Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems
Featured Application
Abstract
1. Introduction
2. Prior and Related Work
- Manual—the knowledge base is created by human experts in the field;
- Semi-automated—the knowledge base’s formation is partly automated;
- Automated—the knowledge base’s formation is fully automated, which is the most interesting for our research.
- The first approach is based on using existing knowledge sources directly in their native formats, e.g., ontologies and databases, without additional transformations.
- The second is applied when existing knowledge sources are transformed into ES knowledge base rules.
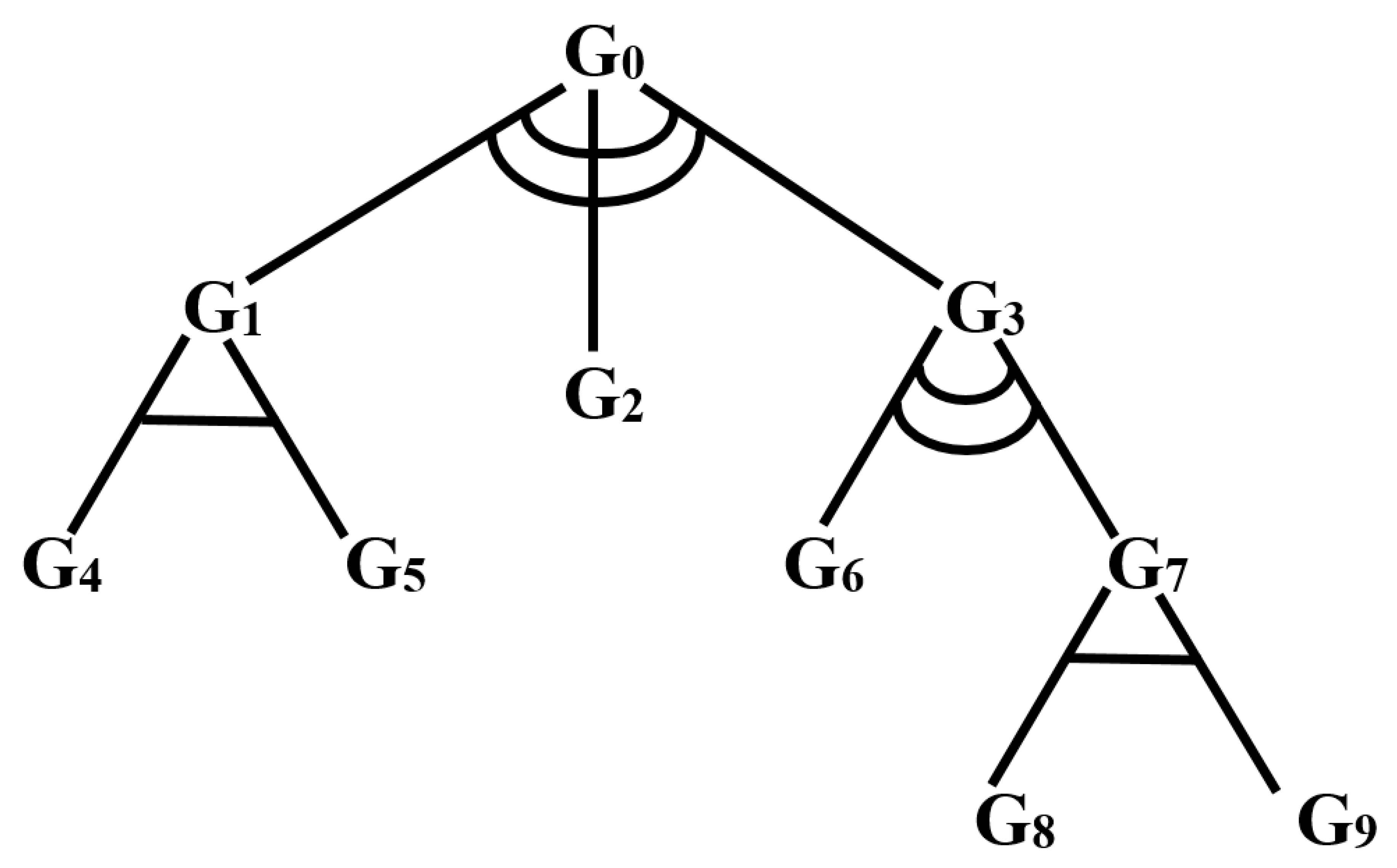
3. Attack Trees in XML
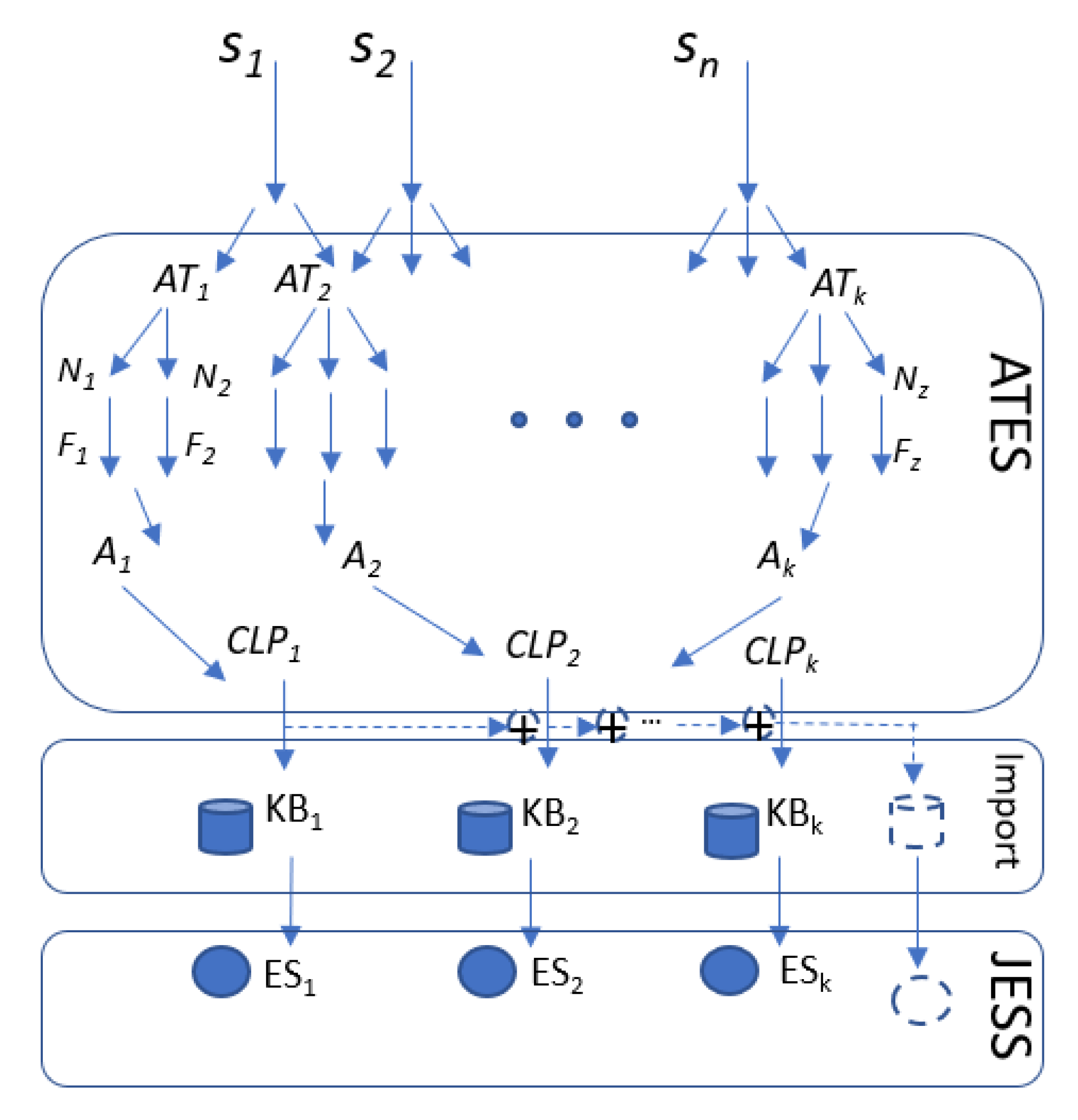
4. Method
- Tree template (TT)—information about the converted attack tree (AT name, and root node (attack goal) name);
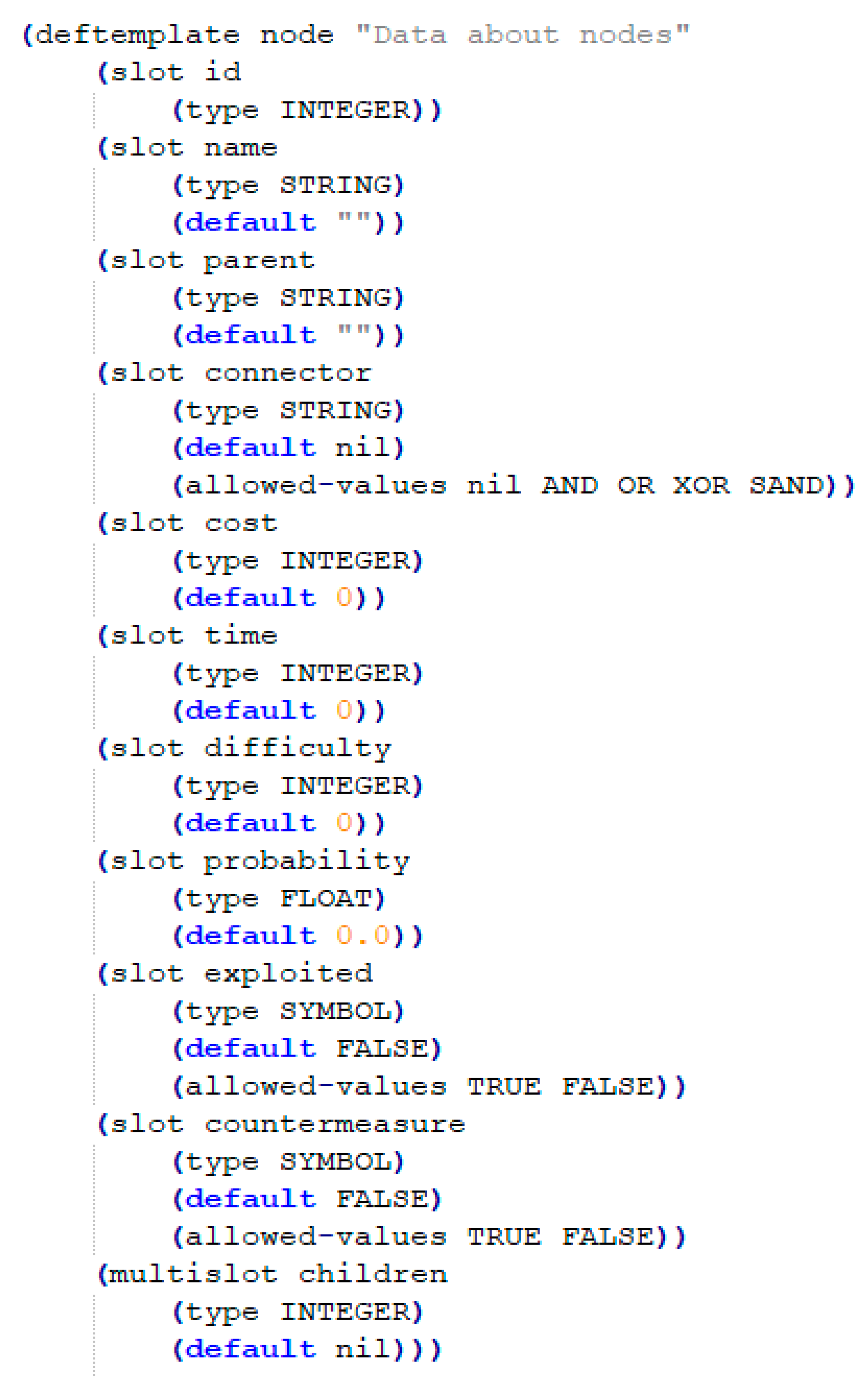
- Node template (NN)—a predefined structure to work with facts generated from attack trees;
- Facts about the attack, generated in the transformation process.
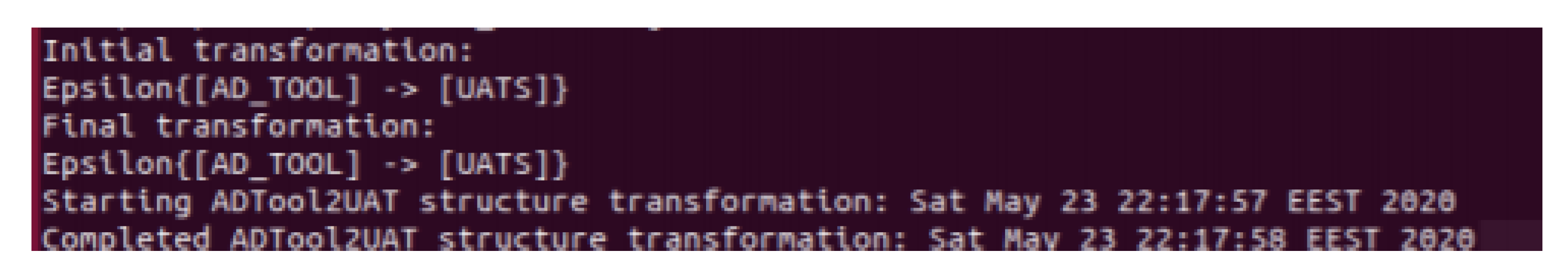
- Get AT data in XML format. The initial transformation of AT into XML format is performed due to its versatility.
- In UATS format. XML UATS format enables the use of a larger variety of AT sources, so our tool is made to work with XML UATS from the beginning. Examples of AT in XML UATS and graphical formats are given in Figure 7.
- Convert to UATS using ATTop. The attack tree can be directly exported to XML UATS or converted from various formats. The tool we propose using in this step is ATTop [37].
- Input AT Data to ATES. ATES is our Python-based software for the method’s practical implementation that performs conversion of UATS into the JESS format.
- Conversion Py script. Conversion engine which converts XML UATS to CLP rules and DAT facts by applying defined patterns. Examples of resulting ES knowledge base facts are presented in Figure 8.
- Exception handler. The exception handler, a “try–except” code block that will terminate the processes and return an error message to the user in case any errors occur.
- Process termination. Terminates the process if any error occurs.
- Output data. Converted rules are exported to the CLP and DAT files (or one combined file if the user selects this option), supported by the JESS ES platform.
- JESS facts. The result of the transformation process is a JESS-based expert system knowledge base of rules and facts.
- Working memory. Automatically generated ES knowledge base rules and facts in CLP format are imported into ES working memory.
- Prepared knowledge base structure. ES should be able to work with the given (imported) facts. Our method utilizes the prepared knowledge base structure (Figure 9), which accepts facts generated by ATES.
- Inference engine. We use the JESS inference engine, which utilizes the RETE algorithm.
- Perform IT security risk analysis. At this moment, our ES is prepared for IT security risk analysis, utilizing automatically generated knowledge base rules from the attack trees.
- Risk analysis results and recommendations. The expert system, interacting with the user, performs risk analysis, and gives the results.
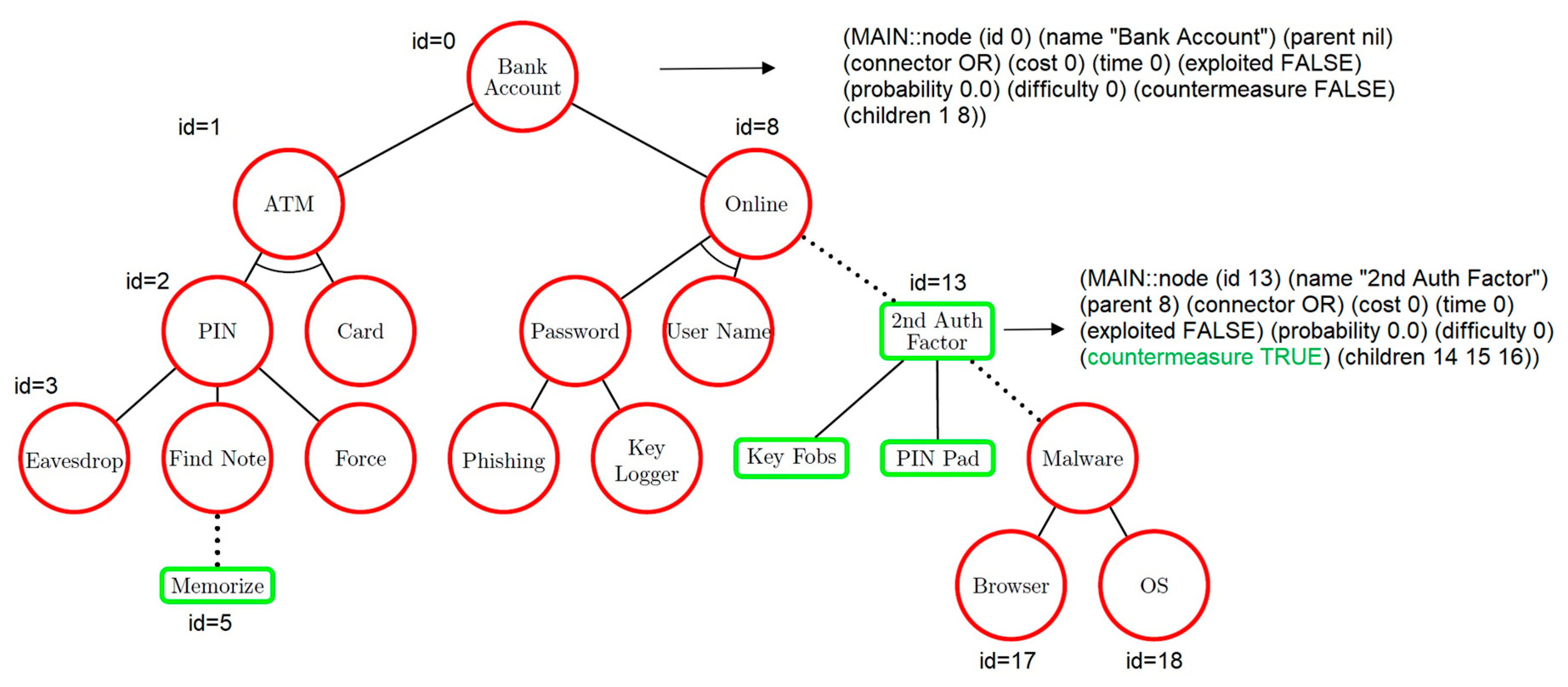
- ID. It is the ID of the node. Count from top to bottom and from left to right.
- Name. The name of the node is read from the attack tree.
- Parent. Depicts which node is the parent of the current node. The value is the node ID number.
- Connector. It defines the node type. Possible values are OR, AND.
- Cost. It is the cost of the attack if this value is specified in the attack tree.
- Time. It is the time needed to perform the attack if this value is given in the attack tree.
- Exploited. It is the state of the node. By default, all values have FALSE values, and they can be changed during the risk analysis process in the ES. A value can become TRUE based on the user’s answers.
- Probability. It is the probability of the attack if this value is given in the attack tree.
- Difficulty. It is the difficulty of the attack if this value is given in the attack tree.
- Countermeasure. It identifies whether the node already has countermeasures applied or not. Possible values are TRUE, FALSE.
- Children. It shows what children this current node has. The value is node ID numbers.
5. Results and Discussion
- Preparing attack tree data (data pre-processing). The creation of an attack tree in one of the various formats accepted by ATTop or direct creation of a UATS XML file must be done by the user. Once the UATS file is returned from ATTop, the ATES program is ready to accept the file for translation. Successful transformation to UATS via ATTop is demonstrated in Figure 12.
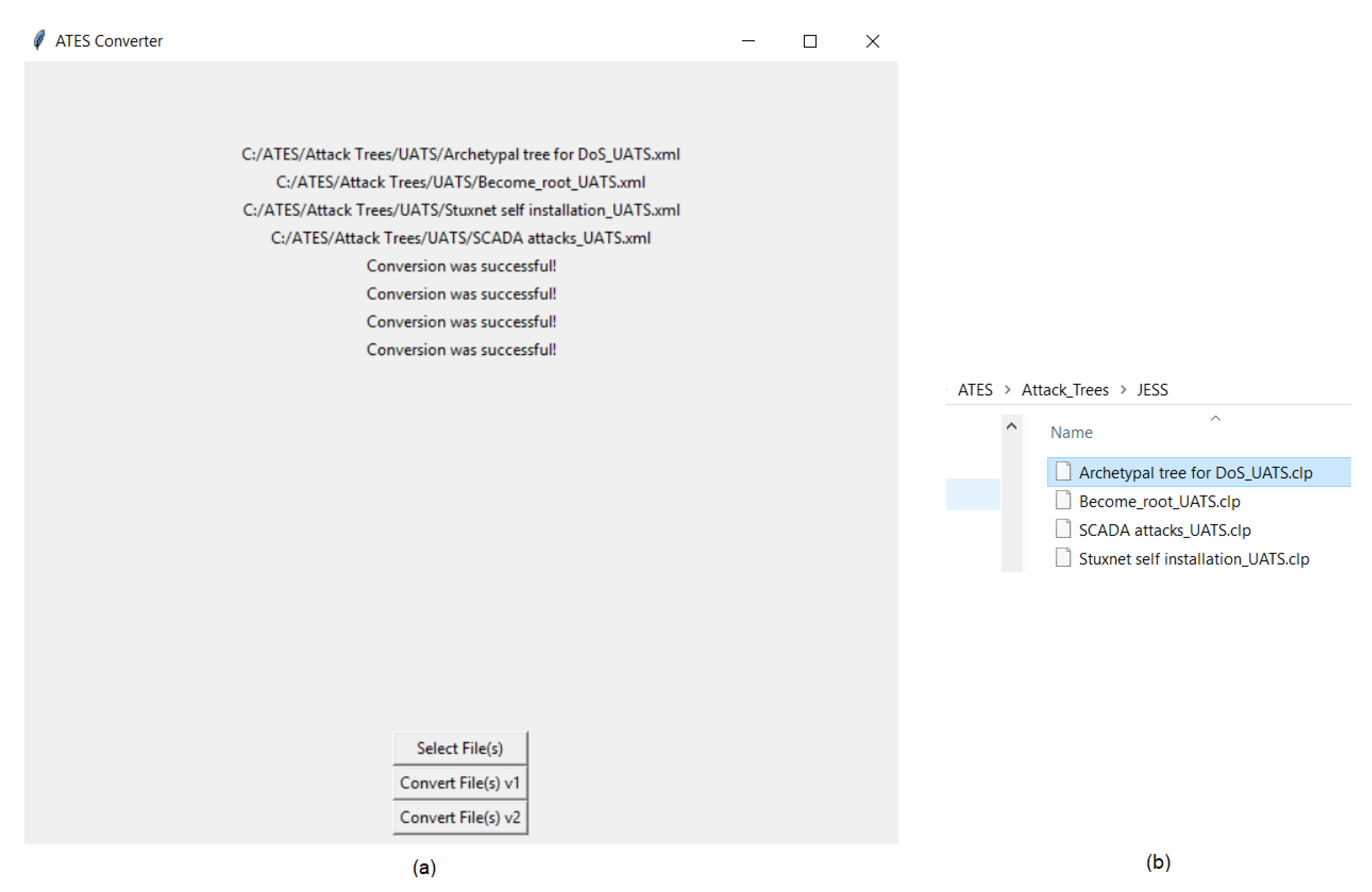
- Add file. Once the UATS file is returned from ATTop, the ATES program is ready to accept the file for translation. ATES has a simple GUI created using the Tkinter package in Python.
- Translatev1/2. This function is wholly encased in a “try–except” block which is a built-in function of Python which is designed for error handling. Any errors from any of the functions within this block result in the deletion of the data and, because of how this “try–except” block is configured, an error message gets displayed on the screen.
- Ates. The ates function first takes the files in input and retrieves the filename; then sends the files to the inputter function for parsing; then sends the parsed data to the inputter function to extract the necessary node information into lists, before finally sending the lists to the printer function which will write the files. The ates function will also take the value sent with file data from the translate functions, called pvalue, and will modify the new file name to differentiate between version one and version two if the pvalue is 2.
- Inputter. The inputter function parses the XML file using the defused XML ElementTree package built into Python. Using the defused XML package prevents code execution from maliciously crafted XML files. The function returns an XML document object model, or DOM, for use by the lister function.
- Lister. The lister function takes the XML DOM from the inputter function and extracts the necessary data from it. It does this by first creating empty lists, then finding the attributes to fill each list. It then returns the full lists to the ates function to be sent to the printer function.
- Printer. The printer function has a “try–except” block for creating a directory to store the output files from the conversion process. The files created by this function will also expect this directory to exist and will provide the user with the command to run if the files are in this directory. Next, the function will open the new .clf file in write mode, or create it in write mode if it does not exist, and write the JESS program code which has been written. If pvalue is 1 then the function will write necessary JESS code and the list data from lister into the same file, but, if pvalue is 2, then it will write an additional JESS code and create a new .dat file for containing the attack tree’s node data. All the files will be named automatically based upon the original input file name. Once these processes have been completed, the files will be saved and closed.
- JESS ES file(s). The produced JESS programs have an initial welcome message at the top of each file with instructions on where to place the files and with what JESS command to run the files. Successful JESS operation is shown in Figure 14.
5.1. Current Issues and Controls Applied
- One potential issue of the method proposed is that there is a small possibility that data are altered during the transformation processes. To resolve this issue, the data were visually compared during the heuristic phase from the input to the resulting files to verify the accuracy.
- Another weakness of the proposed method is that the output data will only be as reliable as the input data. That is to say that, if an inaccurate attack tree is converted to the expert system rules, then the expert system will not provide accurate information regarding any eventual risk assessments. There is, ultimately, not any way around this issue beyond double-checking that the attack trees are accurate, come from the reliable sources, and apply to the system in question. This will require that users of this method would have some knowledge of their systems and that they are receiving accurate attack tree information.
- Potentially, the greatest issue in this method lies in the extreme variability within XML. This has been mitigated somewhat by using the output from ATTop to standardize the expected input to ATES. However, the naming conventions of various tools being capable of significant differences for the same attributes (e.g., the attribute identifier “duration” referring to the length of time required for an attack could also be called “time” or even “length” by specific tools) means that the only solution is to code each tool’s naming convention into the lister function.
5.2. Advantages of the Methodology
- Due to the popularity and ease of use of the Python programming language, it is relatively easy to increase the acceptable attack tree formats by determining the attribute identifiers used within that tool’s XML format. Utilizing an “if–then” statement within the lister function would allow for the conversion of these attack trees as well.
- The configuration of version two allows for a relatively small set of changes which would mean a single JESS expert system could read the .dat files for multiple attack trees. As the data are already in a separate file, it would be possible to select multiple .dat files to minimize consumed storage space on a device. This was not pursued by the authors due to a lack of necessity in modern systems.
- Finally, there are several points where data can be configured by the user, and it will be accepted throughout. It is possible to set the attribute values either before translation in ATTop, after translation from ATTop and before input to ATES, after output from ATES by manually editing the data files, or inside the JESS program created by ATES. The most efficient and accurate method is to either modify the final JESS .dat files or the XML files after being output from ATTop.
5.3. Future Work
- Incorporation of PDF files as a source of attack tree;
- Minimizing the time for the file inputting process by creating the automated input file batch process;
- Resolving the issues related to the variability of attack tree representation and naming formats.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Janulevičius, J.; Čenys, A. Development of a Risk Assessment Model for IT Risk Self-Assessment Expert System for SMEs. Int. J. Comput. Commun. Eng. 2016, 3, 306–309. [Google Scholar] [CrossRef]
- Abraham, A. Rule-Based Expert Systems. In Handbook of Measuring System Design; John Wiley and Sons: New York, NY, USA, 2005. [Google Scholar]
- Akerkar, R.A.; Sajja, P.S. KnowledgeBased Systems; Jones & Bartlett Publishers: Toronto, ON, Canada, 2010. [Google Scholar]
- Batista, L.O.; de Silva, G.A.; Araujo, V.S.; Araujo, V.J.S.; Rezende, T.S.; Guimaraes, A.J.; Souza, P.V.D.C. Fuzzy neural networks to create an expert system for detecting attacks by sql injection. Int. J. Forensic Comput. Sci. 2018, 1, 8–21. [Google Scholar] [CrossRef]
- Dheir, I.; Abu-Naser, S.S. Knowledge Based System for Diagnosing Guava Problems. Int. J. Acad. Inf. Syst. Res. (IJAISR) 2019, 3, 9–15. [Google Scholar]
- Atymtayeva, L.; Kozhakhmet, K.; Bortsova, G. Building a Knowledge Base for Expert System in Information Security. In Soft Computing in Artificial Intelligence; Advances in Intelligent Systems and Computing Series; Springer: Cham, Switzerland, 2014; pp. 57–76. [Google Scholar]
- Ivkin, A.N.; Burlakov, M.E. Realization of expert intrusion detection system based on the results of datasets and machine learning algorithm analysis. Prikaspijskij Zurnal Upravelnije Vysok. Technol. 2020, 2, 100–107. [Google Scholar]
- Pinto, F.J. Application of the Bayesian Model in Expert Systems. In Proceedings of the International Symposium on Distributed Computing and Artificial Intelligence, Ávila, Spain, 26–28 June 2019; Springer: Cham, Switzerland, 2019; pp. 117–124. [Google Scholar]
- Vitkus, D.; Steckevičius, Ž.; Goranin, N.; Kalibatienė, D.; Čenys, A. Automated Expert System Knowledge Base Development Method for Information Security Risk Analysis. Int. J. Comput. Commun. Control 2019, 14, 743–758. [Google Scholar] [CrossRef]
- Vitkus, D.; Jezukevičiūtė, J.; Goranin, N. Dynamic Expert System-Based Geographically Adapted Malware Risk Evaluation Method. Int. J. Comput. Commun. Control 2020, 15. [Google Scholar] [CrossRef]
- Kim, D.; Shin, D.; Shin, D.; Kim, Y.H. Attack detection application with attack tree for mobile system using log analysis. Mob. Netw. Appl. 2019, 24, 184–192. [Google Scholar] [CrossRef]
- Kornecki, A.J.; Liu, M. Fault tree analysis for safety/security verification in aviation software. Electronics 2013, 2, 41–56. [Google Scholar] [CrossRef]
- Rios, E.; Rego, A.; Iturbe, E.; Higuero, M.; Larrucea, X. Continuous Quantitative Risk Management in Smart Grids Using Attack Defense Trees. Sensors 2020, 20, 4404. [Google Scholar] [CrossRef]
- Qiu, S.; Liu, Q.; Zhou, S.; Wu, C. Review of artificial intelligence adversarial attack and defense technologies. Appl. Sci. 2019, 9, 909. [Google Scholar] [CrossRef]
- Ingoldsby, T.R. Attack Tree-Based Threat Risk Analysis; Amenaza Technologies Limited: Calgary, AB, Canada, 2010; pp. 3–9. [Google Scholar]
- Lohner, B. Attack-Defense-Trees and other Security Modeling Tools. Network 2018, 97, 97–103. [Google Scholar]
- Kordy, B.; Kordy, P.; Mauw, S.; Schweitzer, P. ADTool: Security analysis with attack-defense trees. In Quantitative Evaluation of Systems; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin, Germany, 2013; pp. 173–176. [Google Scholar] [CrossRef]
- Gadyatskaya, O.; Harpes, C.; Mauw, S.; Muller, C.; Muller, S. Bridging two worlds: Reconciling practical risk assessment methodologies with theory of attack trees. Artif. Intell. Lect. Notes Bioinform. 2016, 9987, 80–93. [Google Scholar] [CrossRef]
- Shostack, A. Threat Modeling: Designing for Security; Wysopal, C., Ed.; John Wiley & Sons, Inc.: Indianapolis, IN, USA, 2014. [Google Scholar]
- Wenli, S.; Tianyu, G.; Chunyu, C.; Jing, H.; Peng, Z. Information Security Risk Assessment Method for Ship Control System Based on Fuzzy Sets and Attack Trees. Secur. Commun. Netw. 2019, 2019, 3574675. [Google Scholar] [CrossRef]
- Fila, B.; Wideł, W. Exploiting attack–defense trees to find an optimal set of countermeasures. In Proceedings of the 2020 IEEE 33rd Computer Security Foundations Symposium (CSF), Boston, MA, USA, 22–26 June 2020; pp. 395–410. [Google Scholar]
- Moore, A.P.; Ellison, R.J.; Linger, R.C. Attack Modelling for Information Security and Survivability; Carnegie Mellon University, Software Engineering Institute: Pittsburgh, PA, USA, 2001. [Google Scholar]
- Schneier, B. Attack Trees. Dr. Dobb’s J. 1999, 24, 21–29. [Google Scholar]
- Huistra, D.J. Automated gEneration of Attack Trees by Unfolding Graph Transformation Systems. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2016. [Google Scholar]
- Kordy, B.; Pietre-Cambacedes, L.; Schweitzer, P. DAG-based attack and defense modeling: Don’t miss the forest for the attack trees. Comput. Sci. Rev. 2014, 13–14, 1–38. [Google Scholar] [CrossRef]
- Saini, V.; Duan, Q.; Paruchuri, V. Threat modeling using attack trees. J. Comput. Sci. Coll. 2008, 23, 124–131. [Google Scholar]
- Salter, C.; Saydjari, O.S.; Schneier, B.; Wallner, J. Toward a secure system engineering methodolgy. In Proceedings of the 1998 Workshop on New Security Paradigms—NSPW ’98, Charlottsville, VA, USA, 22–25 September 1998; pp. 2–10. [Google Scholar] [CrossRef]
- Sheyner, O.; Wing, J. Tools for generating and analyzing attack graphs. In Proceedings of the International Symposium on Formal Methods for Components and Objects, Leiden, The Netherlands, 4–7 November 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 344–371. [Google Scholar] [CrossRef]
- Gadyatskaya, O.; Jhawar, R.; Kordy, P.; Lounis, K.; Mauw, S.; Trujillo-Rasua, R. Attack trees for practical security assessment: Ranking of attack scenarios with ADTool 2.0. In Proceedings of the International Conference on Quantitative Evaluation of Systems, Glasgow, UK, 10–12 September 2016; pp. 159–162. [Google Scholar]
- Vigo, R.; Nielson, F.; Nielson, H.R. Automated generation of attack trees. In Proceedings of the 2014 IEEE 27th Computer Security Foundations Symposium, Vienna, Austria, 19–22 July 2014; pp. 337–350. [Google Scholar]
- Wang, P.; Lin, W.H.; Kuo, P.T.; Lin, H.T.; Wang, T.C. Threat risk analysis for cloud security based on Attack-Defense Trees. In Proceedings of the 2012 8th International Conference on Computing Technology and Information Management (NCM and ICNIT), Seoul, Korea, 24–26 April 2012; Volume 1, pp. 106–111. [Google Scholar]
- Pinchinat, S.; Acher, M.; Vojtisek, D. Towards synthesis of attack trees for supporting computer-aided risk analysis. In Proceedings of the International Conference on Software Engineering and Formal Methods, Amsterdam, The Netherlands, 14–17 September 2014; pp. 363–375. [Google Scholar]
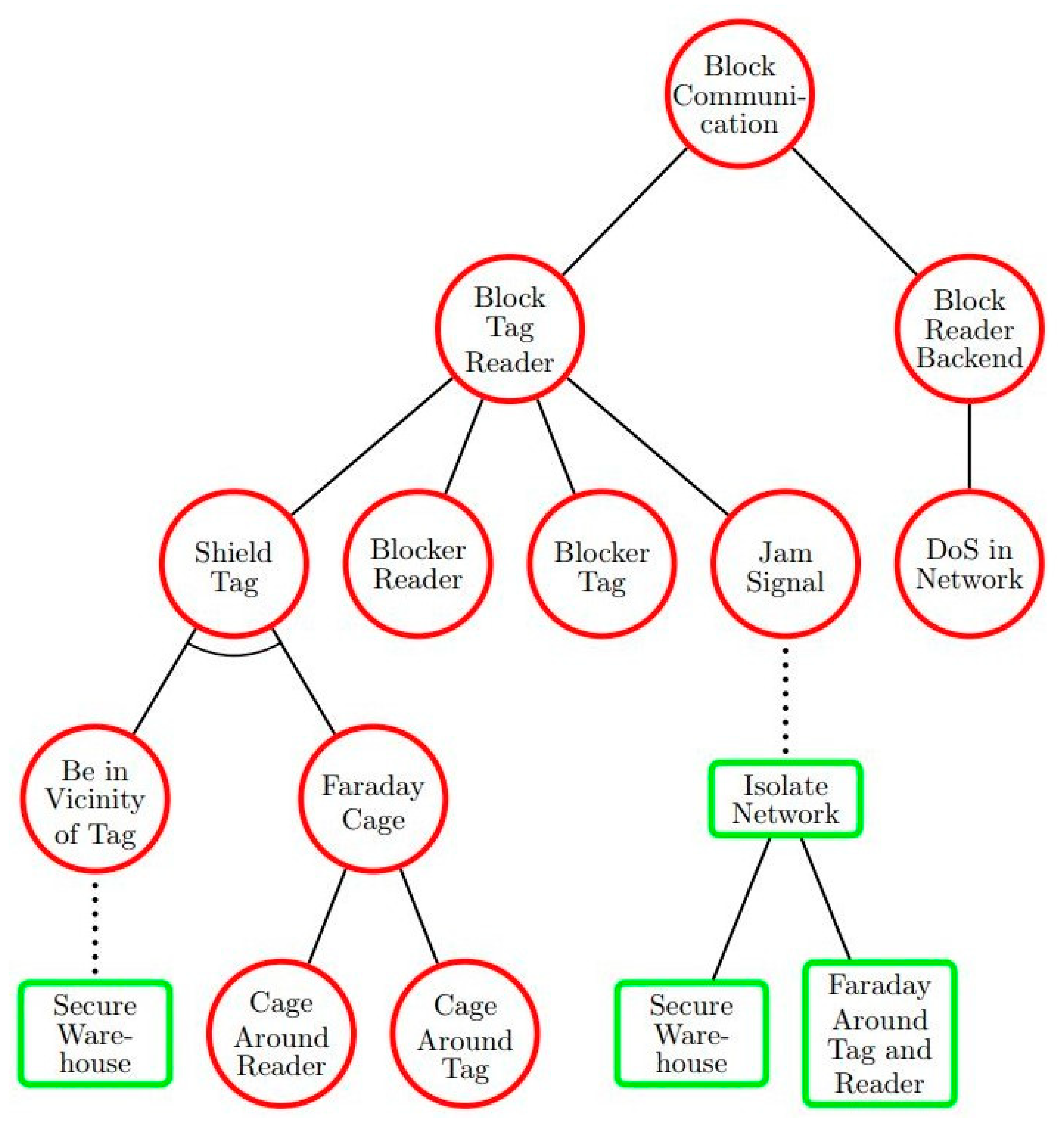
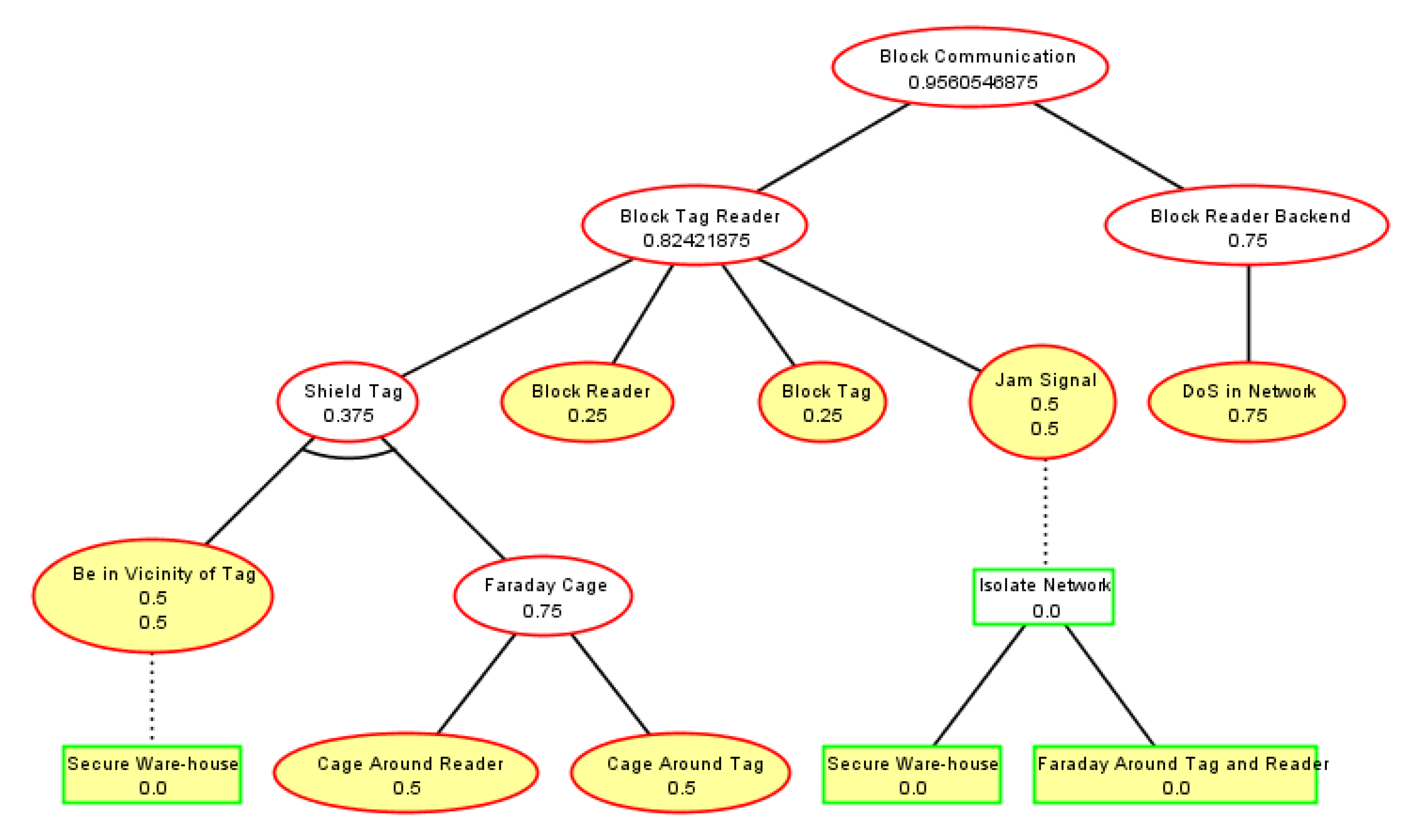
- RFID Communication Block. Security and Trust of Software Systems. Available online: https://satoss.uni.lu/projects/atrees/trees/block_communication.pdf (accessed on 14 April 2020).
- Audinot, M.; Pinchinat, S.; Kordy, B. Is my attack tree correct? In Computer Security—ESORICS 2017; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2017; pp. 83–102. [Google Scholar] [CrossRef]
- Jhawar, R.; Lounis, K.; Mauw, S.; Ramírez-Cruz, Y. Semi-automatically Augmenting Attack Trees Using an Annotated Attack Tree Library. In Security and Trust Management; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; pp. 85–101. [Google Scholar] [CrossRef]
- Tentilucci, M.; Roberts, N.; Kandari, S.; Johnson, D.; Bogaard, D.; Stackpole, B.; Markowsky, G. Crowdsourcing Computer Security Attack Trees. In Proceedings of the 10th Annual Symposium on Information Assurance (ASIA’15), Albany, NY, USA, 2–3 June 2015; pp. 19–23. [Google Scholar]
- Attack Tree Translator and Analyzer ATTop. University of Twente—Formal Methods and Tools. Available online: https://github.com/utwente-fmt/attop (accessed on 18 March 2020).
- Common Attack Pattern Enumeration and Classification. Mitre. Available online: https://capec.mitre.org (accessed on 20 April 2020).
- Knowledge Base of Adversary Tactics and Techniques. Mitre. Available online: https://attack.mitre.org (accessed on 20 April 2020).
- Abdo, H.; Kaouk, M.; Flaus, J.M.; Masse, F. A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie—Combining new version of attack tree with bowtie analysis. Comput. Secur. 2018, 72, 175–195. [Google Scholar] [CrossRef]
- Library of Trees. Security and Trust of Software Systems. Available online: https://satoss.uni.lu/projects/atrees/library.php (accessed on 14 April 2020).
- Vintr, Z.; Valis, D.; Malach, J. Attack tree-based evaluation of physical protection systems vulnerability. In Proceedings of the 2012 IEEE International Carnahan Conference on Security Technology (ICCST), Boston, MA, USA, 15–18 October 2012; pp. 59–65. [Google Scholar] [CrossRef]
- Jhawar, R.; Kordy, B.; Mauw, S.; Radomirović, S.; Trujillo-Rasua, R. Attack trees with sequential conjunction. JIFIP Adv. Inf. Commun. Technol. 2015, 455, 339–353. [Google Scholar] [CrossRef]
- Pietre-Cambacedes, L.; Bouissou, M. Beyond attack trees: Dynamic security modeling with Boolean logic Driven Markov Processes (BDMP). In Proceedings of the 2010 European Dependable Computing Conference, Valencia, Spain, 28–30 April 2010; pp. 199–208. [Google Scholar]
- Kumar, R.; Schivo, S.; Ruijters, E.; Yildiz, B.M.; Huistra, D.; Brandt, J.; Stoelinga, M. Effective Analysis of Attack Trees: A Model-Driven Approach. In Fundamental Approaches to Software Engineering; Russo, A., Schurr, A., Eds.; Springer: Cham, Switzerland, 2018; pp. 56–73. [Google Scholar] [CrossRef]
- Buckshaw, D.L.; Parnell, G.S.; Unkenholz, W.L.; Parks, D.L.; Wallner, J.M.; Saydjari, O.S. Mission oriented risk and design analysis of critical information systems. Mil. Oper. Res. 2005, 10, 19–38. [Google Scholar] [CrossRef]
- McLaughlin, S.; Podkuiko, D.; Miadzvezhanka, S.; Delozier, A.; McDaniel, P. Multi-vendor penetration testing in the advanced metering infrastructure. In Proceedings of the 26th Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2010; pp. 107–116. [Google Scholar] [CrossRef]
- Bogaard, D.; Johnson, D. Producing and Evaluating Crowdsourced Computer Security Attack Trees. In Proceedings of the 2016 IEEE Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 10–11 May 2016; pp. 1–4. [Google Scholar] [CrossRef]
- Ru, Y.; Wang, Y.; Li, J.; Liu, J.; Yang, G.; Yuan, K.; Liu, K. Risk assessment of cyber attacks in ECPS based on attack tree and AHP. In Proceedings of the 2016 12th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD 2016), Changsha, China, 13–15 August 2016; pp. 465–470. [Google Scholar] [CrossRef]
- Cole, E. SANS ICS Attack Surfaces. Available online: https://www.sans.org/summit-archives/file/summit-archive-1493739527.pdf (accessed on 14 April 2020).
- Kong, H.K.; Hong, M.K.; Kim, T.S. Security risk assessment framework for smart car using the attack tree analysis. J. Ambient Intell. Humaniz. Comput. 2018, 9, 531–551. [Google Scholar] [CrossRef]
- Petrica, G.; Axinte, S.; Bacivarov, I.C.; Firoiu, M.; Mihai, I.C. Studying Cyber Security Threats to Web Platforms Using Attack Tree Diagrams. In Proceedings of the 2017 9th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Targoviste, Romania, 29 June–1 July 2017; pp. 1–6. [Google Scholar]
- Xiao, Y.; Wang, Y.J.; Huang, Z.G. Survivability analysis of SOA based on attack tree models. In Proceedings of the International Conference on Communication Technology Proceedings, Chengdu, China, 9–11 November 2012; pp. 819–823. [Google Scholar] [CrossRef]
- Ingoldsby, T.R. Understanding risk through attack tree analysis. Comput. Secur. J. 2004, 20, 33–59. [Google Scholar]
- OWASP Risk Rating Methodology. Available online: https://owasp.org/www-project-risk-assessment-framework/ (accessed on 17 February 2020).







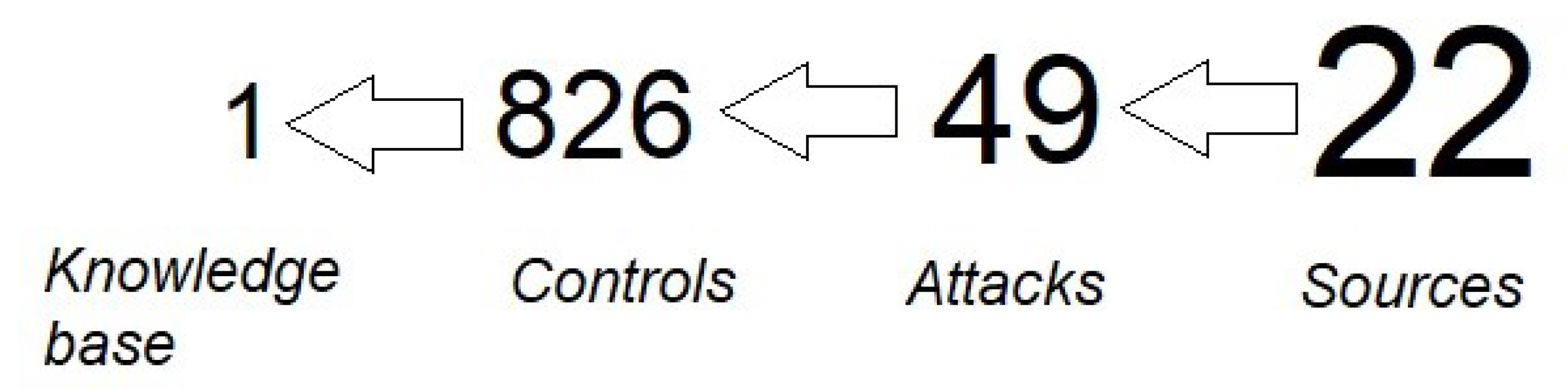

| Attack Tree Sources | Quantity of Attack Trees |
|---|---|
| A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie—combining new version of attack tree with bowtie analysis [40] | 7 |
| ADTool example attack trees [41] | 10 |
| Attack Modelling for Information Security and Survivability [22] | 2 |
| Attack tree-based evaluation of physical protection systems vulnerability [42] | 1 |
| Attack trees with sequential conjunction [43] | 2 |
| Automated Generation of Attack Trees by Unfolding Graph Transformation Systems [24] | 2 |
| Beyond attack trees: dynamic security modelling with Boolean logic Driven Markov Processes (BDMP ) [44] | 2 |
| Bridging two worlds: Reconciling practical risk assessment methodologies with theory of attack trees [18] | 1 |
| Crowdsourcing Computer Security Attack Trees [36] | 1 |
| DAG-based attack and defense modelling: Don’t miss the forest for the attack trees [25] | 1 |
| Effective Analysis of Attack Trees: A Model-Driven Approach [45] | 1 |
| Is my attack tree correct? [34] | 1 |
| Mission oriented risk and design analysis of critical information systems [46] | 1 |
| Multi-vendor Penetration Testing in the Advanced Metering Infrastructure [47] | 3 |
| Producing and Evaluating Crowdsourced Computer Security Attack Trees [48] | 1 |
| Risk assessment of cyber attacks in ECPS based on attack tree and AHP [49] | 1 |
| SANS ICS Attack Surfaces [50] | 1 |
| Security risk assessment framework for smart car using the attack tree analysis [51] | 5 |
| Semi-automatically Augmenting Attack Trees using an Annotated Attack Tree Library [35] | 2 |
| Studying Cyber Security Threats to Web Platforms Using Attack Tree Diagrams [52] | 1 |
| Survivability analysis of SOA based on attack tree models [53] | 1 |
| Understanding risk through attack tree analysis [54] | 2 |
| The total quantity of sourced attack trees: | 49 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vitkus, D.; Salter, J.; Goranin, N.; Čeponis, D. Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems. Appl. Sci. 2020, 10, 8423. https://doi.org/10.3390/app10238423
Vitkus D, Salter J, Goranin N, Čeponis D. Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems. Applied Sciences. 2020; 10(23):8423. https://doi.org/10.3390/app10238423
Chicago/Turabian StyleVitkus, Donatas, Jonathan Salter, Nikolaj Goranin, and Dainius Čeponis. 2020. "Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems" Applied Sciences 10, no. 23: 8423. https://doi.org/10.3390/app10238423
APA StyleVitkus, D., Salter, J., Goranin, N., & Čeponis, D. (2020). Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems. Applied Sciences, 10(23), 8423. https://doi.org/10.3390/app10238423







