Towards a Better Understanding of Mobile Banking App Adoption and Use: Integrating Security, Risk, and Trust into UTAUT2
Abstract
1. Introduction
- 72% of respondents reported using their banking app multiple times per week.
- 74% stated that they feel secure using their banking app for online banking.
- 51% expressed concerns about fraud when shopping online.
- 71% indicated that they prioritise transaction security over user experience.
2. Background
2.1. Factors Influencing Adoption
2.1.1. Security, Risk, and Trust
2.1.2. Individual Characteristics
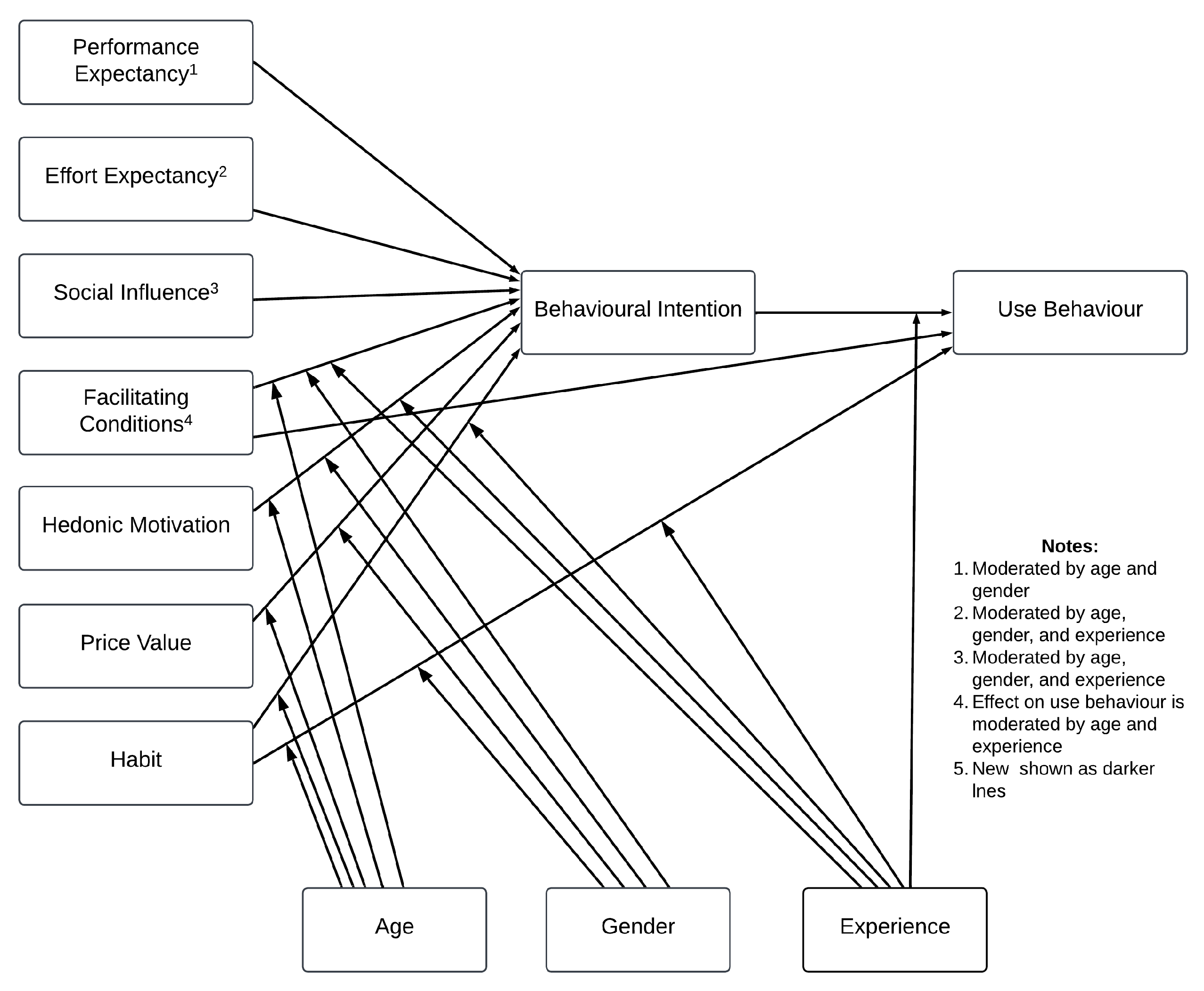
2.2. Theoretical Framework
UTAUT Models
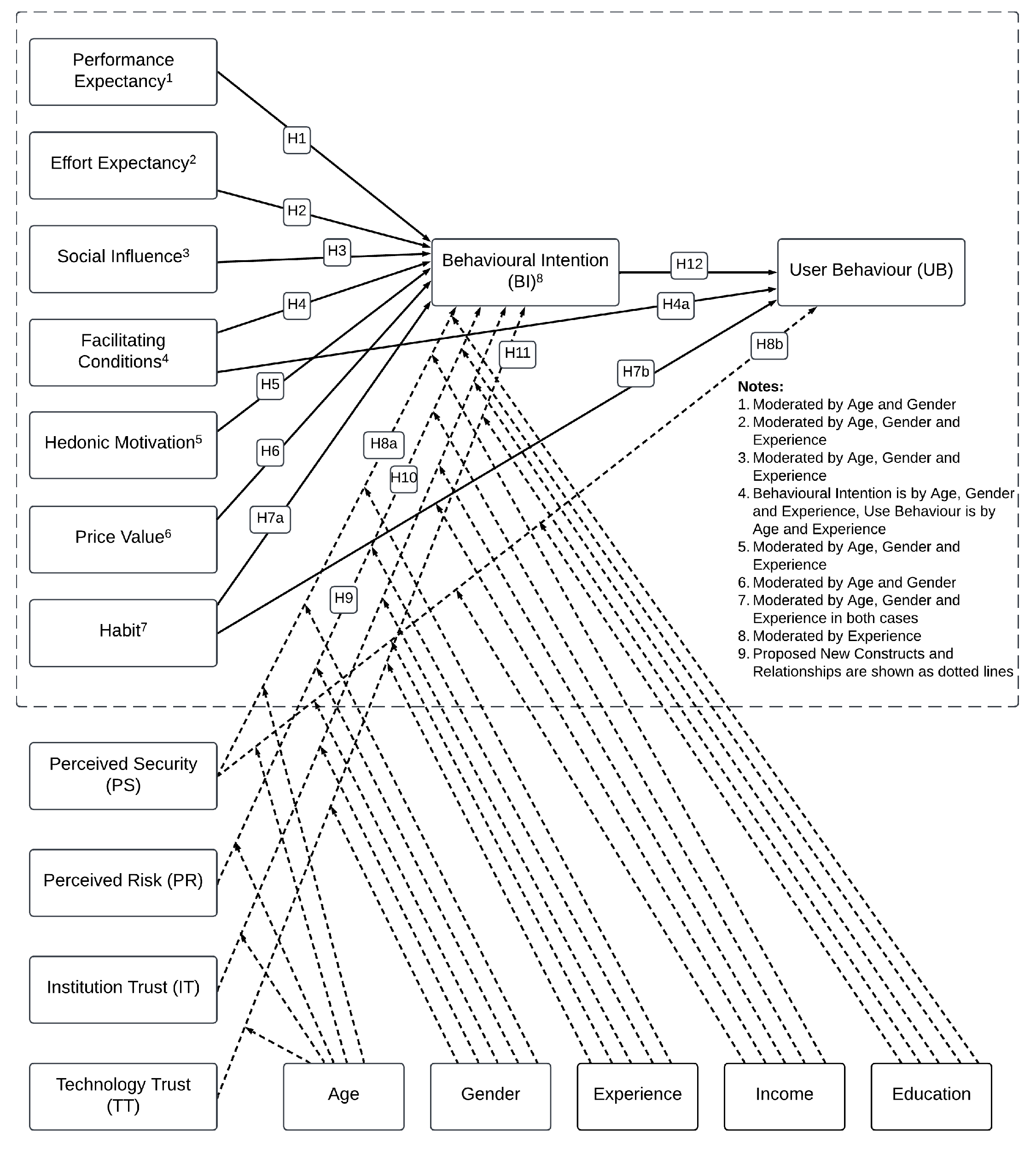
2.3. Conceptual Model for the Study
2.4. Hypotheses Formulation
2.5. Performance Expectancy (PE)
2.6. Effort Expectancy (EE)
2.7. Social Influence (SI)
2.8. Facilitating Conditions (FC)
2.9. Hedonic Motivation (HM)
2.10. Price Value (PV)
2.11. Habit (HB)
2.12. Perceived Security (PS)
2.13. Perceived Risk (PR)
2.14. Institutional Trust (IT)
2.15. Technological Trust (TT)
2.16. Behavioural Intention (BI)
3. Methodology
3.1. Data Collection
3.2. Measurements of the Latent Variables
3.3. Data Analysis
4. Results
4.1. Descriptive Analysis
4.2. Analysis of Measurement Model
- CR values need to exceed the recommended level of 0.7 to ensure adequate or sufficient internal consistency [100]; similarly, a large Cronbach’s alpha (>0.7) suggests high internal consistency, meaning that the test is measuring one attribute.
- Convergent validity confirms the reflective nature of each construct by its own indicators, ensuring that multiple-item factors are unidimensional [89] and that unreliable indicators are eliminated [101]. To ensure convergent validity, AVE should exceed 0.5 [102], in addition to being smaller than the CR.
- Discriminant validity ensures that the latent constructs used for measuring the causal relationships under study are truly distinct from one another, eliminating risk of multicollinearity [89]. Discriminant validity of the construct is achieved when the square root of the AVE is greater than the correlation between the constructs, which is a method known as the Fornell–Lacker criterion [103].
- The discriminant validity can be further evaluated by using cross-loadings. Cross-loading indicates that the item measures several factors. This item could be the source of multicollinearity between the factors, which is not desirable, as distinct factors are required. To establish discriminant validity at the item level, there should be a high correlation between items of the same construct and a very weak correlation between items of a different construct. A “cross-loading” item is an item that loads at 0.32 or higher on two or more factors. However, the rule of thumb suggests that a cross factor loading of not more than 0.7 is acceptable for discriminant validity [103]. By looking at cross-loading, the factor loading indicators on the assigned construct have to be higher than all loading of other constructs with the condition that the cut-off value of factor loading is higher than 0.7.
- KMO can be used to assess sampling adequacy, referring to how strongly an item is correlated with other items in the EFA correlation matrix. KMO ranges from 0 to 1, with a correlation above 0.6 indicating sample adequacy for analysing the EFA output (Netemeyer et al., 1991 [104], Bearden et al., 2003 [105]). On the other hand, Bartlett’s test of sphericity (Bartlett 1950 [106]) indicates the item correlation matrix is not an identity matrix, providing a chi-square output that must be significant (p < 0.05) for factor analysis to be suitable. When both measures are satisfactory, researchers can move forward with exploratory factor analysis (EFA).
4.3. Analysis of Structural Model
4.3.1. Hypothesis Testing
- H2 which posited a positive impact of EE on BI;
- H4 which posited a positive impact of both FC on BI and UB;
- H5 which posited a positive impact of HM on BI;
- H6 which posited a positive impact of PV on BI;
- H7 which posited a positive impact of HB on both BI and UB.
- H8, which posited a positive impact of PS on both BI and UB;
- H10, which posited a positive impact of IT on BI;
- H11, which posited a positive impact of TT on BI.
4.3.2. Moderating Effects
- Age, gender, experience, income, and education moderated the relationship between PS and BI (, p > 0.05), and between IT and BI ( = −1.718, p > 0.01), which supported H8 and H10. For PS, the effect was stronger for younger men, particularly with high income and high education in early stages of experience with m-banking adoption; whereas for IT, the effect was stronger for older women, particularly with high income and education in later stages of experience.
- Age, education, and experience moderated the relationship between TT and BI ( = −1.523, p > 0.01), such that the effect was stronger for older people with high education in later stages of experience. This confirmed H11.
- Age, gender, and experience moderated the relationship between PS and UB ( = 2.344, p > 0.001), such that he effect was stronger for younger men in early stages of experience. This confirmed H8.
5. Discussion
5.1. Perceived Security
5.2. Perceived Risk
5.3. Trust
5.4. Validated Constructs
5.4.1. Effort Expectancy
5.4.2. Facilitating Condition
5.4.3. Hedonic Motivation
5.4.4. Price Value
5.4.5. Habit
5.4.6. Performance Expectancy and Social Influence
6. Conclusions and Future Work
6.1. Conclusions
6.2. Main Contribution and Advancement of Research
6.3. Managerial and Practical Implications
6.4. Limitations and Directions for Future Research
- Non-probability convenience sampling: This method involves selecting participants who are readily available and willing to participate, rather than using random sampling techniques.
- Homogeneity and accessibility: While the study considered the homogeneity of the population and ease of access to respondents, it did not ensure that all relevant subgroups of the population were proportionately represented.
- Demographic representation: The study did not specify whether key demographic characteristics of the sample matched those of the overall population of mobile banking users.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Shankar, A.; Rishi, B. Convenience matter in mobile banking adoption intention? Australas. Mark. J. 2020, 28, 273–285. [Google Scholar] [CrossRef]
- Zhu, Q.; Lyu, Z.; Long, Y.; Wachenheim, C.J. Adoption of mobile banking in rural China: Impact of information dissemination channel. Socio-Econ. Plan. Sci. 2022, 83, 101011. [Google Scholar] [CrossRef]
- Jebarajakirthy, C.; Shankar, A. Impact of online convenience on mobile banking adoption intention: A moderated mediation approach. J. Retail. Consum. Serv. 2021, 58, 102323. [Google Scholar] [CrossRef]
- Karjaluoto, H.; Shaikh, A.A.; Saarijärvi, H.; Saraniemi, S. How perceived value drives the use of mobile financial services apps. Int. J. Inf. Manag. 2019, 47, 252–261. [Google Scholar] [CrossRef]
- Entersekt. Fighting Back Against Mobile Banking and Payments Fraud in Europe. Entersekt Blog. 2022. pp. 1–12. Available online: https://www.entersekt.com/resources/blog/tpost/s6kn87x601-fighting-mobile-banking-and-online-payme (accessed on 1 April 2025).
- To, A.T.; Trinh, T.H.M. Understanding behavioral intention to use mobile wallets in vietnam: Extending the tam model with trust and enjoyment. Cogent Bus. Manag. 2021, 8, 1891661. [Google Scholar] [CrossRef]
- Nokia. Threat Intelligence Report. Nokia. 2023. pp. 1–12. Available online: https://www.nokia.com/networks/security-portfolio/threat-intelligence-report/ (accessed on 1 April 2025).
- UKFinance. 2023 Half Year Fraud Report. UKFinance. 2023. pp. 1–12. Available online: https://www.ukfinance.org.uk/policy-and-guidance/reports-and-publications/2023-half-year-fraud-report (accessed on 1 April 2025).
- Irwin, K. New ‘Snowblind’ Banking Malware Targets Android Users with Linux Kernel Exploit. PCMag 2024, pp. 1–12. Available online: https://uk.pcmag.com/security/152989/new-snowblind-banking-malware-targets-android-users-with-linux-kernel-exploit (accessed on 1 April 2025).
- Alnajim, A.M.; Habib, S.; Islam, M.; AlRawashdeh, H.S.; Wasim, M. Exploring cybersecurity education and training techniques: A comprehensive review of traditional, virtual reality, and augmented reality approaches. Symmetry 2023, 15, 2175. [Google Scholar] [CrossRef]
- Ramli, Y.; Harwani, Y.; Soelton, M.; Hariani, S.; Usman, F.; Rohman, F. The implication of trust that influences customers’ intention to use mobile banking. J. Asian Financ. Econ. Bus. 2021, 8, 353–361. [Google Scholar] [CrossRef]
- Kumar, S.; Yukita, A.L.K. Millennials behavioral intention in using mobile banking: Integrating perceived risk and trust into tam (a survey in jawa barat). In International Conference on Business and Engineering Management (ICONBEM 2021); Atlantis Press: Dordrecht, The Netherlands, 2021; pp. 210–217. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Al-Otaibi, S.; Shishakly, R.; Hassan, L.; Lutfi, A.; Alrawad, M.; Qatawneh, M.; Alghanam, O.A. Investigating the role of perceived risk, perceived security and perceived trust on smart m-banking application using sem. Sustainability 2023, 15, 9908. [Google Scholar] [CrossRef]
- Abdennebi, H.B. M-banking adoption from the developing countries perspective: A mediated model. Digit. Bus. 2023, 3, 100065. [Google Scholar] [CrossRef]
- Obaid, T. Predicting mobile banking adoption: An integration of tam and tpb with trust and perceived risk. Financ. Internet Q. 2021, 17, 35–46. [Google Scholar] [CrossRef]
- Merhi, M.; Hone, K.; Tarhini, A.; Ameen, N. An empirical examination of the moderating role of age and gender in consumer mobile banking use: A cross-national, quantitative study. J. Enterp. Inf. Manag. 2021, 34, 1144–1168. [Google Scholar] [CrossRef]
- Merhi, M.; Hone, K.; Tarhini, A. A cross-cultural study of the intention to use mobile banking between lebanese and british consumers: Extending utaut2 with security, privacy and trust. Technol. Soc. 2019, 59, 101151. [Google Scholar] [CrossRef]
- Mutahar, A.M.; Daud, N.M.; Ramayah, T.; Isaac, O.; Aldholay, A.H. The effect of awareness and perceived risk on the technology acceptance model (tam): Mobile banking in yemen. Int. J. Serv. Stand. 2018, 12, 180–204. [Google Scholar] [CrossRef]
- Lim, S.H.; Kim, D.J.; Hur, Y.; Park, K. An empirical study of the impacts of perceived security and knowledge on continuous intention to use mobile fintech payment services. Int. J. Hum.-Comput. Interact. 2019, 35, 886–898. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, R.; Kumar, K.; Khan, S.; Corvello, V. How does perceived risk and trust affect mobile banking adoption? empirical evidence from india. Sustainability 2023, 15, 4053. [Google Scholar] [CrossRef]
- Tian, Y.; Chan, T.J.; Suki, N.M.; Kasim, M.A. Moderating role of perceived trust and perceived service quality on consumers’ use behavior of alipay e-wallet system: The perspectives of technology acceptance model and theory of planned behavior. Hum. Behav. Emerg. Technol. 2023, 2023, 5276406. [Google Scholar] [CrossRef]
- Jadil, Y.; Rana, N.P.; Dwivedi, Y.K. A meta-analysis of the UTAUT model in the mobile banking literature: The moderating role of sample size and culture. J. Bus. Res. 2021, 132, 354–372. [Google Scholar] [CrossRef]
- Lin, R.-R.; Zheng, Y.; Lee, J.-C. Artificial intelligence-based pre-implementation interventions in users’ continuance intention to use mobile banking. Int. J. Mob. Commun. 2023, 21, 518–540. [Google Scholar] [CrossRef]
- Tang, J.W.; Tsai, P.H. Exploring critical determinants influencing businesses’ continuous usage of mobile payment in post-pandemic era: Based on the UTAUT2 perspective. Technol. Soc. 2024, 77, 102554. [Google Scholar] [CrossRef]
- Zhang, M.; Hassan, H.; Migin, M.W. Exploring the consumers’ purchase intention on online community group buying platform during pandemic. Sustainability 2023, 15, 2433. [Google Scholar] [CrossRef]
- Kimiagari, S.; Baei, F. Promoting e-banking actual usage: Mix of technology acceptance model and technology-organisation-environment framework. Enterp. Inf. Syst. 2022, 16, 1894356. [Google Scholar] [CrossRef]
- Ahmed, M.S.; Everett, J.; Turnbull, W. Extracting best set of factors that affect students’ adoption of smartphone for university education: Empirical evidence from utaut-2 model. J. Manag. Econ. Ind. Organ. 2017, 1, 51–64. [Google Scholar] [CrossRef]
- El-Masri, M.; Tarhini, A. Factors affecting the adoption of e-learning systems in qatar and USA: Extending the unified theory of acceptance and use of technology 2 (utaut2). Educ. Technol. Res. Dev. 2017, 65, 743–763. [Google Scholar] [CrossRef]
- Rehman, Z.U.; Shaikh, F.A. Critical factors influencing the behavioral intention of consumers towards mobile banking in malaysia. Eng. Technol. Appl. Sci. Res. 2020, 10, 5265–5269. [Google Scholar] [CrossRef]
- Prabhakaran, S.; Vasantha, D.S.; Sarika, P. Effect of social influence on intention to use mobile wallet with the mediating effect of promotional benefits. J. Xi’An Univ. Archit. Technol. 2020, 12, 3003–3019. [Google Scholar]
- Win, N.N.; Aung, P.P.; Phyo, M.T. Factors influencing behavioral intention to use and use behavior of mobile banking in myanmar using a model based on unified acceptance theory. Hum. Behav. Dev. Soc. 2021, 22. [Google Scholar]
- Tham, J.; Ab Yazid, M.S.; Khatibi, A.A.; Azam, S.F. Internet and data security–understanding customer perception on trusting virtual banking security in malaysia. Eur. J. Soc. Sci. Stud. 2017. Available online: https://oapub.org/soc/index.php/EJSSS/article/view/199 (accessed on 1 April 2025).
- Stewart, H.; Jürjens, J. Data security and consumer trust in fintech innovation in germany. Inf. Comput. Secur. 2018, 26, 109–128. [Google Scholar] [CrossRef]
- Apau, R.; Koranteng, F.N.; Gyamfi, S.A. Cyber-crime and its effects on e-commerce technologies. J. Inf. 2019, 5, 39–59. [Google Scholar] [CrossRef]
- Chen, C. Perceived risk, usage frequency of mobile banking services. Manag. Serv. Qual. Int. J. 2013, 23, 410–436. [Google Scholar] [CrossRef]
- Chand, K.; Tiwari, R.; Gupta, A.; Taneja, S.; Özen, E. How does perceived security influence mobile wallet users’ behavior? A SEM investigation. Manag. Financ. 2025, 51, 146–165. [Google Scholar] [CrossRef]
- Nguyen, G.D.; Dao, T.H.T. Factors influencing continuance intention to use mobile banking: An extended expectation-confirmation model with moderating role of trust. Humanit. Soc. Sci. Commun. 2024, 11, 1–14. [Google Scholar] [CrossRef]
- Pentina, I.; Zhang, L.; Bata, H.; Chen, Y. Exploring privacy paradox in information-sensitive mobile app adoption: A cross-cultural comparison. Comput. Hum. Behav. 2016, 65, 409–419. [Google Scholar] [CrossRef]
- Williams, M.D. Social commerce and the mobile platform: Payment and security perceptions of potential users. Comput. Hum. Behav. 2021, 115, 105557. [Google Scholar] [CrossRef]
- Hanif, Y.; Lallie, H.S. Security factors on the intention to use mobile banking applications in the uk older generation (55+). A mixed-method study using modified utaut and mtam-with perceived cyber security, risk, and trust. Technol. Soc. 2021, 67, 101693. [Google Scholar] [CrossRef]
- Rahi, S.; Abd. Ghani, M. The role of utaut, doi, perceived technology security and game elements in internet banking adoption. World J. Sci. Technol. Sustain. Dev. 2018, 15, 338–356. [Google Scholar] [CrossRef]
- Singh, S.; Srivastava, R. Understanding the intention to use mobile banking by existing online banking customers: An empirical study. J. Financ. Serv. Mark. 2020, 25, 86–96. [Google Scholar] [CrossRef]
- Namahoot, K.S.; Laohavichien, T. Assessing the intentions to use internet banking: The role of perceived risk and trust as mediating factors. Int. J. Bank Mark. 2018, 36, 256–276. [Google Scholar] [CrossRef]
- Alonso-Dos-Santos, M.; Soto-Fuentes, Y.; Valderrama-Palma, V. Determinants of mobile banking users’ loyalty. J. Promot. Manag. 2020, 26, 615–633. [Google Scholar] [CrossRef]
- Chauhan, V.; Yadav, R.; Choudhary, V. Adoption of electronic banking services in india: An extension of utaut2 model. J. Financ. Serv. Mark. 2022, 27, 27–40. [Google Scholar] [CrossRef]
- Arenas Gaitán, J.; Peral Peral, B.; Ángeles Ramón Jerónimo, M. Elderly and internet banking: An application of UTAUT2. J. Internet Bank. Commer. 2015, 20, 1–23. [Google Scholar]
- Wang, X. Exploring the relationship among technology acceptance, learner engagement, and critical thinking. Educ. Inf. Technol. 2021, 26, 13375–13390. [Google Scholar] [CrossRef]
- Chawla, D.; Joshi, H. The moderating effect of demographic variables on mobile banking adoption: An empirical investigation. Glob. Bus. Rev. 2018, 19, S90–S113. [Google Scholar] [CrossRef]
- Liébana-Cabanillas, F.; Sánchez-Fernández, J.; Muñoz-Leiva, F. Antecedents of the adoption of the new mobile payment systems: The moderating effect of age. Comput. Hum. Behav. 2014, 35, 464–478. [Google Scholar] [CrossRef]
- Sharma, N. A digital cohort analysis of consumers’ mobile banking app experience. Int. J. Consum. Stud. 2024, 48, e12989. [Google Scholar] [CrossRef]
- Merhi, M. Investigating the Factors Driving Consumers’ Intention to Use Mobile Banking; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar] [CrossRef]
- Merhi, M. A systematic review of the behavior intention on mobile banking. Semant. Sch. 2019, 7, 2024112. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. Mis Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Venkatesh, V.; Thong, J.Y.; Xu, X. Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology. Mis Q. 2012, 36, 157–178. [Google Scholar] [CrossRef]
- Rogers, E. Diffusion of Innovations; The Free Press: New York, NY, USA, 1995. [Google Scholar]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Addison-Wesley: Boston, MA, USA, 1977. [Google Scholar]
- Ajzen, I. The theory of planned behaviour. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. Mis Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Featherman, M.S.; Pavlou, P.A. Predicting e-services adoption: A perceived risk facets perspective. Int. J. Hum.-Comput. Stud. 2003, 59, 451–474. [Google Scholar] [CrossRef]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. Extrinsic and intrinsic motivation to use computers in the workplace 1. J. Appl. Soc. Psychol. 1992, 22, 1111–1132. [Google Scholar] [CrossRef]
- Thompson, R.L.; Higgins, C.A.; Howell, J.M. Personal computing: Toward a conceptual model of utilization. Mis Q. 1991, 15, 125–143. [Google Scholar] [CrossRef]
- Bandura, A. Social Foundations of Thought and Action; SAGE: Englewood Cliffs, NJ, USA, 1986; p. 2. [Google Scholar] [CrossRef]
- Taylor, S.; Todd, P.A. Understanding information technology usage: A test of competing models. Inf. Syst. Res. 1995, 6, 144–176. [Google Scholar] [CrossRef]
- Venkatesh, V.; Brown, S.A.; Bala, H. Bridging the qualitative-quantitative divide: Guidelines for conducting mixed methods research in information systems. Mis Q. 2013, 37, 21–54. [Google Scholar] [CrossRef]
- Venkatesh, V.; Zhang, X. Unified theory of acceptance and use of technology: US vs. China. J. Glob. Inf. Technol. Manag. 2010, 13, 5–27. [Google Scholar] [CrossRef]
- Negahban, A.; Chung, C.-H. Discovering determinants of users perception of mobile device functionality fit. Comput. Hum. Behav. 2014, 35, 75–84. [Google Scholar] [CrossRef]
- Montesdioca, G.P.Z.; Maçada, A.C.G. Measuring user satisfaction with information security practices. Comput. Secur. 2015, 48, 267–280. [Google Scholar] [CrossRef]
- Alalwan, A.A.; Dwivedi, Y.K.; Rana, N.P. Factors influencing adoption of mobile banking by jordanian bank customers: Extending utaut2 with trust. Int. J. Inf. Manag. 2017, 37, 99–110. [Google Scholar] [CrossRef]
- Aboelmaged, M.G.; Gebba, T.R. Mobile banking adoption: An examination of technology acceptance model and theory of planned behavior. Int. J. Bus. Res. Dev. 2013, 2, 35–50. [Google Scholar] [CrossRef]
- Raza, S.A.; Umer, A.; Shah, N. New determinants of ease of use and perceived usefulness for mobile banking adoption. Int. J. Electron. Cust. Relatsh. Manag. 2017, 11, 44–65. [Google Scholar] [CrossRef]
- Akturan, U.; Tezcan, N. Mobile banking adoption of the youth market: Perceptions and intentions. Mark. Intell. Plan. 2012, 30, 444–459. [Google Scholar] [CrossRef]
- Oliveira, T.; Thomas, M.; Baptista, G.; Campos, F. Mobile payment: Understanding the determinants of customer adoption and intention to recommend the technology. Comput. Hum. Behav. 2016, 61, 404–414. [Google Scholar] [CrossRef]
- Wazid, M.; Zeadally, S.; Das, A.K. Mobile banking: Evolution and threats: Malware threats and security solutions. IEEE Consum. Electron. Mag. 2019, 8, 56–60. [Google Scholar] [CrossRef]
- Saibaba, S. Examining the determinants of mobile banking app continuance intention in India: An extension of the IS success model. J. Internet Commer. 2024, 23, 50–89. [Google Scholar] [CrossRef]
- Mullan, J.; Bradley, L.; Loane, S. Bank adoption of mobile banking: Stakeholder perspective. Int. J. Bank Mark. 2017, 35, 1154–1174. [Google Scholar] [CrossRef]
- Aggarwal, A.; Sharma, R.; Singh, P. Will I virtually try and buy?—exploring the adoption of virtual fitting rooms through the lens of perceived value, risk, and consumer characteristics. Int. Rev. Retail. Distrib. Consum. Res. 2025, 2025, 1–32. [Google Scholar] [CrossRef]
- Martins, C.; Oliveira, T.; Popovič, A. Understanding the internet banking adoption: A unified theory of acceptance and use of technology and perceived risk application. Int. J. Inf. Manag. 2014, 34, 1–13. [Google Scholar] [CrossRef]
- Du, T.; Agami, A. Examining young users’ security perceptions of mobile banking: A qualitative study on users’ insights about mobile banking. Umeå Sch. Bus. Econ. 2017, 1–30. [Google Scholar] [CrossRef]
- Roy, S.K.; Balaji, M.; Kesharwani, A.; Sekhon, H. Predicting internet banking adoption in india: A perceived risk perspective. J. Strateg. Mark. 2017, 25, 418–438. [Google Scholar] [CrossRef]
- Roopnarain, M.; Mwapwele, S.D. Factors influencing the adoption and usage of blockchain in e-commerce: A systematic literature review. Afr. J. Sci. Technol. Innov. Dev. 2025, 2025, 1–14. [Google Scholar] [CrossRef]
- Apau, R.; Koranteng, F.N. Impact of cybercrime and trust on the use of e-commerce technologies: An application of the theory of planned behavior. Int. J. Cyber Criminol. 2019, 13, 228–254. [Google Scholar]
- Al-Sharafi, A.; Arshah, R.A.; Alajmi, Q.; Herzallah, A.; Qasem, Y. The influence of perceived trust on understanding banks’ customers behavior to accept internet banking services. Indian J. Sci. Technol. 2018, 11, 1–9. [Google Scholar] [CrossRef]
- Fachrudin, K.A.; Amin, S.I.M.; Ab Hamid, S.N.; Latifah, S.; Lubis, M.A. Which UTAUT Elements Drive Mobile Banking Adoption in Indonesia, Despite Security and Trust Concerns? J. Ecohumanism 2025, 4, 682–693. [Google Scholar] [CrossRef]
- Resnik, D. The Ethics of Research with Human Subjects: Protecting People, Advancing Science, Promoting Trust; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- O’Sullivan, L.; Feeney, L.; Crowley, R.K.; Sukumar, P.; McAuliffe, E.; Doran, P. An evaluation of the process of informed consent: Views from research participants and staff. Trials 2021, 22, 544. [Google Scholar] [CrossRef]
- Brace, I. Questionnaire Design: How to Plan, Structure and Write Survey Material for Effective Market Research; Kogan Page Publishers: London, UK, 2018. [Google Scholar]
- Preston, C.C.; Colman, A.M. Optimal number of response categories in rating scales: Reliability, validity, discriminating power, and respondent preferences. Acta Psychol. 2000, 104, 1–15. [Google Scholar] [CrossRef]
- Im, I.; Hong, S.; Kang, M.S. An international comparison of technology adoption: Testing the utaut model. Inf. Manag. 2011, 48, 1–8. [Google Scholar] [CrossRef]
- Gefen, D.; Straub, D.; Boudreau, M.-C. Structural equation modeling and regression: Guidelines for research practice. Commun. Assoc. Inf. Syst. 2000, 4, 7. [Google Scholar] [CrossRef]
- Jöreskog, K.G.; Sörbom, D. Recent developments in structural equation modeling. J. Mark. Res. 1982, 19, 404–416. [Google Scholar] [CrossRef]
- Chin, W.; Cheah, J.-H.; Liu, Y.; Ting, H.; Lim, X.-J.; Cham, T.H. Demystifying the role of causal-predictive modeling using partial least squares structural equation modeling in information systems research. Ind. Manag. Data Syst. 2020, 120, 2161–2209. [Google Scholar] [CrossRef]
- Tabachnick, B.G.; Fidell, L.S.; Ullman, J.B. Using Multivariate Statistics; Pearson: Boston, MA, USA, 2013; Volume 6. [Google Scholar]
- Wang, J.; Wang, X. Structural Equation Modeling: Applications Using Mplus; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar] [CrossRef]
- Anderson, J.C.; Gerbing, D.W. Structural equation modeling in practice: A review and recommended two-step approach. Psychol. Bull. 1988, 103, 411. [Google Scholar] [CrossRef]
- Coltman, T.; Devinney, T.M.; Midgley, D.F.; Venaik, S. Formative versus reflective measurement models: Two applications of formative measurement. J. Bus. Res. 2008, 61, 1250–1262. [Google Scholar] [CrossRef]
- Pezzullo, J.C. Biostatistics for Dummies; John Wiley & Sons: Hoboken, NJ, USA, 2013. [Google Scholar]
- Kline, R.B. Principles and Practice of Structural Equation Modeling; Guilford Publications: New York, NY, USA, 2023. [Google Scholar]
- Brown, T.A. Confirmatory Factor Analysis for Applied Research; Guilford Publications: New York, NY, USA, 2015. [Google Scholar]
- Ryans, A.B. Estimating consumer preferences for a new durable brand in an established product class. J. Mark. Res. 1974, 11, 434–443. [Google Scholar] [CrossRef]
- Hair, J.F., Jr.; Sarstedt, M.; Matthews, L.M.; Ringle, C.M. Identifying and treating unobserved heterogeneity with fimix-pls: Part i—Method. Eur. Bus. Rev. 2016, 28, 63–76. [Google Scholar] [CrossRef]
- Bollen, K.A. A new incremental fit index for general structural equation models. Sociol. Methods Res. 1989, 17, 303–316. [Google Scholar] [CrossRef]
- Wixom, B.H.; Watson, H.J. An empirical investigation of the factors affecting data warehousing success. Mis Q. 2001, 25, 17–41. [Google Scholar] [CrossRef]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Netemeyer, R.G.; Durvasula, S.; Lichtenstein, D.R. A cross-national assessment of the reliability and validity of the CETSCALE. J. Mark. Res. 1991, 28, 320–327. [Google Scholar] [CrossRef]
- Bearden, W.O.; Carlson, J.P.; Hardesty, D.M. Using invoice price information to frame advertised offers. J. Bus. Res. 2003, 56, 355–366. [Google Scholar] [CrossRef]
- Bartlett, M.S. Tests of significance in factor analysis. Br. J. Psychol. 1950, 3, 77–85. [Google Scholar] [CrossRef]
- Tomaschek, F.; Hendrix, P.; Baayen, R.H. Strategies for addressing collinearity in multivariate linguistic data. J. Phon. 2018, 71, 249–267. [Google Scholar] [CrossRef]
- Liang, H.; Saraf, N.; Hu, Q.; Xue, Y. Assimilation of enterprise systems: The effect of institutional pressures and the mediating role of top management. Mis Q. 2007, 31, 59–87. [Google Scholar] [CrossRef]
- Malhotra, N.K.; Kim, S.S.; Patil, A. Common method variance in is research: A comparison of alternative approaches and a reanalysis of past research. Manag. Sci. 2006, 52, 1865–1883. [Google Scholar] [CrossRef]
- Lindell, M.K.; Whitney, D.J. Accounting for common method variance in cross-sectional research designs. J. Appl. Psychol. 2001, 86, 114. [Google Scholar] [CrossRef] [PubMed]
- Patel, K.J.; Patel, H.J. Adoption of internet banking services in gujarat: An extension of tam with perceived security and social influence. Int. J. Bank Mark. 2018, 36, 147–169. [Google Scholar] [CrossRef]
- Shareef, M.A.; Baabdullah, A.; Dutta, S.; Kumar, V.; Dwivedi, Y.K. Consumer adoption of mobile banking services: An empirical examination of factors according to adoption stages. J. Retail. Consum. Serv. 2018, 43, 54–67. [Google Scholar] [CrossRef]
- Wiafe, I.; Koranteng, F.N.; Obeng, E.N.; Assyne, N.; Wiafe, A.; Gulliver, S.R. Artificial intelligence for cybersecurity: A systematic mapping of literature. IEEE Access 2020, 8, 146598–146612. [Google Scholar] [CrossRef]


| Construct | Indicators | Indicators Text |
|---|---|---|
| Performance Expectancy (PE) | PE1 | I find mobile banking apps useful in my daily life [53,64] |
| PE2 | Using mobile banking apps help me accomplish tasks more quickly | |
| PE3 | Using mobile banking apps increase my productivity | |
| Effort Expectancy (EE) | EE1 | Learning how to use mobile banking apps is easy for me |
| EE2 | My interaction with mobile banking apps is clear and understandable | |
| EE3 | I find mobile banking apps easy to use | |
| EE4 | It is easy for me to become skilful at using mobile banking apps | |
| Social Influence (SI) | SI1 | People who are important to me think I should use mobile banking apps |
| SI2 | People who influence my behaviour think that I should use mobile banking apps | |
| SI3 | People whose opinions that I value prefer that I use mobile banking apps | |
| Facilitating Conditions (FC) | FC1 | I have the resources necessary to use mobile banking apps |
| FC3 | I have the knowledge necessary to use mobile banking apps | |
| FC3 | Mobile banking apps are compatible with other technologies I use | |
| FC4 | I can get help from others when I have difficulties using mobile banking apps | |
| Hedonic Motivation (HM) | HM1 | Using mobile banking apps is fun [54] |
| HM2 | Using mobile banking apps is enjoyable | |
| HM3 | Using mobile banking apps is very entertaining | |
| Habit (HB) | HB1 | The use of mobile banking apps has become a habit for me |
| HB2 | I am addicted to using mobile banking apps | |
| HB3 | I must use mobile banking apps | |
| Price Value (PV) | PV1 | Mobile banking apps I use are reasonably priced |
| PV2 | Mobile banking apps I use are good value for the money | |
| PV3 | At the current price, the mobile banking apps I use provide good value | |
| Perceived Security (PS) | PS1 | I perceive mobile banking apps as secure [48] |
| PS2 | Mobile banking apps have rigorous security controls | |
| PS3 | I believe that transactions through mobile banking apps are protected and secured [17] | |
| Perceived Risk (PR) | PR1 | The chances of losing money if I use mobile banking apps are high [59] |
| PR2 | Internet hackers (criminals) might take control of my account if I use mobile banking apps | |
| PR3 | On the whole, considering all sorts of factors, it would be risky if I use mobile banking apps | |
| Institutional Trust (IT) | IT1 | I trust the banks’ privacy protection to the users [48] |
| IT2 | I feel assured that banks have the legal and technological structures to protect my transactions [17] | |
| IT3 | I trust the banks’ system will perform well and thus process my transaction correctly | |
| Technological Trust (TT) | TT1 | I believe that mobile banking apps are trustworthy |
| TT2 | Even if not monitored, I trust mobile banking apps to do the right job | |
| TT3 | I trust that information concerning my mobile transactions will not be known to others [48] | |
| Behavioural Intention (BI) | BI1 | I intend to use mobile banking apps in the future [53,54] |
| BI2 | I will always try to use mobile banking apps in my daily life | |
| BI3 | I plan to continue to use mobile banking apps frequently | |
| Usage Behaviour (UB) | UB | What is your actual frequency of use of mobile banking apps? (i) Have not used; (ii) once a month; (iii) once a week; (iv) multiple times a week [88] |
| Items | Min | Max | Mean | SD | Skewness | Kurtosis | K-S | Df | Sig. | S-W | Df | Sig. |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| PE1 | 1 | 7 | 6.38 | 1.205 | −3.291 | 10.166 | 0.309 | 315 | 0 | 0.514 | 315 | 0 |
| PE2 | 0 | 7 | 6.07 | 1.67 | −2.448 | 5.223 | 0.348 | 315 | 0 | 0.578 | 315 | 0 |
| PE3 | 0 | 7 | 5.84 | 1.542 | −1.882 | 3.335 | 0.31 | 315 | 0 | 0.825 | 315 | 0 |
| EE1 | 1 | 7 | 6.07 | 1.036 | −2.271 | 8.77 | 0.256 | 315 | 0 | 0.818 | 315 | 0 |
| EE2 | 1 | 7 | 6.01 | 1.085 | −1.862 | 5.091 | 0.275 | 315 | 0 | 0.861 | 315 | 0 |
| EE3 | 1 | 7 | 6.04 | 1.082 | −1.608 | 3.906 | 0.242 | 315 | 0 | 0.884 | 315 | 0 |
| EE4 | 1 | 7 | 6.04 | 1.286 | −2.24 | 5.705 | 0.301 | 315 | 0 | 0.89 | 315 | 0 |
| SI1 | 1 | 7 | 5.02 | 1.607 | −0.881 | −0.22 | 0.195 | 315 | 0 | 0.894 | 315 | 0 |
| SI2 | 1 | 7 | 4.77 | 1.586 | −0.419 | −0.825 | 0.197 | 315 | 0 | 0.902 | 315 | 0 |
| SI3 | 1 | 7 | 4.67 | 1.614 | −0.39 | −0.838 | 0.177 | 315 | 0 | 0.916 | 315 | 0 |
| FC1 | 2 | 7 | 6.22 | 1.007 | −1.738 | 3.445 | 0.263 | 315 | 0 | 0.833 | 315 | 0 |
| FC2 | 1 | 7 | 6.39 | 0.89 | −3.302 | 10.169 | 0.273 | 315 | 0 | 0.583 | 315 | 0 |
| FC3 | 2 | 7 | 6.05 | 0.991 | −1.672 | 3.584 | 0.316 | 315 | 0 | 0.853 | 315 | 0 |
| FC4 | 1 | 7 | 5.47 | 1.474 | −1.255 | 1.06 | 0.306 | 315 | 0 | 0.821 | 315 | 0 |
| HM1 | 1 | 7 | 5.02 | 1.532 | −0.895 | 0.03 | 0.178 | 315 | 0 | 0.902 | 315 | 0 |
| HM2 | 1 | 7 | 5.18 | 1.495 | −0.951 | 0.361 | 0.236 | 315 | 0 | 0.868 | 315 | 0 |
| HM3 | 1 | 7 | 4.3 | 1.565 | −0.465 | −0.384 | 0.188 | 315 | 0 | 0.927 | 315 | 0 |
| HB1 | 1 | 7 | 5.56 | 1.398 | −1.438 | 1.794 | 0.304 | 315 | 0 | 0.804 | 315 | 0 |
| HB2 | 1 | 7 | 4.38 | 1.783 | 0.279 | −1.132 | 0.216 | 315 | 0 | 0.909 | 315 | 0 |
| HB3 | 1 | 7 | 4.23 | 1.89 | −0.407 | −1.042 | 0.179 | 315 | 0 | 0.901 | 315 | 0 |
| PV1 | 1 | 7 | 4.98 | 1.711 | −0.849 | −0.255 | 0.23 | 315 | 0 | 0.883 | 315 | 0 |
| PV2 | 1 | 7 | 5.4 | 1.366 | −0.812 | 0.092 | 0.224 | 315 | 0 | 0.88 | 315 | 0 |
| PV3 | 1 | 7 | 5.33 | 1.469 | −0.913 | 0.304 | 0.264 | 315 | 0 | 0.868 | 315 | 0 |
| PS1 | 1 | 7 | 5.51 | 1.324 | −1.513 | 2.406 | 0.265 | 315 | 0 | 0.802 | 315 | 0 |
| PS2 | 1 | 7 | 5.28 | 1.427 | −1.342 | 1.748 | 0.229 | 315 | 0 | 0.832 | 315 | 0 |
| PS3 | 1 | 7 | 5.51 | 1.303 | −1.458 | 2.369 | 0.254 | 315 | 0 | 0.814 | 315 | 0 |
| PR1 | 1 | 7 | 4.26 | 1.638 | 0.565 | −0.824 | 0.214 | 315 | 0 | 0.897 | 315 | 0 |
| PR2 | 1 | 7 | 4.65 | 1.687 | 0.193 | −0.958 | 0.166 | 315 | 0 | 0.929 | 315 | 0 |
| PR3 | 1 | 7 | 4.88 | 1.485 | 1.131 | 0.534 | 0.259 | 315 | 0 | 0.833 | 315 | 0 |
| IT1 | 1 | 7 | 5.25 | 1.46 | −1.4 | 1.696 | 0.248 | 315 | 0 | 0.814 | 315 | 0 |
| IT2 | 1 | 7 | 5.38 | 1.252 | −1.541 | 2.654 | 0.257 | 315 | 0 | 0.895 | 315 | 0 |
| IT3 | 1 | 7 | 5.6 | 1.088 | −1.538 | 3.558 | 0.284 | 315 | 0 | 0.804 | 315 | 0 |
| TT1 | 1 | 7 | 5.37 | 1.264 | −1.524 | 2.656 | 0.258 | 315 | 0 | 0.804 | 315 | 0 |
| TT2 | 1 | 7 | 4.53 | 1.663 | −0.409 | −1.017 | 0.193 | 315 | 0 | 0.905 | 315 | 0 |
| TT3 | 1 | 7 | 5.16 | 1.409 | −1.007 | 0.893 | 0.224 | 315 | 0 | 0.875 | 315 | 0 |
| BI1 | 4 | 7 | 6.37 | 0.88 | −0.972 | 1.178 | 0.285 | 315 | 0 | 0.848 | 315 | 0 |
| BI2 | 1 | 7 | 5.85 | 1.265 | −1.448 | 2.157 | 0.281 | 315 | 0 | 0.802 | 315 | 0 |
| BI3 | 1 | 7 | 6.02 | 1.235 | −2.052 | 4.678 | 0.304 | 315 | 0 | 0.811 | 315 | 0 |
| Demographic | Value | Frequency | Percentage | Cum. |
|---|---|---|---|---|
| Gender | Female | 144 | 45.71 | 45.71 |
| Male | 171 | 54.29 | 100 | |
| Age (years) | 16–24 | 45 | 14.29 | 14.29 |
| 25–44 | 243 | 77.14 | 91.43 | |
| 45–64 | 6 | 1.9 | 93.33 | |
| 65–74 | 12 | 3.81 | 97.14 | |
| 75 and above | 9 | 2.86 | 100 | |
| Education | GCSE (Level 1–2) | 6 | 1.9 | 1.9 |
| Bachelors (Level 6) | 87 | 27.62 | 29.52 | |
| Masters (Level 7) | 195 | 61.91 | 91.43 | |
| PhD (Level 8) | 24 | 7.62 | 99.05 | |
| Others | 3 | 0.95 | 100 | |
| Occupation | Academic/Teacher | 12 | 3.81 | 3.81 |
| Clerical/Administrative | 15 | 4.76 | 8.57 | |
| Computer Technician/Engineering | 33 | 10.48 | 19.05 | |
| Executive/Manager | 27 | 8.57 | 27.62 | |
| Retired | 15 | 4.76 | 32.38 | |
| Self-employed/own company | 15 | 4.76 | 37.14 | |
| Service/Customer Support | 15 | 4.76 | 41.9 | |
| Student (college/university) | 183 | 58.1 | 100 | |
| Income (Annual) | less than 3000 | 72 | 22.86 | 22.86 |
| 3000–10,000 | 66 | 20.95 | 43.81 | |
| 10,001–15,000 | 63 | 20 | 63.81 | |
| 15,001–20,000 | 42 | 13.33 | 77.14 | |
| 20,001–25,000 | 18 | 5.71 | 82.85 | |
| 25,001 and above | 54 | 17.15 | 100 | |
| Usage of Mobile Banking App | Multiple times a week | 195 | 61.9 | 61.9 |
| Once a week | 75 | 23.81 | 85.71 | |
| Once a month | 45 | 14.29 | 100 | |
| Up to one year | 45 | 14.29 | 14.29 | |
| Experience in using mobile banking app | 2–4 years | 144 | 45.71 | 60 |
| More than 4 years | 126 | 40 | 100 |
| Fit Index | Recommended Values | Measurement Model | Structural Model |
|---|---|---|---|
| Fit Index Degree of Freedom (df) | N/A | 610 | N/A |
| X2/df | <5 | 2.275 | 2.076 |
| Goodness-Of-Fit Index (GFI) | >0.90 | 0.978 | 1 |
| Adjusted Goodness-Of-Fit Index (AGFI) | >0.80 | 0.901 | 0.997 |
| Comparative Fit Index (CFI) | >0.90 | 0.911 | 1 |
| Root Mean Square Residuals (RMSR) | <0.08 | 0.001 | 0.001 |
| Root Mean Square Error of Approximation (RMSEA) | <0.08 | 0.017 | 0 |
| Normed Fit Index (NFI) | >0.90 | 0.669 | 1 |
| Parsimony Normed Fit Index (PNFI) | >0.60 | 0.868 | 0.718 |
| Constructs and Indicators | Factor Loadings | Variance (%) | KMO | Bartlett’s Test of Sphericity | Cronbach’s Alpha () | CR | AVE |
|---|---|---|---|---|---|---|---|
| Performance Expectancy (PE) | 0.706 | 325.497 * | 00.805 | 0.891 | 0.733 | ||
| PE1 | 0.855 | 72.903 | |||||
| PE2 | 0.879 | 15.664 | |||||
| PE3 | 0.826 | 11.433 | |||||
| Effort Expectancy (EE) | 0.75 | 569.741 * | 00.833 | 0.892 | 0.673 | ||
| EE1 | 0.722 | 67.357 | |||||
| EE2 | 0.879 | 15.896 | |||||
| EE3 | 0.876 | 11.753 | |||||
| EE4 | 0.795 | 4.994 | |||||
| Social Influence (SI) | 0.722 | 886.804 * | 00.931 | 0.961 | 0.881 | ||
| SI1 | 0.896 | 87.959 | |||||
| SI2 | 0.961 | 9.437 | |||||
| SI3 | 0.955 | 2.605 | |||||
| Facilitating Conditions (FC) | 0.671 | 218.841 * | 00.759 | 0.812 | 0.524 | ||
| FC1 | 0.788 | 51.775 | |||||
| FC2 | 0.831 | 19.976 | |||||
| FC3 | 0.741 | 17.628 | |||||
| FC4 | 0.704 | 10.62 | |||||
| Hedonic Motivation (HM) | 0.702 | 513.774 * | 00.868 | 0.922 | 0.792 | ||
| HM1 | 0.915 | 79.349 | |||||
| HM2 | 0.921 | 14.4 | |||||
| HM3 | 0.833 | 6.251 | |||||
| Habit (HB) | 0.64 | 136.668 * | 00.795 | 0.781 | 0.563 | ||
| HB1 | 0.777 | 55.69 | |||||
| HB2 | 0.864 | 30.002 | |||||
| HB3 | 0.835 | 14.308 | |||||
| Price Value (PV) | 0.672 | 237.266 * | 00.745 | 0.861 | 0.674 | ||
| PV1 | 0.762 | 67.225 | |||||
| PV2 | 0.855 | 19.691 | |||||
| PV3 | 0.84 | 13.084 | |||||
| Perceived Security (PS) | 0.747 | 550.724 * | 00.892 | 0.932 | 0.821 | ||
| PS1 | 0.896 | 82.323 | |||||
| PS2 | 0.917 | 9.859 | |||||
| PS3 | 0.909 | 7.818 | |||||
| Perceived Risk (PR) | 0.733 | 491.538 * | 00.875 | 0.923 | 0.802 | ||
| PR1 | 0.879 | 80.151 | |||||
| PR2 | 0.915 | 11.598 | |||||
| PR3 | 0.892 | 8.251 | |||||
| Institutional Trust (IT) | 0.668 | 490.611 * | 00.853 | 0.922 | 0.783 | ||
| IT1 | 0.853 | 78.454 | |||||
| IT2 | 0.936 | 15.016 | |||||
| IT3 | 0.866 | 6.53 | |||||
| Technological Trust (TT) | 0.694 | 309.124 * | 00.791 | 0.881 | 0.721 | ||
| TT1 | 0.861 | 71.699 | |||||
| TT2 | 0.803 | 17.038 | |||||
| TT3 | 0.876 | 11.263 | |||||
| Behavioural Intention (BI) | 0.624 | 290.988 * | 00.752 | 0.862 | 0.683 | ||
| BI1 | 0.789 | 67.696 | |||||
| BI2 | 0.888 | 22.896 | |||||
| BI3 | 0.876 | 9.408 |
| AVE | VIF | UB | PE | EE | SI | FC | HM | HB | PV | PS | PR | IT | TT | BI | GEN | AGE | EDU | INC | EXP | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| UB | N/A | N/A | N/A | |||||||||||||||||
| PE | 0.733 | 1.542 | 0.009 | 0.856 | ||||||||||||||||
| EE | 0.673 | 2.103 | 0.032 | 0.547 ** | 0.82 | |||||||||||||||
| SI | 0.881 | 1.539 | −0.05 | 0.252 ** | 0.353 ** | 0.939 | ||||||||||||||
| FC | 0.524 | 1.926 | 0.05 | 0.309 ** | 0.565 ** | 0.263 ** | 0.724 | |||||||||||||
| HM | 0.792 | 1.78 | −0.047 | 0.261 ** | 0.440 ** | 0.432 ** | 0.476 ** | 0.889 | ||||||||||||
| HB | 0.863 | 1.723 | 0.103 | 0.215 ** | 0.256 ** | 0.429 ** | 0.113 * | 0.406 ** | 0.75 | |||||||||||
| PV | 0.674 | 1.252 | −0.157 ** | −0.092 | 0.075 | 0.154 ** | 0.170 ** | 0.085 | 0.167 ** | 0.821 | ||||||||||
| PS | 0.821 | 2.793 | −0.02 | 0.199 ** | 0.327 ** | 0.386 ** | 0.253 ** | 0.243 ** | 0.370 ** | 0.321 ** | 0.901 | |||||||||
| PR | 0.802 | 1.496 | 0.061 | −0.026 | −0.088 | − 0.126 * | −0.076 | −0.073 | 0.085 | −0.163 ** | −0.473 ** | 0.896 | ||||||||
| IT | 0.783 | 2.249 | 0.044 | 0.153 ** | 0.354 ** | 0.216 ** | 0.258 ** | 0.260 ** | 0.266 ** | 0.251 ** | 0.658 ** | −0.271 ** | 0.885 | |||||||
| TT | 0.721 | 2.134 | 0.023 | 0.139 * | 0.226 ** | 0.274 ** | 0.261 ** | 0.209 ** | 0.337 ** | 0.305 ** | 0.597 ** | −0.259 ** | 0.701 ** | 0.849 | ||||||
| BI | 0.683 | 1.234 | −0.015 | 0.275 ** | 0.444 ** | 0.326 ** | 0.227 ** | 0.380 ** | 0.417 ** | 0.211 ** | 0.512 ** | −0.135 * | 0.499 ** | 0.416 ** | 0.826 | |||||
| GEN | N/A | 1.141 | 0.049 | 0.027 | −0.039 | −0.088 | 0.116 * | −0.111 * | −0.161 ** | −0.091 | −0.103 | −0.006 | −0.216 ** | −0.106 | −0.131 * | N/A | ||||
| AGE | N/A | 1.24 | −0.223 ** | −0.07 | −0.011 | 0.02 | −0.118 * | 0.034 | −0.045 | 0.05 | 0.032 | −0.081 | −0.096 | −0.210 ** | 0.044 | −0.08 | N/A | |||
| EDU | N/A | 1.146 | 0.119 * | 0.157 ** | 0.039 | −0.009 | 0.02 | −0.082 | 0.011 | −0.157 ** | 0.003 | 0.078 | −0.165 ** | −0.173 ** | 0.078 | 0.066 | 0.004 | N/A | ||
| INC | N/A | 1.154 | 0.249 ** | 0.107 | 0.055 | 0.059 | 0.026 | −0.007 | 0.088 | −0.103 | 0.007 | −0.074 | −0.073 | −0.004 | 0.081 | 0.127 * | 0.215 ** | 0.066 | N/A | |
| EXP | N/A | 1.118 | 0.116 * | 0.066 | 0.154 ** | −0.073 | 0.170 ** | 0.079 | 0.07 | 0.031 | 0.036 | 0.042 | 0.074 | −0.026 | 0.087 | 0.037 | 0.146 ** | 0.041 | 0.122 * | N/A |
| Relationship | Hypothesis | T Statistic | Coefficient | p Values | Results |
|---|---|---|---|---|---|
| PE → BI | H1 | 0.727 | −0.024 | 0.468 | Not Supported |
| EE → BI | H2 | 4.981 | 0.124 * | 0.021 | Supported |
| SI → BI | H3 | 0.701 | −0.094 | 0.484 | Not Supported |
| FC → BI | H4(a) | −1.731 | 0.113 ** | 0.005 | Supported |
| FC → UB | H4(b) | 1.061 | 0.288 *** | 0 | Supported |
| HM → BI | H5 | 2.501 | 0.132 * | 0.013 | Supported |
| PV → BI | H6 | 3.06 | 0.263 *** | 0 | Supported |
| HB → BI | H7(a) | 4.218 | 0.141 * | 0.031 | Supported |
| HB → UB | H7(b) | 2.243 | 0.354 ** | 0.006 | Supported |
| PS → BI | H8(a) | 3.662 | 0.332 *** | 0 | Supported |
| PS → UB | H8(b) | −0.866 | 0.191 * | 0.048 | Supported |
| PR → BI | H9 | 1.213 | −0.071 | 0.226 | Not Supported |
| IT → BI | H10 | 3.223 | 0.181 ** | 0.001 | Supported |
| TT → BI | H11 | 2.423 | 0.218 *** | 0 | Supported |
| BI → UB | H12 | −0.848 | 0.432 ** | 0.007 | Supported |
| UTAUT2 | Model 1 | Model 2 | Model 3 | Model 4 | ||||
|---|---|---|---|---|---|---|---|---|
| B | S.E | B | S.E | B | S.E | B | S.E | |
| PE | 0.041 | 0.057 | 0.033 | 0.053 | 0.013 | 0.053 | −0.024 | 0.052 |
| EE | 0.33 *** | 0.066 | 0.266 *** | 0.062 | 0.26 *** | 0.062 | 0.124 * | 0.064 |
| SI | 0.039 | 0.056 | −0.014 | 0.053 | −0.012 | 0.053 | −0.094 | 0.052 |
| FC | −0.106 | 0.061 | 0.148 ** | 0.057 | 0.155 ** | 0.059 | 0.113 ** | 0.061 |
| HM | 0.151 ** | 0.06 | 0.17 ** | 0.056 | 0.188 ** | 0.057 | 0.132 * | 0.056 |
| HB | 0.233 *** | 0.055 | 0.123 * | 0.055 | 0.108 * | 0.056 | 0.263 *** | 0.054 |
| PV | 0.15 ** | 0.049 | 0.056 | 0.047 | 0.176 ** | 0.048 | 0.141 * | 0.052 |
| UTAUT2 + PS + PR + IT + TT | ||||||||
| PS | 0.255 *** | 0.07 | 0.21 ** | 0.071 | 0.332 *** | 0.055 | ||
| PR | 0.063 | 0.052 | 0.062 | 0.052 | −0.071 | 0.09 | ||
| IT | 0.273 ** | 0.07 | 0.159 *** | 0.056 | 0.181 ** | 0.071 | ||
| TT | 0.193 ** | 0.06 | 0.259 *** | 0.064 | 0.218 *** | 0.09 | ||
| Moderators | ||||||||
| Gender | −0.006 | 0.046 | −0.033 | 0.045 | ||||
| Age | 0.051 | 0.047 | 0.068 | 0.053 | ||||
| Education | 0.133 ** | 0.046 | 0.057 | 0.075 | ||||
| Income | 0.062 | 0.046 | 0.032 | 0.047 | ||||
| Experience | 0.01 | 0.045 | 0.013 | 0.046 | ||||
| Interaction Terms | ||||||||
| PS x GEN | −0.207 * | 0.107 | ||||||
| IT x GEN | 0.209 * | 0.093 | ||||||
| TT x AGE | 1.498 * | 0.053 | ||||||
| TT x EDU | 1.321 ** | 0.034 | ||||||
| PS x GEN x INC | −0.362 *** | 0.106 | ||||||
| IT x GEN x INC | 0.401 *** | 0.085 | ||||||
| PS x AGE x EXP | −1.866 * | 0.455 | ||||||
| TT x AGE x EXP | −1.766 * | 0.855 | ||||||
| PS x GEN x AGE x INC | −2.188 ** | 0.809 | ||||||
| IT x GEN x AGE x INC | 1.373 ** | 0.54 | ||||||
| TT x GEN x AGE x INC | 0.433 | 0.67 | ||||||
| PS x GEN x AGE x EXP | 2.498 ** | 0.985 | ||||||
| IT x GEN x AGE x EXP | −2.187 * | 1.1 | ||||||
| TT x AGE x EDU x EXP | −1.523 ** | 0.056 | ||||||
| PS x GEN x AGE x EDU x INC x EXP | 2.767 * | 1.14 | ||||||
| IT x GEN x AGE x EDU x INC x EXP | −1.718 ** | 0.637 | ||||||
| Model Summary | ||||||||
| F | 21.851 *** | 23.294 *** | 16.785 *** | 8.539 *** | ||||
| R2 | 0.415 | 0.43 | 0.59 | 0.79 | ||||
| Adjusted R2 | 0.415 | 0.42 | 0.59 | 0.78 | ||||
| UTAUT2 | Model 1 | Model 2 | Model 3 | Model 4 | ||||
|---|---|---|---|---|---|---|---|---|
| B | S.E | B | S.E | B | S.E | B | S.E | |
| FC | 0.162 ** | 0.059 | −0.059 | 0.068 | −0.202 ** | 0.056 | 0.288 *** | 0.056 |
| HB | 0.142 * | 0.063 | 0.223 * | 0.063 | 0.108 * | 0.059 | 0.354 ** | 0.06 |
| BI | 0.158 * | 0.069 | 0.01 | 0.063 | 0.076 | 0.064 | 0.191 * | 0.067 |
| UTAUT2 + PS | 0.165 * | 0.053 | 0.321 *** | 0.071 | 0.432 ** | 0.055 | ||
| Moderators | ||||||||
| Gender | −0.021 | 0.055 | −0.019 | 0.055 | ||||
| Age | −0.298 *** | 0.055 | −0.283 *** | 0.057 | ||||
| Education | 0.103 * | 0.052 | 0.114 * | 0.054 | ||||
| Income | 0.293 *** | 0.055 | 0.291 *** | 0.055 | ||||
| Experience | 0.121 * | 0.054 | 0.108 * | 0.055 | ||||
| Interaction Terms | ||||||||
| PS x AGE x EXP | −1.334 *** | 0.556 | ||||||
| PS x GEN x AGE x EXP | 2.344 *** | 0.966 | ||||||
| Model Summary | ||||||||
| F | 17.59 | 27.171 *** | 19.171 *** | 5.564 *** | ||||
| R2 | 0.159 | 0.321 | 0.397 | 0.547 | ||||
| Adjusted R2 | 0.159 | 0.312 | 0.397 | 0.531 | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Apau, R.; Titis, E.; Lallie, H.S. Towards a Better Understanding of Mobile Banking App Adoption and Use: Integrating Security, Risk, and Trust into UTAUT2. Computers 2025, 14, 144. https://doi.org/10.3390/computers14040144
Apau R, Titis E, Lallie HS. Towards a Better Understanding of Mobile Banking App Adoption and Use: Integrating Security, Risk, and Trust into UTAUT2. Computers. 2025; 14(4):144. https://doi.org/10.3390/computers14040144
Chicago/Turabian StyleApau, Richard, Elzbieta Titis, and Harjinder Singh Lallie. 2025. "Towards a Better Understanding of Mobile Banking App Adoption and Use: Integrating Security, Risk, and Trust into UTAUT2" Computers 14, no. 4: 144. https://doi.org/10.3390/computers14040144
APA StyleApau, R., Titis, E., & Lallie, H. S. (2025). Towards a Better Understanding of Mobile Banking App Adoption and Use: Integrating Security, Risk, and Trust into UTAUT2. Computers, 14(4), 144. https://doi.org/10.3390/computers14040144







