ARCFIRE: Experimentation with the Recursive InterNetwork Architecture
Abstract
1. Introduction
- (1)
- Compare the design of converged operator networks using RINA to state-of-the-art operator network designs.
- (2)
- Produce a robust RINA software suite; mature enough for large-scale lab experiments.
- (3)
- Provide relevant experimental evidence of the RINA benefits for network operators, application developers, and end-users.
- (4)
- Raise the number of organizations involved in RINA research, development, and innovation activities.
- (5)
- Enhance FIRE+ as a platform for large-scale experimentation with RINA. FIRE+ (Future Internet Research and Experimentation) is a European experimental infrastructure for Future Internet research.
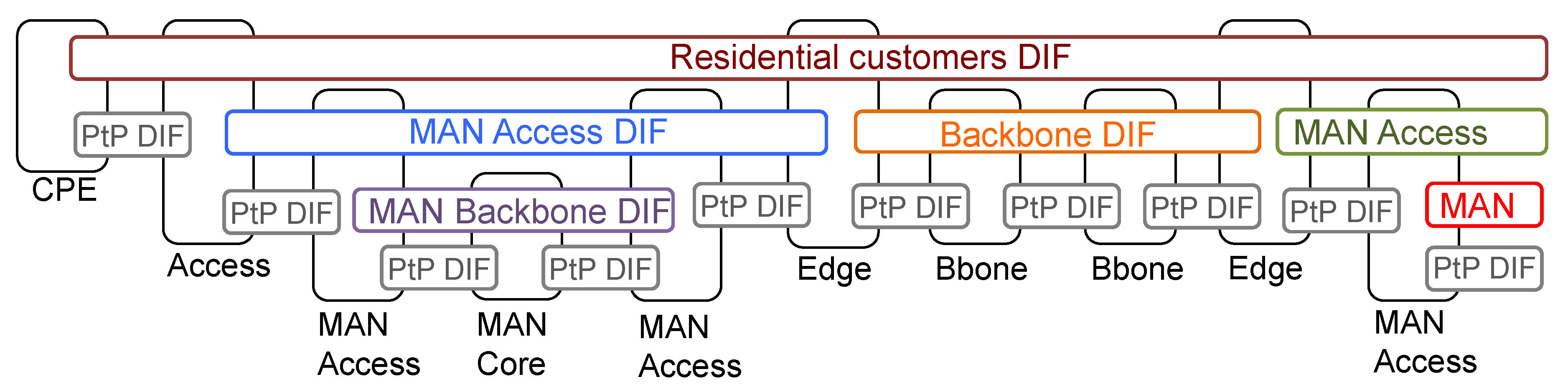
2. Modeling a Converged Network Operator
- Create the overall layered structure. The network is partitioned into a set of inter-operable layers (DIFs), each with a certain scope. The lower layers focus on resource allocation and QoS of more deterministic traffic, while the higher layers focus on grooming traffic to effectively use the lower layers. A trade-off has to be taken into account to decide the optimal number (typically no more than 5), since having more layers will have the effect of bounding the router table size [6], yet it also means an increase in delay and more packet headers.
- Characterize the QoS requirements for each layer. Each network is designed to serve a set of applications with specific traffic characteristics over a set of physical media. The way in which the network is broken up into layers as well as the role of each layer will define a set of QoS characteristics that need to be supported by each layer. Recognizing that these systems are not sufficiently sensitive to be configured to a precise point in “QoSspace”, i.e., precise set of values for the QoS parameters, it is defined in terms of one or more “QoS-cubes”. Network designers can map regions in this performance space to the QoS-cubes to be supported by each layer.
- Characterize the security requirements of each layer, in terms of authentication, access control, confidentiality or integrity protection.
- Specify the exact packet header syntax in the layer, based on the expected number of concurrent flows, the number of addressable IPC Processes, the maximum size of payload (larger packet sizes towards the backbone), the number of QoS cubes, etc.
- Decide per-layer policies, which allow the layer to operate effectively and meet the quality requirements (expressed via the QoS cubes).
- Identify operating ranges for the network and define monitors/triggers to sense them and choose/design the most appropriate strategies to automatically transition in the Network Management System (NMS) between different policy sets for each layer associated to the identified network operating ranges.
3. Scaling up RINA Networks
3.1. Resiliency within a Single DIF
3.2. Renumbering RINA Networks
3.3. Providing QoS Guarantees
3.4. Distributed Mobility Management
4. Simplification of Network Management
- Speed of node creation and validation. The average time to create or validate a node is 85 ms (on Raspberry Pi), 15 ms (on UNIX machines), and 3 ms (on Windows/-Cygwin). The creation adds a node to a network with its configuration. The validation runs a topological sort over the nodes’ configuration, and adds its DIFs and their structure to the network. These times scale linear up to larger networks, non-linear for the very large metro networks.
- Complexity. We measured the complexity of nodes for the operations creation and validation. The minimum complexity for node creation is 5, for node validation is 3. The maximum complexity for node creation is 28, for node validation 48. The largest complexities can be found in the metro networks. The other networks have node creation complexities between 5 and 13, node validation between 3 and 12. From the numbers we can see that most nodes are rather simple in terms of DIFs and PtP DIFs, while being part of comprehensive and complex service provider networks. This simplicity is largely due to the RINA simplification using DIFs instead of complex TCP/IP configurations without scope separation.
- Degree of automation. The test runs are fully automated using DMS scenarios. However, we did experience race conditions on slow machines (in this experiment the Raspberry Pi) for all networks, on medium size machines (in this experiment on Windows/Cygwin) for larger networks, and on all machines for very large networks. So, the degree of automation is 100% on most test runs on most machines, but less in the mentioned conditions.
- Touches. The number of manual operations for the management strategy to succeed is 0 on small to large networks on standard or powerful UNIX machines. The number increases by 1 per network for very large networks.
- DMS Scale, including time and cost. Taking each individual test run of each of the modelled networks as a network segment, we can see that the DMS is able to handle super large networks. In this context, we created a network with 6950 segments with overall 945,400 nodes in 55:42:05 hours. On all the 4 large UNIX machines combined, and without the very large metro networks, we created a network with 4000 segments and overall 57,600 nodes in 10:07:23 hours. We can state that scaling out the DMS components happens in less than 1 s, while scaling out APEX (the underlying DMS engine) can take 5 or 10 s, depending on the chosen option. This means that we can react to event storms within a few (minimum 5) seconds for the DMS strategy. This time ‘should’ be enough if we get an early indicator of an event storm, and the potential size the storm implies. Since event storms for configuration management are only when either a large network (many nodes) or a large number of smaller networks (with some or many nodes are created. These actions tend to happen in planned operations, not in unusual or accidental operations. One example is the action to add for instance 10,000 new nodes to a mobile network, or to deploy a new metro network, or to initially create an enterprise network.
5. Discussion of Experimental Results
5.1. Resiliency Experiments
5.2. Renumbering Experiments
5.3. Quality of Service Experiments
5.4. Distributed Mobility Management Experiments
5.5. Network Management Experiments
- The separation of mechanism and policy is the key abstraction, especially for network management. Mechanism’ and ‘policy’ are relative and related to the scope of the system. In other words what is ‘the mechanism’ in one system (and scope) can be ‘policy’ in another (larger) system and scope.
- There is only one application protocol (CDAP, the Common Distributed Application Protocol) with only six operations: create, delete, read, write, start, and stop. CDAP operations are executed on well-defined objects in the Resource Information Base (RIB).
- Management is monitoring and repair, everything else is most likely control. The term management and its activities (often called management functions) are relative, i.e., more a continuum than a specific box in a system architecture. We can therefore use ‘monitoring and repair’ on different system levels (with associated scope).
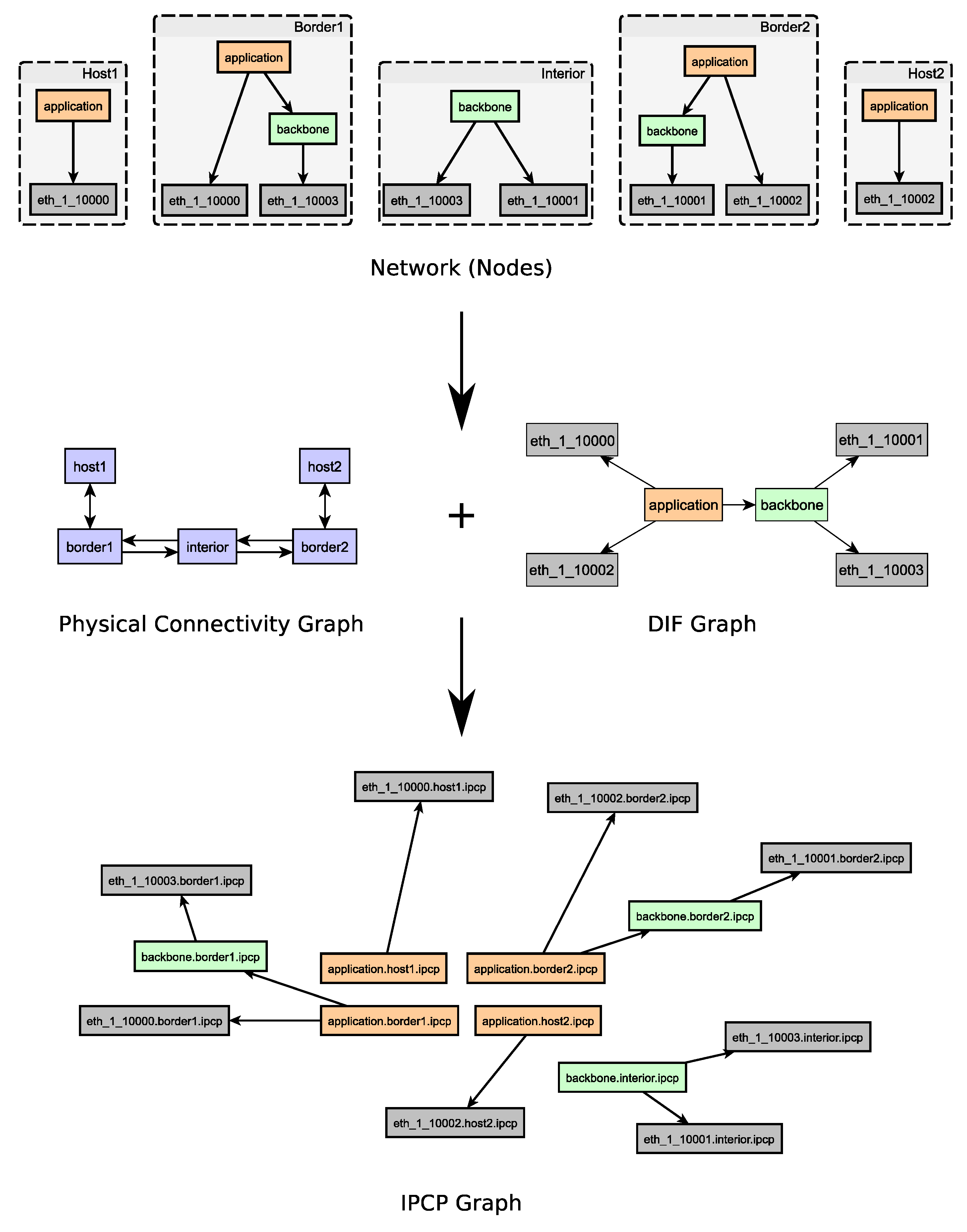
- A network in the RINA sense is a set of nodes and DIFs plus the IPCPs in the DIFs. This seems to imply that we need more than one dimension to show and explore a Recursive InterNetworking Architecture (RINA) network, i.e., a simple ‘topology’ is not enough.
- A node can be created and validated independent of any other node. Its configuration only requires its DIFs and their connections (plus the Distributed IPC Facility (DIF) QoS cubes). This has been demonstrated in the Rumba tool.
- A network can be created and validated only using individual node configurations. There is no further information required.
- All aspects of a RINA network can be shown and explored using four different graphs: a network (nodes) graph with the individual nodes and their configuration, a PtP graph with point-to-point connections between nodes, a DIF graph showing all defined DIFs and their connections, and a network graph (or IPCP graph) showing all IPCPs with their DIF and their connections. Some of these graphs are trees (in the mathematical sense), the PtP graph can be any type of graph.
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Day, J. Patterns in Network Architecture: A Return to Fundamentals; Prentice Hall: Upper Saddle River, NJ, USA, 2008. [Google Scholar]
- Vrijders, S.; Staessens, D.; Colle, D.; Salvestrini, F.; Grasa, E.; Tarzan, M.; Bergesio, L. Prototyping the Recursive Internet Architecture: The IRATI project approach. IEEE Netw. 2014, 28, 20–25. [Google Scholar] [CrossRef]
- Maffione, V.; Salvestrini, F.; Grasa, E.; Bergesio, L.; Tarzan, M. A Software Development Kit to Exploit RINA Programmability. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–7. [Google Scholar]
- IRINA: Investigating RINA as the Next Generation G’EANT and NREN Network Architecture (Online). Available online: https://geant3plus.archive.geant.net/opencall/Optical/Pages/IRINA.aspx (accessed on 19 July 2020).
- Van der Meer, S.; Grasa, E.; Bergesio, L.; Tarzan, M.; Fallon, L.; Keeney, J. Deliverable D2.2: Converged Service Provider Network Design Report; ARCFIRE Project Research Report; European Commission: Brussels, Belgium, May 2017. [Google Scholar]
- Day, J.; Trouva, E.; Grasa, E.; Phelan, P.; De Leon, M.P.; Bunch, S.; Matta, I.; Chitkushev, L.T.; Pouzin, L. Bounding the Router Table Size in an ISP Network Using RINA. In Proceedings of the 2011 International Conference on the Network of the Future, Paris, France, 28–30 November 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 57–61. [Google Scholar]
- Grasa, E.; Bergesio, L.; Tarzan, M.; Lopez, D.; van der Meer, S.; Day, J.; Chitkushev, L. Mobility Management in RINA Networks: Experimental Verification of Architectural Properties. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Lopez, D.; Grasa, E.; Bergesio, L.; Tarzan, M.; van der Meer, S. Deliverable D2.1: Converged Network Operational Environment Report; ARCFIRE Project Research Report; European Commission: Brussels, Belgium, August 2016. [Google Scholar]
- The IRATI Git Repository. (Online). Available online: https://github.com/IRATI (accessed on 19 July 2020).
- Vrijders, S.; Staessens, D.; Capitani, M.; Maffione, V. Python Framework for Automating Largescale Recursive Internet Experiments on GENI and FIRE+. In Proceedings of the IEEE INFOCOM, Honolulu, HI, USA, 15 April 2018; pp. 324–329. [Google Scholar]
- Atlas, A.; Zinin, A. Basic Specification for IP Fast Eeroute: Loop-Free Alternates. In RFC 5286; IETF: Fremont, CA, USA, 2008. [Google Scholar]
- Carpenter BAtkinson, R.; Flinck, H. Renumbering Still Needs Work, Internet Requests for Comments. In RFC 5887; IETF: Fremont, CA, USA, 2010. [Google Scholar]
- Leroy, D.; Bonaventure, O. Preparing network configurations for ipv6 renumbering. Int. J. Netw. Manag. 2009, 19, 415–426. [Google Scholar] [CrossRef]
- Grasa, E.; Bergesio, L.; Tarzan, M.; Lopez, D.; Day, J.; Chitkushev, L. Seamless Network Renumbering in RINA: Automate Address Changes without Breaking Flows! In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Finland, 12–15 June 2017; IEEE: Piscataway, NJ, USA, 2017. [Google Scholar]
- Lee, M.; Sheu, J.P. An efficient routing algorithm based on segment routing in software-defined networking. Comput. Netw. 2016, 103, 44–55. [Google Scholar] [CrossRef]
- Gaixas, S.L.; Perelló, J.; Careglio, D.; Grasa, E.; Tarzán, M. End-user traffic policing for QoS assurance in polyservice RINA networks. Telecommun. Syst. 2018, 70, 365–377. [Google Scholar] [CrossRef]
- Giust, F.; Cominardi, L.; Bernardos, C. Distributed mobility management for future 5G networks: Overview and analysis of existing approaches. IEEE Commun. Mag. 2015, 53, 142–149. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On Multi-Access Edge Computing: A survey of Emerging 5G Network Edge Cloud Architecture and Orchestration. IEEE Commun. Surv. 2017, 19, 1657–1681. [Google Scholar] [CrossRef]
- IRATI Tutorial #11: Distributed Mobility Management: Multiple Providers, Multiple Access Technologies. Available online: https://github.com/IRATI/stack/wiki/Tutorial-11:-DMM-multi-access-ARCFIRE-2018 (accessed on 19 July 2020).
- Staessens, D.; Vrijders, S.; Grasa, E.; Tarzan, M.; van der Meer, S.; Maffione, V.; Carrozzo, G.; Lopez, D.; Day, J. Deliverable D4.4: Execution of Experiments, Analysis of Results and Benchmarking against KPIs; ARCFIRE Project Research Report; European Commission: Brussels, Belgium, June 2016. [Google Scholar]
- Welzl, M.; Teymoori, P.; Gjessing, S.; Islam, S. Follow the Model: How Recursive Networking Can Solve the Internet’s Congestion Control Problems. In Proceedings of the 2020 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 17–20 February 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Thompson, P.; Davies, N. Towards a RINA-based architecture for performance management of large-scale distributed systems. Computers 2020, 9, 53. [Google Scholar] [CrossRef]
- De Leon, M.P.; Ranganathan, R.; Bainbridge, D.; Ramanarayanan, K.; Corston-Petrie, A.; Fundacio, E.G. Multi-Operator IPC VPN Slices: Applying RINA to Overlay Networking. In Proceedings of the RINA Workshop 2019, Colocated with ICIN 2019, Paris, France, 19–21 February 2019. [Google Scholar]
- RIN Armenia Initiative Website. Available online: https://rinarmenia.com/ (accessed on 19 July 2020).
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G.; et al. P4: Programming Protocol-Independent Packet Processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]













| CON Design | with Current Network Architectures | with RINA |
|---|---|---|
| Structure | Different layers, different functions | Different layers, same functions with different policies |
| Functions in different layers are not always independent | Strict layering: layers are black boxes, only the service interface is visible | |
| Fixed and static number of layers, require additional constructs such as tunnelling, virtualization, etc. | Variable number of layers, decided at network design or operation time | |
| Incomplete and/or missing layer service definitions | Consistent and common service definition across layers | |
| Unclear division of functions at each layer, “control” and “data” planes | Precise and consistent structure of the functions within each layer | |
| Protocol Design | Multiple protocols per layer, protocol proliferation | Only two protocol frameworks per layer, configurable via policies |
| Protocols independently designed from each other: high variability | Common functions in all layers, only policies can change: simplicity | |
| Naming, addressing, and routing | Lack of application names: the network uses IP addresses and port numbers to identify applications | Complete naming and addressing architecture, simplifies mobility, and multi-homing of applications |
| Naming the interface instead of the node, making transparent multi-homing and mobility hard to achieve | Addresses assigned to nodes, simplifies multi-homing, and mobility of network connected devices | |
| Network renumbering causes downtime | Transparent network renumbering | |
| No names for layers, no layer directory | Naming DIFs enables application discovery across layers | |
| Mobility and multi-homing | Mobility and multi-homing limited and requires specialized protocols | Mobility and multi-homing achieved via constructs in the architecture |
| Resource allocation and Quality of Service (QoS) | Lack of consistent QoS model, each protocol family has its own | Consistent QoS model across layers, from application to physical layers |
| Only end-to-end congestion control loops—reaction time is maximized | Congestion control loops shorter, closer where congestion occurs | |
| Implicit congestion detection in many cases—false positives and overreaction | Explicit Congestion Detection always, for a precise response | |
| Homogeneous congestion control policies for heterogeneous networks | Per-layer congestion control policies: optimal reaction to congestion in different parts of the network | |
| Security | Most protocol enforce their own security model, introducing complexity | Secure layers instead of individual protocols: consistent security model |
| Use of well-known ports facilitates transport layer attacks | Use of application names, dynamic transport port allocation | |
| Network addresses exposed to applications, facilitates network scanning | Addresses are internal to a layer and never exposed outside of it | |
| Network Management | Too little commonality in network protocols, making management of CONs increasingly complex | Two immutable protocol frameworks and a well-defined set of policies simplify the network structure |
| No well-defined model for the interaction between layers | Consistent service definition and function structuring across layers | |
| Different protocols and object modelling frameworks for network management | Single network management protocol and common layer object model |
| KPI | Part | Specialized KPI | Value | Description |
|---|---|---|---|---|
| Speed | DMS | Network | 4 min | Large, 50 tests |
| Test runs | Create node | P: 85, U: 15, C: 3 | milliseconds | |
| Validate node | P: 85, U: 15, C: 3 | milliseconds | ||
| Scale | Networks | Scale of networks | 2–2110 nodes | Small < 80, Large < 150 |
| 207.300 nodes | Very large > 150 | |||
| 945.400 nodes | Aggregated extra large | |||
| Test runs | DMS | Very low | No requirements on scale | |
| DMS, time and cost | Medium | New APEX distribution | ||
| Complexity | DMS | Lines of Code | 3019 | 2327 Bash, 375 Python |
| Strategy | Lines of Code | All: 3072 Compact JS: 517 | JavaScript(JS): 916 APEX CLI: 840, AVRO: 316 | |
| Networks | Node Complexity | Create: 5–28 min/max (10–6180) | Min/max operations, ms | |
| Validate: 3–48 min/max (6–2037) | Min/max operations, ms | |||
| Network Complexity | 28 to 32468 | Tiny to very large | ||
| Degree of Automation | DMS | Scenario Automation | High but no 100% | Easy to get to 100% |
| Networks | Create Configuration | Very low | Automated with scalingtime | |
| Create Network | 100% | Fully automated | ||
| Create Network Graphs | 100%, Medium | GraphML, post-processing | ||
| Test runs | Complete a test run | Medium | Wait points (race conditions) | |
| Touch | Networks | Manual operations | 0–1, 0–4 | Mandatory, optional |
| Test runs | Manual operations | 122 in 139 networks | With better policies |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vrijders, S.; Staessens, D.; Colle, D.; Grasa, E.; Tarzan, M.; van der Meer, S.; Capitani, M.; Maffione, V.; Lopez, D.; Chitkushev, L.; et al. ARCFIRE: Experimentation with the Recursive InterNetwork Architecture. Computers 2020, 9, 59. https://doi.org/10.3390/computers9030059
Vrijders S, Staessens D, Colle D, Grasa E, Tarzan M, van der Meer S, Capitani M, Maffione V, Lopez D, Chitkushev L, et al. ARCFIRE: Experimentation with the Recursive InterNetwork Architecture. Computers. 2020; 9(3):59. https://doi.org/10.3390/computers9030059
Chicago/Turabian StyleVrijders, Sander, Dimitri Staessens, Didier Colle, Eduard Grasa, Miquel Tarzan, Sven van der Meer, Marco Capitani, Vincenzo Maffione, Diego Lopez, Lou Chitkushev, and et al. 2020. "ARCFIRE: Experimentation with the Recursive InterNetwork Architecture" Computers 9, no. 3: 59. https://doi.org/10.3390/computers9030059
APA StyleVrijders, S., Staessens, D., Colle, D., Grasa, E., Tarzan, M., van der Meer, S., Capitani, M., Maffione, V., Lopez, D., Chitkushev, L., & Day, J. (2020). ARCFIRE: Experimentation with the Recursive InterNetwork Architecture. Computers, 9(3), 59. https://doi.org/10.3390/computers9030059





