MITM- and DoS-Resistant PUF Authentication for Industrial WSNs via Sensor-Initiated Registration
Abstract
1. Introduction
1.1. Background and Motivation
1.2. Problem Statement
1.3. Research Questions and Objectives
- RQ1: What security vulnerabilities are present in existing PUF-based authentication protocols for IWSNs, particularly focusing on the protocol phases that lack adequate protection mechanisms?
- RQ2: How can adversaries exploit weaknesses in the sensor registration phase to compromise the overall security of the authentication protocols?
- RQ3: What modifications can be implemented to strengthen existing authentication schemes while preserving their lightweight characteristics, which are essential for IWSN deployments?
- RQ4: How effective are the proposed security enhancements in mitigating the identified vulnerabilities without introducing a significant performance overhead?
- Security Analysis: Conduct a systematic security analysis of Gope et al.’s PUF-based authentication protocol to identify potential vulnerabilities and attack vectors.
- Attack Development: Develop and demonstrate practical attack scenarios that exploit the identified weaknesses, focusing on man-in-the-middle (MITM) and denial-of-service (DoS) attacks.
- Protocol Enhancement: Design an improved authentication scheme that addresses the identified vulnerabilities while maintaining the lightweight properties required for IWSN applications.
- Security Validation: Provide security justification for the proposed enhancements and demonstrate their effectiveness in preventing the identified attacks.
- Performance evaluation: The computational and communication overheads introduced by the proposed modifications were assessed to ensure practical applicability in resource-constrained environments.
1.4. Contributions
- C1: Comprehensive Security Analysis—We provide a detailed security analysis of Gope et al.’s authentication protocol, identifying critical vulnerabilities in the sensor registration phase that enable sophisticated attacks against the overall protocol security.
- C2: Attack Demonstration—We demonstrate practical MITM and DoS attacks that exploit the identified vulnerabilities, showing how adversaries can compromise session keys and disrupt network operations. The attacks are presented with detailed step-by-step procedures and an analysis of their impact on protocol security.
- C3: Enhanced Authentication Scheme—We propose an improved authentication protocol that introduces sensor-initiated registration mechanisms to prevent unauthorized PUF queries. The enhanced scheme addresses the identified vulnerabilities while preserving the lightweight characteristics that are essential for IWSN deployments.
- C4: Security Justification—We provide a comprehensive security analysis demonstrating that the proposed enhancements effectively mitigate the identified attacks. The analysis includes informal security reasoning and a comparative evaluation with the original protocol.
- C5: Practical Validation—We evaluate the practical applicability of the proposed scheme through an analysis of computational and communication overheads, demonstrating that security improvements can be achieved without significant performance penalties.
1.5. Paper Organization
2. Background and Preliminaries
2.1. Industrial Wireless Sensor Networks
- IWSN Architecture
- Security Requirements for IWSNs
2.2. Physically Unclonable Functions (PUFs)
- PUF Fundamentals
- PUF Implementation Technologies
2.3. Cryptographic Primitives for Resource-Constrained Environments
- Hash Functions
- Symmetric Key Cryptography
- Message Authentication Codes
2.4. Security Requirements and Attack Models for IWSN Authentication
- Mutual Authentication Requirements
- User devices and gateways: Users accessing industrial data must be authenticated to prevent unauthorized access [36].
- Sensor nodes and gateways: Sensors must verify the legitimacy of gateway devices to prevent data theft and control manipulations [37].
- Inter-gateway communication: Multiple gateways in large deployments must authenticate each other for secure data sharing [38].
- Session Key Establishment
- Forward Secrecy: Compromise of long-term secrets should not compromise previously established session keys [40].
- Perfect Forward Secrecy: Compromise of long-term secrets should not enable decryption of past communications [41].
- Key Freshness: Each authentication session should establish a new, unique session key to prevent replay attacks [42].
- Privacy and Anonymity Requirements
- User Anonymity: The identity of users accessing the system should be protected from external observers [44].
- Device Unlinkability: It is possible to link multiple communications from the same device to track device movements or usage patterns [45].
- Location Privacy: The physical location of sensor nodes should be protected when possible to prevent targeted physical attacks [46].
- Common Attack Vectors
- Eavesdropping: Passive monitoring of wireless communications to gather intelligence or credentials [48].
- Man-in-the-Middle (MITM): Active interception and manipulation of communications between legitimate parties [34].
- Replay Attacks: Retransmission of previously captured messages to gain unauthorized access [35].
- Denial-of-Service (DoS): Attacks designed to disrupt service availability and prevent legitimate communication [36].
- Physical Attacks: Direct access to sensor devices to extract secrets or modify functionality [37].
3. Related Work
3.1. PUF-Based Authentication Protocols
3.2. Lightweight Authentication Schemes for Wireless Sensor Networks
3.3. Research Gaps and Motivation
- Security Analysis Limitations
- Inadequate Consideration of Registration Phase Security
- Limited Real-World Attack Scenarios
- Insufficient Performance Validation
4. System Model and Threat Model
4.1. System Architecture
4.2. Adversarial Model
4.3. Security Goals
- Primary Goals: Mutual authentication between all entities, secure session key establishment, data confidentiality and integrity, and resistance to replay attacks [43].
- Performance Requirements: Computational efficiency suitable for resource-constrained devices, minimal communication overhead, denial-of-service resistance, and scalability for large deployments [44].
- Industrial Requirements: Real-time performance for time-critical applications, integration with existing industrial infrastructure, and compliance with relevant security standards [45].
5. Review of Gope et al.’s Scheme
5.1. Enhanced Threat Model for Vulnerability Analysis
- Full network control (Dolev–Yao model): The attacker can control all communication channels in the IWSN. This includes eavesdropping on transmissions, intercepting and dropping messages at will, modifying message contents, and injecting forged messages into the network. However, the adversary is computationally bounded and cannot break standard cryptographic primitives (e.g., cannot invert one-way hash functions or derive secret keys from intercepted data).
- Physical compromise of sensor nodes: The attacker may physically capture sensor devices deployed in the field. By gaining physical access, the adversary could extract confidential information (such as cryptographic keys or passwords) stored on a sensor or reset/reprogram the device. This capability means the adversary might impersonate a legitimate sensor after extracting its credentials or trigger the sensor to undergo the authentication process under adversarial timing and control.
- Exploitation of unauthenticated protocol phases: The adversary can take advantage of any step in the scheme that is not yet protected by authentication or encryption. For example, if an initial handshake or registration message is sent without verification, the attacker can intercept and manipulate it. The adversary might replay initial messages or send fraudulent initiation requests to confuse the legitimate parties, insert itself as a man-in-the-middle before authentication is finalized, or flood the gateway with spurious requests to exhaust its resources (denial-of-service).
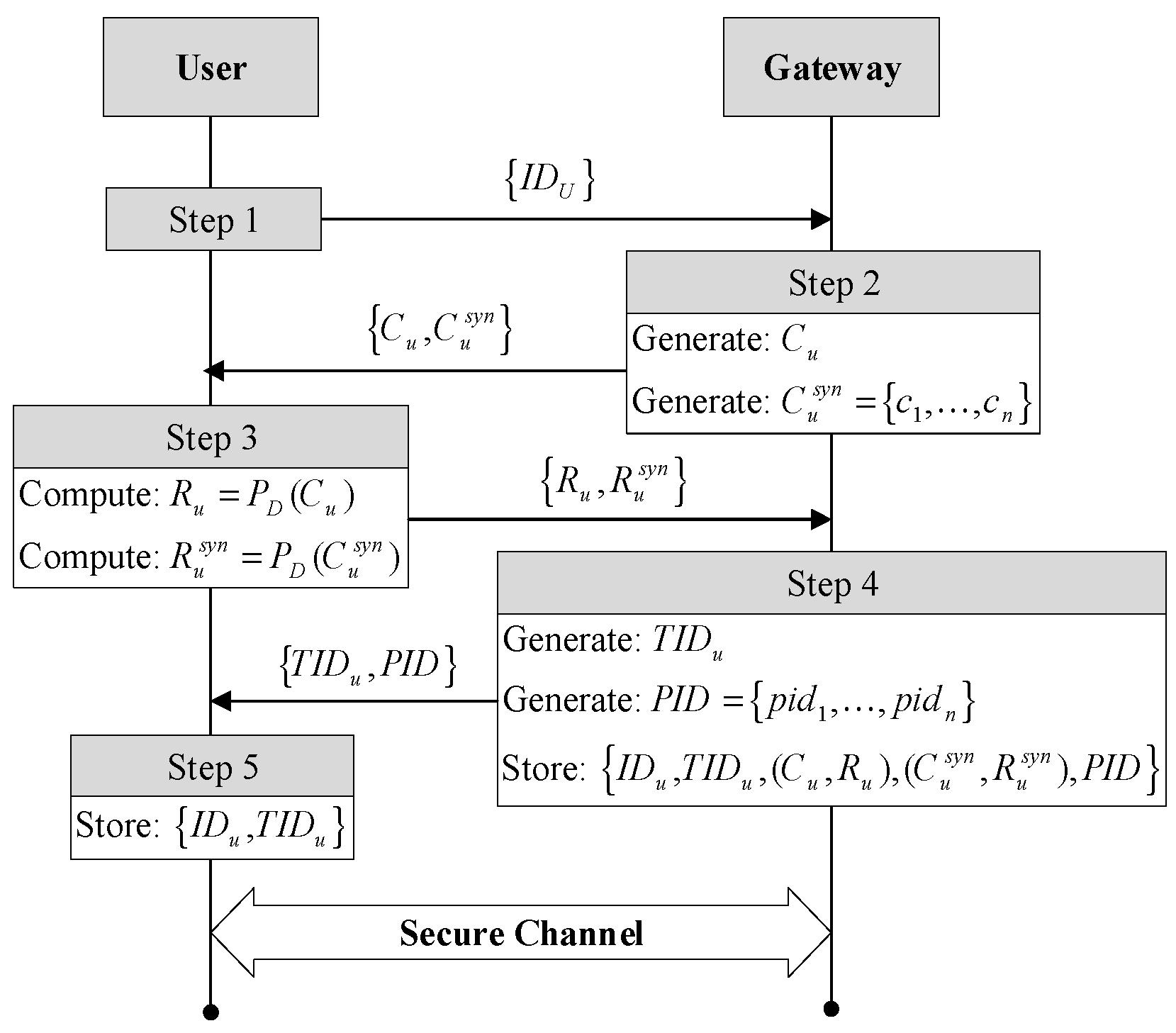
5.2. User Registration Phase
- Step 1.
- U transmits its identity to the gateway.
- Step 2.
- The gateway generates a random challenge for the normal authentication process and a set of new challenges for resynchronization with the user U and sends to U.
- Step 3.
- D extracts the PUF outputs of , and sends to the gateway.
- Step 4.
- The gateway randomly generates a unique temporary identity and a set of pseudo-identities and transmits to U. The gateway stores , , , , and .
- Step 5.
- U stores in the device D. Next, U inputs his/her biometric thumb impression into the device. The device extracts and then the user U selects a password and inputs it into the device. The device computes and stores for user verification, where h is a one-way cryptographic hash function.
5.3. Sensor Node Registration Phase
- Step 1.
- The gateway generates a challenge for each sensor node and a set of new challenges for resynchronization with , and sends to .
- Step 2.
- extracts the PUF outputs of , i.e., , . Finally, sends to the gateway.
- Step 3.
- The gateway generates a unique identity for the sensor and stores , , and . However, does not require to store any secret credentials.
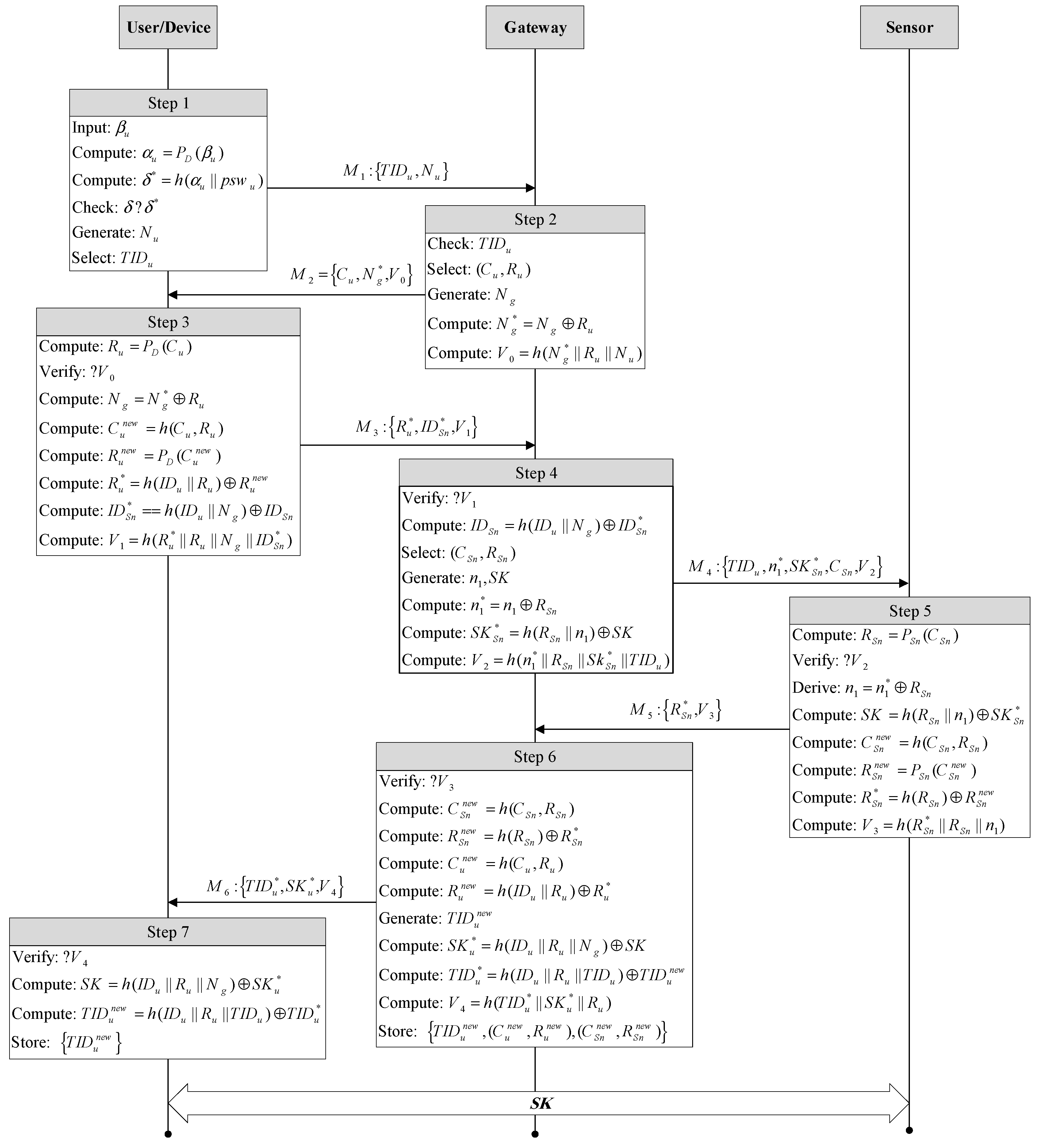
5.4. Authentication Phase
- Step 1.
- U inputs his/her biometric thumb impression into the device. The device extracts and then the user U inputs his password into the device. The device computes and compares it with the stored to either accept or reject the user. Device D generates a nonce and sends to the gateway through a public channel.
- Step 2.
- The gateway selects and generates a nonce . Next, the gateway calculates and . Finally, the gateway sends to the user U.
- Step 3.
- The user’s device D computes and verifies . If the verification is successful, the device D calculates , , and . The device uses and the identity of the accessed sensor node to compute the following:Finally, the device sends to the gateway.
- Step 4.
- The gateway verifies and derives and selects . Next, the gateway generates a random number and a session key SK and then computes the following:Finally, the gateway sends the message to the sensor through a public channel.
- Step 5.
- The sensor computes the PUF output and verifies . After successful verification, the sensor computes the following:
- Step 6.
- ,
- ,
- .
Finally, the sensor sends to the gateway.- Step 7.
- The gateway verifies and calculates the following:
- .
The gateway also generates a new temporary identity for the user U as and computes the following:- .
Finally, the gateway sends to the user U and stores , , and . - Step 8.
- The user U’s device verifies and computes the session key , and stores .
5.5. SPDC Phase
- Step 1.
- The gateway generates a nonce , calculates , , and sends to .
- Step 2.
- The sensor calculates and then verifies . If the verification is successful, generates a nonce and calculates the following:Finally, sends to the gateway.
- Step 3.
- The gateway verifies and computes the following:
- .
Finally, the gateway stores .
6. Cryptanalysis of Gope et al.’s Scheme
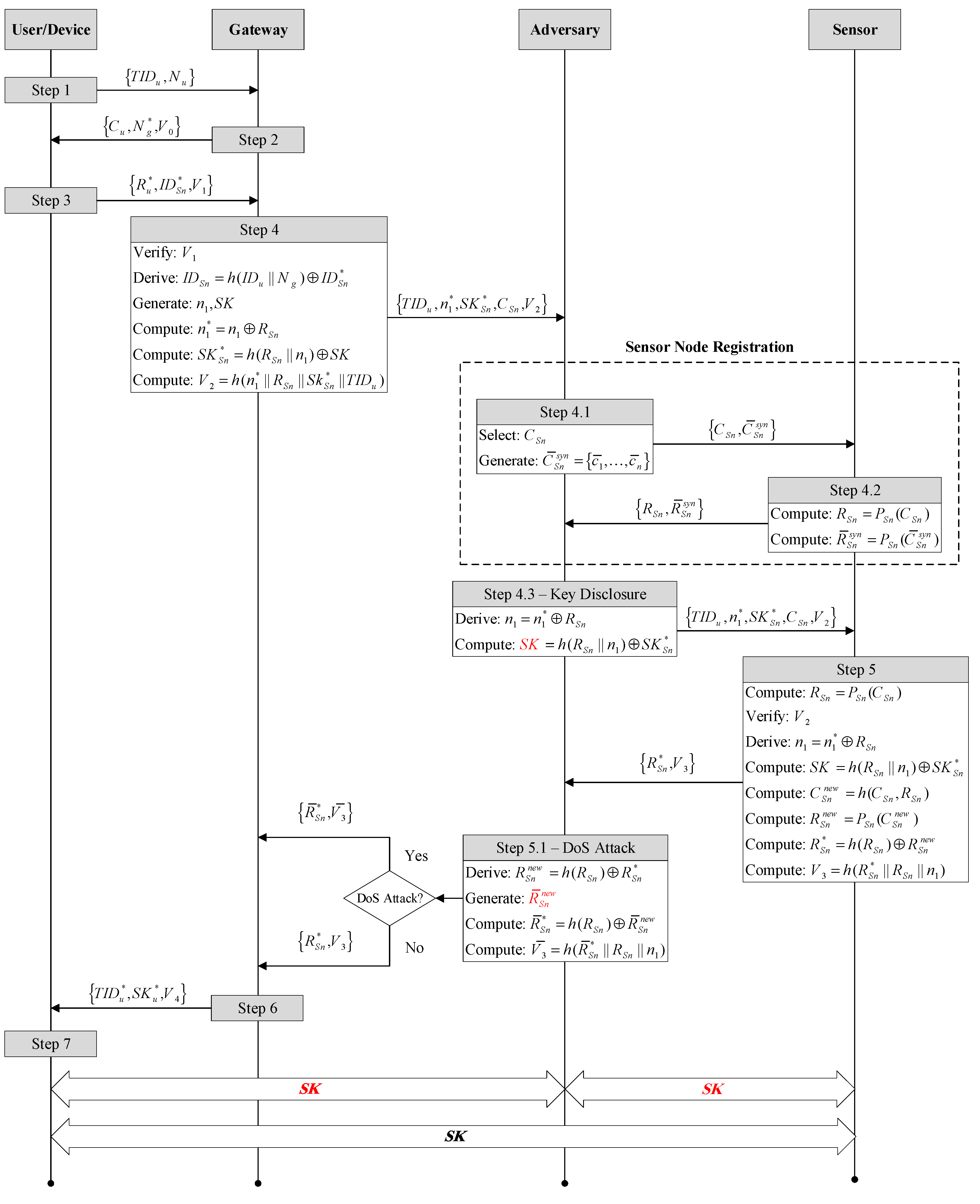
6.1. Attacks on the Authentication Phase
- Step 4.1.
- The adversary A intercepts message communicated from the gateway to . Next, adversary A generates a set of challenges and starts the sensor node registration phase by transmitting to .
- Step 4.2.
- extracts the PUF outputs of , and sends to adversary A, which acts as a gateway.
- Step 4.3.
- Next, the adversary computes and uses it to recover the session key SK by computing . Finally, the adversary releases the message to be sent to Sn to complete the authentication phase with the gateway.
- Step 5.1.
- The adversary A intercepts .Next, A derives the PUF output and generates a unique PUF output . Finally, A computes and , and it sends to the gateway as a response to .
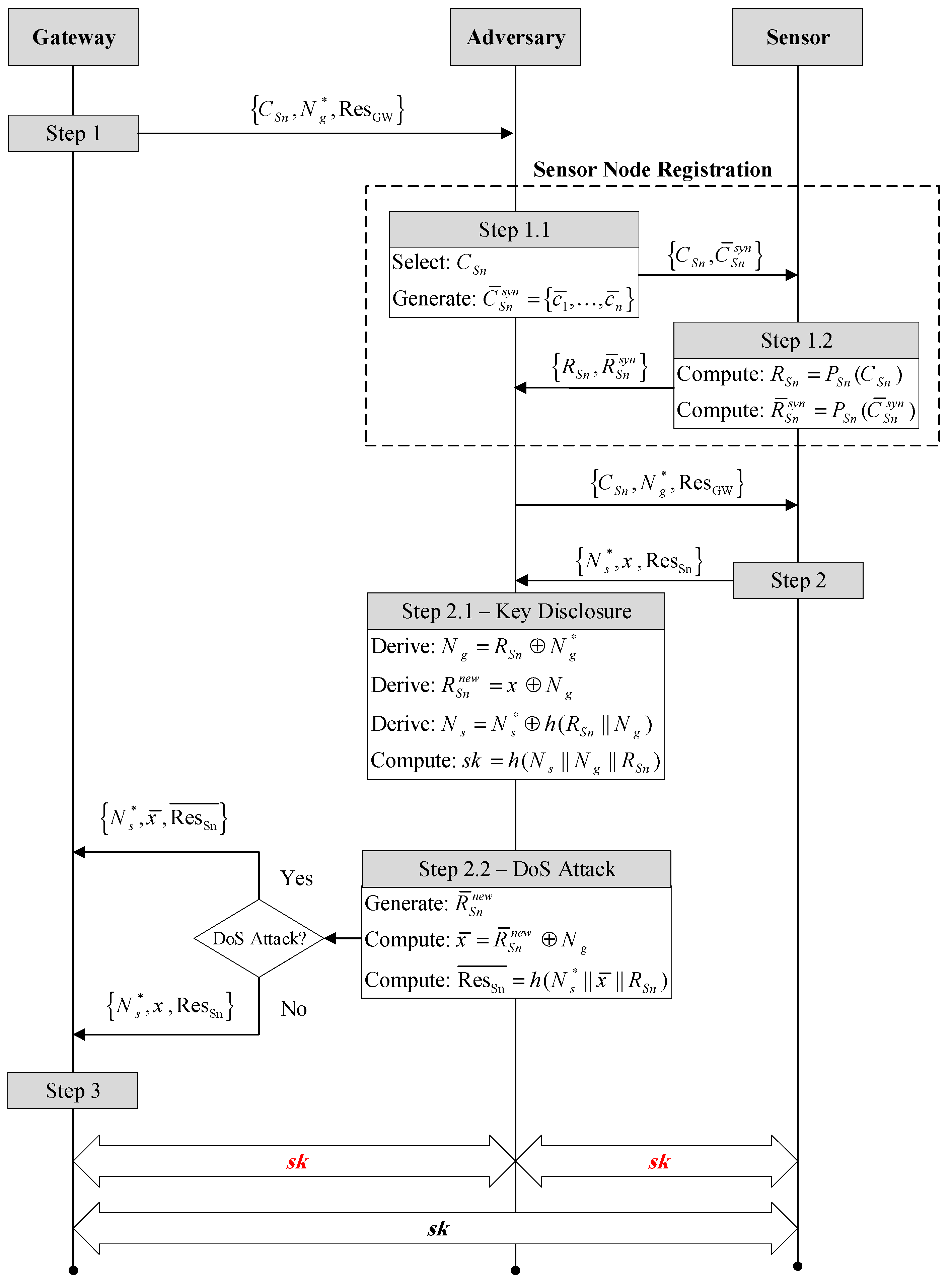
6.2. Attacks on SPDC Phase
- Step 1.1.
- The adversary A intercepts message communicated from the gateway to in Step 1. Next, adversary A generates a set of challenges and starts the sensor node registration phase by transmitting to .
- Step 1.2.
- extracts the PUF outputs of and , and it sends to adversary A, which acts as a gateway. Finally, the adversary releases the message to be sent to Sn.
- Step 2.1.
- After the completion of Step 2 of this phase, adversary A intercepts the message . Next, the adversary computes , , and . Finally, the adversary computes the session key and releases the message to be sent to the gateway.
- Step 2.2.
- The adversary generates and computes and . Finally, A sends to the gateway instead of .
6.3. Attack Feasibility and Impact Assessment
7. Proposed Enhanced Authentication Protocol
7.1. Design Rationale and Core Modification
7.2. Modified Sensor Node Registration Phase
- Step 1.
- The gateway sends a registration request to the sensor node .
- Step 2.
- The sensor node generates a challenge and a set of new challenges . Next, extracts the PUF outputs of , namely, and , and sends to the gateway through a secure channel.
7.3. Informal Security Justification of Modified Sensor Registration Phase
7.4. Comparative Analysis and Performance Considerations
8. Security Analysis and Performance Evaluation
8.1. Security Properties of the Enhanced Scheme
- Mutual Authentication: The enhanced protocol ensures mutual authentication between all communicating entities through the sensor-controlled challenge generation process [36]. During registration, sensor nodes generate unique challenges that must be properly handled by legitimate gateways, establishing the foundation for mutual verification in subsequent protocol phases. The authentication and SPDC phases maintain their original mutual authentication properties while benefiting from the strengthened registration foundation [37].
- Session Key Security: The protocol establishes cryptographically strong session keys that remain secure against the MITM attacks demonstrated in Section 6 [38]. Since adversaries cannot obtain unauthorized PUF responses through rogue registrations, they cannot derive the session keys SK and sk used in the authentication and SPDC phases, respectively. The session keys maintain their unpredictability and uniqueness properties from the original protocol [39].
- Forward Secrecy: The enhanced scheme preserves the forward secrecy properties of the original protocol [40]. Compromise of current session keys does not enable decryption of past communications, as each authentication session establishes fresh keys based on new nonces and PUF evaluations. The sensor-initiated registration does not affect this property since registration occurs infrequently compared to authentication sessions [41].
- Anonymity and Privacy: User anonymity and device unlinkability properties are maintained in the enhanced protocol [42]. The modifications affect only the sensor registration phase and do not alter the privacy-preserving mechanisms used in the authentication and data collection phases. Temporary identities and pseudo-identities continue to protect user and device privacy from external observers [43].
8.2. Attack Resistance Analysis
- MITM Attack Resistance: The sensor-initiated registration prevents MITM attacks by eliminating unauthorized PUF access [45]. Adversaries cannot perform rogue registrations because sensor nodes control the challenge generation process and only respond to legitimate registration requests. Without access to valid PUF challenge–response pairs, adversaries cannot derive the session keys required for MITM attacks during the authentication and SPDC phases. The mutual verification mechanisms ensure that any attempt to insert a malicious intermediary will be detected and rejected [46].
- DoS Attack Resistance: The enhanced scheme provides comprehensive protection against DoS attacks through multiple mechanisms [47]. First, sensor nodes cannot be forced to perform unwanted cryptographic operations because they only initiate registration when receiving legitimate requests from authorized gateways. Second, the gateway can quickly reject spurious registration requests without significant computational overhead by performing lightweight verification of incoming messages. Third, the protocol prevents the injection of false PUF responses that could corrupt the cryptographic state stored at gateways, eliminating the persistent DoS attacks demonstrated against the original scheme [48].
- Physical Attack Considerations: While sensor nodes may still be physically accessible to adversaries in industrial environments, the enhanced protocol limits the impact of physical compromise [34]. An adversary gaining physical access to a sensor cannot extract long-term secrets (since none are stored) and cannot force the sensor to reveal arbitrary PUF responses. The controlled challenge generation ensures that physical access does not automatically grant the ability to compromise other network communications [35].
- Replay Attack Resistance: The protocol maintains strong resistance to replay attacks through the use of fresh nonces and timestamps in each protocol session [36]. The sensor-initiated registration does not affect these properties, as the registration phase continues to use secure channels that provide replay protection. The authentication and SPDC phases retain their original replay resistance mechanisms [37].
- Physical Attack Considerations: While sensor nodes may still be physically accessible to adversaries in industrial environments, the enhanced protocol limits the impact of physical compromise. An adversary gaining physical access to a sensor cannot extract long-term secrets (since none are stored) and cannot force the sensor to reveal arbitrary PUF responses due to controlled challenge generation. The protocol maintains forward secrecy properties—compromise of current session keys does not enable decryption of past communications since each authentication session establishes fresh keys based on new nonces and PUF evaluations. However, physical capture of multiple sensors could potentially compromise their individual communications. The sensor-initiated registration ensures that physical access does not automatically grant the ability to compromise other network communications, which represents a significant improvement over the original protocol’s vulnerabilities.
8.3. Security Requirements Validation
- Requirement R1 (Mutual Authentication): The enhanced protocol ensures that all communicating parties can verify each other’s identity.
- Proof sketch: During registration, sensor S generates challenge and sends it with response to gateway GW. Only legitimate gateways can properly utilize this information in subsequent authentication phases. In the authentication phase, mutual verification occurs through challenge–response exchanges that depend on the securely established PUF challenge–response pairs. An adversary A without access to valid PUF responses cannot complete authentication with either party.
- Requirement R2 (Session Key Security): The protocol establishes unpredictable session keys resistant to derivation by adversaries.
- Proof sketch: Session keys are derived using PUF responses that are only available to legitimate parties due to the sensor-controlled registration process. Since adversary A cannot obtain PUF responses through rogue registration (as shown in Section 6.1), A cannot compute the required hash operations to derive session keys.
- Requirement R3 (DoS Resistance): The protocol remains available under denial-of-service attacks.
- Proof sketch: The enhanced design eliminates both DoS vectors identified in Section 6.1 (1) Battery drain attacks are prevented because sensors only respond to legitimate registration triggers, not arbitrary adversarial requests. (2) Gateway flooding attacks are mitigated through lightweight verification that quickly discards invalid requests without resource expenditure.
- Requirement R4 (Forward Secrecy): Compromise of current secrets does not affect past communications.
- Proof sketch: Each authentication session uses fresh nonces and establishes new session keys independent of previous sessions. The registration phase provides PUF challenge–response pairs but does not affect the session-specific key derivation process that ensures forward secrecy.
8.4. Formal Security Verification
8.4.1. Formal Model Design
8.4.2. Security Properties Specification
8.4.3. Verification Results and Attack Prevention Validation
8.4.4. Model Validation and Industrial Deployment Significance
8.5. Computational Complexity Analysis
- Sensor Node Computation: The primary additional computation required at sensor nodes is the generation of random challenges during registration [40]. This operation can be performed using lightweight pseudorandom number generators (PRNGs) that are typically already present in sensor hardware for other protocol operations. The computational cost of PRNG operations is negligible compared to PUF evaluations, which remain unchanged from the original protocol [41].
- Gateway Computation: Gateways experience no additional computational overhead during normal operations [42]. The registration phase requires the same PUF response processing as the original protocol, with the addition of lightweight verification operations for incoming registration requests. These verification operations involve simple hash computations or message authentication code (MAC) checks that impose minimal computational burden on gateway devices [43].
- PUF Operations: The number and complexity of PUF evaluations remain identical to the original protocol [44]. Sensor nodes perform the same PUF computations during registration, and no additional PUF operations are required during authentication or data collection phases. This ensures that the most computationally expensive operations in the protocol are not affected by the security enhancements [45].
- Cryptographic Operations: The enhanced protocol uses the same lightweight cryptographic primitives as the original scheme, including hash functions and XOR operations [46]. No additional cryptographic algorithms are introduced, maintaining the protocol’s suitability for resource-constrained environments. The cryptographic complexity remains at O(1) for individual operations and O(n) for protocol sessions involving n participants [47].
8.6. Communication Overhead Evaluation
- Message Count: The enhanced registration phase maintains the same number of messages as the original protocol [34]. Step 1 involves sending a registration request (replacing the challenge message), Step 2 involves the sensor response with challenge–response pairs, and Step 3 involves gateway acknowledgment and identity assignment. The authentication and SPDC phases are unchanged, preserving their original message complexity [35].
- Message Size: The total size of messages exchanged during registration remains essentially unchanged [36]. The registration request message (Q_GW) is typically smaller than the original challenge message, while the sensor response message maintains the same size as it carries the same cryptographic content. The overall communication overhead is therefore not increased by the security enhancements [37].
- Network Traffic: The enhanced protocol does not generate additional network traffic during normal operations [38]. The registration phase occurs infrequently (typically only during initial device deployment), so any minor changes in registration message patterns have negligible impact on overall network utilization. The authentication and data collection phases, which constitute the majority of network traffic, remain unmodified [39].
- Bandwidth Requirements: The protocol maintains the same bandwidth requirements as the original scheme [40]. Industrial wireless sensor networks typically operate under strict bandwidth constraints, and the enhanced protocol ensures that these limitations are respected. The lightweight message structure continues to support efficient operation in bandwidth-limited environments [41].
- Scalability Considerations: The enhanced protocol maintains the same storage requirements as the original scheme. Gateways store the same PUF challenge–response for each sensor, with storage scaling linearly O(n) for n sensors. PUF challenge–response table lookup remains unchanged since the same data structures are used, with standard hash table implementations providing O(1) average lookup time. For deployments with hundreds of sensors per gateway, the storage overhead remains manageable (typically few KB per sensor for challenge–response pairs), and lookup latency is not impacted since our modifications only change the registration phase control flow without affecting operational data access patterns.
8.7. Energy Consumption and Battery Life Analysis
- Registration Phase Energy: The additional computation required for challenge generation introduces minimal energy overhead [43]. Random number generation operations consume significantly less energy than radio transmission or PUF evaluation operations. The energy cost of the enhanced registration remains dominated by wireless communication rather than computational operations [44].
- Operational Phase Energy: The authentication and SPDC phases are unmodified in the enhanced protocol, ensuring that the energy consumption patterns during normal operation remain identical to the original scheme [45]. This preservation of operational energy efficiency is crucial for maintaining the expected battery life of deployed sensor nodes [46].
- Lifetime Impact: Analysis indicates that the energy overhead introduced by the enhanced registration has negligible impact on overall sensor battery life [47]. Since registration occurs infrequently compared to authentication and data collection operations, the additional energy consumption represents a minimal fraction of total device energy usage. The enhanced security properties are therefore achieved without compromising the multi-year operational lifetimes expected from industrial sensor deployments [48].
- Comparative Analysis: When compared to alternative security enhancement approaches that might require additional cryptographic operations or increased message exchanges, our sensor-initiated registration provides superior energy efficiency [34]. The protocol modifications achieve substantial security improvements while maintaining the energy characteristics that make the original protocol suitable for resource-constrained industrial applications [35].
9. Conclusions
Supplementary Materials
Funding
Data Availability Statement
Conflicts of Interest
Correction Statement
References
- Xu, L.D.; Xu, E.L.; Li, L. Industry 4.0: State of the art and future trends. Int. J. Prod. Res. 2018, 56, 2941–2962. [Google Scholar] [CrossRef]
- Kang, H.S.; Lee, J.Y.; Choi, S.; Choi, S.; Hong, B.; Choi, J.; Han, I.; Lee, J.K.; Hwang, J.; Kang, M. Smart manufacturing: Past research, present findings, and future directions. Int. J. Precis. Eng. Manuf.-Green Tech. 2016, 3, 111–128. [Google Scholar] [CrossRef]
- Sheng, Z.; Mahapatra, C.; Zhu, C.; Leung, V.C.M. Recent advances in industrial wireless sensor networks toward efficient management in IoT. IEEE Access 2015, 3, 622–637. [Google Scholar] [CrossRef]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Sen, J. Security and privacy issues in wireless sensor networks. In Wireless Sensor Networks: Current Status and Future Trends; CRC Press: Boca Raton, FL, USA, 2012; pp. 407–460. [Google Scholar]
- Zhang, Y.; Liu, W.; Lou, W.; Fang, Y. Location-based compromise-tolerant security mechanisms for wireless sensor networks. IEEE J. Sel. Areas Commun. 2006, 24, 247–260. [Google Scholar] [CrossRef]
- Cardenas, A.A.; Amin, S.; Sastry, S. Research challenges for the security of control systems. In Proceedings of the 3rd USENIX Workshop on Hot Topics in Security, San Jose, CA, USA, 29 July 2008. [Google Scholar]
- Zhu, B.; Joseph, A.; Sastry, S. A taxonomy of cyber attacks on SCADA systems. In Proceedings of the IEEE Internet of Things (iThings/CPSCom), Dalian, China, 19–22 October 2011; pp. 380–388. [Google Scholar]
- Li, X.; Ibrahim, M.H.; Kumari, S.; Sangaiah, A.K.; Gupta, V.; Choo, K.K.R. Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput. Netw. 2017, 129, 429–443. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Rodrigues, J.J.P.C.; Shetty, S.; Park, Y. LDAKM-EIoT: Lightweight device authentication and key management mechanism for edge-based IoT deployment. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inf. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Yannam, A.R.; Rodrigues, J.J.P.C.; Park, Y. Provably secure ECC-based device access control and key agreement protocol for IoT environment. IEEE Access 2019, 7, 55382–55397. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Gassend, B.; Clarke, D.; Van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Maes, R.; Verbauwhede, I. Physically unclonable functions: A study on the state of the art and future research directions. In Towards Hardware-Intrinsic Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 3–37. [Google Scholar]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical one-way functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Rührmair, U.; Devadas, S.; Koushanfar, F. Security based on physical unclonability and disorder. In Introduction to Hardware Security and Trust; Springer: New York, NY, USA, 2012; pp. 65–102. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Holcomb, D.E.; Burleson, W.P.; Fu, K. Power-up SRAM state as an identifying fingerprint and source of true random numbers. IEEE Trans. Comput. 2009, 58, 1198–1210. [Google Scholar] [CrossRef]
- Lim, D.; Lee, J.W.; Gassend, B.; Suh, G.E.; Van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2005, 13, 1200–1205. [Google Scholar]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and physically secure anonymous mutual authentication protocol for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inf. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Tomić, I.; McCann, J.A. A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet Things J. 2017, 4, 1910–1923. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.J.; Yoo, K.Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumari, S.; Li, X.; Wu, F. Design of sinkhole node detection mechanism for hierarchical wireless sensor networks. Secur. Commun. Netw. 2016, 9, 4596–4614. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, X. Industry 4.0: A survey on technologies, applications and open research issues. J. Ind. Inf. Integr. 2017, 6, 1–10. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and privacy for cloud-based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Sadeghi, A.R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous secure framework in connected smart home environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and privacy in smart city applications: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Ning, H.; Liu, H.; Yang, L.T. Cyberentity security in the internet of things. Computer 2013, 46, 46–53. [Google Scholar] [CrossRef]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the International Conference on Computational Intelligence and Security, Emeishan, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. PUF modeling attacks on simulated and silicon data. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1876–1891. [Google Scholar] [CrossRef]
- Machida, T.; Yamamoto, D.; Iwamoto, M.; Sakiyama, K. A new mode of operation for arbiter PUF to improve uniqueness on FPGA. In Proceedings of the Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 871–878. [Google Scholar]
- Rührmair, U.; Hilgers, C.; Urban, S.; Weiershausen, A.; Dinter, E.; Forster, T.; Sturm, C. Optical PUFs reloaded. IACR Cryptol. ePrint Arch. 2013, 2013, 215. [Google Scholar]
- Alvarez, R.; Peris-Lopez, P.; Tapiador, J.E. Physical unclonable functions: A piece-wise linear approach. In Information Security and Privacy Research; Springer: Berlin/Heidelberg, Germany, 2012; pp. 431–442. [Google Scholar]
- Majzoobi, M.; Koushanfar, F.; Potkonjak, M. Lightweight secure PUFs. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 10–13 November 2008; pp. 670–673. [Google Scholar]
- Helfmeier, C.; Boit, C.; Nedospasov, D.; Seifert, J.P. Cloning physically unclonable functions. In Proceedings of the IEEE International Symposium on Hardware-Oriented Security and Trust, Austin, TX, USA, 2–3 June 2013; pp. 1–6. [Google Scholar]
- Yu, M.D.; M’Raihi, D.; Verbauwhede, I.; Devadas, S. A noise bifurcation architecture for linear additive physical functions. In Proceedings of the IEEE International Symposium on Hardware-Oriented Security and Trust, Arlington, VA, USA, 6–7 May 2014; pp. 124–129. [Google Scholar]
- Delvaux, J.; Verbauwhede, I. Side channel modeling attacks on 65nm arbiter PUFs exploiting CMOS device variation. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition, Austin, TX, USA, 2–3 June 2013; pp. 97–102. [Google Scholar]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embed. Comput. Syst. 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT systems: Design challenges and opportunities. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 2–6 November 2014; pp. 417–423. [Google Scholar]
- Braeken, A. PUF based authentication protocol for IoT. Symmetry 2018, 10, 352. [Google Scholar] [CrossRef]
- Alamelou, Q.; Berthier, P.E.; Cachet, C.; Cagli, E.; Dassance, F.; Durvaux, F.; Fontaine, C.; Giry, C.; Grosso, V. A PUF-based mutual authentication protocol for IoT. In Cryptology and Network Security; Springer: Singapore, 2018; pp. 209–233. [Google Scholar]
- Tsudik, G. A family of dunces: Trivial RFID identification and authentication protocols. In Privacy Enhancing Technologies; Springer: Berlin/Heidelberg, Germany, 2007; pp. 45–61. [Google Scholar]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Estevez-Tapiador, J.M.; Ribagorda, A. RFID systems: A survey on security threats and proposed solutions. In Personal Wireless Communications; Springer: Berlin/Heidelberg, Germany, 2006; pp. 159–170. [Google Scholar]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; pp. 244–251. [Google Scholar]



| Notation | Description |
|---|---|
| A sensor node in IWSN | |
| U | A user in IWSN |
| The unique identity of U | |
| Temporary identity of U | |
| The unique identity of Sn | |
| PID | Set of pseudo identities |
| Challenge–response pair | |
| P | Physically unclonable function |
| Password of U | |
| Biometric thumb impression of U | |
| sk, SK | Session keys |
| A one-way cryptographic hash function |
| Aspect | Gope et al. [27] (Original) | Proposed Scheme |
| Challenge Generation | Gateway-initiated handshake. Sensor passively responds to gateway challenges. | Sensor-initiated handshake. Sensor generates and controls its own challenges. |
| MITM resistance | Vulnerable. No mechanism to prevent unauthorized PUF queries during registration. | Resistant. Sensor controls challenge generation, preventing rogue registrations. |
| DoS resistance | Vulnerable. Attackers can exploit unverified registration requests. | Resistant. Sensor ignores unsolicited requests; gateway performs lightweight verification. |
| Performance Overhead | Baseline | Negligible additional overhead (same message count, minimal computation) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alyanbaawi, A. MITM- and DoS-Resistant PUF Authentication for Industrial WSNs via Sensor-Initiated Registration. Computers 2025, 14, 347. https://doi.org/10.3390/computers14090347
Alyanbaawi A. MITM- and DoS-Resistant PUF Authentication for Industrial WSNs via Sensor-Initiated Registration. Computers. 2025; 14(9):347. https://doi.org/10.3390/computers14090347
Chicago/Turabian StyleAlyanbaawi, Ashraf. 2025. "MITM- and DoS-Resistant PUF Authentication for Industrial WSNs via Sensor-Initiated Registration" Computers 14, no. 9: 347. https://doi.org/10.3390/computers14090347
APA StyleAlyanbaawi, A. (2025). MITM- and DoS-Resistant PUF Authentication for Industrial WSNs via Sensor-Initiated Registration. Computers, 14(9), 347. https://doi.org/10.3390/computers14090347






