SDN-based VANETs, Security Attacks, Applications, and Challenges
Abstract
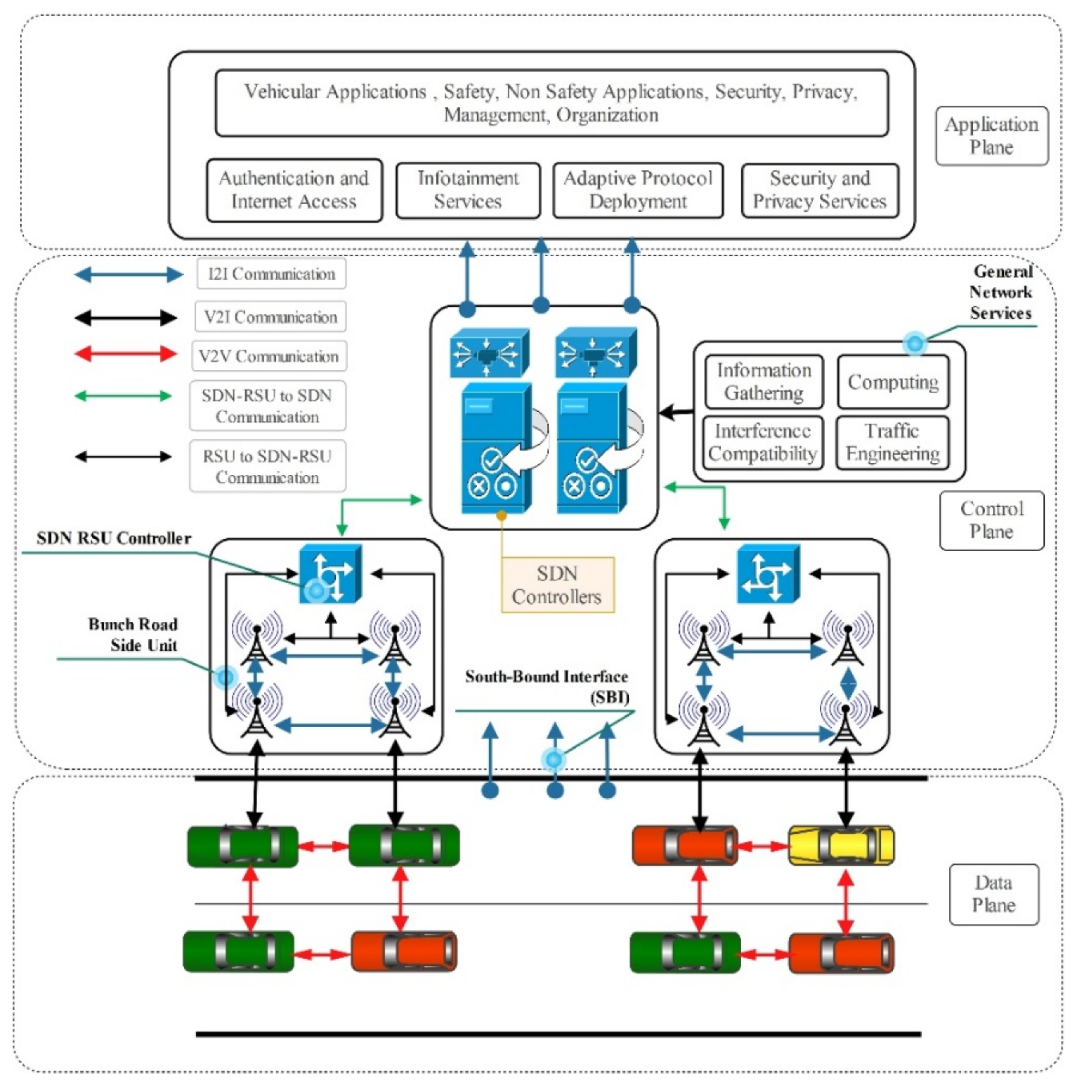
1. Introduction
1.1. Data Plane
1.2. Control Plane
1.3. Application Plane
1.4. The relationship of SDN and Network Function Virtualization (NFV)
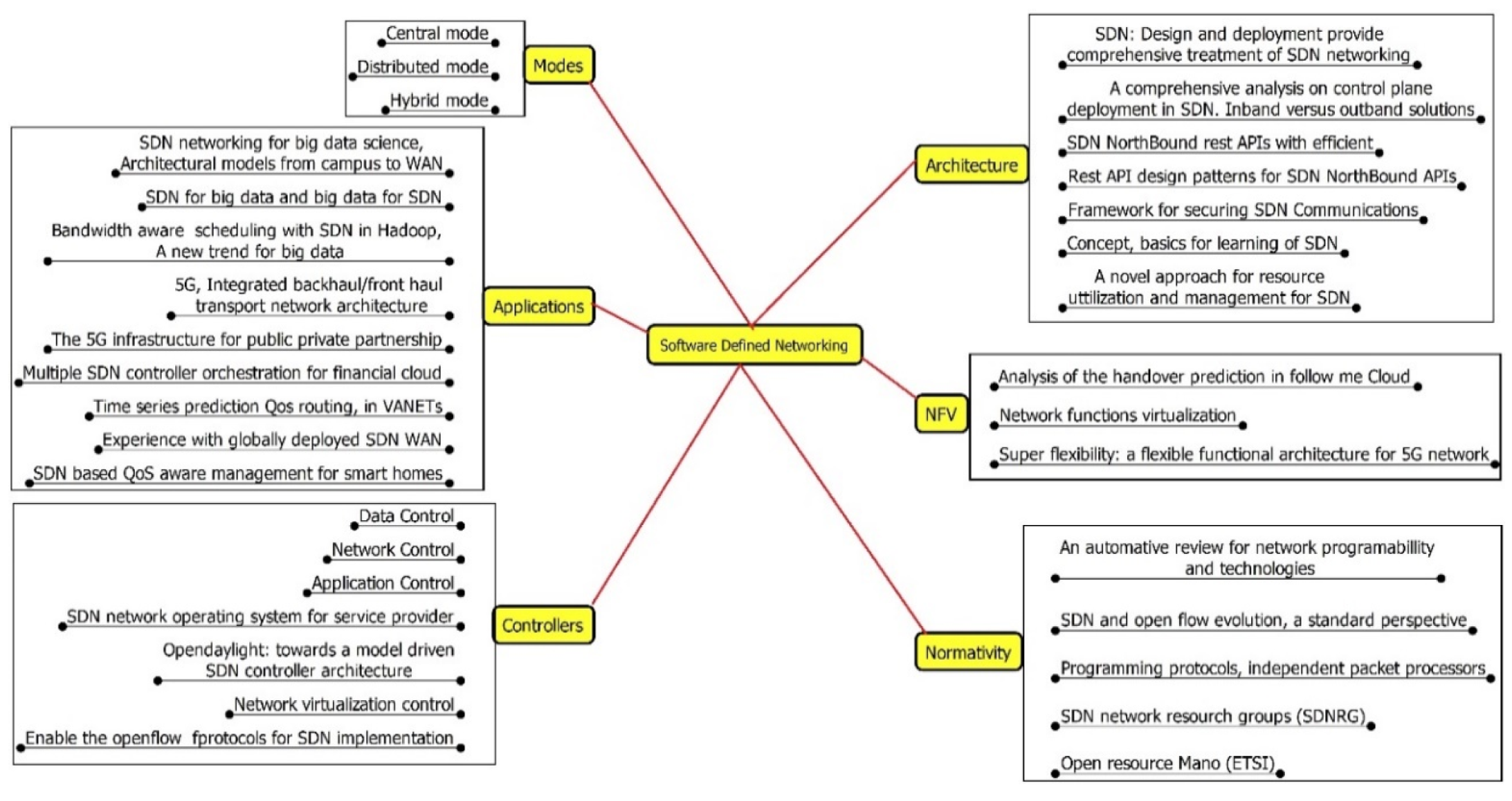
2. Evolution of SDN Control Architecture for VANETs
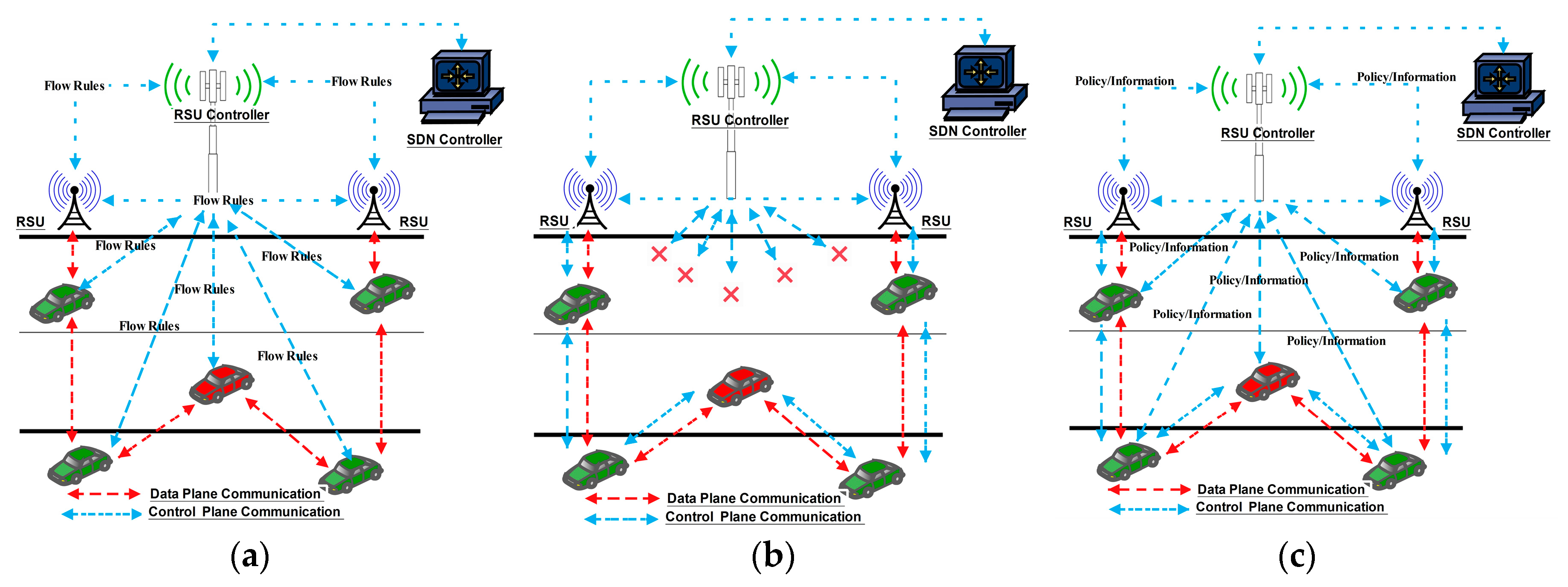
2.1. Centralized Controller Model
2.2. Distributed Controller Model
2.3. Hybrid Controller Architecture
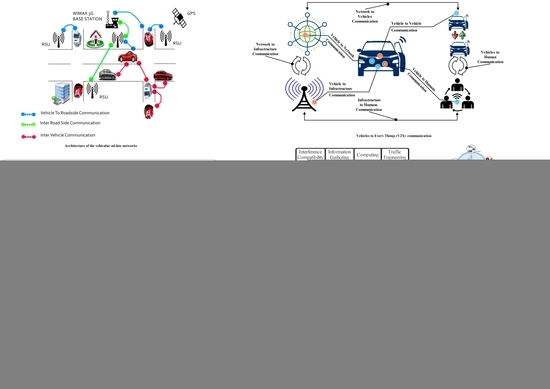
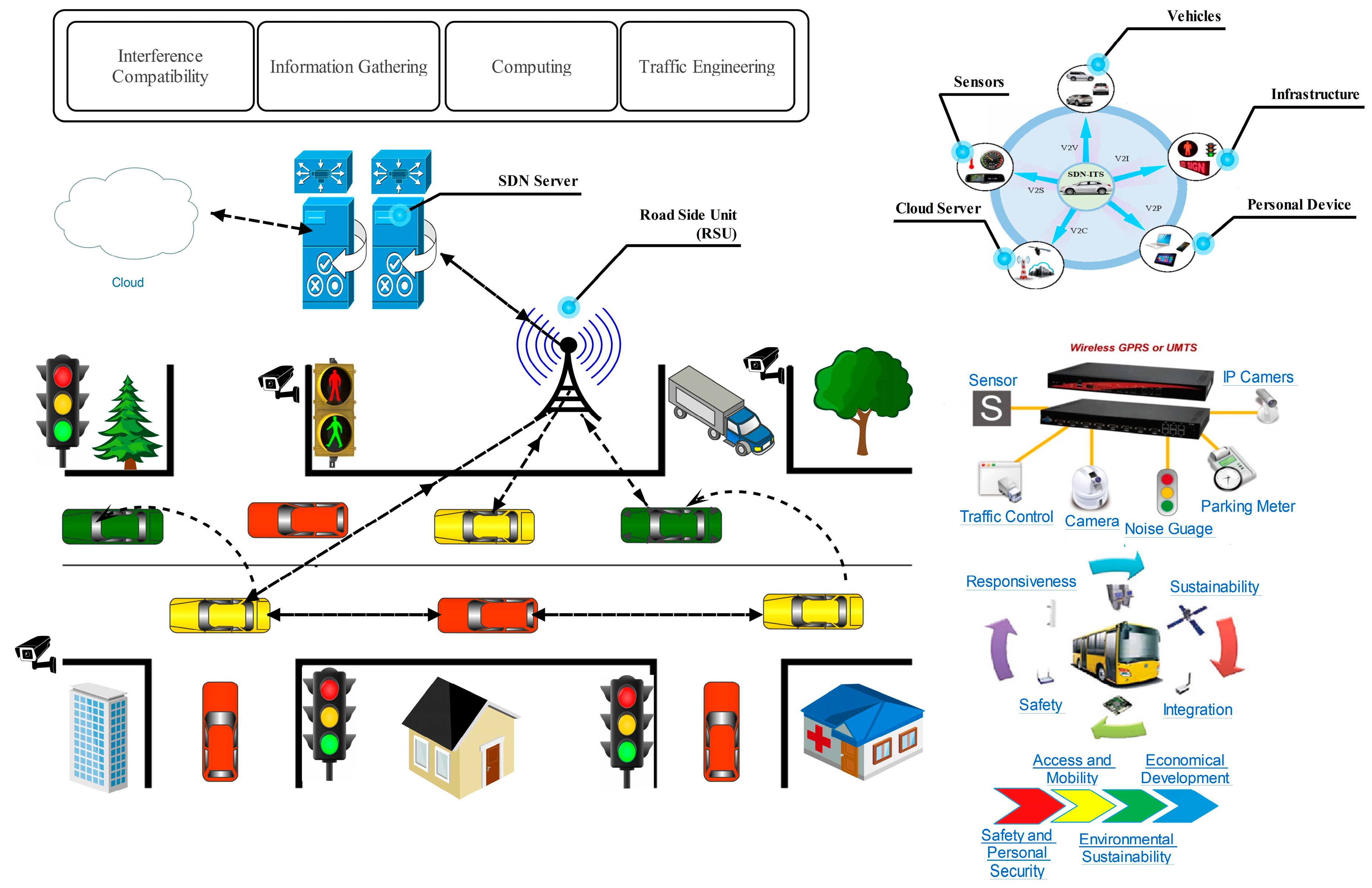
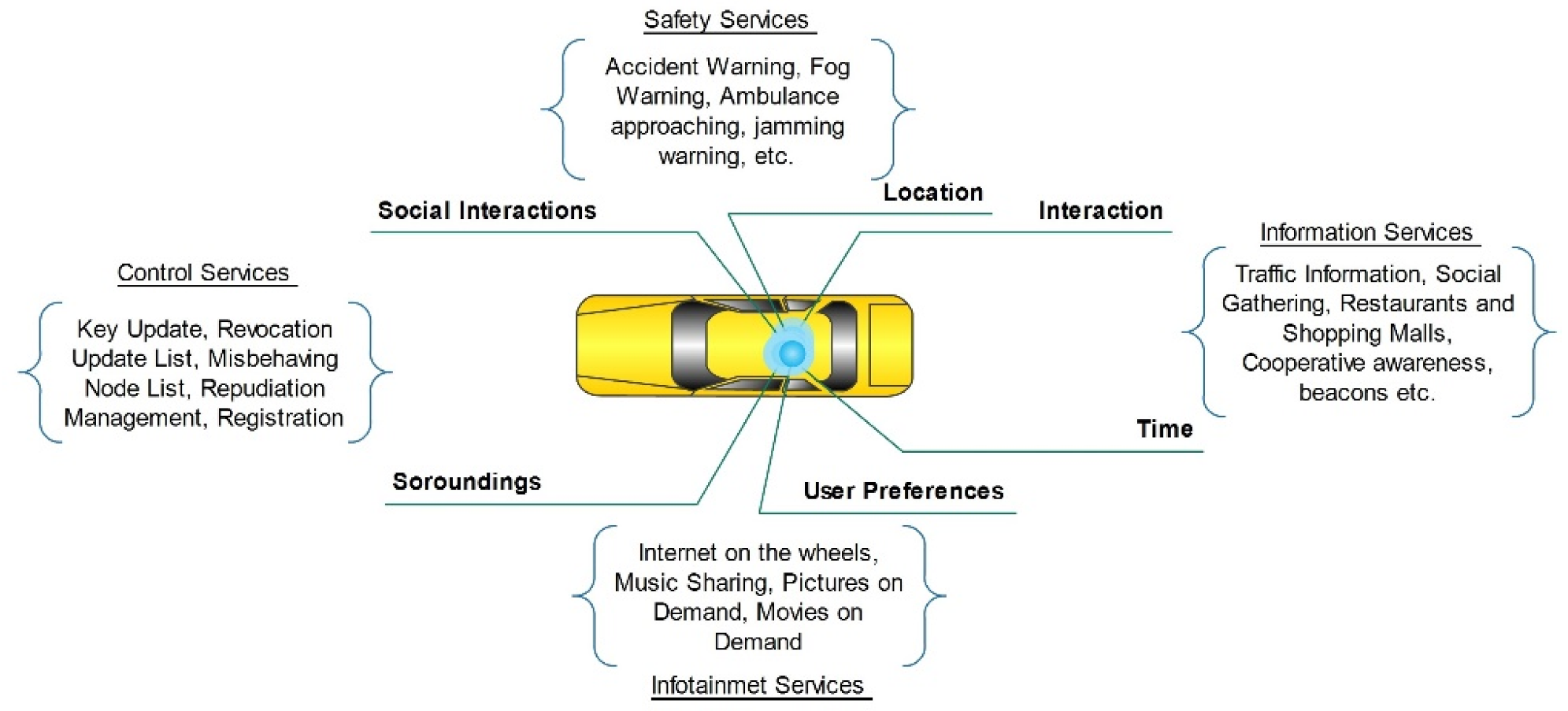
3. SDN-based Intelligent Transportation System
4. SDN-based VANETs
Modeling and Implementations of SDNs for Vehicular Networks
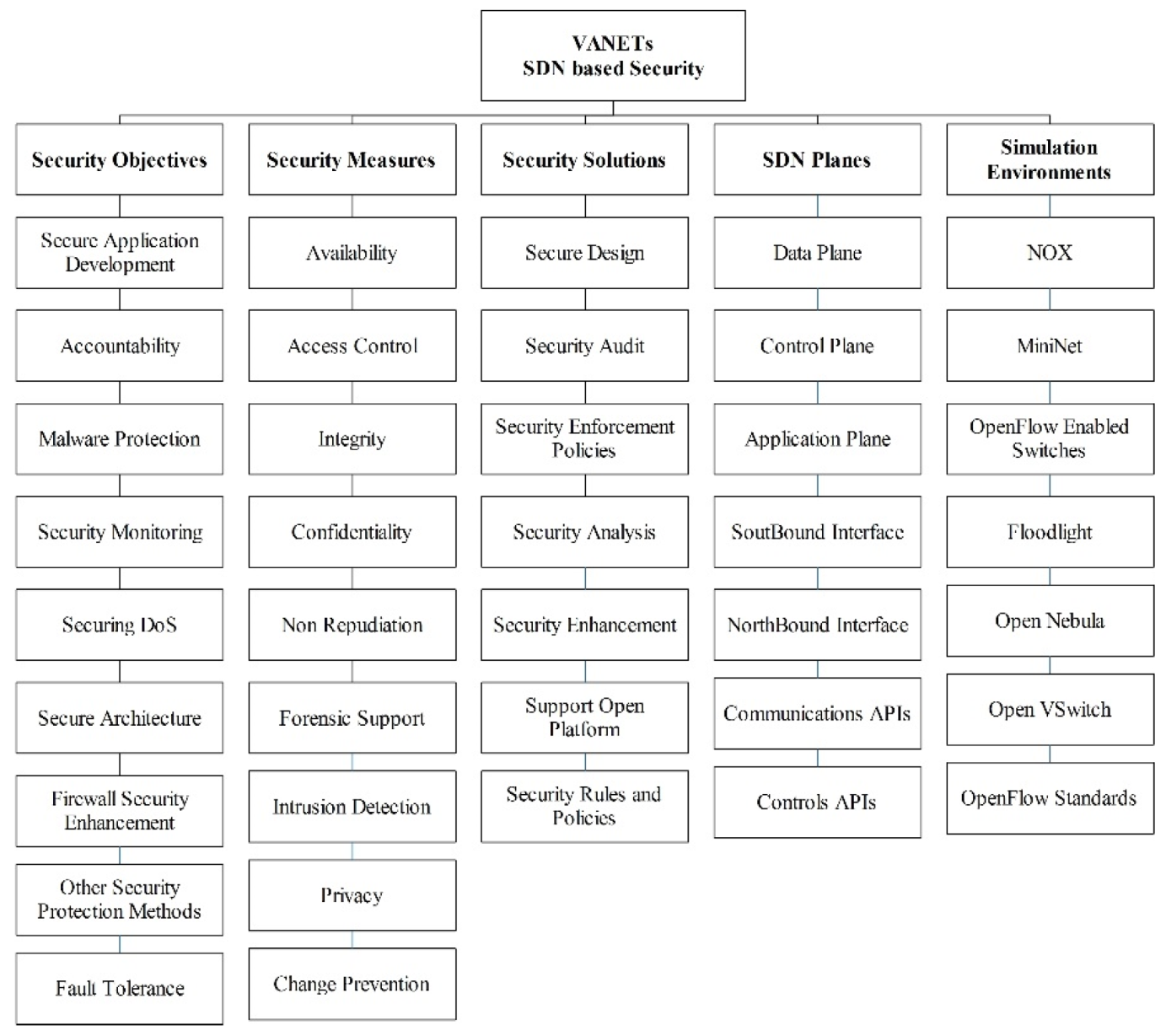
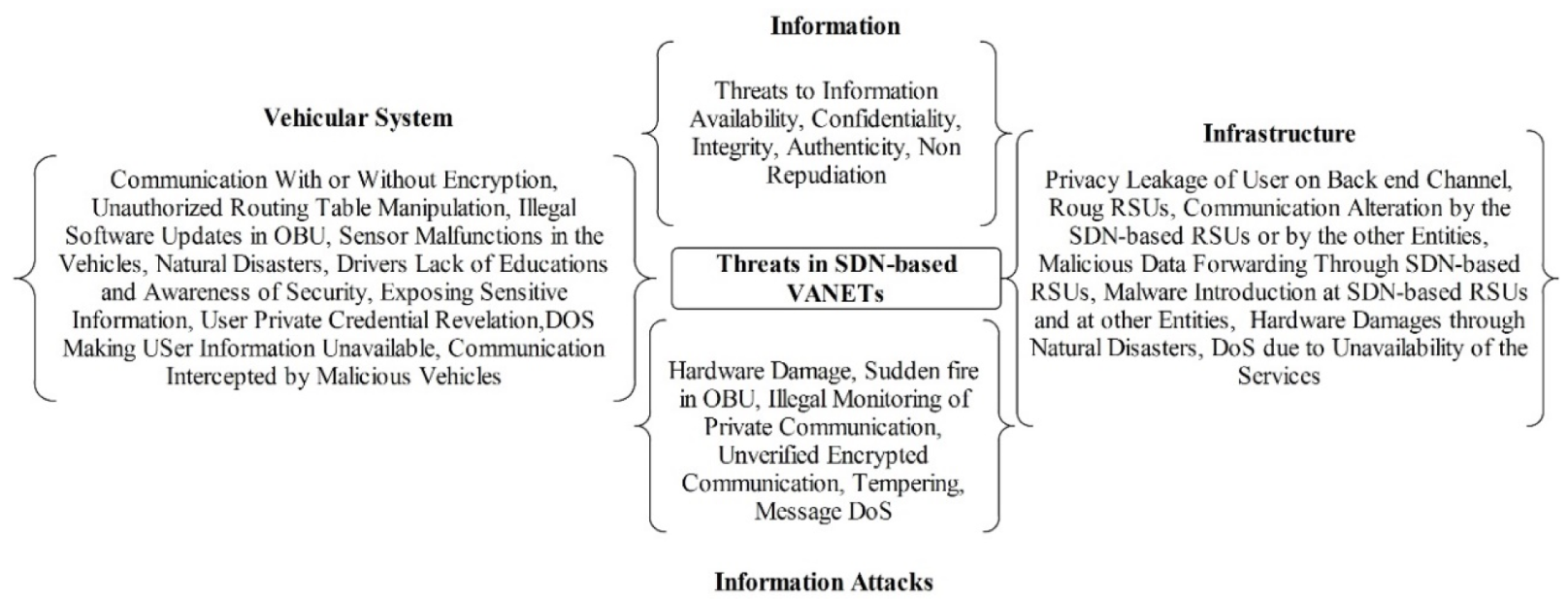
5. SDN-based VANETs Security Challenges
5.1. Security Threats
5.1.1. Application-Level
5.1.2. Control Plane
5.1.3. Communication APIs
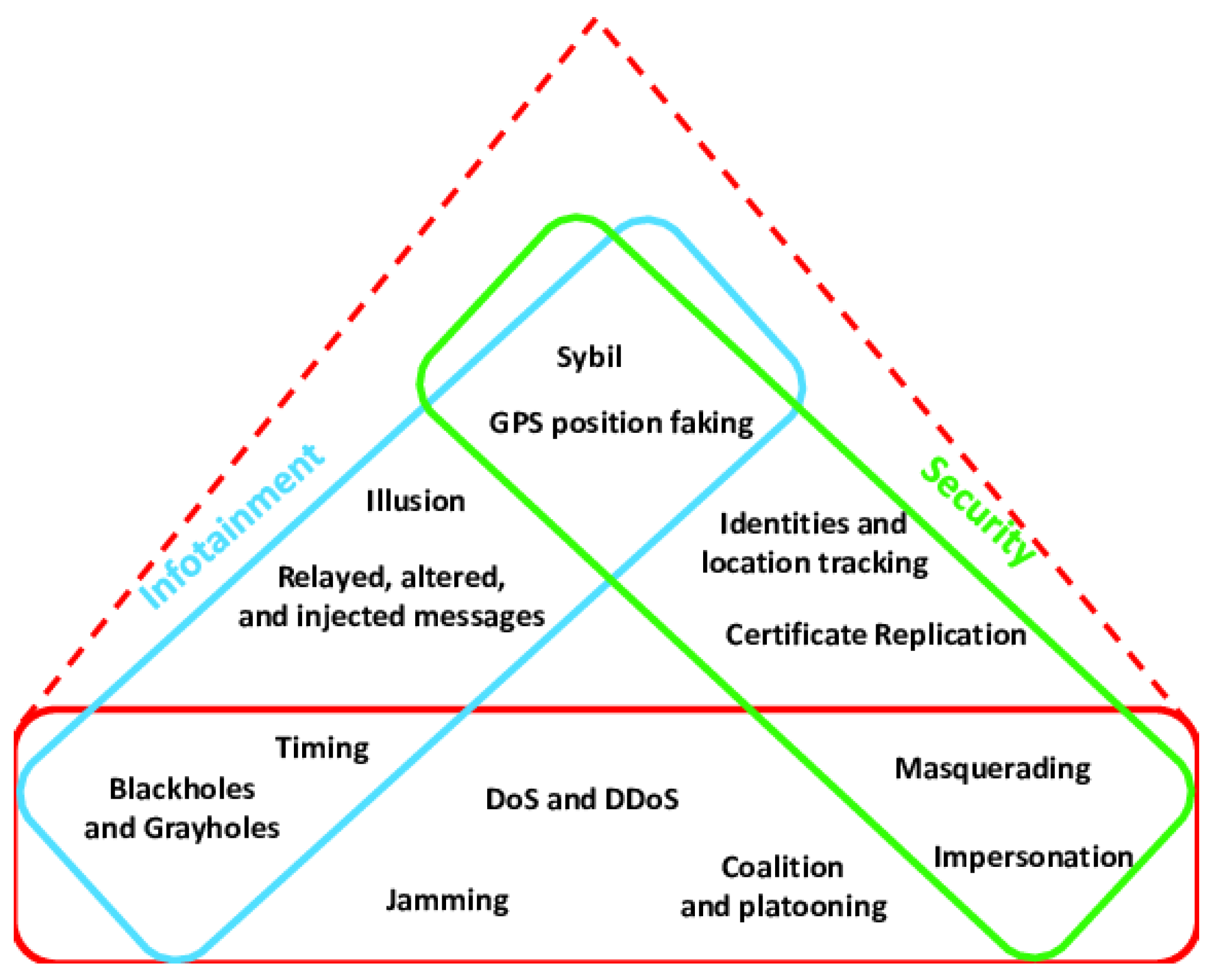
5.2. Possible Security Attacks on SDN-based VANETs
- Internal and the external attackers;
- Rational or malicious attackers;
- Passive or active attackers.
5.3. Attacks on the Resource Consumption of the Control Plane
5.4. Poisoning Attack on the Network Topology
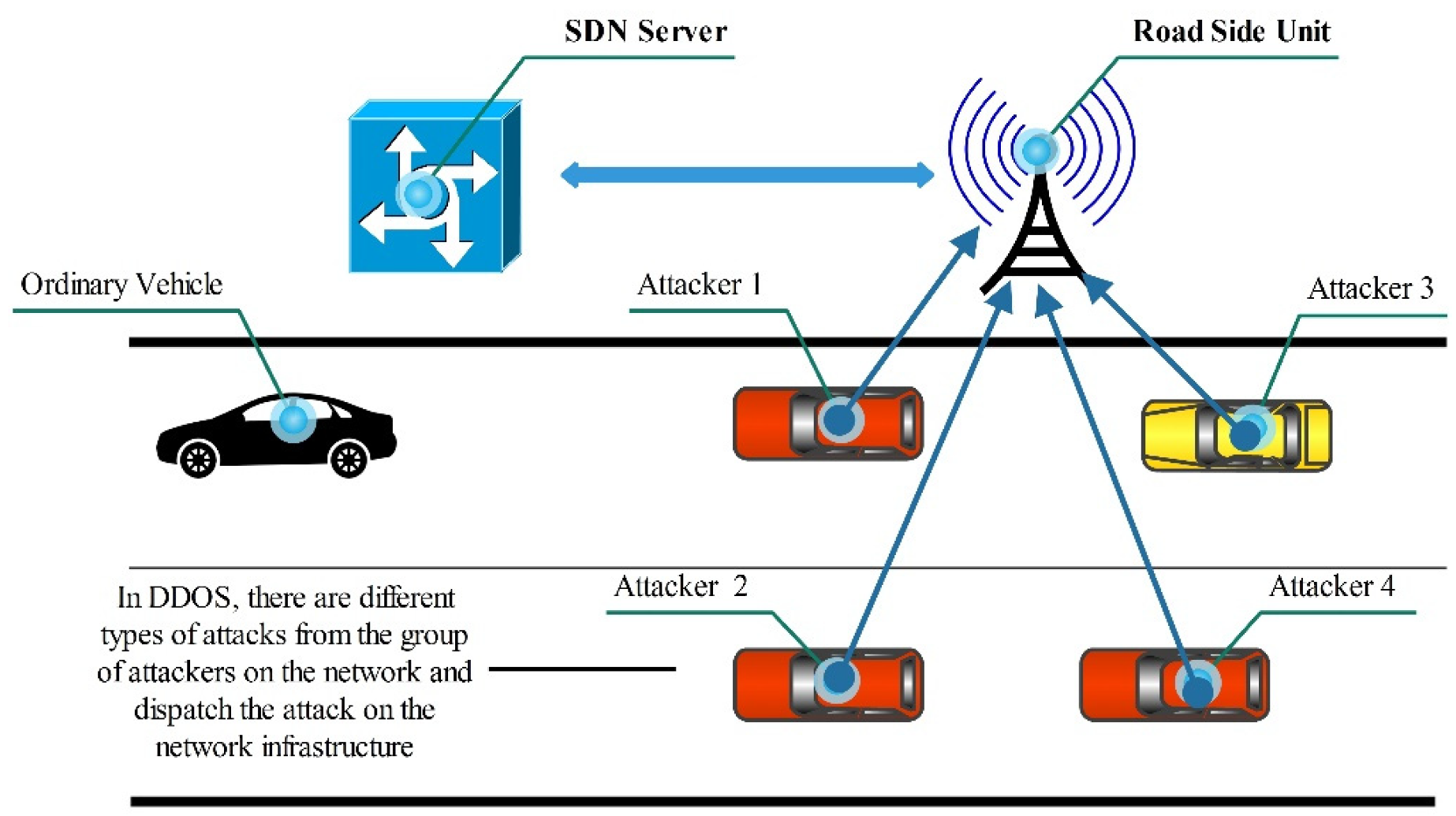
5.5. Denial of Service Attacks (DoS)
Distributed Denial of Service (DDoS)
5.6. Rule Conflicts
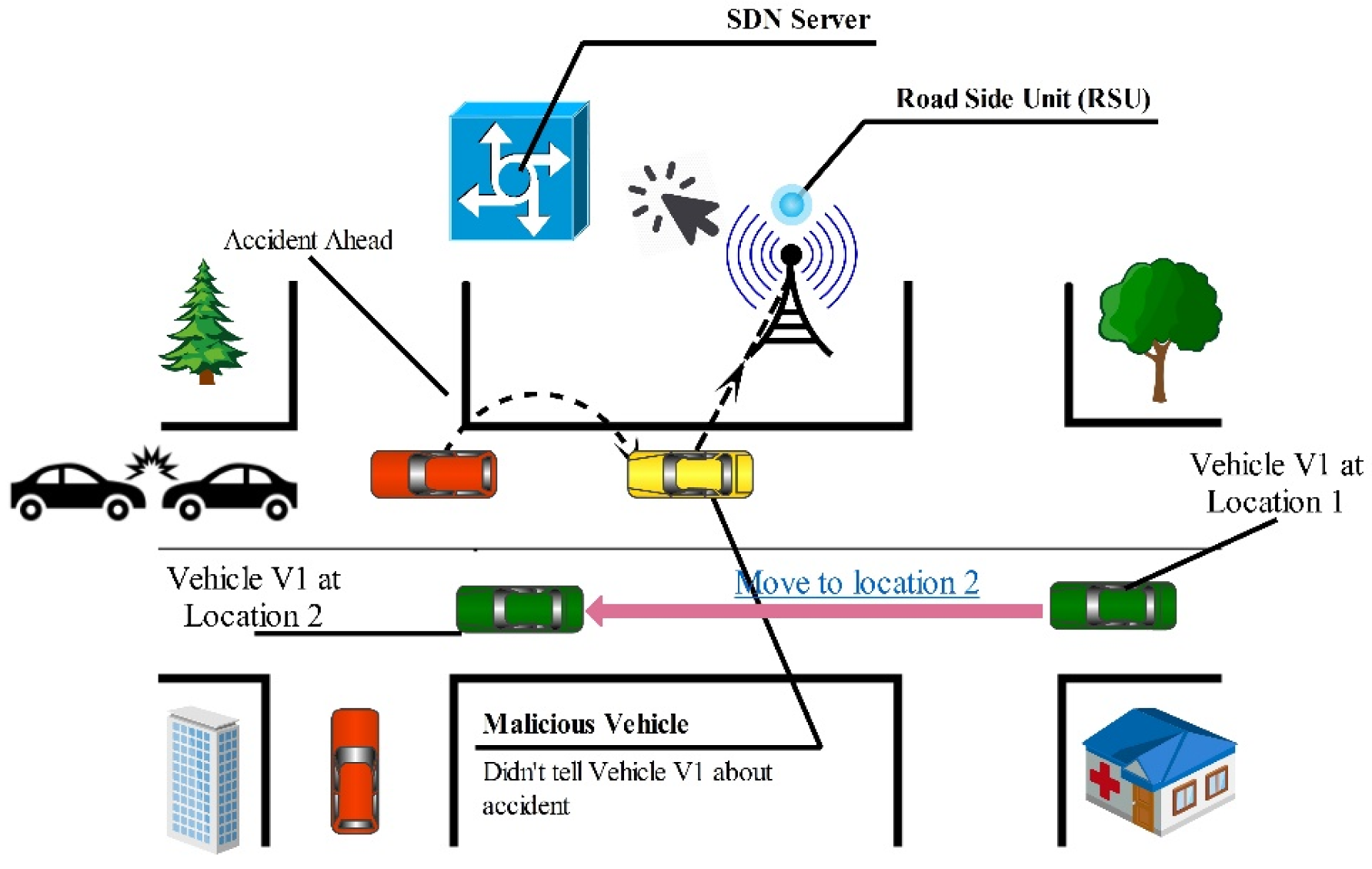
5.7. Privacy Attack
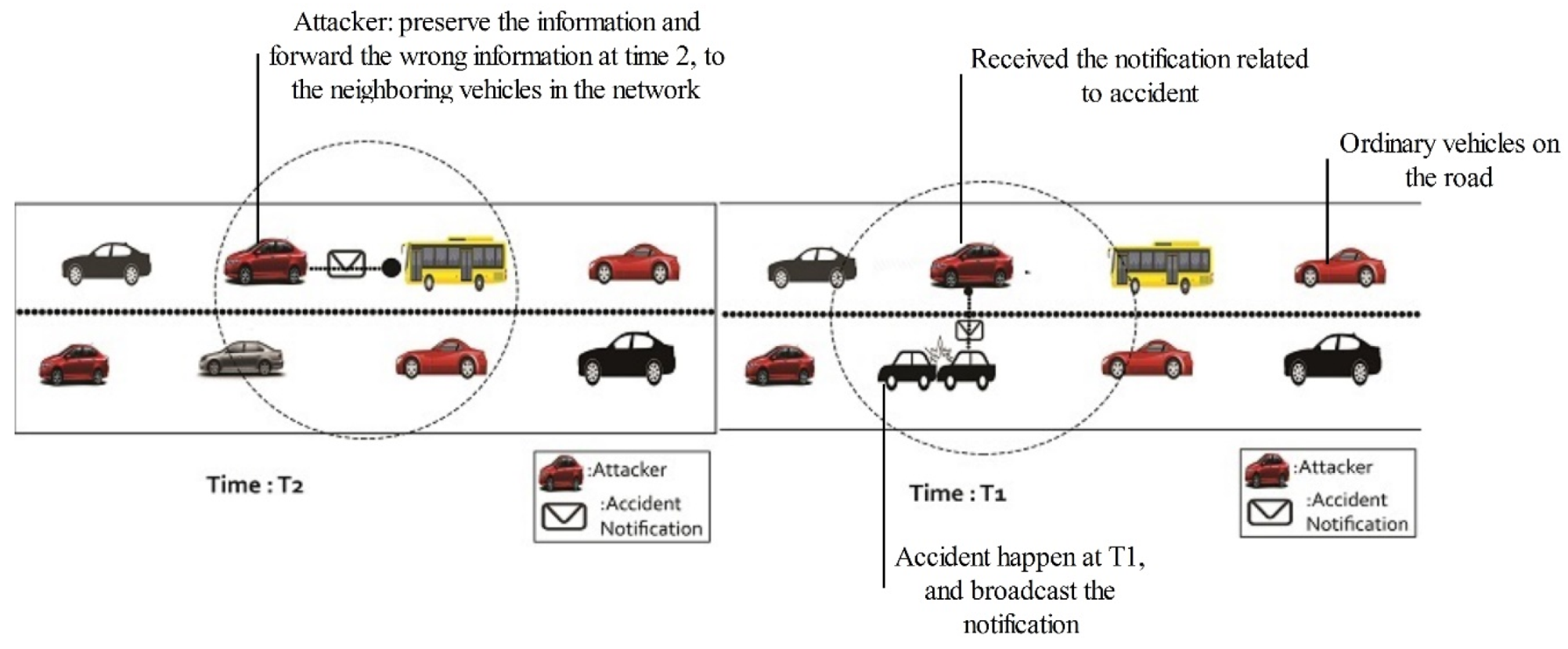
5.8. Forgery Attack
5.9. Tampering Attack
5.10. Jamming Attack
5.11. Impersonation Attack
5.12. Black Hole and Gray Hole Attacks
5.13. Wormhole Attack
5.14. Man-in-the-Middle Attack (MiMA)
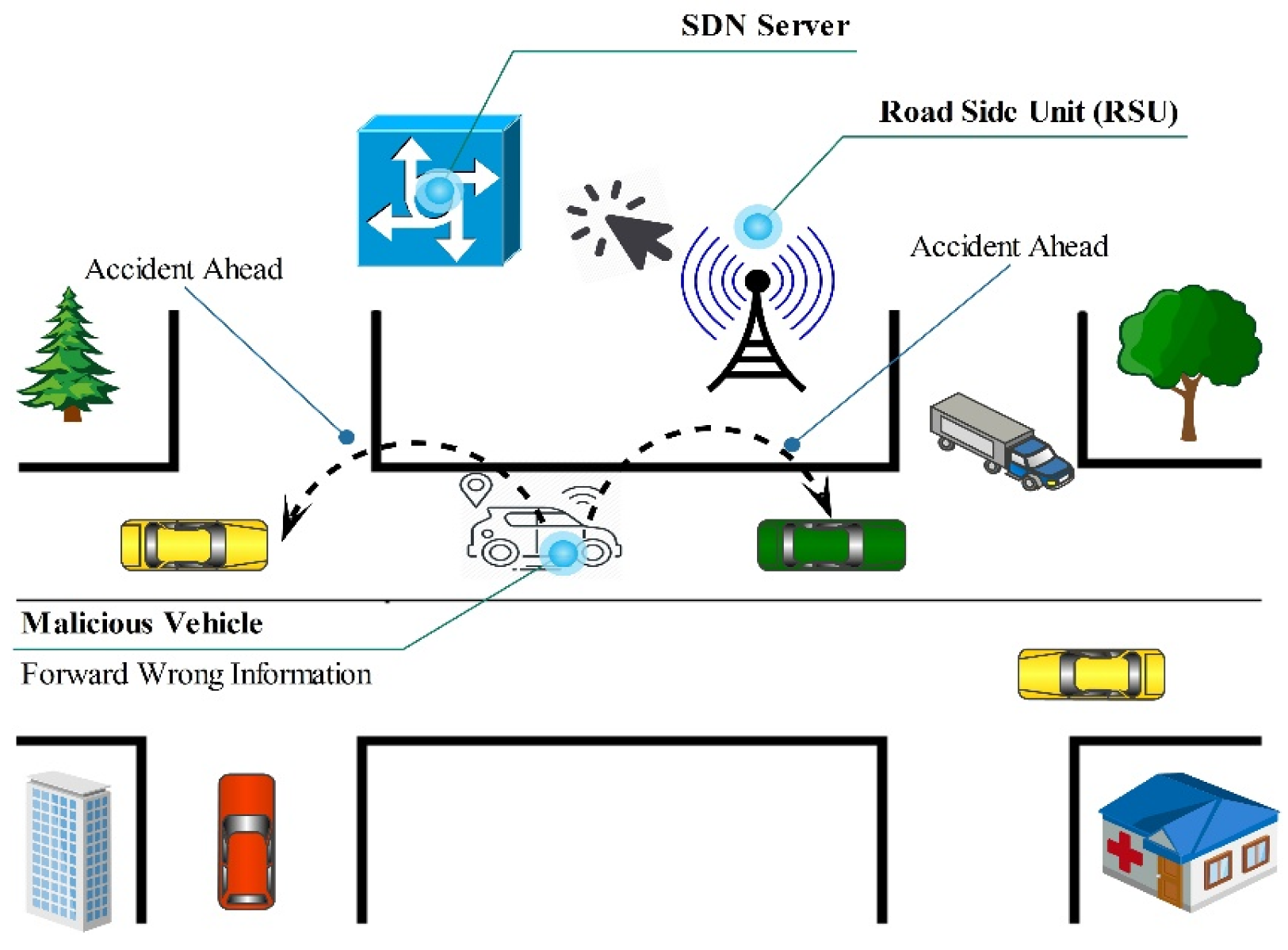
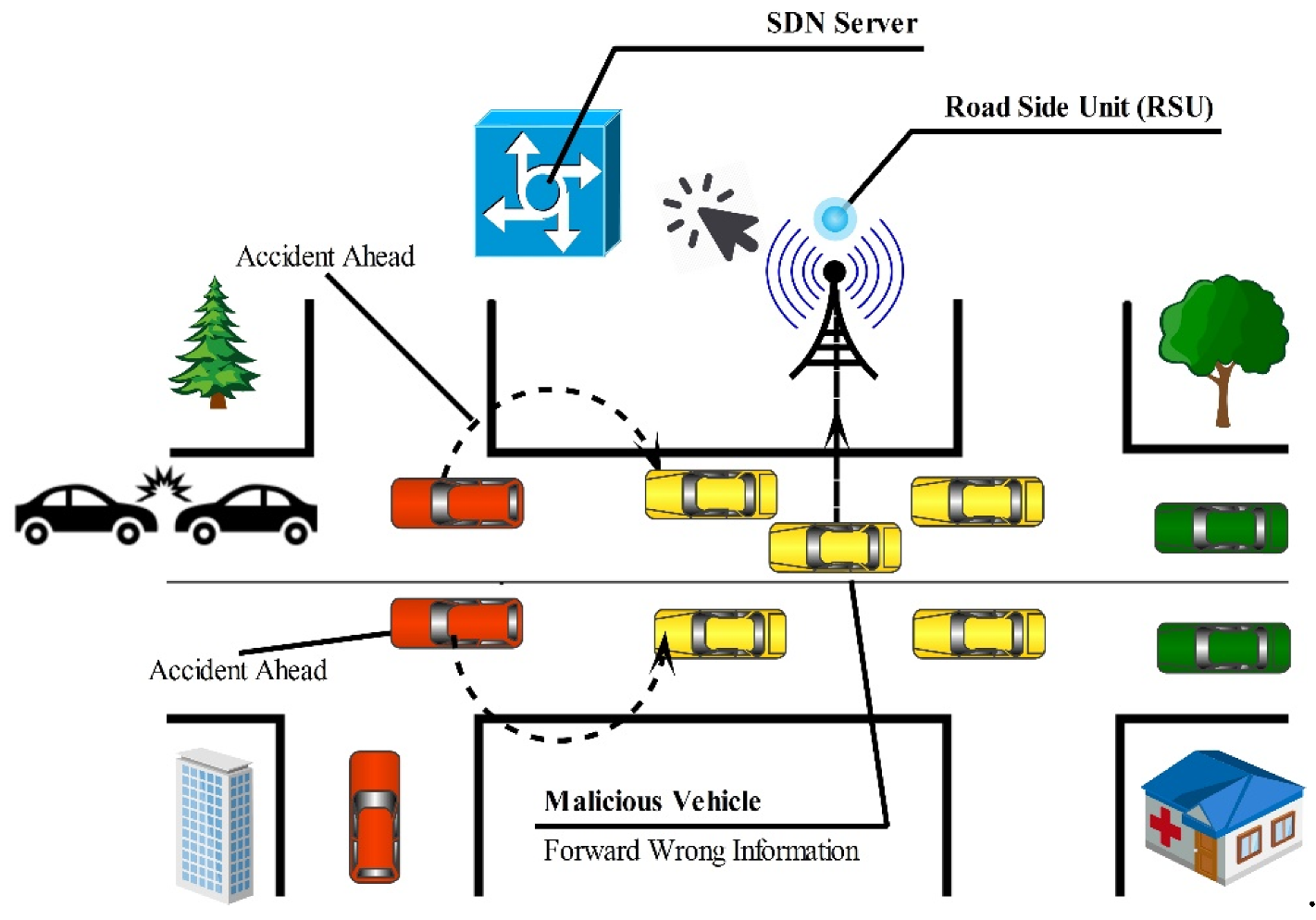
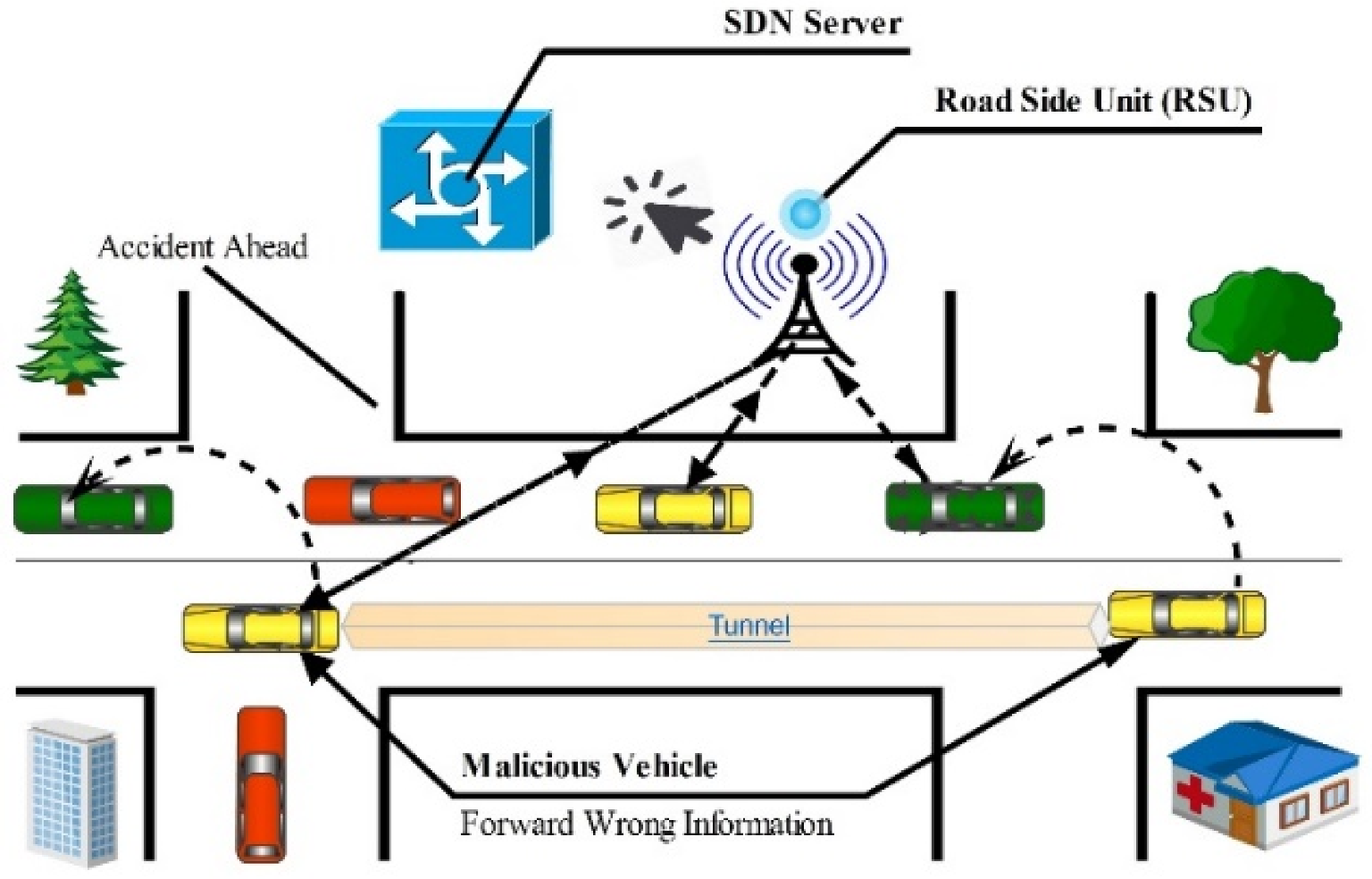
5.15. Bogus Information
5.15.1. False Position Information
5.15.2. GPS Spoofing
5.15.3. Illusion Attack
5.16. Replay Attack
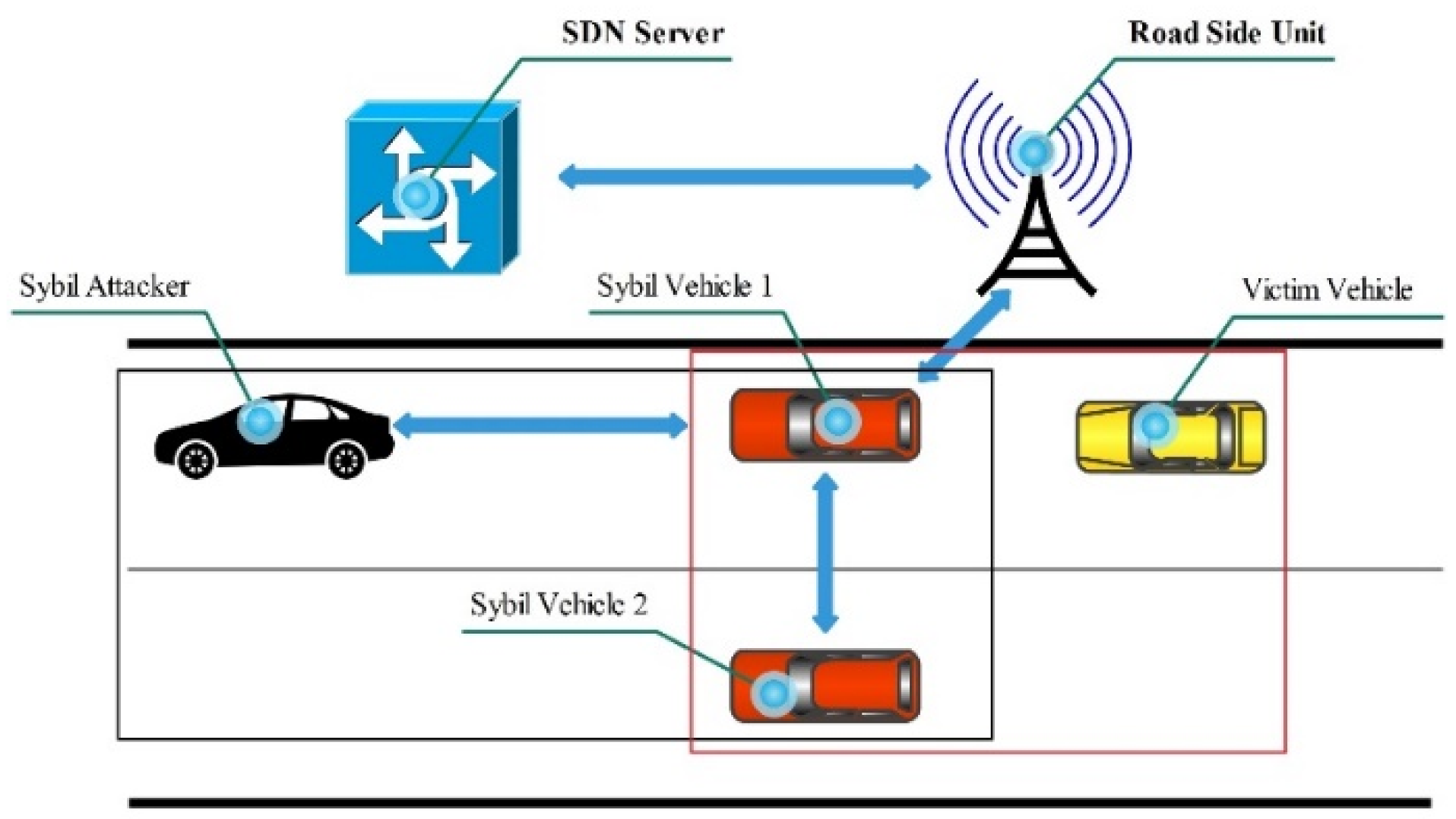
5.17. Sybil and Masquerade Attacks
5.18. Timing Attack
5.19. Snooping Attack
6. Challenges in SDN-based VANETs
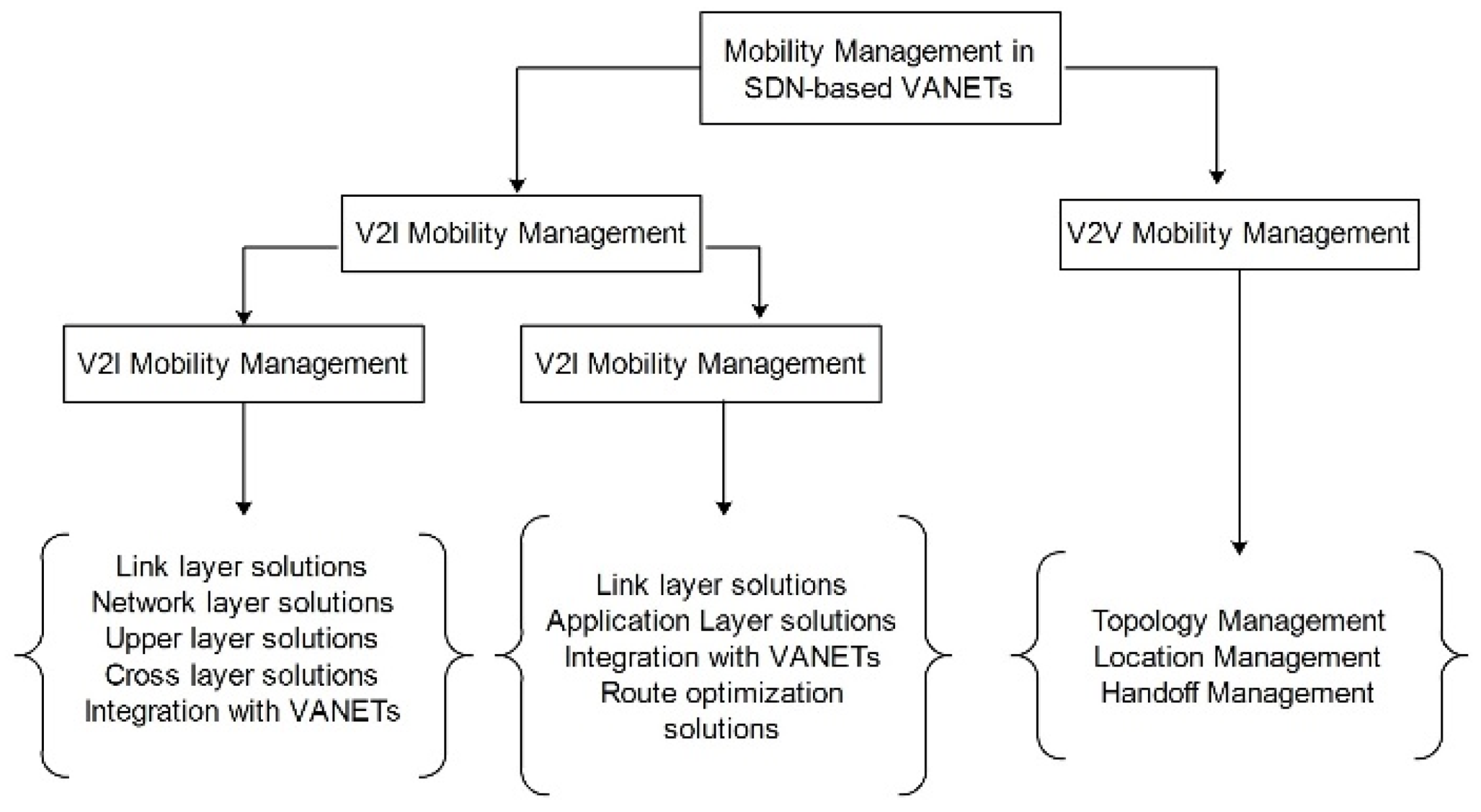
6.1. Mobility of the Vehicles
6.2. Switching, Routing, and Forwarding
6.2.1. SDN Server Switching
6.2.2. Service Switching
6.2.3. Content Caching
- In spite of the fact that vehicle-to-vehicle correspondence can improve the limit of the system regarding content reserving, they are not yet ready to approve a dependable and highest-rate information administration for vehicles because of the amazingly powerful and unsure system topologies and severe channels conditions.
- Since the SDN-RSUs are sent in various areas and diverse system administrators possess them, the participation of the SDN-RSUs to give substance to the vehicles must be considered as far as the valuing model.
- A reserving plan should be created to improve the content hit rates by the base handovers cost by recognizing store size parting, predominant substance refreshes, and guaranteeing portability mindful reserving for the smooth handover even with the highest versatility of vehicles. In addition, these vehicular storing frameworks require such procedures, which by considering the geologies and system setups effectively investigate the points of interest.
6.3. Need to Deploy Network Elements
6.4. Ubiquitous and Network Connectivity
- For the available networks, it is necessary to determine the need of the handover.
- The target selection of handover is the best network among the all available networks.
- Handover-activating conditions approximate in deciding the exact time to trigger the handover for the chosen system. Since the unified SDN-based controller in a distributed system has a 10,000 foot perspective on the whole fundamental design, it can meet the consistent, omnipresent, and undistinguishable system networks.
6.5. Heterogeneous Multi-Hop Routing
6.6. Broadcast Storm Mitigation and Network Slicing
6.7. Dynamic Network Topology
6.8. Broader Flow Rule Definitions and Policies
- Information sending rules
- The actions list for the communication rules
- A counter list to measure the communication
6.9. Security and Privacy Considerations
6.10. Interworking Gaps Among Heterogeneous Networks
6.11. Misbehavior of Elements from Different Technologies
6.12. Highly Dynamic and Distributed Behaviour of Vehicles
6.13. Mobility-Aware Edge Caching
6.14. Management of Rapidly Changing SDN-based VANETs
6.15. Security of SDN-based VANETs
6.16. Latency Control in SDN-based VANETs
6.17. Scalability of Architecture
6.18. Heterogeneous Network
6.19. Trustworthiness Evaluation, Misbehavior Detection, and Revocation Process
6.20. Demarcation of SDN into VANETs
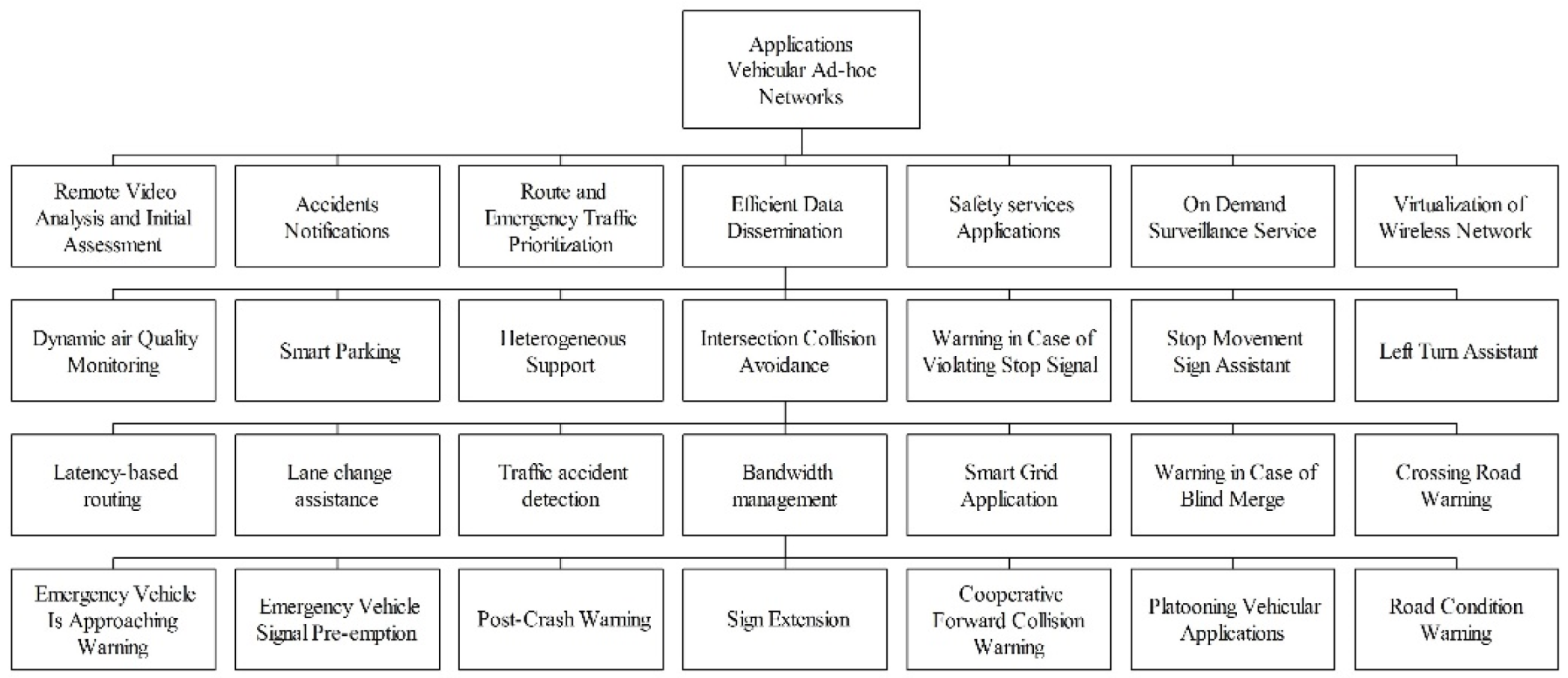
7. Applications in SDN-based VANETs
7.1. Remote Video Analysis and Initial Assessment
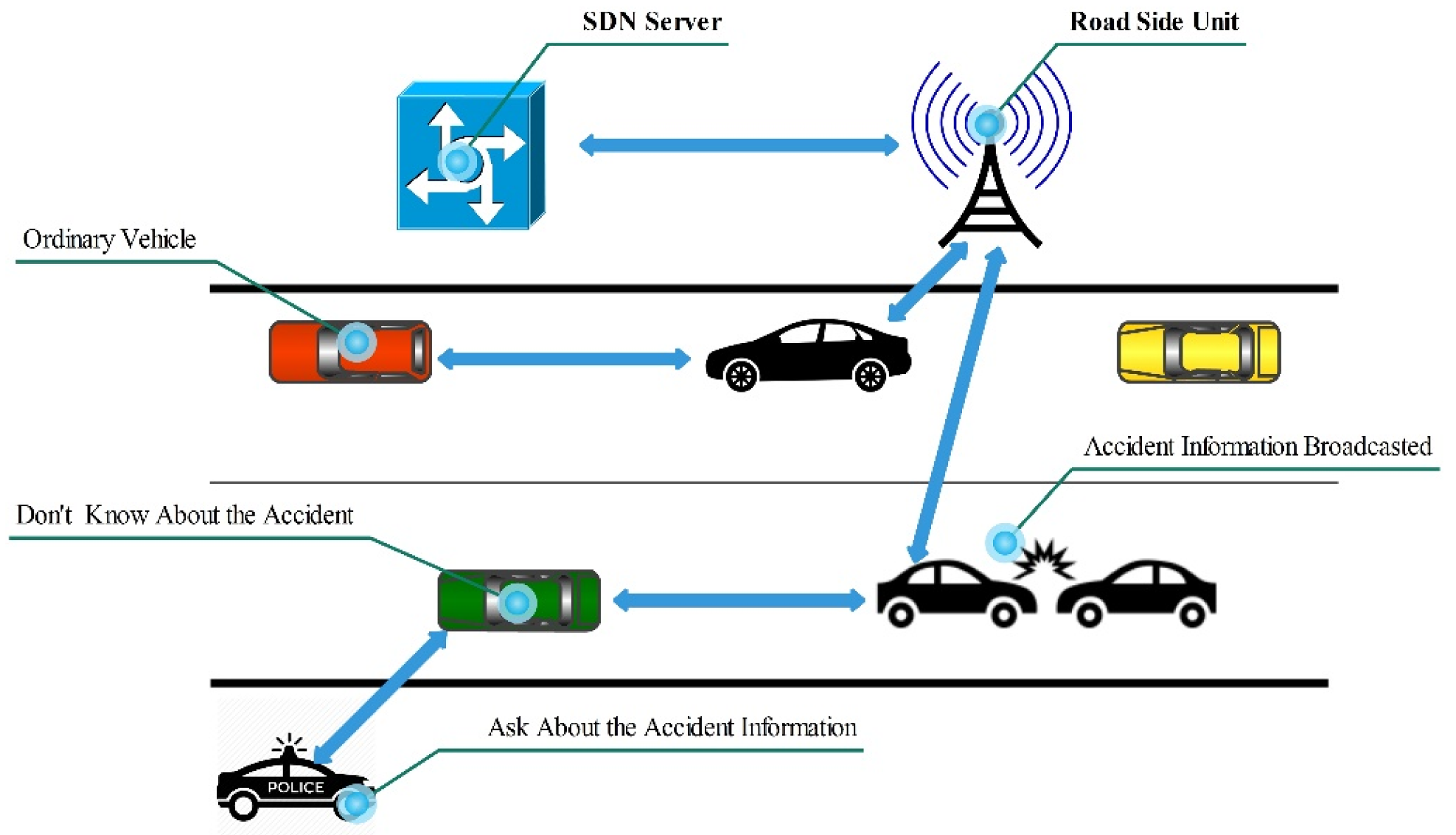
7.2. Accident Notification and Congestion Avoidance
7.3. Fast Rescue Route and Emergency Traffic Prioritization
7.4. Efficient Data Dissemination
7.5. Applications-based Safety Services
7.6. On Demand Reconnaissance Service
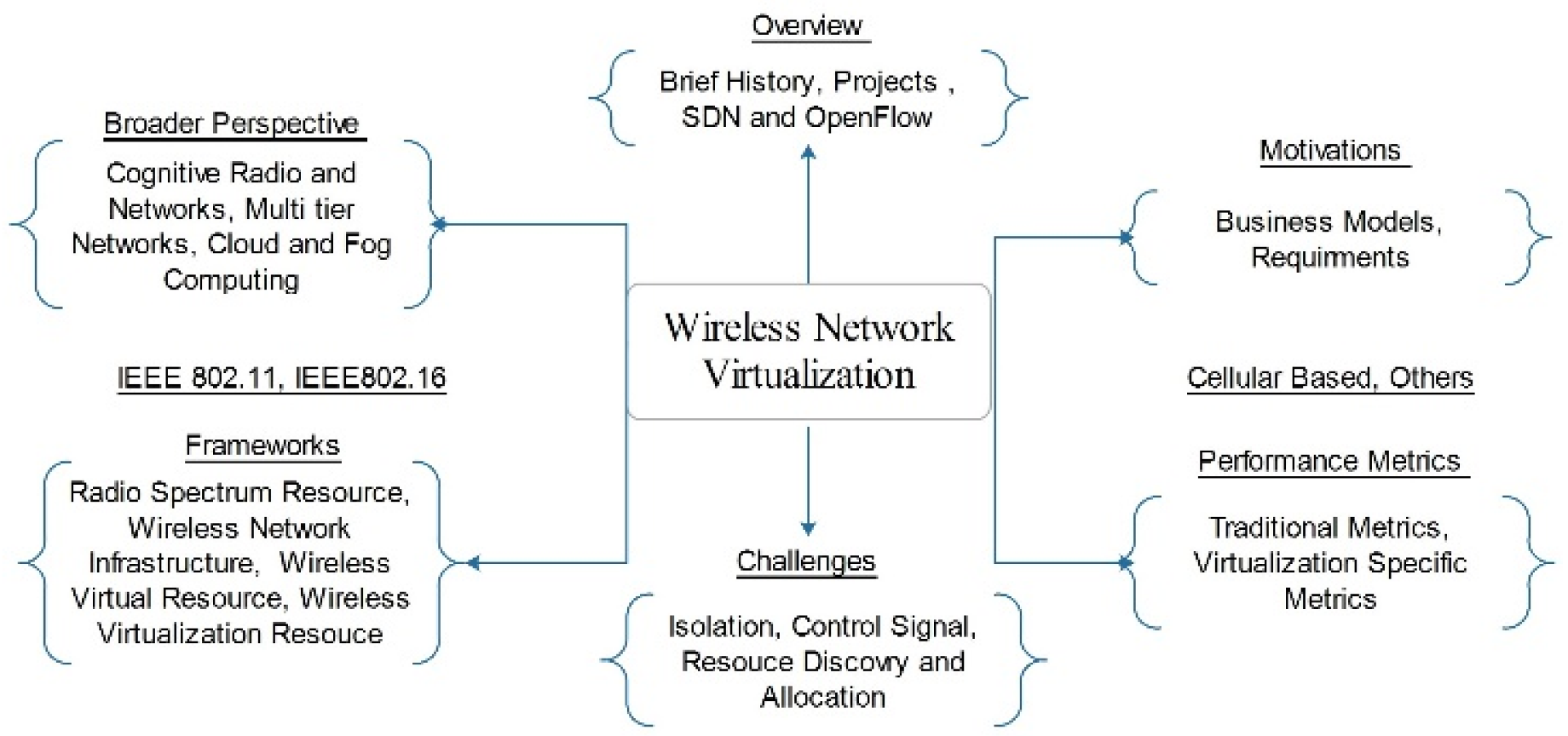
7.7. Virtualization of Wireless Network
7.8. Dynamic Air Quality Monitoring
7.9. Heterogeneous Support
7.10. Intersection Collision Avoidance
7.11. Warning in Case of Violating Stop Signal
7.12. Stop Movement Signal Assistant
7.13. Left/Right Turn Assistant
7.14. Latency-based Routing
7.15. Lane Change Assistance
7.16. Traffic Accident Detection
7.17. Bandwidth Management
7.18. Smart Grid Application
7.19. Warning in Case of Blind Merge
7.20. Crossing Road Warning
7.21. Emergency Vehicle is Approaching Warning
7.22. Emergency Vehicle Signal Pre-emption
7.23. Post-Crash Warning
7.24. Sign Extension
7.25. Cooperative Forward Collision Warning
7.26. Road Condition Warning
8. Future Directions
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Pérez, M.Á.B.; Losada, N.Y.S.; Sánchez, E.R.; Gaona, G.M. State of the art in Software Defined Networking (SDN). Visión Electrónica 2019, 13, 178–194. [Google Scholar] [CrossRef]
- Schafer, V.; Cooper, S.; Paloque-Bergès, C. Back to the roots of ARPANET and Internet history with Alexandre Serres. Internet Hist. 2019, 3, 51–67. [Google Scholar] [CrossRef]
- Karmakar, K.K.; Varadharajan, V.; Tupakula, U. Mitigating attacks in software defined networks. Clust. Comput. 2019, 22, 1143–1157. [Google Scholar] [CrossRef]
- Balmakhtar, M.; Rajagopal, A.; Persson, C.J. Software Defined Network (SDN) Proxy Correlation Index (PCI) Information Distribution across an SDN Data-Plane. U.S. Patent 10,313,193, 4 June 2019. [Google Scholar]
- Hoang, H.D.; Pham, V.-H. A Security-Enhanced Monitoring System for Northbound Interface in SDN using Blockchain. In Proceedings of the Tenth International Symposium on Information and Communication Technology (SoICT), Hanoi-Ha long Bay, Veitnam, 4–6 December 2019; pp. 197–204. [Google Scholar]
- Sen, S.; Gupta, K.D.; Ahsan, M.M. Leveraging Machine Learning Approach to Setup Software-Defined Network (SDN) Controller Rules during DDoS Attack. In Proceedings of the International Joint Conference on Computational Intelligence, Singapore, 4 July 2019; pp. 49–60. [Google Scholar]
- Bhatia, J.; Dave, R.; Bhayani, H.; Tanwar, S.; Nayyar, A. SDN based real-time urban traffic analysis in VANET environment. Comput. Commun. 2020, 149, 162–175. [Google Scholar] [CrossRef]
- You, Z.; Cheng, G.; Wang, Y.; Chen, P.; Chen, S. Cross-Layer and SDN Based Routing Scheme for P2P Communication in Vehicular Ad-Hoc Networks. Appl. Sci. 2019, 9, 4734. [Google Scholar] [CrossRef]
- Srinivasagopalan, P. Fernweh Travelogues in a Self-Driving Car; State University of New York at Buffalo: Buffalo, NY, USA, 2017. [Google Scholar]
- Nehra, A.; Tripathi, M.; Gaur, M.S. ‘Global view’ in SDN: Existing implementation, vulnerabilities & threats. In Proceedings of the 10th International Conference on Security of Information and Networks, Jaipur, India, 13–15 October 2017; pp. 303–306. [Google Scholar]
- Shafiq, H.; Rehman, R.A.; Kim, B.-S. Services and security threats in sdn based VANETs: A survey. Wirel. Commun. Mob. Comput. 2018, 2018, 1–14. [Google Scholar] [CrossRef]
- Di Maio, A.; Palattella, M.; Soua, R.; Lamorte, L.; Vilajosana, X.; Alonso-Zarate, J.; Engel, T. Enabling SDN in VANETs: What is the impact on security? Sensors 2016, 16, 2077. [Google Scholar] [CrossRef]
- Truong, N.B.; Lee, G.M.; Ghamri-Doudane, Y. Software defined networking-based vehicular adhoc network with fog computing. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 1202–1207. [Google Scholar]
- Chahal, M.; Harit, S.; Mishra, K.K.; Sangaiah, A.K.; Zheng, Z. A survey on software-defined networking in vehicular ad hoc networks: Challenges, applications and use cases. Sustain. Cities Soc. 2017, 35, 830–840. [Google Scholar] [CrossRef]
- Boucetta, S.I.; Johanyák, C.; Pokorádi, L.K. Survey on software defined VANETs. Gradus 2017, 4, 272–283. [Google Scholar]
- Barakabitze, A.A.; Ahmad, A.; Mijumbi, R.; Hines, A. 5G network slicing using SDN and NFV: A survey of taxonomy, architectures and future challenges. Comput. Netw. 2020, 167, 106984. [Google Scholar] [CrossRef]
- Papavassiliou, S. Software Defined Networking (SDN) and Network Function Virtualization (NFV). Future Internet 2020, 12, 7. [Google Scholar] [CrossRef]
- Qu, K.; Zhuang, W.; Ye, Q.; Shen, X.; Li, X.; Rao, J. Dynamic Flow Migration for Embedded Services in SDN/NFV-Enabled 5G Core Networks. IEEE Trans. Commun. 2020, 68, 2393–2408. [Google Scholar] [CrossRef]
- Kazmi, A.; Khan, M.A.; Bashir, F.; Saqib, N.A.; Alam, M.; Alam, M. Model Driven Architecture for Decentralized Software Defined VANETs. In Proceedings of the International Conference on Future Intelligent Vehicular Technologies, Porto, Portugal, 15 September 2016; pp. 46–56. [Google Scholar]
- Soua, A.; Tohme, S. Multi-level SDN with vehicles as fog computing infrastructures: A new integrated architecture for 5G-VANETs. In Proceedings of the 2018 21st Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), Paris, France, 19–22 February 2018; pp. 1–8. [Google Scholar]
- Kalinin, M.; Krundyshev, V.; Zegzhda, P.; Belenko, V. Network security architectures for VANET. In Proceedings of the 10th International Conference on Security of Information and Networks, Jaipur, India, 13–15 October 2017; pp. 73–79. [Google Scholar]
- Arif, M.; Wang, G.; Wang, T.; Peng, T. SDN based secure VANETs communication with fog computing. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Melbourne, NSW, Australia, 11 September 2018; pp. 46–59. [Google Scholar]
- Gaur, K.; Grover, J. Exploring VANET Using Edge Computing and SDN. In Proceedings of the 2019 Second International Conference on Advanced Computational and Communication Paradigms (ICACCP), Gangtok, India, 25 February 2019; pp. 1–4. [Google Scholar]
- Trivedi, H.; Tanwar, S.; Thakkar, P. Software Defined Network-Based Vehicular Adhoc Networks for Intelligent Transportation System: Recent Advances and Future Challenges. In Proceedings of the International Conference on Futuristic Trends in Network and Communication Technologies, Chandigarh, India, 22 November 2019; pp. 325–337. [Google Scholar]
- Din, S.; Paul, A.; Ahmad, A.; Ahmed, S.H.; Jeon, G.; Rawat, D.B. Hierarchical architecture for 5g based software-defined intelligent transportation system. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15 April 2018; pp. 462–467. [Google Scholar]
- Hasan, K.F.; Kaur, T.; Hasan, M.; Feng, Y. Cognitive Internet of Vehicles: Motivation, Layered Architecture and Security Issues. arXiv 2019, arXiv:1912.03356. [Google Scholar]
- Dai, P.; Liu, K.; Wu, X.; Yu, Z.; Xing, H.; Lee, V.C.S. Cooperative Temporal Data Dissemination in SDN Based Heterogeneous Vehicular Networks. IEEE Internet Things J. 2018, 6, 72–83. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed]
- Mahmood, A.; Zhang, W.E.; Sheng, Q.Z. Software-Defined Heterogeneous Vehicular Networking: The Architectural Design and Open Challenges. Future Internet 2019, 11, 70. [Google Scholar] [CrossRef]
- Rezaee, M.; Moghaddam, M.H.Y. SDN based Quality of Service Networking for Wide Area Measurement System. IEEE Trans. Ind. Inform. 2019, 16, 3018–3028. [Google Scholar] [CrossRef]
- Tello-Oquendo, L.; Akyildiz, I.F.; Lin, S.-C.; Pla, V. Sdn based architecture for providing reliable internet of things connectivity in 5g systems. In Proceedings of the 2018 17th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Capri, Italy, 22 June 2018; pp. 1–8. [Google Scholar]
- Raza, N.; Jabbar, S.; Han, J.; Han, K. Social Vehicle-to-Everything (V2X) communication model for intelligent transportation systems based on 5G scenario. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems (ICFNDS), Amman, Jordan, 26–27 June 2018; pp. 1–8. [Google Scholar]
- Li, B.; Zhao, X.; Han, S.; Chen, Z. New sdn based architecture for integrated vehicular cloud computing networking. In Proceedings of the 2018 International Conference on Selected Topics in Mobile and Wireless Networking (MoWNeT), Tangier, Morocco, 20 June 2018; pp. 1–4. [Google Scholar]
- Han, R.; Shi, J.; Banoori, F.; Shen, W. A Novel Next-Hop Selection Scheme Based on GPSR in VANETs. In Proceedings of the International Conference on Internet of Things as a Service, Xian, China, 16 November 2019; pp. 101–110. [Google Scholar]
- Buinevich, M.; Vladyko, A. Forecasting Issues of Wireless Communication Networks Cyber Resilience for an Intelligent Transportation System: An Overview of Cyber Attacks. Information 2019, 10, 27. [Google Scholar] [CrossRef]
- Cho, W.; Han, K.-S.; Choi, H.K.; Oh, H.S. Realization of anti-collision warning application using V2V communication. In Proceedings of the 2009 IEEE Vehicular Networking Conference (VNC), Tokyo, Japan, 28 October 2009; pp. 1–5. [Google Scholar]
- Yousefi, S.; Mousavi, M.S.; Fathy, M. Vehicular ad hoc networks (VANETs): Challenges and perspectives. In Proceedings of the 2006 6th International Conference on ITS Telecommunications, Chengdu, China, 21 June 2006; pp. 761–766. [Google Scholar]
- Arif, M.; Wang, G.; Peng, T. Track me if you can? Query Based Dual Location Privacy in VANETs for V2V and V2I. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1 August 2018; pp. 1091–1096. [Google Scholar]
- Arif, M.; Alam, K.A.; Hussain, M. Crime Mining: A Comprehensive Survey. Int. J. u- e-Serv. Sci. Technol. 2015, 8, 357–364. [Google Scholar] [CrossRef][Green Version]
- Ku, I.; Lu, Y.; Gerla, M.; Gomes, R.L.; Ongaro, F.; Cerqueira, E. Towards software-defined VANET: Architecture and services. In Proceedings of the Med-Hoc-Net, Piran, Slovenia, 2 June 2014; pp. 103–110. [Google Scholar]
- Liu, Y.-C.; Chen, C.; Chakraborty, S. A software defined network architecture for geobroadcast in VANETs. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 2 June 2015; pp. 6559–6564. [Google Scholar]
- Kazmi, A.; Khan, M.A.; Akram, M.U. DeVANET: Decentralized software-defined VANET architecture. In Proceedings of the 2016 IEEE International Conference on Cloud Engineering Workshop (IC2EW), Berlin, Germany, 4 April 2016; pp. 42–47. [Google Scholar]
- Soua, R.; Kalogeiton, E.; Manzo, G.; Duarte, J.M.; Palattella, M.R.; Di Maio, A.; Braun, T.; Engel, T.; Villas, L.A.; Rizzo, G.A. SDN coordination for CCN and FC content dissemination in VANETs. In Ad Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2017; pp. 221–233. [Google Scholar]
- Todorova, M.S.; Todorova, S.T. DDoS Attack Detection in SDN based VANET Architectures. Master’s Thesis, Aalborg University, Aalborg, Denmark, 2016. [Google Scholar]
- Venkatramana, D.K.N.; Srikantaiah, S.B.; Moodabidri, J. SCGRP: SDN-enabled connectivity-aware geographical routing protocol of VANETs for urban environment. IET Netw. 2017, 6, 102–111. [Google Scholar] [CrossRef]
- Thun, S.; Saivichit, C. Performance improvement of vehicular ad hoc network environment by cooperation between sdn/openflow controller and ieee 802.11 p. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 95–99. [Google Scholar]
- Borcoci, E.; Ambarus, T.; Vochin, M. Distributed control plane optimization in sdn-fog vanet. ICN 2017, 2017, 135. [Google Scholar]
- Gao, J.; Agyekum, K.O.-B.O.; Sifah, E.B.; Acheampong, K.N.; Xia, Q.; Du, X.; Guizani, M.; Xia, H. A Blockchain-SDN enabled Internet of Vehicles Environment for Fog Computing and 5G Networks. IEEE Internet Things J. 2019. [Google Scholar] [CrossRef]
- Duan, X. Software-defined Networking Enabled Resource Management and Security Provisioning in 5G Heterogeneous Networks. Ph.D. Thesis, The University of Western Ontario, Ontario, ON, Canada, 2017. [Google Scholar]
- Cox, J.H.; Chung, J.; Donovan, S.; Ivey, J.; Clark, R.J.; Riley, G.; Owen, H.L. Advancing software-defined networks: A survey. IEEE Access 2017, 5, 25487–25526. [Google Scholar] [CrossRef]
- Peng, H.; Ye, Q.; Shen, X.S. SDN based resource management for autonomous vehicular networks: A multi-access edge computing approach. IEEE Wirel. Commun. 2019, 26, 156–162. [Google Scholar] [CrossRef]
- Camacho, F.; Cárdenas, C.; Muñoz, D. Emerging technologies and research challenges for intelligent transportation systems: 5G, HetNets, and SDN. Int. J. Interact. Des. Manuf. (IJIDeM) 2018, 12, 327–335. [Google Scholar] [CrossRef]
- Chekired, D.A.; Togou, M.A.; Khoukhi, L.; Ksentini, A. 5G-slicing-enabled scalable SDN core network: Toward an ultra-low latency of autonomous driving service. IEEE J. Sel. Areas Commun. 2019, 37, 1769–1782. [Google Scholar] [CrossRef]
- Simsek, M.; Aijaz, A.; Dohler, M.; Sachs, J.; Fettweis, G. The 5g-enabled tactile internet: Applications, requirements, and architecture. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3 April 2016; pp. 1–6. [Google Scholar]
- Arif, M.; Wang, G.; Bhuiyan, M.Z.A.; Wang, T.; Chen, J. A survey on security attacks in VANETs: Communication, applications and challenges. Veh. Commun. 2019, 19, 100179. [Google Scholar] [CrossRef]
- Hussein, A.; Elhajj, I.H.; Chehab, A.; Kayssi, A. SDN VANETs in 5G: An architecture for resilient security services. In Proceedings of the 2017 Fourth International Conference on Software Defined Systems (SDS), Valencia, Spain, 8 May 2017; pp. 67–74. [Google Scholar]
- Arif, M.; Dar, A.R. Survey on Fraud Detection Techniques Using Data Mining. Int. J. u- e-Serv. Sci. Technol. 2015, 8, 165–170. [Google Scholar] [CrossRef]
- Arif, M.; Wang, G.; Balas, V.E. Secure VANETs: Trusted communication scheme between vehicles and infrastructure based on fog computing. Stud. Inform. Control 2018, 27, 235–246. [Google Scholar] [CrossRef]
- Jaballah, W.B.; Conti, M.; Lal, C. A Survey on Software-Defined VANETs: Benefits, Challenges, and Future Directions. arXiv 2019, arXiv:1904.04577. [Google Scholar]
- Arif, M.; Wang, G.; Chen, S. Deep learning with non-parametric regression model for traffic flow prediction. In Proceedings of the 2018 IEEE 16th Intl Conf on Dependable, Autonomic and Secure Computing, 16th Intl Conf on Pervasive Intelligence and Computing, 4th Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Athens, Greece, 12 August 2018; pp. 681–688. [Google Scholar]
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: A survey, some research issues, and challenges. IEEE Commun. Surv. Tutor. 2015, 18, 602–622. [Google Scholar] [CrossRef]
- Shin, S.W.; Gu, G. Attacking software-defined networks: A first feasibility study. In Proceedings of the ACM SIGCOMM workshop on Hot topics in software defined networking, Hong Kong, China, 16 August 2013; pp. 165–166. [Google Scholar]
- Cabaj, K.; Wytrebowicz, J.; Kuklinski, S.; Radziszewski, P.; Dinh, K.T. SDN Architecture Impact on Network Security. In Proceedings of the FedCSIS position papers, Warsaw, Poland, 7 September 2014; pp. 143–148. [Google Scholar]
- Hizver, J. Taxonomic modeling of security threats in software defined networking. In Proceedings of the BlackHat Conference, Las Vegas, NV, USA, 5 August 2015; pp. 1–16. [Google Scholar]
- Ulema, M. Vulnerabilities and opportunities in SDN, NFV, and NGSON. IEEE CQR 2014, 2014, 24. [Google Scholar]
- Arbettu, R.K.; Khondoker, R.; Bayarou, K.; Weber, F. Security analysis of OpenDaylight, ONOS, Rosemary and Ryu SDN controllers. In Proceedings of the 2016 17th International telecommunications network strategy and planning symposium (Networks), Montreal, QC, Canada, 26 September 2016; pp. 37–44. [Google Scholar]
- He, Z.; Cao, J.; Liu, X. SDVN: Enabling rapid network innovation for heterogeneous vehicular communication. IEEE Netw. 2016, 30, 10–15. [Google Scholar] [CrossRef]
- Correia, S.; Boukerche, A.; Meneguette, R.I. An architecture for hierarchical software-defined vehicular networks. IEEE Commun. Mag. 2017, 55, 80–86. [Google Scholar] [CrossRef]
- Lai, C.-F.; Chang, Y.-C.; Chao, H.-C.; Hossain, M.S.; Ghoneim, A. A buffer-aware QoS streaming approach for SDN-enabled 5G vehicular networks. IEEE Commun. Mag. 2017, 55, 68–73. [Google Scholar] [CrossRef]
- Khan, A.A.; Abolhasan, M.; Ni, W. 5G next generation VANETs using SDN and fog computing framework. In Proceedings of the 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12 January 2018; pp. 1–6. [Google Scholar]
- Wang, H.; Xu, L.; Gu, G. Floodguard: A dos attack prevention extension in software-defined networks. In Proceedings of the 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Rio de Janeiro, Brazil, 22 June 2015; pp. 239–250. [Google Scholar]
- Wei, L.; Fung, C. FlowRanger: A request prioritizing algorithm for controller DoS attacks in Software Defined Networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8 June 2015; pp. 5254–5259. [Google Scholar]
- Ambrosin, M.; Conti, M.; De Gaspari, F.; Poovendran, R. Lineswitch: Tackling control plane saturation attacks in software-defined networking. IEEE/ACM Trans. Netw. 2016, 25, 1206–1219. [Google Scholar] [CrossRef]
- Shang, G.; Zhe, P.; Bin, X.; Aiqun, H.; Kui, R. FloodDefender: Protecting data and control plane resources under SDN-aimed DoS attacks. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Atlanta, GA, USA, 1 May 2017; pp. 1–9. [Google Scholar]
- Hong, S.; Xu, L.; Wang, H.; Gu, G. Poisoning Network Visibility in Software-Defined Networks: New Attacks and Countermeasures. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 8 November 2015; pp. 8–11. [Google Scholar]
- Aujla, G.S.; Chaudhary, R.; Kumar, N.; Rodrigues, J.J.; Vinel, A. Data offloading in 5g-enabled software-defined vehicular networks: A stackelberg-game-based approach. IEEE Commun. Mag. 2017, 55, 100–108. [Google Scholar] [CrossRef]
- Dhawan, M.; Poddar, R.; Mahajan, K.; Mann, V. SPHINX: Detecting Security Attacks in Software-Defined Networks. In Proceedings of the Network and Distributed System Security (NDSS), San Diego, CA, USA, 8 November 2015; pp. 8–11. [Google Scholar]
- Khelifi, H.; Luo, S.; Nour, B.; Shah, S.C. Security and Privacy Issues in Vehicular Named Data Networks: An Overview. Mob. Inf. Syst. 2018, 2018, 1–11. [Google Scholar] [CrossRef]
- Alrehan, A.M.; Alhaidari, F.A. Machine Learning Techniques to Detect DDoS Attacks on VANET System: A Survey. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1 May 2019; pp. 1–6. [Google Scholar]
- Hussain, R.; Hussain, F.; Zeadally, S. Integration of VANET and 5G Security: A review of design and implementation issues. Future Gener. Comput. Syst. 2019, 101, 843–864. [Google Scholar] [CrossRef]
- Shin, S.W.; Porras, P.; Yegneswara, V.; Fong, M.; Gu, G.; Tyson, M. Fresco: Modular composable security services for software-defined networks. In Proceedings of the 20th Annual Network and Distributed System Security (NDSS), San Diego, CA, USA, 24 February 2013; pp. 1–16. [Google Scholar]
- Porras, P.; Shin, S.; Yegneswaran, V.; Fong, M.; Tyson, M.; Gu, G. A security enforcement kernel for OpenFlow networks. In Proceedings of the first workshop on Hot topics in software defined networks, Helsinki, Finland, 13–17 August 2012; pp. 121–126. [Google Scholar]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Lin, X.; Sun, X.; Ho, P.-H.; Shen, X. GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Zhang, C.; Lu, R.; Ho, P.-H.; Chen, A. A location privacy preserving authentication scheme in vehicular networks. In Proceedings of the 2008 IEEE Wireless Communications and Networking Conference, Las Vegas, NV, USA, 31 March 2008; pp. 2543–2548. [Google Scholar]
- Wu, Z.; Wei, Q.; Ren, K.; Wang, Q. A Dynamic Defense Using Client Puzzle for Identity-Forgery Attack on the South-Bound of Software Defined Networks. KSII Trans. Internet Inf. Syst. 2017, 11, 846–864. [Google Scholar]
- Abu-Ghazaleh, N.; Kang, K.-D.; Liu, K. Towards resilient geographic routing in wsns. In Proceedings of the 1st ACM international workshop on Quality of service & security in wireless and mobile networks, Montreal, QC, Canada, October 2005; pp. 71–78. [Google Scholar]
- Capkun, S.; Hubaux, J.-P. Secure positioning in wireless networks. IEEE J. Sel. Areas Commun. 2006, 24, 221–232. [Google Scholar] [CrossRef]
- Leinmüller, T.; Maihöfer, C.; Schoch, E.; Kargl, F. Improved security in geographic ad hoc routing through autonomous position verification. In Proceedings of the third international workshop on Vehicular ad hoc networks, Los Angeles, CA, USA, 29 September 2006; pp. 57–66. [Google Scholar]
- Jaballah, W.B.; Conti, M.; Mosbah, M.; Palazzi, C.E. Fast and secure multihop broadcast solutions for intervehicular communication. IEEE Trans. Intell. Transp. Syst. 2013, 15, 433–450. [Google Scholar] [CrossRef]
- Li, Z.; Chigan, C.; Wong, D. AWF-NA: A complete solution for tampered packet detection in VANETs. In Proceedings of the IEEE GLOBECOM 2008IEEE Global Telecommunications Conference, New Orleans, LO, USA, 30 November 2008; pp. 1–6. [Google Scholar]
- Kalinin, M.O.; Krundyshev, V.; Semianov, P. Architectures for building secure vehicular networks based on SDN technology. Autom. Control Comput. Sci. 2017, 51, 907–914. [Google Scholar] [CrossRef]
- Waraich, P.S.; Batra, N. Prevention of denial of service attack over vehicle ad hoc networks using quick response table. In Proceedings of the 2017 4th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 21 September 2017; pp. 586–591. [Google Scholar]
- Nikam, A.S.; Sarawagi, A. Security over Wormhole Attack in VANET Network System. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2017, 7, 196–200. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Kaddoum, G.; Ahmed, S.H.; Jayakody, D.N.K. SDN based Secure and Privacy-preserving Scheme for Vehicular Networks: A 5G Perspective. IEEE Trans. Veh. Technol. 2019, 68, 8421–8434. [Google Scholar] [CrossRef]
- Stolyarova, E.S.; Shiryaev, D.M.; Vladyko, A.G.; Buinevich, M.V. VANET/ITS cybersecurity threats: Analysis, categorization and forecasting. In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow, Russia, 29 January 2018; pp. 136–141. [Google Scholar]
- Al-Kahtani, M.S. Survey on security attacks in Vehicular Ad hoc Networks (VANETs). In Proceedings of the 2012 6th International Conference on Signal Processing and Communication Systems, Gold Coast, Australia, 12 December 2012; pp. 1–9. [Google Scholar]
- Chowdhury, M.; Gawande, A.; Wang, L. Anonymous authentication and pseudonym-renewal for VANET in NDN. In Proceedings of the 4th ACM Conference on Information-Centric Networking, Berlin, Germany, 26–28 September 2017; pp. 222–223. [Google Scholar]
- Chowdhury, M.; Gawande, A.; Wang, L. Secure information sharing among autonomous vehicles in NDN. In Proceedings of the 2017 IEEE/ACM Second International Conference on Internet-of-Things Design and Implementation (IoTDI), Pittsburgh, PA, USA, 18 April 2018; pp. 15–26. [Google Scholar]
- Bechler, M.; Wolf, L. Mobility management for vehicular ad hoc networks. In Proceedings of the 2005 IEEE 61st Vehicular Technology Conference, Stockholm, Sweden, 30 May 2005; pp. 2294–2298. [Google Scholar]
- Lee, J.M.; Yu, M.J.; Yoo, Y.H.; Choi, S.G. A new scheme of global mobility management for inter-VANETs handover of vehicles in V2V/V2I network environments. In Proceedings of the 2008 Fourth International Conference on Networked Computing and Advanced Information Management, Gyeongju, Korea, 2 September 2008; pp. 114–119. [Google Scholar]
- Meneguette, R.I.; Bittencourt, L.F.; Madeira, E.R.M. A seamless flow mobility management architecture for vehicular communication networks. J. Commun. Netw. 2013, 15, 207–216. [Google Scholar] [CrossRef]
- Heinonen, J.; Partti, T.; Kallio, M.; Lappalainen, K.; Flinck, H.; Hillo, J. Dynamic tunnel switching for SDN based cellular core networks. In Proceedings of the 4th workshop on All things cellular: Operations, applications, & challenges, Chicago, IL, USA, 22 August 2014; pp. 27–32. [Google Scholar]
- Yoshida, Y.; Maruta, A.; Kitayama, K.-i.; Nishihara, M.; Tanaka, T.; Takahara, T.; Rasmussen, J.C.; Yoshikane, N.; Tsuritani, T.; Morita, I. SDN based network orchestration of variable-capacity optical packet switching network over programmable flexi-grid elastic optical path network. J. Lightwave Technol. 2014, 33, 609–617. [Google Scholar] [CrossRef]
- Liu, J.; Xu, X.; Chen, W.; Hou, Y. QoS guaranteed resource allocation with content caching in SDN enabled mobile networks. In Proceedings of the 2016 IEEE/CIC International Conference on Communications in China (ICCC Workshops), Chengdu, China, 27 July 2017; pp. 1–6. [Google Scholar]
- Rizzo, G.; Palattella, M.R.; Braun, T.; Engel, T. Content and context aware strategies for QoS support in VANETs. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 25 March 2016; pp. 717–723. [Google Scholar]
- Kirichek, R.; Vladyko, A.; Paramonov, A.; Koucheryavy, A. Software-defined architecture for flying ubiquitous sensor networking. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), Bongpyeong, Korea, 19 February 2017; pp. 158–162. [Google Scholar]
- Lee, C.S.; Lee, G.M.; Rhee, W.S. Standardization and challenges of smart ubiquitous networks in ITU-T. IEEE Commun. Mag. 2013, 51, 102–110. [Google Scholar] [CrossRef]
- Lacoste, M.; Armand, D.; L’Hereec, F.; Prévost, F.; Rafflée, Y.; Roché, S. Software-Defined Vehicular Networking Security: Threats and Security Opportunities for 5G. Available online: https://www.cesar-conference.org/wp-content/uploads/2019/10/20191119_J1_090_M-LACOSTE_Software_Defined_Vehicular_Network.pdf (accessed on 5 May 2020).
- Zhu, M.; Cao, J.; Pang, D.; He, Z.; Xu, M. SDN based routing for efficient message propagation in VANET. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Honolulu, HI, USA, 24 June 2019; pp. 788–797. [Google Scholar]
- Dong, B.; Wu, W.; Yang, Z.; Li, J. Software defined networking based on-demand routing protocol in vehicle ad hoc networks. In Proceedings of the 2016 12th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), Hefei, China, 16 December 2016; pp. 207–213. [Google Scholar]
- Kalinin, M.; Zegzhda, P.; Zegzhda, D.; Vasiliev, Y.; Belenko, V. Software defined security for vehicular ad hoc networks. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 19–21 October 2016; pp. 533–537. [Google Scholar]
- Imran, M.A.; Sambo, Y.A.; Abbasi, Q.H. Future Perspectives. In Enabling 5G Communication Systems to Support Vertical Industries; John Wiley & Sons, Incorporated: Hoboken, NI, USA, 2019. [Google Scholar]
- Rivas, D.A.; Barceló-Ordinas, J.M.; Zapata, M.G.; Morillo-Pozo, J.D. Security on VANETs: Privacy, misbehaving nodes, false information and secure data aggregation. J. Netw. Comput. Appl. 2011, 34, 1942–1955. [Google Scholar] [CrossRef]
- Kim, C.-H.; Bae, I.-H. A misbehavior-based reputation management system for VANETs. In Embedded and Multimedia Computing Technology and Service; Springer: Berlin/Heidelberg, Germany, 2012; pp. 441–450. [Google Scholar]
- Pathan, A.-S.K. Security of Self-Organizing Networks: MANET, WSN, WMN, VANET; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Maglaras, L.A.; Al-Bayatti, A.H.; He, Y.; Wagner, I.; Janicke, H. Social internet of vehicles for smart cities. J. Sens. Actuator Netw. 2016, 5, 3. [Google Scholar] [CrossRef]
- Alouache, L.; Nguyen, N.; Aliouat, M.; Chelouah, R. Toward a hybrid SDN architecture for V2V communication in IoV environment. In Proceedings of the 2018 Fifth International Conference on Software Defined Systems (SDS), Barcelona, Spain, 23 April 2018; pp. 93–99. [Google Scholar]
- Abolhasan, M.; Lipman, J.; Ni, W.; Hagelstein, B. Software-defined wireless networking: Centralized, distributed, or hybrid? IEEE Netw. 2015, 29, 32–38. [Google Scholar] [CrossRef]
- Zhang, K.; Leng, S.; He, Y.; Maharjan, S.; Zhang, Y. Cooperative content caching in 5G networks with mobile edge computing. IEEE Wirel. Commun. 2018, 25, 80–87. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Ahmed, S.H.; Bradai, A.; Kaddoum, G.; Atiquzzaman, M. MobQoS: Mobility-Aware and QoS-Driven SDN Framework for Autonomous Vehicles. IEEE Wirel. Commun. 2019, 26, 12–20. [Google Scholar] [CrossRef]
- Lazar, S.-A.; Stefan, C.-E. Future vehicular networks: What control technologies? In Proceedings of the 2016 International Conference on Communications (COMM), Bucharest, Romania, 9 June 2016; pp. 337–340. [Google Scholar]
- Li, H.; Dong, M.; Ota, K. Control plane optimization in software-defined vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2016, 65, 7895–7904. [Google Scholar] [CrossRef]
- Bhatia, A.; Haribabu, K.; Gupta, K.; Sahu, A. Realization of flexible and scalable VANETs through SDN and virtualization. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10 January 2018; pp. 280–282. [Google Scholar]
- Huang, C.-M.; Chiang, M.-S.; Dao, D.-T.; Pai, H.-M.; Xu, S.; Zhou, H. Vehicle-to-Infrastructure (V2I) offloading from cellular network to 802.11 p Wi-fi network based on the Software-Defined Network (SDN) architecture. Veh. Commun. 2017, 9, 288–300. [Google Scholar]
- Zhang, D.; Yu, F.R.; Wei, Z.; Boukerche, A. Software-defined vehicular ad hoc networks with trust management. In Proceedings of the 6th ACM Symposium on Development and Analysis of Intelligent Vehicular Networks and Applications, Malta, Malta, 13–17 November 2016; pp. 41–49. [Google Scholar]
- Bhatia, J.; Modi, Y.; Tanwar, S.; Bhavsar, M. Software defined vehicular networks: A comprehensive review. Int. J. Commun. Syst. 2019, 32, e4005. [Google Scholar] [CrossRef]
- Raza, S.; Wang, S.; Ahmed, M.; Anwar, M.R. A Survey on Vehicular Edge Computing: Architecture, Applications, Technical Issues, and Future Directions. Wirel. Commun. Mob. Comput. 2019, 2019, 1–19. [Google Scholar] [CrossRef]
- Rak, J.; Papadimitriou, D.; Niedermayer, H.; Romero, P. Information-driven network resilience: Research challenges and perspectives. Opt. Switch. Netw. 2017, 23, 156–178. [Google Scholar] [CrossRef]
- Chiu, K.L.; Hwang, R.H.; Chen, Y.S. Cross-layer design vehicle-aided handover scheme in VANETs. Wirel. Commun. Mob. Com. 2011, 11, 916–928. [Google Scholar] [CrossRef]
- Moreira, E. An evaluation of reputation with regard to the opportunistic forwarding of messages in VANETs. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 204. [Google Scholar]
- Nobre, J.C.; de Souza, A.M.; Rosario, D.; Both, C.; Villas, L.A.; Cerqueira, E.; Braun, T.; Gerla, M. Vehicular software-defined networking and fog computing: Integration and design principles. Ad Hoc Netw. 2019, 82, 172–181. [Google Scholar] [CrossRef]
- Liu, J.; Wan, J.; Jia, D.; Zeng, B.; Li, D.; Hsu, C.-H.; Chen, H. High-efficiency urban-traffic management in context-aware computing and 5G communication. IEEE Commun. Mag. 2017, 55, 34–40. [Google Scholar] [CrossRef]
- Ullah, A.; Yaqoob, S.; Imran, M.; Ning, H. Emergency message dissemination schemes based on congestion avoidance in VANET and vehicular FoG computing. IEEE Access 2018, 7, 1570–1585. [Google Scholar] [CrossRef]
- Fan, Y.; Zhang, N. A Survey on Software-defined Vehicular Networks. J. Comput. 2017, 28, 236–244. [Google Scholar]
- Zhou, Y.; Zheng, K.; Ni, W.; Liu, R.P. Elastic switch migration for control plane load balancing in SDN. IEEE Access 2018, 6, 3909–3919. [Google Scholar] [CrossRef]
- Li, M.; Yu, F.R.; Si, P.; Sun, E.; Zhang, Y. Random access optimization for M2M communications in vanet with wireless network virtualization. In Proceedings of the 6th ACM Symposium on Development and Analysis of Intelligent Vehicular Networks and Applications, Valleta, Malta, 13–17 November 2016; pp. 1–7. [Google Scholar]
- Li, H.; Ota, K.; Dong, M. Network virtualization optimization in software defined vehicular ad-hoc networks. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18 September 2016; pp. 1–5. [Google Scholar]
- Bizanis, N.; Kuipers, F.A. SDN and virtualization solutions for the Internet of Things: A survey. IEEE Access 2016, 4, 5591–5606. [Google Scholar] [CrossRef]
- Arif, M.; Shakeel, H. Virtualization security: Analysis and open challenges. Int. J. Hybrid Inf. Technol. 2015, 8, 237–246. [Google Scholar] [CrossRef]
- Qafzezi, E.; Bylykbashi, K.; Spaho, E.; Barolli, L. A New Fuzzy-Based Resource Management System for SDN-VANETs. Int. J. Mob. Comput. Multimed. Commun. (IJMCMC) 2019, 10, 1–12. [Google Scholar] [CrossRef]
- Arif, M.; Mahmood, T. Cloud computing and its environmental effects. Int. J. Grid Distrib. Comput. 2015, 8, 279–286. [Google Scholar] [CrossRef]
- Geman, O.; Chiuchisan, I.; Ungurean, I.; Hagan, M.; Arif, M. Ubiquitous Healthcare System Based on the Sensors Network and Android Internet of Things Gateway. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8 October 2018; pp. 1390–1395. [Google Scholar]
- Duarte, J.M.; Kalogeiton, E.; Soua, R.; Manzo, G.; Palattella, M.R.; Di Maio, A.; Braun, T.; Engel, T.; Villas, L.A.; Rizzo, G.A. A multi-pronged approach to adaptive and context aware content dissemination in VANETs. Mob. Netw. Appl. 2018, 23, 1247–1259. [Google Scholar] [CrossRef]
- Arif, M.; Alam, K.A.; Hussain, M. Application of data mining using artificial neural network: Survey. Int. J. Database Theory Appl. 2015, 8, 245–270. [Google Scholar] [CrossRef]
- Das, T.; Sridharan, V.; Gurusamy, M. A Survey on Controller Placement in SDN. IEEE Commun. Surv. Tutor. 2020, 22, 472–503. [Google Scholar] [CrossRef]
- Ji, X.; Yu, H.; Fan, G.; Fu, W. SDGR: An SDN based geographic routing protocol for VANET. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15 December 2016; pp. 276–281. [Google Scholar]
- Secinti, G.; Canberk, B.; Duong, T.Q.; Shu, L. Software defined architecture for VANET: A testbed implementation with wireless access management. IEEE Commun. Mag. 2017, 55, 135–141. [Google Scholar] [CrossRef]
- Huang, C.-M.; Chiang, M.-S.; Dao, D.-T.; Su, W.-L.; Xu, S.; Zhou, H. V2V data offloading for cellular network based on the Software Defined Network (SDN) inside Mobile Edge Computing (MEC) architecture. IEEE Access 2018, 6, 17741–17755. [Google Scholar] [CrossRef]
- Khan, A.A. Optimized Communication in 5G-Driven Vehicular Ad-Hoc Networks (VANETs). Ph.D. Thesis, University of Technology Sydney, Ultimo, Australia, 2019. [Google Scholar]
- Xie, L.; Ding, Y.; Yang, H.; Wang, X. Blockchain-Based Secure and Trustworthy Internet of Things in SDN-Enabled 5G-VANETs. IEEE Access 2019, 7, 56656–56666. [Google Scholar] [CrossRef]
- Zhuang, W.; Ye, Q.; Lyu, F.; Cheng, N.; Ren, J. SDN/NFV-Empowered Future IoV With Enhanced Communication, Computing, and Caching. Proc. IEEE 2020, 108, 274–291. [Google Scholar] [CrossRef]
- Iwendi, C.; Uddin, M.; Ansere, J.A.; Nkurunziza, P.; Anajemba, J.H.; Bashir, A.K. On detection of sybil attack in large-scale VANETs using spider-monkey technique. IEEE Access 2018, 6, 47258–47267. [Google Scholar] [CrossRef]
- Chahal, M.; Harit, S. Network Selection and Data Dissemination in Heterogeneous Software-defined Vehicular Network. Comput. Netw. 2019, 161, 32–44. [Google Scholar] [CrossRef]
- Shahzad, M.; Antoniou, J. Quality of User Experience in 5G-VANET. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11 September 2019; pp. 1–6. [Google Scholar]
- Singh, P.K.; Sharma, S.; Nandi, S.K.; Nandi, S. Multipath TCP for V2I communication in SDN controlled small cell deployment of smart city. Veh. Commun. 2019, 15, 1–15. [Google Scholar] [CrossRef]
- Vladyko, A.; Khakimov, A.; Muthanna, A.; Ateya, A.A.; Koucheryavy, A. Distributed Edge Computing to Assist Ultra-Low-Latency VANET Applications. Future Internet 2019, 11, 128. [Google Scholar] [CrossRef]
- Xiao, K.; Liu, K.; Xu, X.; Zhou, Y.; Feng, L. Efficient fog-assisted heterogeneous data services in software defined VANETs. J. Ambient Intell. Humaniz. Comput. 2019, 1–13. [Google Scholar] [CrossRef]








© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Arif, M.; Wang, G.; Geman, O.; Balas, V.E.; Tao, P.; Brezulianu, A.; Chen, J. SDN-based VANETs, Security Attacks, Applications, and Challenges. Appl. Sci. 2020, 10, 3217. https://doi.org/10.3390/app10093217
Arif M, Wang G, Geman O, Balas VE, Tao P, Brezulianu A, Chen J. SDN-based VANETs, Security Attacks, Applications, and Challenges. Applied Sciences. 2020; 10(9):3217. https://doi.org/10.3390/app10093217
Chicago/Turabian StyleArif, Muhammad, Guojun Wang, Oana Geman, Valentina Emilia Balas, Peng Tao, Adrian Brezulianu, and Jianer Chen. 2020. "SDN-based VANETs, Security Attacks, Applications, and Challenges" Applied Sciences 10, no. 9: 3217. https://doi.org/10.3390/app10093217
APA StyleArif, M., Wang, G., Geman, O., Balas, V. E., Tao, P., Brezulianu, A., & Chen, J. (2020). SDN-based VANETs, Security Attacks, Applications, and Challenges. Applied Sciences, 10(9), 3217. https://doi.org/10.3390/app10093217