Performance Evaluation and Comparison of Cooperative Frameworks for IoT-Based VDTN
Abstract
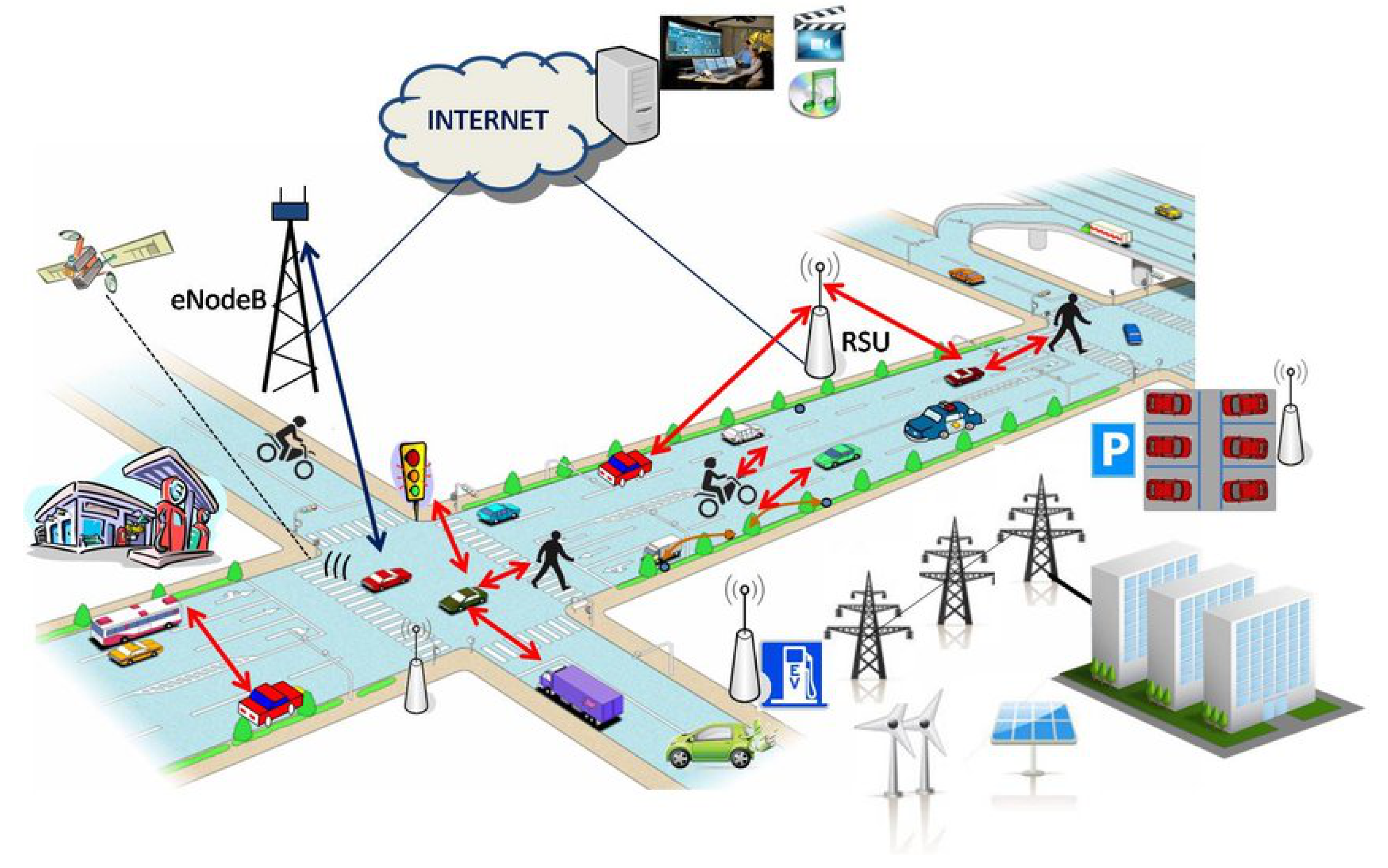
1. Introduction
- A review of the state-of-the-art that takes into consideration the most significant contributions to IoT-Based VDTN cooperation.
- Recommendations for six IoT-based VDTN cooperation methods.
- A study of the impact of node misbehavior on IoT-Based VDTN schemes using a large set of simulations.
- An evaluation and comparison of the performance of IoT-based VDTN cooperation methods in terms of different parameters, including packet delivery probability, packet delivery delay, throughput, overhead ratio, throughput, number of packets dropped, and energy consumption.
2. Related Works
3. Cooperation Strategies for IoT-Based VDTNs
3.1. Socially Omitting Selfishness in IoT for Smart and Connected Communities
3.2. Honesty-Based Democratic Scheme for Community Cooperation
3.3. Routing Defense Mechanism using Evolutionary Game Theory
3.4. Collaborative Trust Management Scheme
3.5. Incentive and Punishment Scheme for Internet of Vehicles
3.6. Active Trust Verification Data Collection Framework
4. Simulation Settings
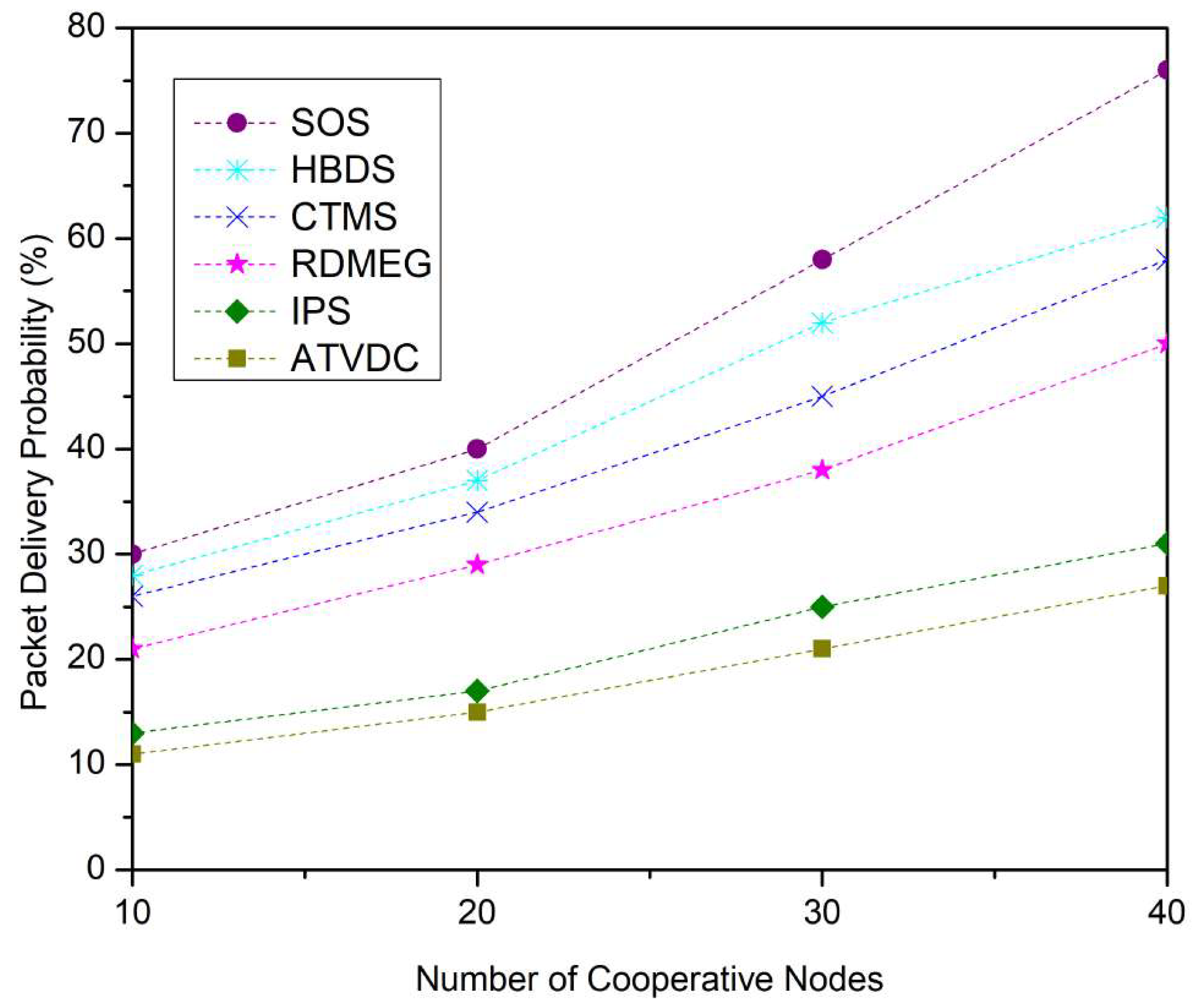
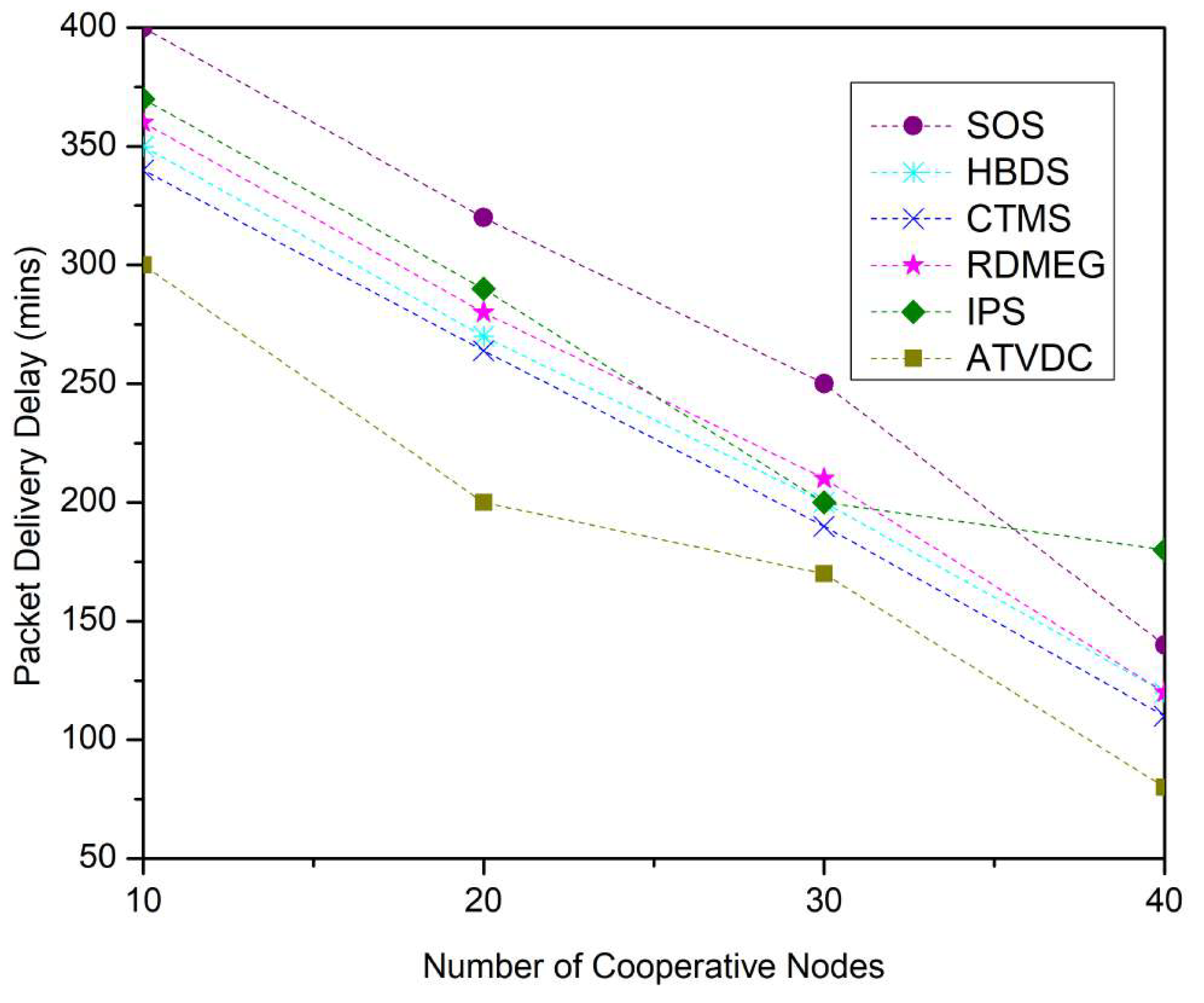
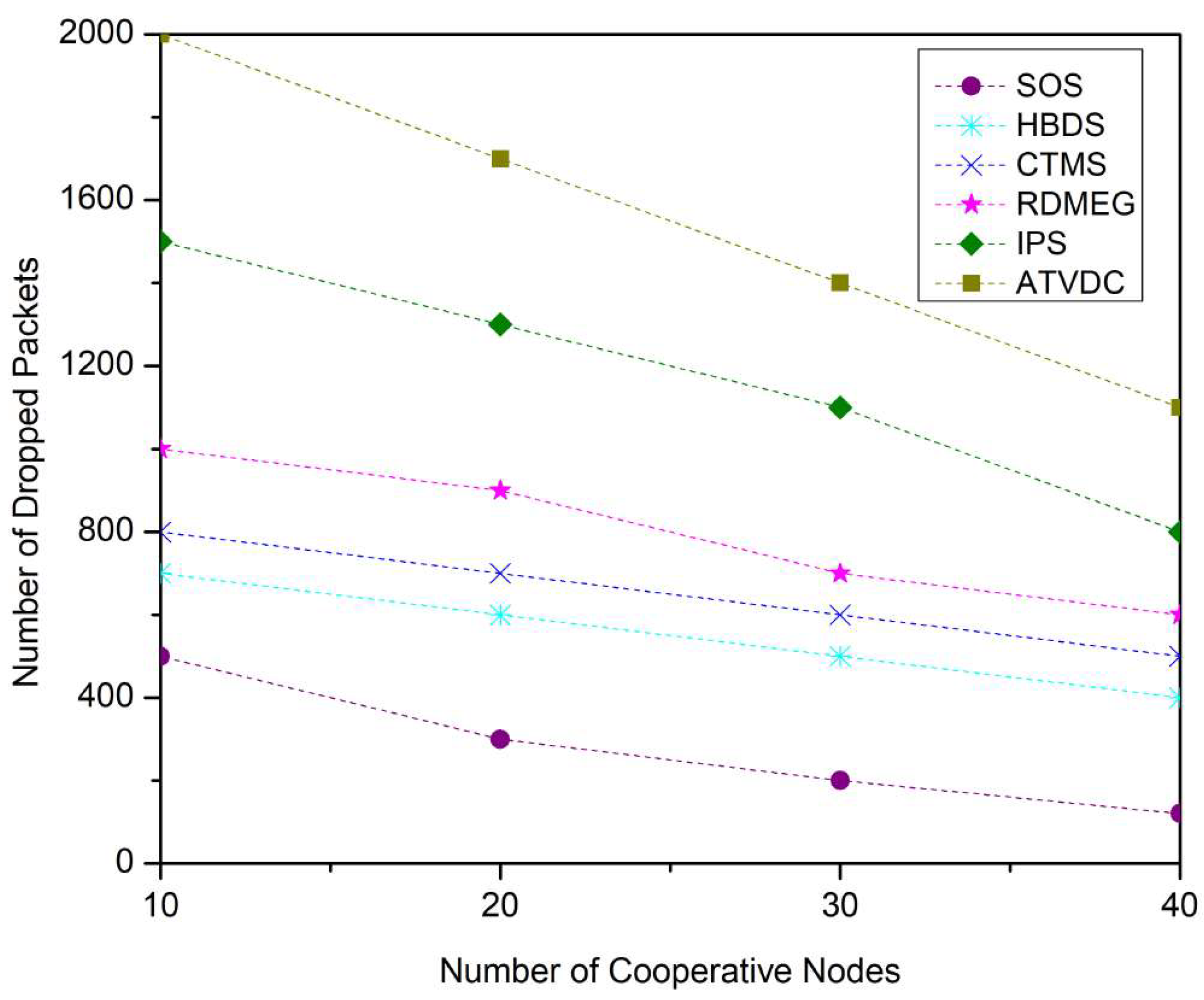
4.1. Performance Metrics
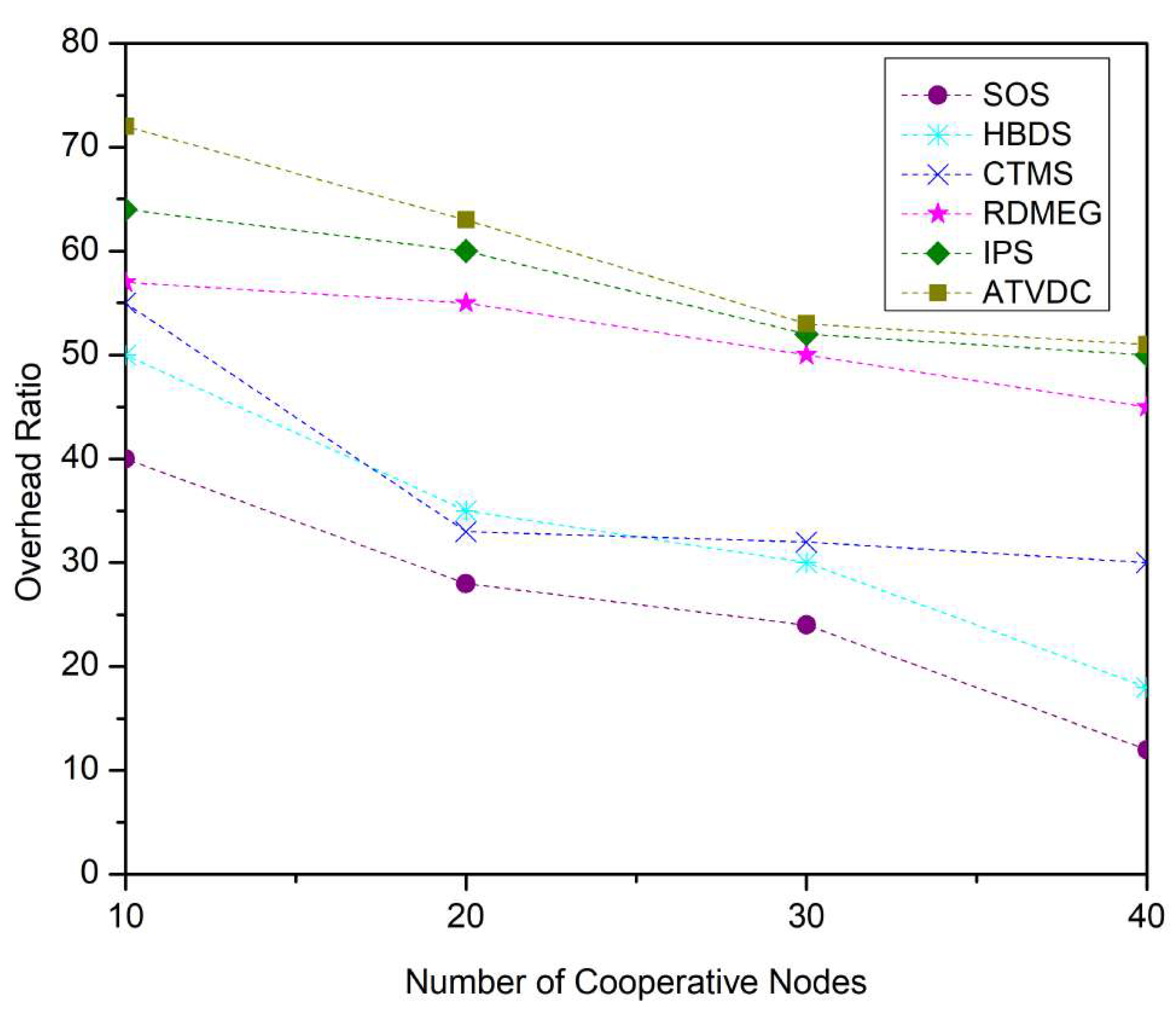
4.2. Results and Discussions
5. Conclusions and Future Works
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Piran, M.J.; Verma, S.; Menon, V.G.; Suh, D.Y. Energy-efficient transmission range optimization model for wsn-based internet of things. Comput. Mater. Contin. 2021, 67, 2989–3007. [Google Scholar]
- Awan, S.H.; Ahmed, S.; Safwan, N.; Najam, Z.; Hashim, M.Z.; Safdar, T. Role of internet of things (IoT) with blockchain technology for the development of smart farming. J. Mech. Contin. Math. Sci. 2019, 14, 170–188. [Google Scholar]
- Rehman, G.U.; Zubair, M.; Qasim, I.; Badshah, A.; Mahmood, Z.; Aslam, M.; Jilani, S.F. EMS: Efficient Monitoring System to Detect Non-Cooperative Nodes in IoT-Based Vehicular Delay Tolerant Networks (VDTNs). Sensors 2023, 23, 99. [Google Scholar] [CrossRef] [PubMed]
- Radwan, N.; Farouk, M. The Growth of Internet of Things (IoT) In The Management of Healthcare Issues and Healthcare Policy Development. Int. J. Technol. Innov. Manag. IJTIM 2021, 1, 69–84. [Google Scholar] [CrossRef]
- Jan, B.; Farman, H.; Khan, M.; Talha, M.; Din, I.U. Designing a smart transportation system: An internet of things and big data approach. IEEE Wirel. Commun. 2019, 26, 73–79. [Google Scholar] [CrossRef]
- Farman, H.; Khan, Z.; Jan, B.; Boulila, W.; Habib, S.; Koubaa, A. Smart transportation in developing countries: An Internet-of-Things-based conceptual framework for traffic control. Wirel. Commun. Mob. Comput. 2022, 8219377. [Google Scholar] [CrossRef]
- Kumar, S.; Tiwari, P.; Zymbler, M. Internet of Things is a revolutionary approach for future technology enhancement: A review. J. Big Data 2019, 6, 1–21. [Google Scholar] [CrossRef]
- Yuehong, Y.; Zeng, Y.; Chen, X.; Fan, Y. The internet of things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar]
- Aly, W.H.F. A New Controller Placement Technique using Colored Petri-Nets Modelling for SDNs. In Proceedings of the 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Exeter, UK, 17–19 December 2020; pp. 941–947. [Google Scholar]
- Rehman, G.u.; Ghani, A.; Zubair, M.; Ghayyure, S.A.; Muhammad, S. Honesty based democratic scheme to improve community cooperation for Internet of Things based vehicular delay tolerant networks. Trans. Emerg. Telecommun. Technol. 2021, 32, e4191. [Google Scholar] [CrossRef]
- Rehman, G.U.; Haq, M.I.U.; Zubair, M.; Mahmood, Z.; Singh, M.; Singh, D. Misbehavior of nodes in IoT based vehicular delay tolerant networks VDTNs. Multimed. Tools Appl. 2022, 1–19. [Google Scholar] [CrossRef]
- Magaia, N.; Mastorakis, G.; Mavromoustakis, C.; Pallis, E.; Markakis, E.K. Intelligent Technologies for Internet of Vehicles; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Mahi, M.J.N.; Chaki, S.; Ahmed, S.; Biswas, M.; Kaiser, S.; Islam, M.S.; Sookhak, M.; Barros, A.; Whaiduzzaman, M. A Review on VANET Research: Perspective of Recent Emerging Technologies. IEEE Access 2022, 10, 65760–65783. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Tran, N.H.; Kazmi, S.A.; Dang, T.N.; Hong, C.S. Edge-computing-enabled smart cities: A comprehensive survey. IEEE Internet Things J. 2020, 7, 10200–10232. [Google Scholar] [CrossRef]
- Dey, K.C.; Rayamajhi, A.; Chowdhury, M.; Bhavsar, P.; Martin, J. Vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communication in a heterogeneous wireless network–Performance evaluation. Transp. Res. Part C Emerg. Technol. 2016, 68, 168–184. [Google Scholar] [CrossRef]
- Li, M.; Si, P.; Zhang, Y. Delay-tolerant data traffic to software-defined vehicular networks with mobile edge computing in smart city. IEEE Trans. Veh. Technol. 2018, 67, 9073–9086. [Google Scholar] [CrossRef]
- Vasilakos, A.; Zhang, Y.; Spyropoulos, T. Delay Tolerant Networks; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Sobin, C.; Raychoudhury, V.; Marfia, G.; Singla, A. A survey of routing and data dissemination in delay tolerant networks. J. Netw. Comput. Appl. 2016, 67, 128–146. [Google Scholar]
- Bylykbashi, K.; Spaho, E.; Barolli, L.; Xhafa, F. Routing in a many-to-one communication scenario in a realistic VDTN. J. High Speed Netw. 2018, 24, 107–118. [Google Scholar] [CrossRef]
- AlArnaout, Z.; Mostafa, N.; Alabed, S.; Aly, W.H.F.; Shdefat, A. RAPT: A Robust Attack Path Tracing Algorithm to Mitigate SYN-Flood DDoS Cyberattacks. Sensors 2023, 23, 102. [Google Scholar] [CrossRef]
- Zhao, K.; Wang, R.; Burleigh, S.C.; Sabbagh, A.; Wu, W.; De Sanctis, M. Performance of bundle protocol for deep-space communications. IEEE Trans. Aerosp. Electron. Syst. 2016, 52, 2347–2361. [Google Scholar] [CrossRef]
- Hentati, A.I.; Fourati, L.C. Comprehensive survey of UAVs communication networks. Comput. Stand. Interfaces 2020, 72, 103451. [Google Scholar] [CrossRef]
- Sharma, M.; Kumar, P.; Tomar, R.S. Vehicular connectivity algorithm for cooperative transportation systems. Comput. Electr. Eng. 2022, 102, 108199. [Google Scholar] [CrossRef]
- Raymond, J.W.; Olwal, T.O.; Kurien, A.M. Cooperative communications in machine to machine (M2M): Solutions, challenges and future work. IEEE Access 2018, 6, 9750–9766. [Google Scholar] [CrossRef]
- Khan, F.; Rehman, A.U.; Yahya, A.; Jan, M.A.; Chuma, J.; Tan, Z.; Hussain, K. A quality of service-aware secured communication scheme for internet of things-based networks. Sensors 2019, 19, 4321. [Google Scholar] [CrossRef] [PubMed]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Ben Zid, M. Security and privacy challenges in vehicular ad hoc networks. In Connected Vehicles in the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2020; pp. 223–251. [Google Scholar]
- Alaslani, M.; Nawab, F.; Shihada, B. Blockchain in IoT systems: End-to-end delay evaluation. IEEE Internet Things J. 2019, 6, 8332–8344. [Google Scholar] [CrossRef]
- Long, N.B.; Tran-Dang, H.; Kim, D.S. Energy-aware real-time routing for large-scale industrial internet of things. IEEE Internet Things J. 2018, 5, 2190–2199. [Google Scholar] [CrossRef]
- Ge, Y.; Nan, Y.; Guo, X. Maximizing network throughput by cooperative reinforcement learning in clustered solar-powered wireless sensor networks. Int. J. Distrib. Sens. Netw. 2021, 17, 15501477211007411. [Google Scholar] [CrossRef]
- Felemban, M.; Felemban, E.; Kobes, J.; Ghafoor, A. Threat management in data-centric IoT-based collaborative systems. ACM Trans. Internet Technol. TOIT 2019, 19, 1–19. [Google Scholar] [CrossRef]
- Ijemaru, G.K.; Ang, L.M.; Seng, K.P. Transformation from IoT to IoV for waste management in smart cities. J. Netw. Comput. Appl. 2022, 204, 103393. [Google Scholar] [CrossRef]
- Dias, J.A.; Rodrigues, J.J.; Kumar, N.; Saleem, K. Cooperation strategies for vehicular delay-tolerant networks. IEEE Commun. Mag. 2015, 53, 88–94. [Google Scholar] [CrossRef]
- Machado, C.; Westphall, C.M. Blockchain incentivized data forwarding in MANETs: Strategies and challenges. Ad Hoc Netw. 2021, 110, 102321. [Google Scholar] [CrossRef]
- Rehman, G.U.; Ghani, A.; Muhammad, S.; Singh, M.; Singh, D. Selfishness in vehicular delay-tolerant networks: A review. Sensors 2020, 20, 3000. [Google Scholar] [CrossRef]
- Magaia, N.; Sheng, Z. ReFIoV: A novel reputation framework for information-centric vehicular applications. IEEE Trans. Veh. Technol. 2018, 68, 1810–1823. [Google Scholar] [CrossRef]
- Dias, J.A.F.F. Performance of Management Solutions and Cooperation Approaches for Vehicular Delay-Tolerant Networks. Ph.D. Thesis, Universidade da Beira Interior, Covilhã, Portugal, 2017. [Google Scholar]
- Yan, L.; Shen, H.; Chen, K. MobiT: A distributed and congestion-resilient trajectory based routing algorithm for vehicular delay tolerant networks. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; pp. 209–214. [Google Scholar]
- Dias, J.A.; Rodrigues, J.J.; Xia, F.; Mavromoustakis, C.X. A cooperative watchdog system to detect misbehavior nodes in vehicular delay-tolerant networks. IEEE Trans. Ind. Electron. 2015, 62, 7929–7937. [Google Scholar] [CrossRef]
- Magaia, N.; Borrego, C.; Pereira, P.R.; Correia, M. ePRIVO: An enhanced privacy-preserving opportunistic routing protocol for vehicular delay-tolerant networks. IEEE Trans. Veh. Technol. 2018, 67, 11154–11168. [Google Scholar] [CrossRef]
- Benamar, N.; Singh, K.D.; Benamar, M.; El Ouadghiri, D.; Bonnin, J.M. Routing protocols in vehicular delay tolerant networks: A comprehensive survey. Comput. Commun. 2014, 48, 141–158. [Google Scholar] [CrossRef]
- Park, Y.; Sur, C.; Rhee, K.H. A secure incentive scheme for vehicular delay tolerant networks using cryptocurrency. Secur. Commun. Netw. 2018, 2018, 5932183. [Google Scholar] [CrossRef]
- Triadi, M.B.; Perdana, D.; Munadi, R.; Wenzao, L. A new variant of game theory based decision making (GTDM) algorithm routing protocols to improve energy efficiency on vehicular delay tolerant network (VDTN). Int. J. Commun. Netw. Inf. Secur. 2019, 11, 224–231. [Google Scholar] [CrossRef]
- Ogah, C.P.A. Security and Privacy in VANET-Based Intelligent Transport Systems (ITS); University of Surrey: Guildford, UK, 2018. [Google Scholar]
- Loudari, S.; Abouhassane, A.; Benamar, N.; Younis, M. DASH: A Distributed Approach for Selfishness Handling in a DTN. In Proceedings of the 2019 2nd IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Manama, Kingdom of Bahrain, 19–21 November 2019; pp. 1–6. [Google Scholar]
- Ye, F.; Chen, C.; Zheng, Z. Deep autoencoder-like nonnegative matrix factorization for community detection. In Proceedings of the 27th ACM International Conference on Information and Knowledge Management, Turin, Italy, 22–26 October 2018; pp. 1393–1402. [Google Scholar]
- Ning, Z.; Liu, L.; Xia, F.; Jedari, B.; Lee, I.; Zhang, W. CAIS: A copy adjustable incentive scheme in community-based socially aware networking. IEEE Trans. Veh. Technol. 2016, 66, 3406–3419. [Google Scholar] [CrossRef]
- Jain, S.; Verma, A. Bubble rap incentive scheme for prevention of node selfishness in delay-tolerant networks. In Smart Innovations in Communication and Computational Sciences; Springer: Berlin/Heidelberg, Germany, 2019; pp. 289–303. [Google Scholar]
- Hasani, H.; Babaie, S. Selfish node detection in ad hoc networks based on fuzzy logic. Neural Comput. Appl. 2019, 31, 6079–6090. [Google Scholar] [CrossRef]
- Jedari, B.; Liu, L.; Qiu, T.; Rahim, A.; Xia, F. A game-theoretic incentive scheme for social-aware routing in selfish mobile social networks. Future Gener. Comput. Syst. 2017, 70, 178–190. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, H.; Zhang, L.; Fang, L.; Li, F. Incentive mechanism for cooperative intrusion detection: An evolutionary game approach. In International Conference on Computational Science; Springer: Berlin/Heidelberg, Germany, 2018; pp. 83–97. [Google Scholar]
- Haq, A.; Faheem, Y. A peer-to-peer communication based content distribution protocol for incentive-aware delay tolerant networks. Wirel. Netw. 2020, 26, 583–601. [Google Scholar] [CrossRef]
- Sharma, A.; Goyal, N.; Guleria, K. Performance optimization in delay tolerant networks using backtracking algorithm for fully credits distribution to contrast selfish nodes. J. Supercomput. 2021, 77, 6036–6055. [Google Scholar] [CrossRef]
- Jethawa, H.; Madria, S. Reputation and credit based incentive mechanism for data-centric message delivery in DTNs. In Proceedings of the 2018 19th IEEE International Conference on Mobile Data Management (MDM), Aalborg, Denmark 26–28 June 2018; pp. 207–216. [Google Scholar]
- Dias, J.A.; Rodrigues, J.J.; Kumar, N.; Mavromoustakis, C.X. A hybrid system to stimulate selfish nodes to cooperate in vehicular delay-tolerant networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 5910–5915. [Google Scholar]
- Available online: https://www.researchgate.net/figure/The-Internet-of-Vehicles-scenario_fig1_310734157 (accessed on 12 December 2022).
- Rehman, G.u.; Ghani, A.; Zubair, M.; Saeed, M.I.; Singh, D. SOS: Socially omitting selfishness in IoT for smart and connected communities. Int. J. Commun. Syst. 2023, 36, e4455. [Google Scholar] [CrossRef]
- Guo, H.; Wang, X.; Cheng, H.; Huang, M. A routing defense mechanism using evolutionary game theory for delay tolerant networks. Appl. Soft Comput. 2016, 38, 469–476. [Google Scholar] [CrossRef]
- Asuquo, P.; Cruickshank, H.; Ogah, C.P.A.; Lei, A.; Sun, Z. A collaborative trust management scheme for emergency communication using delay tolerant networks. In Proceedings of the 2016 8th Advanced Satellite Multimedia Systems Conference and the 14th Signal Processing for Space Communications Workshop (ASMS/SPSC), Palma de Mallorca, Spain, 5–7 September 2016; pp. 1–6. [Google Scholar]
- Rehman, G.U.; Ghani, A.; Zubair, M.; Naqvi, S.H.A.; Singh, D.; Muhammad, S. Ips: Incentive and punishment scheme for omitting selfishness in the internet of vehicles (iov). IEEE Access 2019, 7, 109026–109037. [Google Scholar] [CrossRef]
- Huang, S.; Gui, J.; Wang, T.; Li, X. Joint mobile vehicle–UAV scheme for secure data collection in a smart city. Ann. Telecommun. 2021, 76, 559–580. [Google Scholar] [CrossRef]
- Fakhar, F. Investigate Network Simulation Tools in designing and managing intelligent systems. J. Inf. Syst. Telecommun. 2019, 7, 278–293. [Google Scholar]


| Scheme | Contributions | Strengths | Weaknesses |
|---|---|---|---|
| SOS [56] | Election scheme based on weight to handle the issue of selfishness | Alternate cooperation criteria | Monitoring nodes can be selfish |
| HBDS [10] | Election scheme based on honesty to solve the problem of selfishness | Incentive differentiation and normal punishment | Each node needs to use its memory to maintain the reputation file |
| CTMS [58] | Trust-based scheme is used to address the issue of selfishness | Efficient watchdog system | Due to the higher threshold reputation, nodes may be expelled from the network if they are not qualified |
| RDMEG [57] | Game theory scheme for motivating nodes to cooperate | Optimal decision-making | No incentive differentiation |
| IPS [59] | Incentive scheme for encouraging selfish nodes to cooperate | Efficient monitoring system | Ignores the selfish behaviors such as plotting, scheming, deception, self-interest, etc |
| ATVDC [60] | Trust-based scheme to handle the selfishness problem | Lower cost while gathering more data | Exchange of information between nodes can lead to leakage of private information |
| Parameters | Values |
|---|---|
| Simulation Area | 5000 × 4000 m |
| Number of nodes | 150 |
| Transmission Range | 500 m |
| Comparison | SOS, HBDS, CTMS, RDMEG, IPS, and ATVDC |
| Simulation Time | 48 h |
| Number of Relay Nodes | 50 |
| Number of Terminal Nodes | 100 |
| Terminal Nodes Buffer Capacity | 200 MB |
| Relay Node Buffer Capacity | 300 MB |
| Average Speed | 80 km/h |
| Number of Cooperative Nodes | 10, 20, 30, 40 |
| Interval for Packets Generation | [30, 40] s |
| Node Communication | IEEE 802.11a |
| Size of Packets | [100, 650 KB] |
| Packets TTL | 350 min |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, G.U.; Zubair, M.; Aly, W.H.F.; Farman, H.; Mahmood, Z.; Hoxha, J.; Butt, N.A. Performance Evaluation and Comparison of Cooperative Frameworks for IoT-Based VDTN. Sustainability 2023, 15, 5454. https://doi.org/10.3390/su15065454
Rehman GU, Zubair M, Aly WHF, Farman H, Mahmood Z, Hoxha J, Butt NA. Performance Evaluation and Comparison of Cooperative Frameworks for IoT-Based VDTN. Sustainability. 2023; 15(6):5454. https://doi.org/10.3390/su15065454
Chicago/Turabian StyleRehman, Ghani Ur, Muhammad Zubair, Wael Hosny Fouad Aly, Haleem Farman, Zafar Mahmood, Julian Hoxha, and Naveed Anwer Butt. 2023. "Performance Evaluation and Comparison of Cooperative Frameworks for IoT-Based VDTN" Sustainability 15, no. 6: 5454. https://doi.org/10.3390/su15065454
APA StyleRehman, G. U., Zubair, M., Aly, W. H. F., Farman, H., Mahmood, Z., Hoxha, J., & Butt, N. A. (2023). Performance Evaluation and Comparison of Cooperative Frameworks for IoT-Based VDTN. Sustainability, 15(6), 5454. https://doi.org/10.3390/su15065454







