Search-Space Reduction for S-Boxes Resilient to Power Attacks
Abstract
:1. Introduction
2. Basic Concepts
| Factorial | Stirling’s Formula | Upper Bound | Lower Bound |
|---|---|---|---|
| 70! | |||
| 56! | |||
| 28! | |||
| 8! |
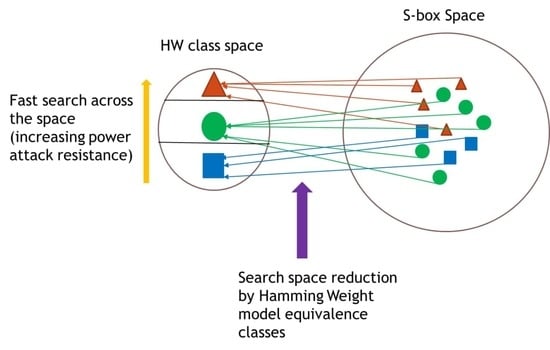
3. Our Contributions: Reduction of the S-Boxes Search-Space into a Hamming Weight Class SEARCH-Space
3.1. S-Boxes HW Equivalent
3.2. Redefining the Equivalence Relation and the HW Classes
- : inputs x such that .
- : inputs x such that .
- : inputs x such that .
- : inputs x such that .
- .
- .
- C(FAES)2 = {5,6,9,24,50,54,5c,5f,71,72,7a,7d,7e,7f,91,9d,b3,b8,c0,c3,c4,cb,cf,e2,e6,ed,f3,ff}.
- .
- .
- .
- .
- .
- .
3.3. Generation of HW Equivalent S-Boxes. ESboxG Algorithm
| Algorithm 1 ESboxG |
| Input: S-box s Integer //Number of sets to be swapped Integer // Max number of outputs that can be swapped Output: S-box r // HW equivalent with s 1: Select weights 2: for each k weight do 3: create two lists and // where each input holds in 4: end for 5: for each of the selected k weights do 6: 7: for to do 8: 9: end for 10: end for 11: return r |
- The maximum complexity is reached when all elements of all sub-assemblies are exchanged (maximum values of and ).
- The complexity can be reduced by exchanging only elements of a single subset .
- The minimum complexity is reached when only two elements are permuted within a single subset ().
- 1.
- The S-boxes of a class are generated by permuting the elements inside the sets
- 2.
- The sets and have a single element.
3.4. Experimental Verification That all S-Boxes of a Class Have the Same Resistance to Power Attacks
3.5. Experimental Verification of the Constant Value of Confusion Coefficient Variance CCV within HW Classes
- ;
- ;
- ; and
- .
3.6. New Search Strategy for S-Boxes Resistant to Power Attacks Based on HW Classes
3.7. Comparison between the Partition of the Space of S-Boxes in Related Classes and Hamming Weight Classes
- 1.
- Constant cryptographic properties within classes.
- –
- The nonlinearity is constant within each class: the classes, by way of construction, fulfill the property that all the S-boxes of a class have the same nonlinearity value. This ensures that all S-boxes in a class have the same resistance against linear attacks.
- –
- Other cryptographic properties are not constant within each class since they were not taken into account for the definition of these classes. For example, the resistance to power attacks is not constant within the class; if measured with the theoretical metric of the confusion coefficient variance (CCV), this metric can take different values for S-boxes that belong to the same class.
- 2.
- Movement between classes and within classes.
- –
- Movement within each class: Given an S-box , to obtain another S-box of the same class, transformations related to are performed.
- –
- Movement between different classes: Given an S-box , to obtain another S-box belonging to a different class, it is enough that affine transformations do not relate the two S-boxes.
- 3.
- Number of classes.
- –
- The number of affine classes is approximately , where is the linear or affine group size, as estimated in [27].
- 1.
- Constant cryptographic properties within classes.
- –
- The variance of the confusion coefficient variance (CCV) is constant within each class: the “theoretical” resistance to power attacks is constant within the class. The HW classes, by the way of construction, fulfill the property that all the S-boxes of a class have the same value of the confusion coefficient variance (CCV). This ensures that all S-boxes in a class have the same “theoretical” resistance against power attacks, based on this metric.
- –
- None of the known theoretical metrics of resistance against Power Attacks is exact, nor is the confusion coefficient variance (CCV), therefore, the actual resistance against these attacks is “approximately” constant within the class.
- –
- Other cryptographic properties are not constant within each class, since they were not taken into account for the definition of these classes. For example, nonlinearity can take different values for S-boxes that belong to the same Hamming weight class.
- 2.
- Movement between classes and within classes.
- –
- Movement within each class: Given an S-box , to obtain another S-box of the same class, it is necessary and sufficient to swap between two elements of the output of that have the same Hamming weight. The swap can be generalized between several pairs of elements, as long as the two elements of each pair have the same weight, which can be different between the pairs.
- –
- Movement between different classes: Given an S-box , to obtain another S-box belonging to a different class, it is necessary and sufficient to perform the swap between two elements of the output that have different Hamming weights.
- 3.
- Number of classes.
- –
- The number of classes and the number of S-boxes in each class are estimated in this work (by two different ways) for any n, by means of Propositions 5 and 6.
- –
- The number of classes is exponentially less than the number of S-boxes.
- –
- For , in Partition of the 3 × 3S-box space into equivalence classes, the list of the 1120 HW classes is given.
3.8. Quantifying the Search-Space Reduction Achieved Using the Partition into HW Classes Instead of Searching by S-Boxes
3.8.1. Estimate of the Number of HW Classes and the Number of S-Boxes in Each Class as Permutation with Repetition
- (a)
- The total number of HW equivalence classes is: .
- (b)
- The total number of S-boxes in each HW equivalence class is: .
3.8.2. Reduced Search-Space
3.8.3. Examples of the Number of HW Classes, the Number of S-Boxes per Class and the Reduction in Search-Space Achieved with the New Proposed Strategy
3.8.4. Estimation of the Number of HW classes and the Number of S-boxes in Each Class as an Occupation Problem
- (a)
- The number of “” equivalence classes is equal to:
- (b)
- The number of S-boxes within each HW equivalence class is exactly equal to:
3.9. Examples Using Proposition 6
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A Example S-Box 4×4 Equivalent to the PRESENT Cipher S-Box from Its HW Class
| 0 | 1 | 2 | 3 | |
| 0 | 2 | 2 | 2 | 3 |
| 1 | 2 | 0 | 2 | 3 |
| 2 | 2 | 3 | 4 | 1 |
| 3 | 1 | 3 | 1 | 1 |
| 0 | 1 | 2 | 3 | |
| 0 | C | 5 | 6 | B |
| 1 | 9 | 0 | A | D |
| 2 | 3 | E | F | 8 |
| 3 | 2 | 7 | 1 | 4 |
Appendix B S-Box 8 × 8 Equivalent to the AES Cipher S-Box from Its HW Class
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 4 | 5 | 6 | 6 | 5 | 5 | 6 | 4 | 2 | 1 | 5 | 4 | 7 | 6 | 5 | 5 |
| 1 | 4 | 2 | 4 | 6 | 6 | 4 | 4 | 4 | 5 | 4 | 3 | 6 | 4 | 3 | 4 | 2 |
| 2 | 6 | 7 | 4 | 3 | 4 | 6 | 7 | 4 | 3 | 4 | 5 | 5 | 4 | 4 | 3 | 3 |
| 3 | 1 | 5 | 3 | 4 | 2 | 4 | 2 | 4 | 3 | 2 | 1 | 4 | 6 | 4 | 4 | 5 |
| 4 | 2 | 3 | 3 | 3 | 4 | 5 | 4 | 2 | 3 | 5 | 5 | 5 | 3 | 5 | 5 | 2 |
| 5 | 4 | 4 | 0 | 6 | 1 | 6 | 4 | 5 | 4 | 5 | 6 | 4 | 3 | 3 | 3 | 6 |
| 6 | 3 | 7 | 4 | 7 | 3 | 4 | 4 | 3 | 3 | 6 | 1 | 7 | 2 | 4 | 6 | 3 |
| 7 | 3 | 4 | 1 | 5 | 3 | 5 | 3 | 6 | 5 | 5 | 5 | 2 | 1 | 8 | 6 | 4 |
| 8 | 5 | 2 | 3 | 5 | 6 | 5 | 2 | 4 | 3 | 5 | 6 | 5 | 3 | 5 | 3 | 5 |
| 9 | 2 | 2 | 5 | 5 | 2 | 3 | 2 | 2 | 3 | 6 | 4 | 2 | 6 | 5 | 3 | 6 |
| A | 3 | 3 | 4 | 2 | 3 | 2 | 2 | 4 | 3 | 5 | 4 | 3 | 3 | 4 | 4 | 5 |
| B | 6 | 3 | 5 | 5 | 4 | 5 | 4 | 4 | 4 | 4 | 5 | 5 | 4 | 5 | 5 | 1 |
| C | 5 | 4 | 3 | 4 | 3 | 4 | 4 | 4 | 4 | 6 | 4 | 5 | 4 | 6 | 4 | 3 |
| D | 3 | 5 | 5 | 4 | 2 | 2 | 6 | 3 | 3 | 4 | 5 | 5 | 3 | 3 | 4 | 5 |
| E | 4 | 5 | 3 | 2 | 4 | 5 | 4 | 3 | 5 | 4 | 4 | 5 | 5 | 4 | 2 | 7 |
| F | 3 | 3 | 3 | 3 | 7 | 5 | 2 | 3 | 2 | 4 | 4 | 4 | 3 | 3 | 6 | 3 |
| x0 | xl | x2 | x3 | x4 | x5 | x6 | x7 | x8 | x9 | xa | xb | xc | xd | xe | xf | |
| 0x | 63 | f2 | 77 | 7b | 7c | 67 | 6f | c5 | 30 | 01 | 6b | 2b | fe | d7 | 76 | ab |
| lx | ca | 82 | c9 | 7d | fa | 59 | 47 | fO | ad | d4 | a2 | af | 9c | a4 | 72 | c0 |
| 2x | b7 | fd | 93 | 26 | 36 | 3f | f7 | ce | 34 | a5 | e5 | fl | 71 | d8 | 31 | 15 |
| 3x | 04 | c7 | 23 | c3 | lb | 96 | 05 | 9a | 07 | 12 | 80 | e2 | eb | 27 | b2 | 75 |
| 4x | 09 | 83 | 2c | la | lb | 6e | 5a | a0 | 52 | 3b | d6 | b3 | 29 | e3 | 2f | 84 |
| 5x | 53 | dl | 00 | ed | 20 | fe | bl | 5b | 6a | cb | be | 39 | la | 4c | 59 | cf |
| 6x | dO | ef | aa | fb | 43 | 4d | 33 | 85 | 45 | f9 | 02 | 7f | 50 | 3c | 9f | aa |
| 7x | 51 | a3 | 40 | 8f | 92 | 9d | 38 | fS | be | b6 | da | 21 | 10 | ff | f3 | d2 |
| 8x | cd | 0c | 13 | ec | 5f | 97 | 44 | 17 | c4 | a7 | 7e | 3d | 64 | 5d | 19 | 73 |
| 9x | 60 | 81 | 4f | de | 22 | 2a | 90 | 89 | 46 | ee | b8 | 14 | de | 5e | 0b | db |
| ax | e0 | 32 | 3a | 0a | 49 | 06 | 24 | 5e | c2 | d3 | ac | 62 | 91 | 95 | e4 | 79 |
| bx | e7 | c9 | 37 | 6d | 8d | d5 | 4e | a9 | 6c | 56 | f4 | ea | 65 | 7a | ae | 08 |
| ex | ba | 78 | 25 | 2e | le | a6 | b4 | c6 | e8 | dd | 74 | lf | 4b | bd | 8b | 9a |
| dx | 70 | 3e | b5 | 66 | 4b | 03 | f6 | 0e | 61 | 35 | 57 | b9 | 86 | el | ld | 9e |
| ex | el | f8 | 9b | 11 | 69 | d9 | be | 94 | 9b | le | 87 | e9 | ce | 55 | 2b | df |
| fx | be | al | 89 | 0d | b f | e6 | 42 | 69 | 41 | 99 | 2d | 0f | b0 | 54 | bb | 16 |
Appendix C
- Construction, by columns, of the 36 equivalent S-boxes from the HW class of the PRINT cipher’s S-box . All of them have .Let the S-box be of the PRINT cipher’s (Example 3).
Column 1 2 3 4 5 6 7 8 Input x to the
S-box0 1 2 3 4 5 6 7 Output 0 1 3 6 7 4 5 2 Hamming weight
of the output0 1 2 2 3 1 2 1 The class can be represented directly by the output weight vector: , of the last row; however, for the construction of the class, it is more convenient to use the representation through the sets = .Class construction:- –
- Column 1: Input 0 with output 0 of weight 0. Taking into account that, for the weight , the set has cardinal one, its elements cannot be permuted with each other, therefore all the S-boxes of the class satisfy that (Proposition 4).
- –
- Column 5: . Input 4, with output 7 of weight 3. Analogously for the weight , the set has cardinal one and its elements cannot be permuted with each other; therefore, all S-boxes of the class satisfy that (Proposition 4).
- –
- Columns 2, 6, and 8: . inputs with outputs of weight 1. The three outputs can be interchanged in Columns , without altering the weight of the outputs, and therefore the hypothetical leakage of the S-box is not altered according to the Hamming weight leakage model.
- –
- Columns 3, 4, and 7: . Inputs with outputs of weight 2.The three outputs can be interchanged in Columns without altering the weight of the outputs and therefore the hypothetical leakage of the S-box according to the Hamming weight leak model is not altered.Cartesian product of the two sets of permutations: By making the Cartesian product of the two sets of six permutations each in Columns and in Columns , keeping Columns 1 and 5 fixed, the 36 S-boxes of the class are obtained. Due to their construction, the 36 S-boxes have the same hypothetical leakage according to the. “Hamming weight” leakage model.The 36 S-boxes of this class are shown below (some rows are left blank to visualize the Cartesian product better).
| Row/Column | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| Input x to the S-box | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| S-box | 0 | 1 | 3 | 6 | 7 | 4 | 5 | 2 |
| S-box equiv. F2 | 0 | 1 | 3 | 5 | 7 | 4 | 6 | 2 |
| S-box equiv.F3 | 0 | 1 | 5 | 3 | 7 | 4 | 6 | 2 |
| S-box equiv.F4 | 0 | 1 | 5 | 6 | 7 | 4 | 3 | 2 |
| S-box equiv.F5 | 0 | 1 | 6 | 3 | 7 | 4 | 5 | 2 |
| S-box equiv.F6 | 0 | 1 | 6 | 5 | 7 | 4 | 3 | 2 |
| S-box equiv.F7 | 0 | 1 | 3 | 6 | 7 | 2 | 5 | 4 |
| S-box equiv.F8 | 0 | 1 | 3 | 5 | 7 | 2 | 6 | 4 |
| S-box equiv.F9 | 0 | 1 | 5 | 3 | 7 | 2 | 6 | 4 |
| S-box equiv.F10 | 0 | 1 | 5 | 6 | 7 | 2 | 3 | 4 |
| S-box equiv.F11 | 0 | 1 | 6 | 3 | 7 | 2 | 5 | 4 |
| S-box equiv.F12 | 0 | 1 | 6 | 5 | 7 | 2 | 3 | 4 |
| S-box equiv.F13 | 0 | 4 | 3 | 6 | 7 | 1 | 5 | 2 |
| S-box equiv.F14 | 0 | 4 | 3 | 5 | 7 | 1 | 6 | 2 |
| S-box equiv.F15 | 0 | 4 | 5 | 3 | 7 | 1 | 6 | 2 |
| S-box equiv.F16 | 0 | 4 | 5 | 6 | 7 | 1 | 3 | 2 |
| S-box equiv.F17 | 0 | 4 | 6 | 3 | 7 | 1 | 5 | 2 |
| S-box equiv.F18 | 0 | 4 | 6 | 5 | 7 | 1 | 3 | 2 |
| S-box equiv.F19 | 0 | 4 | 3 | 6 | 7 | 2 | 5 | 1 |
| S-box equiv.F20 | 0 | 4 | 3 | 5 | 7 | 2 | 6 | 1 |
| S-box equiv.F21 | 0 | 4 | 5 | 3 | 7 | 2 | 6 | 1 |
| S-box equiv.F22 | 0 | 4 | 5 | 6 | 7 | 2 | 3 | 1 |
| S-box equiv.F23 | 0 | 4 | 6 | 3 | 7 | 2 | 5 | 1 |
| S-box equiv.F24 | 0 | 4 | 6 | 5 | 7 | 2 | 3 | 1 |
| S-box equiv.F25 | 0 | 2 | 3 | 6 | 7 | 1 | 5 | 4 |
| S-box equiv.F26 | 0 | 2 | 3 | 5 | 7 | 1 | 6 | 4 |
| S-box equiv.F27 | 0 | 2 | 5 | 3 | 7 | 1 | 6 | 4 |
| S-box equiv.F28 | 0 | 2 | 5 | 6 | 7 | 1 | 3 | 4 |
| S-box equiv.F29 | 0 | 2 | 6 | 3 | 7 | 1 | 5 | 4 |
| S-box equiv.F30 | 0 | 2 | 6 | 5 | 7 | 1 | 3 | 4 |
| S-box equiv.F31 | 0 | 2 | 3 | 6 | 7 | 4 | 5 | 1 |
| S-box equiv.F32 | 0 | 2 | 3 | 5 | 7 | 4 | 6 | 1 |
| S-box equiv.F33 | 0 | 2 | 5 | 3 | 7 | 4 | 6 | 1 |
| S-box equiv.F34 | 0 | 2 | 5 | 6 | 7 | 4 | 3 | 1 |
| S-box equiv.F35 | 0 | 2 | 6 | 3 | 7 | 4 | 5 | 1 |
| S-box equiv.F36 | 0 | 2 | 6 | 5 | 7 | 4 | 3 | 1 |
- All classes. For , the 1120 HW equivalence classes were constructed. They can be seen by consulting the link:
References
- Avanzi, R. A Salad of Block Ciphers. The State of the Art in Block Ciphers and Their Analysis; IACR: Lyon, France, 2017. [Google Scholar]
- Kryszczuk, K. Springer Encyclopedia of Cryptography and Security; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Mihailescu, M.I.; Nita, S.L. Linear and Differential Cryptanalysis. In Pro Cryptography and Cryptanalysis; Springer: Berlin/Heidelberg, Germany, 2021; pp. 457–481. [Google Scholar]
- Biryukov, A.; De Cannière, C.; Braeken, A.; Preneel, B.A. A toolbox for cryptanalysis: Linear and affine equivalence algorithms. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2656, pp. 33–50. [Google Scholar] [CrossRef] [Green Version]
- Leander, G.; Poschmann, A. On the classification of 4 bit S-boxes. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4547 LNCS, pp. 159–176. [Google Scholar] [CrossRef]
- Nyberg, K. On the construction of highly nonlinear permutations. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1992; pp. 92–98. [Google Scholar]
- Ramamoorthy, V.; Silaghi, M.C.; Matsui, T.; Hirayama, K.; Yokoo, M. The design of cryptographic S-Boxes using CSPs. In Proceedings of the International Conference on Principles and Practice of Constraint Programming, Perugia, Italy, 12–16 September 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 54–68. [Google Scholar]
- Picek, S. Applications Of Evolutionary Computation to Cryptology. J. Chem. Inf. Model. 2015, 53, 1689–1699. [Google Scholar] [CrossRef]
- Picek, S.; Ege, B.; Papagiannopoulos, K.; Batina, L.; Jakobović, D. Optimality and beyond: The case of 4 × 4 S-boxes. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust, HOST, Arlington, VA, USA, 6–7 May 2014; pp. 80–83. [Google Scholar] [CrossRef]
- Prouff, E. DPA attacks and S-boxes. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3557, pp. 424–441. [Google Scholar] [CrossRef] [Green Version]
- Gupta, D.; Tripathy, S.; Mazumdar, B. Correlation Power Analysis of KASUMI and Power Resilience Analysis of Some Equivalence Classes of KASUMI S-Boxes. J. Hardw. Syst. Secur. 2020, 4, 297–313. [Google Scholar] [CrossRef]
- Carlet, C.; Heuser, A.; Picek, S. Trade-offs for S-boxes: Cryptographic properties and side-channel resilience. In Proceedings of the International Conference on Applied Cryptography and Network Security, Kanazawa, Japan, 10–12 July 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 393–414. [Google Scholar] [CrossRef]
- Chakraborty, K.; Sarkar, S.; Maitra, S.; Mazumdar, B.; Mukhopadhyay, D.; Prouff, E. Redefining the transparency order. Des. Codes Cryptogr. 2017, 82, 95–115. [Google Scholar] [CrossRef] [Green Version]
- Li, H.; Zhou, Y.; Ming, J.; Yang, G.; Jin, C. The Notion of Transparency Order, Revisited. Comput. J. 2020. [Google Scholar] [CrossRef]
- Picek, S.; Papagiannopoulos, K.; Ege, B.; Batina, L.; Jakobovic, D. Confused by confusion: Systematic evaluation of DPA resistance of various S-boxes. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8885, pp. 374–390. [Google Scholar] [CrossRef] [Green Version]
- Freyre-Echevarría, A.; Martínez-Díaz, I.; Legón-Pérez, C.M.; Sosa-Gómez, G.; Rojas, O. Evolving Nonlinear S-Boxes With Improved Theoretical Resilience to Power Attacks. IEEE Access 2020, 8, 202728–202737. [Google Scholar] [CrossRef]
- Xu, Y.; Wang, Q. Searching for Balanced S-Boxes with High Nonlinearity, Low Differential Uniformity, and Improved DPA-Resistance. In Proceedings of the International Conference on Information Security, Bali, Indonesia, 16–18 December 2020; Springer: Berlin/Heidelberg, Germany; pp. 95–106. [Google Scholar]
- Ng, J.S.; Chen, J.; Kyaw, N.A.; Lwin, N.K.Z.; Ho, W.G.; Chong, K.S.; Gwee, B.H. A Highly Efficient Power Model for Correlation Power Analysis (CPA) of Pipelined Advanced Encryption Standard (AES). In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 10–21 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Carlet, C. Vectorial Boolean Functions for Cryptography. In Boolean Models and Methods in Mathematics, Computer Science, and Engineering; Crama, Y., Hammer, P.L., Eds.; Cambridge University Press: Cambridge, UK, 2013; pp. 398–470. [Google Scholar] [CrossRef] [Green Version]
- Brier, E.; Clavier, C.; Olivier, F. Correlation power analysis with a leakage model. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3156, pp. 16–29. [Google Scholar] [CrossRef] [Green Version]
- Fei, Y.; Luo, Q.; Ding, A.A. A statistical model for DPA with novel algorithmic confusion analysis. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7428 LNCS, pp. 233–250. [Google Scholar] [CrossRef] [Green Version]
- Fei, Y.; Ding, A.A.; Lao, J.; Zhang, L. A Statistics-based Fundamental Model for Side-channel Attack Analysis. IACR Cryptol. EPrint Arch. 2014, 2014, 152. [Google Scholar]
- Heuser, A.; Rioul, O.; Guilley, S. A theoretical study of Kolmogorov-Smirnov distinguishers. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design, Paris, France, 13–15 April 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 9–28. [Google Scholar]
- Feller, W. An Introduction to Probability Theory and its Applications; John Wiley & Sons: Hoboken, NJ, USA, 2008; Volume 2. [Google Scholar]
- Veshchikov, N. SILK: High Level of Abstraction Leakage Simulator for Side Channel Analysis; ACM International Conference Proceeding Series; ACM: New York, NY, USA, 2014. [Google Scholar] [CrossRef]
- Lerman, L.; Markowitch, O.; Veshchikov, N. Comparing Sboxes of ciphers from the perspective of side-channel attacks. In Proceedings of the 2016 IEEE Asian Hardware Oriented Security and Trust Symposium, AsianHOST 2016, Taipei Area, Taiwan, 19–20 December 2016. [Google Scholar] [CrossRef]
- De Cannière, C. Analysis and Design of Symmetric Encryption Algorithms. Ph.D. Thesis, KULeuven, Leuven, Belgium, 2007. [Google Scholar]
- Knudsen, L.; Leander, G.; Poschmann, A.; Robshaw, M.J. PRINTcipher: A block cipher for IC-printing. In Lecture Notes in Computer Science; Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6225 LNCS, pp. 16–32. [Google Scholar] [CrossRef] [Green Version]
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|---|---|
| 0 | 1 | 3 | 6 | 7 | 4 | 5 | 2 | |
| 0 | 1 | 2 | 2 | 3 | 1 | 2 | 1 |
| n | Number of S-Boxes | Number of HW Classes | of S-Boxes in Each Class | |
|---|---|---|---|---|
| 3 | ∼ | 1120∼ | 36∼ | ∼ |
| 4 | ∼ | ∼ | ∼ | ∼ |
| 5 | ∼ | ∼ | ∼ | ∼ |
| 6 | ∼ | ∼ | ∼ | ∼ |
| 7 | ∼ | ∼ | ∼ | ∼ |
| 8 | 256∼ | ∼ | ∼ | ∼ |
| r | Estimated Value | Accumulated Product | |
|---|---|---|---|
| 0 | C(256, 1) = 256 | ∼ | ∼ |
| 1 | C(256-1, 8) = C(255, 8) | ∼ | ∼ |
| 2 | C(255-8, 28) = C(247, 28) | ∼ | ∼ |
| 3 | C(255-8, 28) = C(219, 56) | ∼ | ∼ |
| 4 | C(219-56, 70) = C(163, 70) | ∼ | ∼ |
| 5 | C(163-70, 56) = C(93, 56) | ∼ | ∼ |
| 6 | C(93-56, 28) = C(37, 28) | ∼ | ∼ |
| 7 | C(37-28, 8) = C(9, 8) = 9 | ∼ | ∼ |
| 8 | C(9-8, 1) = C(1, 1) = 1 | ∼ | ∼ |
| # of classes | Exactly | Approximately ∼ |
| Estimated Number of HW Classes of | |
|---|---|
| Proposition 5 | ∼ |
| Proposition 6 | ∼ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Legón-Pérez, C.M.; Sánchez-Muiña, R.; Miyares-Moreno, D.; Bardaji-López, Y.; Martínez-Díaz, I.; Rojas, O.; Sosa-Gómez, G. Search-Space Reduction for S-Boxes Resilient to Power Attacks. Appl. Sci. 2021, 11, 4815. https://doi.org/10.3390/app11114815
Legón-Pérez CM, Sánchez-Muiña R, Miyares-Moreno D, Bardaji-López Y, Martínez-Díaz I, Rojas O, Sosa-Gómez G. Search-Space Reduction for S-Boxes Resilient to Power Attacks. Applied Sciences. 2021; 11(11):4815. https://doi.org/10.3390/app11114815
Chicago/Turabian StyleLegón-Pérez, Carlos Miguel, Ricardo Sánchez-Muiña, Dianne Miyares-Moreno, Yasser Bardaji-López, Ismel Martínez-Díaz, Omar Rojas, and Guillermo Sosa-Gómez. 2021. "Search-Space Reduction for S-Boxes Resilient to Power Attacks" Applied Sciences 11, no. 11: 4815. https://doi.org/10.3390/app11114815
APA StyleLegón-Pérez, C. M., Sánchez-Muiña, R., Miyares-Moreno, D., Bardaji-López, Y., Martínez-Díaz, I., Rojas, O., & Sosa-Gómez, G. (2021). Search-Space Reduction for S-Boxes Resilient to Power Attacks. Applied Sciences, 11(11), 4815. https://doi.org/10.3390/app11114815