Cloud Computing Security: A Survey
Abstract
:1. Introduction
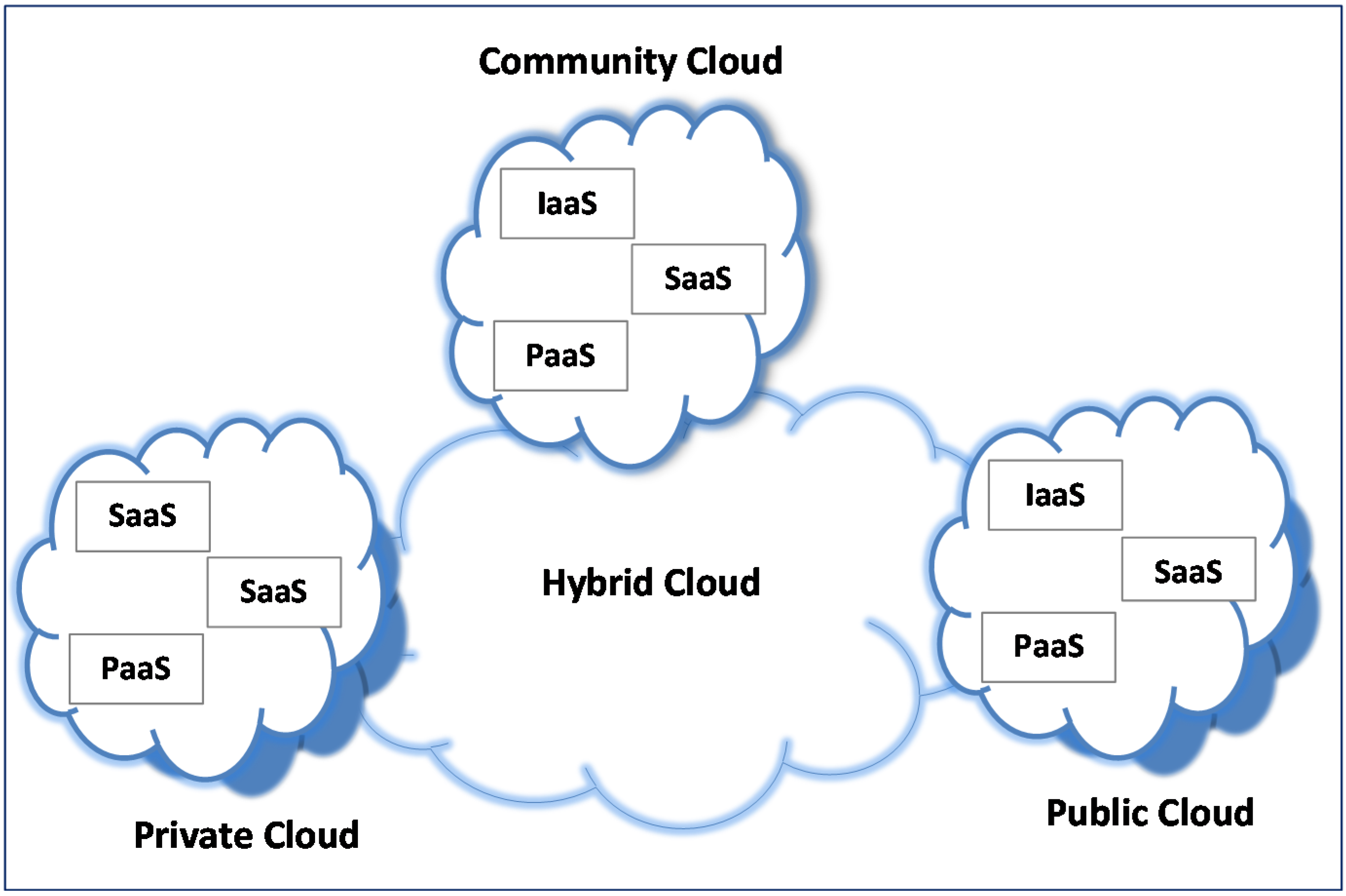
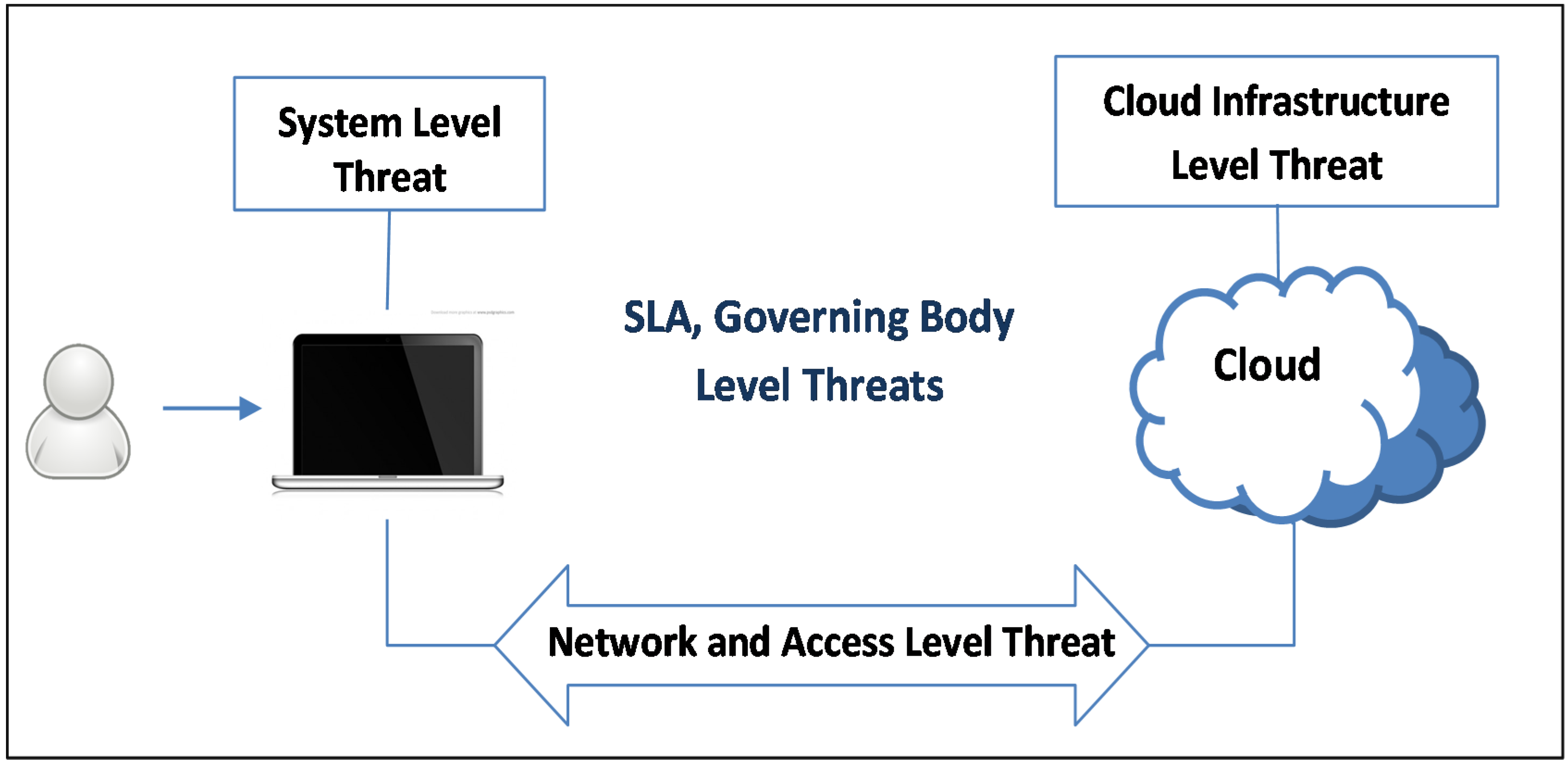
2. Cloud Security Categories, Issues and Dependencies
2.1. Categories and Issues
- (C1)
- The Security Standards category deals with regulatory authorities and governing bodies that define cloud security policies to ensure secure working environment over the clouds. It includes service level agreements, auditing and other agreements among users, service provider and other stakeholders.
- (C2)
- The Network category refers to the medium through which the users connect to cloud infrastructure to perform the desired computations. It includes browsers, network connections and information exchange through registration.
- (C3)
- The Access Control category is a user-oriented category and includes identification, authentication and authorization issues.
- (C4)
- The Cloud Infrastructure category includes security issues within SaaS, PaaS and IaaS and is particularly related with virtualization environment.
- (C5)
- The Data category covers data integrity and confidentiality issues.
| No. | Category | Description |
|---|---|---|
| C1 | Security Standards | Describes the standards required to take precaution measures in cloud computing in order to prevent attacks. It governs the policies of cloud computing for security without compromising reliability and performance. |
| C2 | Network | Involves network attacks such as Connection Availability, Denial of Service (DoS), DDoS, flooding attack, internet protocol vulnerabilities, etc. |
| C3 | Access Control | Covers authentication and access control. It captures issues that affect privacy of user information and data storage. |
| C4 | Cloud Infrastructure | Covers attacks that are specific to the cloud infrastructure (IaaS, PaaS and SaaS) such tampered binaries and privileged insiders. |
| C5 | Data | Covers data related security issues including data migration, integrity, confidentiality, and data warehousing. |
| Category | Label | Issues |
|---|---|---|
| Security Standards | I1 | Lack of security standards |
| I2 | Compliance risks | |
| I3 | Lack of auditing | |
| I4 | Lack of legal aspects (Service level agreement) | |
| I5 | Trust | |
| Network | I6 | Proper installation of network firewalls |
| I7 | Network security configurations | |
| I8 | Internet protocol vulnerabilities | |
| I9 | Internet Dependence | |
| Access | I10 | Account and service hijacking |
| I11 | Malicious insiders | |
| I12 | Authentication mechanism | |
| I13 | Privileged user access | |
| I14 | Browser Security | |
| Cloud Infrastructure | I15 | Insecure interface of API |
| I16 | Quality of service | |
| I17 | Sharing technical flaws | |
| I18 | Reliability of Suppliers | |
| I19 | Security Misconfiguration | |
| I20 | Multi-tenancy | |
| I21 | Server Location and Backup | |
| Data | I22 | Data redundancy |
| I23 | Data loss and leakage | |
| I24 | Data location | |
| I25 | Data recovery | |
| I26 | Data privacy | |
| I27 | Data protection | |
| I28 | Data availability |
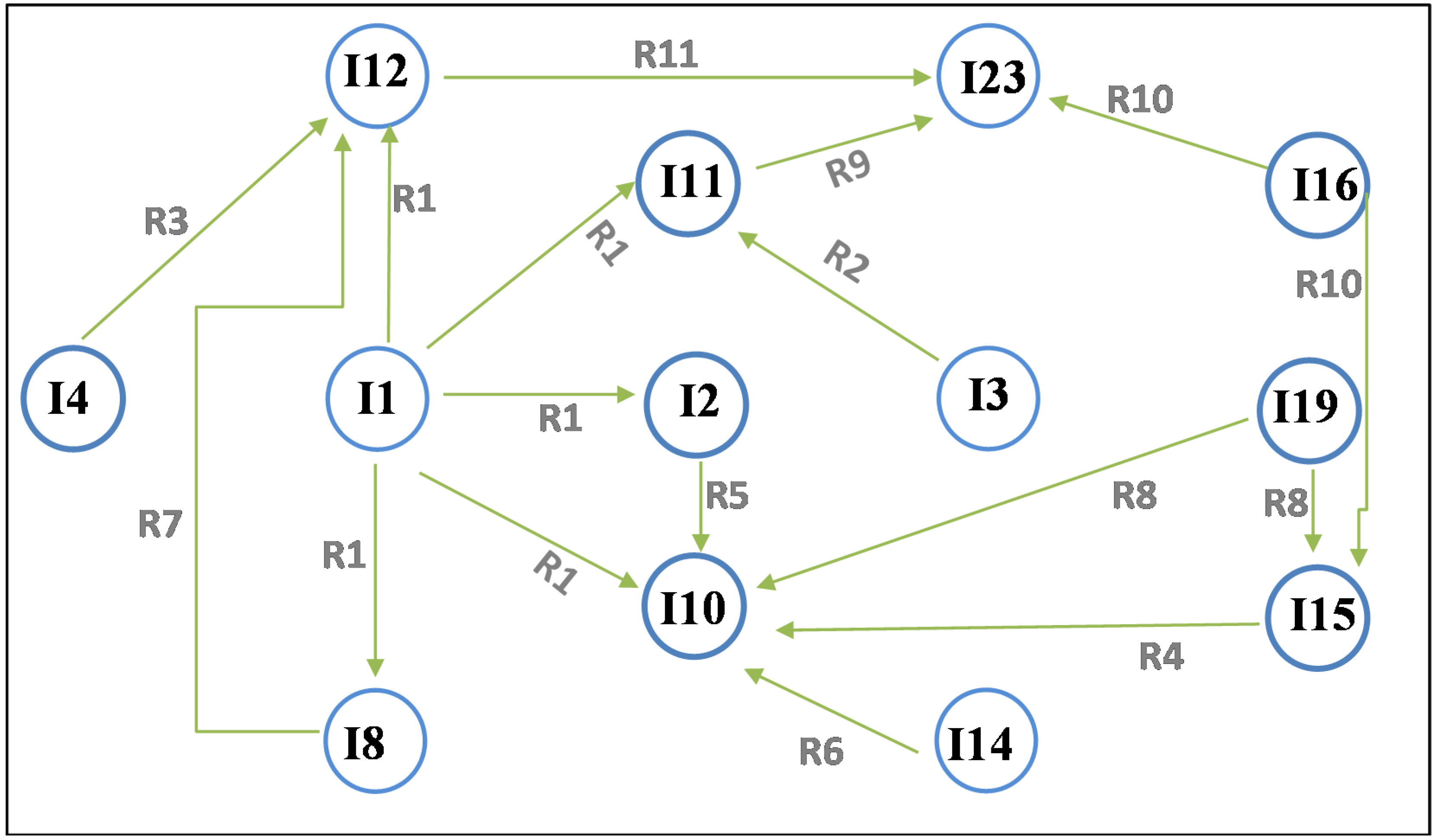
2.2. Dependencies among Cloud Security Categories and Issues
| Text Extraction (from Primary Studies) | Problems Coded | Identified Rule | Rule Description |
|---|---|---|---|
| Account and service hijacking involves phishing, fraud and software vulnerabilities where attackers steal credentials and gain an unauthorized access to server [1]. |
| Account and service hijacking → Data Loss and Leakage | Account and service hijacking increase the possibility of data loss and leakage |
| Insecure interface of API (customers use these APIs to connect to cloud) which can expose organization to several threats such as unauthorized access, content transmission [1] |
| Insecure interface of API’s → authentication mechanism weakness, Data Loss and Leakage | Insecure interface of API’s leads to increase in the probability of information leakage and the weakness of the authentication mechanism. |
| No. | Rules | Sample References |
|---|---|---|
| 1 | Lack of security standard (I1) → compliance risks (I2), account and service hijacking (I10), internet protocol vulnerabilities (I8), malicious insider (I11), authentication mechanisms weakness (I12) | [1,4,7,41,42] |
| 2 | Lack of auditing (I3) → malicious insider (I11) | [7,37,39,41,44,45] |
| 3 | Lack of legal aspects (Service level agreement) (I4) → authentication mechanism weakness (I12) | [1,2,4,19,32,46] |
| 4 | Insecure interface of API (I15) → account and service hijacking (I10) | [1,4] |
| 5 | Compliance risk (I2) → account and service hijacking (I10) | [41] |
| 6 | Weak Browser security (I14) → account and service hijacking (I10) | [4,41] |
| 7 | Internet protocol vulnerabilities (I8) → authentication mechanism weakness (I12) | |
| 8 | Security misconfiguration (I19) → insecure interfaces of API (I15), account and service hijacking (I10) | [4,41,42,43] |
| 9 | Malicious insider (I11) → Data loss and Leakage (123) | [6,33] |
| 10 | Lack of quality of service (I16) → insecure interfaces of API (I15), Data loss and Leakage (I23) | [4,6,33,41,43] |
| 11 | Authentication mechanism weakness (I12) → Data loss and Leakage (123) | [6,33] |
3. Known Attacks and Countermeasures: An Evaluation
3.1. Theft of Service Attacks
| Sr. # | Attack Name | Attack Incidents | Consequences | Category | Vulnerability/ Caused by | Sample References |
|---|---|---|---|---|---|---|
| 1 | Theft-of-service |
| Cloud Infrastructure | I1, I3, I6, I8, I11, I14, I19 | [37,44] | |
| 2 | Denial of service | DDoS |
| Network, Cloud Infrastructure | I1, I3, I10, I14, I19 | [34,49] |
| Http-Based DDoS | ||||||
| Xml-Based DDoS | ||||||
| REST-Based-DDoS | ||||||
| Shrew attack (light traffic) DoS) | ||||||
| 3 | Cloud malware injection |
| Cloud Infrastructure | I7, I11, I13, I15 | [44,50,51,52] | |
| 4 | Cross VM side channels | Timing side channels |
| Cloud Infrastructure | I15, I19 | [53,54,55] |
| Energy-consumption side channels | ||||||
| 5 | Targeted shared memory |
| Cloud Infrastructure | I1, I3, I10, I15, I19, | [53,56,57] | |
| 6 | Phishing |
| Cloud Infrastructure, Network, Access | I1, I6, I8, I10, I12, I14 | [58,59] | |
| 8 | Audio Steganography |
| Cloud infrastructure, Access, | I1, I3, I6, I10, I14, I19 | [62,63] | |
| 9 | VM rollback attack |
| Cloud Infrastructure, Access | I1, I3, I6, I10, I14, I19 | [64,65] |
3.2. Denial of Service Attacks
- Sensor: It monitors the incoming request messages. If it identifies that there is hypothetical increase in number of messages coming from same or particular consumer, it marks it as suspicious.
- HOP Count filter: It will count the hop count value (how many nodes, does message traverse from source to destination) and compare it with pre-defined HOP count. If a difference is found, it means that the header or the message has been modified on hacker machine and thus is marked suspicious.
- IP Frequency Divergence: Marks a message suspicious, if there is same frequency of IP messages.
- Double Signature: It doubles the XML signature: one in header and one in bottom. In case of attack, both XML signatures need to be verified.
- Puzzle Solver: It deals with some intelligent puzzles, where results should be imbedded in some Simple Object Access Protocol (SOAP) header. In case of attack (HTTP DDoS), the cloud defender will send back the puzzle to IP, from which it is receiving messages. If the cloud defender received back the solved puzzle then the request is deemed legitimate, otherwise it is marked as HTTP DDoS attack.
3.3. Malware Injection Attacks
- Antivirus as a network service: the detection capabilities by host-based antivirus can be more efficiently and effectively provided as cloud-network-service. Each host runs a light weight process to detect new files and then sends them to network service for quarantine and for further analysis rather than running complex analysis software on each end-host.
- N-version protection: malicious software identification is determined by multiple heterogonous detection engines in parallel similar to the idea of N-version programming. The notion of N-version protection has been provided in this solution so that the malware detection system should leverage detection capabilities of multiple heterogeneous detection engines to determine malicious and unwanted files more effectively. However, the number of false positives encountered during normal operations increase compared to 1-version engines. To manage the false positives, the administrator has to set a trade-off between coverage (a single detector is enough to mark a file as malicious) and false positives (a consensus of a number of detectors is required to mark a file as malicious).
3.4. Cross VM Side-Channel Attacks
3.6. Phishing Attacks
3.7. Botnet Attacks (Stepping-Stone Attack)
3.8. Audio Steganography Attacks
3.9. VM Rollback Attacks
4. Comparative Evaluation of Well-Known General Cloud Security Mechanisms
4.1. Intrusion Detection Systems (IDS)
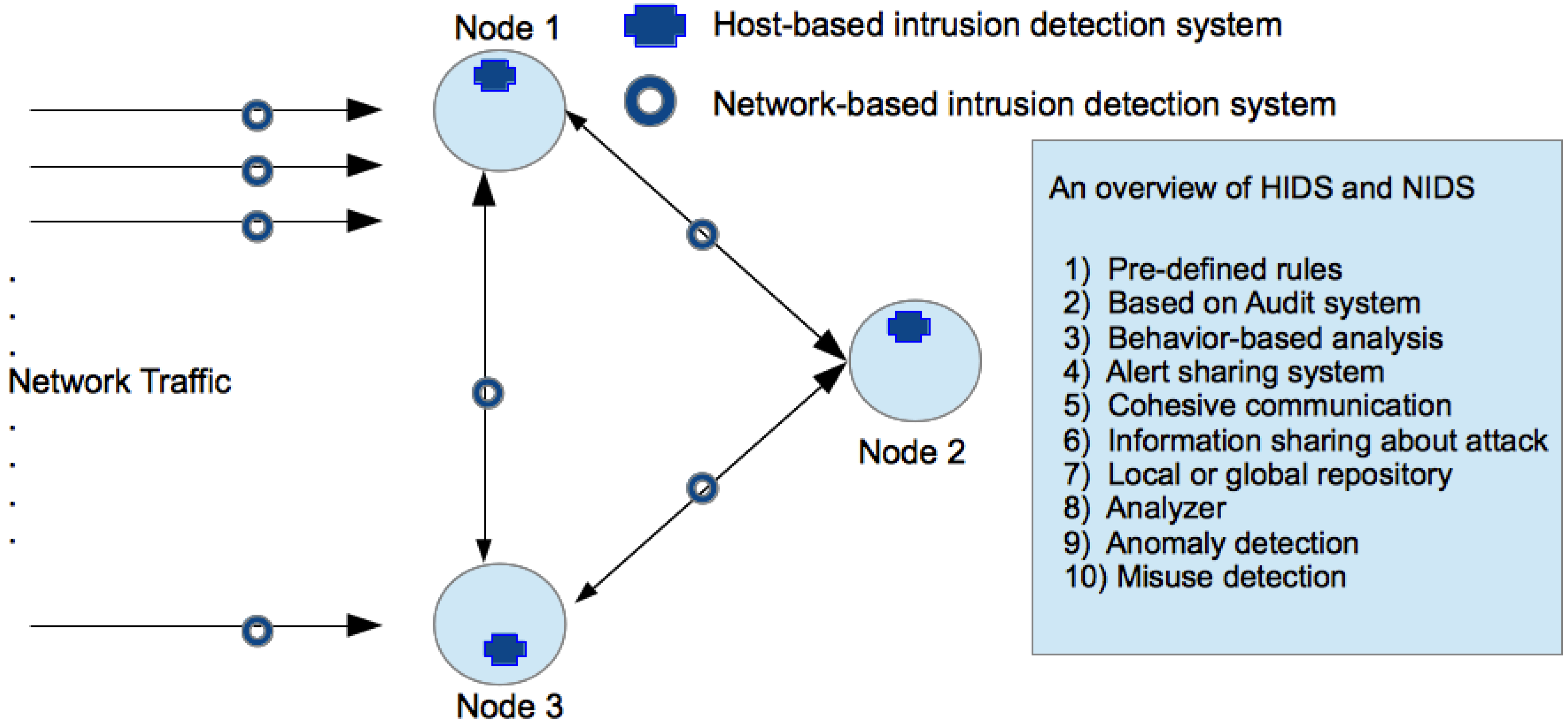
4.2. Autonomous Systems
4.3. Federated Identity Management System
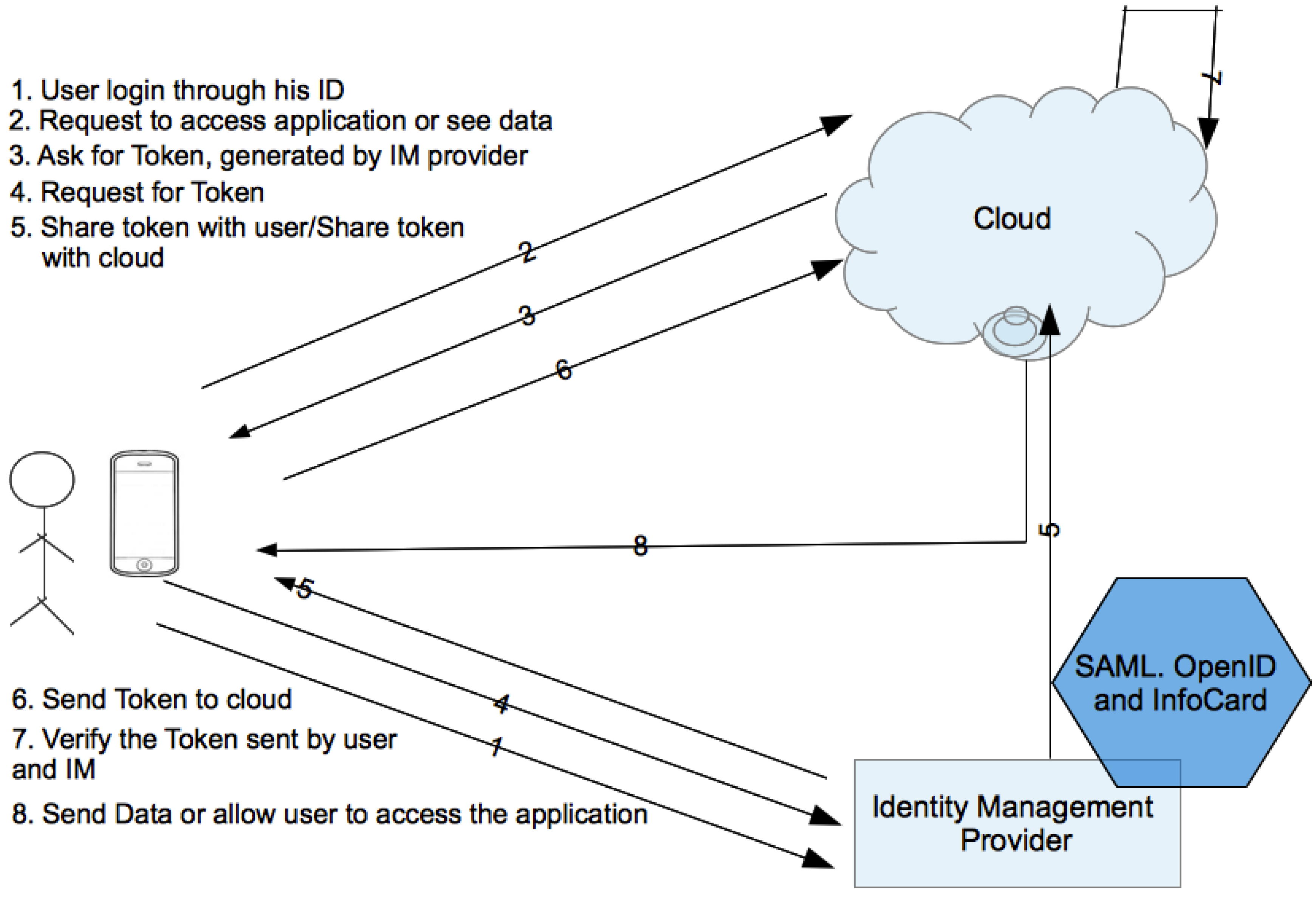
5. Discussion
6. Conclusions
Conflicts of Interest
References
- Tripathi, A.; Mishra, A. Cloud computing security considerations. In Proceedings of the 2011 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Xi’an, China, 14–16 September 2011; pp. 1–5.
- Wang, J.-J.; Mu, S. Security issues and countermeasures in cloud computing. In Proceedings of the 2011 IEEE International Conference on Grey Systems and Intelligent Services (GSIS), Nanjing, China, 15–18 September 2011; pp. 843–846.
- Final Version of NIST Cloud Computing Definition Published. Available online: http://www.nist.gov/itl/csd/cloud-102511.cfm (accessed on 25 August 2013).
- Lv, H.; Hu, Y. Analysis and research about cloud computing security protect policy. In Proceedings of the 2011 International Conference on Intelligence Science and Information Engineering (ISIE), Wuhan, China, 20–21 August 2011; pp. 214–216.
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing; NIST: USA USA. , 2009. available at: http://csrc.nist.gov/publications/nistpubs/800-145/SP800-145.pdf.
- Jain, P.; Rane, D.; Patidar, S. A survey and analysis of cloud model-based security for computing secure cloud bursting and aggregation in renal environment. In Proceedings of the 2011 World Congress on Information and Communication Technologies (WICT), Mumbai, India, 11–14 December 2011; pp. 456–461.
- Gowrigolla, B.; Sivaji, S.; Masillamani, M.R. Design and auditing of cloud computing security. In Proceedings of the 2010 5th International Conference on Information and Automation for Sustainability (ICIAFs), Colombo, Sri Lanka, 17–19 December 2010; pp. 292–297.
- Houmansadr, A.; Zonouz, S.A.; Berthier, R. A cloud-based intrusion detection and response system for mobile phones. In Proceedings of the 2011 IEEE/IFIP 41st International Conference on Dependable Systems and Networks Workshops (DSN-W), Hong Kong, China, 27–30 June 2011; pp. 31–32.
- Gu, C.-D.; Li, J.-X.; Wu, J.-P.; Fu, Y.-L.; Lu, K.; Si, M.-X. Wireless broadband application technology investigation of IPv6 optical network cloud computing. In Proceedings of the 2010 6th International Conference on Advanced Information Management and Service (IMS), Seoul, Korea, 30 November–2 December 2010; pp. 191–194.
- Sabahi, F. Virtualization-level security in cloud computing. In Proceedings of the 2011 IEEE 3rd International Conference on Communication Software and Networks (ICCSN), Xi’an, China, 27–29 May 2011; pp. 250–254.
- Wang, C.; Wang, Q.; Ren, K.; Lou, W. Towards secure and dependable storage services in cloud computing. IEEE Trans. Serv. Comput. 2012, 5, 220–232. [Google Scholar] [CrossRef]
- Lingfeng, C.; Hoang, D.B. Towards scalable, fine-grained, intrusion-tolerant data protection models for healthcare cloud. In Proceedings of the 2011 IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Changsha, China, 16–18 November 2011; pp. 126–133.
- Morin, J.; Aubert, J.; Gateau, B. Towards cloud computing SLA risk management: Issues and challenges. In Proceedings of the 2012 45th Hawaii International Conference on System Science (HICSS), Maui, HI, USA, 4–7 January 2012; pp. 5509–5514.
- Khalil, I.M. ELMO: Energy aware local monitoring in sensor networks. IEEE Trans. Dependable Secur. Comput. 2011, 8, 523–536. [Google Scholar] [CrossRef]
- Khalil, I.; Bagchi, S. MISPAR: Mitigating stealthy packet dropping in locally-monitored multi-hop wireless Ad Hoc networks. In Proceedings of the 4th International Conference on Security and Privacy in Communication Netowrks (SecureComm ’08), Istanbul, Turkey, 22–25 September 2008; ACM: New York, NY, USA, 2008. article 28. 1–10. [Google Scholar]
- Khalil, I. MCC: Mitigating colluding collision attacks in wireless sensor networks. In Proceedings of the 2010 IEEE Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–5.
- Hayajneh, M.; Khalil, I.; Gadallah, Y. An OFDMA-based MAC protocol for under water acoustic wireless sensor network. In Proceedings of the 2009 ACM International Conference on Wireless Communications and Mobile Computing (IWCMC’09), Leipzig, Germany, June 21 – 24 2009; pp. 810–814.
- Khalil, I.; Hayajneh, M.; Awad, M. SVNM: Secure verification of neighborhood membership in static multi-hop wireless networks. In Proceedings of the IEEE Symposium on Computers and Communications, 2009, ISCC 2009, Sousse, 5–8 July 2009; pp. 368–373.
- Sengupta, S.; Kaulgud, V.; Sharma, V.S. Cloud computing security—Trends and research directions. In Proceedings of the 2011 IEEE World Congress on Services (SERVICES), Washington, DC, USA, 4–9 July 2011; pp. 524–531.
- Chow, R.; Golle, P.; Jakobsson, M.; Shi, E.; Staddon, J.; Masuoka, R.; Molina, J. Controlling data in the cloud: Outsourcing computation without outsourcing control. In Proceedings of the 2009 ACM Workshop on Cloud Computing Security, Chicago, IL, USA, 13 November 2009; ACM Press: New York, NY, USA, 2009; pp. 85–90. [Google Scholar]
- Samarati, P.; di Vimercati, S.D.C. Data protection in outsourcing scenarios: Issues and directions. In Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security (ASIACCS ’10), Chicago, IL, USA, 4–8 October 2010; ACM: New York, NY, USA, 2010; pp. 1–14. [Google Scholar]
- Popovic, O.; Jovanovic, Z.; Jovanovic, N.; Popovic, R. A comparison and security analysis of the cloud computing software platforms. In Proceedings of the 2011 10th International Conference on Telecommunication in Modern Satellite Cable and Broadcasting Services (TELSIKS), Nis, Serbia, 5–8 October 2011; Volume 2, pp. 632–634.
- Gul, I.; ur Rehman, A.; Islam, M.H. Cloud computing security auditing. In Proceedings of the 2011 The 2nd International Conference on Next Generation Information Technology (ICNIT), Gyeongju, Korea, 21–23 June 2011; pp. 143–148.
- Kandukuri, B.R.; Paturi, V.R.; Rakshit, A. Cloud security issues. In Proceedings of the IEEE International Conference on Services Computing, 2009 (SCC ’09), Bangalore, India, 21–25 September 2009; pp. 517–520.
- Chen, Z.; Yoon, J. IT auditing to assure a secure cloud computing. In Proceedings of the 2010 6th World Congress on Services (SERVICES-1), Miami, FL, USA, 5–10 July 2010; pp. 253–259.
- Ryan, G.W.; Bernard, H.R. Data Management and Analysis Methods. Available online: http://www.rand.org/pubs/external_publications/EP20000033.html (accessed on 25 August 2013).
- Holloway, I.; Todres, L. The status of method: Flexibility, consistency and coherence. Qual. Res. 2003, 3, 345–357. [Google Scholar] [CrossRef]
- Hashizume, K.; Rosado, D.G.; Fernández-Medina, E.; Fernandez, E.B. An analysis of security issues for cloud computing. J. Internet Serv. Appl. 2013, 4, 5. [Google Scholar]
- Zissis, D.; Lekkas, D. Addressing cloud computing security issues. Future Gener. Comput. Syst. 2012, 28, 583–592. [Google Scholar] [CrossRef]
- Md Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2013. [Google Scholar] [CrossRef]
- Braun, V.; Clarke, V. Using thematic analysis in psychology. Qual. Res. Psychol. 2006, 3, 77–101. [Google Scholar] [CrossRef]
- A Survey on Cloud Computing Security, Challenges and Threats|Whitepapers|TechRepublic. Available online: http://www.techrepublic.com/whitepapers/a-survey-on-cloud-computing-security-challenges-and-threats/3483757 (accessed on 18 March 2012).
- Thalmann, S.; Bachlechner, D.; Demetz, L.; Maier, R. Challenges in cross-organizational security management. In Proceedings of the 2012 45th Hawaii International Conference on System Science (HICSS), Maui, HI, USA, 4–7 January 2012; pp. 5480–5489.
- Riquet, D.; Grimaud, G.; Hauspie, M. Large-scale coordinated attacks: Impact on the cloud security. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Palermo, Italy, 4–6 July 2012; pp. 558–563.
- Gonzalez, N.; Miers, C.; Redigolo, F.; Carvalho, T.; Simplicio, M.; Naslund, M.; Pourzandi, M. A quantitative analysis of current security concerns and solutions for cloud computing. In Proceedings of the 2011 IEEE Third International Conference on Cloud Computing Technology and Science (CloudCom), Athens, Greece, 29 November–1 December 2011; pp. 231–238.
- Rachel Suresh, N.; Mathew, S.V. Security concerns for cloud computing in aircraft data networks. In Proceedings of the 2011 International Conference for Internet Technology and Secured Transactions (ICITST), Abu Dhabi, United Arab Emirates, 11–14 December 2011; pp. 132–136.
- Fangfei, Z.; Goel, M.; Desnoyers, P.; Sundaram, R. Scheduler vulnerabilities and coordinated attacks in cloud computing. In Proceedings of the 2011 10th IEEE International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 25–27 August 2011; pp. 123–130.
- Who Can You Trust in the Cloud? A Review of Security Issues within Cloud Computing. Available online: http://www.drjeffdaniels.com/1/post/2011/10/who-can-you-trust-in-the-cloud-a-review-of-security-issues-within-cloud-computing.html (accessed on 18 March 2012).
- Mollet, N.G. Cloud Computing Security. Bachelor of Engineering Degree Information Technology Thesis, Helsinki Metropolia University of Applied Sciences, Helsinki, Finland, 11 April 2011. [Google Scholar]
- Behl, A. Emerging security challenges in cloud computing: An insight to cloud security challenges and their mitigation. In Proceedings of the 2011 World Congress on Information and Communication Technologies (WICT), Mumbai, India, 11–14 December 2011; pp. 217–222.
- Mathisen, E. Security challenges and solutions in cloud computing. In Proceedings of the 2011 5th IEEE International Conference on Digital Ecosystems and Technologies Conference (DEST), Daejeon, Korea, 31 May–3 June 2011; pp. 208–212.
- Bhardwaj, A.; Kumar, V. Cloud security assessment and identity management. In Proceedings of the 2011 14th International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 22–24 December 2011; pp. 387–392.
- Mahmood, Z. Data location and security issues in cloud computing. In Proceedings of the 2011 International Conference on Emerging Intelligent Data and Web Technologies (EIDWT), Tirana, Albania, 7–9 September 2011; pp. 49–54.
- Gruschka, N.; Jensen, M. Attack surfaces: A taxonomy for attacks on cloud services. In Proceedings of the 2010 IEEE 3rd International Conference on Cloud Computing (CLOUD), Miami, FL, USA, 5–10 July 2010; pp. 276–279.
- Cherkasova, L.; Gupta, D.; Vahdat, A. Comparison of the three CPU schedulers in Xen. ACM SIGMETERICS Perform. Eval. Rev. 2007, 35, 42–51. [Google Scholar] [CrossRef]
- Fu, W.; Li, X. The study on data security in cloud computing based on virtualization. In Proceedings of the 2011 International Symposium on IT in Medicine and Education (ITME), Cuangzhou, China, 9–11 December 2011; Volume 2, pp. 257–261.
- Kim, H.; Lim, H.; Jeong, J.; Jo, H.; Lee, J. Task-aware virtual machine scheduling for I/O Performance. In Proceedings of the 2009 ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments, Washington, DC, March 11-13, 2009; pp. 101–110.
- Cherkasova, L.; Gupta, D.; Vahdat, A. When virtual is harder than real: Resource allocation challenges in virtual machine based IT environments. Technical Report HPL-2007-25. HP Laboratories: Palo. Alto, Feb 2007. [Google Scholar]
- Karnwal, T.; Sivakumar, T.; Aghila, G. A comber approach to protect cloud computing against XML DDoS and HTTP DDoS attack. In Proceedings of the 2012 IEEE Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), Bhopal, India, 1–2 March 2012; pp. 1–5.
- Liu, S.-T.; Chen, Y.-M. Retrospective detection of malware attacks by cloud computing. In Proceedings of the 2010 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Huangshan, China, 10–12 October 2010; pp. 510–517.
- Oberheide, J.; Cooke, E.; Jahanian, F. CloudAV: N-version antivirus in the network cloud. In Proceedings of the 17th Conference on Security Symposium (SS ’08); USENIX Association: Berkeley, CA, USA, 2008; pp. 91–106. [Google Scholar]
- Martignoni, L.; Paleari, R.; Bruschi, D. A framework for behavior-based malware analysis in the cloud. In Proceedings of the 5th International Conference on Information Systems Security (ICISS ’09), Kolkata, India, 14–18 December 2009; Springer-Verlag: Berlin, Heidelberg, 2009; pp. 178–192. [Google Scholar]
- Khorshed, M.T.; Ali, A.B.M.S.; Wasimi, S.A. A survey on gaps, threat remediation challenges and some thoughts for proactive attack detection in cloud computing. Future Gener. Comput. Syst. 2012, 28, 833–851. [Google Scholar] [CrossRef]
- Aviram, A.; Hu, S.; Ford, B.; Gummadi, R. Determinating timing channels in compute clouds. In Proceedings of the 2010 ACM Workshop on Cloud Computing Security Workshop (CCSW ’10); ACM: New York, NY, USA, 2010; pp. 103–108. [Google Scholar]
- Hlavacs, H.; Treutner, T.; Gelas, J.; Lefevre, L.; Orgerie, A. Energy consumption side-channel attack at virtual machines in a cloud. In Proceedings of the 2011 IEEE Ninth International Conference on Dependable, Autonomic and Secure Computing (DASC), Sydney, NSW, Australia, 12–14 December 2011; pp. 605–612.
- Rocha, F.; Correia, M. Lucy in the sky without diamonds: Stealing confidential data in the cloud. In Proceedings of the 2011 IEEE/IFIP 41st International Conference on Dependable Systems and Networks Workshops (DSNW ’11), Hong Kong, China, 27–30 June 2011; IEEE Computer Society: Washington, DC, USA, 2011; pp. 129–134. [Google Scholar]
- Ristenpart, T.; Tromer, E.; Shacham, H.; Savage, S. Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS ’09), Chicago, IL, USA, 9–13 November 2009; ACM: New York, NY, USA, 2009; pp. 199–212. [Google Scholar]
- Top Threats to Cloud Computing V1.0, Cloud Security Alliance, March 2010.
- Grosse, E.; Howie, J.; Ransome, J.; Reavis, J.; Schmidt, S. Cloud computing roundtable. IEEE Secur. Priv. 2010, 8, 17–23. [Google Scholar] [CrossRef]
- Lin, W.; Lee, D. Traceback attacks in cloud—Pebbletrace botnet. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops (ICDCSW), Macau, China, 18–21 June 2012; pp. 417–426.
- Kourai, K.; Azumi, T.; Chiba, S. A self-protection mechanism against stepping-stone attacks for IaaS clouds. In Proceedings of the UIC/ATC; 2012; pp. 539–546. [Google Scholar]
- Liu, B.; Xu, E.; Wang, J.; Wei, Z.; Xu, L.; Zhao, B.; Su, J. Thwarting audio steganography attacks in cloud storage systems. In Proceedings of the 2011 International Conference on Cloud and Service Computing (CSC), Hong Kong, China, 12–14 December 2011; pp. 259–265.
- Mazurczyk, W.; Szczypiorski, K. Is cloud computing steganography-proof? In Proceedings of the 2011 Third International Conference on Multimedia Information Networking and Security (MINES ’11), Shanghai, China, 4–6 November 2011; IEEE Computer Society: Washington, DC, USA, 2011; pp. 441–442. [Google Scholar]
- Antunes, N.; Vieira, M. Defending against web application vulnerabilities. Computer 2012, 45, 66–72. [Google Scholar] [CrossRef]
- Parno, B.; Lorch, J.R.; Douceur, J.R.; Mickens, J.; McCune, J.M. Memoir: Practical state continuity for protected modules. In Proceedings of the 2011 IEEE Symposium on Security and Privacy (SP ’11), Oakland, CA, USA, 22–25 May 2011; IEEE Computer Society: Washington, DC, USA, 2011; pp. 379–394. [Google Scholar]
- Zeus Bot Found Using Amazon’s EC2 as C&C Server. Available online: http://www.theregister.co.uk/2009/12/09/amazon ec2 bot control channel/ (accessed on: Feb 1, 2014).
- Google Cloud Platform Used for Botnet Control. Available online: http://www.infosecurity-magazine.com/view/5115/google-cloud-platform-used-for-botnet-control/ (accessed on: Feb 1, 2014).
- Raytheon UK Targeted in Cloud-Based Attack. Available online: http://www.zdnet.co.uk/news/security-threats/2011/10/12/raytheon-uk-targeted-in-cloud-based-attack-40094173/ (accessed on: Feb 1, 2014).
- Srivastava, A.; Giffin, J. Tamper-resistant, application-aware blocking of malicious network connections. In Proceedings of the 11th International Symposium, RAID 2008, Cambridge, MA, USA, 15–17 September 2008; pp. 39–58.
- Tupakula, U.; Varadharajan, V.; Akku, N. Intrusion detection techniques for infrastructure as a service cloud. In Proceedings of the 2011 IEEE Ninth International Conference on Dependable, Autonomic and Secure Computing (DASC), Sydney, Australia, 12–14 Dec. 2011; pp. 744–751.
- Szefer, J.; Lee, R.B. Architectural support for hypervisor-secure virtualization. SIGARCH Comput. Arch. News 2012, 40, 437–450. [Google Scholar]
- Lo, C.-C.; Huang, C.-C.; Ku, J. A cooperative intrusion detection system framework for cloud computing networks. In Proceedings of the 2010 39th International Conference on Parallel Processing Workshops (ICPPW), San Diego, CA, USA, 13–16 September 2010; pp. 280–284.
- Vieira, K.; Schulter, A.; Westphall, C.B.; Westphall, C.M. Intrusion detection for grid and cloud computing. IT Prof. 2010, 12, 38–43. [Google Scholar]
- Wang, D.; Zhou, Z. Application of cloud model in intrusion detection. In Proceedings of the 2010 2nd International Conference on e-Business and Information System Security (EBISS), Wuhan, China, 22–23 May 2010; pp. 1–4.
- Van athi, R.; Gunasekaran, S. Comparison of network intrusion detection systems in cloud computing environment. In Proceedings of the 2012 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 10–12 January 2012; pp. 1–6.
- Roschke, S.; Cheng, F.; Meinel, C. Intrusion detection in the cloud. In Proceedings of the Eighth IEEE International Conference on Dependable, Autonomic and Secure Computing, 2009 (DASC ’09), Chengdu, China, 12–14 December 2009; pp. 729–734.
- Zargar, S.T.; Takabi, H.; Joshi, J.B.D. DCDIDP: A distributed, collaborative, and data-driven intrusion detection and prevention framework for cloud computing environments. In Proceedings of the 2011 7th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Orlando, FL, USA, 15–18 October 2011; pp. 332–341.
- Dastjerdi, A.V.; Bakar, K.A.; Tabatabaei, S.G.H. Distributed intrusion detection in clouds using mobile agents. In Proceedings of the Third International Conference on Advanced Engineering Computing and Applications in Sciences, 2009 (ADVCOMP ’09), Sliema, Malta, 11–16 October 2009; pp. 175–180.
- Ye, D.; Bai, Q.; Zhang, M.; Ye, Z. P2P distributed intrusion detections by using mobile agents. In Proceedings of the Seventh IEEE/ACIS International Conference on Computer and Information Science, 2008 (ICIS 08), Portland, OR, USA, 14–16 May 2008; pp. 259–265.
- Kannadiga, P.; Zulkernine, M. DIDMA: A distributed intrusion detection system using mobile agents. In Proceedings of the Sixth International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, and First ACIS International Workshop on Self-Assembling Wireless Networks, 23–25 May 2005; pp. 238–245.
- Erdil, D.C. Dependable autonomic cloud computing with information proxies. In Proceedings of the 2011 IEEE International Symposium on Parallel and Distributed Processing Workshops and Phd Forum (IPDPSW), Shanghai, China, 16–20 May 2011; pp. 1518–1524.
- Doelitzscher, F.; Reich, C.; Knahl, M.; Clarke, N. An autonomous agent based incident detection system for cloud environments. In Proceedings of the 2011 IEEE Third International Conference on Cloud Computing Technology and Science (CloudCom), Athens, Greece, 29 November–1 December 2011; pp. 197–204.
- Balen, D.; Westphall, C.; Westphall, C. Experimental assessment of routing for grid and cloud. In Proceedings of the Tenth International Conference on Networks (ICN 2011), St. Maarten, The Netherlands Antilles, January 23-28, 2011; pp. 341–346.
- Sodhi, B.; Prabhakar, T.V. A cloud architecture using smart nodes. In Proceedings of the 2011 IEEE Asia-Pacific Services Computing Conference (APSCC), Jeju Island, Korea, 12–15 December 2011; pp. 116–123.
- Yazir, Y.O.; Matthews, C.; Farahbod, R.; Neville, S.; Guitouni, A.; Ganti, S.; Coady, Y. Dynamic resource allocation in computing clouds using distributed multiple criteria decision analysis. In Proceedings of the 2010 IEEE 3rd International Conference on Cloud Computing (CLOUD), Miami, FL, USA, 5–10 July 2010; pp. 91–98.
- Mareschal, B. Aide a la Decision Multicritere: Developpements Recents des Methodes PROMETHEE; Cahiers du Centre d’Etudes en Recherche Operationelle: Bruxelles, Belgium, 1987; pp. 175–241. [Google Scholar]
- Uchida, N.; Takahata, K.; Shibata, Y. Proposal of overlay cloud computing system by virtual autonomous network configuration. In Proceedings of the 2011 International Conference on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC), Barcelona, Spain, 26–28 October 2011; pp. 307–310.
- Bishop, M. Computer Security: Art and Science; Addison-Wesley Professional: Reading, MA, USA, 2002. [Google Scholar]
- Leandro, M.A.P.; Nascimento, T.J.; dos Santos, D.R.; Westphall, C.M.; Westphall, C.B. Multi-tenancy authorization system with federated identity for cloud-based environments using shibboleth. In Proceedings of the Eleventh International Conference on Networks; 2012; pp. 88–93. [Google Scholar]
- Sanchez, R.; Almenares, F.; Arias, P.; Diaz-Sanchez, D.; Marin, A. Enhancing privacy and dynamic federation in IdM for consumer cloud computing. IEEE Trans. Consum. Electron. 2012, 58, 95–103. [Google Scholar] [CrossRef]
- Revealed: Why Android Beats iPhone for Organized Crime. Available online: http://blogs.computerworld.com/16392/security_android_beats_iphone_for_crime (accessed on 13 January 2013).
- Oxford English Dictionary; In Shibboleth; 1989.
- Albeshri, A.; Caelli, W. Mutual protection in a cloud computing environment. In Proceedings of the 2010 12th IEEE International Conference on the High Performance Computing and Communications (HPCC), Melbourne, VIC, Australia, 1–3 September 2010; pp. 641–646.
- Angin, P.; Bhargava, B.; Ranchal, R.; Singh, N.; Linderman, M.; Othmane, L.B.; Lilien, L. An entity-centric approach for privacy and identity management in cloud computing. In Proceedings of the 2010 29th IEEE Symposium on Reliable Distributed Systems, New Delhi, India, 31 October–3 November 2010; pp. 177–183.
- Ates, M.; Ravet, S.; Ahmat, A.M.; Fayolle, J. An identity-centric internet: Identity in the cloud, identity as a service and other delights. In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; pp. 555–560.
- Kaspersky Security Bulletin. Statistics 2011. Available online: http://www.securelist.com/en/analysis/204792216/Kaspersky_Security_Bulletin_Statistics_2011 (accessed on 13 January 2013).
- You, P.; Peng, Y.; Liu, W.; Xue, S. Security issues and solutions in cloud computing. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops (ICDCSW), Macau, China, 18–21 June 2012; pp. 573–577.
- Bhadauria, R.; Chaki, R.; Chaki, N.; Sanyal, S. A Survey on Security Issues in Cloud Computing. Cornell University Library: USA, 2013. Available online: http://arxiv.org/abs/1109.5388 (Accessed on: Feb 1, 2014).
- Kanday, R. A survey on cloud computing security. In Proceedings of the 2012 International Conference on Computing Sciences (ICCS), Phagwara, India, 14–15 September 2012; pp. 302–311.
- Zhou, M.; Zhang, R.; Xie, W.; Qian, W.; Zhou, A. Security and privacy in cloud computing: A survey. In Proceedings of the 2010 Sixth International Conference on Semantics Knowledge and Grid (SKG), Beijing, China, 1–3 November 2010; pp. 105–112.
- Verma, A.; Kaushal, S. Cloud Computing Security Issues and Challenges: A Survey. In Advances in Computing and Communications; Abraham, A., Mauri, J.L., Buford, J.F., Suzuki, J., Thampi, S.M., Eds.; Communications in Computer and Information Science; Springer Berlin Heidelberg: Berlin, Germany, 2011; pp. 445–454. [Google Scholar]
- Ren, K.; Wang, C.; Wang, Q. Security challenges for the public cloud. IEEE Internet Comput. 2012, 16, 69–73. [Google Scholar]
- Panta, R. K.; Bagchi, S.; Khalil, I. Efficient wireless reprogramming through reduced bandwidth usage and opportunistic sleeping. Ad Hoc Networks (an Elsevier Journal) 2009, Volume 7(Issue 1), 42–62. [Google Scholar] [CrossRef]
- Khalil, I. MCC: Mitigating colluding collision attacks in wireless sensor networks. In Proceedings of the IEEE Global Communications Conference (IEEE GLOBECOM’10), Miami, Florida, USA, December 6 – 10, 2010; pp. 1–5.
- 105. http://blog.scalar.ca/Blog/bid/87248/Mitigating-common-cloud-computing-risks (Accessed on: Feb 1, 2014).
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Khalil, I.M.; Khreishah, A.; Azeem, M. Cloud Computing Security: A Survey. Computers 2014, 3, 1-35. https://doi.org/10.3390/computers3010001
Khalil IM, Khreishah A, Azeem M. Cloud Computing Security: A Survey. Computers. 2014; 3(1):1-35. https://doi.org/10.3390/computers3010001
Chicago/Turabian StyleKhalil, Issa M., Abdallah Khreishah, and Muhammad Azeem. 2014. "Cloud Computing Security: A Survey" Computers 3, no. 1: 1-35. https://doi.org/10.3390/computers3010001
APA StyleKhalil, I. M., Khreishah, A., & Azeem, M. (2014). Cloud Computing Security: A Survey. Computers, 3(1), 1-35. https://doi.org/10.3390/computers3010001




