The Architecture of the Access Protocols of the Global Infocommunication Resources †
Abstract
:1. Introduction
- -
- Accumulation, consolidation, storage and analysis of all data required for making an informed decision about the vertical handover procedure;
- -
- Selecting the appropriate access radio network from several currently available ones;
- -
- Connecting the terminal device to the new radio network (without losing the existing communication session).
- -
- Analysis of existing solutions used in practice to implement procedures for selecting a suitable access radio network;
- -
- A new, centralized strategy for selecting the access radio network is proposed and a scenario for interaction between terminal devices, aggregating devices, and access radio networks is developed;
- -
- Developed a mathematical model of the process of information interaction on the last mile in the case of using a centralized strategy and selecting a radio access network.
- -
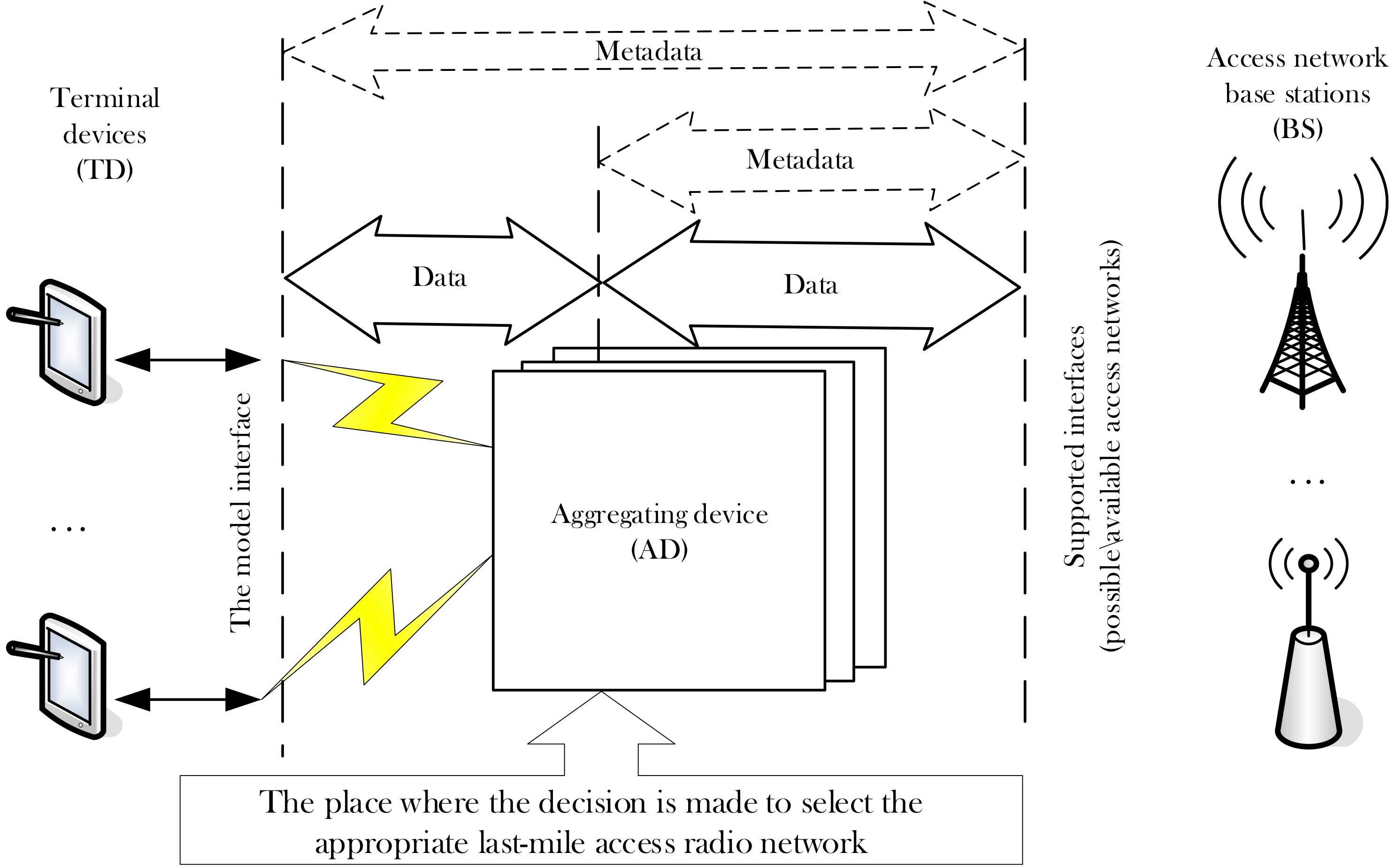
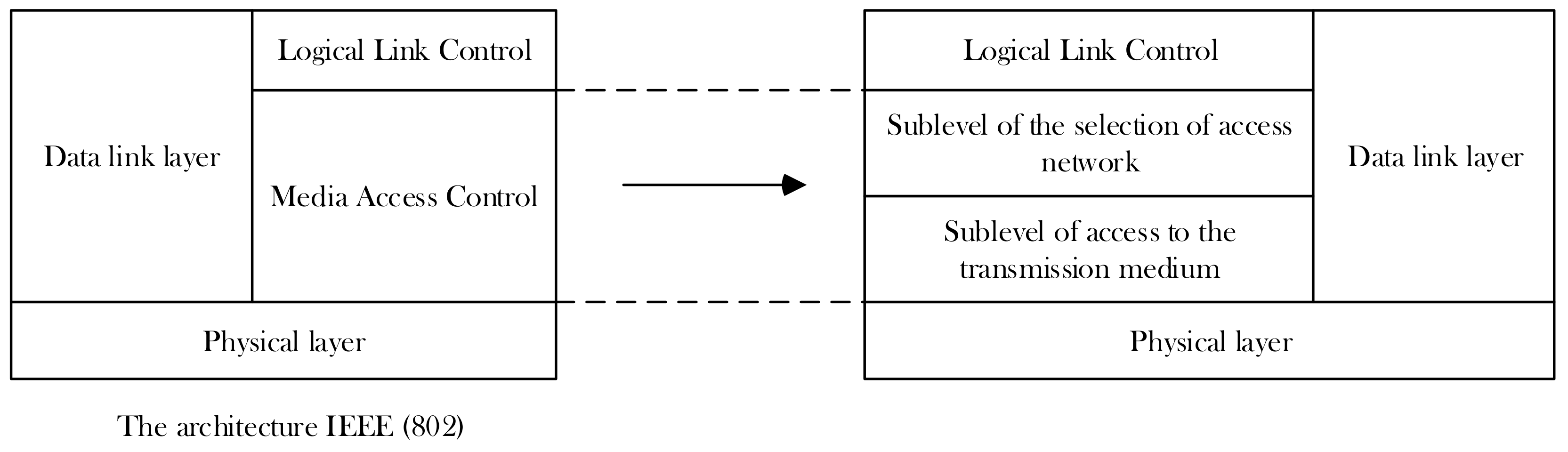
- First, the emphasis is on developing the architecture of protocols for interaction between terminal devices and the base station. The proposed architecture is an extension of the previously known and developed Institute of Electrical and Electronics Engineers architecture described in the 802 group of standards [6].
- -
- Secondly, the problem of studying the impact of traffic restriction procedures at the first stage of access on the probability-time characteristics of the data delivery process from the terminal devices of the base station is solved.
2. Materials and Methods
- -
- Implementation of last-mile access radio network selection;
- -
- Support the transfer of blocks of user data between the interfaces, terminal devices and interfaces in radio networks the last mile.
- -
- Sublevel of the selection of access network;
- -
- Sublevel of access to the transmission medium.
2.1. Step I. Selecting the Radio Network to Access
- -
- Quality of data transmission in the access radio network;
- -
- Terminal devices;
- -
- Resource requirements that depend on the type of telecommunications service;
- -
- Subscriber profile;
- -
- Requirements for safety and reliability.
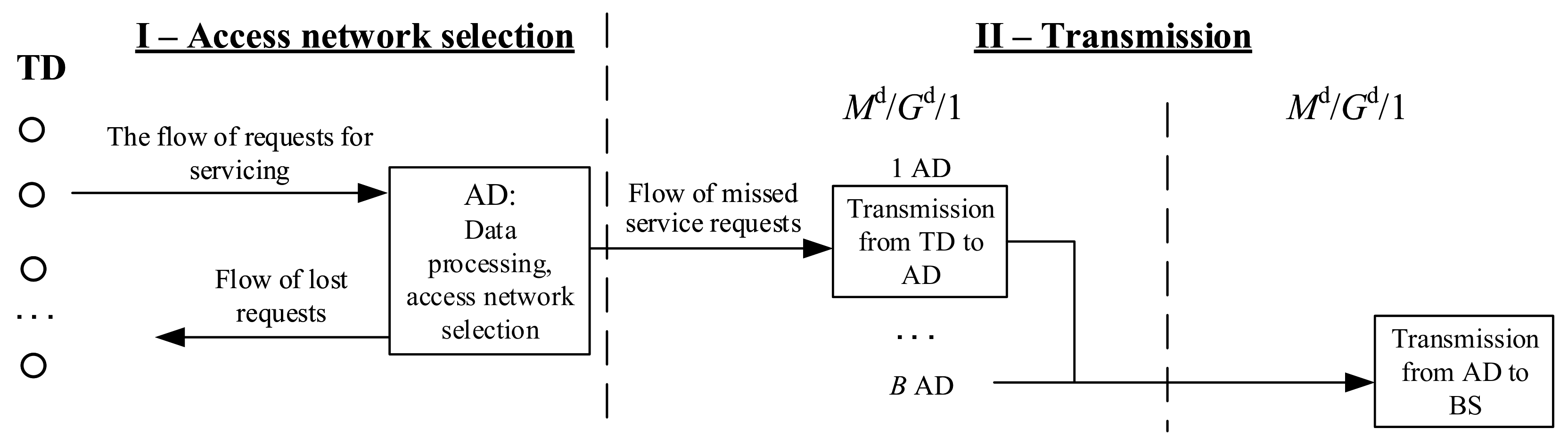
2.2. Step II. Data Transfer from the Terminal Device to the Base Station
- 1
- Simulates the process of transferring user data blocks from/to terminal devices to/from the radio network aggregator;
- 2
- Simulates the process of transmitting user data blocks from/to the aggregator of access radio networks to/from the base station of the selected radio network.
- Intensity of the flow of user data units coming from a single terminal device [1/s];
- D
- The number of terminal devices that are within the range of a single radio network aggregator;
- B
- Number of radio network aggregators;
- N
- Number of access radio networks;
- l
- Length [bits] of user data blocks to transmit;
- p
- Probability of receiving a refusal to provide the service at the Ist step;
- Q = 1-P
- Probability of getting permission to provide the service at step I;
- ,
- Bit rate on phase 1 and 2 [bit/s];
- ,
- Mathematical expectation of the allowed time of information aging at phase 1 and 2, respectively [s].
- –
- At the output of each terminal device for transmitting over the network access to the base station a uniform simple stream of user data blocks is formed l [bit]. Flow intensity [1/s] and it is a Bernoulli flow with the parameter on interval . which we will use as the minimum clock cycle for simulating the transfer of user data blocks in phase 1 = 1/ [s];
- –
- At the output of each radio network aggregator for transmission to the base station, a stream of uniform user data blocks for transmission is formed, which form a Bernoulli-type stream with the parameter on interval which we will use as the minimum clock cycle for simulating the transfer of user data blocks in phase 2 = 1/ [s];
- –
- Direct transmission of user data blocks is performed (i.e., feedback is not provided). Transmitted user data blocks that were damaged in phase 1 and 2 when transmitting over the radio channel are discarded when receiving;
- –
- In the 1st and 2nd phases of the second step of the scenario, multiple access of terminal and aggregating devices to the transmission medium is implemented using TDM technology.
2.2.1. Mathematical Model
2.2.2. Expressions for Calculating Probability-Time Characteristics (PTC)
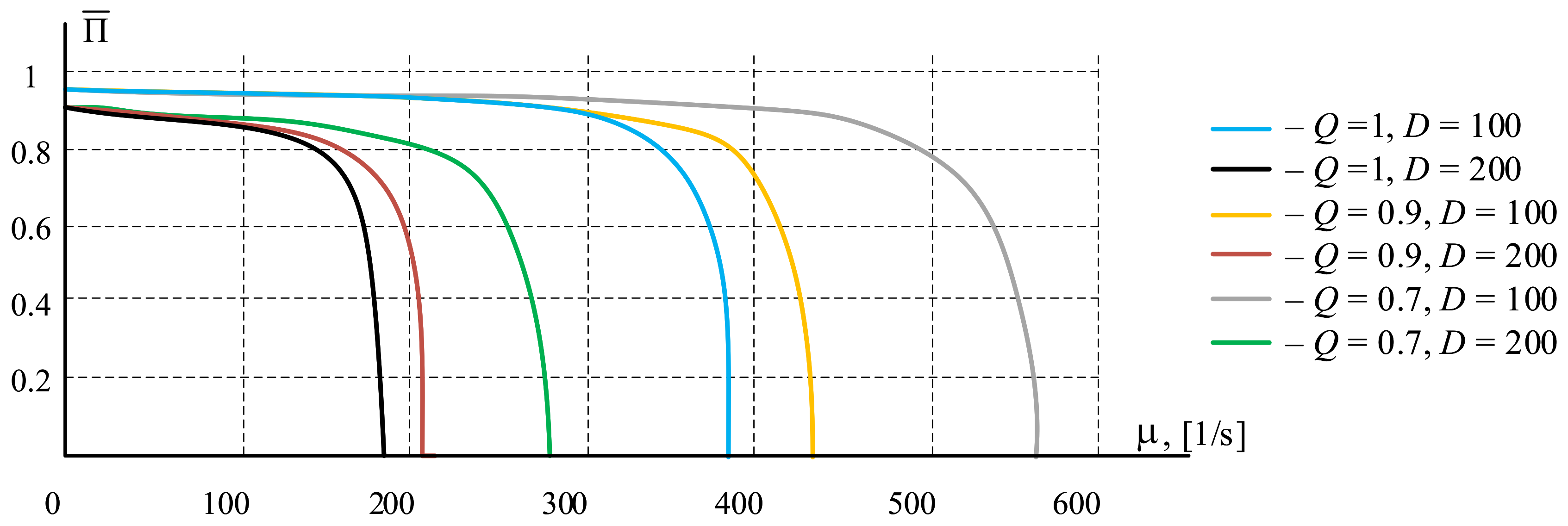
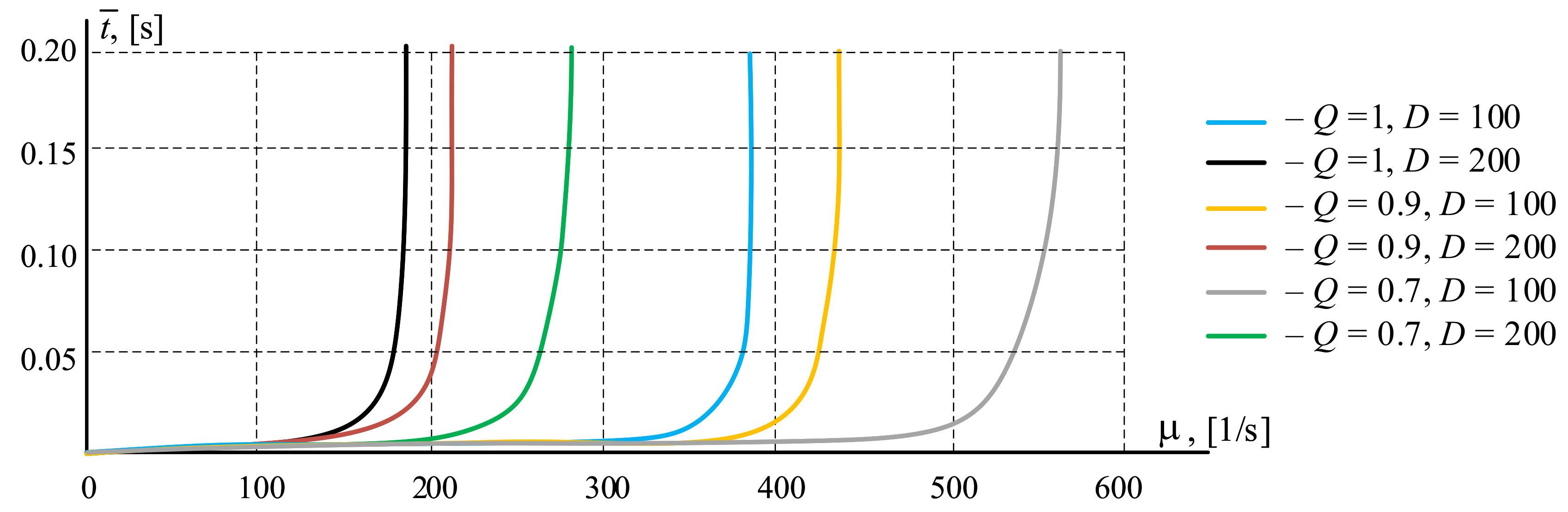
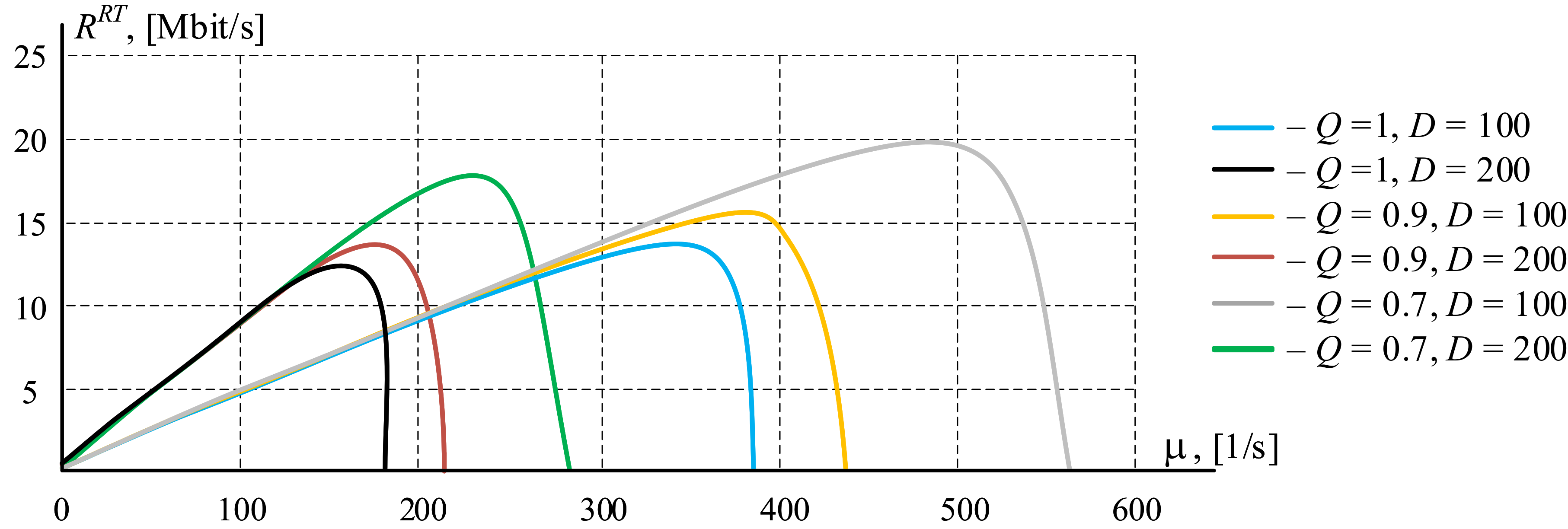
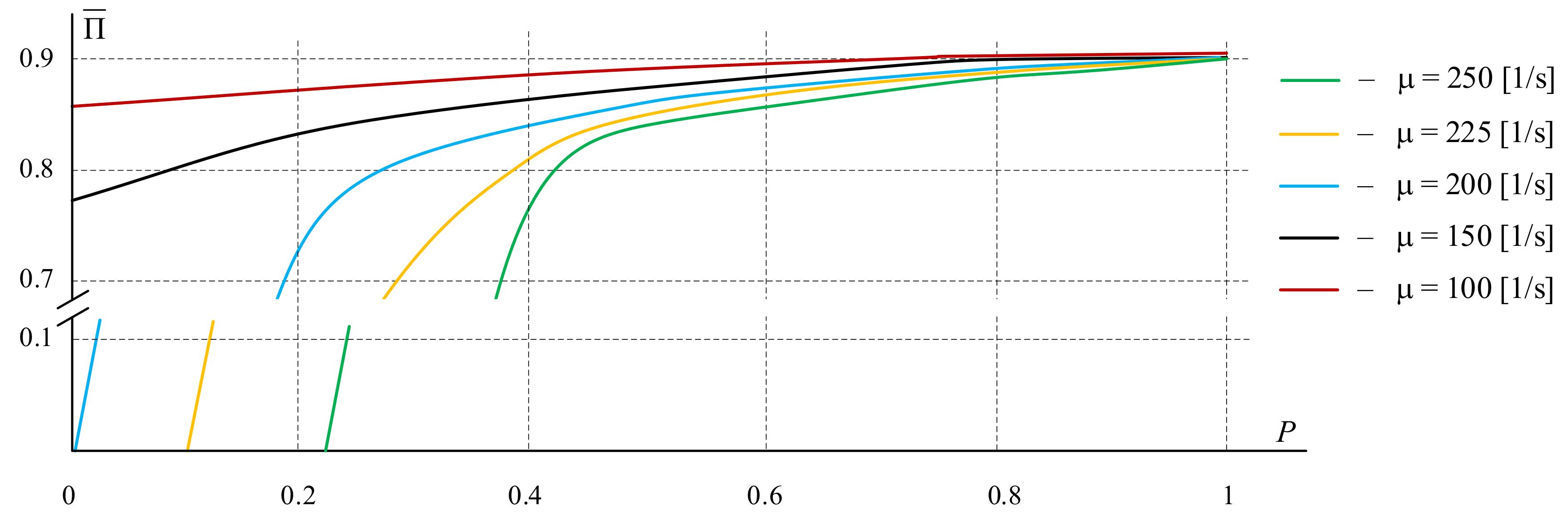
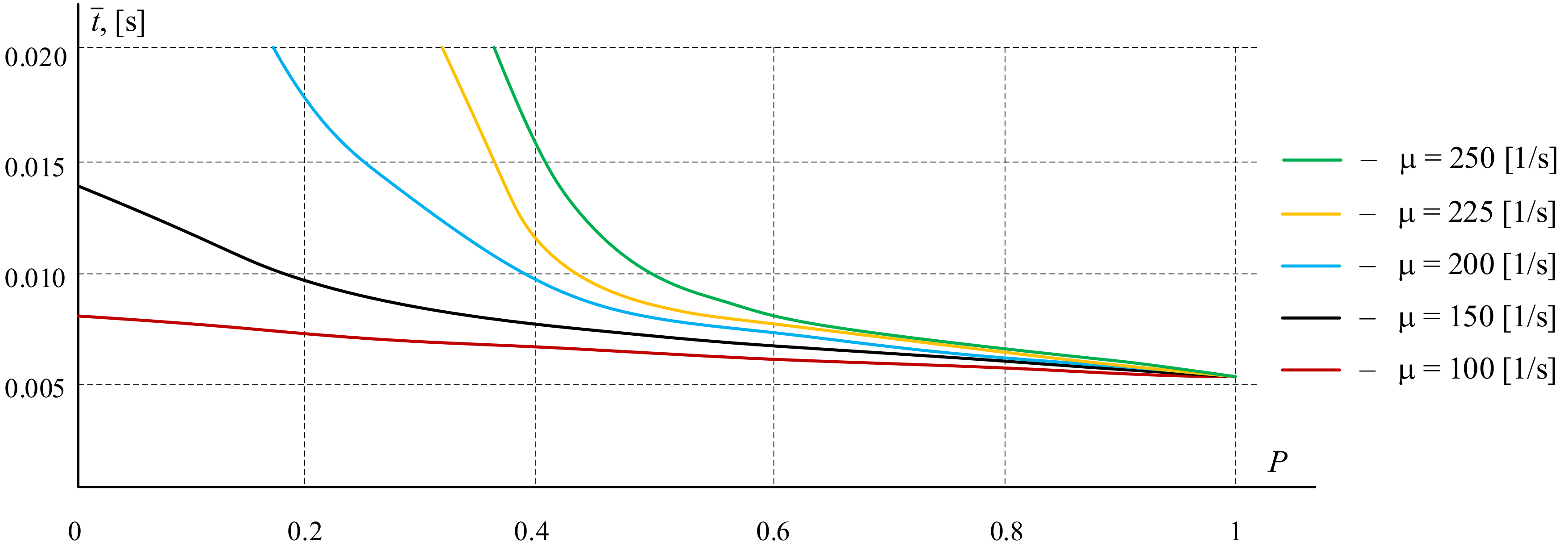
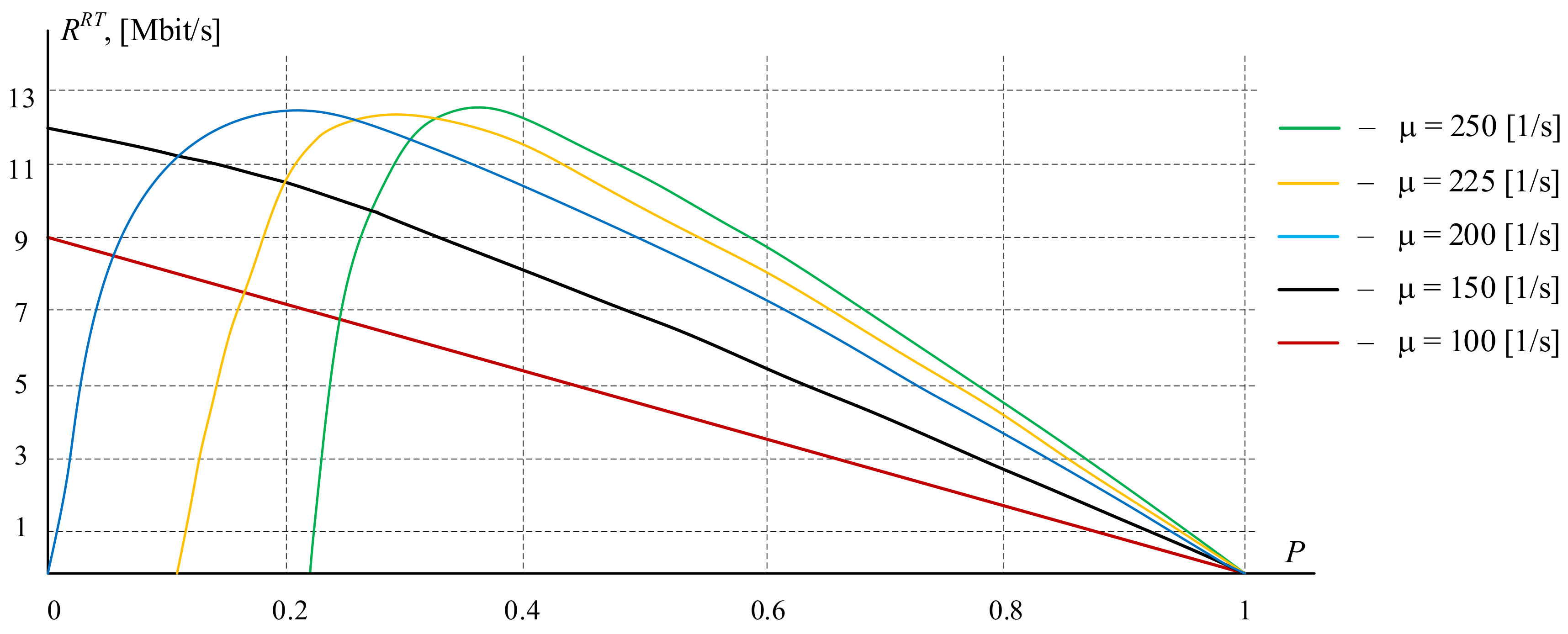
2.2.3. Numerical Experiments
3. Results
- The developed centralized access network architecture differs from the known ones by using special protocols located between the physical and channel levels of the reference model of open systems interaction, which allows solving the problems of vertical handover using a new network element-a hardware and software aggregator, simplifying the schemes of terminal devices and increasing the use of networks in the last mile.
- The sharing architecture of access protocols to global infocommunication devices has been developed, which provides for splitting the access level to the transmission medium (MAC) at the last mile into two sublevels: the sublevel of access network selection and the sublevel of access to the transmission medium. At the selection sub-level, a comprehensive selection of wireless networks from among those that meet the quality of service requirements is implemented.
- A queuing model is obtained that describes the process of interaction between network terminals and the base station through a centralized network element in the form of a two-phase QS, which allows to evaluate the PTC of the data circulation process between the terminals and the base station.
- Numerical experiments were carried out to assess the impact of the data block transfer process on the access network of the procedure for limiting input traffic, which confirmed the effectiveness of using the proposed sharing architecture to improve the quality of transmission, especially in overload mode.
4. Discussion
- -
- Increasing the cost of terminal devices that must implement many protocols and contain special software that can form the criteria and selection procedures;
- -
- Increasing complexity of terminal devices in the process of developing new and new technologies, standards and access procedures, the need to replace functional terminal devices with new ones due to the emergence of new technologies;
- -
- Complex algorithms for interaction of network elements and, as a result, intensive exchange of service traffic using last-mile resources. For example, on LTE networks, service traffic exceeds the intensity of user traffic;
- -
- Increase in energy consumption of terminal devices, which is unacceptable for devices with Autonomous power supply, such as sensory devices of the Internet of things.
- -
- Saving and analyzing data about available wireless access networks;
- -
- Making decisions about choosing the best network according to the available criteria for all communication sessions;
- -
- Dynamic reallocation of network resources between active terminals during their movement in space;
- -
- Overload protection of individual networks,
- -
- Practical implementation of the ABC concept.
- -
- Simple and inexpensive terminal devices—less stringent requirements for hardware and software resources of terminals than with a decentralized approach;
- -
- The volume of service traffic is less than in the case of a decentralized approach;
- -
- As terminal devices can be not only smartphones (people), but also smart things;
- -
- Corresponds to the national 5G launch programs, which involve: combining the resources of Telecom operators in the last mile, forming telecommunications ecosystems, and focusing on simple and inexpensive terminals [17];
- -
- Meets the requirements for future infocommunications formulated in the Future Network concept of IEEE 3001 [18].
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Verzun, N.; Kolbanev, M.; Vorobeva, D. Model of a Centralized Strategy for Selecting the Last Mile Access Network. In Proceedings of the 11th Majorov International Conference on Software Engineering and Computer Systems, Saint Petersburg, Russia, 12–13 December 2019. [Google Scholar]
- Roadmap for the Development of “end-to-end” Digital Technology “Wireless Technology”. 2019. Available online: https://digital.gov.ru/uploaded/files/07102019vrar.pdf (accessed on 25 April 2020).
- Gustafsson, E.; Jonsson, A. Always best connected. IEEE Wirel. Commun. 2003, 10, 49–55. [Google Scholar] [CrossRef]
- Davalos, G.A.; Escobar, L.; Navarro, A. Vertical handoff algorithms—A new approach for performance evaluation. In Proceedings of the IEEE Globecom 2010 Workshop on Ubiquitous Computing and Networks, Miami, FL, USA, 6–10 December 2010; pp. 1724–1728. [Google Scholar]
- Yan, X.; Sekercioglu, A.; Narayanan, S.Y. A survey of vertical handoff decision algorithms in Fourth Generation heterogeneous wireless networks. Comput. Netw. 2010, 11, 1848–1863. [Google Scholar] [CrossRef]
- IEEE 802 LAN/MAN Standards Committee. Available online: http://www.ieee802.org/ (accessed on 25 April 2020).
- Network 2030—A Blueprint of Technology, Applications and Market Drivers Towards the Year 2030 and Beyond; FG-NET-2030; Futurewei Technologies, Inc.: Santa Clara, CA, USA, 2019.
- Verzun, N.A.; Kolbanev, M.O.; Omelyan, A.V. Controlled multiple access in wireless network of smart things. Omsk. Sci. Bull. 2016, 4, 147–151. [Google Scholar]
- Bogatyrev, V.A.; Bogatyrev, S.V.; Bogatyrev, A.V. Model and Interaction Efficiency of Computer Nodes Based on Transfer Reservation at Multipath Routing. In Proceedings of the 2019 Wave Electronics and its Application in Information and Telecommunication Systems (WECONF), St. Petersburg, Russia, 3–7 June 2019. [Google Scholar]
- Bogatyrev, A.V.; Bogatyrev, S.V.; Bogatyrev, V.A. Analysis of the timeliness of redundant service in the system of the parallel-series connection of nodes with unlimited queues. In Proceedings of the 2018 Wave Electronics and its Application in Information and Telecommunication Systems (WECONF), St. Petersburg, Russia, 26–30 November 2018. [Google Scholar]
- Astakhova, T.; Verzun, N.; Kolbanev, M.; Shamin, A. A model for estimating energy consumption seen when nodes of ubiquitous sensor networks communicate information to each other. In Proceedings of the 10th Majorov International Conference on Software Engineering and Computer Systems, Saint Petersburg, Russia, 12–13 December 2019. [Google Scholar]
- Astakhova, T.N.; Verzun, N.A.; Kasatkin, V.V.; Kolbanev, M.O.; Shamin, A.A. Sensor network connectivity models. Informatsionno Upr. Sist. 2019, 5, 38–50. [Google Scholar] [CrossRef]
- Grebeshkov, A.Y. Method of selecting a communication network to provide a service using a multifunctional subscriber device. Electrosvyaz 2011, 4, 53–55. [Google Scholar]
- Grebeshkov, A.Y. Making a decision to provide a service with using a multifunctional SDR subscriber terminal in cognitive communication networks. In Proceedings of the VI Branchscientic and Technical Conference “Information society Technologies”, Moscow, Russia, 3–4 March 2012; pp. 120–124. [Google Scholar]
- IEEE Standard for Local and Metropolitan Area Networks—Part 21: Media Independent Handover. Available online: http://www.ieee802.org/21 (accessed on 25 April 2020).
- O Svyazi [About the Connection]; Federal Law of Russia; Russian Government: Moscow, Russia, 2003.
- 5G na Poroge. Available online: https://www.rspectr.com/articles/521/5g-na-poroge (accessed on 25 April 2020).
- Y 3001: Objectives and Design Goals. Available online: https://www.itu.int/itu-t/recommendations/rec.aspx?rec=11083 (accessed on 25 April 2020).
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Verzun, N.; Kolbanev, M.; Shamin, A. The Architecture of the Access Protocols of the Global Infocommunication Resources. Computers 2020, 9, 49. https://doi.org/10.3390/computers9020049
Verzun N, Kolbanev M, Shamin A. The Architecture of the Access Protocols of the Global Infocommunication Resources. Computers. 2020; 9(2):49. https://doi.org/10.3390/computers9020049
Chicago/Turabian StyleVerzun, Natalya, Mikhail Kolbanev, and Alexey Shamin. 2020. "The Architecture of the Access Protocols of the Global Infocommunication Resources" Computers 9, no. 2: 49. https://doi.org/10.3390/computers9020049
APA StyleVerzun, N., Kolbanev, M., & Shamin, A. (2020). The Architecture of the Access Protocols of the Global Infocommunication Resources. Computers, 9(2), 49. https://doi.org/10.3390/computers9020049




