Abstract
Although the electronic health (e-health) cloud computing system is a promising innovation, its adoption in the healthcare industry has been slow. This study investigated the adoption of e-health cloud computing systems in the healthcare industry and considered security functions, management, cloud service delivery, and cloud software for e-health cloud computing systems. Although numerous studies have determined factors affecting e-health cloud computing systems, few comprehensive reviews of factors and their relations have been conducted. Therefore, this study investigated the relations between the factors affecting e-health cloud computing systems by using a multiple criteria decision-making technique, in which decision-making trial and evaluation laboratory (DEMATEL), DANP (DEMATEL-based Analytic Network Process), and modified VIKOR (VlseKriterijumska Optimizacija I Kompromisno Resenje) approaches were combined. The intended level of adoption of an e-health cloud computing system could be determined by using the proposed approach. The results of a case study performed on the Taiwanese healthcare industry indicated that the cloud management function must be primarily enhanced and that cost effectiveness is the most significant factor in the adoption of e-health cloud computing. This result is valuable for allocating resources to decrease performance gaps in the Taiwanese healthcare industry.
1. Introduction
Electronic health (e-health) cloud computing is a progressive technology that can revolutionize the healthcare industry. Cloud computing has numerous advantages such as high speed, flexibility, scalability, fast deployment, resource sharing, energy saving, and cost-effective infrastructure, which can considerably influence daily life [1]. Computing facilities and resources can be established conveniently in any location. The healthcare industry is focused on sustainable development, and future healthcare models are expected to be data centric. Cloud computing can facilitate coordination, communication, and collaboration between various healthcare systems [2].
The rapid development of information and technology has resulted in advances in numerous healthcare applications such as hospital information systems, medical diagnostic systems, electronic health records, and healthcare monitoring [3,4]. Improving the efficiency and accuracy of healthcare information systems requires critical decision-making. Cloud computing is a novel technology that combines storage resource assignment and computing technology. The market of cloud computing is developing steadily and is prospective to be valued at approximately US$225 billion by 2020 [5]. Companies such as Aetna and IBM’s Active Health Management subsidiary have established novel clinical data management systems according to the structure of cloud computing [6]. The aim of the collaborative care solution is to provide controlled access to various types of clinical patient data from various sources, such as medication records, lab data, and claims as well as electronic medical records [1,7,8]. Microsoft and Google services such as Microsoft HealthVault and Google Health focus on novel services for storing medical records [7,8].
E-health cloud computing systems are preferable to e-health systems because of their agility and portability, and because they can be applied in remote areas with limited access to general medical services. E-health cloud computing systems are a low-cost method for transporting health services. Although numerous studies have been conducted on e-health cloud computing systems globally, the effectiveness of e-health cloud computing systems remains widely debated [8,9,10,11]. Nevertheless, e-health cloud computing system applications may revolutionize the healthcare industry in the future. Marcolino et al. [12] studied this efficiency of e-health cloud computing systems for managing illnesses and revealed mixed results. However, e-health cloud computing systems could be used to develop complementary devices for handling health problems in the future. E-health cloud computing systems can decrease healthcare service costs [13], and they can augment healthcare services by sending health-associated data to various departments [14,15]. Moreover, e-health cloud computing systems can be used to develop supportive devices that provide answers to health questions.
Studies on e-health cloud computing systems have focused on the following aspects: (1) evolving novel applications associated to fitness and health; (2) technology adoption of e-health cloud computing systems; and (3) clinical trials of e-health cloud computing system adoption [13,16,17,18]. However, few studies have focused on developing a context for evaluating this adoption of e-health cloud computing systems. Because of the widespread application of the cloud services and internet, the decision to adopt e-health cloud computing systems is critical.
Furthermore, cloud computing services are in the conceptualization phases at most medical organizations in Taiwan. Transitioning from conventional services to a cloud computing models is challenging for the healthcare industry. Therefore, the development of a systematic estimation model for medical institutions would promote the design systems of cloud computing and the prioritization and ranking of administration factors. Such an estimation model could also provide support to managers in administrative tasks, improve the effectiveness of cloud computing systems, indicate a suitable assignment of limited resources, and avoid needless resource waste and replacement.
Currently, although the healthcare industry is aggressively implementing cloud computing applications [19,20,21], a proper structure to evaluate the effectiveness of their adoption in the marketplace has received little attention. To satisfy these research gaps, this paper proposed a combined multicriteria decision making (MCDM) model to build an influential relations map (IRM) that combines DEMATEL (decision-making trial and evaluation laboratory) and DANP (DEMATEL-based Analytic Network Process) to investigate the influence weights of factors. The weights of the modified VIKOR (VlseKriterijumska Optimizacija I Kompromisno Resenje) technique were considered to integrate and estimate the factors of these gaps (financial performance & business performance) and the gaps were reduced based on IRM for evaluating cloud e-health system adoption. The purpose of this study is not to offer a multifaceted MCDM structure relating multiplex mathematical operations and functions, but, according to the empirical outcomes, these administrators can adopt approaches to successfully devote limited resources on suitable events for evaluating the model of cloud e-health system adoption.
The contributions of this paper are as follows: The adoption of e-health cloud computing systems is considered a decision-making concern with interaction and dependence factors. Interviews with experts and literature reviews were performed to generate 12 factors and four dimensions of e-health cloud computing functions to evaluate the e-health cloud computing system adoption for the healthcare industry. Next, we combined DEMATEL, DANP, and modified VIKOR to enhance an e-health cloud computing system adoption assessment model, which prioritizes the influence weights of e-health cloud computing function dimensions and factors and determines the obstacles during the adoption of e-health cloud computing systems. This proposed techniques not only address the dependence and interaction of factors but also provide valued data to establish an effect and cause map for strategy formation. Finally, the investigation of the assessment outcomes provides guidance to healthcare managers for detecting crucial factors influencing weights or gap assessments and provides the optimal method to enhance the existing adoption of e-health cloud computing systems.
This research is systematized as follows: Section 2 states these corresponding literatures relevant to the approaches and applications of e-health cloud computing system selection. Section 3 shows the planned approaches. It clarifies the numerical instance of the illustrated process in Section 4. Finally, it concludes the paper in Section 5.
2. Literature Review
2.1. Applications in E-Health Cloud Computing Systems
Cloud computing which is applied for enhancing patient care is called e-health cloud computing, and it offers chances to address some limitations of hospital information systems [22,23]. The ability to access medical records anywhere and anytime can considerably improve healthcare services. Cloud computing can be used to access medical records and therefore improve healthcare facilitates. Because cloud computing is frequently operated in a shared and open environment, it is susceptible to malicious data thefts, attacks, and information losses. Security concerns are detrimental to the implementation of cloud computing systems in the healthcare industry. Healthcare specialists are distrustful of cloud computing because hackers may be able to access patient medical records. Thus, security and privacy concerns are valid [22,23]. Cloud computing service providers should address security concerns to improve trust among healthcare providers and patients [24,25]. A review verified that a growing number of healthcare administrations plan to implement cloud computing services to exploit cloud computing [26]. However, as mentioned previously, the adoption of cloud computing technology has presented numerous applications for the healthcare industry, principally with respect to their management (e.g., information integration, convenient information sharing, and cost effectiveness), service delivery (e.g., testing and debugging, software research and development, and system stability), security (e.g., confidentiality, data integrity, and access control), and software (e.g., software convenience, cloud-based medical image exchange, and software scalability) [18,24,25,27]. The healthcare industry is highly complex because of the operational difficulties of providing medical services [25,27,28]. Healthcare includes dissimilar stakeholders with various interests and industry-specific features [27,29]. Hence, cloud computing in healthcare is multifaceted, and its application via healthcare institutions can be ensured only under certain requirements [19]. When implementing cloud computing systems (i.e., making decisions about e-health cloud computing system adoption), numerous determinant problems associated with these conditions should be considered. An implementation decision without critical thought on the determining factors can not only hinder the productive application of cloud computing in the healthcare industry but also present problems. For example, an uninformed cloud computing adoption decision via a huge UK hospital did not provide the expected benefits and resulted in a financial deficit of £8.6 million and the temporary disruption of medical services [30,31].
E-health cloud computing systems are revolutionizing healthcare by providing users with novel protocols, which were not possible a decade ago. Innovative e-health cloud computing systems will finally become the novel cornerstone of modern health systems. Ambarkar and Shekokar [32] analyzed the security measures incorporated in the healthcare system. Farahani et al. [33] presented the benefits of implementing e-health cloud computing systems to enhance diagnostics in various applications. Cloud computing devices provide physicians with data-driven treatment plans to improve effective recovery. Abouelmehdi et al. [34] used big data to drive e-health cloud computing systems, personal health management, and knowledge discovery. They investigated the advantages and disadvantages of e-health cloud computing systems with regard to privacy and security technologies. Liao and Qiu [24] indicated that healthcare cloud management, cloud service delivery, and cloud software issues can influence the evaluation of cloud computing systems for healthcare industry. They proposed the practical application of a cloud computing-based approach for addressing healthcare issues. Hathaliya and Tanwar [23] offered a detailed literature review and investigation on the privacy and security problems in healthcare. Similarly, Semantha et al. [35] studied the current literature on privacy design in the healthcare industry and classified the limitations of the designs in the healthcare sector. They also provided crucial development directions for future study.
After literature review, we discuss with administrators and experts in depth on the factors influencing the cloud computing system adoption in Taiwan’s healthcare industry. We summarized the factors which including cloud management, cloud service delivery, cloud security, and cloud software as our decision-making model. We discussed the detailed information in Section 2.2.
2.2. The Factors Influencing the Cloud Computing System Adoption
2.2.1. Cloud Management
The adoption of cloud computing is partly driven by management concerns including information integration, information sharing, and cost effectiveness [26]. Implementing a system of cloud computing can cause considerable savings; the more expenditures a system saves with cloud computing, the greater is the effectiveness of the system—such as, when using software as a service—companies usually purchase version updates and pay monthly software fees based on the numeral of users, thereby decreasing information technology expenses and information integration. Therefore, if healthcare industry pays license fees by monthly, they could extend the of product lifecycle of software without bearing the risks of product redundancy or being bound via the models of traditional software licensing. Furthermore, service providers supply unlimited client services, pay-per-use, and dynamically adjustable via saving consumers the expenses, building virtual resource pools of maintaining, adopting, designing, and integrating infrastructures of customization. The services of the cloud also remove the expenditures related to buying data storage devices, providing management and maintenance, enabling convenient information sharing, and purchasing other hardware. Without cloud services, customers would need to solve these management problems [24,25]. Therefore, information integration, convenient information sharing, and cost effectiveness are serious concerns in the assessment of cloud management functions for e-health cloud computing systems.
2.2.2. Cloud Service Delivery
Steady high-quality systems of cloud computing yield trustworthy services. Moreover, testing and debugging, software research and development, and system stability are closely related with system security owing to the degree to which system engineers stress that information security is related to the probability of realizing the security of data storage and system stability. As the service systems of healthcare cloud computing operate on the structures of network, they are weak to viruses, information theft, and hackers [24,25]. Therefore, testing and debugging, software research and development, and system stability are serious factors in the evaluation of cloud service delivery for e-health cloud computing systems.
2.2.3. Cloud Security
We focused on three critical factors, namely confidentiality, data integrity, and access control. Delegating control of data to the cloud enhances the data compromise risk, owing to the data becoming reachable to numerous parties. The increase in the number of devices, applications, and parties increases the risk of data compromise. Integrity ensures the health data offered to any entity or captured via a system are consistent and accurate through the intended information and not modified in any method [36,37,38,39,40,41,42,43,44]. E-health cloud requires high reliability. E-health cloud data and services must be no error. This control policy is set such that only an authorized practitioner or a trusted third party can obtain the patient’s medical records. Numerous resolutions have been presented to deal with these access and control security worries. Attribute-based and role-based access controls are the most prevalent models for healthcare cloud computing.
2.2.4. Cloud Software
The software function forms the crux of all services in e-health cloud computing systems. In the healthcare industry, convenient software, cloud-based medical image exchange, and software scalability are mostly critical. Owing to software convenience, software design and software scalability should satisfy the demands of the environment of healthcare, healthcare personnel and patients should be able to configure and regulate the functions of systems; when such demands are satisfied, the resulting cloud computing systems of healthcare can yield high user fulfillment [24,25]. Cloud-based medical image exchange is a critical requirement because this function may focus on emergency care. Hence, the information systems of health should include the structures that enable smooth and rapid transmission of medical information and classification of the medical data or images of critical patients, thus enabling staff to efficiently flag emergencies.
Based on literature review, expert opinions, and in-depth discussions with administrators of the healthcare industry and researchers, we summarized the cloud computing functions and security of e-health cloud computing systems as having the following four aspects: cloud management, cloud service delivery, cloud security, and cloud software. Table 1 displays a comprehensive report of these elements. Cloud management is affected by three factors, namely information integration, convenient information sharing, and cost effectiveness. Cloud service delivery is affected by three factors, namely testing and debugging, software research and development, and system stability. Cloud security is affected by three factors, namely confidentiality, data integrity, and access control. Cloud software is affected by three factors, namely software convenience, cloud computing medical image exchange, and software scalability. This study investigated the relationships between various elements and determined the significance of the factors to provide guidance on attaining the desired financial and business performance.

Table 1.
Explanation of dimensions and factors.
3. Methodology
In this research, we concisely illustrate the presented integrated MCDM model. Due to prior practice, this model is determined to be a suitable technique for estimating a strategy to ensure success when adopting an e-health cloud computing system. The present study integrated cloud management, cloud service delivery, cloud security, and cloud software. The combined model was used to address decision-making and assessment for e-health cloud computing system adoption problems. All infrastructural and assessment factors of e-health cloud computing systems and their relations with financial and business performance were investigated. The object of this research is to combine the model to provide ranking and selection, as well as enhanced performance. Finally, the main enhancement of our integrated model is its managerial ability in selection and enhancement; thus, this model can support healthcare managers to enhance their decision-making. This integrated model is separated into three parts [45,46,47,48,49,50]: (1) DEMATEL is used to build a structure with an influence relationship map (IRM) based on the factors/dimensions (the first survey: DEMATEL questionnaire). (2) DEMATEL-based ANP (DANP) is used to attain these influence weights (from the DEMATEL method and outcomes). (3) This modified VIKOR approach is applied to empirically estimate gap performance (financial and business performance) in the healthcare industry, which occur during e-health cloud computing system adoption (the second survey: performance questionnaire). Hence, this integrated method can help managers to define how to evaluate the adoption of an e-health cloud computing system, in order to achieve a good fit outcome, which is followed by IRM for each alternative. The development of the combined model is shown in Figure 1.
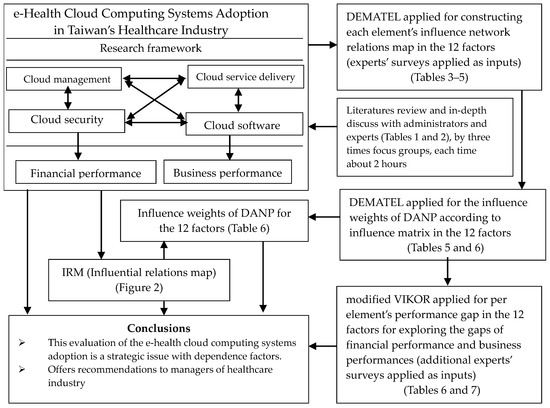
Figure 1.
Modeling procedures of our proposed combined MCDM model.
3.1. Data Collection
Through this literature review and 15 experts’ opinions with conducting focus groups at least three times, each time we spent about 2 h (we discussed the topic, the factors of influence on the e-health cloud computing systems adoption via literature review and discussed with administrators and experts in depth regarding the factors of influence in Taiwan’s healthcare industry in the real world). Based on the consensus via focus groups, we present four dimensions and confirm 12 factors of influence on the e-health cloud computing systems adoption. After that, we built up two sets of surveys of DEMATEL and performance questionnaires (see Appendix A and Appendix C stages). For the DEMATEL questionnaire, we used the five Likert scales, which are settled the scale through “very high influence (4)” to “lack of influence (0)”. In addition, for the performance questionnaire, we used the 11 Likert scales in which the scored responses range from 0 to 10: totally dissatisfied (0) to extremely satisfied (10). Finally, the two set of surveys of DEMATEL and performance questionnaires which are confirmed by the 15 experts. The study used the proposed approach in the healthcare industry in Taiwan as a case research. All data were collected from the 15 experts. To ensure the reliability of these experts, this research established personal interviews face-to-face to make sure that the definitions of the questions inquired could be realized. These experts are researchers and those at the upper administration level, with an average working experience in the healthcare industry of more than 10 years, and the related information of the specialists is shown as Table 2. They agreed that all elements are crucial and comprehensive, showing that the elements need to be implemented into this research. For the consistency (in consensus, see Table 3 in Note 1), the statistical significance confidence is 95.381%, in consensus, that is greater than 95%, and this error gap less than 5% is 4.619% in this study. As this consistency ratio is less than the significance value, the threshold is usually set to 5%—it can be determined that the 15 specialists’ replies have achieved a suitable consensus and consistency.

Table 2.
The information of experts.

Table 3.
Initial influence matrix for each factor.
3.2. DEMATEL for Assembling an Evalution Structure through IRM
The DEMATEL technique was established via the Battelle Memorial Institute of Geneva from 1972 for the Science and Human Affairs Program. This objective was to investigate difficult and multifaceted real-life issues—for example, energy, ethnicity related problems, and environmental protections—and detect practical resolutions via a hierarchical construction [51,52]. This technique can effectually integrate professional domain knowhow and make clear the causal relations among influence elements. Moreover, regarding the causal relations between factors into an easy to understand systemic pattern, this technique uses a mathematical theory to calculate the degrees of indirect and direct influences per factor/dimension [45,46,47,48,49,50]. The most characteristic factor of the DEMATEL technique is its ability to demonstrate the relations among groups and acquire the key aspects of the demonstrative factors. In addition, DEMATEL has been effectively applied in numerous applications, for example, RFID adoption, legal AI Bot implementation, strategic orientations for promoting hotel services, and estimating sustainable development performance [48,53,54,55].
The DEMATEL method comprises four main stages: (1) using the direct relationship matrix for constructing this research framework; (2) acquiring a normalized matrix of direct relationship; (3) obtaining a matrix of full influence relationship; and (4) creating an influence relationship map (see Appendix A).
3.3. DANP Technique for Derviving Influence Weights
DANP is used to determine this relationship matrix of full influence to acquire these interdependent relationship weights among the factors/dimensions via applying the procedures and conceptions of ANP [56]. The traditional approach that is using DEMATEL and ANP needs to apply both surveys. This survey of DEMATEL is primarily applied to decide the mutual influences between estimation attributes and set up a hierarchic structure; then, the ANP survey is used to acquire the weights of the factors and estimation outcomes. However, the DANP technique only needs the survey of DEMATEL [57]. This DANP’s weight value indicates the ratio of the factors/dimensions, as well as their influence degree on the full model, which is simultaneously according to the degrees of received and given effects in a circumstance. The DANP technique comprises three main stages: (1) emerging an unweighted super-matrix; (2) creating a super-matrix weight; and (3) assembling the supermatrix weight (see Appendix B).
3.4. Modified VIKOR Technique
The modified VIKOR technique was developed via Opricovic and Tzeng [58,59] as a technique of counting the factor score as the approach for the order of preference via similarity to an ideal solution (TOPSIS) was not available. These TOPSIS and VIKOR techniques are ranking approaches applied in MCDM. Both approaches utilize the conception of compromise to deal with the disadvantages and advantages of the estimation elements, and both rank the alternatives according to the nearness of a limited number of estimated elements to the ideal resolution.
The TOPSIS technique ranks all resolutions via the distance through the negative ideal resolution and closeness to the positive ideal resolution. Nevertheless, as estimating two factors in cases when the scenarios fall diagonally on the plane, the TOPSIS technique cannot really reflect per scenario’s closeness to the ideal resolution, and the most optimal resolution cannot be determined. To avoid the defect in the TOPSIS technique, the modified VIKOR technique applies the aspired value and worst level to compare the alternatives estimation scores and detect an ideal resolution. Based on the positive ideal and negative ideal, as determined by a preference for remaining near the positive ideal point, that is the fundamental idea of conventional thought. This conception of gap estimates the nearness positive ideal point [45,46,47,48,49,50]. A modified VIKOR has been effectively applied in numerous applications, for example, B2B commerce implementation, RFID adoption, and Legal AI Bot implementation [53,54].
Modified VIKOR comprises these next stages: (1) invent the worst and the best values in evaluation factors. It shifts from selection and ranking as defining the best methods to performance enhancement of present approaches according to IRM; (2) analyze the mean of group utility and maximal regret; and (3) acquire the comprehensive indicator and sort out the outcomes (see Appendix C).
4. Case Analysis
In this study, we performed a case on the healthcare industry in Taiwan. This MCDM model was used to investigate the interdependence and feedback between the factors affecting performance when adopting an e-health cloud computing system for the healthcare industry in Taiwan. The results can help managers and decision-makers and strongly affects e-health cloud computing system adoption, particularly when healthcare resources are limited. The outcomes of the empirical case are presented along with related discussions.
4.1. Analytical Results
The DEMATEL assessment structure was developed for the e-health cloud computing systems with four dimensions and 12 factors. The factors and dimensions for the total influence matrix, as stated in Table 3 and Table 4, were attained through expert surveys. Experts’ views on the four dimensions were collected, and the relations between these spaces of impact associated with the other dimensions were determined (Table 4).

Table 4.
Summation of effects on dimensions and total influence matrix.
Based on the summation of row and column aggregations means that any of the factor x effects on all other factors, named , and x is influenced by all other factors, named . For the total influence prominence , the cloud management (A1) exhibited the most critical effect on the strength of the relationships. By contrast, cloud software (A4) exhibited the weakest effect. Based on this net influence , cloud service delivery (A2) exhibited the most direct effects among the dimensions, and cloud security (A3) was the most vulnerable.
Table 4 displays the influence relationship factors, and Table 5 illustrates the relationships between the degrees of direct and indirect influences as well as comparisons with other factors. Information integration (S1) was the most critical factor for intelligent administration; software scalability (S12) had the weakest effect on other factors. According to Table 5, software research and development (S5) had the strongest influence on other factors, and cost effectiveness (S3) was the most influenced by other factors.

Table 5.
Sum of effects of each factor, weight and ranking.
By using the proposed DEMATEL model, this study determined the relationship between numerous factors and dimensions through IRM. Figure 2 illustrates that the cloud service delivery function (A2) influenced other aspects, namely, the cloud software (A4), cloud security (A3), and cloud management (A1), whereas cloud service delivery (A2) had the strongest effect on other dimensions.
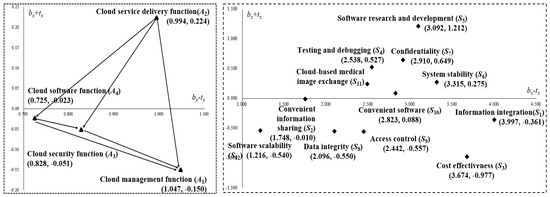
Figure 2.
The influential relationship map (IRM) for dimension and factor separately.
Figure 2 displays the IRM of the 12 factors in four dimensions. Based on the cause-and-effect relation, Quadrant I in the map covers the main factors (S5, S7, S4, S6, S11, and S10) to be determined. These factors are critical for various approaches for the adoption of an e-health cloud computing system in the healthcare industry, and cover the driving factors (S2, S1, S12, S8, S9, and S3), which only affect other factors in Quadrant II. Therefore, regarding the relationship of factors, the most influenced factors are S5, S7, S4, S6, S11, S10, S2, S1, S12, S8, S9, and S3. Regarding software research and development (S5), the adoption of an e-health cloud computing system indicates operational applications in the healthcare industry.
DANP was used to obtain the influence weights of the individual factors, as illustrated in Table 5 and Table 6. The outcomes demonstrated cost effectiveness (S3), information integration (S1), and access control (S9) are the critical factors for improving adoption. Furthermore, the weights of influence are combined with the DEMATEL technique to explain the sequence of decreasing these gaps, as determined through the IRM and modified VIKOR.

Table 6.
Gap assessment of e-health cloud computing systems adoption via modified VIKOR.
This study assessed e-health cloud computing system adoption, and investigated the effect of its adoption on financial (&1) and business performance (&2). Furthermore, the modified VIKOR approach was used to estimate and improve reliance. Table 6 illustrates the gap estimation for adopting an e-health cloud computing system through the modified VIKOR approach. Managers can distinguish questions based on the composite index according to holistic or individual dimensions for using these outcomes (see the Table 6).
By applying the guidelines to these dimensions and factors, these gaps of performances can be prioritized and determined to achieve the desired level. Regarding financial performance (&1), cost effectiveness (S3) exhibited a maximum gap of 0.553 and was the initial factor to be enhanced, followed by system stability (S6) and software scalability (S12). Among all factors for financial performance (&1), administrators should focus on cost effectiveness (S3). Regarding business performance (&2), cost effectiveness (S3) exhibited the highest gap of 0.513 and was the main factor to be enhanced, followed by information integration (S1) and system stability (S6). For business performance (&2), administrators should focus on cost effectiveness (S3). These results indicated that a sequence array, from the most to the least significant, is required for all the factors to attain the desired level.
Improvement priorities can also be used in separate dimensions—for example, regarding financial performance (&1). Within cloud management (A1), the gap values are prioritized as follows: cost effectiveness (S3), information integration (S1), and convenient information sharing (S2). Within cloud service delivery (A2), the gap values are prioritized as follows: system stability (S6), testing and debugging (S4), and software research and development (S5). Regarding cloud security (A3), enhancement priorities are ordered as follows: confidentiality (S7), access control (S9), and data integrity (S8). Regarding cloud software (A4), enhancement priorities are ordered as follows: software scalability (S12), cloud-based medical image exchange (S11), and software convenience (S10). Regarding business performance (&2), enhancement priorities are ordered as follows: (S3), (S1), and (S2) within for cloud management (A1); (S6), (S5), and (S4) for cloud service delivery (A2); (S9), (S7), and (S8) for cloud security (A3); and (S12), (S11), and (S10) for cloud software (A4).
4.2. Discussion
Most approaches cannot determine the multifaceted interrelationships between the numerous dimensions and factors that influence the adoption of an e-health cloud computing system. This study distinguished the relationships between various dimensions and factors. Based on the matrix of total influence, cloud service delivery (A2) exhibited the greatest influence. According to this net effect, cloud service delivery (A2) also exhibited the strongest net effect on the other aspects. Managers in the healthcare industry should enhance cloud service delivery (A2) first, followed by cloud software (A4), cloud security (A3), and cloud management (A1) when enhancing system adoption.
The proposed framework involves cloud management (A1), cloud service delivery (A2), cloud security (A3), and cloud software (A4) based on the recommendations of experts regarding the factors affecting system adoption performance. According to recommendations by specialists in the healthcare industry, the recommended structure relates cloud management functions, cloud service delivery function, cloud security function, and cloud software function (A4) dimensions to investigate these factors impacting e-health cloud computing system adoption performance (see Figure 2).
These empirical outcomes also indicated the premeditated factors within the separate dimensions. Table 7 summarizes the sequence of influence factors in the separate dimensions according to the outcomes of DEMATEL and modified VIKOR. For cloud service delivery function (A2), software research and development (S5) were the most affected factors and required initial enhancement, followed by testing and debugging (S4), and system stability (S6). After using the gap values, as presented via the panel of specialists, crucial enhancement designs were comprehensively and uniquely considered in terms of both holistic and separate dimensions. For managers in the healthcare industry in Taiwan, understanding the improvement priorities for e-health cloud computing system adoption is critical. The results displayed in Table 7 indicate enhancement sequences that can be implemented to achieve the intended financial and business performance. For example, to decrease the performance gaps among the existing and aspired levels of financial performance, the sequence for enhancement is cloud management (A1), cloud software (A4), cloud service delivery (A2), and cloud security (A3). However, managers in the healthcare industry should be cautious because, when using the MCDM model, the significance of the 12 factors might change according to circumstances. Thus, administrators must identify gaps before making decisions.

Table 7.
Sequence of enhancement priority for the strategy.
5. Conclusions
This study proposed a MCDM technique in which DEMATEL, DANP, and the modified VIKOR approach were combined to estimate the interdependence and feedback between numerous features when adopting an e-health cloud computing system in the healthcare industry. Because the various healthcare departments have limited resources, in the suggested structure, cloud management, cloud service delivery, cloud security, and cloud software should be incorporated. According to these outcomes, cloud service delivery exhibited the highest net influence of 0.224, and thus should be enhanced initially. Cost effectiveness, which exhibited the maximum global weight of 0.144, is the most critical feature for improving system adoption performance in the healthcare industry in Taiwan. When scheduling the adoption of a cloud computing system, companies typically estimate their return on investment (ROI) to determine whether an adoption plan is suitable. Companies generally avoid adopting a system if the cost does not justify the expenses. Although healthcare institutions are not focused on profit, they must demonstrate that their decision-making procedures are similar to those of for-profit organizations regarding the assessment and planning of a service system for e-health cloud computing. Decision-makers need to carefully determine the cost savings that cloud computing services can yield. The costs of implementing an e-health cloud computing service system can be avoided if the ROI is not high. The gap values of total performance represent the ranges for enhancement, which are 0.382 for financial performance (&1) and 0.361 for business performance (&2). Cloud management (A1) exhibited the largest gap (0.420) in financial performance (&1) and the largest gap (0.425) in business performance (&2). Thus, cloud management should be enhanced first if managers hope to achieve the anticipated performance. Moreover, the results suggested that managers can select a suitable sequence of factors to enhance system adoption.
The proposed method has several limitations. Firstly, the sample size in this study was limited; thus, a higher number of samples should be considered to obtain complementary explanatory abilities for multifaceted and specialized assessment research. Next, the outcomes obtained in this study should be verified with more samples. MCDM helps managers to understand the elements required to improve performance assessment. Finally, this is a case study in Taiwan that may not be applicable in other countries with different health systems and legislation. Future studies can consider additional multiple criteria approaches (for example, the best–worst method and outranking methods) to evaluate the influence of the weights of e-health cloud computing system adoption estimation. Finally, numerous approaches, such as longitudinal studies, can be used to determine the factors related to the adoption of an e-health cloud computing system in future research.
Author Contributions
Conceptualization, M.-T.L. & S.-C.C. & T.-H.P. & C.-S.C.; Methodology, M.-T.L.; Formal analysis, M.-T.L.; Investigation, M.-T.L.; Writing—original draft, M.-T.L.; Writing—review & editing, M.-T.L.; visualization, M.-T.L.; supervision, M.-T.L.; project administration, S.-C.C. & T.-H.P. & C.-S.C.; funding acquisition, S.-C.C. & T.-H.P. & C.-S.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. DEMATEL Technique
The technique of DEMATEL has four stages, as follows:
Appendix A.1. Stage 1: Using the Direct-Relation Matrix for Constructing the Research Framework
As the (z) factors in an estimation structure have been established, this regular influence degree scale is settled (scale through “very high influence (4)” to “lack of influence (0)”). These measured degrees of effect among the dimensions or factors are applied via natural language. The regular of specialists apply a regular scale to demonstrate the direct influence degree through factor/dimension x on factor/dimension y in matrix (in which ; otherwise, , and is the amount of specialists). Lastly, the mean is applied to assimilate a major matrix of the direct relationship, which demonstrate the actual practices of the experts.
Appendix A.2. Stage 2: Acquiring a Normalized Matrix of the Direct Relationship
A normalized major direct relationship matrix P is reached through normalizing this major direct relationship matrix U uses Equations (A1) and (A2) where all the matrix O diagonal terms are 0, and the maximum summation of each column and row is 1:
Appendix A.3. Stage 3: Obtaining a Matrix of Full Influence Relationship
This matrix O has a full influence relationship, which is obtained by Equation (A3). It is able to provide assurances of convergent determinations to the matrix reversal in a method similar to capturing the matrix of a Markov chain. Therefore, the full influence relationship matrix O can be obtained from the values in the normalized matrix P of the direct relationship, and L is the individuality matrix, as follows:
The matrix O of the full influence relationship can be obtained by Ok and OV is based on a hierarchical framework, as shown by Equations (A4) and (A5), respectively.
Appendix A.4. Stage 4: Creating an Influence Relationship Map
By summing the separate rows and columns of this full influence relationship matrix P, we obtain the summation of the vectors by all rows and columns, as shown below:
As (i.e., the summation of row and column aggregations means that any of the factor x effects on all other factors, named , and x is influenced by all other factors, named ), this value illustrates the total influences given and received via enabler factor (i.e., representing the degree of effect that the enabler factor plays in the entire system, also called “prominence”). Moreover, the value indicates the clear influence of enabler on this entire method. If is a positive value, then belongs to the net cause group. Otherwise, if is a negative value, then belongs to the net effect group. Hence, via drawing the dataset of the (,), we obtain the IRM of the dimensions and factors.
Appendix B. DANP Technique
This DANP technique contains three key stages, as follows:
Appendix B.1. Stage 1: Emerging an Unweighted Super-Matrix
The emerging supermatrix is unweighted, and can be separated into two stages: the initial act normalizes matrix with the full influence relationship to attain the normalized full-influence relationship matrix , while the second act transposes the normalized matrix full influence relationship to attain .
This normalized matrix of the full influence relationship (Equation (A9)) is attained via separately normalizing the rows of the dimensions in the full relationship matrix (Equation (A8)), and the summation of the separate rows equals the number of dimensions:
, as a normalized instance, determines how to normalize activities for the fundamental concept, as shown in Equations (A9) and (A10):
Secondly, the normalized matrix of the full-influence relationship is altered to obtain the super-matrix which is unweighted, as shown in Equation (A11):
Appendix B.2. Stage 2: Creating a Super-Matrix Weight
The super-matrix weight is able to be separated into two stages: the initial act normalizes the matrix of the full influence relationship (Equation (A5)), and transposes it to obtain the normalized matrix of the full influence relationship, as shown in Equations (A12) and (A13). Then, the normalized matrix of the full influence relationship is multiplied by the super-matrix unweighted , which can determine weighted super-matrix , as shown in Equation (A14):
Appendix B.3. Stage 3: Assembling the Supermatrix Weight
This paper applies the Makov chain procedure of ANP to assemble the super-matrix weight via itself several times till the supermatrix was converted into a steady supermatrix with an adequately large power . Therefore, the influence ratio levels of the factors are attained by . Lastly, we acquire a series of influence weights for factors and dimensions .
Appendix C. Modified VIKOR Technique
We define the modified VIKOR technique, as follows.
Stage 1: indicates the levels and in quality factor assessment. The level denotes the positive-ideal point, which is the best score for factor j; and denotes the negative-ideal point, which is the worst score for factor j. represents the performance score of k alternative for j factor. The enhancement of the modified VIKOR technique is initiated by the next procedure of the _metric:
As and it influences weight, is obtained by DANP. This study applied the novel concepts of Equations (A16) and (A17) to acquire the outcomes for the development gaps per dimension/factor according to feedback and interdependence issues:
We set the aspired values, vector
We set the worst values, vector
In the paper, we used questionnaires in which the scored responses range from 0 to 10: totally dissatisfied (0) to extremely satisfied (10). The fundamental concept of this technique is to apply performance scores according to experts; thus, the worst value is set at zero and the aspired level is set at 10. Hence, we set , j = 1,2, …, n as the aspired level and , j = 1,2, …, n as the worst value, which differs from the traditional method. In this method, we use as aspired value and as the worst value, in order to prevent selecting the best from among inferior alternatives.
Stage 2: indicates the minimum mean of cluster utility and maximal regret :
where indicates the ratio of the gap; indicates the average gap ratios through aspirated value to performance value in factor j of alternative k, and this study focused on how to minimalize gap for all factors . Formerly, indicated the relative influence weight of factor j; can be determined through DANP according DEMATEL. indicates the maximum gap for all factors.
Stage 3: indicates comprehensive factor and its various consequences. Equation (A20) computes the values. From Equation (A20), we can detect how to enhance the adoption of an e-health cloud computing system, in order to decrease the gaps in reaching the desired values according to the influence relationship map:
This study applied the levels obtained by or , or ; or ), or . Therefore, the gap for , , , and ; thus, we can re-write Equation (A20) as . Weight only indicates how to reduce the average gap, while weight only decides how to choose the largest gap for enhancement. Generally, can be used to according to this condition.
According to the above concepts and applying the influential network relationship map, we can simply attain how to enhance these gaps rkj (k = 1, 2, …, m; j = 1, 2, …, n), that is, the enhancement sequence to attain the aspired value.
References
- Ali, O.; Shrestha, A.; Soar, J.; Wamba, S.F. Cloud computing-enabled healthcare opportunities, issues, and applications: A systematic review. Int. J. Inf. Manag. 2018, 43, 146–158. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. Industry 4.0 and Health: Internet of Things, Big Data, and Cloud Computing for Healthcare 4.0. J. Ind. Inf. Integr. 2020, 18, 100129. [Google Scholar] [CrossRef]
- Shamshad, S.; Minahil; Mahmood, K.; Kumari, S.; Chen, C.-M. A secure blockchain-based e-health records storage and sharing scheme. J. Inf. Secur. Appl. 2020, 55, 102590. [Google Scholar] [CrossRef]
- Pai, F.-Y.; Huang, K.-I. Applying the Technology Acceptance Model to the introduction of healthcare information systems. Technol. Forecast. Soc. Chang. 2011, 78, 650–660. [Google Scholar] [CrossRef]
- Behrend, T.S.; Wiebe, E.N.; London, J.E.; Johnson, E.C. Cloud computing adoption and usage in community colleges. Behav. Inf. Technol. 2011, 30, 231–240. [Google Scholar] [CrossRef]
- Löhr, H.; Sadeghi, A.-R.; Winandy, M. Securing the e-Health Cloud. 2010. Available online: http://www.slideshare.net/BongYoungSung/securing-the-e-health-cloud (accessed on 10 August 2011).
- Sujith, E. Cloud Computing in Healthcare. 2008. Available online: http://www.frost.com/prod/servlet/market-insight-top.pag?docid=135578323 (accessed on 8 October 2011).
- Nobakht, M.; Sui, Y.; Seneviratne, A.; Hu, W. PGFit: Static permission analysis of health and fitness apps in IoT programming frameworks. J. Netw. Comput. Appl. 2020, 152, 102509. [Google Scholar] [CrossRef]
- Liu, C.; Zhu, Q.; Holroyd, K.A.; Seng, E.K. Status and trends of mobile-health applications for iOS devices: A developer’s perspective. J. Syst. Softw. 2011, 84, 2022–2033. [Google Scholar] [CrossRef]
- Silva, B.M.C.; Rodrigues, J.J.P.C.; de la Torre Díez, I.; López-Coronado, M.; Saleem, K. Mobile-health: A review of current state in 2015. J. Biomed. Inform. 2015, 56, 265–272. [Google Scholar] [CrossRef] [PubMed]
- Iwaya, L.; Gomes, M.; Simplício, M.; Carvalho, T.; Dominicini, C.; Sakuragui, R.; Rebelo, M.; Gutierrez, M.; Näslund, M.; Håkansson, P. Mobile health in emerging countries: A survey of research initiatives in Brazil. Int. J. Med. Inform. 2013, 82, 283–298. [Google Scholar] [CrossRef] [PubMed]
- Marcolino, M.S.; Oliveira, J.A.Q.; D’Agostino, M.; Ribeiro, A.L.; Alkmim, M.B.M.; Novillo-Ortiz, D. The Impact of mHealth Interventions: Systematic Review of Systematic Reviews. JMIR mHealth uHealth 2018, 6, e23. [Google Scholar] [CrossRef]
- Kumar, S.; Nilsen, W.J.; Abernethy, A.; Atienza, A.; Patrick, K.; Pavel, M.; Hedeker, D. Mobile health technology evaluation: The mHealth evidence workshop. Am. J. Prev. Med. 2013, 45, 228–236. [Google Scholar] [CrossRef] [PubMed]
- West, D. How mobile devices are transforming healthcare. Technol. Innovat. 2012, 18, 1–11. [Google Scholar]
- Krishnan, S.; Lokesh, S.; Devi, M.R. An efficient Elman neural network classifier with cloud supported internet of things structure for health monitoring system. Comput. Netw. 2019, 151, 201–210. [Google Scholar] [CrossRef]
- Razmak, J.; Bélanger, C.H. Comparing Canadian physicians and patients on their use of e-health tools. Technol. Soc. 2017, 51, 102–112. [Google Scholar] [CrossRef]
- Khansa, L.; Davis, Z.; Davis, H.; Chin, A.; Irvine, H.; Nichols, L.; Lang, J.A.; MacMichael, N. Health information technologies for patients with diabetes. Technol. Soc. 2016, 44, 1–9. [Google Scholar] [CrossRef]
- Spatar, D.; Kok, O.; Basoglu, N.; Daim, T. Adoption factors of electronic health record systems. Technol. Soc. 2019, 58, 101144. [Google Scholar] [CrossRef]
- Gao, F.; Sunyaev, A. Context matters: A review of the determinant factors in the decision to adopt cloud computing in healthcare. Int. J. Inf. Manag. 2019, 48, 120–138. [Google Scholar] [CrossRef]
- Chen, C.; Watanabe, C.; Griffy-Brown, C. The co-evolution process of technological innovation—An empirical study of mobile phone vendors and telecommunication service operators in Japan. Technol. Soc. 2007, 29, 1–22. [Google Scholar] [CrossRef]
- Buyya, R.; Yeo, C.S.; Venugopal, S. Market-Oriented Cloud Computing: Vision, Hype, and Reality for Delivering IT Services as Computing Utilities. In Proceedings of the 10th IEEE International Conference on High Performance Computing and Communications, Dalian, China, 25–27 September 2008; pp. 5–13. [Google Scholar]
- Vaquero, L.M.; Rodero-Merino, L.; Caceres, J.; Lindner, M. A break in the clouds: Towards a cloud definition. ACM SIGCOMM Comp. Commun. Rev. 2008, 39, 50–55. [Google Scholar] [CrossRef]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Liao, W.-H.; Qiu, W.-L. Applying analytic hierarchy process to assess healthcare-oriented cloud computing service systems. SpringerPlus 2016, 5, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Butpheng, C.; Yeh, K.H.; Xiong, H. Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of Cloud computing and Internet of Things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Azeez, N.A.; van der Vyver, C. Security and privacy issues in e-health cloud-based system: A comprehensive content analysis. Egypt. Inform. J. 2019, 93, 237–255. [Google Scholar] [CrossRef]
- Singh, S.; Wachter, R. Perspectives on medical outsourcing and telemedicine: Rough edges in a flat world? N. Engl. J. Med. 2008, 358, 1622–1627. [Google Scholar] [CrossRef] [PubMed]
- Standing, S.; Standing, C. Mobile technology and healthcare: The adoption issues and systemic problems. Int. J. Electron. Healthc. 2008, 4, 221–235. [Google Scholar] [CrossRef]
- Mathieson, S. Does Cambridge University Hospital’s Epic Project Indicate NHS Lacks Capacity? 2015. Available online: http://www.computerweekly.com/feature/Does-Cambridge-Universitys-Epic-project-indicate-NHS-lacks-capacity (accessed on 17 November 2015).
- Moore-Colyer, R. HP Overhauls Cambridge University Hospitals? IT in £200m Project. 2015. Available online: https://www.v3.co.uk/v3-uk/news/2414532/hp-overhauls-cambridge-university-hospitals-it-in-gbp200m-project (accessed on 17 November 2015).
- Ambarkar, S.S.; Shekokar, N. Toward Smart and Secure IoT Based Healthcare System. In Internet of Things, Smart Computing and Technology: A Roadmap Ahead; Springer: Cham, Switzerland, 2020; pp. 283–303. [Google Scholar]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Abouelmehdi, K.; Beni-Hssane, A.; Khaloufi, H.; Saadi, M. Big data security and privacy in healthcare: A Review. Procedia Comput. Sci. 2017, 113, 73–80. [Google Scholar] [CrossRef]
- Semantha, F.H.; Azam, S.; Yeo, K.C.; Shanmugam, B. A Systematic Literature Review on Privacy by Design in the Healthcare Sector. Electronics 2020, 9, 452. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Gia, T.N.; Negash, B.; Anzanpour, A.; Azimi, I.; Jiang, M.; Liljeberg, P. Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Future Gener. Comput. Syst. 2018, 78, 641–658. [Google Scholar] [CrossRef]
- Shewale, A.D.; Sankpal, S.V. IOT & Raspberry Pi based Smart and Secure Health Care System using BSN. Int. J. Res. Appl. Sci. Eng. Technol. 2020, 8, 506–510. [Google Scholar]
- Dang, L.M.; Piran, J.; Han, D.; Min, K.; Moon, H. A Survey on Internet of Things and Cloud Computing for Healthcare. Electronics 2019, 8, 768. [Google Scholar] [CrossRef]
- Wu, J.; Tian, X.; Tan, Y. Hospital evaluation mechanism based on mobile health for IoT system in social networks. Comput. Biol. Med. 2019, 109, 138–147. [Google Scholar] [CrossRef] [PubMed]
- Tuli, S.; Basumatary, N.; Gill, S.S.; Kahani, M.; Arya, R.C.; Wander, G.S.; Buyya, R. HealthFog: An ensemble deep learning based Smart Healthcare System for Automatic Diagnosis of Heart Diseases in integrated IoT and fog computing environments. Future Gener. Comput. Syst. 2020, 104, 187–200. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. Secure healthcare monitoring framework integrating NDN-based IoT with edge cloud. Future Gener. Comput. Syst. 2020, 112, 320–329. [Google Scholar] [CrossRef]
- Alihamidi, I.; Madi, A.A.; Addaim, A. Proposed Architecture of e-health IOT. In Proceedings of the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 29 October–1 November 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Perera, C.; Barhamgi, M.; Bandara, A.K.; Ajmal, M.; Price, B.; Nuseibeh, B. Designing privacy-aware internet of things applications. Inf. Sci. 2020, 512, 238–257. [Google Scholar] [CrossRef]
- Kalyani, G.; Chaudhari, S. An efficient approach h for enhancing security in the Internet of Things using the optimum authentication key. Int. J. Comput. Appl. 2019, 42, 306–314. [Google Scholar] [CrossRef]
- Lu, M.-T.; Hu, S.-K.; Huang, L.-H.; Tzeng, G.-H. Evaluating the implementation of business-to-business m-commerce by SMEs based on a new hybrid MADM model. Manag. Decis. 2015, 53, 290–317. [Google Scholar] [CrossRef]
- Liou, J.J.H.; Lu, M.-T.; Hu, S.-K.; Cheng, C.-H.; Chuang, Y.-C. A Hybrid MCDM Model for Improving the Electronic Health Record to Better Serve Client Needs. Sustainability 2017, 9, 1819. [Google Scholar] [CrossRef]
- Lu, M.-T.; Hsu, C.-C.; Liou, J.J.; Lo, H.-W. A hybrid MCDM and sustainability-balanced scorecard model to establish sustainable performance evaluation for international airports. J. Air Transp. Manag. 2018, 71, 9–19. [Google Scholar] [CrossRef]
- Lu, M.-T.; Tsai, J.-F.; Shen, S.-P.; Lin, M.-H.; Hu, Y.-C. Estimating sustainable development performance in the electrical wire and cable industry: Applying the integrated fuzzy MADM approach. J. Clean. Prod. 2020, 277, 122440. [Google Scholar] [CrossRef]
- Lu, M.-T.; Tzeng, G.-H.; Cheng, H.; Hsu, C.-C. Exploring mobile banking services for user behavior in intention adoption: Using new hybrid MADM model. Serv. Bus. 2014, 9, 541–565. [Google Scholar] [CrossRef]
- Lu, M.T.; Tzeng, G.H.; Tang, L.L. Environmental strategic orientations for improving green innovation performance in fuzzy environment-Using new fuzzy Hybrid MCDM model. Int. J. Fuzzy Syst. 2013, 15, 297–316. [Google Scholar]
- Fontela, E.; Gabus, A. The DEMATEL Observer; DEMATEL 1976 Report; Battelle Geneva Research Center: Geneva, Switzerland, 1976. [Google Scholar]
- Gabus, A.; Fontela, F. Perceptions of the World Problematique: Communication Procedure, Communicating with Those Bearing Collective Responsibility; Battelle Geneva Research Center: Geneva, Switzerland, 1973; L Report No. 1. [Google Scholar]
- Lu, M.-T.; Lin, S.-W.; Tzeng, G.-H. Improving RFID adoption in Taiwan’s healthcare industry based on a DEMATEL technique with a hybrid MCDM model. Decis. Support Syst. 2013, 56, 259–269. [Google Scholar] [CrossRef]
- Ho, J.-H.; Lee, G.-G.; Lu, M.-T. Exploring the Implementation of a Legal AI Bot for Sustainable Development in Legal Advisory Institutions. Sustainability 2020, 12, 5991. [Google Scholar] [CrossRef]
- Liou, J.J.H.; Kaklauskas, A.; Lu, M.-T.; Chuang, Y.-C. Improving strategic orientations for promoting hotel services using an integrated rough magdm model. Technol. Econ. Dev. Econ. 2019, 25, 188–218. [Google Scholar] [CrossRef]
- Saaty, T.L. Decision Making with Dependence and Feedback: Analytic Network Process; RWS Publications: Pittsburgh, PA, USA; New York, NY, USA, 1996. [Google Scholar]
- Ou Yang, Y.P.; Shieh, H.M.; Tzeng, G.H. A novel hybrid MCDM model combined with DEMATEL and ANP with applications. Int. J. Oper. Res. 2008, 5, 160–168. [Google Scholar]
- Opricovic, S.; Tzeng, G.-H. Compromise solution by MCDM methods: A comparative analysis of VIKOR and TOPSIS. Eur. J. Oper. Res. 2004, 156, 445–455. [Google Scholar] [CrossRef]
- Opricovic, S.; Tzeng, G.-H. Extended VIKOR method in comparison with outranking methods. Eur. J. Oper. Res. 2007, 178, 514–529. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).