1. Introduction
Scholars have also examined how youth in the U.S. cope and seek help when experiencing TFA. Common coping strategies identified include self-reliance (such as blocking accounts or reporting incidents to platforms), seeking help from trusted individuals, and third-party interventions initiated by adults or peers. However, these approaches are often constrained by youth’s limited understanding of abuse severity, concerns over social stigma, fear of adult overreach, and the delicate balance between seeking support and preserving privacy and autonomy
Freed et al. (
2025). This help-seeking takes place in a broader ecosystem in which youth interact with technologies and the stakeholders who influence their ability to navigate TFA. Youth rely on parents, educators, mental health professionals, policymakers, and technology developers to create supportive environments and tools that enable them to build resilience and seek help when needed. However, existing approaches to digital safety often fail to fully account for the interconnected roles of these stakeholders, resulting in fragmented efforts that leave critical gaps in support systems.
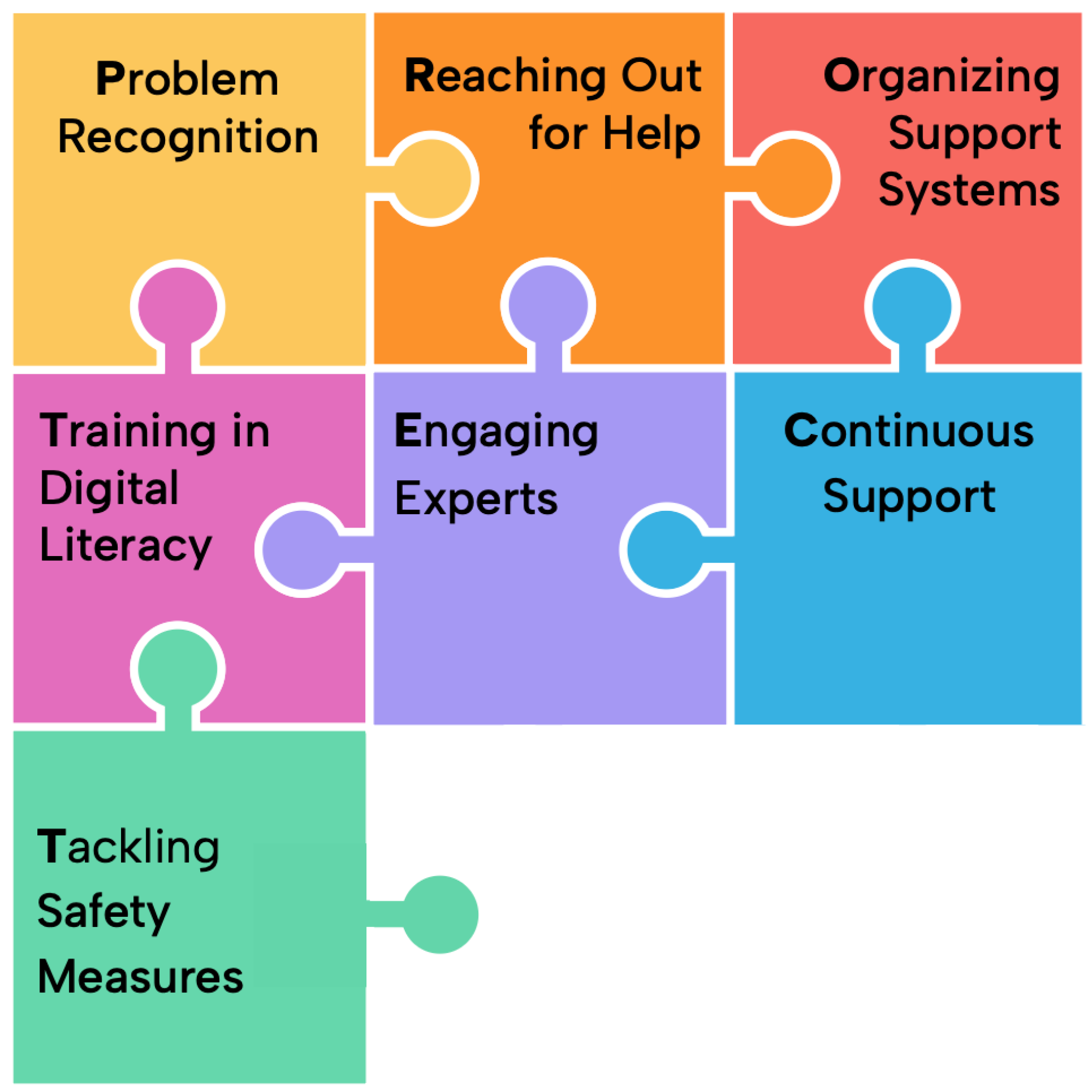
In this paper, we present the PROTECT framework (see
Figure 1), aimed at equipping adult stakeholders with concepts and strategies needed to help youth navigate and mitigate challenges posed by TFA. The PROTECT framework stems from empirical research with youth and adult stakeholders
Freed et al. (
2025) and builds on theoretical accounts of help seeking
Rickwood et al. (
2005), digital skills development
Livingstone et al. (
2022), and social support systems
Vaux (
1990);
Lyons et al. (
1998). The framework seeks to integrate this academic work and make it more accessible to youth, parents, and support professionals, guiding them through recognizing, addressing, and preventing TFA.
PROTECT foregrounds the interconnected social, contextual, and dynamic aspects of help-seeking behaviors while addressing digital risks and harms. It also emphasizes that navigating TFA is not a linear sequence of steps around specific threats with clear responses. The situated, longitudinal, recurrent, and evolving nature of TFA means that the elements of the framework will need to be put together and instantiated in different ways based on the needs and abilities of the individual youth and the adults who want to support them in a given situation.
To assess the potential for PROTECT to be useful to adult stakeholders, we conducted five focus groups with 34 adult stakeholders who used the framework to think about specific scenarios provided by the research team and their own needs, as well as offer conceptual and design critiques of the framework. Participants were largely positive about the framework, seeing value in how it foregrounded activities around building digital resilience that call out the role of both individual youth and the support systems around them. They were able to use it to generate specific ideas for interventions with youth and provided useful insights into future work that would be needed to fully transition the framework to practice. Together, this suggests that the PROTECT framework makes a valuable contribution to the growing body of research on youth digital safety and resilience by integrating that work and making it accessible through articulating collaborative, context-sensitive, and actionable strategies for parents and stakeholders that support youth.
2. Background
Before introducing the PROTECT framework in more detail, we first describe the empirical research and theoretical foundations regarding help-seeking, skill development, and social support that inform it. In particular, this framework draws significantly from the empirical insights presented by
Freed et al. (
2025), highlighting key patterns in youth responses and coping strategies as well as adult perspectives when faced with digital threats and harms.
2.1. Empirical Motivation and Key Challenges
Prior empirical research has surfaced critical challenges in help-seeking behaviors and support systems
Freed et al. (
2025), emphasizing the need to strengthen coping mechanisms and enhance available support systems. Ghosh et al. proposed the “Circle of Trust”, a model explicitly designed to balance adolescent privacy with parental concerns by fostering trust and open communication, providing an alternative to traditional parental control methods often seen as invasive and restrictive
Ghosh et al. (
2020). Akter et al. found that collaborative approaches involving both parents and teens, while challenging, significantly improve communication and transparency around mobile safety, suggesting an important shift from traditional parental control methods toward joint oversight models that can better empower youth
Akter et al. (
2023). Additionally, Alluhidan et al. illustrate how teens experience diverse impacts of social media, stressing the importance of recognizing both positive and negative dimensions to provide balanced and effective support
Alluhidan et al. (
2024). Their findings demonstrate the need for targeted safety strategies that align interventions with the distinct features and risks of specific platforms, complementing PROTECT’s tailored intervention approach.
Youth consistently report significant obstacles to seeking help when experiencing digital harm. Freed et al. found that concerns about stigma, fears of losing autonomy, and a lack of trusted resources frequently discouraged youth from reaching out to others
Freed et al. (
2025). In the absence of accessible and reliable support, many youth adopted self-reliant coping strategies, such as blocking perpetrators or ignoring harmful content. Although these strategies offered temporary relief, they often failed to address the underlying causes of harm and in some instances placed youth in an ongoing cycle of perpetual harm. Moreover, limited digital literacy compounded these difficulties, leaving young people ill-equipped to recognize risks or respond effectively
Freed et al. (
2025).
For adult stakeholders, Freed et al. found that despite their proximity to young people and their potential as sources of support, adults frequently felt that they were not prepared to address digital harm. Parents, educators, and mental health professionals reported that they struggled to recognize signs of harm, foster trust, and create safe spaces for youth to seek help. They also highlighted difficulties in coordinating responses to complex and multi-platform threats, particularly given the fragmented nature of current support systems
Freed et al. (
2025). These gaps often left stakeholders unsure how to respond effectively, resulting in inconsistent or incomplete guidance.
Throughout this research, both youth and adults consistently highlighted the urgent need for clear guiding principles or a cohesive framework to better support youth and foster meaningful collaboration with parents and other stakeholders. Youth shared compelling stories of navigating systems that felt disjoint and reactive, where inconsistent practices frequently defaulted to punitive measures rather than approaches rooted in empathy, growth, and a youth-centered mindset. They described feeling frustrated and in need of guidance that aligns with their agency, experiences, and needs for privacy and self-development.
2.2. Conceptual Models for Understanding Offline Help-Seeking and Digital Resilience
The empirical work calls out youth’s needs for effective help-seeking systems and self-reliant digital skills. Among the frameworks that respond to these concerns are Rickwood’s model of help-seeking behavior
Rickwood et al. (
2005) and Livingstone’s youth skills model
Livingstone et al. (
2022).
Addressing the mental health needs of young people aged 14–25, Rickwood’s model offers a structured approach to understanding the factors that affect help-seeking behavior among young people
Rickwood et al. (
2005). The model, which was developed in the context of offline help-seeking around mental health, identifies four key stages of help-seeking behavior: recognizing one’s own distress (awareness), articulating this distress (expression), acknowledging the existence of helpful resources (availability), and finally, deciding to seek help (willingness)
Pretorius et al. (
2019);
Rickwood et al. (
2005). Both prior literature
Pretorius et al. (
2019) and the empirical work described above suggest the potential value of adapting theoretical help-seeking frameworks to help conceptualize online help-seeking and guide the development of improved resources.
Livingstone’s youth skills (ySKILLS) model centers around the premise that adolescents are active participants in their development, with their digital skills serving as crucial mediators between the risks and opportunities related to use of Information and Communication Technology (ICT)
Livingstone et al. (
2022). The ySKILLs model highlights the concept of digital resilience, suggesting that fostering this trait in youth can empower them to effectively cope with online threats. This resilience is crucial for youth’s help-seeking behavior, providing them the ability to identify and respond to digital risks while managing their mental health vulnerabilities. The model also calls out how various societal factors such as adult norms, familial expectations, and business policies significantly shape these digital skills, as well as the potential insufficiency of even the most advanced digital skills in managing the intricacy of digital services and products.
Rickwood’s help-seeking model can offer insights into the individual mental health factors influencing an individual’s decision to seek help, while Livingstone’s ySKILLS conceptual model provides a framework for understanding the acquisition, use, and influence of digital skills among youth. While both models are concerned with youth mental health, they approach help-seeking from complementary perspectives. Rickwood’s model is centered on the help-seeking process. It offers insights into why young people may or may not seek help for mental health issues, and what factors can facilitate or hinder this process
Rickwood et al. (
2005). Livingstone’s work, conversely, focuses on digital skills and their role in mediating the risks and opportunities of ICT use. It examines how these skills, and the factors that influence them, impact the well-being of young people, particularly those with mental health difficulties
Livingstone et al. (
2022).
2.3. Socially-Oriented Models of Help and Support
Together, the Rickwood and Livingstone models provide a view of help-seeking centered on the perspective of youth. However, the empirical work described earlier also implicates the larger ecosystem of actors involved in helping youth manage digital risks. This led us to look for models of support that emphasize social context, two of which stood out as well-fit to the empirical observations: Vaux’s ecological support model
Vaux (
1990) and Lyons’ communal coping model
Lyons et al. (
1998). These models provide complementary perspectives on how individuals and communities respond to challenges, highlighting the critical role of social systems and collaborative strategies in building resilience and mitigating harm.
Vaux’s ecological model prioritizes the dynamic transactional process between an individual and their environment
Vaux (
1990). Vaux describes these “networks” as sustainable and able to give support on an ongoing basis. This emphasis is particularly relevant when studying help-seeking behaviors for TFA. Rather than looking at these behaviors and the resources they engage with as static components of a person’s experience, Vaux suggests focusing on the fluid relationship among appraisal processes, behaviors, and resources
Vaux (
1990). The approach calls for (a) mapping the links between appraisals, behaviors, and resources and (b) understanding of personal and ecological factors that shape the help-seeking process
Vaux (
1990). In the context of youth and digital abuse, this perspective illuminates how young people become cognizant of, evaluate, and decide upon the myriad support resources available to them. Applied to digital safety, this perspective emphasizes the need for multilayered adaptive systems that empower youth to seek help and rely on trusted relationships to manage risks effectively.
Lyons’ communal coping model
Lyons et al. (
1998) further emphasizes the role of community in providing support. The model describes coping with challenges as a “social process” that draws in others, including parents, peers, schools, and mental health professionals, who confront the problem individually and together. Instead of individuals independently managing their own stress or challenges, communal coping involves a shared perception of the problem, collective action, and shared responsibility. Like other coping strategies, communal coping is not a straightforward, calculated, two-phase evaluation and action procedure. Instead, its course tends to be more complex, involving a series of iterative assessment-action cycles
Lyons et al. (
1998).
Both the social-ecological support and communal coping perspectives foreground the embeddedness of help-seeking into a social context, along with the importance of relationships and circumstances in providing support. Youth’s own help-seeking and skill development behaviors are necessary, but not sufficient, to help youth manage and grow around TFA. Further, the social context (such as youth’s often-justified perceptions of adults’ lack of digital knowledge) will shape those help-seeking behaviors and affect the resources youth have to develop digital skills.
3. Framework
The PROTECT framework looks to integrate the empirical and theoretical research described earlier into a distilled form more accessible to adult stakeholders. We structure the framework around seven interconnected components: Problem recognition, Reaching out, Organizing support systems, Training in digital literacy, Engaging experts, Continuous support, and Tackling safety measures.
The framework is designed so that the components capture key constructs from the grounding research in a comprehensive but minimally prescriptive way that stakeholders can interpret in their own contexts. In particular, the framework prescribes few specific remedies because Vaux’s and Lyons’ models suggest that social context will affect both the resources that are needed and available. The framework also does not impose a sequencing or priority of the components, as the grounding research shows that there are many pathways through managing tech-facilitated abuse. Instead, the “puzzle piece” design in
Figure 1 looks to convey that these elements should be seen as things that youth advocates need to put together to work in their own situations. Each component responds to specific challenges called out in the empirical and theoretical grounding described earlier while strengthening the overall system of support, creating a resilient and collaborative foundation for digital safety. We now discuss each in turn.
Problem Recognition. We begin with the importance of Problem Recognition. Youth frequently face barriers in identifying risks—ranging from normalizing harmful behavior to lacking the digital literacy necessary to recognize covert threats. Similarly, advocates often miss signs of harm, particularly when that harm occurs in subtle or ambiguous ways, such as manipulative online interactions or covert data exploitation. Problem Recognition addresses this gap by highlighting the importance of fostering awareness at both individual and systemic levels. Youth should be equipped to discern risks in their own experiences, while advocates should be trained to recognize early warning signs and engage proactively. This shared foundation of awareness is essential to enable timely and effective responses.
Reaching Out. Recognition alone is insufficient without pathways to support; here, Reaching Out becomes critical. Many youth hesitate to seek help, fearing judgment, stigma, or a lack of understanding from adults. Reaching Out focuses on creating environments where youth feel safe to disclose their experiences, whether to parents, peers, or professionals. Reaching Out also draws attention to the importance of equipping advocates with practical strategies to foster trust and openness, ensuring that youth perceive help-seeking as accessible and non-threatening. This emphasis on bridging youth and adult stakeholders looks to dismantle the psychological and structural barriers that prevent youth from accessing the support they need.
Organizing Support Systems. Addressing digital harm requires more than individual effort—it requires Organizing Support Systems that unite families, schools, healthcare providers, and community organizations. Fragmentation within these systems is a common barrier to effective support, leaving youth to navigate disconnected and often conflicting resources. Organizing Support Systems emphasizes the need for building cohesive networks that align formal and informal supports. Advocates should be empowered to coordinate their efforts, ensuring that responses are timely, comprehensive, and tailored to the unique needs of each situation. By focusing on collaboration, this component signals the need to reduce the burden on youth while enhancing the overall effectiveness of support systems.
Training in Digital Literacy. Prevention is equally central to the PROTECT framework, and Training in Digital Literacy plays a vital role in equipping youth and advocates with the tools to proactively navigate online spaces. Digital literacy, in this context, extends beyond technical skills to include the ability to identify risks, implement protective strategies, and engage responsibly in digital environments. Training in Digital Literacy needs to be considered across the support ecosystem. For youth, this training should foster confidence and self-efficacy, empowering them to act decisively in the face of potential threats. For advocates, it should bridge gaps in generational and technical understanding, enabling them to support youth more effectively in a rapidly changing digital landscape.
Engaging Experts. When harm escalates or requires specialized expertise, Engaging Experts ensures access to tailored resources. Youth navigating high-risk scenarios, such as TFA or severe online harassment, often need intervention from professionals, including mental health practitioners, legal advisors, law enforcement, and digital safety specialists. Engaging Experts often involves reaching beyond existing support networks to recruit and integrate support. This component emphasizes the importance of connecting youth and their support networks with appropriate expertise, ensuring that complex challenges are addressed with care, precision, and professionalism.
Continuous Support. Another key concern in help-seeking is Continuous Support, as many digital threats develop over time (e.g., grooming), are persistent (e.g., cyberbullying), and/or have lasting impacts on youth victims. Continuous Support underscores the importance of long-term engagement aimed at building stability and trust over time, ensuring that youth have access to evolving support systems as their needs change. For advocates, Continuous Support underscores the role of maintaining relationships and addressing the ongoing challenges that youth face in rebuilding confidence and resilience.
Tackling Safety Measures. Finally, Tackling Safety Measures shifts the focus from individual and relational solutions to system-wide accountability. Digital harm does not occur in isolation; as implied by the phrase “Technology-Facilitated Abuse”, the algorithmic and interface design of the technologies, and the policies and practices of the companies and countries they operate in affect both youth’s risks around digital harms and their resources for managing. Tackling Safety Measures emphasizes the need for structural improvements, such as privacy-enhancing technologies, robust content moderation systems, algorithmic transparency, and effective policy around TFA. Tackling Safety Measures ensures that digital environments are designed to prioritize safety and equity, reducing harm at its source and creating conditions where youth and advocates can thrive.
The PROTECT framework positions advocates, parents, educators and other key stakeholders to see themselves as partners with youth facing abuse in a collaborative system of resilience building. Its interconnected components are designed to empower both youth and advocates to recognize and respond to risks while equipping them with the tools and confidence to act effectively. Whether through fostering awareness, coordinating responses, or driving systemic change, the framework ensures that youth are supported not only in addressing immediate challenges but also in developing the skills and systems necessary to navigate the complexities of the digital world in the long term. Youth are equipped to discern risks in their own experiences, while advocates are trained to recognize early warning signs and engage proactively. This shared foundation of awareness is essential to enable timely and effective responses.
4. Materials and Methods
After developing an initial version of the PROTECT framework, we conducted a series of five 60-min focus groups where we asked youth advocates to interact with the framework and suggest improvements to both its content and presentation. The goals of this study were to member check the analysis—advocates are familiar with the empirical situations that informed the framework and are also the main target users—and to iterate on the graphic design and communication to make it more accessible to future users. The research design was approved by the lead author’s IRB.
4.1. Participants (N = 34)
Thirty-four participants who support and advocate for youth participated in this study. The participant group included educators, medical doctors, lawyers, advocates, governmental representatives, and other health professionals, all of whom work directly with youth populations. Participants were recruited through community healthcare organizations and government partners in a large urban area and its surrounding suburbs.
Of the 34 participants, 25 identified as female, 8 as male, and 1 as non-binary. This composition reflects a broad representation of professionals involved in supporting youth, contributing varied insights and expertise to the evaluation process. Four sessions had 7 participants, and one had 6.
4.2. Study Design
Focus groups were designed to facilitate discussion and gather feedback on the relevance, applicability, and design of the PROTECT framework. Each session began with a 15 min overview of the framework, including its conceptual foundations, goals, and practical elements such as scenarios, step-by-step guidance, and reflective exercises. Participants were provided with visual and textual representations of the framework and were invited to review its components before engaging in guided discussions.
The lead author facilitated all sessions based on a structured guide to ensure consistency across focus groups while allowing flexibility for participants to share emergent ideas. The guide included discussion prompts organized around three primary themes:
Clarity and Usability: Assessing how effectively the framework communicated its concepts and practical steps.
Relevance: Exploring the framework’s applicability to participants’ professional contexts.
Strengths and Gaps: Identifying aspects of the framework that resonated strongly as well as areas requiring further development.
The guide also incorporated several collaborative activities, to encourage interaction and surface diverse perspectives:
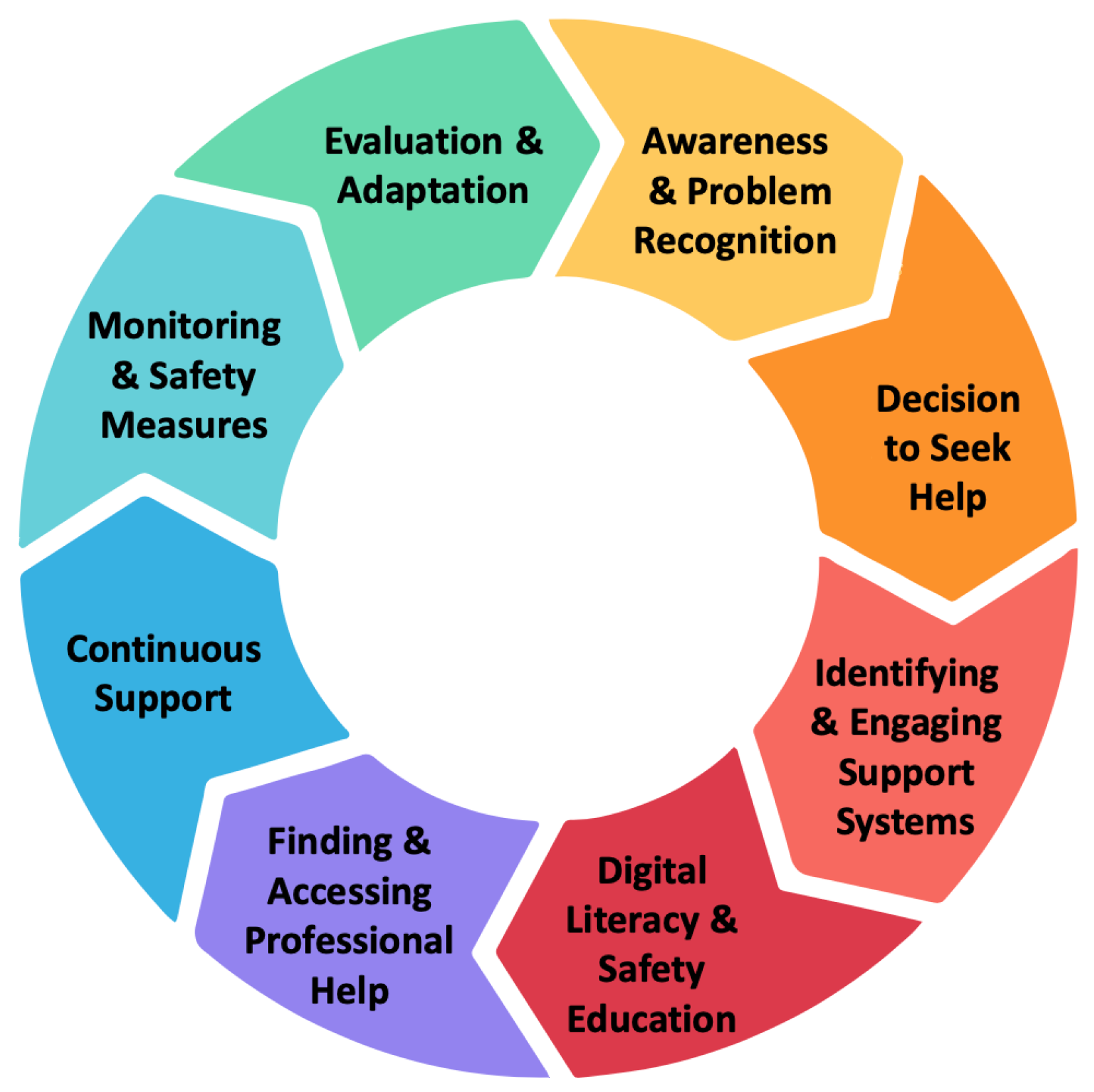
Feedback on Visual Design: Participants critiqued the framework’s visual elements, such as a circular representation that was used in the first iteration of the framework (see
Figure 2) intended to convey the non-linear nature of the framework.
Scenario Testing: Participants discussed the relevance of example scenarios to their fields and suggested ways to tailor them for specific audiences.
Brainstorming Adaptations: Participants explored how the framework could be adapted for different cultural, institutional, and resource settings.
4.3. Data Collection and Analysis
Detailed notes and session recordings were transcribed and used to inform iterations on the PROTECT framework. The focus group sessions provided rich, actionable feedback, demonstrating the value of co-creation in refining the PROTECT framework. The insights gained from these sessions informed iterative improvements to enhance the framework’s clarity, accessibility, and adaptability for diverse professional audiences.
5. Results
The evaluation of the PROTECT framework provided valuable insights into its strengths, relevance, and areas for refinement, highlighting its potential to address youth digital safety challenges. By engaging a diverse group of stakeholders through collaborative discussions, this process illuminated how the framework aligns with real-world practices and identified opportunities to enhance its usability and impact.
Participants emphasized the importance of the framework’s focus on fostering digital resilience, which they recognized as an essential skill for navigating the complexities of the digital landscape. Their contributions offered practical suggestions for refining key aspects of the framework, including its visual representation, audience-specific tailoring, language accessibility, and adaptability to diverse contexts.
Integration of Help, Skill, and Collaborative Support Perspectives on Digital Resilience. Digital resilience emerged as the cornerstone of the PROTECT framework, resonating strongly with many stakeholders. As one participant noted:
“It’s not just about avoiding risks but about building skills to face challenges better in the future. Many ways we handle things today are one-offs. Here, PROTECT is weaving together important threads that can be used to guide youth. Continuous support speaks to what is needed.”
(Educator, P5)
The framework emphasizes resilience as a shared responsibility, requiring active collaboration among youth, families, professionals, and digital platforms. This holistic approach equips youth with the tools and support systems needed to navigate and succeed in digital environments.
Visual Representation: Clarifying Non-Linear Help-Seeking. The initial circular design of the framework reflects the non-linear and iterative nature of help-seeking behaviors, allowing youth to engage at any entry point. However, some stakeholders noted that the visual design could imply a fixed starting point. One participant remarked,
“When I see circular diagrams with arrows, my first thought is, where do I start? Since, as the PROTECT framework states, help-seeking can begin anywhere, let’s make sure to visualize that.”
(Social Worker, P9)
Another participant emphasized the value of making the non-linear, start-anywhere nature of both help seeking and the framework clear, suggesting,
“Adding a phrase like ‘You can start anywhere’ in the center could clarify that any entry point is valid. This approach aligns with my emphasis on fostering open communication and patient-centered care. Right now, we don’t have a structured process in place to guide patients through this, but incorporating such language could make a meaningful difference in helping them feel supported and understood.”
(Physician, P29)
Participants shared that simplifying the graphic by removing arrows or explicitly labeling it as a continuum of interconnected elements was recommended to enhance its clarity and reinforce its adaptability. Many participants suggested these refinements align with the framework’s emphasis on resilience by recognizing that youth and professionals may revisit or re-engage with different components of the framework as situations evolve.
Multiple Versions to Support Stakeholders Working Together. Participants highlighted the need to create companion materials to broaden the audiences the framework speaks to, tune it to their differing needs, and support interaction between stakeholder groups. Many participants suggested that PROTECT can be used with curated case studies to guide professionals that include, law enforcement, healthcare professsionals, parents, and youth. While the current version is designed to empower professionals to guide youth, some language implied that the framework was directed at youth as the primary agents of change. One stakeholder advised,
“Whose journey is this? Are we guiding youth or providing tools for professionals? Why not both. This can apply to both and should. I treat youth and adults. I could use this with parents too.”
(Social Worker, P1)
Twenty-nine participants suggested creating materials tailored to different groups, including youth and professionals. For youth, materials should focus on building agency and empowerment, while for professionals, they should emphasize actionable steps and institutional strategies. One participant noted,
“For youth, it should be part of a toolkit they can use. For professionals, it offers clear steps they can take. It would be great if they can be used together. We don’t have these things. We need to speak the same language with the parents too.”
(Educator, P19)
These distinctions ensure the framework remains relevant to diverse stakeholders while reinforcing resilience through collaboration.
Language Accessibility and Adaptability Across Stakeholder Groups. Ensuring the language used in the framework is accessible and relevant to its intended audiences was another key theme. Stakeholders emphasized the need to adapt terminology to reflect the evolving ways younger generations discuss digital platforms and risks. A participant remarked,
“The way younger generations talk about social media is so different. If the language isn’t relevant, it might not resonate.”
(Lawyer, P30)
Simplified and jargon-free language was recommended to maintain engagement and build trust. Participants shared that training materials should include strategies to bridge generational language gaps, enabling more effective communication. Accessible language is critical to fostering resilience by ensuring that youth and professionals can navigate and implement the framework confidently.
Potential Versatility of Implementation Contexts. Participants saw the PROTECT framework as potentially being versatile across diverse settings, underscoring its value in promoting youth digital safety. Schools were highlighted as primary venues, with one participant suggesting,
“Schools already do screenings for vision and dental health—why not digital safety too? We don’t have something like this in our district. This is actionable and kids will get it.”
(Educator, P18)
Healthcare settings, such as outpatient and primary care environments, were also identified as potential contexts for implementation. One participant noted,
“It could even be a visual in the waiting room to start conversations about digital safety.”
(Physician, P5)
Community programs and youth services were also highlighted as spaces where the framework could empower educators and social workers to support youth effectively. These implementation opportunities connect directly to resilience by integrating digital safety practices into everyday environments, ensuring sustained engagement and support.
Digital Safety Training. Many participants thought the framework itself could be used as a digital safety training tool. One participant asked,
“If a child discloses something serious, like harassment, in front of their parents, how do we handle that? We might need to know beyond PROTECT, what we can do. Maybe add training needs to prepare providers for that.”
(Social Worker, P17)
Training should equip professionals with strategies to navigate complex ethical situations while adhering to legal and institutional requirements. Participants emphasized the need for actionable guidance in training programs, with one participant stating,
“It’s not enough to hand someone a tool; they need to know how to use it effectively.”
(Educator, P19)
These elements ensure that professionals can confidently apply the framework to build digital resilience within their communities. All participants agreed with the seven components of the PROTECT Framework.
Value and Necessity of the Framework. The PROTECT framework addresses critical gaps in youth digital safety by offering a structured, adaptable approach to help-seeking. Its emphasis on non-linear, collaborative processes makes it uniquely suited to the realities of digital risk navigation. A stakeholder summarized its importance:
“This isn’t just about solving immediate problems—it’s about building a foundation for long-term resilience.”
(Nurse Practitioner, P12)
6. Discussion
Feedback from our participants suggests that the PROTECT framework has real potential for helping advocates improve their ability to help youth manage digital harms. They appreciated the emphasis the framework places on digital resilience and its framing of resilience as a collective effort centered on youth. We see this interpretation of the framework as evidence it does make progress toward our goal of successfully integrating the individual help-seeking, digital skill-building, and collective support frameworks we draw on. Participants were also able to use the framework to brainstorm a number of ideas for developing resources to support youth resilience, as well as ideas for improving the framework itself.
In this section we discuss how doing the study has already improved the framework, and how participants’ ideas suggest important next steps in moving the framework toward practice.
6.1. Improvements to the Framework Itself
Participants’ reactions led to several concrete improvements to clarify the framework for potential users, including clearer conceptual definitions of the high level constructs and the visual design.
As noted in the results, the study version’s circle-with-arrows visual design did not adequately convey the non-linear and iterative nature of help-seeking and harm prevention. Instead, participants expressed concerns that the circle implied a fixed starting point or a rigid sequence of steps, which conflicted with the framework’s emphasis on flexibility. Based this feedback, the authors explored several alternative visualizations before converging on the puzzle-inspired representation shown at the beginning of the paper (see
Figure 1). This revised design was sent to participants for feedback and on balance resonated with adult stakeholders. They saw it as conveying the framework’s adaptability while maintaining a cohesive structure. The interlocking pieces emphasized the interdependence of the components and the flexibility to engage with them dynamically and at any entry point, capturing real-world processes of help-seeking and harm prevention. The puzzle metaphor also looks to convey the collaborative and systemic aspects of the framework in an abstract way, highlighting the importance of integrating efforts across families, educators, professionals, and platforms to create a comprehensive support ecosystem. More concretely, the puzzle-like design lends itself to physical instantiations that health professionals and educators thought could be helpful when working with youth.
Discussions with participants were also instrumental in clarifying definitions of several of the framework components. In particular, the descriptions of the “Identifying & Engaging Support Systems” and “Finding & Accessing Professional Help” constructs in the original framework muddied a fundamental question about whether needed expertise was already available within a support system. Participants’ feedback made clear that a distinction needed to be made between working within an existing support system and the resources it offers, versus reaching beyond the existing structures to engage stakeholders with special expertise not already available. This was reflected in changes to both the definitions and the titles of those components (with “Identifying & Engaging Support Systems” becoming “Organizing Support Systems”) and “Finding & Accessing Professional Help” becoming “Engaging Experts”).
We also removed the “Evaluation & Adaptation” and “Monitoring & Safety Measures” constructs from the study version, replacing them with the more comprehensive“Tackling Safety Measures” component in the current version. We made this change to streamline and consolidate safety-related constructs, ensuring clarity and reducing redundancy.
6.2. Case Study: An Example Using PROTECT to Identify Needs
Perhaps the most common way we envision stakeholders using the framework is as a tool for identifying gaps in or brainstorming improvements to support systems for youth navigating TFA. Here, we provide an example of what this might look like, based on a composite case drawn from real-world accounts
Freed et al. (
2025). In this composite case, Anita is a 16-year-old high school student who encountered harmful interactions online over fourteen months. She has finally gathered up the courage to talk to a school counselor about the issues she faced and how she felt facing them. The callouts to elements of the PROTECT framework present how the counselor might use aspects of the framework to think about Anita’s needs and the state of the support system around her.
One of the earliest forms of harm Anita experienced was through private messages from anonymous individuals. Initially framed as casual compliments, these interactions quickly escalated into explicit demands for inappropriate images. The anonymity of the online environment and the ability to create multiple accounts emboldened perpetrators, leaving Anita feeling cornered and powerless to escape the pressure.
Training in Digital Literacy: Anita doesn’t appear to know how to restrict access from strangers on this platform. Also, Tackling Safety Measures: features of the platform enable harms.
In these instances Anita feared she would get in trouble because adults might blame her for encouraging the explicit requests. This initial exposure set a troubling precedent for her subsequent digital experiences.
Reaching Out: the concerns about getting in trouble suggest a lack of trusted relationships with adults who might otherwise help.
In another instance, Anita encountered financial exploitation in the guise of a “sugar daddy” offering financial support in exchange for a relationship. What initially seemed like an innocuous proposal quickly turned manipulative, as the individual normalized predatory behavior and used the payments as a blackmail threat. Although Anita eventually blocked the perpetrator, the experience left her feeling emotionally manipulated and exposed to more risks.
Problem Recognition: Anita didn’t see the danger that the financial aspects of the relationship might pose. Also, Training in Digital Literacy: On the plus side, Anita does demonstrate digital skills for mitigating the direct harm (though as noted it left lasting effects).
Exposure to bullying from peers further compounded Anita’s challenges. Hurtful comments, exclusion from online group chats, and targeted mockery about her appearance and interests were pervasive on her social media platforms. These incidents contributed to Anita’s growing sense of isolation and self-doubt, while attempts to report them to teachers were ineffective (and not communicated to parents or school counselors).
Organizing Support Systems: the lack of effective support from the school and coordination with other adult stakeholders highlights important gaps in the support networks available to Anita.
Over time, the combination of repeated harassment and sustained bullying normalized the harms, making Anita question whether her feelings of distress were valid or whether she was simply overreacting. This resignation further eroded her willingness to seek help or to recognize the seriousness of her experiences.
6.3. Lessons from the Case Study
The example above is short, but hopefully gives a sense of how the framework provides sensitizing concepts for thinking about barriers to youth’s effective navigation of TFA. A more complete example might involve analyzing a set of youth’s TFA journeys to look for common breakdowns. It might also include the counselor and other school stakeholders analyzing their own stories of how they have responded to youth’s needs in the past to identify gaps in their own digital literacy training, ability to recognize problems, and organize support systems. This might move from identifying problems and needs to brainstorming possible changes to the ways the school looks out for students, provides resources, communicates with parents, or other ideas for trying to improve the support ecosystem and their effectiveness in it. The specific forms of those needs and ideas for improvement will be context-dependent and may focus on particular parts of the framework that a given stakeholder is best equipped to reason about or act on. The PROTECT framework is designed to encourage this through its flexible and non-linear design.
At a more general level, the case study highlights critical lessons for addressing youth digital safety and the role of the PROTECT framework as an organizing construct for stakeholders. Anita’s experiences underscore the pervasive and interconnected nature of digital risks, which require a non-linear and holistic approach to effectively support youth. The PROTECT framework offers a way to structure responses to these challenges, focusing on promoting awareness, fostering resilience, and creating systems of shared responsibility. The framework addresses these challenges by emphasizing collaboration among stakeholders, including families, educators, professionals, and digital platforms, to create accessible, stigma-free pathways for support. The interchangeable nature of the framework enables stakeholders to engage with youth at any point in their journey, ensuring that interventions are both timely and context-sensitive.
Anita’s case also highlights the emotional toll of navigating digital harm, from feelings of helplessness and frustration to desensitization caused by repeated exposure to harmful content. The PROTECT framework responds to these challenges by prioritizing resilience-building strategies, which equip youth with the skills and confidence to navigate the digital landscape while recognizing their own agency.
6.4. Limitations
While the PROTECT framework represents a significant advancement in youth digital safety, it is not without limitations. First, its applicability across cultural and socioeconomic contexts requires further exploration to ensure global relevance. Tailoring the framework to address local norms, values, and resources will be critical for broader adoption. Second, its dependence on institutional systems may not address the needs of youth who lack access to such environments. Alternative delivery models, such as mobile applications or virtual communities, could help bridge this gap. Additionally, we recognize the importance of including youth perspectives directly and our future work is focused on youth perspectives regarding PROTECT.
7. Conclusions
The flexibility of the PROTECT framework makes it suitable for implementation in diverse contexts, including schools, healthcare settings, and community programs. Stakeholders highlighted its potential for addressing systemic gaps in help-seeking and promoting digital literacy.
Moving forward, we will collaborate with youth and advocates to evaluate the PROTECT framework in real world contexts to understand its effectiveness in addressing the nuanced challenges of youth digital safety. By deploying the framework in schools, community organizations, and health care settings, our objective is to evaluate its practical impact on youth help seeking behaviors, resilience, and digital literacy. This work will involve participatory methods, ensuring that youth perspectives remain central to the evaluation, and will focus on identifying opportunities to refine and adapt the framework for diverse sociocultural contexts.