Abstract
Bit commitment is a cryptographic task in which Alice commits a bit to Bob such that she cannot change the value of the bit after her commitment and Bob cannot learn the value of the bit before Alice opens her commitment. According to the Mayers–Lo–Chau (MLC) no-go theorem, ideal bit commitment is impossible within quantum theory. In the information theoretic-reconstruction of quantum theory, the impossibility of quantum bit commitment is one of the three information-theoretic constraints that characterize quantum theory. In this paper, we first provide a very simple proof of the MLC no-go theorem and its quantitative generalization. Then, we formalize bit commitment in the theory of dagger monoidal categories. We show that in the setting of dagger monoidal categories, the impossibility of bit commitment is equivalent to the unitary equivalence of purification.
1. Introduction
Bit commitment, used in a wide range of cryptographic protocols (e.g., zero-knowledge proof, multiparty secure computation, and oblivious transfer), consists of two phases, namely: commit and opening. In the commit phase, Alice the sender chooses a bit a ( or 1) which she wishes to commit to the receiver Bob. Then, Alice presents Bob some evidence about the bit. The committed bit cannot be known by Bob prior to the opening phase. Later, in the opening phase, Alice announces some information for reconstructing a. Bob then reconstructs a bit using Alice’s evidence and announcement. A correct bit commitment protocol will ensure that . A bit commitment protocol is concealing if Bob cannot know the bit Alice committed before the opening phase and it is binding if Alice cannot change the bit she committed after the commit phase. It is secure if it is both concealing and binding. It is unconditionally secure if it is secure and the security does not rely on any computational assumption.
Quantum bit commitment (QBC) [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16] protocol was first proposed by Bennett and Brassard in 1984 [1]. Later, several QBC protocols were designed to achieve unconditional security, such as those in [17,18]. However, in 1996, Mayers [19] and Lo and Chau [20,21] showed that all previously proposed QBC protocols were vulnerable to an entanglement attack which can be launched by Alice. This result was later referred to as the Mayers–Lo–Chau (MLC) no-go theorem.
This no-go theorem has been continuously challenged in the past two decades. Yuen [22,23] repeatedly argued that the no-go proof is not general enough to exhaust all conceivable quantum bit commitment protocols. On the other hand, the no-go theorem has also been extended by several scholars. Nambu and Chiba-Kohno [24] gave a constructive proof of the theorem from the viewpoint of quantum information theory. Spekkens and Rudolph [25] and He [26] extended the no-go theorem with quantitative bounds on the degree of concealment and bindingness. D’Ariano et al. [27] provided a strengthened and explicit impossibility proof exhausting all conceivable protocols in which not only quantum information, but also classical information is exchanged between the two parties. However, the considerable length of the proof in [27] makes it still hard to follow. Chiribella et al. [28] simplified the proof in [27]. In the works of Cohn-Gordon [29] and Heunen and Kissinger [30], a clear and rigorous formalization of QBC is developed in the setting of categorical quantum mechanics. Cohn-Gordon [29] also provided a proof of the no-go theorem. While this proof is already simpler than all previous proofs, we find there is still room for simplification and extension.
In Clifton et al.’s information theoretic-reconstruction of quantum theory [31], the impossibility of bit commitment is conceived as one of the three fundamental information-theoretic constraints that characterize quantum theory. In [31], the authors partially proved that the impossibility of bit commitment is equivalent to the existence of entangled, or nonlocal, states. This result was questioned by Heunen and Kissinger [30], who demonstrated that, in the categorical setting, the impossibility of bit commitment is not equivalent to the existence of entangled states. Which quantum feature is the one that is equivalent to the impossibility of bit commitment is left unanswered in [30].
The contributions of this paper are ass follows.
- The length of the proof in Cohn-Gordon [29] is more than two pages. We provide a simpler proof which takes only a few lines.
- The proof in [29] only concerns the qualitative version of the no-go theorem. We formalize and prove the quantitative version of the no-go theorem.
- We show that the impossibility of bit commitment is equivalent to the unitary equivalence of purification in the setting of dagger monoidal categories. This provides an answer to the problem left by Heunen and Kissinger [30].
The structure of this paper is as follows. We simplify and extend the proof of Cohn-Gordon [29] in Section 2. Then, in Section 3, we study the impossibility of bit commitment in the setting of dagger monoidal categories and demonstrate that the quantum feature corresponding to the impossibility of bit commitment in the categorical setting is the unitary equivalence of purification. In Section 4, we discuss some related work. We conclude this paper with future work in Section 5.
2. The No-Go Theorem of Quantum Bit Commitment
In the literature [19,20,25,29,30], it is acknowledged that a general model of QBC protocols should at least includes the following ingredients:
- The Hilbert space required to describe the protocol is the tensor product of the Hilbert spaces that play a role in the protocol.
- The total system is initially in a pure state.
- Every action taken by a party corresponds to that party performing a unitary operation on the systems in his/her possession.
- Every communication corresponds to a party sending a subset of the systems in his/her possession to the other party.
Bearing this common knowledge in mind, we propose the most rigorous and simplest formalization of quantum bit commitment as follows.
Definition 1.
A quantum bit commitment protocol consists of the following:
- (1)
- Two finite-dimensional Hiblert spaces A and B
- (2)
- Two pure states
- (3)
- A quantum operation (i.e., completely positive, trace-preserving super operator) on such that
This QBC protocol is concealing if . It is binding if there is no unitary U on A such that .
This formalization provides a high level description of quantum bit commitment. Initially, Alice (possibly with the help of Bob) prepares a state or of quantum system depending on the value of Alice’s bit. Note that and are not the initial states of the QBC protocol, but the final states of the commit phase. Starting from a pure state, a commit phase may involve many rounds of actions and communications. Alice sends or to Bob to perform the commitment. At the opening stage, Alice sends the rest sub-state of or to Bob to allow him to verify her commitment. Bob applies the quantum operation to determine Alice’s commitment.
In our definition of bindingness, we only consider the situation in which Alice applies unitary operators to the pure state in her possession, instead of complete positive maps on mixed states. This is a reasonable assumption in the sense that complete positive maps on mixed states can be purified to unitary map on pure states via Stinespring representation [32]. This notion of bindingness is very strong: Alice must be able to alter to with certainty. In Section 2.2, we introduce -binding, a weaker notion of bindingness that allows Alice to alter to a state which is similar to . Another issue concerning bindingness is that the operation plays no role in the current definition of bindingness. We discuss an alternative notion of bindingness which involves in Section 4.
Example 1.
The QBC protocol due to Bennett and Brassard [1] goes as follows: Alice and Bob first agree on a security parameter, a positive integer s.
- 1.
- Commit phase:
- (a)
- Alice chooses the value of the committed bit c and the auxiliary bits .
- (b)
- If , she prepares and sends Bob s qubits, which are chosen to be either or . The value of c is kept secret during the commit phase. If , then Alice sets the ith qubit to be . If , then she sets the ith qubit to be . The value of are also kept secret during the commit phase.
- (c)
- Similarly, if , she prepares and sends Bob s qubits, which are chosen to be either or . If , then Alice sets the ith qubit to be . If , and then she sets the ith qubit to be . The value of are kept secret during the commit phase.
- 2.
- Opening phase:
- (a)
- Bob randomly prepares auxiliary bits . If , and then Bob measures the ith qubit in the basis. If , then Bob measures the ith qubit in the basis.
- (b)
- Alice announces the value of .
- (c)
- Bob accepts Alice’s commitment if and only if, for all indexes with , Bob’s measurement outcome agrees with Alice’s announcement.
We can formalize this QBC protocol as follows:
- Let and .
- Let , where is the identity operator and is the Pauli X operator.
- Let , where is the Hadamard operator H and is .
- Let be a completely positive map such that
- -
- , where is the completely positive map which represents the measurement on the basis and is the completely positive map which represents the measurement on the basis.
- -
- .
Note that, although our formalization of QBC protocols in Definition 1 looks simple, it is in fact already more general than the formalizations by Lo and Chau [20] and Cohn-Gordon [29]. It is also a proper extension of the purification bit commitment protocol by Spekkens and Rudolph [25].
Example 2.
A purification bit commitment protocol [25] makes use of two systems, the token system and the proof system. These are associated with Hilbert spaces and . A purification bit commitment protocol also specifies two orthogonal states and , which are states of the system . At the commit phase, Alice prepares the two systems in the state in order to commit to bit b, and sends the token system to Bob. At the opening phase, Alice sends the proof system to Bob, and Bob performs a measurement of the projector valued measure , where .
We further discuss the generality of our formalism in Section 4.
2.1. The Qualitative No-Go Theorem
Within our formalization, the no-go theorem of quantum bit commitment becomes a precise mathematical statement. To prove this statement, we make use of the unitary equivalence of purification, which can be found in standard textbooks of quantum information [32,33].
Definition 2
(purification). Let A and B be two Hilbert spaces and be the set of all positive semidefinite operators on A. For and , is a purification of ρ if .
Lemma 1
(unitary equivalence of purification). Let and be two purifications of a positive smiedefinite operator . There is a unitary transformation U acting on B such that .
Theorem 1
(no-go theorem, the qualitative version). If a quantum bit commitment protocol is concealing, then it is not binding.
Proof.
If a QBC is concealing, then . Hence, and are two purifications of the same mixed state. By Lemma 1, we know there is a unitary operator such that , which means that the QBC is not binding. □
The astonishing simplicity of the above proof suggests a close relationship between the unitary equivalence of purification and the impossibility of quantum bit commitment. In Section 3, we show that they are actually equivalent in an abstract categorical framework.
2.2. The Quantitative No-Go Theorem
The qualitative version of the no-go theorem states that it is impossible for a QBC protocol to be both absolute concealing and absolute binding. However, it does not exclude the possibility of a QBC protocol to be both partially concealing and partially binding. We now formalize and prove the quantitative version of the no-go theorem, which establishes a relation between partially concealing and partially binding. The key notion we use is the fidelity between quantum states.
Definition 3
(fidelity [33]). Let and be two pure states of a Hilbert space. The fidelity of and is . Let ρ and σ be two mix states of a Hilbert space. The fidelity of ρ and σ is .
After some careful calculation, we know that . We define the relation , where , between quantum states as follows: iff . Apparently, iff .
Definition 4
(-concealing, -binding). A quantum bit commitment protocol is ϵ-concealing if . It is ϵ-binding if there is no unitary U on A such that .
The following Uhlmann’s theorem is used in the proof of the quantitative version of the no-go theorem.
Theorem 2
(Uhlmann’s theorem [33]). , where ranges over all purifications of ρ and ψ ranges over all purifications of σ. If is a fixed purification of ρ, then , where ψ ranges over all purifications of σ.
Theorem 3
(no-go theorem, the quantitative version). If a quantum bit commitment protocol is ϵ-concealing, then it is not ϵ-binding.
Proof.
If a QBC protocol is -concealing, then . Thus, we have . Now, by Uhlmann’s theorem, we know there exists a purification of such that . Therefore, and . Note that, by the unitary equivalence of purification, we have . This means that . Therefore, the QBC protocol is not -binding. □
3. Bit Commitment in Categorical Quantum Mechanics
Categorical quantum mechanics (CQM) [34,35,36,37,38,39,40,41,42,43,44,45] is the study of quantum computation and quantum foundations using category theory, as well as the graphical language closely related to category theory. In CQM, dagger monoidal categories (DMC) are used as an axiomatic basis for quantum mechanics, providing a generalization of the usual axiomatization in terms of Hilbert spaces.
Definition 5
(strict monoidal category [43]). A strict monoidal category is a category equipped with:
- 1.
- a parallel composition operation for objects:
- 2.
- a unit object ; and
- 3.
- a parallel composition operation for morphisms:
satisfying the following conditions:
- 1.
- ⊗ is associative and unital on objects:
- 2.
- ⊗ is associative and unital on morphisms:
- 3.
- ⊗ and ∘ satisfy the interchange law:.
Definition 6
(dagger functor † [43]). A dagger functor for a strict monoidal category is an operation † that satisfies the following:
- identity on objects: ;
- reserves morphisms: ;
- is involutive: ; and
- respects the symmetric monoidal category structure:
A dagger monoidal category is a strict monoidal category equipped with a dagger functor.
Example 3.
The category of finite dimensional Hilbert spaces FinHilb is a DMC. In FinHilb, objects are finite-dimensional Hilbert spaces over complex numbers, morphisms are linear maps, parallel composition is the tensor product, I is the one-dimensional Hilbert spaces , and † is the adjoin operator.
Example 4.
The category Dens of density operators and completely positive maps is a DMC. The objects of Dens are the same as the objects of FinHilb. A morphism from object to object is a completely positive map . Parallel composition is the tensor product, I is the one-dimensional Hilbert spaces , and † is the adjoin operator.
Example 5.
The category of arbitrary dimensional Hilbert spaces Hilb is a DMC. In Hilb, objects are Hilbert spaces over complex numbers, morphisms are bounded linear maps, parallel composition is the tensor product, I is the one-dimensional Hilbert spaces , and † is the adjoin operator.
To formalize bit commitment in DMC, we further need concepts such as environment structure and purification.
3.1. Environment Structure and Purification
Definition 7
(environment structure [46]). Let be a dagger monoidal category. An environment structure for is a monoidal category with the same objects as , together with a strict monoidal functor with , and for each object A a morphism in , which we depict as:
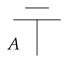
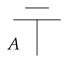
satisfying:
- 1.
- We have , and for all objects A and B: .
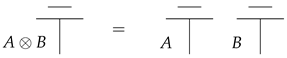
- 2.
- For morphisms and in , in if and only if in .

- 3.
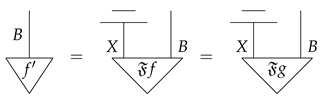
- For each , there is for some object X such that in . Such an f is called a purification of .
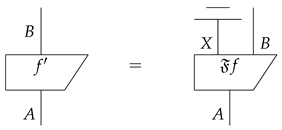
Intuitively, if we think of the category as consisting of pure states, then the category consists of mixed states. The morphisms can be viewed as discarding system A to the environment, or, in other words, trace out A.
Example 6.
provides an environment structure for , in which is the trace operator . The functor maps a liner map to a completely positive operator such that .
Definition 8
(unitary equivalence of purification). An environment structure for satisfies the unitary equivalence of purification if the following is satisfied: for all , if are purifications of , then there exists a unitary morphism such that .
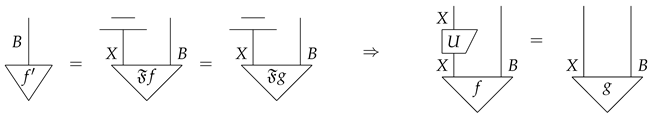

3.2. Bit Commitment in Dagger Monoidal Category
Now, we formalize bit commitment in the setting of dagger monoidal categories. We do not assume compactness in our formalization. This is because assuming compactness will impose finite dimensionality on Hilbert spaces [47]: the DMC FinHilb is compact, while Hilb is not compact. Assuming no compactness makes our formalization more general than most formalizations in the literature, which only formalize bit commitment in finite dimensional Hilbert spaces.
Definition 9
(bit commitment in DMC). Let be a dagger monoidal category with an environment structure . A bit commitment protocol on consists of the following:
- 1.
- Two objects A and B
- 2.
- Two states in
- 3.
- A morphism on in such that in
A bit commitment protocol on is concealing if in .
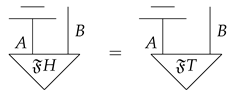
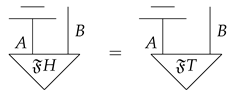
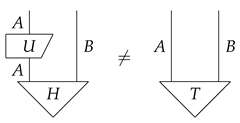
It is binding if there is no unitary morphism such that in . Equivalently, it is binding if, for all unitary morphisms , it holds that in .

Theorem 4.
Let be a dagger monoidal category with an environment structure . The following are equivalent:
- (1)
- The unitary equivalence of purification is satisfied.
- (2)
- For all bit commitment protocols on , if it is concealing, then it is not binding.
Proof.
Assume the unitary equivalence of purification is satisfied. If a bit commitment protocol on is concealing, then in . By the third requirement in the definition of environment structure, we know H and T are two purifications of the same state. By the unitary equivalence of purification, we know there is a unitary morphism such that , which means that the bit commitment protocol is not binding.
Assume for all bit commitment protocol on , if it is concealing then it is not binding. Let B be an arbitrary object in and . Assume are purifications of . This means that .

- If , then by the second requirement in the definition of environment structure, we know that . Now, we let . Then, it holds that .
- If , then we design a bit commitment protocol in which . Since , we know this protocol is concealing. Hence, it cannot be binding, which means there is a unitary morphism such that .
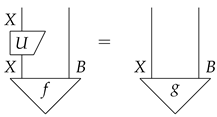 To conclude, no matter or , the unitary equivalence of purification is satisfied. □
To conclude, no matter or , the unitary equivalence of purification is satisfied. □
4. Related Work and Discussion
4.1. An Alternative Notion of Bindingness
The definition of bindingness described in Section 2 essentially says that Alice cannot change to by operating on the quantum system under her control. This definition is reasonable, but not uniquely reasonable. Another reasonable definition of bindingness, which says that Alice cannot change to by operating on the quantum system under her control, is formally given as follows.
Definition 10
(-posterior binding). A quantum bit commitment protocol is ϵ-posterior binding if there is no unitary U on A such that .
We can prove that, if a QBC protocol is -concealing, then it is not -posterior binding by combining Theorem 3 and the following theorem.
Theorem 5.
If a quantum bit commitment protocol is not ϵ-binding, then it is not ϵ-posterior binding.
Proof.
If a QBC protocol is not -binding, then there is a unitary map U on A such that . Therefore, . Note that . Now, by the monotonicity of the fidelity function under quantum operations [32], we know that . Therefore, the QBC protocol is not -posterior binding. □
4.2. Mixed State Formalization of QBC
To the best of our knowledge, the most mathematically involved formalization of QBC was given by D’Ariano et al. [27] and Chiribella et al. [28]. In their formalization, the original state is a mixed state and the strategies that Alice and Bob can use are represented by super operators. These super operators are decomposed to a sequence of super operators to characterize the actions Alice and Bob may take at different steps of the protocol. Some distance functions between super operators are adopted to define -concealing and -binding.
Since super operators on mixed states can be represented by linear maps on pure states with some ancillary states by the Stinespring dilation, we conject that our formalism is equivalent to the mixed state formalism. A detailed comparison of these formalism is left as future work.
5. Conclusions and Future Work
In this paper, we first provide a very simple proof of the no-go theorem of quantum bit commitment and its quantitative generalization. Then, we formalize the no-go theorem in the theory of dagger monoidal categories. We show that, in the setting of dagger monoidal categories, the impossibility of bit commitment is equivalent to the unitary equivalence of purification.
The presented material also indicates some directions for future research:
- Sikora and Selby [48] formalized bit commitment in generalized probabilistic theories and showed that the no-go theorem holds by presenting a quantitative trade-off between Alice’s and Bob’s cheating probabilities. A comparison between our formalization and theirs will be carried out in the future.
- It was shown by Kent et al. [5,6,7,12] that perfect bit commitment is possible in the theory of relativity. Baez [49] pointed out that, from a categorical perspective, the theory of relativity and quantum theory resemble each other quite well. DMC plays an important role in both theories. In particular, nCob, the DMC which contains manifold as object and cobordism as morphism, plays an important role in general relativity. It will be interesting to formalize bit commitment in nCob and use it to analyze the similarity and difference of quantum theory and the theory of relativity.
- We also plan to apply the axiomatic and graphical language of categorical quantum mechanics in the formal verification of concrete QBC protocols in the future.
- The MLC no-go theorem does not rule out the feasibility of designing secure QBC in practice. Several practically secure QBC protocols have been devised and experimentally implemented in the last decade [50,51,52]. The security of those protocols typically relies on the current technological limitation on non-demolition measurement and long-term quantum memory. The implementation of those protocols often uses quantum optical devices such as nanosecond pulse laser, single mode optical fiber, and Mach–Zehnder interferometer for the generation, communication, and operation of non-entangled photons. With the recent development on the generation and manipulation of entangled photons [53], in the future, we are also interested in implementing QBC protocols based on (low-dimensional) entangled states [9,16].
Author Contributions
Conceptualization, X.S. and Q.W.; Formal analysis, X.S.; Methodology, F.H.; Validation, Q.W.; Writing – original draft, X.S.; Writing – review and editing, F.H. All authors have read and agreed to the published version of the manuscript.
Funding
The project is funded by the Minister of Science and Higher Education within the program under the name “Regional Initiative of Excellence” in 2019-2022, project number: 028/RID/2018/19, the amount of funding: 11 742 500 PLN.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bennetta, C.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 1984, 560, 175–179. [Google Scholar] [CrossRef]
- Hardy, L.; Kent, A. Cheat Sensitive Quantum Bit Commitment. Phys. Rev. Lett. 2004, 92, 1–4. [Google Scholar] [CrossRef] [PubMed]
- Buhrman, H.; Christandl, M.; Hayden, P.; Lo, H.K.; Wehner, S. Possibility, impossibility, and cheat sensitivity of quantum-bit string commitment. Phys. Rev. A 2008, 78, 1–10. [Google Scholar] [CrossRef]
- Shimizu, K.; Fukasaka, H.; Tamaki, K.; Imoto, N. Cheat-sensitive commitment of a classical bit coded in a block of m × n round-trip qubits. Phys. Rev. A 2011, 84, 1–14. [Google Scholar] [CrossRef]
- Kent, A. Unconditionally secure bit commitment with flying qudits. New J. Phys. 2011, 13, 1–16. [Google Scholar] [CrossRef]
- Kent, A. Unconditionally Secure Bit Commitment by Transmitting Measurement Outcomes. Phys. Rev. Lett. 2012, 109, 130501. [Google Scholar] [CrossRef]
- Lunghi, T.; Kaniewski, J.; Bussières, F.; Houlmann, R.; Tomamichel, M.; Kent, A.; Gisin, N.; Wehner, S.; Zbinden, H. Experimental Bit Commitment Based on Quantum Communication and Special Relativity. Phys. Rev. Lett. 2013, 111, 180504. [Google Scholar] [CrossRef]
- He, G.P. Simplified quantum bit commitment using single photon nonlocality. Quantum Inf. Process. 2014, 13, 2195–2211. [Google Scholar] [CrossRef]
- Li, Y.; Wen, Q.; Li, Z.; Qin, S.; Yang, Y. Cheat sensitive quantum bit commitment via pre- and post-selected quantum states. Quantum Inf. Process. 2014, 13, 141–149. [Google Scholar] [CrossRef]
- Adlam, E.; Kent, A. Device-independent relativistic quantum bit commitment. Phys. Rev. A 2015, 92, 1–9. [Google Scholar] [CrossRef]
- Lunghi, T.; Kaniewski, J.; Bussières, F.; Houlmann, R.; Tomamichel, M.; Wehner, S.; Zbinden, H. Practical Relativistic Bit Commitment. Phys. Rev. Lett. 2015, 115, 030502. [Google Scholar] [CrossRef] [PubMed]
- Verbanis, E.; Martin, A.; Houlmann, R.; Boso, G.; Bussières, F.; Zbinden, H. 24-Hour Relativistic Bit Commitment. Phys. Rev. Lett. 2016, 117, 140506. [Google Scholar] [CrossRef] [PubMed]
- Song, Y.; Yang, L. Practical Quantum Bit Commitment Protocol Based on Quantum Oblivious Transfer. Appl. Sci. 2018, 8, 1990. [Google Scholar] [CrossRef]
- Nagy, M.; Nagy, N. An Information-Theoretic Perspective on the Quantum Bit Commitment Impossibility Theorem. Entropy 2018, 20, 193. [Google Scholar] [CrossRef]
- He, G.P. Unconditionally secure quantum bit commitment based on the uncertainty principle. Proc. R. Soc. Math. Phys. Eng. Sci. 2019, 475, 20180543. [Google Scholar]
- Zhou, L.; Sun, X.; Su, C.; Liu, Z.; Choo, K.R. Game theoretic security of quantum bit commitment. Inf. Sci. 2019, 479, 503–514. [Google Scholar] [CrossRef]
- Brassard, G.; Crépeau, C. Quantum Bit Commitment and Coin Tossing Protocols. In Advances in Cryptology—CRYPTO ’90, Proceedings of the 10th Annual International Cryptology Conference, Santa Barbara, CA, USA, 11–15 August 1990; Menezes, A., Vanstone, S.A., Eds.; Springer: Berlin/Heidelberg, Germany, 1990; pp. 49–61. [Google Scholar]
- Brassard, G.; Crépeau, C.; Jozsa, R.; Langlois, D. A Quantum Bit Commitment Scheme Provably Unbreakable by both Parties. In Proceedings of the 34th Annual Symposium on Foundations of Computer Science, Palo Alto, CA, USA, 3–5 November 1993; IEEE Computer Society: Washington, DC, USA, 1993; pp. 362–371. [Google Scholar] [CrossRef]
- Mayers, D. Unconditionally secure quantum bit commitment is impossible. Phys. Rev. Lett. 1997, 78, 3414–3417. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Is Quantum Bit Commitment Really Possible? Phys. Rev. Lett. 1997, 78, 3410–3413. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Why quantum bit commitment and ideal quantum coin tossing are impossible. Phys. Nonlinear Phenom. 1998, 120, 177–187. [Google Scholar] [CrossRef]
- Yuen, H. Unconditionally Secure Quantum Bit Commitment Is Possible. 2000. Available online: https://arxiv.org/abs/quant-ph/0006109 (accessed on 6 January 2020).
- Yuen, H. Unconditionally Secure Quantum Bit Commitment. 2005. Available online: https://arxiv.org/abs/quant-ph/0505132 (accessed on 6 January 2020).
- Nambu, Y.; Chiba-Kohno, Y. Information-Theoretic Description of No-go Theorem of a Bit Commitment. 2000. Available online: https://arxiv.org/abs/quant-ph/0011068 (accessed on 6 January 2020).
- Spekkens, R.W.; Rudolph, T. Degrees of concealment and bindingness in quantum bit commitment protocols. Phys. Rev. A 2001, 65, 012310. [Google Scholar] [CrossRef]
- He, G.P. Security bound of cheat sensitive quantum bit commitment. Sci. Rep. 2015, 5, 9398. [Google Scholar] [CrossRef] [PubMed]
- D’Ariano, G.M.; Kretschmann, D.; Schlingemann, D.; Werner, R.F. Reexamination of quantum bit commitment: The possible and the impossible. Phys. Rev. A 2007, 76, 032328. [Google Scholar] [CrossRef]
- Chiribella, G.; D’Ariano, G.M.; Perinotti, P.; Schlingemann, D.; Werner, R. A short impossibility proof of quantum bit commitment. Phys. Lett. A 2013, 377, 1076–1087. [Google Scholar] [CrossRef]
- Cohn-Gordon, K. Commitment Algorithms. Master’s Thesis, University of Oxford, Oxford, UK, 2012. [Google Scholar]
- Heunen, C.; Kissinger, A. Can Quantum Theory Be Characterized in Terms of Information-Theoretic Constraints? 2016. Available online: http://homepages.inf.ed.ac.uk/cheunen/publications/2016/cbh/cbh.pdf (accessed on 6 January 2020).
- Clifton, R.; Bub, J.; Halvorson, H. Characterizing Quantum Theory in Terms of Information-Theoretic Constraints. Found. Phys. 2003, 33, 1561–1591. [Google Scholar] [CrossRef]
- Watrous, J. The Theory of Quantum Information; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Nielsen, M.; Chuang, I. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Abramsky, S.; Coecke, B. A Categorical Semantics of Quantum Protocols. In Proceedings of the 19th IEEE Symposium on Logic in Computer Science (LICS 2004), Turku, Finland, 14–17 July 2004; IEEE Computer Society: Washington, DC, USA, 2004; pp. 415–425. [Google Scholar] [CrossRef]
- Selinger, P. Dagger Compact Closed Categories and Completely Positive Maps: (Extended Abstract). Electr. Notes Theor. Comput. Sci. 2007, 170, 139–163. [Google Scholar] [CrossRef]
- Coecke, B.; Duncan, R. Interacting Quantum Observables. In Automata, Languages and Programming, Proceedigs of the 35th International Colloquium, ICALP 2008, Reykjavik, Iceland, 7–11 July 2008, Part II—Track B: Logic, Semantics, and Theory of Programming & Track C: Security and Cryptography Foundations; Lecture Notes in Computer Science; Aceto, L., Damgård, I., Goldberg, L.A., Halldórsson, M.M., Ingólfsdóttir, A., Walukiewicz, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5126, pp. 298–310. [Google Scholar] [CrossRef]
- Vicary, J. Categorical Formulation of Finite-dimensional C*-algebras. Electr. Notes Theor. Comput. Sci. 2011, 270, 129–145. [Google Scholar] [CrossRef][Green Version]
- Coecke, B.; Duncan, R. Interacting quantum observables: categorical algebra and diagrammatics. New J. Phys. 2011, 13, 1–85. [Google Scholar] [CrossRef]
- Coecke, B.; Wang, Q.; Wang, B.; Wang, Y.; Zhang, Q. Graphical Calculus for Quantum Key Distribution (Extended Abstract). Electr. Notes Theor. Comput. Sci. 2011, 270, 231–249. [Google Scholar] [CrossRef]
- Selinger, P. Finite Dimensional Hilbert Spaces are Complete for Dagger Compact Closed Categories (Extended Abstract). Electr. Notes Theor. Comput. Sci. 2011, 270, 113–119. [Google Scholar] [CrossRef]
- Coecke, B.; Perdrix, S. Environment and classical channels in categorical quantum mechanics. Log. Methods Comput. Sci. 2012, 8, 1–24. [Google Scholar] [CrossRef]
- Backens, M. The ZX-calculus is complete for stabilizer quantum mechanics. New J. Phys. 2014, 16, 093021. [Google Scholar] [CrossRef]
- Coecke, B.; Kissinger, A. Picturing Quantum Processes: A First Course in Quantum Theory and Diagrammatic Reasoning; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Zhou, L.; Wang, Q.; Sun, X.; Kulicki, P.; Castiglione, A. Quantum technique for access control in cloud computing II: Encryption and key distribution. J. Netw. Comput. Appl. 2018, 103, 178–184. [Google Scholar] [CrossRef]
- Hadzihasanovic, A.; Ng, K.F.; Wang, Q. Two complete axiomatisations of pure-state qubit quantum computing. In Proceedings of the 33rd Annual ACM/IEEE Symposium on Logic in Computer Science, LICS 2018, Oxford, UK, 9–12 July 2018; Dawar, A., Grädel, E., Eds.; ACM: New York, NY, USA, 2018; pp. 502–511. [Google Scholar] [CrossRef]
- Coecke, B.; Heunen, C. Pictures of complete positivity in arbitrary dimension. Inf. Comput. 2016, 250, 50–58. [Google Scholar] [CrossRef]
- Heunen, C. Compactly Accessible Categories and Quantum Key Distribution. Log. Methods Comput. Sci. 2008, 4. [Google Scholar] [CrossRef]
- Sikora, J.; Selby, J. Simple proof of the impossibility of bit commitment in generalized probabilistic theories using cone programming. Phys. Rev. A 2018, 97, 1–5. [Google Scholar] [CrossRef]
- Baez, J. Quantum Quandaries: A Category-Theoretic Perspective. In The Structural Foundations of Quantum Gravity; Rickles, D., French, S., Saatsi, J.T., Eds.; Oxford Scholarship Online: Oxford, UK, 2006. [Google Scholar]
- Danan, A.; Vaidman, L. Practical quantum bit commitment protocol. Quantum Inf. Process. 2012, 11, 769–775. [Google Scholar] [CrossRef]
- Loura, R.; Almeida, A.J.; André, P.S.; Pinto, A.N.; Mateus, P.; Paunković, N. Noise and measurement errors in a practical two-state quantum bit commitment protocol. Phys. Rev. A 2014, 89, 052336. [Google Scholar] [CrossRef]
- Loura, R.; Arsenović, D.c.v.; Paunković, N.; Popović, D.c.v.B.; Prvanović, S. Security of two-state and four-state practical quantum bit-commitment protocols. Phys. Rev. A 2016, 94, 062335. [Google Scholar] [CrossRef]
- Li, C.; Jiang, Z.; Zhang, Y.; Zhang, Z.; Wen, F.; Chen, H.; Zhang, Y.; Xiao, M. Controlled Correlation and Squeezing in Pr3+: Y2SiO5 to Yield Correlated Light Beams. Phys. Rev. Appl. 2017, 7, 014023. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
