A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks
Abstract
1. Introduction
- Secure and efficient authentication schemes are required to provide various services in GLOMONET.
- Authentication schemes must resist various attacks, including stolen mobile devices, masquerades, and trace attacks.
1.1. Motivation and Contributions
- 1.
- 2.
- Many authentication schemes must provide secure convenience for mobile users in the GLOMONET and must take into account all the security requirements specified in Section 1.2.
- 3.
- Secure and lightweight authentication schemes are essential, which take into account limitations for resource-constrained mobile devices relative to computing power, memory, and battery capacity.
1.2. Security Requirements
1.3. Organization
2. Preliminaries
2.1. Attacker Model
- An adversary is able to eavesdrop, intercept, modify, delete, or insert messages exchanged through an open channel.
- An adversary is able to perform various types of attacks, including replay, masquerade, man-in-the-middle (MITM) and mobile device theft attacks.
2.2. Fuzzy Extractors
- 1.
- : After a user imprints the biometric input , the probabilistic function selects a consistent random string and a random auxiliary string .
- 2.
- : After a new user imprints the biometric input and the string value in a session, successfully recovers the value .
3. Review of Madhusudhan et al.’s Protocol
3.1. Initialization Process
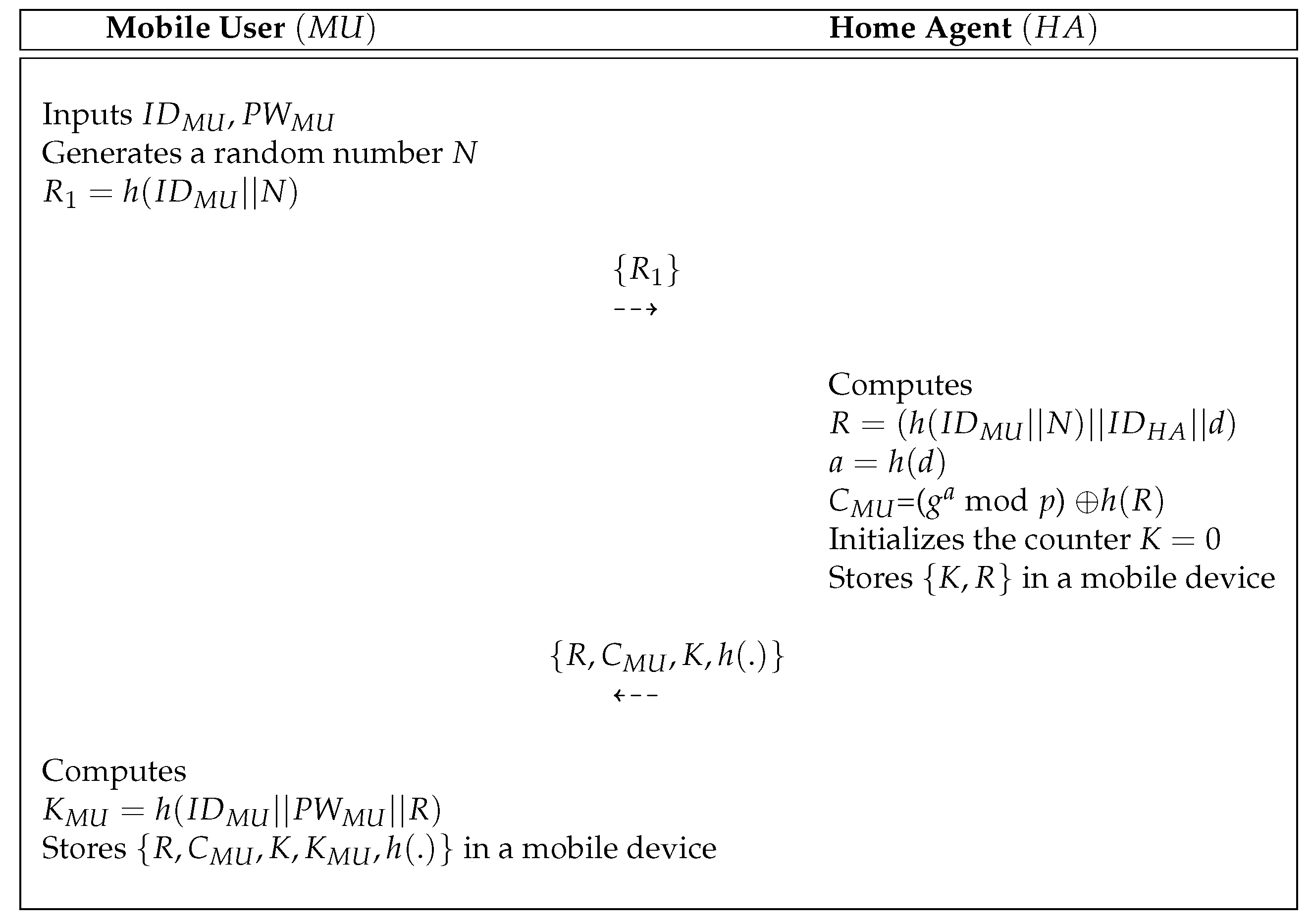
3.2. Registration Process
- Step 1:
- A mobile user inputs and selects a random number N. Then, computes and sends a request message to the via a public channel.
- Step 2:
- After obtaining messages , the calculates , and = ( mod p) . After that, sets the value of the counter and stores in a secure database. Then, sends to over a secure channel.
- Step 3:
- After obtaining messages , the computes and stores it in a mobile device. Finally, the mobile device of the contains .
3.3. Login and Authentication Process
- Step 1:
- The retrieves the authentication data stored in the mobile device and enters and . After that, the mobile device computes and checks whether . If this condition holds, the generates a random number and computes , and . Then, sends the login request message to through an insecure channel.
- Step 2:
- After obtaining the , selects a random number and encrypts and using the shared secret key. The sends the to the .
- Step 3:
- Upon reception of , the checks the identity of and retrieves the secret key corresponding to . After that, the decrypts and computes , mod p, (( mod p)) and . The then checks whether there exists in a secure database. If the condition is valid, the computes =(( mod p)) and checks whether . If it is correct, the computes = mod and sends to the .
- Step 4:
- After obtaining the , the decrypts and computes . Finally, the sends to the .
- Step 5:
- Upon reception of , the computes and . After that, the checks whether . If this holds, the and achieve the successfully.
3.4. Password Update Process
- Step 1:
- When a legitimate wants to update the password, the inputs and the request messages are transmitted via a terminal.
- Step 2:
- The mobile device of calculates and checks whether . If this holds, the is legitimate user. Otherwise, the mobile device terminates the password change process.
- Step 3:
- The selects new password and computes . Finally, the mobile device of replaces with .
4. Cryptanalysis of Madhusudhan et al.’s Protocol
4.1. Masquerade Attack
- Step 1:
- A calculates , and . Then, generates a random number . After that, computes , and and sends to the .
- Step 2:
- After obtaining the , the selects a random number and encrypts using a shared secret key. Then, the sends to the .
- Step 3:
- Upon reception of , the decrypts and computes , mod p, (( mod ) and . Then, the checks whether . After that, computes =( mod p)) and checks whether . Finally, computes mod p) and sends to the .
- Step 4:
- After obtaining the , the decrypts and computes , then sends to the .
- Step 5:
- Upon reception of , the computes the , and checks whether . If it is correct, computes the
4.2. Replay Attack
4.3. Session Key Disclosure Attack
4.4. Mutual Authentication
5. Proposed Secure and Efficient Authentication Protocol for GLOMONET
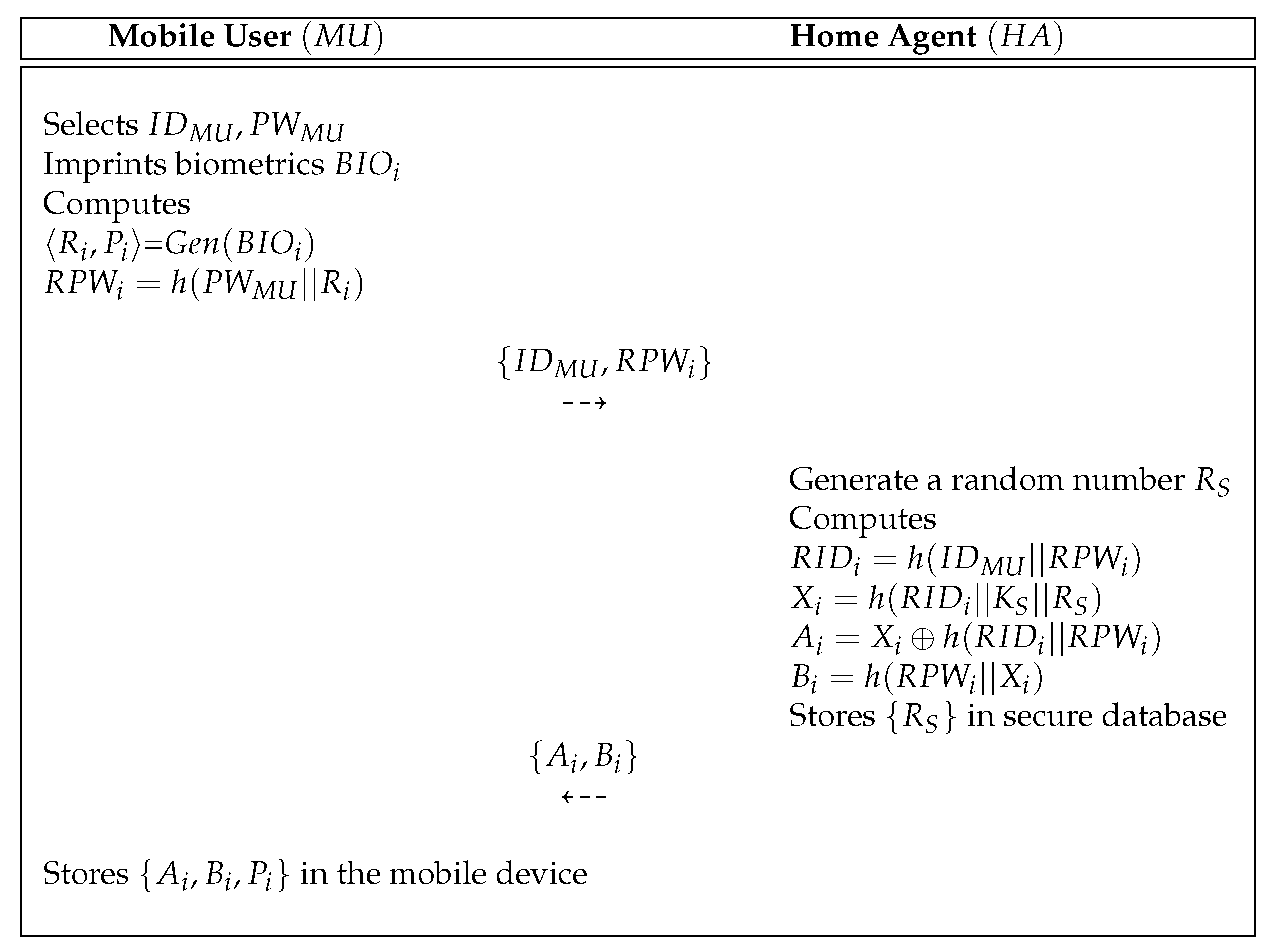
5.1. Registration Process
- Step 1:
- A selects , and imprints biometric . After that, computes =, and sends to the over a secure communication.
- Step 2:
- After obtaining messages , the computes , , and . After that, stores in a secure database. Finally, the sends to the via a secure communication.
- Step 3:
- Upon reception of , the stores in the mobile device.
5.2. Login and Authentication Process
- Step 1:
- The mobile device inputs , and imprints biometrics . The computes , , , , and and checks whether . If this holds, the generates a random nonce and computes , and . After that, sends to the over an open channel.
- Step 2:
- Upon reception of , the selects a random nonce and computes , . After that, the sends to the .
- Step 3:
- Upon reception of , the computes , and checks the identity of the mobile user. Then, computes , and checks whether . If it is valid, the calculates , and checks whether . Then, the computes , and . Finally, the sends an authentication message to the .
- Step 4:
- Upon reception of , the computes , and checks whether . If it is correct, the computes =, and sends to the .
- Step 5:
- Upon reception of , the calculates , , and . Finally, the checks whether . If it holds, the and establish the successfully.
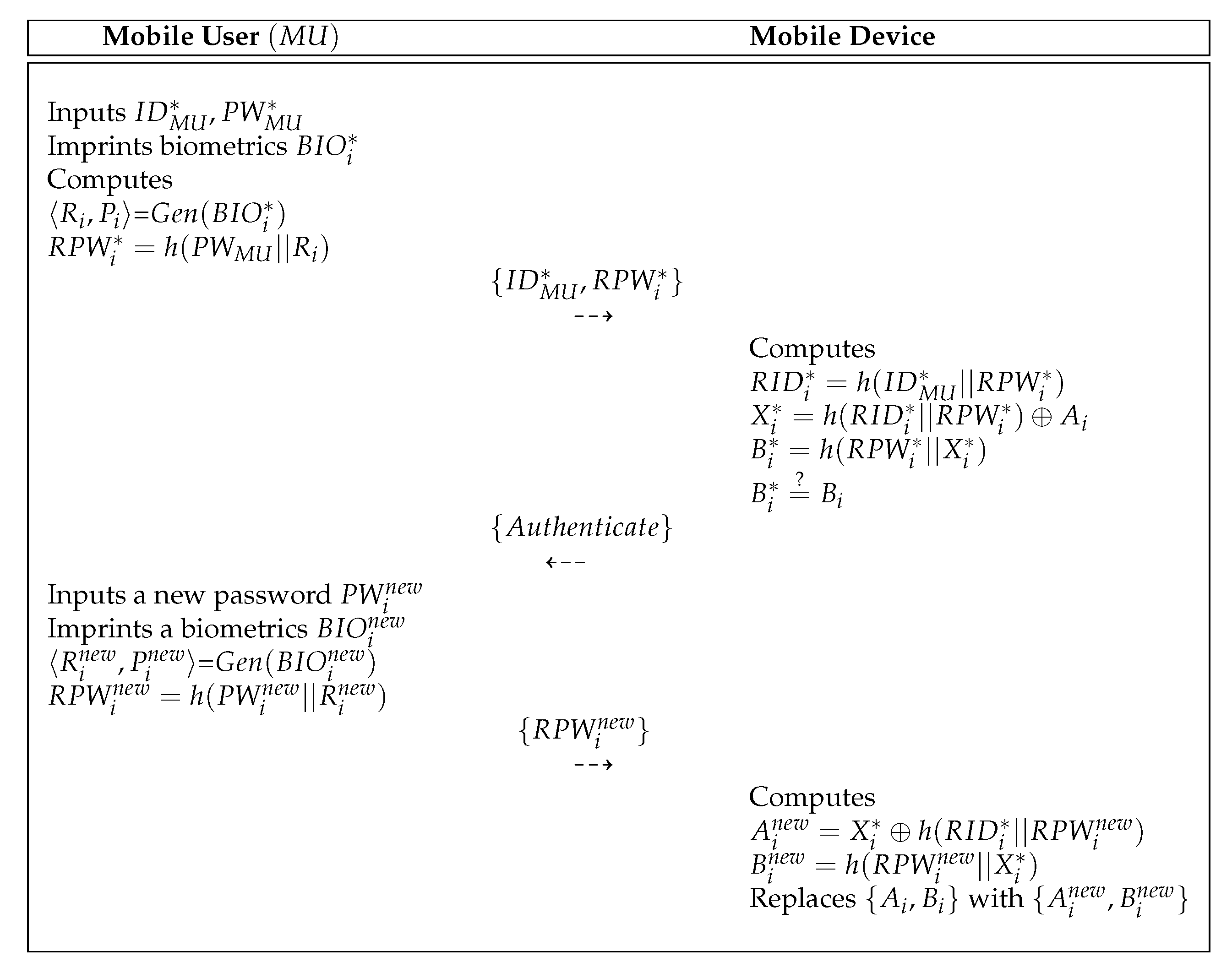
5.3. Password Update Process
- Step 1:
- The inputs , and imprints biometrics . After that, computes =, and sends to the mobile device.
- Step 2:
- Upon reception of , the mobile device computes , , , and the mobile device checks whether . If it is correct, the mobile device sends the authentication response message to the .
- Step 3:
- Upon reception of the authentication response message, the inputs a new password and imprints a new biometrics . computes =, and sends to the mobile device.
- Step 4:
- Upon reception of , the mobile device computes , and replaces with .
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Masquerade Attack
6.1.2. Replay Attack
6.1.3. Stolen Mobile Device Attack
6.1.4. Session Key Disclosure Attack
6.1.5. Anonymity
6.1.6. Mutual Authentication
6.1.7. User Friendliness
6.2. Security Properties
6.3. Authentication Proof Using BAN Logic
6.3.1. Rules of BAN Logic
- 1.
- Message meaning rule:
- 2.
- Nonce verification rule:
- 3.
- Jurisdiction rule:
- 4.
- Freshness rule:
- 5.
- Belief rule:.
6.3.2. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- .
6.3.3. Idealized Forms
- :
- :
- :
- :
- :
- :
- :
- : .
6.3.4. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- .
6.3.5. Proof Using BAN Logic
- Step 1:
- According to , we obtain the following
- Step 2:
- Utilizing and with the “message meaning rule”, the following is obtained
- Step 3:
- Now, using and with the “freshness rule”, the following is obtained
- Step 4:
- Utilizing and with the “nonce verification rule”, we obtain
- Step 5:
- Utilizing and the “belief rule”, we obtain
- Step 6:
- According to , we obtain
- Step 7:
- Utilizing the and with the “message meaning rule”, the following is obtained
- Step 8:
- Now, using and with the “freshness rule”, we obtain
- Step 9:
- Utilizing and with the “nonce verification rule”, the following is obtained
- Step 10:
- According to , we obtain
- Step 11:
- Utilizing and with the “message meaning rule”, the following is obtained
- Step 12:
- Now, using and with the “freshness rule”, we obtain
- Step 13:
- Utilizing and with the “nonce verification rule”, the following is obtained
- Step 14:
- According to , we could obtain
- Step 15:
- Utilizing and with the “message meaning rule”, we obtain
- Step 16:
- Now, using and with the “freshness rule”, the following is obtained
- Step 17:
- Utilizing and with the “nonce verification”, we obtain
- Step 18:
- Utilizing and the belief rule, we obtain
- Step 19:
- Now, using and with the “jurisdiction rule”, the following is obtained
- Step 20:
- Because of , from the , , and we obtain
- Step 21:
- Utilizing and with the “jurisdiction rule”, we obtain
6.4. ROR Model Analysis
- : It denotes that performs the eavesdropping attack by eavesdropping exchanged messages between , , and over wireless communication.
- : It is modeled from the mobile device lost/stolen attack, in which the is able to extract the secret data in the mobile device.
- : In this query, the can dispatch a message M to the instance and can also reply accordingly.
- : It corresponds to the semantic security of the between and following the indistinguishability style in the ROR model [26]. In this query, before the experiment starts, an unbiased coin c is tossed. If the executes query and the established is fresh, then returns for the case when or a random value when . On the other cases, it returns a null value (⊥).
- : With this query, the can reveal the created by its partner to in the current session.
Security Proof
- Game: This game is considered as an actual attack by the for the proposed protocol P. Since the bit c is guessed at the beginning of . According to this game, we obtain the following:
- Game: This game is modeled so that the performs an eavesdropping attack in which the exchanged messages , , , and are intercepted during the authentication phase using the query. Then, performs the query to check whether it is the real SK or a random number. In the proposed protocol, the is calculated as . To derive , the needs secret credentials, such as , , and . Consequently, the ’s probability in winning by eavesdropping on the exchanged messages does not increase. We can obtain
- Game: The difference between and is that the and queries are included in . This game can be considered as an active attack in which the may try to fool a legitimate entity to accept the exchanged messages modified by the . All exchanged messages are protected by using the collision-resistant one-way hash function . All exchanged messages are constructed using the random credentials , , and . All exchanged messages are constructed using the random credentials , , and and these messages are protected by using the collision-resistant one-way hash function . Using birthday paradox, we can obtain the following result:
- Game: In the final game, the query is modeled. In this case, a can extract the secret parameters from a mobile device’s memory utilizing the power-analysis attack. Here, , and . It is computationally infeasible for to derive the real identity and password of correctly via the query without ’s master key and secret parameter . The probability of guessing the biometric key of bits by the is approximately . Consequently, the and are indistinguishable if password/biometrics guessing attacks are not implemented. Therefore, utilizing Zipf’s law [27], we can obtain the following result:
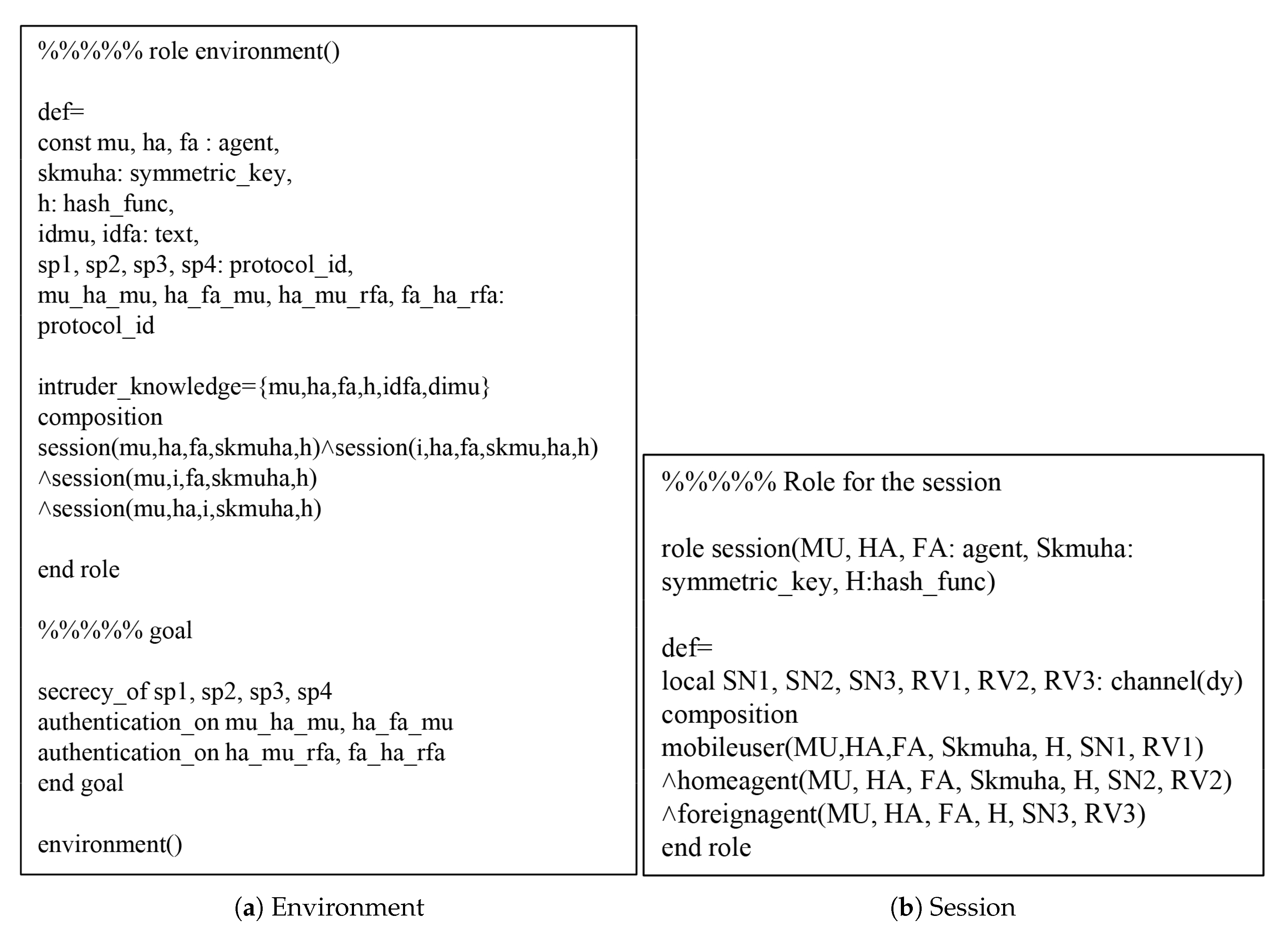
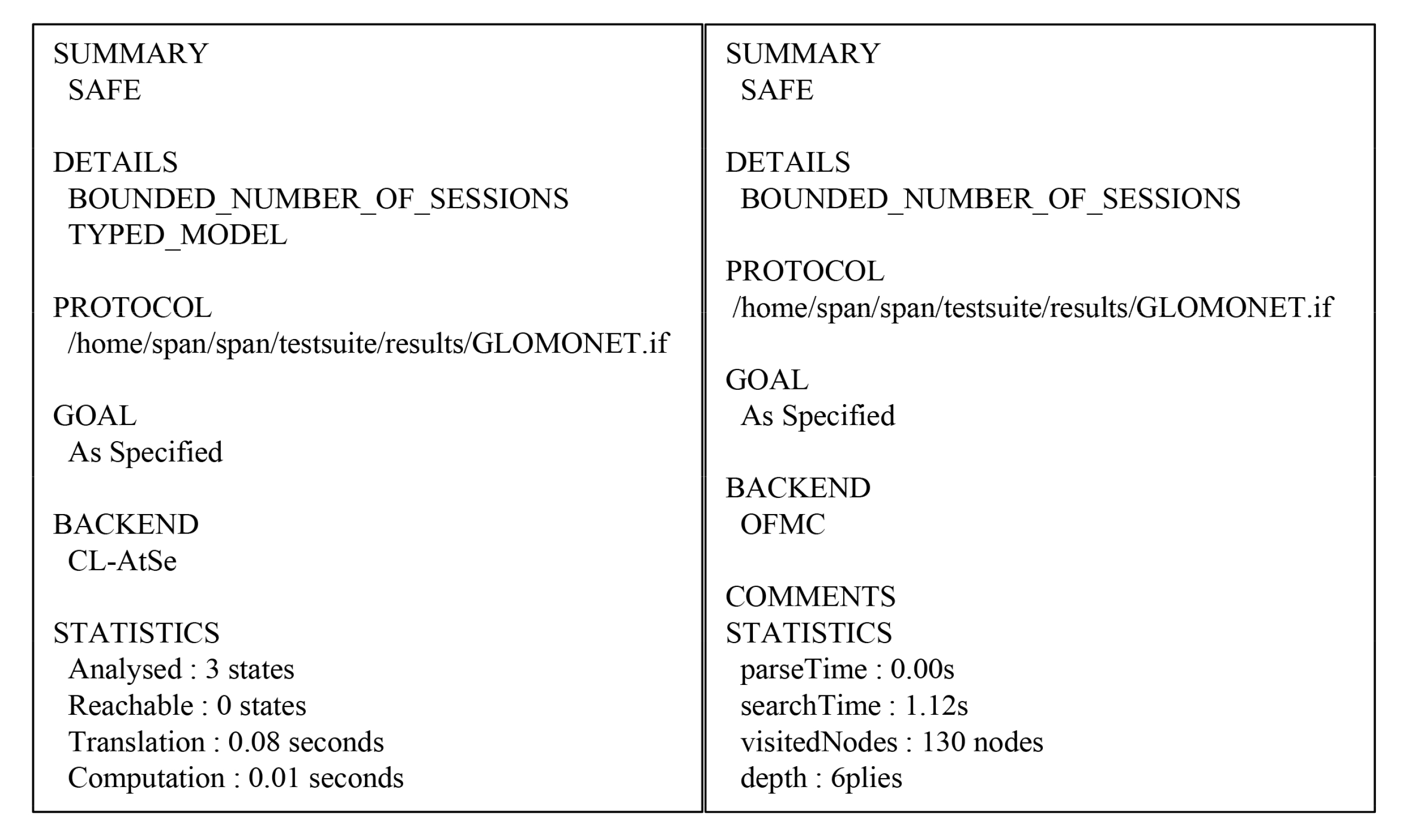
7. AVISPA Simulation
7.1. HLPSL Specification
7.2. Result Analysis of AVISPA Simulation
8. Performance Analysis
8.1. Computation Cost
- The time complexity of a one-way hash function operation s.
- The time complexity of a modular multiplication operation s.
- The time complexity of a modular exponentiation operation s.
- The time complexity of a elliptic curve point multiplication operation s.
- The time complexity of a symmetric encryption/decryption operation s.
- The time complexity of a asymmetric encryption/decryption operation s.
8.2. Communication Cost
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gope, P.; Hwang, T. An efficient mutual authentication and key agreement scheme preserving strong anonymity of the mobile user in global mobility networks. J. Netw. Comput. Appl. 2016, 62, 1–8. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Choo, K.K.R. A robust biometrics based three-factor authentication scheme for global mobility networks in smart city. Future Gener. Comput. Syst. 2018, 83, 607–618. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, G.; Li, L.; Yang, Y. Robust privacy-preserving mutual authenticated key agreement scheme in roaming service for global mobility networks. IEEE Syst. J. 2019, 13, 1454–1465. [Google Scholar] [CrossRef]
- Lee, T.F. User authentication scheme with anonymity, unlinkability and untrackability for global mobility networks. Secur. Commun. Netw. 2013, 6, 1404–1413. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M.; Chen, C.T.; Chen, S.D. Advanced secure anonymous authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2017, 94, 1281–1296. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zhang, Y.; Chen, C.; Bu, J. A strong user authentication scheme with smart cards for wireless communications. Comput. Commun. 2011, 34, 367–374. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Li, G.; Yang, L. An enhanced authentication scheme with privacy preservation for roaming service in global mobility networks. Wirel. Pers. Commun. 2013, 68, 1477–1491. [Google Scholar] [CrossRef]
- Kuo, W.C.; Wei, H.J.; Cheng, J.C. An efficient and secure anonymous mobility network authentication scheme. J. Inf. Secur. Appl. 2014, 19, 18–24. [Google Scholar] [CrossRef]
- Park, K.S.; Park, Y.H.; Park, Y.H.; Reddy, A.G.; Das, A.K. Provably secure and efficient authentication protocol for roaming service in global mobility networks. IEEE Access 2017, 5, 25110–25125. [Google Scholar] [CrossRef]
- Zhu, J.; Ma, J. A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 2004, 50, 231–235. [Google Scholar]
- Lee, C.C.; Hwang, M.S.; Liao, I.E. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Transs. Ind. Electron. 2006, 53, 1683–1687. [Google Scholar] [CrossRef]
- Wu, C.C.; Lee, W.B.; Tsaur, W.J. A secure authentication scheme with anonymity for wireless communications. IEEE Commun. Lett. 2008, 12, 722–723. [Google Scholar]
- Li, C.T.; Lee, C.C. A novel user authentication and privacy preserving scheme with smart cards for wireless communications. Math. Comput. Model. 2012, 55, 35–44. [Google Scholar] [CrossRef]
- Das, A.K. A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Netw. Sci. 2013, 2, 12–27. [Google Scholar] [CrossRef]
- Karuppiah, M.; Saravanan, R. A Secure Authentication Scheme with User Anonymity for Roaming Service in Global Mobility Networks. Wirel. Pers. Commun. 2015, 84, 2055–2078. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Shashidhara. A secure and lightweight authentication scheme for roaming service in global mobile networks. J. Inf. Secur. Appl. 2018, 38, 96–110. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Karati, A.; Biswas, G.P.; Khan, M.K. A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 2017, 41, 50. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology–CRYPTO; Lecture Notes in Computer Science; Springer: Santa Barbara, CA, USA, 1999; pp. 388–397. [Google Scholar]
- Yu, S.J.; Lee, J.Y.; Lee, K.K.; Park, K.S.; Park, Y.H. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Interlaken, Switzerland, 2004; pp. 523–540. [Google Scholar]
- Odelu, V.; Das, A.K.; Goswami, A. An efficient biometric-based privacy-preserving three-party authentication with key agreement protocol using smart cards. Secur. Commun. Netw. 2015, 8, 4136–4156. [Google Scholar] [CrossRef]
- Park, Y.H.; Park, Y.H. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password based authenticated key exchange in the three-party setting. In Public Key Cryptography; Springer: Les Diablerets, Switzerland, 2005; pp. 65–84. [Google Scholar]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Yu, S.J.; Park, K.S.; Lee, J.Y.; Park, Y.H.; Park, Y.H.; Lee, S.W.; Chung, B.H. Privacy-preserving lightweight authentication protocol for demand response management in smart grid environment. Appl. Sci. 2020, 10, 1758. [Google Scholar] [CrossRef]
- Park, K.S.; Park, Y.H.; Park, Y.H.; Das, A.K. 2PAKEP: Provably Secure and Efficient Two-Party Authenticated Key Exchange Protocol for Mobile Environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 8 February 2020).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 8 February 2020).
- Kumar, V.; Jangirala, S.; Ahmad, M. An efficient mutual authentication framework for healthcare system in cloud computing. J. Med. Syst. 2018, 42, 142. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Lee, H.J.; Lee, D.H.; Moon, J.H.; Jung, J.W.; Kang, D.W.; Kim, H.S.; Won, D.H. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13, e0193366. [Google Scholar] [CrossRef]
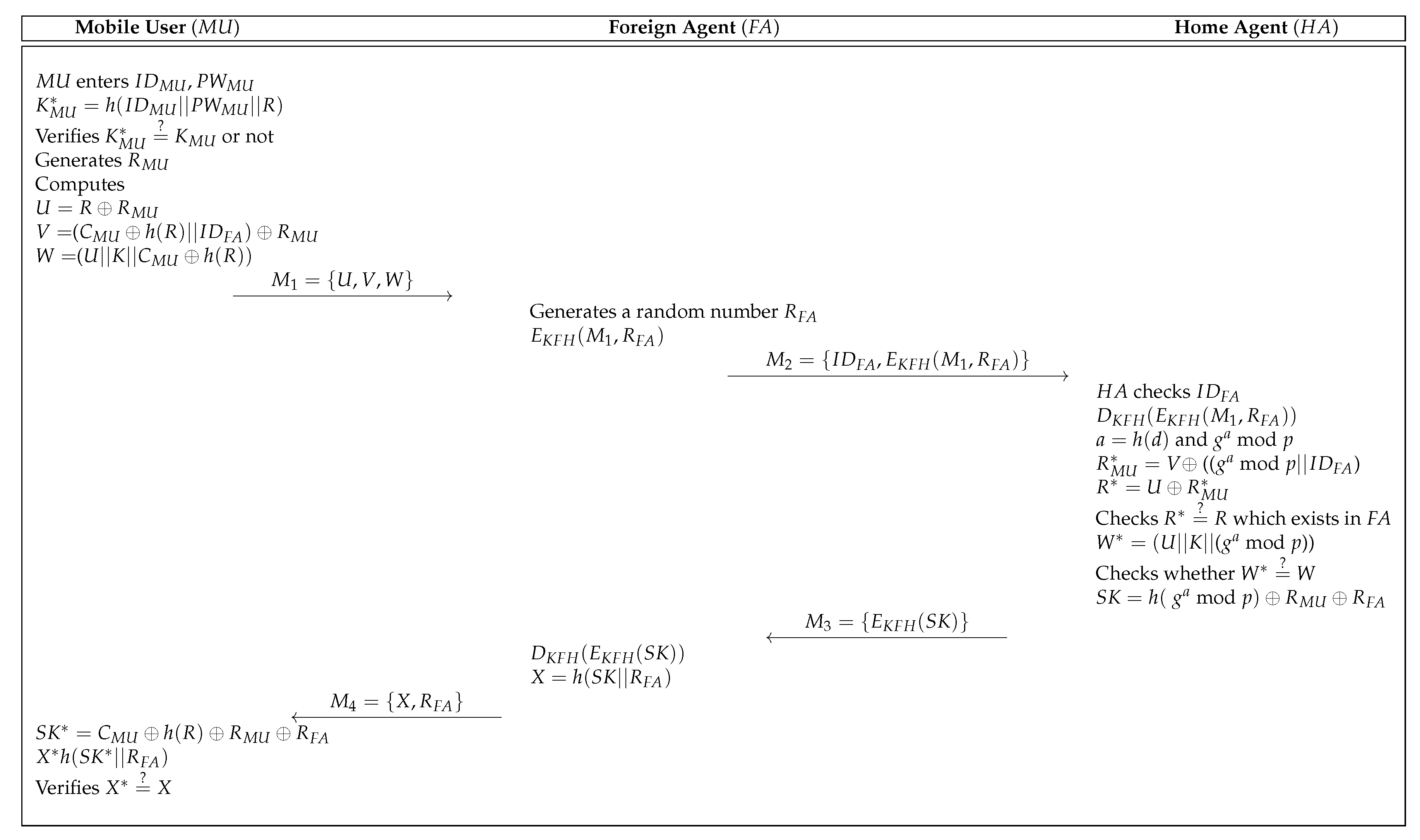



| Properties | Description |
|---|---|
| Three-factor security | This should remain secure even if any two of the three factors are compromised. |
| Resisting known attacks | This requires that the authentication protocol for GLOMONET is secure from various known attacks, including privileged insider, replay, session key disclosure, MITM, and masquerade attacks. |
| Resisting stolen mobile device attack | If an unauthorized person obtains the lost/stolen mobile device, it is impossible for him to impersonate a valid user with a counterfeit login request by using the information extracted from the mobile device. |
| Forward and backward secrecy | This requires that the attacker is not able to obtain the previous session keys or future ones by using the compromised session key. |
| Secure mutual authentication and key agreement | This is an essential requirement in the GLOMONET scenario, and requires the communication parties to be able to authenticate each other and generate a shared session key to provide confidentiality of messages in public channels. |
| User friendliness | The mobile user should freely select his/her own identity and password. In addition, the mobile user should be allowed to update the password without the assistance of the home agent. |
| Anonymity and untraceability | A malicious attacker is incapable of revealing and tracking the real identity of the legitimate user, and this is an important privacy-preserving requirement for users. |
| Notation | Description |
|---|---|
| ’s identity | |
| ’s identity | |
| ’s identity | |
| ’s random number | |
| Random nonce of , , and | |
| ’s password | |
| ’s biometrics | |
| ’s master key | |
| Session key between and | |
| Shared secret key between and | |
| Symmetric encryption/decryption | |
| T | Timestamp |
| Hash function | |
| ⊕ | Bitwise XOR operation |
| Concatenation operation |
| Security Features | He et al. [6] | Kuo et al. [8] | Karuppiah et al. [15] | Madhusudhan et al. [16] | Ours |
|---|---|---|---|---|---|
| User anonymity | × | × | ∘ | ∘ | ∘ |
| User friendliness | ∘ | ∘ | ∘ | ∘ | ∘ |
| Mutual authentication | × | ∘ | ∘ | × | ∘ |
| Insider attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| Replay attack | ∘ | × | ∘ | × | ∘ |
| Perfect forward secrecy attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| Session key disclosure attack | × | × | ∘ | × | ∘ |
| Masquerade attack | × | ∘ | ∘ | × | ∘ |
| Notation | Description |
|---|---|
| Abelieves that B | |
| B is updated and fresh | |
| Asees that B | |
| A once said B | |
| Acontrols that B | |
| B is combined with W | |
| B is encrypted utilizing symmetric key K | |
| A and P can make secure contact utilizing K as the shared secret key | |
| Session key used in communication session |
| Schemes | Registration | Login and Authentication | Total | Total Cost (s) |
|---|---|---|---|---|
| He et al. [6] | 2.5272 | |||
| Kuo et al. [8] | 0.3113 | |||
| Karuppiah et al. [15] | 1.60785 | |||
| Madhusudhan et al. [16] | 1.6058 | |||
| Ours | 0.0135 |
| Schemes | Registration Process | Login and Authentication Process | Total Cost |
|---|---|---|---|
| He et al. [6] | 704 bits | 4992 bits | 5696 bits |
| Kuo et al. [8] | 640 bits | 3872 bits | 4512 bits |
| Karuppiah et al. [15] | 640 bits | 4224 bits | 4864 bits |
| Madhusudhan et al. [16] | 1184 bits | 1344 bits | 2528 bits |
| Ours | 608 bits | 2528 bits | 3136 bits |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks. Appl. Sci. 2020, 10, 3565. https://doi.org/10.3390/app10103565
Yu S, Lee J, Park Y, Park Y, Lee S, Chung B. A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks. Applied Sciences. 2020; 10(10):3565. https://doi.org/10.3390/app10103565
Chicago/Turabian StyleYu, SungJin, JoonYoung Lee, YoHan Park, YoungHo Park, SangWoo Lee, and BoHeung Chung. 2020. "A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks" Applied Sciences 10, no. 10: 3565. https://doi.org/10.3390/app10103565
APA StyleYu, S., Lee, J., Park, Y., Park, Y., Lee, S., & Chung, B. (2020). A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks. Applied Sciences, 10(10), 3565. https://doi.org/10.3390/app10103565






