Security Requirements Engineering: A Review and Analysis
Abstract
1. Introduction
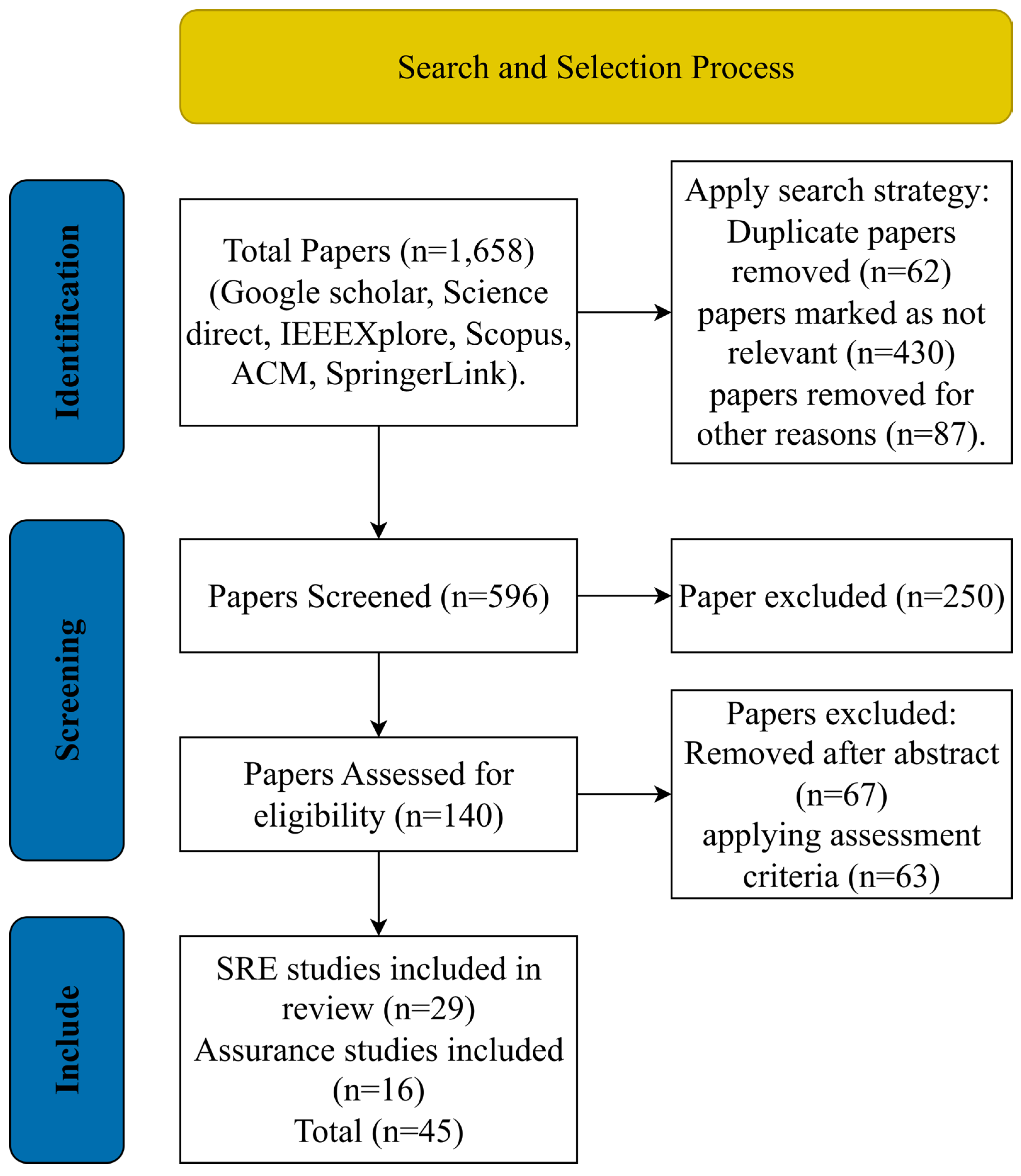
- This study adopts a two-phase methodology that bridges the gap between theoretical research and industry application. The first phase conducts a systematic literature review of 45 studies, while the second phase involves an empirical survey of 58 professionals from diverse industrial domains. This design allows for a holistic exploration of both academic frameworks and real-world challenges in SRE and SRA.
- Nine established SRE approaches including SQUARE, Secure Tropos, SREP, and CLASP are critically compared across 17 Activities such as scalability, flexibility, risk analysis, validation, and integration of standards. This structured evaluation not only identifies the strengths and limitations of each method but also guides practitioners in selecting context-appropriate techniques for secure software development.
- Unlike prior studies that largely focus on the elicitation and analysis of security requirements, this work highlights a critical and underexplored component Security Requirements Assurance. The findings reveal that most existing approaches lack explicit mechanisms to verify and validate security requirements during and after implementation, which poses a serious risk to system reliability.
- Statistical analysis of the survey responses using ANOVA, correlation, regression, and the Kruskal–Wallis test uncovers significant knowledge disparities among professionals. The results indicate that while awareness of SRE and RE is relatively strong, understanding of SRA is notably weak. This empirical insight substantiates the theoretical gap identified in the literature and emphasizes the need for targeted assurance training and framework development.
- By combining analytical comparisons with industry validation, the study offers a practical decision-making guide for selecting suitable SRE methods and integrating assurance activities throughout the SDLC. This contribution is especially valuable for requirement engineers, security analysts, and project managers seeking to implement scalable and verifiable security practices
2. Literature Review
2.1. Security Requirement Engineering
2.2. Security Requirement Assurance
2.3. Automation and AI in Security Requirements Engineering
2.4. Related Reviews and Gap Analysis
3. Research Methodology and Study Design
3.1. Phase 1: Literature Review Process
- (i)
- Studies only provided conceptual discussions or theoretical opinions without practical application.
- (ii)
- Grey literature—including editorials, white papers, unreviewed preprints, and industry reports lacking standardized peer review—was systematically excluded by restricting searches to peer-reviewed databases, filtering publication type metadata, and applying PRISMA guidelines. Studies failing to meet peer-review standards or methodological rigor were removed, while some preprints and industry cases were cited in the Introduction for contextual illustration only, not as part of the SLR dataset.
- (iii)
- Studies did not directly address security requirement engineering but focused on broader cybersecurity or unrelated software security aspects.
- (iv)
- Duplicate studies, where only the latest and most comprehensive version was retained, and.
- (v)
- Lacked methodological rigor, including those with insufficient sample sizes, unclear research methodologies, or missing statistical validation. The application of these criteria ensured that the final selection of studies was methodologically sound and contributed effectively to the research objectives.
3.2. Phase 2—Practical Implementation via Empirical Survey
3.3. Statistical Approach for Data Validation
3.3.1. Descriptive Analysis of Security Knowledge
3.3.2. Inferential Statistical Analysis
3.3.3. Variance Analysis
3.3.4. Predictive Modeling (Regression Analysis)
3.4. Research Questions
3.5. Data Sources and Search Approach
4. Discussion
5. Finding and Implications (Phase 2)
5.1. Descriptive Statistics of Security Knowledge
5.2. Statistical Comparison of Security Knowledge
[1.16, 1.66]
- Start with the test statistics
- 2.
- Compute Cohen’s d from t
- 3.
- Compute the standard error (SE) of d
- 4.
- Build the 95% Confidence interval (CI)
| Comparison | T/F-Statistic | p-Value | Effect Size | Confidence Intervals |
|---|---|---|---|---|
| SRE vs. SRA | 10.78 | 0.0017 | d = 1.41 | [1.16, 1.66] |
| SRE vs. RE | −0.49 | 0.6327 | d = 0.06 | [−0.31, 0.19] |
| SRA vs. RE | −3.69 | 0.0049 | d = 0.48 | [−0.73, −0.23] |
| ANOVA (SRE, SRA, RE) | 8.19 | 0.0066 | η2 = 0.23 | - |
5.3. Relationship Between Security Awareness and Implementation
5.4. Variance and Distribution Analysis
5.5. Predictive Modeling: Impact of SRE Knowledge
5.6. Implications for Practice and Future Research
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Anwar Mohammad, M.N.; Nazir, M.; Mustafa, K. A Systematic Review and Analytical Evaluation of Security Requirements Engineering Approaches. Arab. J. Sci. Eng. 2019, 44, 8963–8987. [Google Scholar] [CrossRef]
- Hnaini, H.; Mazo, R.; Champeau, J.; Vallejo, P.; Galindo, J. E-SCORE: A web-based tool for security requirements engineering. SoftwareX 2024, 26, 101704. [Google Scholar] [CrossRef]
- Khan, R.A.; Khan, S.U.; Akbar, M.A.; Alzahrani, M. Security risks of global software development life cycle: Industry practitioner’s perspective. J. Softw. Evol. Process 2022, 36, e2521. [Google Scholar] [CrossRef]
- Niazi, M.; Saeed, A.M.; Alshayeb, M.; Mahmood, S.; Zafar, S. A maturity model for secure requirements engineering. Comput. Secur. 2020, 95, 101852. [Google Scholar] [CrossRef]
- Sousa-Dias, D.; Amyot, D.; Rahimi-Kian, A.; Mylopoulos, J. A Review of Cybersecurity Concerns for Transactive Energy Markets. Energies 2023, 16, 4838. [Google Scholar] [CrossRef]
- Janisar, A.A.; bin Kalid, K.S.; Sarlan, A.B.; Maiwada, U.D. Software Development Teams Knowledge and Awareness of Security Requirement Engineering and Security Requirement Elicitation and Analysis. Procedia Comput. Sci. 2024, 234, 1348–1355. [Google Scholar] [CrossRef]
- Umar, M.A.; Lano, K. Advances in automated support for requirements engineering: A systematic literature review. Requir. Eng. 2024, 29, 177–207. [Google Scholar] [CrossRef]
- Li, T.; Zhang, X.; Wang, Y.; Zhou, Q.; Wang, Y.; Dong, F. Machine learning for requirements engineering (ML4RE): A systematic literature review complemented by practitioners’ voices from Stack Overflow. Inf. Softw. Technol. 2024, 172, 107477. [Google Scholar] [CrossRef]
- Ozkaya, M.; Akdur, D.; Toptani, E.C.; Kocak, B.; Kardas, G. Practitioners’ Perspectives towards Requirements Engineering: A Survey. Systems 2023, 11, 65. [Google Scholar] [CrossRef]
- Holthouse, R.; Owens, S.; Bhunia, S. The 23andMe Data Breach: Analyzing Credential Stuffing Attacks, Security Vulnerabilities, and Mitigation Strategies. arXiv 2025, arXiv:2502.04303. [Google Scholar] [CrossRef]
- Gentles, J.; Fields, M.; Goodman, G.; Bhunia, S. Breaking the Vault: A Case Study of the 2022 LastPass Data Breach. arXiv 2025, arXiv:2502.04287. [Google Scholar] [CrossRef]
- Sebastian, G. Cyber kill chain analysis of five major US data breaches: Lessons learnt and prevention plan. Int. J. Cyber Warf. Terror. (IJCWT) 2022, 12, 1–15. [Google Scholar] [CrossRef]
- Yeng, P.K.; Fauzi, M.A.; Sun, L.; Yang, B. Assessing the Legal Aspects of Information Security Requirements for Health Care in 3 Countries: Scoping Review and Framework Development. JMIR Hum Factors 2022, 9, e30050. [Google Scholar] [CrossRef]
- Franch, X.; Palomares, C.; Quer, C.; Chatzipetrou, P.; Gorschek, T. The state-of-practice in requirements specification: An extended interview study at 12 companies. Requir. Eng. 2023, 28, 377–409. [Google Scholar] [CrossRef]
- Worakitpreeda, N.; Pongpaibul, M. Framework for Eliciting Security Requirements of Web Application from Business Users. In Proceedings of the 2021 25th International Computer Science and Engineering Conference (ICSEC), Chiang Rai, Thailand, 18–20 November 2021; pp. 216–221. [Google Scholar]
- Sadiq, M.; Devi, V.S.; Ahmad, J.; Mohammad, C.W. Fuzzy logic driven security requirements engineering process. J. Inf. Optim. Sci. 2021, 42, 1685–1707. [Google Scholar] [CrossRef]
- Qadir, N.; Ahmad, R. SecRS template to aid novice developers in security requirements identification and documentation. Int. J. Softw. Eng. Comput. Syst. 2022, 8, 45–52. [Google Scholar] [CrossRef]
- Mažeika, D.; Butleris, R. Integrating Security Requirements Engineering into MBSE: Profile and Guidelines. In Security and Communication Networks; Hindawi: London, UK, 2020; Volume 2020, pp. 1–12. [Google Scholar]
- Ansari, M.T.J.; Pandey, D.; Alenezi, M. STORE: Security Threat Oriented Requirements Engineering Methodology. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 191–203. [Google Scholar] [CrossRef]
- Khan, R.A.; Khan, S.U. A preliminary structure of software security assurance model. In Proceedings of the 13th International Conference on Global Software Engineering, Gothenburg, Sweden, 27–29 May 2018. [Google Scholar]
- Shukla, A.; Katt, B.; Nweke, L.O.; Yeng, P.K.; Weldehawaryat, G.K. System security assurance: A systematic literature review. Comput. Sci. Rev. 2022, 45, 100496. [Google Scholar] [CrossRef]
- Katt, B.; Prasher, N. Quantitative security assurance metrics. In Proceedings of the 12th European Conference on Software Architecture: Companion Proceedings, Madrid, Spain, 24–28 September 2018. [Google Scholar]
- Mohamad, M.; Steghöfer, J.-P.; Scandariato, R. Security assurance cases—State of the art of an emerging approach. Empir. Softw. Eng. 2021, 26, 70. [Google Scholar] [CrossRef]
- Xiong, W.; Lagerström, R. Threat modeling—A systematic literature review. Comput. Secur. 2019, 84, 53–69. [Google Scholar] [CrossRef]
- Sabau, A.R.; Lammers, D.; Lichter, H. SecuRe—An Approach to Recommending Security Design Patterns. arXiv 2025, arXiv:2501.14973. [Google Scholar]
- Luitel, D.; Hassani, S.; Sabetzadeh, M. Improving requirements completeness: Automated assistance through large language models. Requir. Eng. 2024, 29, 73–95. [Google Scholar] [CrossRef]
- Casillo, F.; Deufemia, V.; Gravino, C. Beyond domain dependency in security requirements identification. Inf. Softw. Technol. 2025, 182, 107702. [Google Scholar] [CrossRef]
- Lins, F.A.A.; Freitas, F.A.; Nóbrega, O.O.; Valença, G. Security Requirements Engineering Approaches for IoT-Based Systems: A Comprehensive Review and Open Research Challenges. In Proceedings of the 2024 IEEE 10th World Forum on Internet of Things (WF-IoT), Ottawa, ON, Canada, 10–13 November 2024. [Google Scholar]
- Bhole, M.; Kastner, W.; Sauter, T. From manual to semi-automated safety and security requirements engineering: Ensuring compliance in industry 4.0. In Proceedings of the IECON 2024-50th Annual Conference of the IEEE Industrial Electronics Society, Chicago, IL, USA, 3–6 November 2024. [Google Scholar]
- Aviv, I.; Svetinovic, D.; Lee, S.-W. Requirements Engineering for Web3 Systems: Preface. In Proceedings of the 2024 IEEE 32nd International Requirements Engineering Conference Workshops (REW), Reykjavik, Iceland, 24–25 June 2024. [Google Scholar]
- Herwanto, G.B.; Ekaputra, F.J.; Quirchmayr, G.; Tjoa, A.M. Toward a Holistic Privacy Requirements Engineering Process: Insights From a Systematic Literature Review. IEEE Access 2024, 12, 47518–47542. [Google Scholar] [CrossRef]
- Hassan, S.; Li, Q.; Zubair, M.; Alsowail, R.A.; Umair, M. An Improved Hybrid Deep Learning Approach for Security Requirements Classification. Comput. Mater. Contin. 2025, 82, 4041–4067. [Google Scholar] [CrossRef]
- Span, M.T.; Salinger, G.; Rayno, M.; Daily, J. Security Requirements Engineering: A Survey for the Systems Engineer. In Proceedings of the 2024 IEEE International Symposium on Systems Engineering (ISSE), Perugia, Italy, 16–19 October 2024. [Google Scholar]
- Pargaonkar, S. Synergizing Requirements Engineering and Quality Assurance: A Comprehensive Exploration in Software Quality Engineering. Int. J. Sci. Res. (IJSR) 2023, 12, 2003–2007. [Google Scholar] [CrossRef]
- Ardi, S.; Sandahl, K.; Gustafsson, M. A Case Study of Introducing Security Risk Assessment in Requirements Engineering in a Large Organization. SN Comput. Sci. 2023, 4, 488. [Google Scholar] [CrossRef]
- Olukoya, O. Assessing frameworks for eliciting privacy & security requirements from laws and regulations. Comput. Secur. 2022, 117, 102697. [Google Scholar] [CrossRef]
- Janisar, A.; Shafee, K.; Sarlan, A.; Maiwada, U.; Salameh, A.A. Securing Software Development: A Holistic Exploration of Security Awareness in Software Development Teams. Int. J. Acad. Res. Bus. Soc. Sci. 2024, 14, 1326–1338. [Google Scholar] [CrossRef]
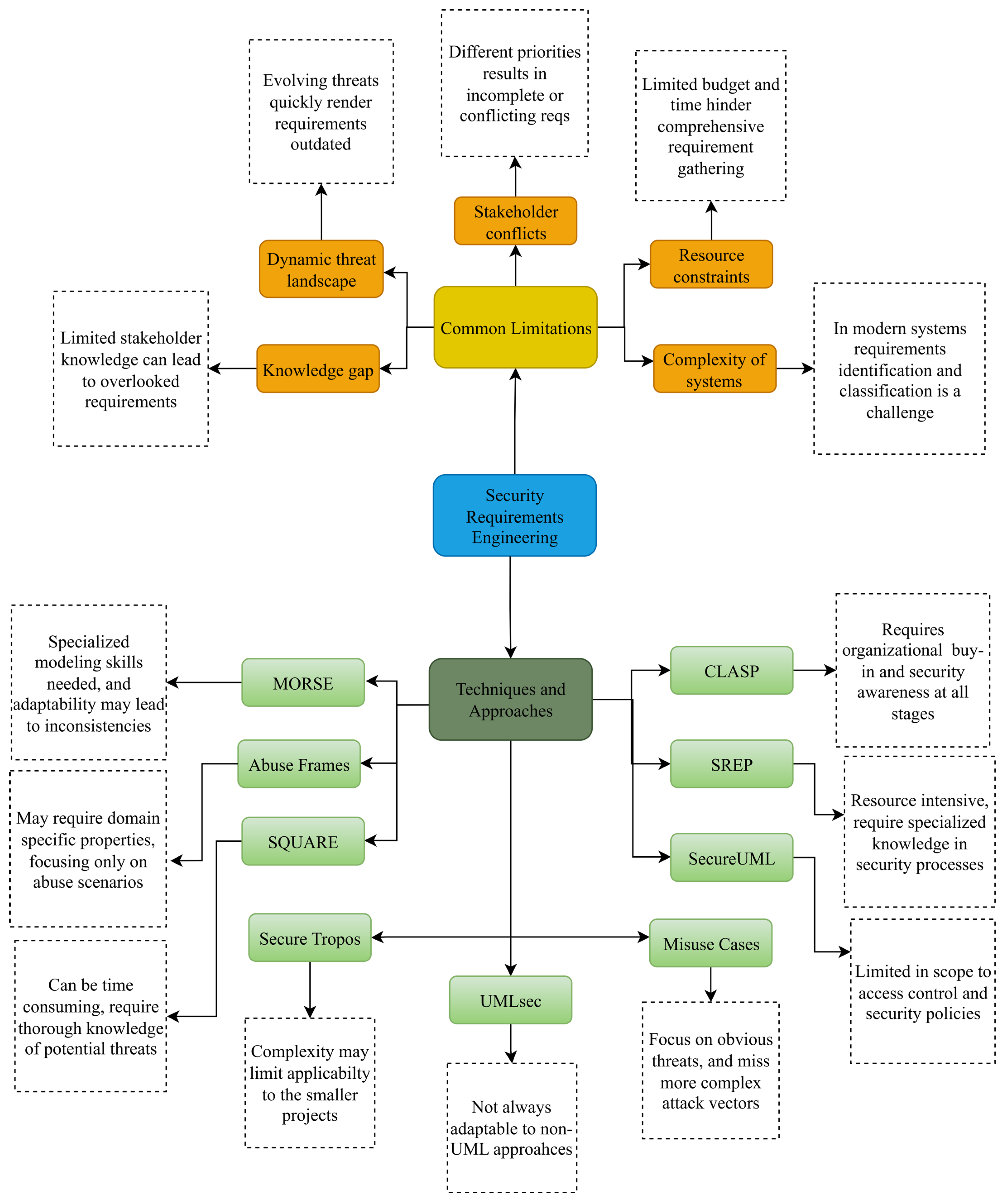

| Method/Approach | Objective and Rationale | Targeted re Stage | Purpose |
|---|---|---|---|
| SQUARE | Integrate security requirements early in SDLC using a 9-step adaptable method for eliciting, categorizing, and prioritizing security needs. | Elicitation, Categorization, Prioritization | To systematically define and prioritize security requirements from the beginning of the SDLC. |
| Secure Tropos | Use agent-oriented models to define security throughout SDLC, focusing on goals, trust, and secure dependencies. | All SDLC Phases (Focus on Early Requirements) | To embed security into the system by modelling goals, actors, and dependencies. |
| Abuse Frames | Represent attacker anti-requirements using modified problem frames to elicit security threats like DoS, and interception. | Elicitation (Threat Modelling) | To identify and analyze potential threats and vulnerabilities from an attacker’s perspective. |
| SREP | Risk-driven, iterative method using Common Criteria and reusable repository to define and prioritize security requirements. | Elicitation, Risk Assessment, Validation | To iteratively derive risk-based, asset-driven security requirements using reusable components. |
| Misuse Cases | Model hostile behaviors in UML with templates and relationships to depict threats and improve security requirement reuse. | Elicitation (Threat Modelling) | To capture and reuse attack scenarios and model malicious behaviors in system analysis. |
| UMLsec | Extend UML diagrams with stereotypes, tags, and constraints for formal security requirement verification and system design. | Design, Verification | To enhance UML models with formalized security specifications and enable automated verification. |
| MORSE | An iterative approach combining SQUARE and misuse cases to elicit, trace, and analyze security requirements in web systems. | Elicitation, Analysis, Traceability | To offer a structured elicitation and analysis approach for security-critical applications. |
| SecureUML | Model role-based access control policies in UML using OCL for formal authorization in secure distributed system design. | Design (Authorization Modelling) | To specify access control policies formally within UML design for secure systems. |
| CLASP | Lightweight, role-based process integrating best practices across SDLC to manage and validate security requirements. | Elicitation, Validation, Management | To guide secure software development through structured activities and best practices. |
| Ref. | Key Focus | Methodologies Used | Validation Approach | Findings | Practical Applicability | Limitation |
|---|---|---|---|---|---|---|
| [1] | Anwar Mohammad et al., 2019, An SLR evaluated 20 SRE approaches, comparing threat modelling and risk analysis. | A comparative synthesis of methodologies. | Theoretical evaluation, no empirical validation. | Identified the most-used SRE techniques and their attributes | Useful for understanding SRE methodologies but lacks implementation insights | Some approaches included design aspects, despite focusing solely on requirement engineering. |
| [2] | Hnaini, Mazo et al., (2024)/E-SCORE streamlines security requirements in engineering, establishing criteria through article evaluation. | Tool-supported SRE through E-SCORE framework | Comparative evaluation using defined criteria | Establishes clear criteria for evaluating SRE completeness | Can formalize RE processes in complex environments | Challenges include a limited understanding of security criteria and low adoption. |
| [4] | Niazi et al., 2020, The study developed RESMM with 79 practices from SLR findings. | Literature-driven framework + case studies | Applied RESMM on two real-world projects | Established a maturity framework for assessing security requirements and engineering readiness | Can help organizations assess security maturity levels | Requires broader validation across diverse industries and complex software development settings. |
| [19] | Ansari et al., (2022)/STORE methodology enhances ERP security requirements, outperforming SQUARE in effectiveness. | STORE methodology for ERP security RE | Compared with SQUARE in ERP projects | Outperforms traditional SRE in ERP-specific needs | Good for enterprise-level applications and standards compliance | STORE needs validation on large-scale projects and a supporting tool. |
| [26] | Luitel et al., 2024, Automated completeness checking for natural language requirements | AI-driven requirement completeness verification | Masked prediction and noise-tolerance testing | Improves quality assurance of natural language requirements | Suitable for documentation-heavy engineering projects | Prone to noise in masked prediction and limited domain scope. |
| [27] | Casillo et al., 2025, Evaluation of domain-independent security requirement identification using NLP and machine learning models. | BERT-based NLP models for security requirement extraction | Computational evaluation of NLP performance | Achieved high accuracy in classifying security-related requirements | Supports automation in requirement engineering tasks | BERT-based models show promise but require extensive computational resources; domain-specific adaptation remains a challenge. |
| [28] | Lins et al., 2024, A comprehensive review of security requirements engineering for IoT-based systems. | SRE review for IoT systems | Systematic literature synthesis | Highlights IoT-specific RE gaps like scalability and heterogeneity | Valuable for IoT-focused development teams | Struggles with heterogeneity and scalability of IoT security requirements. |
| [29] | Bhole et al., 2024, The transition from manual to semi-automated security requirements engineering for Industry 4.0. | Compliance-focused hybrid SRE model for Industry 4.0 | Case studies in industrial environments | Improved security process automation and compliance | Highly applicable to industrial automation and manufacturing | Difficult integration in generic software settings; lacks domain-flexibility |
| [30] | Aviv et al., 2024, Challenges and methodologies in security requirements engineering for Web3 systems. | Conceptual modeling for SRE in Web3 systems | Literature-driven framework | Captures security challenges in decentralized tech ecosystems | Raises awareness of Web3-specific security gaps | Limited by lack of case studies; no practical framework tested |
| [31] | Guntur Budi Herwanto, Fajar J Ekaputra, et al., 2024, Systematic literature review on holistic privacy requirements engineering. | A systematic review of privacy focused RE frameworks | Literature evaluation | Identifies inconsistencies in privacy requirement handling | Useful for privacy-sensitive sectors like healthcare and fintech | The absence of a unified framework requires standardization for broader applicability. |
| [32] | Hassan et al., 2025, Hybrid deep learning model for security requirements classification. | Deep learning-based classification model for SRE | Dataset-driven performance benchmarking | Effective in automating requirement categorization | Supports efficiency in early security requirement analysis | Dependence on dataset quality; generalizability of the model needs further testing. |
| [33] | Span et al., 2024, The research surveys provide Standards-integrated SRE with MBSE and systems theory | Systems theory & MBSE integration into SRE | Comparative framework analysis | Suggests standard-driven security integration strategies | Applicable in model-based development and systems engineering | Scarcity of tools and resource requirements hinder industrial use |
| [34] | Pargaonkar, 2023, The study explores RE-QA synergy, focusing on traceability and communication. | Empirical study on RE and QA alignment | Interviews and traceability analysis | Identifies gaps in requirement traceability and QA workflows | Helps QA and RE teams coordinate effectively | Requires consistent updates; fragile in agile settings |
| [35] | Ardi et al., 2023, The study evaluates upskilling engineers to reduce vulnerabilities and assess training. | Training assessment for secure software engineering | Pre/post-training evaluation | Demonstrates improved security awareness post-training | Enhances human capability in security-sensitive roles | Challenges include training adaptation and workforce distribution; further verification is needed. |
| [36] | Olukoya, (2022)/Compared NDPR with existing standards, showing improvements in completeness and consistency. | NDPR compliance assessment with global standards | Policy-based comparative evaluation | Demonstrates stronger completeness and consistency | Aids compliance alignment for privacy and security standards | Lack of uniform global standards; needs better modelling, automation, and formalization. |
| Current study | Comparative analysis of SRE methods + empirical survey on security knowledge | Mixed method: Literature review + practitioner survey + statistical analysis (ANOVA, regression, correlation) | Empirical validation with 58 professionals from diverse industries | Identifies gaps in security assurance knowledge, emphasizing the need for SRA integration into SDLC | Broad industry applicability; informed by real-world practices | SRA is evaluated via awareness levels, not by actual system deployment; lacks real-world implementation validation |
| Criteria | Inclusion Criteria | Exclusion Criteria |
|---|---|---|
| Publication Year | 2009–2025 (to capture foundational and contemporary developments in SRE and SRA) | Studies published before 2009 or after 2025 |
| Article Type | Peer-reviewed journal papers, conference proceedings, or scholarly book chapters | Editorials, white papers, tutorials, blogs, newsletters, and industry reports (grey literature) |
| Language | English | Non-English publications |
| Availability | Full-text studies available (≥5 pages) | Abstract-only studies or short notes (<5 pages) |
| Relevance | Explicitly addresses Security Requirements Engineering (SRE), Security Requirements Assurance (SRA), or related methodologies | Studies focusing only on general cybersecurity or unrelated software engineering topics |
| Publication Stage | Final, published versions | Drafts, in-press, or unpublished works |
| Methodological Rigor | Provides empirical evidence, case studies, systematic reviews, or comparative analyses | Conceptual-only studies without validation, unclear methods, insufficient sample sizes, or no statistical validation |
| Duplication | Most recent and comprehensive version retained | Duplicate or redundant studies |
| Grey Literature | – | Grey literature excluded (e.g., editorials, white papers, unreviewed preprints such as arXiv, industry reports) |
| Industry Sector | No. of Respondents | Percentage (%) |
|---|---|---|
| IT and Software Development | 23 | 39.7% |
| Finance and Banking | 10 | 17.2% |
| Healthcare | 8 | 13.8% |
| Oil and Gas | 7 | 12.1% |
| Telecom | 5 | 8.6% |
| Academia and Research | 5 | 8.6% |
| Position | Frequency | % |
| Software Engineer | 4 | 10.2 |
| Business/System Analyst | 5 | 12.8 |
| Developer (ML, Android, IOS, Flutter) | 6 | 15.3 |
| SOC Analyst | 9 | 23 |
| Product Manager | 3 | 7.6 |
| Test Engineer/Quality Control | 2 | 5.1 |
| Others | 10 | 25.6 |
| Research Questions | Purpose/Focus | Study Phase Addressed |
|---|---|---|
| Compares existing SRE methods across elicitation, analysis, validation, and management activities. | Phase 1—Systematic Literature Review |
| Identifies concrete practices (e.g., threat modelling, risk assessment) used in SRE approaches and their practical challenges. | Phase 1—Systematic Literature Review |
| Evaluates the presence (or absence) of assurance within SRE frameworks and examines its reflection in industry knowledge levels | Phase 1—Literature + Phase 2—Survey |
| Data Source and Search Approach | |
|---|---|
| Population | Security requirement Engineering, assurance, or security requirements. |
| Intervention | Current methodologies for security requirements engineering and security requirement assurance. |
| Search String | “Security” AND “requirement” AND “engineering” OR “approaches” OR “techniques” OR “methods” OR “frameworks”, “security” AND “requirement engineering” OR “requirements”, “security” AND “requirement” AND “assurance”, “security” AND “assurance”. |
| Requirement Phases | Purpose | Techniques | Potential Challenges |
|---|---|---|---|
| Requirement Elicitation | Gather and understand stakeholder needs and expectations. | Interviews, surveys, workshops, observation, prototyping. | Stakeholders may have conflicting or unclear requirements. |
| Requirement Analysis | Clarify, organize, and prioritize gathered requirements. | Use case analysis, scenario analysis, modelling, and prioritization. | It is difficult to balance competing stakeholder needs and priorities. |
| Requirement Specification/Representation | Document requirements in a structured, clear, and detailed format. | SRS (Software Requirements Specification), diagrams, and user stories. | The risk of ambiguity or over-specification limits flexibility. |
| Requirement Verification and Validation | Ensure requirements meet stakeholders’ needs and are feasible. | Reviews, testing, prototyping, stakeholder validation. | Completeness, Correctness, and Consistency challenges. Time-intensive; requires ongoing stakeholder involvement. |
| SRE Methods and Requirement Phase Activities Comparison | |||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SRE Methods Activities | SR Elicitation | SR Analysis | SR Validation | SR management | Project Size | Standards | |||||||||||
| SRE Methods | Flexibility | scalability | Threats, | Req Validation | Risk analysis | vulnerability | Consistency | SR Integration | Assets identification | Misuse Modeling | Domain Knowledge | SR Identification and elicitation | Analysis of business SR conflicts | support provided for validation | Support provided in management | ||
| SQUARE | √ | √ | √ | √ | √ | √ | √ | x | x | x | √ | √ | √ | x | - | - | |
| Secure Tropos | √ | √ | √ | √ | x | √ | x | √ | x | - | - | √ | √ | √ | √ | L | ISO/IEC |
| Abuse Frame | - | √ | √ | √ | x | √ | - | x | √ | - | - | x | √ | x | √ | M | ISO |
| SREP | √ | √ | √ | √ | √ | √ | √ | x | √ | x | x | x | √ | √ | √ | - | cc |
| Misuse-cases | √ | x | √ | x | x | √ | x | √ | x | √ | x | √ | √ | x | √ | S | - |
| UMLsec | - | - | √ | x | √ | √ | - | - | x | √ | - | x | - | √ | - | M | ISO/IEC, IEEE |
| MORSE | √ | x | √ | x | x | √ | x | √ | x | x | x | √ | √ | x | √ | M | - |
| SecureUML | - | - | x | x | x | x | - | - | x | - | - | x | √ | x | - | M | - |
| CLASP | √ | - | √ | √ | √ | √ | x | √ | √ | x | √ | √ | √ | x | - | L | - |
| Knowledge Area | Mean | Std. Dev |
|---|---|---|
| SRE (RQ 1) | 3.61 | 0.88 |
| RE (RQ 2) | 3.67 | 0.75 |
| SRA (RQ 3) | 2.71 | 1.1 |
| Correlation | r-Value | Confidence Interval |
|---|---|---|
| SRE & Security Techniques | 0.596 | [0.38, 0.74] |
| SRE & SRA | 0.446 | [0.16, 0.65] |
| RE & SRA | 0.267 | [−0.01, 0.52] |
| Test | Statistics | p-Value | Effect Size |
|---|---|---|---|
| Kruskal–Wallis (SRE, SRA, RE) | 7.35 | 0.02537 | (ε2 = 0.10) |
| Regression Model | β Coefficient | Confidence Interval (β) | R-Squared | p-Value |
|---|---|---|---|---|
| SRE → SRA | 0.50 | [0.31, 0.69] | 0.42 | 0.015 |
| SRE → RE | 0.12 | [−0.05, 0.29] | 0.29 | 0.082 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Janisar, A.A.; Meidan, A.; Kalid, K.S.b.; Gilal, A.R.; Sarlan, A.B. Security Requirements Engineering: A Review and Analysis. Computers 2025, 14, 429. https://doi.org/10.3390/computers14100429
Janisar AA, Meidan A, Kalid KSb, Gilal AR, Sarlan AB. Security Requirements Engineering: A Review and Analysis. Computers. 2025; 14(10):429. https://doi.org/10.3390/computers14100429
Chicago/Turabian StyleJanisar, Aftab Alam, Ayman Meidan, Khairul Shafee bin Kalid, Abdul Rehman Gilal, and Aliza Bt Sarlan. 2025. "Security Requirements Engineering: A Review and Analysis" Computers 14, no. 10: 429. https://doi.org/10.3390/computers14100429
APA StyleJanisar, A. A., Meidan, A., Kalid, K. S. b., Gilal, A. R., & Sarlan, A. B. (2025). Security Requirements Engineering: A Review and Analysis. Computers, 14(10), 429. https://doi.org/10.3390/computers14100429









