Malicious Powershell Detection Using Graph Convolution Network
Abstract
:1. Introduction
2. Related Work
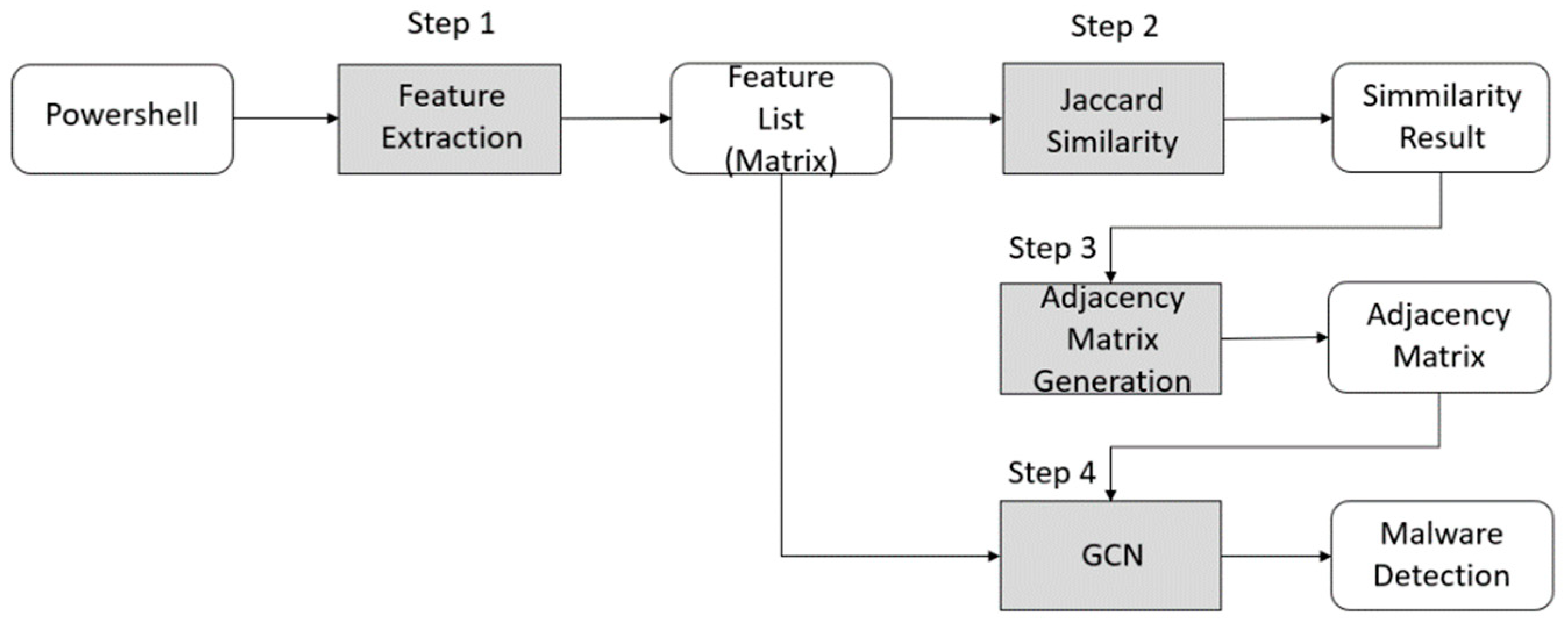
3. Malicious Powershell Detection Method Using Graph Convolution Network (GCN)
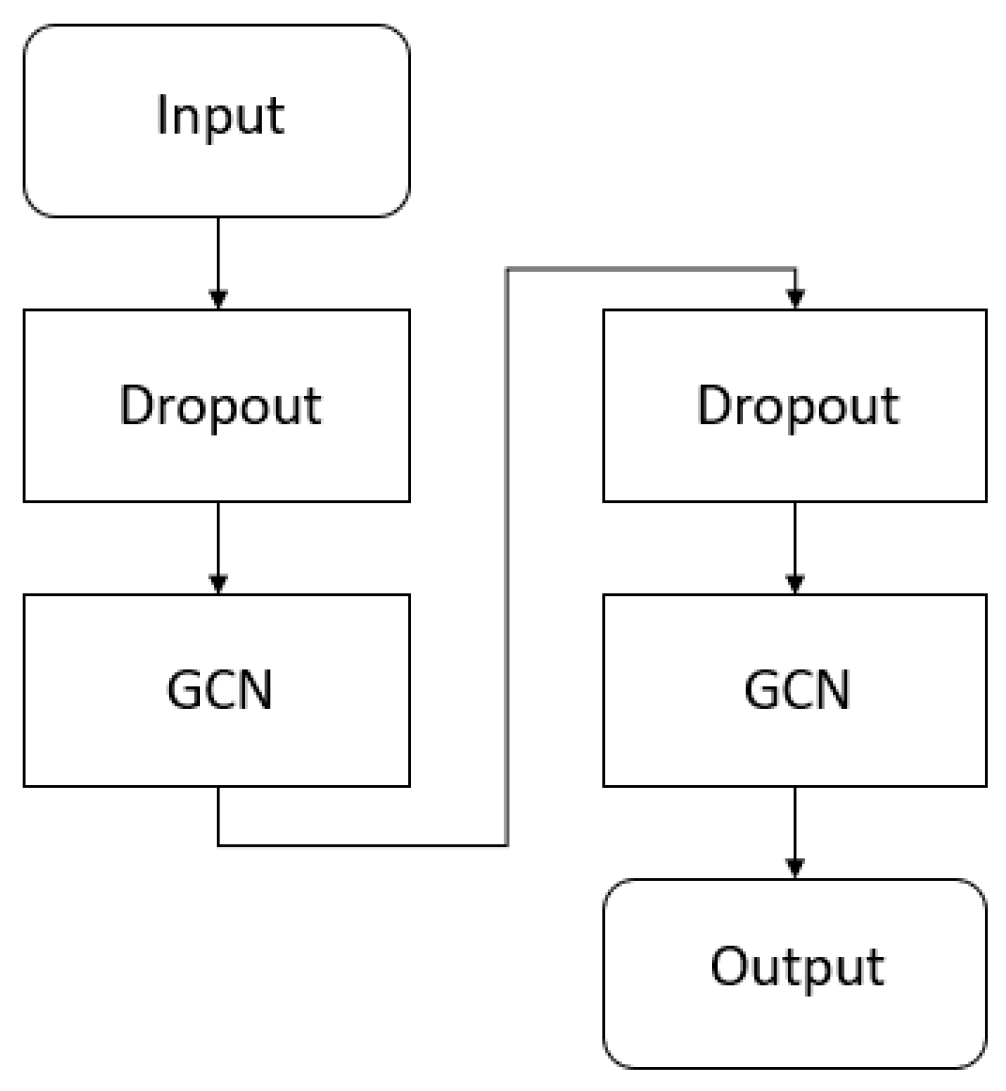
3.1. Graph Convolution Network (GCN)
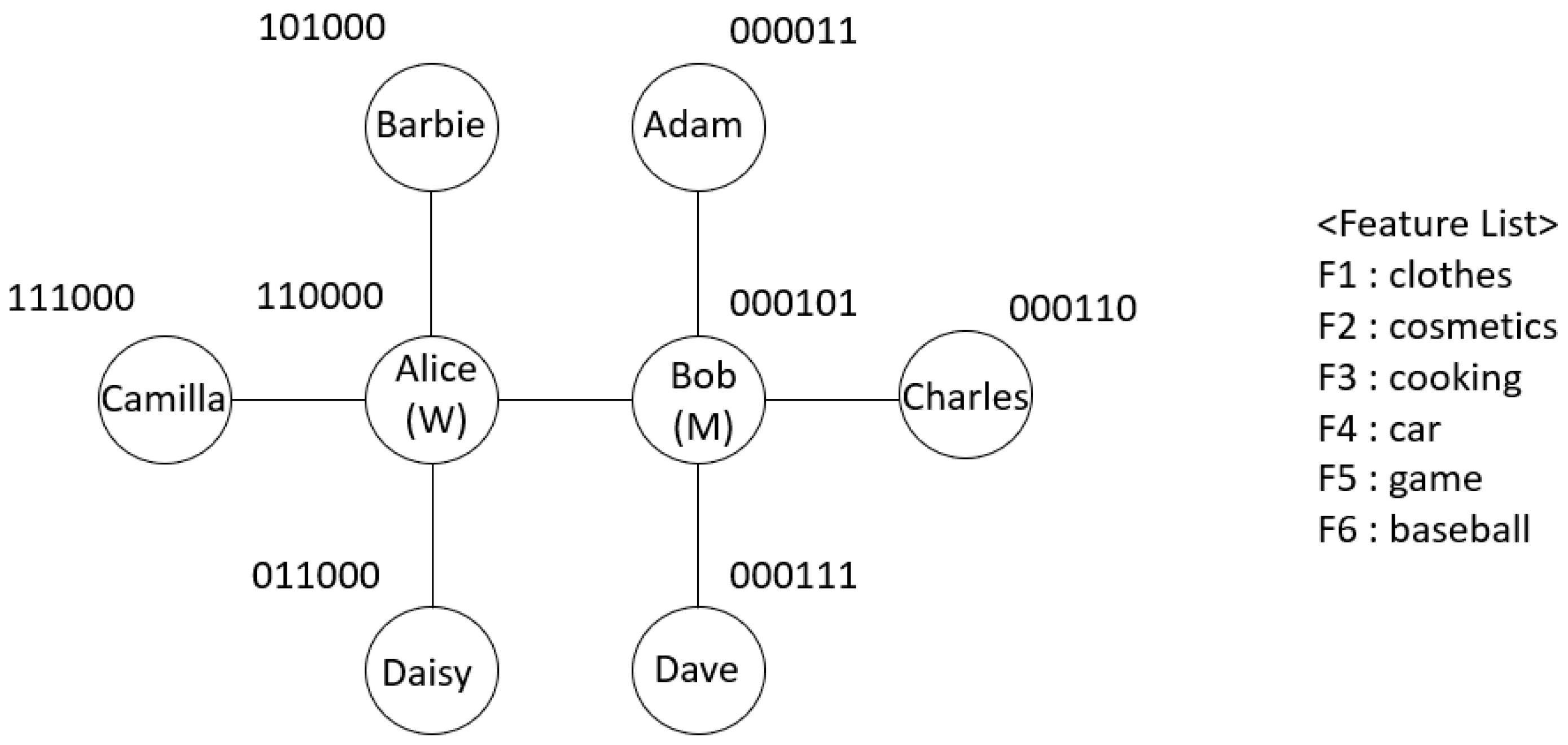
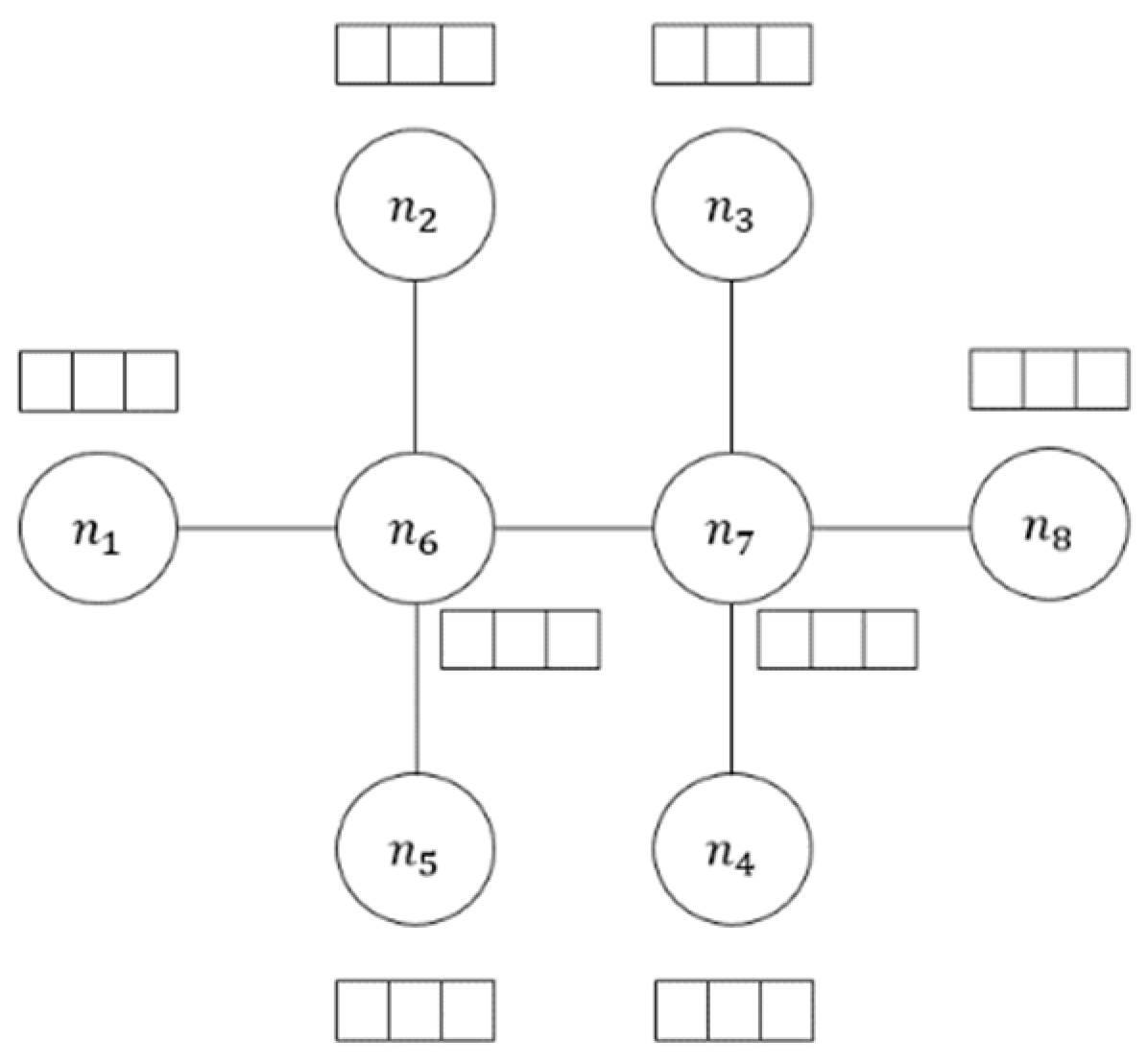
3.2. Malicious Powershell Detection Method Using Adjacency Matrix from Jaccard Similarity
4. Experimental Results
4.1. Setup
4.2. Results
4.2.1. Number of Adjacent Nodes
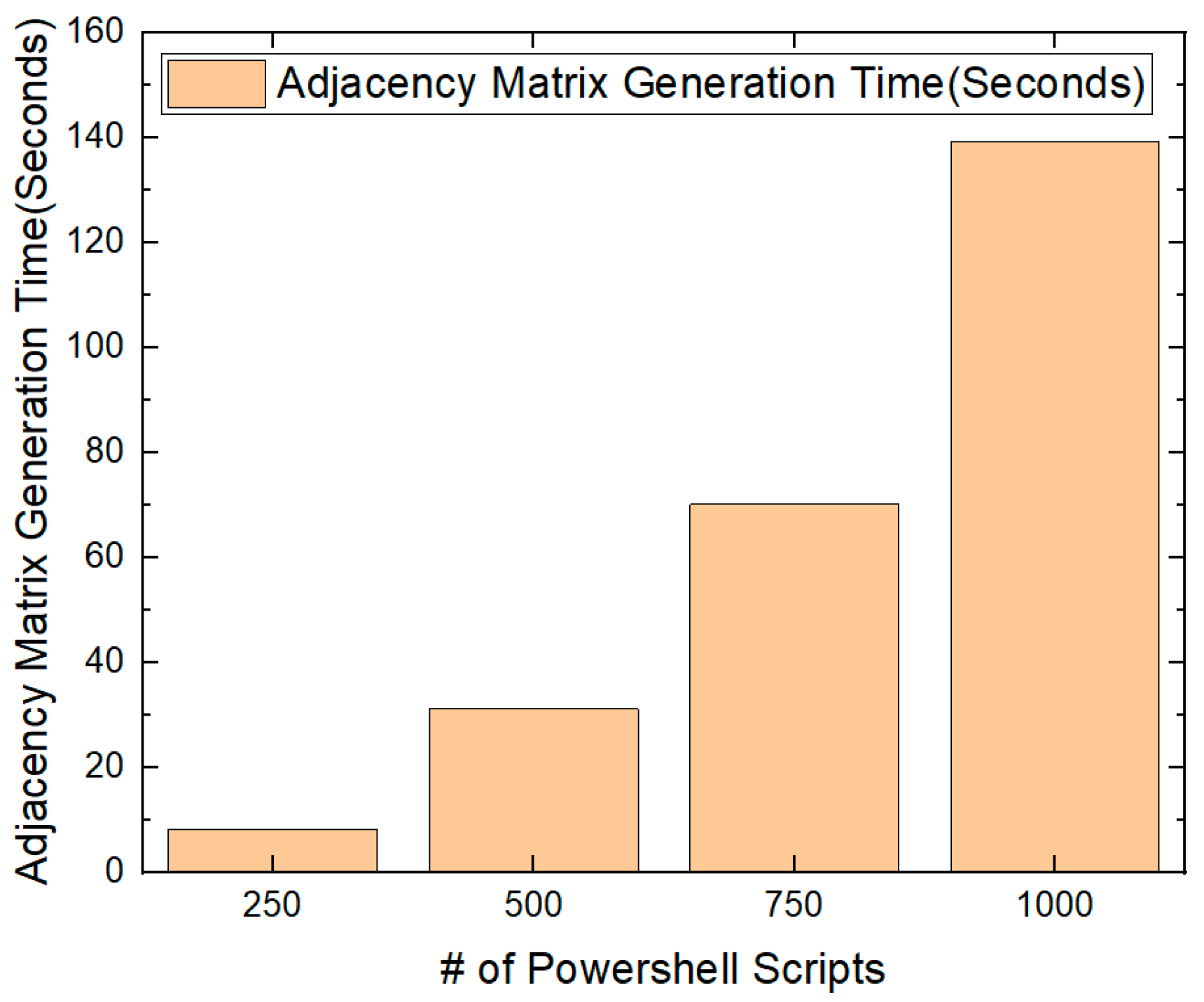
4.2.2. Number of Powershell Scripts
4.2.3. Adjacency Matrix Generation
4.2.4. GCN Training Time
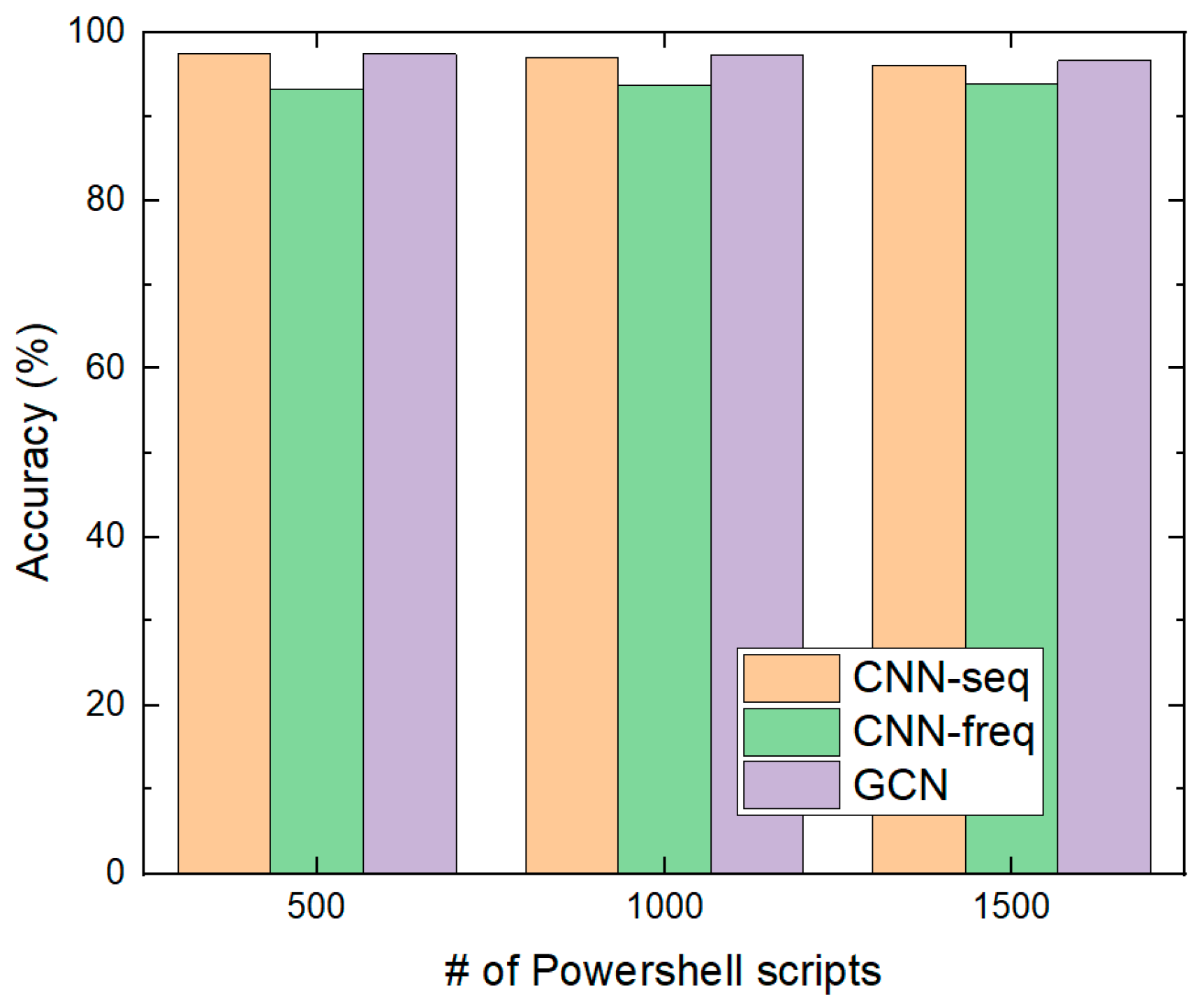
4.2.5. Comparison with Other Research
5. Discussion
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- AV-TEST. Available online: https://www.av-test.org/fileadmin/pdf/security-report/AV-TEST_Security_Report_2018-2019.pdf (accessed on 1 July 2021).
- Hendler, D.; Kels, S.; Rubin, A. Detecting malicious powershell commands using deep neural networks. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security, Incheon, Korea, 29 May 2018. [Google Scholar]
- Song, J.; Kim., J.; Choi, S.; Kim, J.; Kim, I. Implementation of a static powershell analysis based on the cnn-lstm model with token optimizations. In Proceedings of the WISA Workshop, Jeju, Korea, 21–24 August 2019. [Google Scholar]
- Krizhevsky, A.; Sutskever, I.; Hinton, G.E. Imagenet classification with deep convolutional neural networks. Adv. Neural Inf. Process. Syst. 2012, 25, 1097–1105. [Google Scholar] [CrossRef]
- Sutskever, I.; Vinyals, O.; Le, Q.V. Sequence to sequence learning with neural networks. In Proceedings of the 27th International Conference on Neural Information Processing Systems, Montreal, QC, Canada, 8–13 December 2014. [Google Scholar]
- Gibert, D. Convolutional Neural Networks for Malware Classification. Master’s Thesis, Universitat de Barcelona, Barcelona, Spain, 2016. [Google Scholar]
- Pascanu, R.; Stokes, J.W.; Sanossian, H.; Marinescu, M.; Thomas, A. Malware classification with recurrent networks. In Proceedings of the 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brisbane, Australia, 19–24 April 2015; pp. 1916–1920. [Google Scholar]
- Kipf, T.N.; Welling, M. Semi-supervised classification with graph convolutional networks. In Proceedings of the 5th International Conference on Learning Representations, Toulon, France, 24–26 April 2017. [Google Scholar]
- Wu, Z.; Pan, S.; Chen, F.; Long, G.; Zhang, C.; Yu, P.S.; Wu, Z.; Pan, S.; Chen, F.; Long, G.; et al. A Comprehensive Survey on Graph Neural Networks. IEEE Trans. Neural Netw. Learn. Syst. 2021, 32, 4–24. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fan, W.; Ma, Y.; Li, Q.; He, Y.; Zhao, E.; Tang, J.; Yin, D. Graph neural networks for social recommendation. In Proceedings of the World Wide Web Conference (WWW), San Francisco, CA, USA, 13 May 2019. [Google Scholar]
- Jaccard Index. Available online: https://deepai.org/machine-learning-glossary-and-terms/jaccard-index (accessed on 1 July 2021).
- Yan, J.; Yan, G.; Jin, D. Classifying malware represented as control flow graphs using deep graph convolutional neural network. In Proceedings of the 2019 49th IEEE/IFIP International Conference on Dependable Systems and Networks, Portland, OR, USA, 24 June 2019. [Google Scholar]
- Pei, X.; Yu, L.; Tian, S. AMalNet: A deep learning framework based on graph convolutional networks for malware detection. Comput. Secur. 2020, 93, 101792. [Google Scholar] [CrossRef]
- Hong, Y.; Hu, Y.; Lai, C.-M.; Wu, S.F.; Neamtiu, I.; McDaniel, P.; Yu, P.; Cam, H.; Ahn, G.-J. Defining and Detecting Environment Dricrimination in Android Apps. In Proceedings of the International Conference on Security and Privacy in Communication Networks: SecureComm 2017, Niagara Falls, ON, Canada, 22–25 October 2017. [Google Scholar]
- DeFreez, D.; Thakur, A.V.; Rubio-González, C. Path-Based Function Embedding and Its Application to Error-Handling Specification Mining. In Proceedings of the 2018 26th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Lake Buena Vista, FL, USA, 26 October 2018. [Google Scholar]
- Zachary’s Karate Club. Available online: https://konect.cc/networks/ucidata-zachary/ (accessed on 1 July 2021).
- Degree Matrix. Available online: https://faculty.math.illinois.edu/Macaulay2/doc/Macaulay2-1.16/share/doc/Macaulay2/Graphs/html/_degree__Matrix.html (accessed on 1 July 2021).
- PSParser. Available online: https://npmjs.com/package/psparser (accessed on 13 May 2021).
- Electronics and Telecommunication Research Institute (ETRI). Available online: https://etri.re.kr (accessed on 14 May 2021).
- Keras-gcn. Available online: https://github.com/tkipf/keras-gcn (accessed on 14 May 2021).
- A Gentle Introduction to k-Fold Cross Validation. Available online: https://machinelearningmastery.com/k-fold-cross-valication/ (accessed on 1 July 2021).
- Keras. Available online: https://keras.io (accessed on 14 May 2021).
- Identity Matrix. Available online: https://sciencedirect.com/topics/mathematics/identitymatrix (accessed on 1 July 2021).
- Choi, S. Malicious PowerShell Detection Using Attention against Adversarial Attacks. Electron 2020, 9, 1817. [Google Scholar] [CrossRef]
- Mimura, M.; Tajiri, Y. Static detection of malicious PowerShell based on word embeddings. Internet Things 2021, 15, 100404. [Google Scholar] [CrossRef]
- Longest Common Subsequence Problem. Available online: https://ics.uci.edu/~eppstein/151/960229.html (accessed on 1 July 2021).

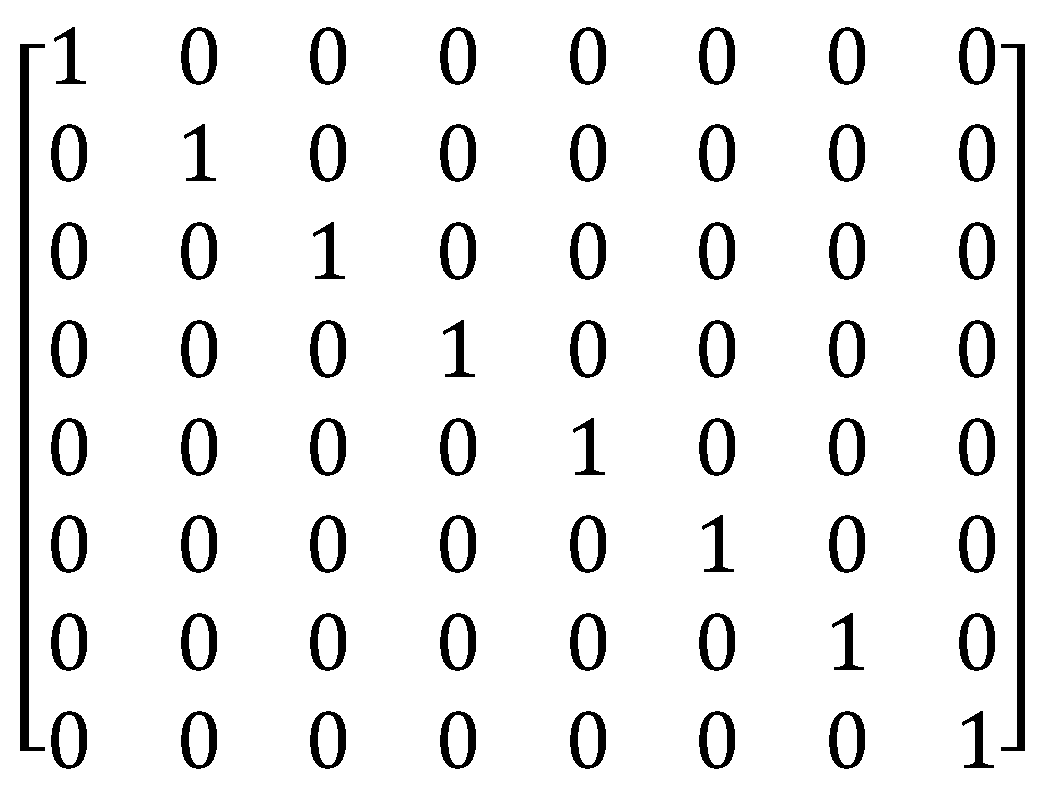
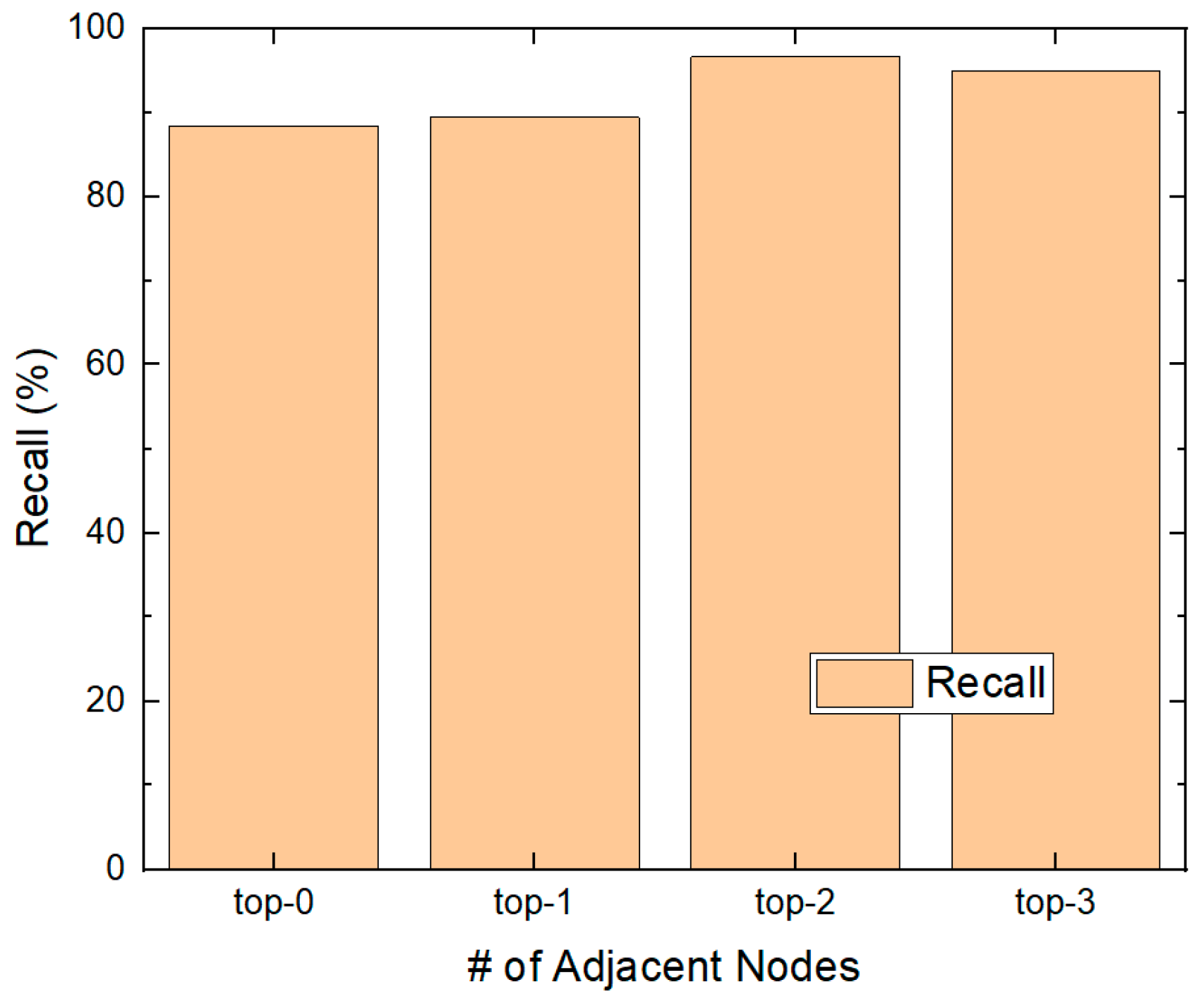




| TP | FN | FP | TN | Recall | FPR | Acc | |
|---|---|---|---|---|---|---|---|
| Top-0 | 88.4 | 11.6 | 1 | 99 | 88.4 | 1 | 93.7 |
| Top-1 | 89.4 | 10.6 | 0.8 | 99.2 | 89.4 | 0.8 | 94.3 |
| Top-2 | 96.6 | 3.4 | 2 | 98 | 96.6 | 2 | 97.3 |
| Top-3 | 95 | 5 | 2 | 98 | 95 | 2 | 96.5 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, S. Malicious Powershell Detection Using Graph Convolution Network. Appl. Sci. 2021, 11, 6429. https://doi.org/10.3390/app11146429
Choi S. Malicious Powershell Detection Using Graph Convolution Network. Applied Sciences. 2021; 11(14):6429. https://doi.org/10.3390/app11146429
Chicago/Turabian StyleChoi, Sunoh. 2021. "Malicious Powershell Detection Using Graph Convolution Network" Applied Sciences 11, no. 14: 6429. https://doi.org/10.3390/app11146429
APA StyleChoi, S. (2021). Malicious Powershell Detection Using Graph Convolution Network. Applied Sciences, 11(14), 6429. https://doi.org/10.3390/app11146429





