International New Venture Legitimation: An Exploratory Study
Abstract
:1. Introduction
2. Theoretical Background
2.1. Positioning and Contextualizing the Research
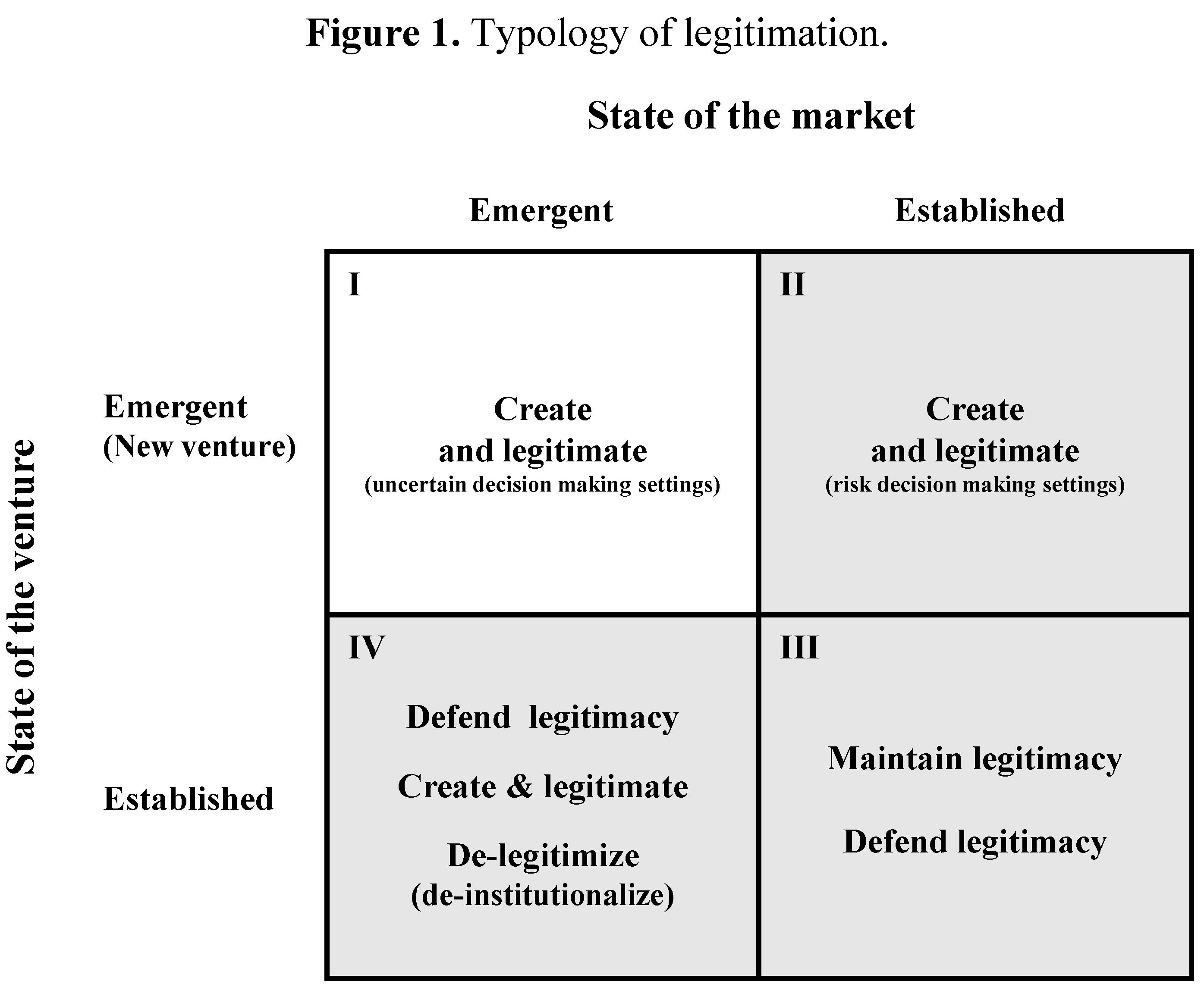
2.2. International New Venture Legitimation
2.3. New Venture Legitimation
3. Research Methodology
Data Collection and Analysis
| Case Company | Business Description | Founded (Year) | Mode of Founding | Emergence of New Business Idea | Gone International | Growth Path | Number of Employees (at its Peak) | Performance |
|---|---|---|---|---|---|---|---|---|
| Finance-Software | B2B platforms for financial service industry | 1996 | Management buy-out | 1998 | 1998 | Organic growth | 60 | Product at least 12 months to soon to the market Ceased trading in 2004 |
| Project-Software | Tools to estimate project costs | 1992 | Start-up | 1995 | 1997 | VC backed | 12 | Liquidated in 2001; bought IP from liquidator Resurrected as Phoenix in 2001 |
| Tool-Software | Tools to estimate and test smart cards | 1985 | Start-up | 1993 | 1995 | Organic growth | 130 | Smart-card technology adopted globally in 1995 Moved to profitability in 1995 |
| Mobile-Software | Platform to integrate mobile workforce data to HQ | 2000 | Start-up | 2000 | 2000 | VC backed | 105 | Were behind revenues and platform development in 2001 Ceased trading in 2002 |
| Data-Software | Data warehouse to convert data into information | 1998 | Spin-out | 1998 | 1999 | VC backed | 40 | The strategic partner announced similar market development plans in 2000 Ceased trading in 2001 |
| Phase 1 1 2000 | Phase 2 2001–2003 | Phase 3 2004 | Phase 4 2005 |
|---|---|---|---|
|
|
|
|
| Technology Legitimation Strategy | Market Legitimation Strategy | Operating Legitimation Strategy | Locational Legitimation Strategy | Alliance Legitimation Strategy | Anchoring Legitimation Strategy | |
|---|---|---|---|---|---|---|
| Aim | To validate the innovation/know-how | To better understand the target market | To have an optimal organizational gestalt | To overcome the disadvantage of foreignness | To mitigate the risk of newness and smallness | To intentionally misrepresent the facts |
| Target | Large enterprise players | Board of directors Potential customers | Potential investors (chiefly) | Potential customers Potential investors | Large enterprise players | Potential investors |
| Means | ‘Built-in’ capability Certification Recruiting key personnel | Non-executive directors Strategic advisors Large consulting firms VCs Referrals (weak ties) | Establish an office Hire employees Develop internal policy and operating procedures Develop incentive mechanisms Attract customers Generate first sale Get business education Procedural justice | Locate venture’s office abroad | International cooperative agreements Partnerships Joint-ventures | Asymmetry of information Hype business plans Accentuate positive and downplay negative Stretching the rules |
| (Perceived) benefits | Recognition Credibility Capability | Market-related capabilities | Efficient Professional | Local venture Potential for very high gains Possibility of early exit strategies Look big | Increased visibility, reputation, image, and prestige Likelihood to attract various types of investors Look big | Increased likelihood to attract venture funding |
| Challenges | To find early adopters willing to try new technology | Loss of control Goal misalignment | To set and commit to long-term outcome goals To develop performance benchmarks Risk of goal misalignment | Services do not travel, hence the need to develop a product-based business Internationalization dimension imposed by investors | Loss of control over own fate (as large enterprise players, alliance partners demand exclusive partnerships, hence captive partnership) | Ethical considerations Diminishing funding |
4. Findings
4.1. Technology Legitimation Strategy
“… technical credibility really; we have one key developer; my co-owner and I are involved in the product architecture development.”—CEO of Project-Software.
“We span-out; prior to that we built advanced systems for a number of multinational companies, and in the meantime developed an IP. I left that company with a small team and IP and set up Data-Software. It was a service-based business. My ambition was to create a product-based business from that.”—CEO of Data-Software
“When we adopted new technology, we did have to bluff quite a lot. We recruited people from banks and insurance companies; so, we gradually brought in the industry knowledge that we ourselves did not have. But when our potential customers decided to use this new technology, the fact that we did not come from financial service was less important to them; important to them was that we knew this technology.”—CEO of Finance-Software
“We did a project for a large computer and mobile manufacturer, and we were left with the software, and decided to do something with it, for example develop it as a tool. We created a tool, the next step then was to see where it can be used, and started hunting out key players.”—CEO of Tool-Software
“We became an authorized [technology] center, which was actually quite nice, as it started to make us look a lot bigger than we were. Because it was an early adopted technology, you could not be a smaller organization, because people would expect early adopters to be big organizations. Up until then we’d just been a group of R&D engineers which did not differentiate us; but as soon as we became an authorized [technology] center, we had the classic USP.”—Marketing Director of Finance-Software
4.2. Market Legitimation Strategy
“We had experience in selling our consulting services, backed up by our technical credibility; selling a product was a completely different thing. We did not have any background in that; that is why we looked for a non-exec in that particular area; someone who actually sold products worldwide.”—CEO of Project-Software
“Getting advisors on board helps companies to get the money; but partly would be to fill in the expertise gaps; also they would be called in to demonstrate a kind of endorsement: the bigger the name of the adviser, the bigger the impression they would make on VCs, kind of window dressing if you like.”—Business Strategy Consultant
“The key to raising venture capital money is to make sure you bring people on board who actually help the company. I liked working with investors and when we opened the office in the US we got all the support we could get.”—CEO of Data-Software
“The key things that make people buy, particularly in B2B market, are if they can refer to somebody else who’s bought from you, and that reference would normally be within the same sector.”—CEO of Finance-Software
“We signed up [a large consulting company] to assist us in raising funds from three venture capitalists. We also have as a sales and marketing director the former vice-president of sales of a large enterprise player, and, as a chairman, the former general manager of another large enterprise player.”—CEO of Mobile-Software
“There are two ways to make a donkey to move, i.e., either to flutter an herb in front of it or hit it with a stick from the back… We found that stick and it worked.”—Marketing Director of Finance-Software
4.3. Operating Legitimation Strategy
“Technology businesses might be very good at generating sales, but a lot of them are not; a lot of them are operating on the expectations for the future; and what they do is they create a structure that in my view is too ambitious; it is ahead of itself in terms of the maturity of the business. In some ways entrepreneurs are a lot more amateur in their management style. They can be extremely naïve about how they have to deal with their new ventures.”
“We felt there was a need to establish more of a real company; we had to hire full time development staff, establish an office. The fact that we had to hire staff brought all these issues of how to motivate staff: we got the best out of them, treated them properly, and did all the things you have to do professionally to have staff; and taking on board the office and other additional overheads.”—CEO of Project-Software
“For our employees that was not a difficult transition; it was something that they grew up with to some extent from universities when this technology started to emerge… We had a profit scheme where we shared some of our profits with all the staff. What we started thinking about was how we could actually develop a market focused proposition... Changing in thinking was also promoted in some way by two of the key executives by getting an MBA.”—CEO of Finance-Software
“I often wondered whether we went to too many markets. Customer base was very important; product was quite important, because while we were building our own platform, we could still deploy their existing products; it meant that we had revenues; so acquiring customer base was good; acquiring the legacy product was good; and the knowledge of customer needs; the development skills were not good; and actually their sales, in terms of scale were not good.”—CEO of Mobile-Software
“We raised more money than we actually needed… I think if we had fewer resources, we would have made better decisions. The pressure was to invest it and the objective was not to do it as cheaply as possible; but to move as quickly as possible... As a relatively new company, when recruiting so many people so quickly and in so many different parts, you have to make sure that everybody understood the vision of what we were trying to accomplish. It was also quite difficult when your customers are in US, but your product development team was back in UK.”—CEO of Data-Software
“In the round one VCs are looking for pre-product; round two is the product, and some reference customers; round three is you’ve got revenue of millions of pounds. If you have pre-product, pre-customer and your management is weak, you won’t get a funding. VCs need an excellent management team when there is no product or customers.”
4.4. Locational Legitimation Strategy
“We opened an office in Silicon Valley so that we can make the company look like an American company to the American market. We also opened two other in different US locations; now we’re just two miles away from our strategic partner.”—CEO of Data-Software
“To enter the enterprise market we had to be perceived as a European, not UK player. And we designed the company that way from day one.”—CEO of Mobile-Software
“One of the keys to the enterprise market was that it was very much populated by very big players so we had to look big.”—Marketing director of Finance-Software
“Businesses that we typically backed are businesses which need to sell internationally. We will not typically back a business if it is not addressing the world market.”
4.5. Alliance Legitimation Strategy
“The funny thing is that nothing was actually signed with [our strategic partner]; it was almost a gentlemen’s agreement. Wanting to go ahead of the game, they were trying to adopt and launch additional SIM capability and they needed tools to test it on mobile phones.”—CEO of Tool-Software
“The goal really was to find out partners that could help us to break into the US. Because we had fairly new technology, we tried to get some help from some of the big enterprise players, like Microsoft, and Oracle. We talked to some of them, and decided to partner with [our strategic partner] with whom we had more tractions than we did with [the other]; we felt we could co-exist alongside [our strategic partner].”—CEO of Data-Software
“Ultimately to really get the product somewhere you have to sell it through a US company; we sell now to a large defense company; we have a good image, even perceived by our clients as a big company.”—CEO of Project-Software
“We wanted to go into enterprise space; we needed a bit of track record and credibility. We had to get into some relationships with a big player.”—Marketing director of Finance-Software
“We could’ve done more to develop relationships with [our strategic partner]; but if we succeeded, we would’ve been just swallowed up, or kicked in one side. So, we could not have grown the business to the extent that we wanted to independently. It was a tradeoff.”—CEO of Mobile-Software
4.6. Anchoring Legitimation Strategy
“When I look at the business plan at forecasts to get the initial funding, I can say straight away: this is ridiculous, absolutely ridiculous, there is no way the company could grow at that pace… The whole trust… if a young technology business is to create large expectations about sales and profits levels, it is kind of hyping and this is how entrepreneurs generate VC money.”—Liquidator
“The hype is important as it creates fashion; hype is driven by fashion. If you like, hype and fashion are the two sides of the same coin. So, if everyone is doing what is fashionable, then by definition, everybody is doing it. The hype releases the investment decisions because they reduce the pain of failure.”—Strategic advisor
“We always felt it was very important to build up our brand. So, we kind of played the press game. To get into papers, you have to give them something. And therefore, you tend to, I would say, make up things; you have to exaggerate things... It is like building people’s expectations.”– CEO of Finance-Software
“Our business plan was a bit ambitious, not to say the least, is the reality of it. We knew it was a bit ambitious as well, but you have to pitch in that fashion in order to secure any investment at all. VCs themselves encouraged this approach and this type of statements.”—CEO of Project-Software
“…the second round funding will support our rapid expansion in a sector currently valued at $10 billion; however, it is estimated that by 2003 the sector will be worth $150bn… Hype, for us, was about timing. At a time people were grossly exaggerating things.”—CEO of Data-Software
“We had to construct the business plan that would give the investors the rates of return to buy them into; so, we had to construct something that would say that we could do it for 15 million. And in the hindsight, that may not have been the best way of going about it.”—CEO of Mobile-Software
5. Discussion and Conclusions
“…the market was extremely bullish, and investors were willing to take very large risks; also, we had an inflated idea of what companies might be worth. The big thing that we’ve been working on quite hard to improve was to get the views on the size and trends of the markets. For example, in [the] case of Project-Software, we did not have that level of information and found out the market was actually much smaller than we thought.”
Conflicts of Interest
References
- Fan, T.; Phan, P. International new ventures: Revisiting the influences behind the ‘born-global’ firm. J. Int. Bus. Stud. 2007, 38, 1113–1131. [Google Scholar] [CrossRef]
- Zahra, S. The theory of international new ventures: A decade of research. J. Int. Bus. Stud. 2005, 36, 20–29. [Google Scholar] [CrossRef]
- Stinchcombe, A. Social Structure and Organizations. In Handbook of Organizations; March, J., Ed.; Rand McNally: Chicago, IL, USA, 1965; pp. 142–193. [Google Scholar]
- Aldrich, H.; Fiol, C. Fools rush in? The institutional context of industry creation. Acad. Manag. Rev. 1994, 19, 645–670. [Google Scholar]
- Zaheer, S. Overcoming the liability of foreignness. Acad. Manag. J. 1995, 38, 341–363. [Google Scholar] [CrossRef]
- Zimmerman, M.; Zeitz, G. Beyond survival: Achieving new venture growth by building legitimacy. Acad. Manag. Rev. 2002, 27, 414–431. [Google Scholar]
- Drori, I.; Honig, B.; Sheaffer, Z. The life cycle of an internet firm: Scripts, legitimacy, and identity. Ent. Theory Pract. 2009, 33, 715–738. [Google Scholar] [CrossRef]
- Suchman, M. Managing legitimacy: Strategic and institutional approaches. Acad. Manag. Rev. 1995, 20, 571–610. [Google Scholar]
- Delmar, F.; Shane, S. Legitimating first: Organizing activities and the survival of new ventures. J. Bus. Ventur. 2004, 19, 385–410. [Google Scholar] [CrossRef]
- Rialp, A.; Rialp, J.; Knight, G. The phenomenon of early internationalizing firms: What do we know after a decade (1993–2003) of scientific inquiry? Int. Bus. Rev. 2005, 14, 147–166. [Google Scholar] [CrossRef]
- Coombs, J.; Sadrieh, F.; Annavarjula, M. Two decades of international entrepreneurship research: What have we learned—where do we go from here? Int. J. Ent. 2009, 13, 23–64. [Google Scholar]
- Keupp, M.; Gassmann, O. The past and the future of international entrepreneurship: A review and suggestions for developing the field. J. Manag. 2009, 35, 600–633. [Google Scholar] [CrossRef]
- Jones, M.; Coviello, N.; Tang, Y. International entrepreneurship research (1989–2009): A domain ontology and thematic analysis. J. Bus. Ventur. 2011, 26, 632–659. [Google Scholar] [CrossRef]
- Kraus, S. State-of-the-art current research in international entrepreneurship: A citation analysis. Afr. J. Bus. Manag. 2011, 5, 1020–1038. [Google Scholar]
- Dyer, G.; Wilkins, A. Better stories, not better constructs, to generate better theory: A rejoinder to Eisenhardt. Acad. Manag. Rev. 1991, 16, 613–619. [Google Scholar]
- Flanagan, J. The critical incident technique. Psychol. Bull. 1954, 51, 327–358. [Google Scholar] [CrossRef]
- Chell, E. Critical Incident Technique. In Qualitative Methods and Analysis in Organizational Research: A Practical Guide; Symon, G., Cassell, C., Eds.; Sage: London, UK, 1998; pp. 51–72. [Google Scholar]
- Butterfield, L.; Borgen, W.; Amundson, N.; Maglio, A.-S. Fifty years of the critical incident technique: 1954–2004 and beyond. Qual. Res. 2005, 5, 475–497. [Google Scholar] [CrossRef]
- Edvardsson, B. Service breakdowns: A study of critical incidents in an airline. Int. J. Ser. Ind. Manag. 1992, 3, 17–29. [Google Scholar]
- Glaser, B. Theoretical Sensitivity; Sociology Press: Mill Valley, CA, USA, 1978. [Google Scholar]
- Dubin, R. Theory Development; Free Press: New York, NY, USA, 1978. [Google Scholar]
- Johnson, C.; Dowd, T.; Ridgeway, C. Legitimacy as a social process. Annu. Rev. Sociol. 2006, 32, 53–78. [Google Scholar] [CrossRef]
- Alvarez, S.; Barney, J. How do entrepreneurs organize firms under conditions of uncertainty? J. Manag. 2005, 31, 776–793. [Google Scholar] [CrossRef]
- Coltman, T.; Devinney, T.; Latukefu, A.; Midgley, D. E-business: Revolution, evolution, or hype. Calif. Manag. Rev. 2001, 44, 57–86. [Google Scholar] [CrossRef]
- OECD (Organisation for Economic Co-operation and Development). The New Economy: Beyond the Hype; OECD Publishing: Paris, France, 2001. [Google Scholar]
- Turcan, R.V. Toward a theory of international new venture survivability. J. Int. Ent. 2011, 9, 213–232. [Google Scholar] [CrossRef]
- Dholakia, N.; Turcan, R.V. Bubbles: Towards a typology. Foresight 2013, 15, 79–88. [Google Scholar] [CrossRef]
- Bitektine, A. Legitimacy-based entry deterrence in inter-population competition. Corp. Reput. Rev. 2008, 11, 73–93. [Google Scholar] [CrossRef]
- Oliver, C. The antecedents of deinstitutionalization. Org. Stud. 1992, 13, 563–588. [Google Scholar] [CrossRef]
- Bassanini, A.; Scarpetta, S. Growth, technological change, and ICT diffusion: Recent evidence from OECD countries. Oxf. Rev. Econ. Policy 2002, 18, 324–344. [Google Scholar] [CrossRef]
- Pilat, D. Digital economy: Going for growth. OECD Obs. 2003, 237, 15–17. [Google Scholar]
- Booz-Allen & Hamilton. Competing in the Digital Age: How the Internet will Transform Global Business; EIU: New York, NY, USA, 1999. [Google Scholar]
- Turcan, R.V.; Fraser, N.M. The Emergence of an International New Software Venture from an Emerging Economy. In Lecture Notes in Business Information Processing: Software Business: Third International Conference; Cusumano, M., Iyer, B., Venkatraman, N., Eds.; Springer Publishing Company: Cambridge, MA, USA, 2012; pp. 114–127. [Google Scholar]
- Groen, A.; Wakkee, I.; Weerd-Nederhof, P. Managing tensions in a high-tech start-up: An innovation journey in social system perspective. Int. Small Bus. J. 2006, 26, 57–81. [Google Scholar]
- Turcan, R.V. External legitimation in international new ventures: Toward the typology of captivity. Int. J. Ent. Small Bus. 2012, 15, 262–283. [Google Scholar]
- Turcan, R.V.; Marinova, S.T.; Rana, M.B. Empirical studies on legitimation strategies: A case for international business research extension: Institutional theory in international business and management. Adv. Int. Manag. 2012, 25, 425–470. [Google Scholar] [CrossRef]
- Tornikoski, E.; Newbert, S. Exploring the determinants of organizational emergence: A legitimacy perspective. J. Bus. Ventur. 2007, 22, 311–335. [Google Scholar] [CrossRef]
- Zott, C.; Huy, Q. How entrepreneurs use symbolic management to acquire resources. Adm. Sci. Q. 2007, 52, 70–105. [Google Scholar] [CrossRef]
- Hargadon, B.; Douglas, Y. When innovations meet institutions: Edison and the design of the electric light. Adm. Sci. Q. 2001, 46, 476–501. [Google Scholar] [CrossRef]
- Wilson, N.C.; Stokes, D. Laments and serenades: Relationship marketing and legitimation strategies for the cultural entrepreneur. Qual. Market Res. 2004, 7, 218–227. [Google Scholar] [CrossRef]
- Lu, J.W.; Xu, D. Growth and survival of international joint ventures: An external-internal legitimacy perspective. J. Manag. 2006, 32, 426–448. [Google Scholar]
- Rao, R.S.; Chandy, R.; Prabhu, J. The fruits of legitimacy: Why some new ventures gain more from innovation than others. J. Mark. 2008, 72, 58–75. [Google Scholar] [CrossRef]
- Kim, H.E.; Pennings, J.M. Innovation and strategic renewal in mature markets: A study of the tennis racket industry. Org. Sci. 2009, 20, 368–383. [Google Scholar] [CrossRef]
- Davidsson, P.; Hunter, E.; Klofsten, M. Institutional forces: The invisible hand that shapes venture ideas? Int. Small Bus. J. 2006, 24, 115–131. [Google Scholar] [CrossRef]
- De Clercq, D.; Voronov, M. Toward a practice perspective of entrepreneurship: Entrepreneurial legitimacy as habitus. Int. Small Bus. J. 2009, 27, 395–419. [Google Scholar] [CrossRef]
- Lovallo, D.; Kahneman, D. Delusions of success: How optimism undermines executives’ decisions. Harv. Bus. Rev. 2003, 81, 56–73. [Google Scholar]
- Storey, D. Understanding the Small Business Sector; Routledge: London, UK, 1994. [Google Scholar]
- Miles, M.; Huberman, M. Qualitative Data Analysis: An Expanded Sourcebook; Sage: London, UK, 1994. [Google Scholar]
- Weick, K. Theory construction as disciplined imagination. Acad. Manag. Rev. 1989, 14, 516–531. [Google Scholar]
- Scott, W. Institutions and Organizations; Sage Publications: Thousand Oaks, CA, USA, 2001. [Google Scholar]
- Turcan, R.V. Entrepreneur-venture capitalist relationships: Mitigating post-investment dyadic tensions. Ventur. Cap: Int. J. Entr. Financ. 2008, 10, 281–304. [Google Scholar] [CrossRef]
- Slevin, D.; Covin, J. Time, growth, complexity, and transitions: Entrepreneurial challenges for the future. Entrep. Theory Pract. 1997, 22, 53–68. [Google Scholar]
- Cuervo-Cazurra, A.; Maloney, M.; Manrakhan, S. Causes of the difficulties in internationalization. J. Int. Bus. Stud. 2007, 38, 709–725. [Google Scholar] [CrossRef]
- Oviatt, B.; McDougall, P. Toward a theory of international new ventures. J. Int. Bus. Stud. 2004, 24, 45–64. [Google Scholar]
- Alvarez, S.; Barney, J. How entrepreneurial firms can benefit from alliances with large partners. Acad. Manag. Exec. 2001, 15, 139–148. [Google Scholar] [CrossRef]
- Barringer, B.; Harrison, J. Walking a tightrope: Creating value through interorganizational relationships. J. Manag. 2000, 26, 367–403. [Google Scholar] [CrossRef]
- Colombo, M.; Grilli, L.; Murtinu, S.; Piscitello, L.; Piva, E. Effects of international R&D alliances on performance of high-tech start-ups: A longitudinal analysis. Strateg. Entrep. J. 2009, 3, 346–368. [Google Scholar] [CrossRef]
- Lounsbury, M.; Glynn, M. Cultural entrepreneurship: Stories, legitimacy, and the acquisitions of resources. Strateg. Manag. J. 2001, 22, 545–564. [Google Scholar] [CrossRef]
- Johanson, J.; Vahlne, J.-E. The Uppsala internationalization process model revisited: From liability of foreignness to liability of outsidership. J. Int. Bus. Stud. 2009, 40, 1411–1431. [Google Scholar] [CrossRef]
- Rutherford, M.; Buller, P. Searching for the legitimacy threshold. J. Manag. Inquiry 2009, 16, 78–92. [Google Scholar] [CrossRef]
- Rutherford, M.; Buller, P.; Stebbins, J. Ethical considerations of the legitimacy lie. Entrep. Theory Pract. 2009, 33, 949–964. [Google Scholar] [CrossRef]
- Autio, E.; George, G.; Alexy, O. International entrepreneurship and capability development—qualitative evidence and future research directions. Entrep. Theory Pract. 2010, 35, 11–37. [Google Scholar] [CrossRef]
- Locke, E.; Latham, G. A Theory of Goal Setting and Task Performance; Prentice Hall: Englewood Cliffs, NJ, USA, 1990. [Google Scholar]
- Sapienza, H.; Korsgaard, M. The role of procedural justice in entrepreneur—venture capital relations. Acad. Manag. J. 1996, 39, 544–574. [Google Scholar] [CrossRef]
- Busenitz, L.; Fiet, J.; Moesel, D. Reconsidering the venture capitalists’ value added proposition: An interorganizational learning perspective. J. Bus. Ventur. 2004, 19, 787–807. [Google Scholar] [CrossRef]
- Kuemmerle, W. A test for the fainthearted. Harv. Bus. Rev. 2002, 80, 122–127. [Google Scholar]
- Merton, R. Social Theory and Social Structure; Free Press: New York, NY, USA, 1968. [Google Scholar]
- DiMaggio, P.; Powell, W. The iron cage revisited: Institutional isomorphism and collective rationality in organizational fields. Am. Sociol. Rev. 1983, 48, 47–160. [Google Scholar]
- Suddaby, R.; Greenwood, R. Rhetorical strategies of legitimacy. Adm. Sci. Q. 2005, 50, 35–67. [Google Scholar]
- Zhara, S. Contextualizing theory building in entrepreneurship research. J. Bus. Ventur. 2007, 22, 443–452. [Google Scholar] [CrossRef]
- Cesinger, B.; Fink, M.; Madsen, T.; Kraus, S. Rapidly internationalizing ventures: How definitions can bridge the gap across contexts. Manag. Decis. 2012, 50, 1816–1842. [Google Scholar] [CrossRef]
Appendix. Critical Event Charts of Case Companies
| Year | QI | QII | QIII | QIV |
|---|---|---|---|---|
| 1996 | Management buy-out of an R&D lab of multinational company | |||
| Internationalized instantly (USA, Brazil, Europe) | ||||
| 1998 | Realized they were operating without any focus; had incurred losses | Decided to focus on new, emerging technology | ||
| Identified the need to diversify and deliver tangible product | Trained staff in that new technology | |||
| Re-engineered the work for its parent company in this new technology | ||||
| 1999 | Decided to focus 100% on domestic financial services sector | Became authorized [new technology] development centre | ||
| Partnered with [MNE] to enter the financial service market | ||||
| 2000 | IT market in the US started to collapse | |||
| 2001 | Opened 3 offices throughout UK | IT market started worsening in the UK | Launched the 1st version of the product | |
| Announced as the fasted growing company of the year | ||||
| 2002 | Was still bullish about its growth | Forced to cut one sixth of staff | ||
| 2003 | Discovered that the product is 'at least 12 months to soon to the market' | Decided to 'cocoon' | ||
| Downsizing continued | Retained the IP and key personnel | |||
| Waits for the market to pick up |
| Year | QI | QII | QIII | QIV |
|---|---|---|---|---|
| 1992 | Started-up as a consulting company | |||
| 1994 | Identified new market opportunity to diversify and deliver tangible product | |||
| 1995 | Started R&D activities | |||
| 1997 | Launched 1st version of the product via a deal with OEM | |||
| 1998 | Deal with OEM failed | Pitched to VCs to raise funds to market the product in UK | Changed the business plan as per VCs request [to market to US] | |
| 1999 | Received 1st round of funding | Had to agree with VCs on entering the European market | Initiated international expansion into Europe and the US | |
| Hired a marketing non-exec from the OEM they had deal with | Established a relationship with a master distributor to enter European market | |||
| 2000 | Started exporting the product to the US and Europe | IT market in the US started to collapse | Received 2nd round of funding | Marketing non-exec stepped down |
| Continued exporting efforts and making trips to the US | Continued exporting efforts and making trips to the US | Continued exporting efforts and making trips to the US | ||
| Abandoned hopes for Europe as no sales were realized | VCs appointed their own non-exec specializing in crisis management | |||
| 2001 | Signed in the US a joint-venture deal with a UK MNE that had a large US customer base | IT market started worsening in the UK Presented to VCs the plan to 'cocoon' | Bank reconsidered its position and offered new terms and conditions | Resurrected: registered as new company |
| Developed a 'dramatic plan to improve things' to be presented to VCs | The plan to 'cocoon' was accepted by all but one investor, the bank of the company | Decided that 'the game was over' | Bought over the IP from the liquidator, re-employed senior software engineer | |
| Were introduced to a liquidator in case the 'dramatic' plan is not backed up by VCs | Approached the liquidator to surrender | Was liquidated | Re-branded the software, launched its 1st version | |
| Re-internationalised |
| Year | QI | QII | QIII | QIV |
|---|---|---|---|---|
| 1985 | Started-up as a service-based company | |||
| 1991 | Won a project to develop a smart-card test application | |||
| Decided to develop that application into a tool | ||||
| 1992 | Reached a "gentlemen's agreement" with a large telecom operator to develop a test tool for mobile phones smart-cards | |||
| 1993 | Released its first version of the tool | Launched 1st version of the product via a deal with OEM | ||
| Took its first version of the tool to Europe | ||||
| 1994 | Tried to raise venture capital, but with no success | |||
| 1995 | Smart-card technology started being adopted globally | Took its products to the US | Moved to profitability | |
| 1999 | Opened its first overseas office in the US | Won a strategic contract with one of the largest software player in the world | ||
| 2000 | Recession of the IT market | That large software player withdrew from the smart-card market, and from that strategic partnership | The opportunity that was identified was not realizing | Laid-off half of its staff, and restructured its overseas offices |
| Grew out of the tool market | Decided to focus back on 2G tools and services business to generate tactical revenue | |||
| Spotted new opportunity to develop a 3G smart-card platform for telecom and finance sectors | ||||
| Received its first round of funding to develop the platform | ||||
| 2001 | Received its second round of funding | Opened its second overseas office: Japan | ||
| 2002 | Received its third round of funding | |||
| 2003 | Had ~ 220 customers in 33 countries | Released the platform |
| Year | QI | QII | QIII | QIV |
|---|---|---|---|---|
| 2000 | Market opportunity identified | IT market in the US started to collapse | Started-up | Started the fund raising process |
| Internationalized instantly via acquisitions (Europe, UK, Midle East) | Hyped' the business plan to 'buy the investors into' | |||
| Turned for help to a leading market research firm and to one of the big four firms to comment on their market proposition | ||||
| 2001 | Opened offices in Europe, Middle East, and Far East | IT market started to worsen in the UK Secured first round of funding: got 1/3 less than 'hyped' | Were behind its planned revenues and with the development of the platform | |
| Held the board meeting with new investors to re-evaluate the business plan: no changes were made | Held next board meeting and decided to raise another £9 million | |||
| 2002 | One of the investors was taken over and withdrew from this portfolio | |||
| Another investor pulled out as well | ||||
| Could not find another investors | ||||
| Ceased trading |
| Year | QI | QII | QIII | QIV |
|---|---|---|---|---|
| 1998 | VC backed management buy-out of an IP and small R&D team from a large software company | Failed to secure a strategic partnership with one of the leading companies in the field | ||
| Used 1st round of funding to prove the technology and the market | ||||
| Started exploring different routes to the US market | ||||
| 1999 | Achieved brake through in product development | Secured a strategic partnership with one of the largest software companies | Opened its first overseas sales office in the US close to its strategic partner | |
| Failed to secure strategic partnership with another market leader in business intelligence | ||||
| 2000 | Received its 2nd round of funding to build sales infrastructures in the US | IT market in the US started to collapse | The strategic partner announced market development plans that overlapped with company's | Adhered to the strategy of fast, out-and-out growth |
| Opened its 2nd sales office in the US | Refuted several offers from trade buyers | Spooked by that event, started thinking and talking as to what to do | Opened another two sales offices in the US | |
| Re-branded the company to align it to the product | ||||
| 2001 | Decision was reached to focus on profitability rather than on out-and-out growth | IT market started to worsen in the UK | New CEO could not attract new funding | |
| It was also decided to withdraw from the US, focus on applications rather than products, and on direct selling | Ceased trading | |||
| Lead entrepreneur stepped down; VCs brought in new CEO to effect new strategy |
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Turcan, R.V. International New Venture Legitimation: An Exploratory Study. Adm. Sci. 2013, 3, 237-265. https://doi.org/10.3390/admsci3040237
Turcan RV. International New Venture Legitimation: An Exploratory Study. Administrative Sciences. 2013; 3(4):237-265. https://doi.org/10.3390/admsci3040237
Chicago/Turabian StyleTurcan, Romeo V. 2013. "International New Venture Legitimation: An Exploratory Study" Administrative Sciences 3, no. 4: 237-265. https://doi.org/10.3390/admsci3040237
APA StyleTurcan, R. V. (2013). International New Venture Legitimation: An Exploratory Study. Administrative Sciences, 3(4), 237-265. https://doi.org/10.3390/admsci3040237




