---|---|---|---|---|---|
| HORS() | t | 1 | ||||
| HORST() | 1 | n | ||||
| HORSIC+() | Equation (34) | |||||
| HORS() | 1024 | 1 | 17 | 96 | ||
| HORST() | 2047 | 1 | 128 | 96 | ||
| HORSIC+() | 13,312 | |||||
| HORS() | 65,536 | 1 | 33 | 352 | ||
| HORST() | 131,071 | 1 | 256 | 352 | ||
| HORSIC+() | 655,360 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Park, Y. HORSIC+: An Efficient Post-Quantum Few-Time Signature Scheme. Appl. Sci. 2021, 11, 7350. https://doi.org/10.3390/app11167350
Lee J, Park Y. HORSIC+: An Efficient Post-Quantum Few-Time Signature Scheme. Applied Sciences. 2021; 11(16):7350. https://doi.org/10.3390/app11167350
Chicago/Turabian StyleLee, Jaeheung, and Yongsu Park. 2021. "HORSIC+: An Efficient Post-Quantum Few-Time Signature Scheme" Applied Sciences 11, no. 16: 7350. https://doi.org/10.3390/app11167350
APA StyleLee, J., & Park, Y. (2021). HORSIC+: An Efficient Post-Quantum Few-Time Signature Scheme. Applied Sciences, 11(16), 7350. https://doi.org/10.3390/app11167350







