VCC-SSF: Service-Oriented Security Framework for Vehicular Cloud Computing
Abstract
:1. Introduction
2. Related Works
2.1. Architecture of VCC
2.2. Security Requirements for VCC
- Confidentiality: In a VCC environment, attackers can easily extort sensitive personal information such as the unique details of a vehicle or email address of driver, phone number, or residential address using man-in-the-middle (MITM) attacks. This is because the unique information of a vehicle or private information are used for application services, and in these cases, the attacker may tap the data using a Sniffing attack in-the-middle. Hence, this information should be encrypted to protect the data from MITM attacks.
- Integrity: Integrity should be provided for the information sent in a VCC environment. If the integrity of the driver’s personal identification information, payment information, or location information is compromised by message forgery or a falsification attack, it could cause financial damage to the user or have fatal consequences in emergency situations. To defend against attacks on data integrity, important data should have its integrity guaranteed by hash functions and digital signatures.
- Availability: In VANET communication, a wireless network is used to communicate between vehicles. In the case of Cluster-based Routing (CBR), a header vehicle and adjacent vehicles form a cluster for mutual communication, and among these vehicles, a malicious user could interrupt or stop the service of the target vehicle with a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack such as Flooding or Jamming. Additionally, an attack on availability could occur if a malicious user hinders the routing of the vehicle network with a black hole attack [14,15,16]. To ensure availability, a vehicle should be authenticated through an authentication mechanism, and only the authenticated vehicle should be able to access the corresponding object.
- Privacy Protection: Because various applications are now provided inside the vehicle, privacy invasions can occur. When the black box data inside the vehicle is exposed, privacy is exposed. Additionally, because of the exposure of personal information, vehicle location information, and vehicle route provided by the navigation service, privacy invasion occurs. To prevent privacy invasions, encryption should be applied to important information. In addition, for identification or authentication of a vehicle or user, instead of using a unique ID, a random ID should be used to provide anonymity.
2.3. Previous Research on VCC
3. VCC-SSF
3.1. Architecture of VCC-SSF
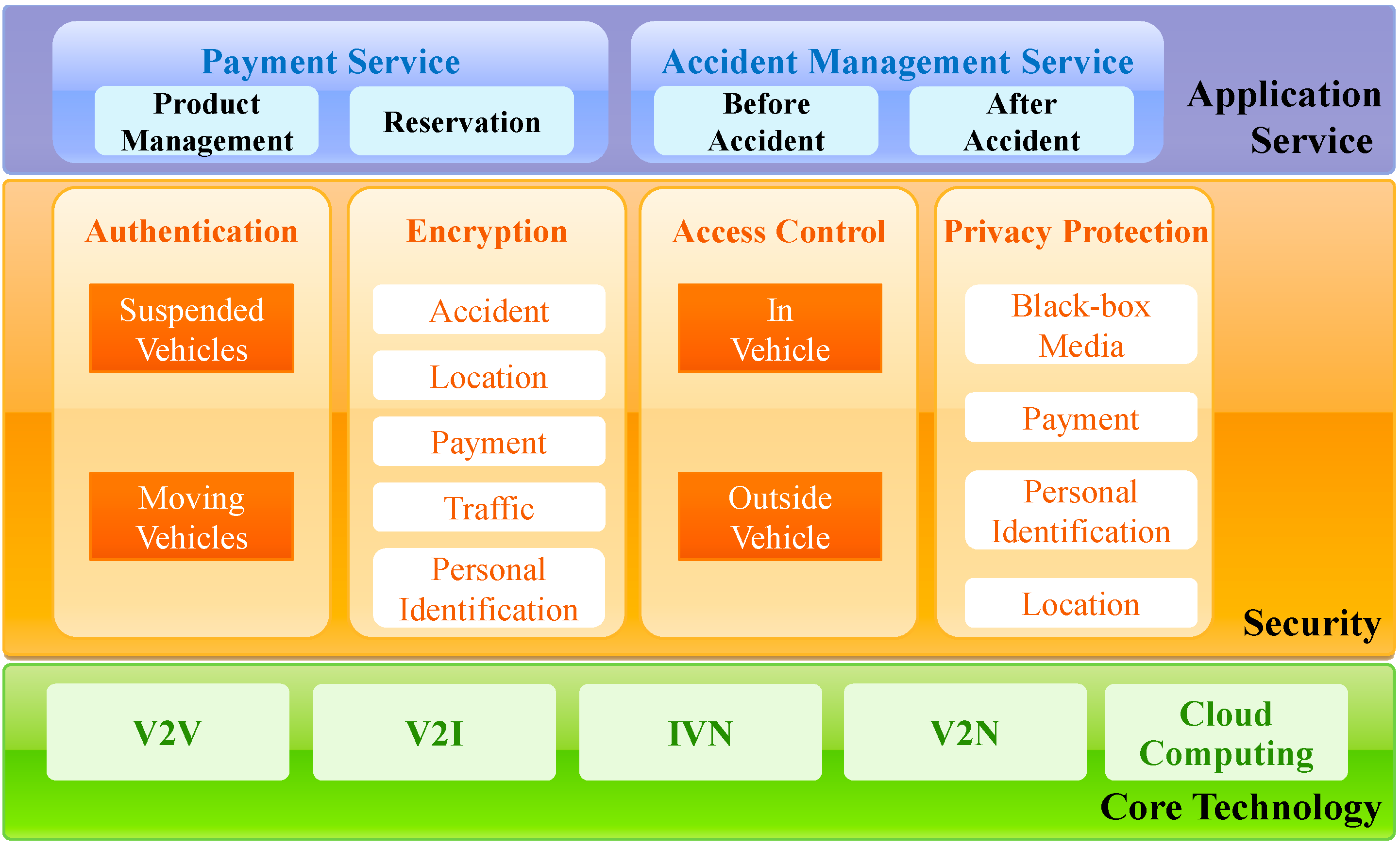
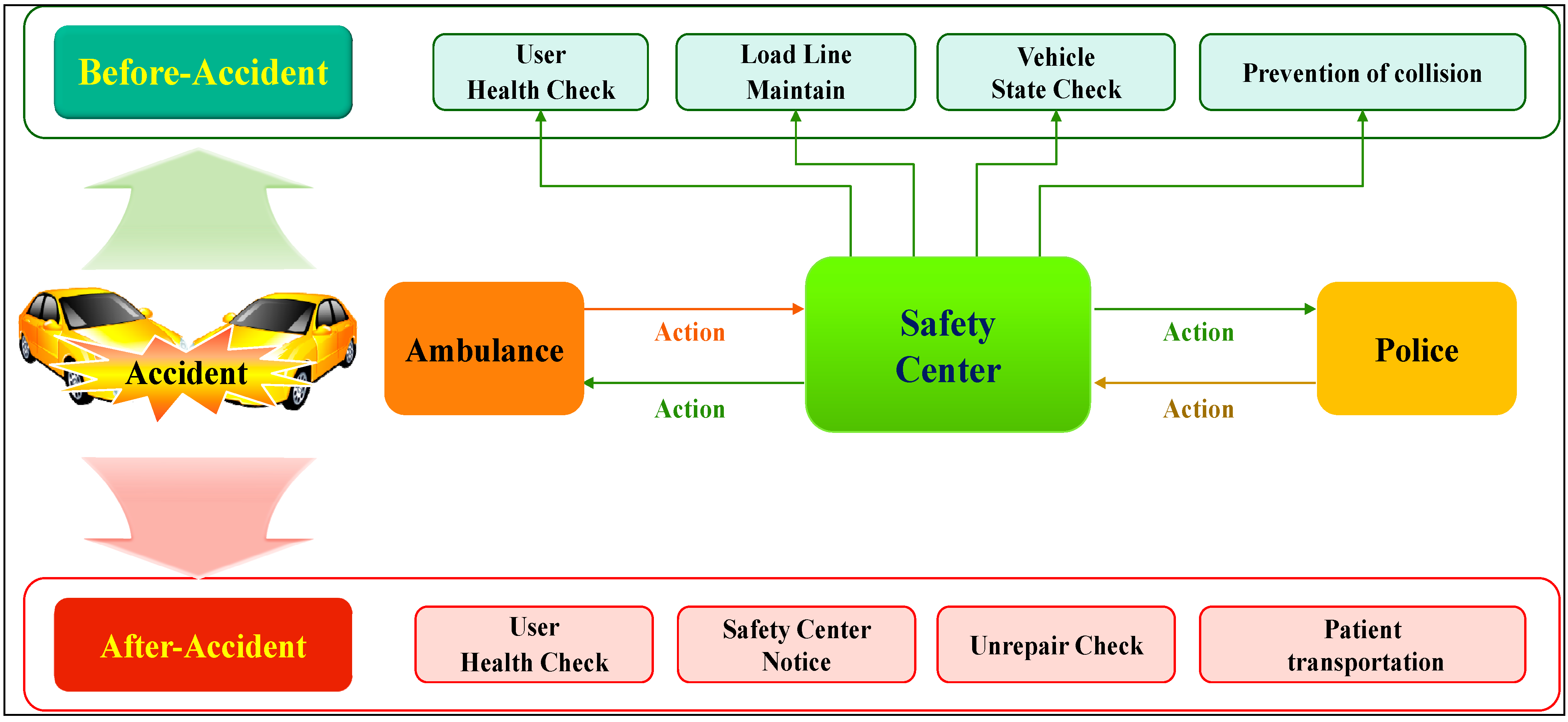
3.2. Application Service Layer
3.3. Security Layer
| Terms | Definition |
|---|---|
| VS/VM | Stationary vehicle/Moving vehicle |
| CA/U/SP | Certificate Authority/User/Service Provider |
| RSU/ECU | Road Side Unit/Electronic Control Unit |
| Hash ( )/Shift ( ) | Hash Algorithm/Circular Shift Operation |
| Ex ( )/Dy ( ) | Encryption algorithm using x key/Decryption algorithm using y key |
| Sigx ( )/Veryy ( ) | Signature algorithm using x key/Verification algorithm using y key |
| C/P/Cert | Encrypted Message/Plain Text/Certificate |
| Kx_prv/Kx_pub | Private Key of X/Public Key of X |
| PVID/RID | Pseudo Vehicular ID/Road Side Unit ID |
| RK | Random Values |
| DN/VN | Driver Number/Vehicle Number |
| X_TS | Time Stamp Values of X |
| ET | Expiry Time of Certificate |
| AcNo | Number of Accesses |
| VC_Int_Info/VC_Ext_Info | Internal/External Information |
- Authentication procedure: Vehicle authentication utilizes V2I communication. Using the Pseudo Vehicular ID (PVID) and driver’s Driver Number (DN) issued by the RSU, certificates are issued from the Certificate Authority (CA). The issued certificates are signed with Kca_prv, and the vehicle verifies the certificate with Kca_pub.If (V_TS = 0) thenDeliver CA → VS: Cert VS = [Hash(PVID ⊕ DN), C_TS, ET, RID, AcNo] Kca_prvelseDeliver CA → VM: Cert VM = [Hash(PVID ⊕ DN), RID, C_TS, ET, RID, AcNo] Kca_prvIf V_TS is 0, the vehicle is considered to be stationary. The stationary vehicle is marked as VS, and the CA issues the certificate to VS. The certificate includes the PVID and DN hash value, Time Stamp values of Certificate (C_TS), Expiry time of Certificate (ET), Road Side Unit ID (RID), and the Number of Accesses (AcNo). The C_TS is the time when the certificate is issued, and the ET is the expiration time of the certificate. The RID is the unique ID of the previous RSU, and by storing the IDs of RSU that vehicle has already passed, the system can verify the previous route. AcNo is the number of authentication attempts allowed. If there are more than AcNo access attempts, access and authentication to the corresponding vehicle is restricted.
- Data integrity procedure: Data integrity is provided for the Critical Info (i.e., Personal Information, Payment Information, Location, User Information, and User State), which is sensitive information used both inside and outside the vehicle. This procedure is as follows.Signing VS, VM → RSU: Sig Kv_prv (Hash(Critical Info)) || PTo maintain data integrity inside the vehicle, the user hashes the Critical Info and signs it with Kv_prv to generate a hash value. This is then sent to the RSU along with the original information P.Verifying RSU: H = Very Kv_pub (Hash(Critical Info))The signed data is verified using Kv_pub, registered in the CA. In addition, the hash value is compared with hashing P. Hash value H is obtained after the mutual verification to check whether data integrity is guaranteed.
- Encryption of the information inside the vehicle: The Drive System, Braking System, Steering System, etc. inside the vehicle are controlled through the ECU. This information is frequently used inside the vehicle for service or function, and hence fast encryption is required. In this system, a symmetric key encryption method is used. Key generation is as follows:Generate Key = Shift(VN) ⊕ RKThe 128-bit unique number (VN) assigned by the manufacturer is used as the key for the symmetric key encryption. We perform a circular shift operation by seven bits on the VN, and eXclusive-OR the result with RK, generated using a random number generator inside the vehicle, to generate the final key.Encrypt OBD, OBU → U: C = EKey (VC_Int_Info)VC_Int_Info (i.e., Speed, Fuel, Oil Pressure, Tire Condition, GPS, Temperature, etc.) is displayed to the user inside the vehicle by the OBD. The OBU is also encrypted using a symmetric key encryption algorithm.
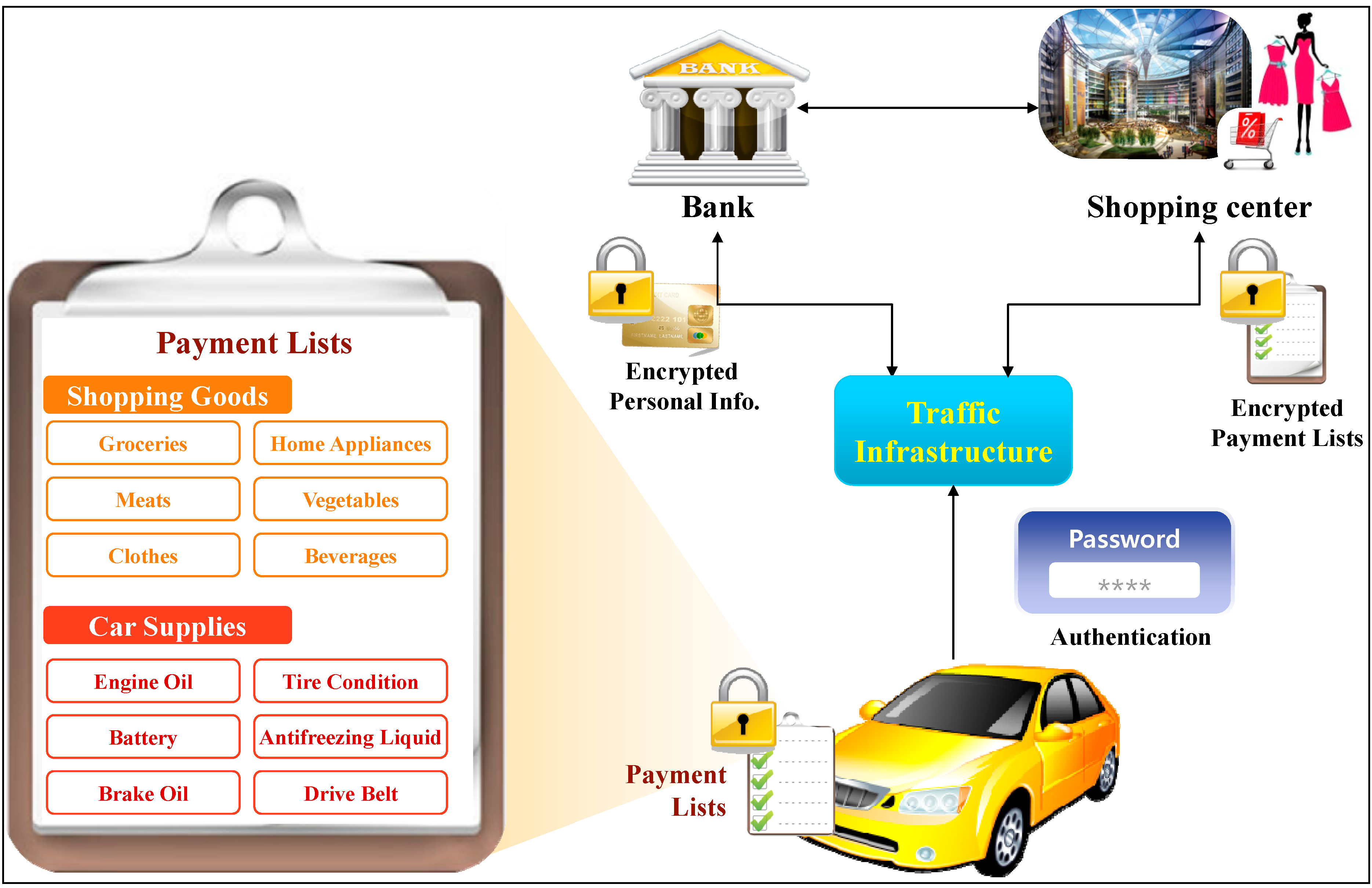
- Encryption for information using infrastructure: In the Application Layer, services are frequently provided through infrastructure, and the VC_Ext_Info (i.e., Personal Information, Payment Information, Location, User Information, and User State) is encrypted using a public key encryption algorithm.Encrypt VS, VM → RSU: C = E Ksp_pub (Hash(VC_Ext_Info))VC_Ext_Info is sent to an RSU by encrypting the hash value obtained by hashing the key of the Service Provider (SP) Ksp_pub. Key Ksp_pub is managed in the CA.SP decrypts the encrypted data using Ksp_prv, and hashes it to finally obtain and use VC_Ext_Info.Decrypt RSU → SP: P = D Ksp_prv (Hash(VC_Ext_Info))
- Access control for the internal system: The internal system displays the sensor information visually to the user through the OBU. There are various subjects that attempt to access this information. For example, car mechanics attempting to repair the vehicle, the vehicle owner, drivers other than the owner, and malicious attackers. When objects try to access this information, the role-based access controls access according to the situation information. In addition, we consider the time and place. No subjects except the vehicle owner can access the personal identification information. The example of role-based access control for time and location is shown in Table 2.
| Situation Information | Role | Permission |
|---|---|---|
| Time | R1: 06:00–24:00 | P1, P2, P3 |
| R2: 00:00–06:00 | P1, P2 (Optional) | |
| Location | R3: Parking lot | P1, P2 (Optional) |
| R4: Road | P1, P2 (Optional) | |
| R5: Repair shop | P1, P3 |
| Object | Access | |
|---|---|---|
| Vehicle owner | P1 | Can access all information |
| Guest driver | P2 | Driving information, traffic information |
| Car mechanic | P3 | Information of Drive System, Braking System, Steering System, etc. |
| Others | P4 | No access |
- Access control for outside the vehicle: From outside the vehicle, using V2V and V2I communication, traffic infrastructure and external vehicles also attempt to access the internal information. The traffic infrastructure attempts to access the location for traffic analysis or vehicle authentication. External vehicles attempt to access the information for services such as collision prevention or traffic lane maintenance as well as V2V communication. In both cases, the corresponding vehicle should also control the access of the traffic infrastructure and external vehicles. Only correctly authenticated vehicles can exchange information, but the other vehicles cannot access the information without permission.
| Classification | Role | Description |
|---|---|---|
| Authentication completed | A1: Full access permitted | Can access all information |
| A2: Only authenticated vehicles inside the cluster can access the information (e.g., location, destination, and traffic information sharing) | Information can be shared only within the cluster | |
| A3: Only the authenticated traffic infrastructure can access the information | Information transmission to the traffic infrastructure | |
| Partial authentication completed | P1: Information is shared with emergency vehicles | First aid, rescue, police vehicles, etc. |
| Authentication is not possible | N1: Cannot access the information | Vehicles without permission cannot access any information |
- Privacy protection with a vehicle alias ID: In the VCC environment, the vehicle authentication process uses the PVID. Instead of using the VN, we use a PVID assigned by an RSU during authentication. The VN is the unique number of each vehicle. Hence there is a risk of exposure of the vehicle owner’s personal information through inquiry to the management system. However, if a PVID is used, authentication can be performed without exposing the VN.
- Privacy protection with data encryption: An invasion of privacy occurs when the private identification information, location information, or video captured by the black box inside the vehicle are exposed to others. However, if this information is encrypted inside or outside the vehicle and not displayed to others, invasion of privacy does not occur. As mentioned above, the privacy of the DN, payment information, location information, and data in the black box can be protected using encryption.
3.4. Analysis of VCC-SSF
| Classification | Wan et al. [12] | Wan et al. [17] | Ma et al. [18] | Hussain and Oh [21] | Sur et al. [22] | VCC-SSF |
|---|---|---|---|---|---|---|
| Confidentiality | ∆ | O | X | O | O | O |
| Integrity | ∆ | O | X | O | X | O |
| Availability | X | X | X | X | X | ∆ |
| Privacy Protection | ∆ | O | X | O | O | ∆ |
4. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar] [CrossRef]
- Dias, J.A.F.F.; Rodrigues, J.J.P.C.; Zhou, L. Cooperation advances on vehicular communications: A survey. Veh. Commun. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Bawa, S. A systematic review on routing protocols for Vehicular Ad Hoc Networks. Veh. Commun. 2014, 1, 33–52. [Google Scholar] [CrossRef]
- Taysi, Z.C.; Yavuz, A.G. ETSI compliant GeoNetworking protocol layer implementation for IVC simulations. Hum.-Centric Comput. Inf. Sci. 2013, 3, 1–12. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular Ad Hoc network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Zeadally, S.; Hunt, R.; Chen, Y.-S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Grant-Muller, S.; Usher, M. Intelligent Transport Systems: The propensity for environmental and economic benefits. Technol. Forecast. Soc. Chang. 2014, 82, 149–166. [Google Scholar] [CrossRef]
- Hussain, R.; Oh, H. Cooperation-Aware VANET Clouds: Providing Secure Cloud Services to Vehicular Ad Hoc Networks. J. Inf. Process. Syst. 2014, 10, 103–118. [Google Scholar] [CrossRef]
- Yu, Z.; Gao, W.; Zuo, X. Design of Novel Intelligent Transportation System based on Wireless Sensor Network and ZigBee Technology. Sens. Transducers 2013, 166, 95–102. [Google Scholar]
- Abid, H.; Phuong, L.T.T.; Wang, J.; Lee, S.; Qaisar, S. V-Cloud: Vehicular cyber-physical systems and cloud computing. In Proceedings of the 4th International Symposium on Applied Sciences in Biomedical and Communication Technologies (ISABEL '11), Barcelona, Spain, 26–29 October 2011; Article 165. pp. 1–5.
- Gu, L.; Zeng, D.; Guo, S. Vehicular Cloud Computing: A Survey. In Proceedings of the 2013 IEEE Globecom Workshops (GC Workshops), Atlanta, GA, USA, 9–13 December 2013; pp. 403–407.
- Wan, J.; Zhang, D.; Sun, Y.; Lin, K.; Zou, C.; Cai, H. VCMIA: A Novel Architecture for Integrating Vehicular Cyber-Physical Systems and Mobile Cloud Computing. Mob. Netw. Appl. 2014, 19, 153–160. [Google Scholar]
- He, W.; Yan, G.; Xu, L.D. Developing Vehicular Data Cloud Services in the IoT Environment. IEEE Trans. Ind. Inform. 2014, 10, 1687–1695. [Google Scholar] [CrossRef]
- Sandhu, G.; Dasgupta, M. Impact of Blackhole Attack in MANET. Int. J. Recent Trends Eng. Technol. 2010, 3, 183–186. [Google Scholar]
- Tseng, F.-H.; Chou, L.-D.; Chao, H.-C. A survey of black hole attacks in wireless mobile ad hoc networks. Hum.-centric Comput. Inf. Sci. 2011. [Google Scholar] [CrossRef]
- Singh, R.; Singh, P.; Duhan, M. An effective implementation of security based algorithmic approach in mobile adhoc networks. Hum.-Centric Comput. Inf. Sci. 2014. [Google Scholar] [CrossRef]
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.T.; Lloret, J. Context-Aware Vehicular Cyber-Physical Systems with Cloud Support Architecture, Challenges, and Solutions. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Ma, M.; Huang, Y.; Chu, C.-H.; Wang, P. User-Driven Cloud Transportation System for Smart Driving. In Proceedings of the IEEE 4th International Conference on Cloud Computing Technology and Science (CloudCom), Taipei, Taiwan, 3–6 December 2012; pp. 658–665.
- Gerla, M.; Lee, E.-K.; Pau, G.; Lee, U. Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds. In Proceedings of the IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 241–246.
- Dressler, F.; Handle, P.; Sommer, C. Towards a Vehicular Cloud—Using Parked Vehicles as a Temporary Network and Storage Infrastructure. In Proceedings of the 2014 ACM international workshop on Wireless and mobile technologies for smart cities (WiMobCity-14), Philadelphia, PA, USA, 11–14 August 2014; pp. 11–18.
- Hussain, R.; Oh, H. A Secure and Privacy-Aware Route Tracing and Revocation Mechanism in VANET-based Clouds. J. Korea Inst. Inf. Secur. Cryptol. 2014, 24, 795–807. [Google Scholar] [CrossRef]
- Sur, C.; Park, Y.H.; Rhee, K.H. An efficient and secure navigation protocol based on vehicular cloud. Int. J. Comput. Math. 2014, 2014, 1–20. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, W.M.; Lee, J.D.; Jeong, Y.-S.; Park, J.H. VCC-SSF: Service-Oriented Security Framework for Vehicular Cloud Computing. Sustainability 2015, 7, 2028-2044. https://doi.org/10.3390/su7022028
Kang WM, Lee JD, Jeong Y-S, Park JH. VCC-SSF: Service-Oriented Security Framework for Vehicular Cloud Computing. Sustainability. 2015; 7(2):2028-2044. https://doi.org/10.3390/su7022028
Chicago/Turabian StyleKang, Won Min, Jae Dong Lee, Young-Sik Jeong, and Jong Hyuk Park. 2015. "VCC-SSF: Service-Oriented Security Framework for Vehicular Cloud Computing" Sustainability 7, no. 2: 2028-2044. https://doi.org/10.3390/su7022028
APA StyleKang, W. M., Lee, J. D., Jeong, Y.-S., & Park, J. H. (2015). VCC-SSF: Service-Oriented Security Framework for Vehicular Cloud Computing. Sustainability, 7(2), 2028-2044. https://doi.org/10.3390/su7022028





_Park.png)

