Spam Classification Based on Signed Network Analysis
Abstract
1. Introduction
- (1)
- To the best of our knowledge, the proposed scheme is the first spam classification method that utilizes the structural balance theory and social status theory. We verify the feasibility of the proposed scheme through extensive experiments with Twitter and Epinions datasets and a comparison with five social-network-analysis-based spam detection approaches.
- (2)
- For applying our scheme to unsigned networks, we develop a graph-converting method. To do this, we utilize the fact that the edge signs have strong correlations with PageRank and Conductance scores from the analysis of the Epinions dataset.
2. Related Work
3. A Primer on Social Psychological Theories for Signed Networks
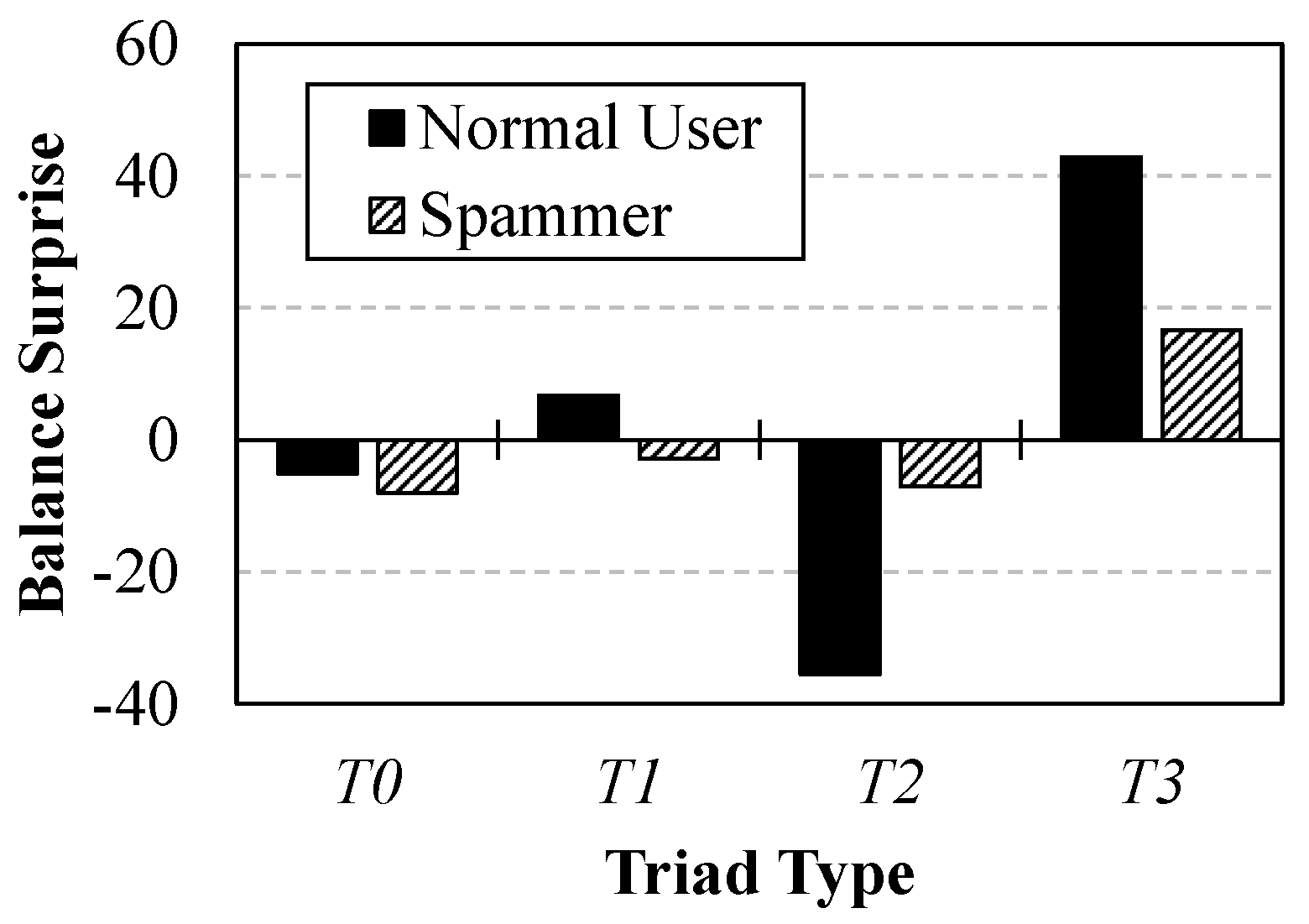
3.1. Structural Balance Theory
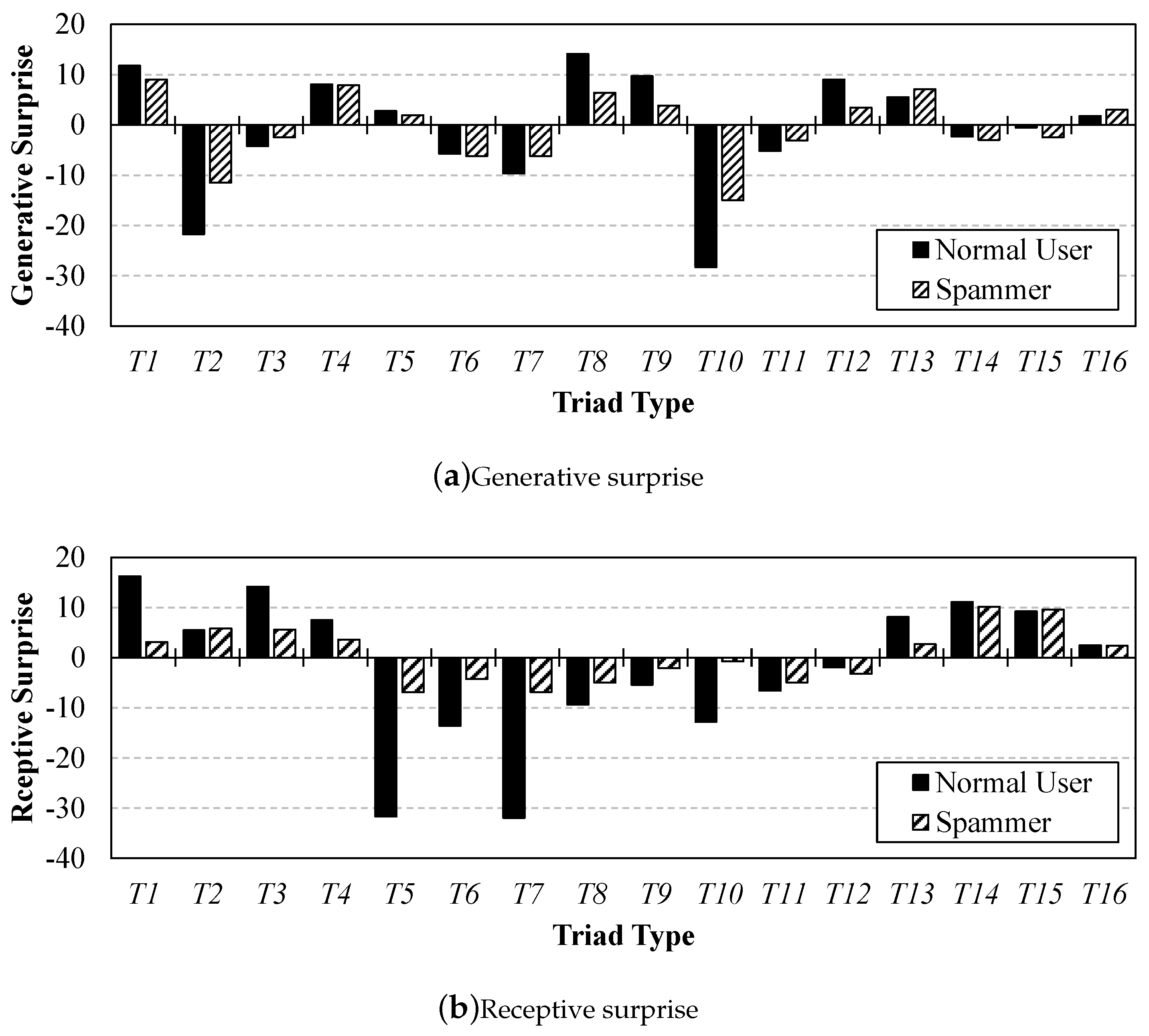
3.2. Social Status Theory
4. Feature Extraction and Validation
4.1. Coping with Unsigned Networks
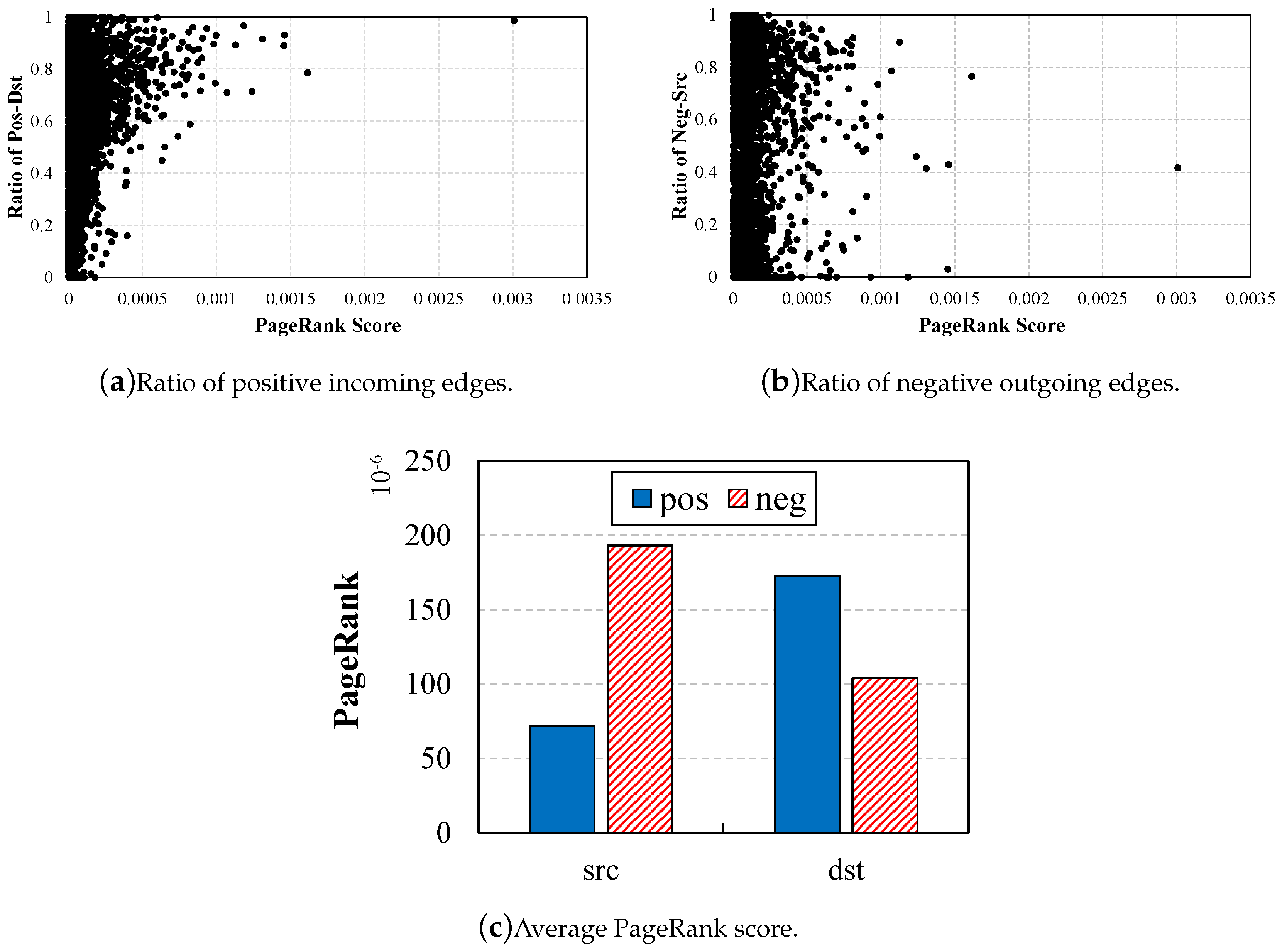
4.1.1. PageRank Analysis
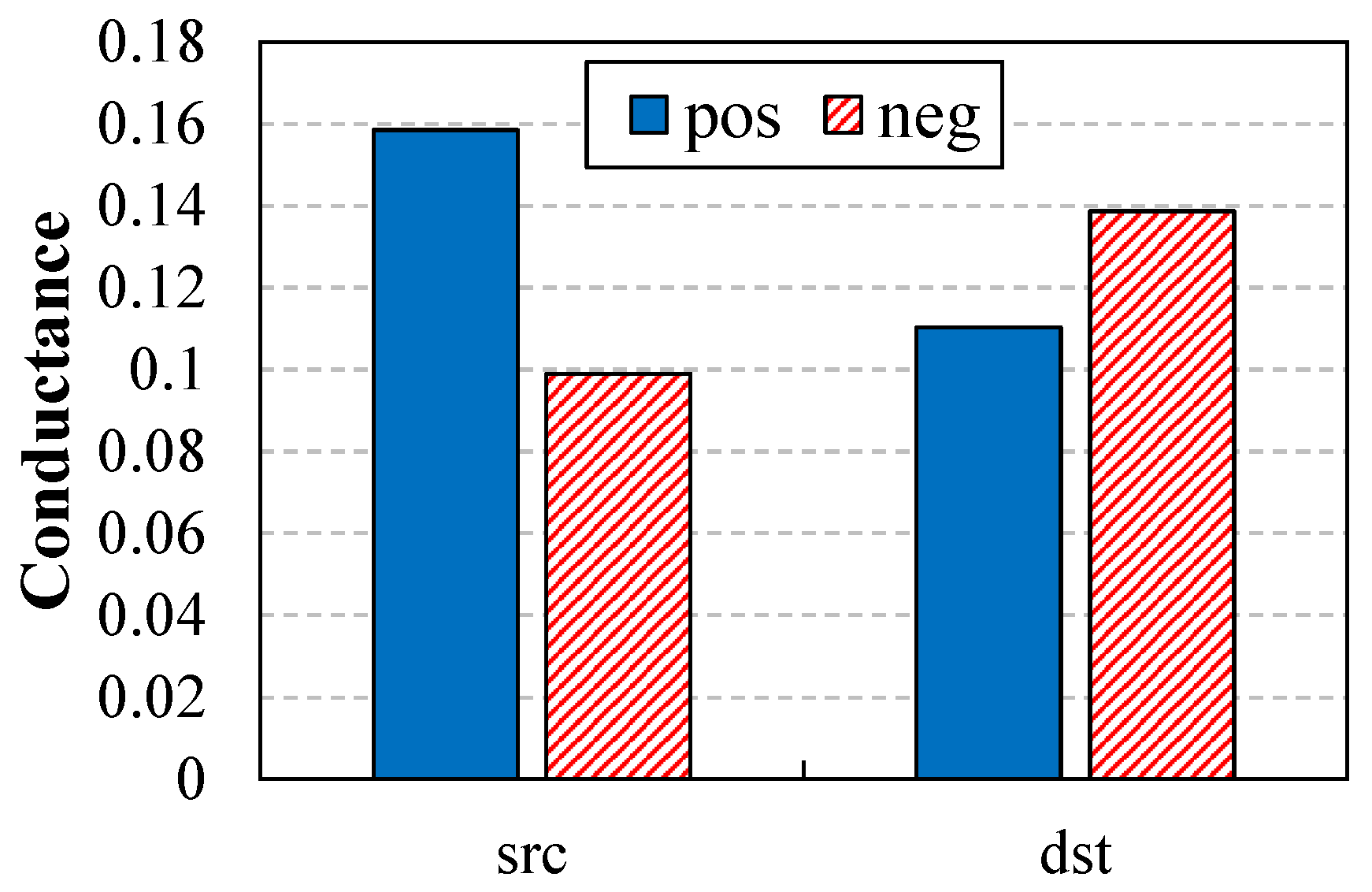
4.1.2. Conductance Analysis
4.1.3. Graph-Converting Method
4.2. Validation
5. Performance Evaluation
5.1. Settings
- Balance: using only the balance feature;
- Status: using only the status feature;
- Balance and Status: using both the balance and status features.
5.2. Results
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Aboulhosn, S. Facebook Statistics. 2020. Available online: https://sproutsocial.com/insights/facebook-stats-for-marketers (accessed on 3 August 2020).
- Benevenuto, F.; Magno, G.; Rodrigues, T.; Almeida, V. Detecting spammers on twitter. In Proceedings of the Collaboration, Electronic Messaging, Anti-Abuse and Spam Conference (CEAS), Redmond, WA, USA, 13–14 July 2010. [Google Scholar]
- Martinez-Romo, J.; Araujo, L. Detecting malicious tweets in trending topics using a statistical analysis of language. Expert Syst. Appl. 2013, 40, 2992–3000. [Google Scholar] [CrossRef]
- Egele, M.; Stringhini, G.; Kruegel, C.; Vigna, G. Towards Detecting Compromised Accounts on Social Networks. IEEE Trans. Dependable Secur. Comput. 2017, 14, 447–460. [Google Scholar] [CrossRef]
- Yardi, S.; Romero, D.; Schoenebeck, G.; Boyd, D. Detecting Spam in a Twitter Network. First Monday 2010, 15. [Google Scholar] [CrossRef]
- Viswanath, B.; Bashir, M.A.; Crovella, M.; Guha, S.; Gummadi, K.P.; Krishnamurthy, B.; Mislove, A. Towards detecting anomalous user behavior in online social networks. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 223–238. [Google Scholar]
- Stringhini, G.; Wang, G.; Egele, M.; Kruegel, C.; Vigna, G.; Zheng, H.; Zhao, B.Y. Follow the green: Growth and dynamics in twitter follower markets. In Proceedings of the 2013 Conference on Internet Measurement Conference, Barcelona, Spain, 23–25 October 2013; pp. 163–176. [Google Scholar]
- Ghosh, S.; Viswanath, B.; Kooti, F.; Sharma, N.K.; Korlam, G.; Benevenuto, F.; Ganguly, N.; Gummadi, K.P. Understanding and combating link farming in the twitter social network. In Proceedings of the 21st International Conference on World Wide Web, Lyon, France, 16–20 April 2012; pp. 61–70. [Google Scholar]
- Boshmaf, Y.; Logothetis, D.; Siganos, G.; Lería, J.; Lorenzo, J.; Ripeanu, M.; Beznosov, K. Integro: Leveraging Victim Prediction for Robust Fake Account Detection in OSNs; NDSS: San Diego, CA, USA, 2015; Volume 15, pp. 8–11. [Google Scholar]
- Cao, Q.; Sirivianos, M.; Yang, X.; Pregueiro, T. Aiding the detection of fake accounts in large scale social online services. In Proceedings of the 9th USENIX Symposium on Networked Systems Design and Implementation (NSDI 12), San Jose, CA, USA, 25–27 April 2012; pp. 197–210. [Google Scholar]
- Li, X.; Liu, Y.; Zhang, M.; Ma, S.; Zhu, X.; Sun, J. Detecting Promotion Campaigns in Community Question Answering; IJCAI: Buenos Aires, Argentina, 2015; Volume 15, pp. 2348–2354. [Google Scholar]
- Page, L.; Brin, S.; Motwani, R.; Winograd, T. The PageRank Citation Ranking: Bringing Order to the Web; Technical Report; Stanford InfoLab: Stanford, CA, USA, 1999. [Google Scholar]
- Chen, R.; Hua, Q.; Wang, B.; Zheng, M.; Guan, W.; Ji, X.; Gao, Q.; Kong, X. A novel social recommendation method fusing user’s social status and homophily based on matrix factorization techniques. IEEE Access 2019, 7, 18783–18798. [Google Scholar] [CrossRef]
- Yin, X.; Hu, X.; Chen, Y.; Yuan, X.; Li, B. Signed-PageRank: An Efficient Influence Maximization Framework for Signed Social Networks. IEEE Trans. Knowl. Data Eng. 2019. [Google Scholar] [CrossRef]
- Kleinberg, J.M. Authoritative sources in a hyperlinked environment. J. ACM (JACM) 1999, 46, 604–632. [Google Scholar] [CrossRef]
- Jiang, M.; Cui, P.; Beutel, A.; Faloutsos, C.; Yang, S. Catchsync: Catching synchronized behavior in large directed graphs. In Proceedings of the 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, New York, NY, USA, 24–27 August 2014; pp. 941–950. [Google Scholar]
- Ye, J.; Akoglu, L. Discovering opinion spammer groups by network footprints. In Joint European Conference on Machine Learning and Knowledge Discovery in Databases; Springer: Berlin/Heidelberg, Germany, 2015; pp. 267–282. [Google Scholar]
- Gao, H.; Yang, Y.; Bu, K.; Chen, Y.; Downey, D.; Lee, K.; Choudhary, A. Spam ain’t as diverse as it seems: Throttling OSN spam with templates underneath. In Proceedings of the 30th Annual Computer Security Applications Conference, New Orleans, LA, USA, 8–12 December 2014; pp. 76–85. [Google Scholar]
- Cao, Q.; Yang, X.; Yu, J.; Palow, C. Uncovering large groups of active malicious accounts in online social networks. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 477–488. [Google Scholar]
- Chino, D.Y.; Costa, A.F.; Traina, A.J.; Faloutsos, C. VolTime: Unsupervised Anomaly Detection on Users’ Online Activity Volume. In Proceedings of the 2017 SIAM International Conference on Data Mining, SIAM, Houston, TX, USA, 27–29 April 2017; pp. 108–116. [Google Scholar]
- Li, X.; Zhang, M.; Liu, Y.; Ma, S.; Jin, Y.; Ru, L. Search engine click spam detection based on bipartite graph propagation. In Proceedings of the 7th ACM International Conference on Web Search and Data Mining, New York, NY, USA, 24–28 February 2014; pp. 93–102. [Google Scholar]
- Tian, T.; Zhu, J.; Xia, F.; Zhuang, X.; Zhang, T. Crowd fraud detection in internet advertising. In Proceedings of the 24th International Conference on World Wide Web, Florence, Italy, 18–22 May 2015; pp. 1100–1110. [Google Scholar]
- Maity, S.K.; KC, S.; Mukherjee, A. Spam2vec: Learning biased embeddings for spam detection in twitter. In Proceedings of the The Web Conference 2018, Lyon, France, 23–27 April 2018; pp. 63–64. [Google Scholar]
- Yuan, C.; Zhou, W.; Ma, Q.; Lv, S.; Han, J.; Hu, S. Learning review representations from user and product level information for spam detection. In Proceedings of the 2019 IEEE International Conference on Data Mining (ICDM), Beijing, China, 8–11 November 2019; pp. 1444–1449. [Google Scholar]
- Liu, Z.; Dou, Y.; Yu, P.S.; Deng, Y.; Peng, H. Alleviating the Inconsistency Problem of Applying Graph Neural Network to Fraud Detection. arXiv 2020, arXiv:2005.00625. [Google Scholar]
- Ji, S.j.; Zhang, Q.; Li, J.; Chiu, D.K.; Xu, S.; Yi, L.; Gong, M. A burst-based unsupervised method for detecting review spammer groups. Inf. Sci. 2020, 536, 454–469. [Google Scholar] [CrossRef]
- Li, H.; Fei, G.; Wang, S.; Liu, B.; Shao, W.; Mukherjee, A.; Shao, J. Bimodal distribution and co-bursting in review spam detection. In Proceedings of the 26th International Conference on World Wide Web, Perth, Australia, 3–7 April 2017; pp. 1063–1072. [Google Scholar]
- Breuer, A.; Eilat, R.; Weinsberg, U. Friend or Faux: Graph-Based Early Detection of Fake Accounts on Social Networks. In Proceedings of the Web Conference 2020, Taipei, Taiwan, 20–24 April 2020; pp. 1287–1297. [Google Scholar]
- Jeong, S.; Noh, G.; Oh, H.; Kim, C.k. Follow spam detection based on cascaded social information. Inf. Sci. 2016, 369, 481–499. [Google Scholar] [CrossRef]
- Leskovec, J.; Huttenlocher, D.; Kleinberg, J. Signed networks in social media. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Atlanta, GA, USA, 10–15 April 2010; pp. 1361–1370. [Google Scholar]
- Heider, F. Social perception and phenomenal causality. Psychol. Rev. 1944, 51, 358. [Google Scholar] [CrossRef]
- Cha, M.; Haddadi, H.; Benevenuto, F.; Gummadi, P.K. Measuring user influence in twitter: The million follower fallacy. Icwsm 2010, 10, 30. [Google Scholar]
- Zhou, D.; Zhang, S.; Yildirim, M.Y.; Alcorn, S.; Tong, H.; Davulcu, H.; He, J. A Local Algorithm for Structure-Preserving Graph Cut. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Association for Computing Machinery, New York, NY, USA, 13–17 August 2017; pp. 655–664. [Google Scholar]
- Riquelme, F.; González-Cantergiani, P. Measuring user influence on Twitter: A survey. Inf. Process. Manag. 2016, 52, 949–975. [Google Scholar] [CrossRef]
- Rosa, H.; Carvalho, J.P.; Astudillo, R.; Batista, F. Detecting user influence in twitter: Pagerank vs. katz, a case study. In Proceedings of the Seventh European Symposium on Computational Intelligence and Mathematics, Cádiz, Spain, 7–10 October 2015; pp. 7–10. [Google Scholar]
- Blondel, V.D.; Guillaume, J.L.; Lambiotte, R.; Lefebvre, E. Fast unfolding of communities in large networks. J. Stat. Mech. Theory Exp. 2008, 2008, P10008. [Google Scholar] [CrossRef]
- Chung, F.R.; Graham, F.C. Spectral Graph Theory; American Mathematical Soc.: Providence, RI, USA, 1997. [Google Scholar]
- Quinlan, J. C4. 5: Programs for Machine Learning; Elsevier: Amsterdam, The Netherlands, 2014. [Google Scholar]
- Witten, I.H.; Frank, E.; Hall, M.A. Weka 3. 2011. Available online: https://www.cs.waikato.ac.nz/ml/weka/ (accessed on 1 September 2020).



| The number of users | 54,981,152 |
| The number of spammers | 41,352 |
| The number of following links | 1,963,263,821 |
| Epinions | |
|---|---|
| The number of nodes | 131,828 |
| The number of edges | 841,372 |
| The ratio of positive edges | 85% |
| The ratio of negative edges | 15% |
| Positive Edge | 464,119 (64.67%) | 252,135 (35.13%) | 1412 (0.20%) |
| Negative Edge | 43,261 (34.97%) | 80,396 (64.99%) | 49 (0.04%) |
| Rank | Information Gain | Feature | Rank | Information Gain | Feature |
|---|---|---|---|---|---|
| 1 | 0.639 | ST9 | 11 | 0.522 | BT2 |
| 2 | 0.613 | ST1 | 12 | 0.507 | ST8 |
| 3 | 0.609 | BT3 | 13 | 0.436 | ST14 |
| 4 | 0.605 | T11 | 14 | 0.411 | ST2 |
| 5 | 0.603 | ST3 | 15 | 0.363 | BT0 |
| 6 | 0.584 | BT1 | 16 | 0.348 | ST10 |
| 7 | 0.573 | ST5 | 17 | 0.339 | ST13 |
| 8 | 0.560 | ST12 | 18 | 0.311 | ST15 |
| 9 | 0.552 | ST7 | 19 | 0.251 | ST6 |
| 10 | 0.551 | ST4 | 20 | 0.211 | ST16 |
| Accuracy | Precision | Recall | FPR | F1-Score | |
|---|---|---|---|---|---|
| SybilRank | 0.283 | 0.303 | 0.335 | 0.769 | 0.318 |
| NFS | 0.572 | 0.597 | 0.443 | 0.299 | 0.509 |
| CatchSync | 0.903 | 0.894 | 0.915 | 0.109 | 0.904 |
| TSP | 0.908 | 0.906 | 0.911 | 0.095 | 0.908 |
| Balance | 0.925 | 0.943 | 0.904 | 0.055 | 0.923 |
| Status | 0.929 | 0.949 | 0.907 | 0.049 | 0.927 |
| Balance + Status | 0.928 | 0.948 | 0.906 | 0.050 | 0.926 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jeong, S.; Lee, K.-h. Spam Classification Based on Signed Network Analysis. Appl. Sci. 2020, 10, 8952. https://doi.org/10.3390/app10248952
Jeong S, Lee K-h. Spam Classification Based on Signed Network Analysis. Applied Sciences. 2020; 10(24):8952. https://doi.org/10.3390/app10248952
Chicago/Turabian StyleJeong, Sihyun, and Kyu-haeng Lee. 2020. "Spam Classification Based on Signed Network Analysis" Applied Sciences 10, no. 24: 8952. https://doi.org/10.3390/app10248952
APA StyleJeong, S., & Lee, K.-h. (2020). Spam Classification Based on Signed Network Analysis. Applied Sciences, 10(24), 8952. https://doi.org/10.3390/app10248952





