Abstract
Information communication technology (ICT) is becoming a pivotal element in the twenty-first century, and while there has been substantial work conducted to understand ICT use by older adults, there is a paucity of knowledge relating to ICT use and behavior by Millennials. The Technology 4 Young Adults (T4YA) study opens the discussion to the barriers and enablers of ICT by Millennials in their day-to-day activities. Eight participants aged 18–33 years were recruited, and open-ended questions were posed to the focus groups participants. A total of three focus groups were conducted, two focus groups were conducted in Pontefract (West Yorkshire, England) and one focus group was conducted in Swansea (West Glamorgan, Wales); all focus groups were recorded and transcribed verbatim. Primary themes included: hardware, privacy issues/concerns, confidence, usability/functionality, day-to-day activities, and content/sharing of information. Day-to-day activities were undertaken primarily on smartphones, such as online banking and shopping, while privacy and trust concerns was a conversation thread throughout the discussions. Further work is needed with larger sample sizes, taking a multi-methods approach to extract quantitative data to underpin qualitative data analysis and frameworks. This exploratory study intersects at the fields of social sciences and human–computer interaction.
1. Introduction
Approximately 90% of UK adults aged between 16 and 44 years old are users of the Internet, in comparison to 44% of adults aged 75+ years old [1]. To date, there has been a dearth of work understanding the impact of information communication technology (ICT) on the lives of Millennials (circa 1982) [2]. Additionally, there is little understanding of how ICTs may impact the lives of Millennials regarding social isolation, reducing loneliness, and increasing active and healthy ageing (AHA).
There are discrepancies across the literature regarding the commencement of the Millennial cohort. Nielsen [3] provides a breakdown of the different cohorts and years (Table 1) throughout the 20th and 21st centuries. While Vogels [4] and Dimock [5] report that those adults who are aged between 38 and 53 years (2018) are Generation X (1965–1980) and the Millennial generation commences at various stages starting from the mid-1970s onwards, Nielsen [3] provides a somewhat different perspective (Table 1) to [4,5]. For the purpose of this paper, the description of Millennials by Vogels [4,5] will be used.

Table 1.
Different cohorts of generations.
In setting the context, for many people in society, in particular demographers, academe, and journalists, the Millennials have grown up in a society with a great sense of freedom, in comparison to their predecessors—the Baby Boomers. The Baby Boomer cohort were born between 1946 and 1964 and are known as a cohort of society who were involved in the civil right movement, the Vietnam War, and the women’s and gay liberation movement [6]. The term Millennial, including those who may be categorized as a post-Millennial [3], will be used throughout this paper.
This paper is distinctive because it aims to explore and present data relating to the day-to-day use of ICTs by Millennials living in two regions of the United Kingdom (UK), England and Wales, and presents qualitative data from three focus groups.
2. Background Literature
ICT and Social Media in Society
The developments in ICT have led to a change in device usage from desktop to mobile and smartphones, facilitating greater access and usage of the Internet, social media platforms, and mobile apps (mApps). Currently, the literature shows 92% of American Millennials own a smartphone, which is higher than people categorized as Generation X (85%), Baby Boomers (67%), or those members of society categorized as the Silent Generation (30%) [4,5]. Moreover, Facebook and other social media platforms facilitate Millennials to play out their life across the respective social media platforms (e.g., Facebook, LinkedIn, Pinterest, Twitter), while communicating and socializing with friends, peers, and strangers, thus resulting in many Millennials showing a positive approach to taking up the varying developments [7] of ICTs and social media platforms.
Since 2014 there has been more than 81% of Millennials engaging with social media platforms [8]. This growth and trend of using social media platforms has resulted in Millennials having approximately 250+ ‘friends’. By comparison, older cohorts tend to have fewer social connections and are more skeptical of using such platforms [7]. Social media platforms offer users a variety of activities, including chatting with friends, sharing information (i.e., news, photographs), updating statuses, and taking ‘selfies’ (i.e., a photograph of yourself).
The Pew Research Center ascertained that 55% of Millennials had taken a ‘selfie’ and shared it across their social media profile. There is a generational divide regarding the concept and activity of sharing content over social media platforms; Millennials perceive this form of activity as an acceptable form of communication, but not so by older generations [7]. Phenomenal ICT developments have, in turn, impacted individuals and users alike from across all age cohorts of society. Whilst this can have a diverse impact overall on society, including smaller groups or communities, such ICT developments can and do offer individuals the ability to share content and enhance one’s social connectedness and potentially reduce isolation and loneliness. The rise and development of social media platforms and communication tools (e.g., WhatsApp, Viber), mApps and mHealth apps, and digital game consoles (i.e., Nintendo Wii) can, for some young people, offer alternative ways of accessing their existing social networks, as well as building new social connections. Furthermore, such ICT developments have facilitated users to share content and communicate easier with friends, family, and community/organizational networks (e.g., hobbies and groups) in real time. They also make it possible to self-monitor one’s health via mHealth apps while also having the opportunity/ability to share this content with individuals or health practitioners. The latter has previously been discussed by Marston and Hall [8], who provide an in-depth understanding of the field of gamification from the standpoint of active and healthy ageing.
From a UK standpoint, the most popular forms of social media platforms used in 2016 were WhatsApp and Facebook, while the use of Pinterest decreased between 2015 and 2016 [9]. Between 2016 and 2017, Ofcom (Office for Communication) identified few changes in online activity by adults aged between 16 and 54 years. While accessing the Internet via smartphones increased from 66% in 2016 to 70% of adults in 2017 [10], Frequency of use showed 40% of adults aged between 16 and 34 years spent more time online than adults aged 55+ years. While 51% of adults aged 16–24 years used on-demand/streaming services in 2016, this did increase slightly to 55% in 2017. Internet access has changed over the decades, and similarly this is true for digital device usage, resulting in a decrease between 2016 and 2015, from 73% to 66%.
Since 2010, Ofcom have identified 52% of adults aged 16–24 years reported owning a smartphone (i.e., BlackBerry, iPhone, and HTC) [11], while 88% of adults aged 25–34 years use smartphone/tablets, and a further 66% of adults also use/own these devices. Younger generations in comparison to older generations are more prone to using social media and mApps [9]. Ofcom reported that 81% of adults in 2014 visited social media platforms or mApps, accessible via various digital devices [11].
The growth and expansion of mobile phones to smartphones has led to the design and development of mApps and mHealth Apps. This has facilitated the general population and those who identify as life-loggers to share (if they choose to) their progress (e.g., health, physical activity) or information (e.g., checking into a restaurant) with friends, family, or health practitioners in different formats (i.e., social media, email, or by clicking on the App and displaying the information) [12]. Fox and Duggan [13] noted, “31% of cell phone owners say they use their phone to look for health or medical information online. That is up from 17% of cell phone owners in September 2010” (p. 4). Furthermore, Fox and Duggan [13] identified the most popular mHealth apps used by 254 respondents, with 84% of users downloading mApps via their smartphones, and 19% of respondents choosing to download an mHealth app to track their health [13].
Given the current functions and capabilities that ICTs can offer users, there are additional fundamentals that users should be aware of and should consider when taking action, for example, securing one’s privacy. Ofcom note, “a number of them are now employing tactics to manage these concerns,” [10] (p. 4) which include multiple email addresses, providing false information to companies to limit the number of spam emails, and managing their own privacy settings. Yet, 22% of the respective participants reported little consideration of their privacy when posting information across social media [9].
Existing literature focusing on ICT use by young people stems from a myriad of disciplines and perspectives, including sociological theory [14], digital inclusion [15,16], demography, socioeconomics and inequality [17,18,19,20,21,22], attitudes, behavior, and identity of users through the lens of using technology and social media within education [23,24,25,26,27,28,29], user behavior, perception and engagement technology of ICTs in society [30,31,32,33,34], and using ICTs to search for sexual health information [35]. While there is existing published work, the body of work in this manuscript, based on an exploratory study, offers a qualitative insight into the behaviour, perception, and impact of ICTs on Millennials.
Internet use and access across the UK by children and teenage aged 9–19 years was previously reported by Livingston and Bober [17], who ascertained that existing inequalities were still prevalent within society. While 75% of households reported having Internet access, a further 74% reported to access the Internet via a digital games console or digital television. However, across UK society 92% reported access to the Internet, with 24% of children and young adults having access to the Internet via their education institute as opposed to their home [17], and a further 64% of respondents noting that they access the Internet in a different location (not in the home or school) [17]. Yet, Livingston and Bober [17] noted that socioeconomics and cultural differences result in greater inequalities, which in turn are allied communities within societies accessing the Internet. Thus, in turn, resulting in 88% of middle-class children and 61% of working-class children having access to the Internet [17]. A myriad of counties and districts across England are categorized as having low deprivation, resulting in 86% of children having opportunities to access the Internet via a home computer. Yet, districts categorized as highly deprived areas highlight the drop-in children (66%) accessing the Internet via a home computer [17]. This illustrates the impact that socioeconomic and cultural differences have on children’s access to ICT and the Internet.
A review conducted by Best, Manktelow, and Taylor [36] identified 43 papers relating to the effects and relationships between online activities associated with ICTs and adolescent mental well-being. Eight online databases were searched, resulting in relevant literature identifying positive engagement with online ICTs, including increased self-esteem, perceived social support, increased social capital, safe identify experimentation, and an increased opportunity for self-disclosure. Yet, this review highlights the negative perceptions of using online ICTs, including increased exposure to harm, social isolation, depression, and cyber-bullying [36]. However, concluding evidence identified contradictions, such as methodological issues, including an over-representation of cross-sectional survey-based research, while the experimental based-research was deemed stronger than the former grounded on respective research questions [36]. Respective recommendations were proposed and included adding a ‘weighting’ approach to measure the quality of methodological approaches used in reviews. Final conclusions note, “[…] technology acts merely as a facilitator of human interaction and is value-free, neither promoting the good nor the bad” [36] (p. 34). This respective review illustrates how social media can be deployed by health and social care practitioners as a means of accessing hard to reach populations (i.e., young males suffering with mental health) [36].
Concerns about users’ privacy through third-party companies knowingly or unknowingly retrieving data via a user agreeing to the terms and conditions of an mApp have become an area of popular research within the fields of computer science and human–computer interaction (HCI); in particular, exploring the notion of privacy by users from a computer science standpoint [37,38,39,40].
In the field of HCI, the exploration and investigation of wearable devices [41] and the Internet of Things (IoT) have become popular areas of research [42]. In 2008, Kwasny et al. [43] conducted a series of focus groups to explore and investigate the privacy beliefs of young adults attending a Higher Education Institute in the USA. A total of 26 students aged between 18 and 28 years old were included, with gender equally represented. The purpose of the focus groups was to ascertain whether there were common privacy issues deriving both on an individual and contextual basis; thus, to understand the notion of one’s privacy in the context of daily activities. Participants were asked to record (written), their own definition of privacy and via a bottom-up coding approach, 59% of views reported that privacy relates to other people, and 52% believed privacy relates to information in one form or other. Also noted were several additional beliefs, including: the notion of controlling a piece of information (26%), deciding what to do with this information (30%), disclosure refers to the act of sharing information (41%), and non-disclosure refers to whether information should be kept to that individual (37%). Additional discussions identified the rights of privacy (22%), and mutual respect (15%) relating to one’s own personal information (11%). Of the participants from this study, 82% reported to have strong privacy beliefs and wish to protect themselves from invasion, while the remaining participants were open to sharing information and access at times. However, this set of results is higher than the respective research by Harris [44], who reported a total of 64% of participants who had similar opinions.
Similarly, Ray and colleagues [45] explored the notion of mental models and privacy in the context of real-life applications, specifically focusing on older adults, to understand their respective understanding of privacy. A total of 20 participants were recruited aged ≥60 years, gender was equally split, and the oldest participant was an 80-year-old male, whilst the oldest female was 73 years old. A total of eight participants did not have a prior ICT background. Results identified areas of privacy. For example, the older adults reported a fear and frustration to their invasion of privacy, such as telemarketers or spam emails (e.g., suspicious). Additionally, via visual constructs these participants reported their barriers and concerns to privacy through imagery. For example, a pile of documents illustrates the participants’ preferences to continuing to use a paper-based approach to their record keeping. Furthermore, the code featured relating to the participants’ visual constructs to ascertain whether their drawings were associated with personal feelings or experience, or whether their perceptions were based on the overall perception of privacy in society. Although the results showed a majority, but not exclusively, negative perception of privacy relating to both aspects, personal and societal experiences were documented. Some participants queried the extent of data held by third party companies, whilst another participant was concerned about using online banking in case a button was pressed wrong and that action was not able to be undone. However, there were positive perceptions, which included online interaction, and five participants reported ease of family interactions and accessing information. Similarly, a study by Oates and colleagues [46] explored the understanding of privacy from the standpoint of a layperson, by qualitatively analyzing 366 drawings associated with privacy from four types of actors (i.e., laypeople, experts, adults, and children). The age ranged between 4 and 91 years old, split across 11 categories. Gender was not equally split, with the majority of participants (n = 149) were female, while 84 participants did not report their gender. Results highlighted many non-experts represented and illustrated a divide between two spaces—physical and private. Yet, the experts were able to derive a more concise and nuanced understanding associated with their perceptions of privacy within spaces. The drawings by the children seldom represented privacy and featured more about home environment or school activities. Furthermore, those children who were 10 and under did not illustrate their respective digital space, unlike the teenagers, who in their respective drawings illustrated computers, phones, and the Internet.
Moreover, Wu and colleagues [40] took the perspective of privacy from the standpoint of user mental models associated with encryption in daily activities. Conducting 19 semi-structured interviews, Wu and colleagues used qualitative data collection to identify four mental models of encryption: (1) access control—minimal/abstract of access control; (2) black box—is viewed by participants as an extension of existing credential-based access, and participants understood this perception/mental model of privacy would change the data; (3) cipher—relates to the participants have substantial understanding of the encryption/data transformation process, understanding that segments of data are changed considerably; (4) iterative encryption, and the participants categorized into this mental model showed detailed understanding of the encryption process.
Conversely, similar scholarly activity has been conducted to develop a privacy framework to inform the development, adoption, and use of home-based ubiquitous technologies aimed at older adults [47]. A total of 65 participants were recruited, with an age range between 70 and 85 years, recruited via local community and university events. A variety of commercial and purpose-built prototypes were available in a living lab environment, which facilitated the research team to give the participants (in small groups of two–four adults), on a rotation basis (every 10 min), the opportunity to engage with the respective technologies. Scenarios and questions were posed to the participants, and by taking a grounded theory approach, the data analysis ascertained eight themes: (a) usability, (b) utility, (c) personal autonomy, (d) technology as replacement, (e) social implications of technology, (f) perceived vulnerability/personal concept of aging, (g) functional types of technologies, (h) privacy and technology ([47] p. 239).
Based on the findings from this study, the scholars noted how the participants perceived privacy as a combination of contextual and individual factors, and is influenced by psychosocial motivations in later life. Furthermore, the privacy framework regarding ubiquitous home-based technologies should consider several elements, including the importance of social relationships, data granularity, sensitivity of activity, and the perceived usefulness. The latter was perceived important by the participants after experiencing a fall or other similar age-related issues (e.g., cognitive decline). Although the participants noted how such technology, which included sensors, could be positive within the home context, it would only be welcome if a fall or other age-related incident occurred (p. 249).
3. Methods
3.1. Aims and Objectives
The Technology 4 Young Adults (T4YA) exploratory study aimed to examine the experiences of ICT use by Millennials aged between 18 and 34 years and explore the day-to-day use of ICTs and privacy issues by Millennials living in England and Wales, UK.
3.2. Ethical Approval
Ethical approval was granted by The Open University human research ethics committee (HREC) [HREC/2017/2525/Marston/2]. Several iterations of the HREC application were undertaken between 5 April and 31 May 2017 due to the recruitment processes changing.
3.3. Study Design
A total of eight participants were recruited, three men and five women, across Pontefract and Swansea in the counties of West Yorkshire and West Glamorgan to take part in focus group discussions. Participant demographics showed a Median age of 18, SD = 7.03. Marital status identified six participants reported to be single, one participant reported to be married and another participant reported other. Education displayed the majority of participants had attained A-level/college qualifications (n = 4), followed by GCSE/Secondary high school (n = 3) education, and one person reported to have a University education (BSc/BA). The majority of participants were employed (n = 6), with two participants reporting to be unemployed, which included one participant reporting that they were in receipt of welfare support. Living status showed the majority of participants (n = 7) lived with friends or family, and one participant reported to live with their spouse.
3.4. Recruitment Material
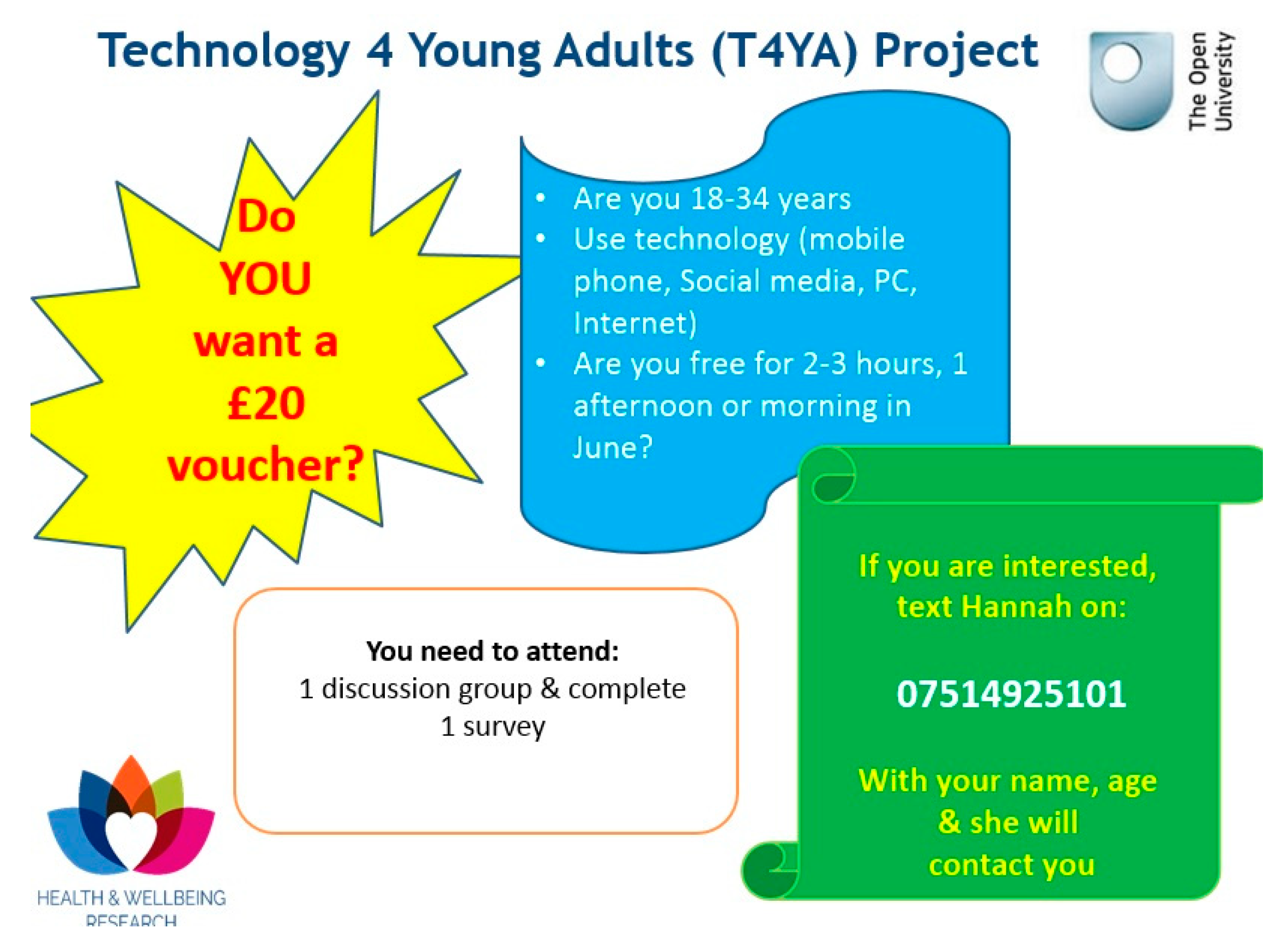
Traditional recruitment approaches were undertaken, i.e., poster, newspaper advertisements were placed (twice) in the Pontefract and Castleford Express over a two-week period (Figure 1). HREC approval was granted on 5 April 2017.
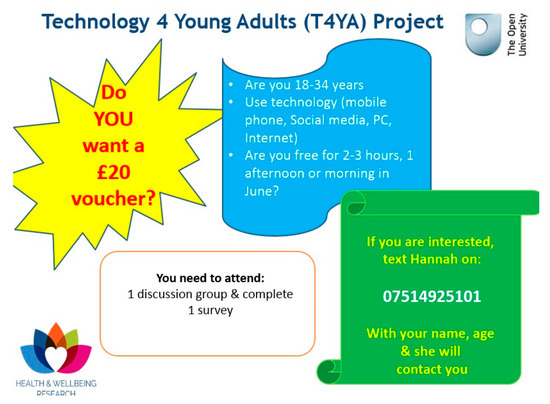
Figure 1.
The amended poste r used for participant recruitment.
As the weeks progressed, there was no interest from prospective participants and the poster was amended with less text, a separate contact number enabling interested participants to contact the researcher with their interest and detailing a remuneration for participant involvement in the project (Figure 1). All participants received a £20 ‘Love to Shop’ voucher for taking part in the study.
Further iterations of the HREC application were conducted to enable participant recruitment via social media—Twitter and Facebook (Figure 2). Recruitment via Facebook was undertaken via the author’s personal profile page, detailing a screen shot of the amended recruitment poster and ensuring the advertisement post was ‘globally visible’, which facilitated friends of friends to share the post.

Figure 2.
The amended poster and its deployment via Facebook for participant recruitment.
Recruitment via social media resulted in six participants, however, three participants dropped out and another participant was recruited on one of the scheduled focus group days. A further four participants were recruited in Swansea and were recruited via word of mouth, through a colleague of the author. Due to limited resources, this focus group was conducted in a colleague’s home.
3.5. Measures
A survey was deployed, based on previous iterations deployed in two international studies, the Technology In Later Life (TILL) Study [48], and the iStoppFalls EU project [49]. To date, there has been four scholarly works published using this survey [50,51,52,53] and an earlier iteration of a survey deployed in the TILL is available [50] for download. All participants recruited to the focus groups were required to complete an 80-item survey [51,52,53,54], which was developed from earlier iterations and included several domains which also informed the focus group discussions, ICT use/ownership and access, Internet use/ownership, digital device ownership and social networking habits, quantified self/lifelogging sharing of information.
Previously, this survey was used on older adults, and given the nature of the survey items, no amendments to the survey were conducted. This is because there were no specific age-related survey items within the survey itself, but items primarily focusing on ICT use and associated behavior. Qualitative data collection instilled an open-ended line of questioning, following the domains within the survey and asking participants to describe their perceptions of future technology use. Only the qualitative data will be reported, since given the small sample size, there is a paucity of sufficient data to report this specific information at this moment in time to draw any firm conclusions. Whilst more data would have helped this exploratory study, it still may not have provided a firm conclusion and thus, by providing a specific qualitative insight from the data collected in this exploratory study, it is anticipated the findings may offer the community a chance to build their work.
The focus group format followed an open-ended line of questioning, incorporating the domains from the survey: computer use, ownership, access, digital game, use, ownership, Internet use and social media habits, life-logging/quantified self, privacy issues, and open questions (e.g., all participants were asked if they had any further information they wish to add). Table 2 presents the different sections of the survey, the survey items, and examples of the questions.

Table 2.
The different survey sections, items, and example questions.
3.6. Procedure
At the beginning of each scheduled focus group, all participants were briefed on the purpose, aims, and objectives of the study. All participants were informed of their right to withdraw their participation from the focus group, including their data, and that all of their information would be kept confidential. Informed consent was obtained prior to the focus groups commencing.
The interviewer explained the focus group would be recorded, and their identities anonymized, by a unique identifying number (i.e., P1, P2). The interviewer referred to each participant by their number during each recording. Concluding the focus groups, participants were thanked, and the recording was stopped.
3.7. Data Collection and Analysis
Focus group discussions lasted between 40 and 60 min in duration and were digitally audio-recorded and transcribed verbatim into Microsoft Word by a UK transcription company. Data were placed into categories as an approach to describing thematically primary, secondary, and tertiary themes [57]. Taking a thematic analysis approach facilitated the opportunity in this exploratory study to explore the generation of new knowledge [58].
Conducting a thematic analysis approach facilitates the researcher to absorb themselves and characterize the data to form an understanding [57,58]. All transcripts (n = 3) were read initially several times to get a sense of the data. Secondly, each transcript was taken separately, and read through, whilst considering the conversations in each focus group and identifying emerging themes. The author noted emerging themes throughout the documents’ margins. Thematic analysis was conducted to group the themes into overarching categories: social media, sharing information, and Wi-Fi. Secondary themes, such as platform engagement and text messaging were contained under the theme hardware, while one of the primary themes, ICT enablers, highlighted several secondary themes—platform engagement, hardware engagement, engagement/functionality, self-confidence in ICTs, and data privacy—with associated Activities of Daily Living (ADLs), such as social media, tablets, sharing information, Wi-Fi access, and 1–2 step verification process (see Table 2).
4. Findings
Data from the focus groups highlighted several primary, secondary, and tertiary themes, which were interconnected based on participants’ perceptions, their confidence using ICTs, and their usability experiences and actions. Grounded on the findings presented here, no one social media platform was the preferred choice by the participants. Participants noted their use of multiple social media platforms (e.g., Twitter, Facebook) and their ownership of a smartphone as their primary ICT device, which enabled participants to review and share information while conducting a variety of activities (e.g., mobile banking/shopping), communicating with friends/family, and searching for information.
Online banking and shopping in conjunction with social media habits and behavior were regular daily activities and accessing the Internet via a private Wi-Fi connection on their smartphone facilitated these daily activities more securely than on a public Wi-Fi connection. Participants in focus group 3 reported the importance of accessing mApps or mHealth apps via a private Wi-Fi, and not necessarily through a public Wi-Fi connection. This decision and thought process was to reduce the risk of the user/participant of their smartphone/mApp being hacked. Mobile banking Apps were used by some participants to check their account, which was preferred via a private Wi-Fi connection rather than a publicly accessible connection. Table 3 illustrates the primary themes (barriers and enablers to ICTs), several secondary themes and the tertiary themes (functionality/purpose).

Table 3.
The overarching, primary, secondary, and tertiary themes.
To illustrate the voices of Millennials in this, a series of quotes have been included under the different themes to enable readers to gain greater insight to the perceptions, behavior, and impact ICTs have on our future ageing cohort.
5. Enablers to ICT
5.1. Platform Engagement and Functionality
Content and social media are interconnected and enable users to look and search for a variety of content and information, relating to one’s interests or humor. Furthermore, some participants noted how different social media platforms were used for different forms of engagement, humor, or interest:
Participant: “[I] really like Instagram because it’s more you can look for stuff that interests you, and it gives you ideas. […] if you’re going somewhere you can search for that place and find out things about it. Facebook would be just to make my brain numb mostly and keep in touch with my friends. And then Snapchat is just for fun.”.[M, 28, Town1]
Information and news reports are easily accessible across multiple platforms throughout the day and for one participant, having confidence in the source of information is important. Sharing information can be for one’s enjoyment or related to a specific activity, such as watching TV. Different SMPs were used by participants to share or access information in different ways—one participant reported how they use multiple platforms to search specific news stories to ascertain whether the information is correct:
Participant: “[…] I think sometimes information you can read, say for newspapers, stuff like that, they’re not always correct. […] I like research a story because I’ll see something on social network and think well that’s been over-exaggerated, and then I’ll Google the story to get a better perspective on it, stuff like that.”[F, 32, Town1]
Another participant noted how he uses Twitter to keep up to date with information, in particular, news relating to television. Yet, he notes how he would prefer to use Facebook to source news and information, instead of Twitter.:
Participant: “I tend to rather read what other people are Tweeting rather than posting myself. It’s almost exclusively surrounding TV, like I’ve never really, I don’t use Twitter for like news for example, whereas you would maybe something along the lines of Facebook.”[M, 30, Town1]
One participant explained how she chooses not to share information on Facebook, which includes her immediate social circle, because she and her friends know what is going on in each other’s lives:
Participant: “We don’t share our personal things on Facebook really. We know stuff about each other but not for the rest of Facebook to see sort of thing. […] I feel like sometimes they’re attention seeking as well, and I just think that some things just need to be kept under wraps.”[F, 18, Town2]
However, a participant from Pontefract described her rationale for using SMPs, in the context of searching for humor rather than lurking or spying on friends or acquaintances:
Participant: “It’s more for looking at funny posts rather than what they’re up to and everything, because I don’t really care. But it’s more just looking for funny pictures or any pictures that they’ve shared, rather than what they’ve been doing through the day.[F, 18, Town2]
Based on the above quotes, the Millennial participants have demonstrated that they will not take informative news from one primary source. Instead, they prefer to choose and read a variety of different sources, and to make their own informed decisions. The final quote illustrates how this group of Millennials feels about sharing personal information. This focus group actively chooses not to share personal information online, because they know what is going on their friends’ lives and they do not feel the need to share with people who are not in their direct social circle:
5.2. Self-Confidence in ICTs
Participants were open to using ICTs for online banking, although one participant described how she does not review her bank statements, while another participant prefers to conduct online on her laptop rather than on her smartphone:
Participant: “Occasionally I do transfer money from my banks, from my accounts. I’ve just very recently got the one for Lloyds because I was spending money on my card online, and then not realising how much I’d spent, and then when my statement came through, I thought oh sugar.[F, 34, Town1]
Participant: I do it on my computer and that’s it.[F, 32, Town1]
Participant: I’ve got like passwords and stuff. The banks have reassured me that it’s safe.[F, 34, Town1]
Another participant described her experiences and those of friends of her mother using Facebook, because they are concerned about their information been leaked:
Participant: “I’ve had some issues with Facebook. […] we’ve got family members and friends of my mum’s that won’t go near Facebook with a bargepole because they’re so concerned that the stuff would leak to anybody. […] I’ve tried to tell them that you can change your privacy settings so that’s not the case. They just won’t.”[F, 34, Town1]
In recent years, the development of mApps to enable users’ convenient ways of conducting business may seem positive. However, as illustrated in the above quotes, mobile banking is perceived negatively, even though the first quote illustrates how the participant uses his smartphone for all activities.
5.3. Hardware Engagement
Participants used a variety of ICTs relating to their daily activities, including mApps for online banking and shopping, for ease of convenience. Although participants engaged with different devices, the purpose for this engagement varied depending upon the task the participant(s) were wanting to undertake. In the following quote, the participant describes how he primarily uses his smartphone for everything, and his laptop is used for activities when at home:
Participant: “I mainly use my smartphone for everything, just because nowadays you can use it for almost everything. I’ve got a smartphone and a laptop and an iPad that I don’t use because it’s kind of redundant now. And my laptop’s just for when I’m home because it’s got a bigger screen or if I want to do any word processing or anything. But for the majority of things, like 99%, I use my phone.”[M, 28, Town1]
Yet, another user described how her ICT use is to assist her with grocery shopping; given her health condition, she manages her online shopping accordingly:
Participant: “you say you do your shopping online, do you find though that when it comes some things are like very close to their sell by date or?[F, 34, Town1]
Participant: A little bit, but because of where I live, and because of the access to my household, because it’s steps and because I’ve got physical disability, I just find it easier to get it online. It depends what I order, like milk and stuff I won’t order it online because its rubbish dates. But a lot of my big shop I will. Like my freezer shop, anything that’s heavy goes on my online shop, and everything else I pick up myself […] I would struggle to live without online shopping and online services.”[F, 32, Town1]
5.4. Data Privacy
With the advent of Twitter, Facebook, Snapchat, Instagram, and communication tools such as WhatsApp and Viber, privacy is a continual concern for many users. Privacy issues are important and with different regulations, updates, and terminology of agreements varying across platforms, this can be troublesome and difficult for many users to understand the implications of agreeing to terms and conditions. In the following quote the participant describes what non-friends on Facebook can see of their profile, they also describe their feelings on who may or may not be viewing their profile page:
Participant: “[…] you can only see my profile picture, you can’t really look at my friends. If you’re not friends with me, you can’t see anything. But if they change something to do with that someone could see it. I wouldn’t feel, I wouldn’t really care but I wouldn’t like it just in case you don’t know who’s looking at you. But obviously if you’ve accepted them as a friend, then you know that they’re looking at you. And then it’s fine. But it’s mostly like people don’t like or you don’t want seeing certain things on your page that you wouldn’t know if you didn’t have a notification.[F, 18, Town2]
Another participant explained the concept of hacking via Facebook, and how they believe having a more open Facebook profile lends itself to being hacked more easily:
Participant: “If you keep your profile quite open then it’s probably going to be quite easy for people to hack your account or make a fake account of you and add all your friends […] My mother’s Instagram account got hacked before, and they change your name and put weird pictures up and things. So, she had to change that. But it kept on happening a couple of times and stuff.”[M, 18, Town2]
A commonality throughout the quotes was ensuring that those ‘friends’ who have been accepted on to one’s Facebook account were real people, while some ‘real people’ are concerned that a lot of their information would be accessible by non-friends. Although this participant informed those older people that they should not be concerned, because their privacy and associated data/information would be protected, in light of recent events whereby Facebook had to report to the US Congress regarding Cambridge Analytica and a breach of trust and activity by third parties, this notion and concern by some older adults proves to have been correct.
5.5. Detractors to ICT
Engagement/Functionality
ICT knowledge and experience vary across different users in society, and in more recent years, interaction and functionality have provided users with a multitude of options to access SMPs, mApps, communication tools, appointments, and verification. In the following quote, one participant describes her experiences of using an online check-in platform at her doctor’s surgery:
Participant: “[…] you can do it online but there’s never appointments […]. I don’t even know how to use it because it’s that far in advance. I can’t say I’m going to have a flare up in three weeks on Tuesday. I have to ring up that day. And depending who I get depends if I get seen. […] Yeah, you can only book it in advance. But you’ve got to sit there at eight o’clock in a morning. If I’m having a bad day, I can’t get my computer out and start messing about, because I can’t physically do it because I’m having a bad day.”[F, 32, Town1]
This participant describes one approach to accessing and booking an appointment to visit a health practitioner. In this experience, the participant found this method frustrating and not helpful, which resulted in her going to the health practitioner and physically waiting for an appointment. Another participant described how to ensure his data and privacy are maintained via his smartphone, through a two-step verification process:
Participant: “I’ve got like two-step verification every time I sign in. You would need to [..] know my password to my phone, and then my fingerprint, and then my login details, and get a text message.”[M, 28, Town1]
5.6. Intergenerational Relationships
For many older adults, using technology and associated ICTs can be a steep learning curve. One participant described her emotions and perceptions of using ICTs when assisting her parents and grandparents to understand the technological issue. In the following quote, the young participant describes a particular function or how to conduct a certain process on a piece of technology:
Participant: “Yeah grandparents, but they’re really annoying because they just don’t understand technology. […] They’re like 70s, well my dad’s side are. My mums are 50s, 60s, but still they’re like really annoying because you tell them stuff and they just don’t listen.[F, 18, Town2]
The quote above illustrates the perception and feelings of a young person who has been asked to help their elder with a technology problem. This thought can also be suggested based on the aforementioned description by a male participant, who explained the concept of hacking via Facebook, and how they believe having a more open Facebook profile lends itself to being hacked more easily.
Another aforementioned participant described her experiences and friends of her mothers’ using Facebook, and how they are concerned about their information been leaked.
However, one participant described her familial dynamic, which impacted her social media content and activity, being respectful to her mother’s beliefs and cautious of her grandfather’s online activity:
Participant: “[…] my mum’s side is very Christian and stuff. And obviously I’m not very Christian so if there’s any posts of swearing or anything I like to keep that under wraps for my dad’s side of the family rather than. Because my granddad’s a bit weird, he searches all of us on Facebook to see if we’re doing anything wrong.”[F, 18, Town2]
The above quotes illustrate how these Millennial participants are savvy when it comes to monitoring privacy on their own social media accounts but who are also acutely aware of the needs of their elders, but yet may lack the understanding or limited steps to take when dealing with one’s privacy issues. Cultural and religious beliefs also played an integral role for one participant, who noted that one of her parents would not be so pleased about content shown on her profile (Facebook).
5.7. Data Privacy
Data privacy is not solely related to social media platforms but was also noted by participants using mobile (banking) apps. While some participants reported positively on using online and mobile banking, one participant described her anxiety of mobile banking, based on her previous employment experience:
Participant: “See I don’t agree because I’ve worked in mobile banking, and I did it as a career before I had to finish work, and the amount of fraud that is committed through online banking is unreal. They kind of look at me gone out, because they’re like well […] do you not do that? I’m like this is my personal preference.”[F, 32, Town2]
Based on the above quotes, the participants described different approaches to accessing a variety of tools and functions available with 21st century technologies. In the first quote, the participant is describing how he logs into his mobile banking app.
However, some people, in particular older adults who may have age-related health conditions, may find the concept of a verification code difficult to understand, and hard remember the process(es) to undertake. However, as illustrated by this quote, Millennials now who use this form of interaction and verification will in the future be used to this type of process. However, in the future, new methods and approaches to accessing data could cause difficulty for them as older adults. Although there was no favorable social media platform, the quotes provide an insight into how the participants perceive social media, digital devices, engagement, and privacy on a day-to-day basis.
6. Discussion
Findings from the focus groups highlighted how Millennials living in two areas of England and Wales, UK, use ICTs on a day-to-day basis for various reasons, which in turn highlighted two primary themes, and 10 secondary themes.
The purpose of the Technology 4 Young Adults (T4YA) exploratory study was two-fold; firstly, to examine the perceptions, behavior, and use of ICTs by Millennials. Reflecting upon the literature and the findings of this exploratory study, it can be perceived how the notion of “digital native, digital immigrant” is continuing with the Millennial cohort, albeit from a different societal domain. At the time of Prensky [59] publishing his paper Digital Native, Digital Immigrant, social media platforms had not been developed. Yet, the differences between the two are stark, for example, digital immigrants are likely to print out a document composed on a computer to edit, while a digital native is likely to edit the document directly on the screen.
For some of the participants in the respective studies [50,53,54], smartphones and mApp usage was preferred for banking, purchasing items, and self-monitoring their health. This approach was preferred over more traditional forms of quantified self or lifelogging, such as walking into a bank or high-street shop, or on a sheet of paper. Based on the body of work presented here, when Prensky [59] published this piece of work, social media platforms, mApps, and much of the technology that is used and accessed in the 21st century was not yet developed or used. However, what is new in this body of work is the initial use and perception of ICTs by Millennials. The notions presented by Prensky are still relevant nearly two decades on. Those current digital immigrants who use contemporary technologies have limited knowledge and understanding of the skills and processes needed to keep themselves and their data safe, whilst the digital natives are keeping up to date with technology changes, using their skills and literacy levels to understand the implications of changes, in addition to the functions of various technologies. For example, the male participant living in Swansea, who described how his mother’s account was hacked. An additional example of the digital native versus the digital immigrant is the two-step verification which is used by another male participant in Pontefract. However, what is interesting about the notion of digital native versus the digital immigrant, can be seen by the female participant living in Pontefract who did not conduct mobile app banking. Her rationale for not engaging in this activity and preferring to use online banking via her laptop was from her personal experiences of working in the banking sector.
Similarly, the results from T4YA study reflect the data presented by [9,10,12,14,60]. Participants from the T4YA study used a similar but diverse range of platforms and social media activity to primarily share or receive information or content, with their friends, networks, and social groups. Communication tools such as WhatsApp and Facetime were the preferred choice of platform(s) with these participants.
Conversely, there are differences between contemporary literature and the findings presented here, culminating in the reasons why Millennials integrate ICTs and social media platforms into their lives. This is particularly so when conducting daily activities such as mobile banking and mobile shopping. However, this was not the case for one participant, who described her attempt to use an ICT appointment system connected to her doctor’s surgery. During her description, she described how she has previously tried to use the online appointment system at her general practitioner (GP) surgery, but has experienced various problems, such as logging in, or accessing/booking an appointment, which has led her to sit in the waiting room and wait for an appointment.
Secondly, participants noted their privacy concerns, which in turn illustrates the concept of digital natives. Participants were aware of their privacy settings across their respective social media platforms. This is demonstrated in one quote, by a participant who described how he helped his mum to reset her privacy settings on her social media platform because she had been hacked. This reiterates the concept by [59], whereby, the mother of the participant is the digital immigrant and her son is the digital native. One participant described their reason for not using a mApp to conduct their banking. The notion of trust was reported by the Millennial participants in the T4YA, who were primarily concerned about the use/access of public or private Wi-Fi connections. Participants commented the need to have reassurance to conduct their mobile banking activities and maintained a positive feeling about their account details and money being safe through a two-step verification process and password protection. However, this was not the case for one participant, who reported how she used to work in bank, which has led to her perception of distrust associated with mBanking apps. Although many of her friends use mBanking apps, she chooses not to. Throughout the focus groups the issue and concerns surrounding ICTs and privacy were noted by the participants, and whilst they reported to use their devices to conduct shopping and banking activities, some participants were more privacy concerned than others. The participant who reported to have concerns about mBanking apps reported using her laptop rather than her mobile phone to conduct her banking activities, whilst another participant who had a two-step verification process activated on his smartphone was confident and comfortable in conducting his mBanking activities.
Within the last 12–18 months, there has been a growth in scholarly work investigating and understanding users’ mental models associated with privacy issues within different environments. As noted by Kwasny et al. [43], defining what privacy means to users can be variable and, in some instances, it is variable based on gender; with women perceiving privacy in terms of others, and respecting privacy rights, whereas men perceive privacy from a more individual standpoint and convenience. Furthermore, the work conducted by Ray et al. [45] and Oates et al. [46] illustrates how a certain approach of qualitative data collection (diagramming exercises) offered the participants to illustrate how they perceive privacy within the context of their own lives and in society. However, neither studies offered the respective participants the opportunity to interact with different types of technology, unlike the work by Lorenzen-Huber et al. [47]. Moreover, the study by Wu et al. [40] did recruit participants across different age cohorts to contribute to understanding the mental models of privacy, while in the other studies [40,45,46], age of the participants was not one of the key primary drivers—unlike the body of work presented here, which primarily focused on individuals categorized as Millennials.
6.1. Strengths
The qualitative results presented here provide an exploratory insight into how ICTs and their associated software/devices are used on a day-to-day basis by Millennials living in two geographically (England and Wales) placed locations in the UK.
The Technology 4 Young Adults (T4YA) study explores the use of ICTs on a day-to-day basis by Millennials living in England and Wales, therefore, taking into account the lessons learned from this exploratory study, the author intends to scale up this work and recruit a larger sample size in a bid to ascertain the needs and requirements of Millennials’ use of ICTs. Similar work was conducted by [52,53], who explored the impacts of ICTs on leisure activities and intergenerational relationships, with a view to successful ageing and how age in place can be garnered through ICTs.
6.2. Limitations
Firstly, the results presented in this body of work should be viewed with caution, as they are not nationally representative of the UK or internationally and given that the T4YA study experienced several limitations, including the recruitment of participants; a key limitation of this study. Although a variety of approaches were undertaken (e.g., traditional approaches, social media, community engagement groups) to recruit greater participant numbers, these processes did not yield a great number of participants. It is difficult to understand why these approaches did not recruit a larger sample size. However, as described in the methods section, the third approach to recruitment via Facebook was the most successful, yet the return of participants was not as high as the author had expected or would have liked. With a total of eight participants, the notion of deploying an ICT survey, which was initially decided in the study design and has previously been deployed in studies [48,49,50,51,52,53], would not have yielded substantial results. Upon reflection, the survey was not available online and/or via a social media platform to increase the sample size. Given the low sample size, this should have been considered. Future studies should consider deploying an ICT survey similar to the approach undertaken by Marston and colleagues [50] in the Technology In Later Life (TILL) study in a bid to gain a quantitative insight into the impact of ICT use by Millennials who live in different geographic locations.
The project was funded by the Health and Wellbeing Priority Research Area (H&W PRA) at The Open University. As part of the funding conditions, the project had to be completed by the end of July 2017 (University financial year). In conjunction with existing commitments of the author, scheduling blocks of time to conduct two focus groups (tentatively) over a period of five days, this was difficult. Although a one-week block in June 2017 was scheduled for the focus groups to take place, which in turn enabled additional time for recruitment, this still did not yield larger participant numbers. Finally, it should be noted that given how the data were analyzed by one person, due to time constraints and the funding period, it was not possible to ask both internal and/or external colleagues to increase their workloads by acting as a second or third coder for this study.
6.3. Future Work
The author is considering submitting an amended ethics application to the University HREC in a bid to collect more quantitative data, which would add to and complement the existing qualitative data. While the author is considering expanding this work to include different sites both on a national and international level, which in turn would add a greater insight into the Millennial cohort, future studies should explore the impact of ICTs on loneliness, increasing active, and healthy ageing from the standpoint of Millennials, Generation X, and Generation Z cohorts.
Future work should encompass larger sample sizes of the Millennial cohort to gauge greater understanding, insights, and perceptions of the impact ICTs have on their day-to-day activities, relating to their social connections.
The participants recruited in this study were all white, six participants reported to be employed, with a further two participants reporting to be unemployed, which included one participant reporting that they were in receipt of welfare support; the participants’ level of education varied from college to university. Therefore, greater representation of participants from different socioeconomic and cultural backgrounds is needed in future research studies. Additional consideration should be taken to expand this work and to include intergenerational relationships from the perspective of Millennials. To date, there is a paucity of work focusing on ICT use from the perspective of intergenerational relationships. Existing work has focused on intergenerational gaming [61,62,63,64] and more recently the work by Taipale [64] focused on intergenerational relationships and ICTs. However, this is an area that needs greater exploration, specifically in the context of successful ageing and age-in-place.
Future work should explore the expectations of this cohort, because Millennials are very different to Baby Boomers, Generation X, and Generation Z, and whilst the academy is focusing its efforts on existing older adults, little attention has been taken regarding younger generations. This information would offer researchers, businesses, stakeholders, and policy makers the opportunity to plan as well as learn from previous cohorts’ (i.e., Baby Boomers) experiences of integrating unfamiliar technological developments into one’s life, be it from an individual or societal space. Research, where possible, should feed into policy strategies in an attempt to demonstrate that one size does not fit all, and to move existing debates and narratives forward [65]. Likewise, this body of work can feed into existing [66] and extended age-friendly [67] frameworks to offer researchers from various fields (e.g., HCI, health, gerontology, gerontechnology, social sciences, geography), planners, developers, policymakers, national and international organizations, and third sector charities the opportunity to build into respective age-friendly strategies appropriate to existing and future cohorts, such as the Millennials.
Given how Millennials are a cohort that use ICT very differently to our existing older adults, they will have different experiences and expectations, which could impact them if ICTs are offered to enhance social connected and physical activity, as noted by Marston and van Hoof [67]. Furthermore, this line of questioning may offer researchers an insight into how Millennials perceive ICT working for them in later life, within their home or physical space, such as their town or city, as they too grow older [67]. Therefore, future work should consider taking a transdisciplinary approach, to include the fields of gerontology, HCI/computer science, urban planning, architecture, and geography, thus, building on and expanding existing work conducted by Lorenzen-Huber and colleagues [47] as an approach to explore how ICTs and privacy issues may vary and intersect across different cohorts (e.g., Gen Z, Millennials, Gen X, and Baby Boomers), and in different scenarios and settings. Conducting a mixed methods approach of a survey, in conjunction with semi-structured focus groups, one-to-one interviews, and employing diagramming exercises similar to the work conducted by Wu and colleagues [40], and Oates et al. [46] could offer a greater understanding and propose a framework that can relate to mental models and privacy; while intersecting across different disciplines which have the potential to be impacted by ICT and privacy related issues. The body of work by Lorenzen-Huber et al. [47] states, “[I]f ubiquitous technology is to be used in a preventive fashion, we will need to better understand older adults’ perception of prevention and self-perception of need” (p. 249). With this in mind, this exploratory study is a growing body of work that sets the initial basis and understanding to the needs and perceptions of ICTs by participants categorized as Millennials.
7. Conclusions
The Technology 4 Young Adults (T4YA) is an exploratory study and has provided initial insights into the use and behavior of ICTs on a day-to-day basis by Millennials located in England and Wales, UK. Findings from the qualitative data identified how privacy is a key concern for these Millennials who were recruited for this particular study, living in two regions of the UK, especially when conducting daily activities such as mBanking and mShopping. Although some participants were very confident conducting these types of behavior, others were not, especially via a public Wi-Fi connection, and those participants preferred connecting to a private Wi-Fi connection to reduce the risk of hacking and their data being stolen. To the knowledge of the author, this is the first piece of work which explores the use, behavior, and attitudes of ICTs from the standpoint of HCI. Privacy is an area that warrants additional investigation and by taking a transdisciplinary approach in addition to combining a mixed methods data collection there is the opportunity to identify and ascertain an appropriate privacy framework that supports users based on both an individual and societal space.
Funding
We received funding from the Health and Wellbeing Priority Research Area (H&W PRA), The Open University.
Acknowledgments
I would like to thank all participants who took their time to attend the focus groups.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Office for National Statistics (ONS). Internet Users, UK: 2018. 2018. Available online: https://www.ons.gov.uk/businessindustryandtrade/itandinternetindustry/bulletins/internetusers/2018 (accessed on 21 November 2019).
- Howe, N.; Strauss, W. Millennials Rising: The Next Great Generation; Vintage: New York, NY, USA, 2000. [Google Scholar]
- Nielsen. Millennials-Breaking the Myths; Nielsen Company: New York, NY, USA; Dieman, The Netherlands, 2014. [Google Scholar]
- Vogels, E.A. Millennials Stand out for Their Technology Use, But Older Generations Also Embrace Digital Life; Pew Research Center: Washington, DC, USA, 2018; Available online: https://www.pewresearch.org/fact-tank/2019/09/09/us-generations-technology-use/ (accessed on 21 November 2019).
- Fry, R. Millennials approach Baby Boomers as America’s Largest Generation in the Electorate, 4. 2018. Available online: http://www.pewresearch.org/fact-tank/2018/04/03/millennials-approach-baby-boomers-as-largest-generation-in-u-s-electorate/ (accessed on 21 November 2019).
- Whitbourne, S.K.; Willis, S.L. (Eds.) The Baby Boomers Grow Up: Contemporary Perspectives on Midlife, 1st ed.; Routledge: Abingdon, UK, 2006. [Google Scholar]
- Pew Research Center. Millennials in Adulthood: Detached from Institions, Networked with Friends; Pew Research Center: Washington, DC, USA, 2014. [Google Scholar]
- Marston, H.R.; Hall, A.K. Gamification: Applications for Health Promotion and Health Information Technology Engagement. In Handbook of Research on Holistic Perspectives in Gamification for Clinical Practice; Novak, D., Tulu, B., Brendryen, H., Eds.; IGI Global: Pennsylvania, PA, USA, 2015. [Google Scholar] [CrossRef]
- Villanti, A.C.; Johnson, A.L.; Ilakkuvan, V.; Jacobs, M.A.; Graham, A.L.; Rath, J.M. Adults’ media use and attitudes report. J. Med. Internet Res. 2016, 182. [Google Scholar] [CrossRef]
- Ofcom. Adults’ Media Use and Attitudes Report; Ofcom: London, UK, 2018. [Google Scholar]
- Ofcom. Adults’ Media Use and Attitudes; Ofcom: London, UK, 2015. [Google Scholar]
- Smith, A.; Page, D.U.S. Smartphone Use in 2015; Pew Research Center: Washington, DC, USA, 2015; Available online: https://www.pewinternet.org/2015/04/01/us-smartphone-use-in-2015/ (accessed on 5 May 2018).
- Fox, S.; Duggan, M. Mobile Health 2012; Pew Internet: Washington, DC, USA, 2012; Available online: https://www.pewinternet.org/wp-content/uploads/sites/9/media/Files/Reports/2012/PIP_MobileHealth2012_FINAL.pdf (accessed on 21 November 2019).
- Selwyn, N. Making sense of young people, education and digital technology: The role of sociological theory. Oxf. Rev. Educ. 2012, 38, 81–96. [Google Scholar] [CrossRef]
- Facer, K.; Furlong, R. Beyond the Myth of the ‘Cyberkid’: Young People at the Margins of the Information Revolution. J. Youth Stud. 2001, 4, 451–469. [Google Scholar] [CrossRef]
- Livingstone, S.; Bober, M. UK Children Go Online: Surveying the Experiences of Young People and Their Parents; London LSE Research Online: London, UK, 2004. [Google Scholar]
- Livingstone, S.; Helsper, E. Gradations in digital inclusion: Children, young people and the digital divide. New Media Soc. 2007, 9, 671–696. [Google Scholar] [CrossRef]
- DiMaggio, P.; Hargittai, E. From the ‘Digital Divide’ to ‘Digital Inequality’: Studying Internet use as Penetration Increases; Center for Arts and Cultural Policy Studies, Princeton University: New Jersey, NJ, USA, 2011; Volume 15, pp. 1–23. [Google Scholar]
- Eszter, H.; Hinnant, A. Differences in Young Adults’ Use of the Internet. Commun. Res. 2008, 35, 602–621. [Google Scholar]
- Henderson, S.; Taylor, R. In touch: Young people, communication and technologies. Inf. Commun. Soc. 2002, 5, 494–512. [Google Scholar] [CrossRef]
- Kim, Y.; Jung, J.; Ball-Rokeach, S.J. Ethnicity, place, and Effects of ethnicity on multi-dimensional internet connectedness. Inf. Technol. People 2007, 20, 282–303. [Google Scholar] [CrossRef]
- North, S.; Snyder, I.; Bulfin, S. DIGITAL TASTES: Social class and young people’s technology use. Inf. Commun. Soc. 2008, 11, 895–911. [Google Scholar] [CrossRef]
- Tondeur, J.; Sinnaeve, I.; Van Braak, J. ICT as cultural capital: The relationship between socioeconomic status and the computer-use profile of young people. New Media Soc. 2010, 13, 151–168. [Google Scholar] [CrossRef]
- Carroll, J.; Howard, S.; Vetere, F.; Peck, J.; Murphy, J. Identity, Power And Fragmentation in Cyberspace: Technology Appropriation by Young People. In Proceedings of the 12th Australasian Conference on Information Systems, Queensland, Australia, 29 January–1 February 2001. [Google Scholar]
- Carroll, J.; Howard, S.; Vetere, F.; Peck, J.; Murphy, J. Just what do the youth of today want? Technology appopriation by young people. In Proceedings of the 35th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 10 January 2002; pp. 1777–1785. [Google Scholar]
- Tully, C.J. Growing Up in Technological Worlds: How Modern Technologies Shape the Everyday Lives of Young People. Bull. Sci. Technol. Soc. 2003, 23, 444–456. [Google Scholar] [CrossRef]
- Walsh, S.P.; White, K.M.; Cox, S.; Mcd, R. Keeping in constant touch: The predictors of young Australians’ mobile phone involvement. Comput. Hum. Behav. 2011, 27, 333–342. [Google Scholar] [CrossRef]
- Walsh, S.P.; White, K.M.; Young, R.M. Needing to connect: The effect of self and others on young people’s involvement with their mobile phones involvement with their mobile phones. Aust. J. Psychol. 2010, 62, 194–203. [Google Scholar] [CrossRef]
- Cohen, A.; Duchan, G. The usage characteristics of Twitter in the learning process. Interdiscip. J. ELearn. Learn. Objects 2012, 8, 149–163. [Google Scholar] [CrossRef][Green Version]
- Wang, S.; Hui-Yin, H.; Campbell, T.; Coster, D.C.; Longhurst, M. An investigation of middle school science teachers and students use of technology inside and outside of classrooms: Considering whether digital natives are more technology savvy than their teachers. Educ. Technol. Res. Dev. 2014, 62, 637–662. [Google Scholar] [CrossRef]
- Albarran, A.B.; Anderson, T.; Bejar, L.G.; Bussart, A.L.; Daggett, E.; Gibson, S.; Gorman, M.; Greer, D.; Guo, M.; Horst, J.L. “What Happened to our Audience?” Radio and New Technology Uses and Gratifications Among Young Adult Users. J. Radio Stud. 2007, 14, 92–101. [Google Scholar] [CrossRef]
- Hynan, A.; Murray, J.; Goldbart, J. ‘Happy and excited’: Perceptions of using digital technology and social media by young people who use augmentative and alternative communication. Child Lang. Teach. Ther. 2014, 30, 175–186. [Google Scholar] [CrossRef]
- Pelling, E.L.; White, K.M. The Theory of Planned Behavior Applied to Young People’s Use of Social Networking Web Sites. CyberPsychol. Behav. 2009, 12, 755–759. [Google Scholar] [CrossRef]
- Quan-haase, A.; Young, A.L. Uses and Gratifications of Social Media: A Comparison of Facebook and Instant Messaging. Bull. Sci. Technol. Soc. 2010, 30, 350–361. [Google Scholar] [CrossRef]
- Madell, D.E.; Muncer, S.J. Control over Social Interactions: An Important Reason for Young People’s Use of the Internet and Mobile Phones for Communication? CyberPsychol. Behav. 2007, 10, 137–140. [Google Scholar] [CrossRef]
- Best, P.; Manktelow, R.; Taylor, B. Online communication, social media and adolescent wellbeing: A systematic narrative review. Child. Youth Serv. Rev. 2014, 41, 27–36. [Google Scholar] [CrossRef]
- Kang, R.; Dabbish, L.; Fruchter, N.; Kiesler, S. “My data just goes everywhere:” user mental models of the internet and implications for privacy and security. In Proceedings of the Symposium on Usable Privacy and Security (SOUPS), Ottawa, ON, Canada, 22–24 July 2015; USENIX Association: Berkeley, CA, USA, 2015; pp. 39–52. [Google Scholar]
- Renaud, K.; Volkamer, M.; Renkema-Padmos, A. Why doesn’t Jane protect her privacy? In Privacy Enhancing Technologies PETs 2014; Lecture Notes in Computer Science; De Cristofaro, E., Murdoch, S.J., Eds.; Springer: Cham, Switzerland, 2014; Volume 8555. [Google Scholar] [CrossRef]
- Schomakers, E.M.; Lidynia, C.; Ziefle, M. Hidden within a Group of People-Mental Models of Privacy Protection. In Internet of Things, Big Data and Security; SCITEPRESS—Science and Technology Publications, lda: Setúbal, Portugal, 2018; pp. 85–94. [Google Scholar]
- Wu, J.; Zappala, D. When is a tree really a truck? Exploring mental models of encryption. In Proceedings of the Fourteenth Symposium on Usable Privacy and Security (SOUPS), Baltimore, MD, USA, 12–14 August 2018; USENIX Association: Berkeley, CA, USA, 2018. [Google Scholar]
- Price, B.A.; Stuart, A.; Calikli, G.; Mccormick, C.; Mehta, V.; Hutton, L.; Bandara, A.K.; Levine, M.; Nuseibeh, B. Logging you, Logging me: A Replicable Study of Privacy and Sharing Behaviour in Groups of Visual Lifeloggers. In Proceedings of the ACM on Interactive Mobile Wearable and Ubiquitous Technologies; ACM: New York, NY, USA, 2017; Volume 1, p. 22. [Google Scholar]
- Ryan, P.J.; Watson, R.B. Research Challenges for the Internet of Things: What Role Can OR Play? Systems 2017, 5, 24. [Google Scholar] [CrossRef]
- Kwasny, M.N.; Caine, K.E.; Rogers, W.A.; Fisk, A.D. Privacy and Technology: Folk Definitions and Perspectives. In Proceedings of the Conference on Human Factors in Computing Systems (SIGCHI), Florence, Italy, 5–10 April 2008; pp. 3291–3296. [Google Scholar] [CrossRef]
- Harris Interactive the Harris Poll®, #17: Most People Are “Privacy Pragmatists Who, While Concerned about Privacy, Will Sometimes Trade It off for Other Benefits. 2003. Available online: https://theharrispoll.com/wp-content/uploads/2017/12/Harris-Interactive-Poll-Research-Most-People-Are-Privacy-Pragmatists-Who-While-Conc-2003-03.pdf (accessed on 25 October 2019).
- Ray, H.; Wolf, F.; Kuber, R.; Aviv, A.J. “Woe is me:” Examining Older Adults’ Perceptions of Privacy. In Proceedings of the CHI Conference on Human Factors in Computing Systems Extended Abstracts (CHI’19 Extended Abstracts), Glasgow, UK, 4–9 May 2019; ACM: New York, NY, USA, 2019; p. 6. [Google Scholar] [CrossRef]
- Oates, M.; Ahmadullah, Y.; Marsh, A.; Swoopes, C.; Zhang, S.; Balebako, R.; Cranor, L.F. Turtles, locks, and bathrooms: Understanding mental models of privacy through illustration. Proc. Priv. Enhancing Technol. 2018, 4, 5–32. [Google Scholar] [CrossRef]
- Lorenzen-Huber, L.; Boutain, M.; Camp, L.J.; Shankar, K.; Connelly, K.H. Privacy, Technology, and Aging: A Proposed Framework. Ageing Int. 2011, 36, 232–252. [Google Scholar] [CrossRef]
- Technology In Later Life (TILL) project, 2015-2017, The Open University (OU), Swansea University (SU), University of Northern British Columbia (UNBC), and University of Regina, (UoR). Available online: https://healthwellbeing.kmi.open.ac.uk/related-projects/technology-in-later-life-till-project/ (accessed on 21 November 2019).
- iStoppFalls (ISF), EU project, 2011–2014. European Community (grant agreement 287361) and the Australian National Health and Medical Research council (grant #1038210). Available online: http://www.istoppfalls.eu/cms/front_content.php (accessed on 21 November 2019).
- Marston, H.R.; Genoe, R.; Freeman, S.; Kulczycki, C.; Musselwhite, C. Older Adults’ Perceptions of ICT: Main Findings from the Technology In Later Life (TILL) Study. Healthcare 2019, 7, 86. [Google Scholar] [CrossRef]
- Marston, H.R.; Kroll, M.; Fink, D.; de Rosario, H.; Gschwind, Y.J. Technology use, adoption and behavior in older adults: Results from the iStoppFalls project. Educ. Gerontol. 2016, 42, 371–387. [Google Scholar] [CrossRef]
- Marston, H.R.; Kroll, M.; Fink, D.; Poveda, R.; Gschwind, Y.J. Digital Game Technology and Older Adults. In Mobile e-Health; Human–Computer Interaction Series; Marston, H., Freeman, S., Musselwhite, C., Eds.; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Marston, H.R. Older adults as 21st century game designers. Comput. Games J. Whitsun 2012, 1, 90–102. [Google Scholar] [CrossRef]
- Rawson, K.A.; Gunstad, J.; Hughes, J.; Spitznagel, M.B.; Potter, V.; Waechter, D.; Rosneck, J. The METER: A brief, self-administered measure of health literacy. J. Gen. Intern. Med. 2010, 25, 67–71. [Google Scholar] [CrossRef]
- Norman, C.D.; Skinner, H.A. ‘eHEALS: The eHealth Literacy Scale Corresponding Author’. JMIR 2006, 8, 1–7. [Google Scholar]
- Sørensen, K.; Van den Broucke, S.; Pelikan, J.M.; Fullam, J.; Doyle, G.; Slonska, Z.; Kondilis, B.; Stoffels, V.; Osborne, R.H.; Brand, H. Measuring health literacy in populations: Illuminating the design and development process of the European Health Literacy Survey Questionnaire (HLS-EU-Q). BMC Public Health 2013, 13, 948. [Google Scholar] [CrossRef]
- Elo, S.; Kyngäs, H. The qualitative content analysis process. J. Adv. Nurs. 2008, 62, 107–115. [Google Scholar] [CrossRef]
- Braun, V.; Clarke, V. Successful Qualitative Research: A Practical Guide for Beginners, 1st ed.; SAGE: London, UK, 2013. [Google Scholar]
- Prensky, M. Digital natives, digital immigrants. Horizon 2001, 9, 1–6. [Google Scholar] [CrossRef]
- Duggan, M.; Page, D. Mobile Messaging and Social Media 2015; Pew Research Center: Washington, DC, USA, 2015. [Google Scholar]
- Voida, A.; Carpendale, S.; Greenberg, S. The individual and the group in console gaming. In Proceedings of the 2010 ACM Conference on Computer Supported Cooperative Work (CSCW’10), Savannah, GA, USA, 6–10 February 2010; p. 371. [Google Scholar] [CrossRef]
- Voida, A.; Greenberg, S. Wii all play: The console game as a computational meeting place. In Proceedings of the 27th International Conference on Human Factors in Computing Systems (CHI’09), Boston, MA, USA, 4–9 April 2009; p. 1559. [Google Scholar] [CrossRef]
- Voida, A.; Greenberg, S. Console gaming across generations: Exploring intergenerational interactions in collocated console gaming. Univers. Access Inf. Soc. 2012, 11, 45–56. [Google Scholar] [CrossRef]
- Taipale, S. Intergenerational Connections in Digital Families; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Marston, H.R.; Musselwhite, C. Ageing: Science, Technology and Healthy Living. Science and Technology Committee (Lords), UK Government Evidence for Q5a-b; Q6a-e; Q7; Q8a; INQ0010. Available online: http://data.parliament.uk/writtenevidence/committeeevidence.svc/evidencedocument/science-and-technology-committee-lords/ageing-science-technology-and-healthy-living/written/104933.html (accessed on 11 November 2019).
- World Health Organization. Global Age-Friendly Cities: A Guide; World Health Organization: Geneva, Switzerland, 2007; ISBN 9789241547307. [Google Scholar]
- Marston, H.R.; van Hoof, J. “Who Doesn’t Think about Technology When Designing Urban Environments for Older People?” A Case Study Approach to a Proposed Extension of the WHO’s Age-Friendly Cities Model. Int. J. Environ. Res. Public Health 2019, 16, 3525. [Google Scholar] [CrossRef] [PubMed]
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).