Evaluating the Efficiency of Non-Orthogonal MU-MIMO Methods in Smart Cities Technologies & 5G Communication
Abstract
1. Introduction
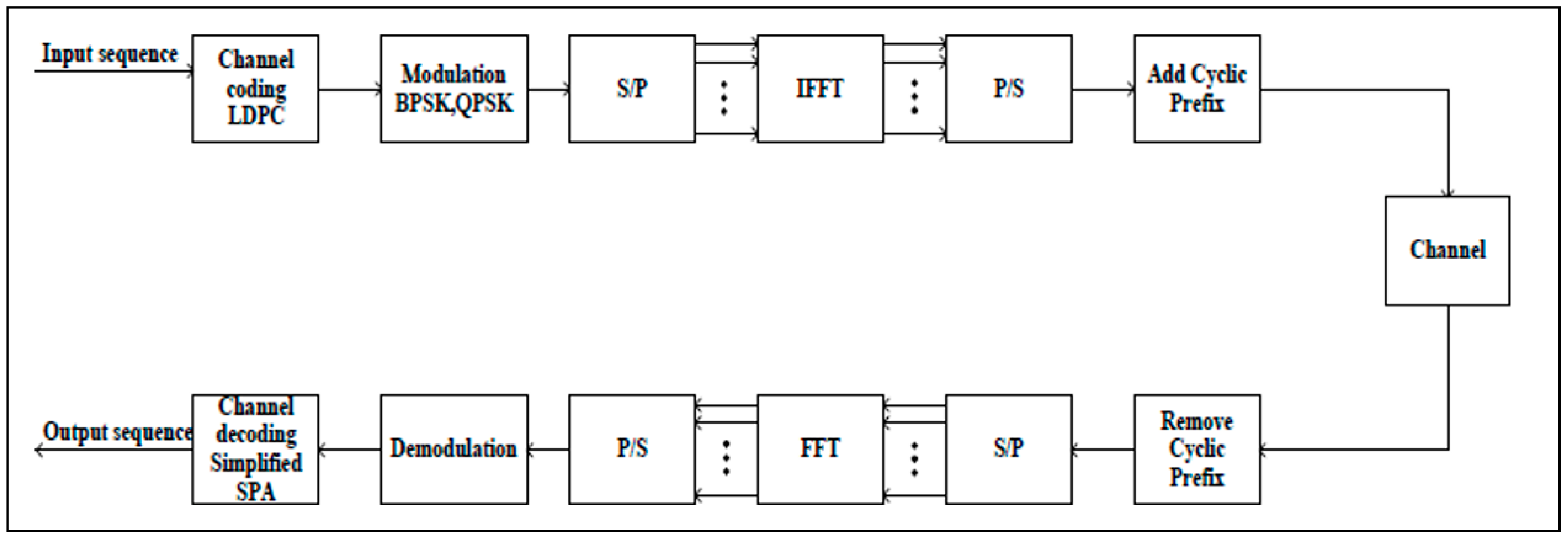
2. Schematic Model of Novel Approach
2.1. Coding and Decoding Algorithm Using LDPC
- (a)
- LDPC codes
- (b)
- Decoders
- Initialize variable notes
- Evaluate variable node ‘n’ and update all incoming messages.
- Variable node updation
- Decision-making from Step 2
2.2. OFDM Method
- Decide the length of spread codes based on no. of users
- Define the values set (−1, 0, 1)
- Generate Matrix
- Find out inter-correlation
- Identify zero values
- Generate Matrix which includes all zero correlation
- Finish the matrix using (6)
- Assign codes to different users
- Decide the degree of polynomial based on users
- Find out the length of polynomial
- Select the generating polynomial
- Establish a matrix that generates PN code
- Create a collection of intricate PN codes with actual and fictitious parts.
- Cross verify inter-correlation
- Assign codes to users.
2.3. Transmission Using Relay
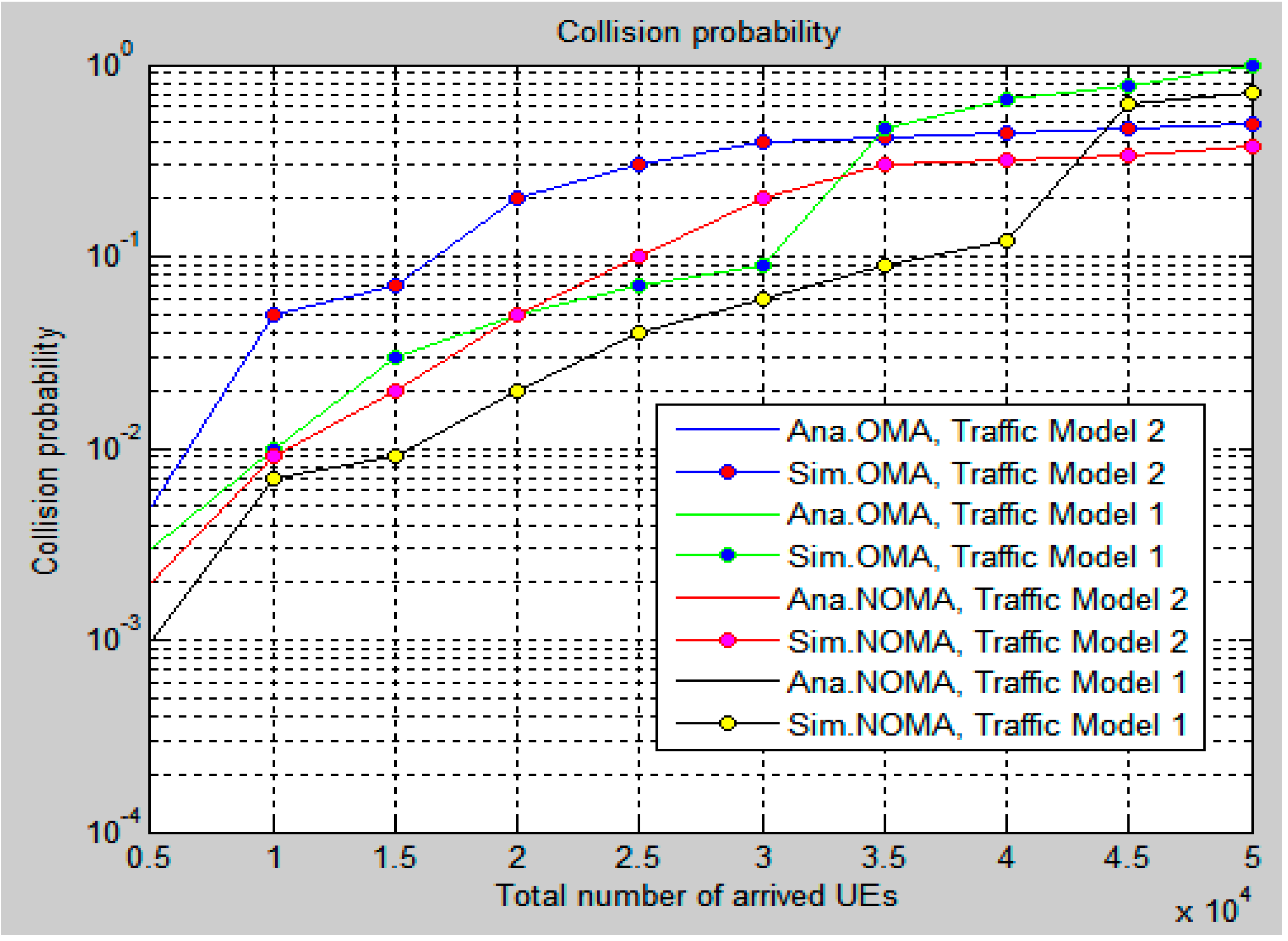
3. Simulation Outputs
4. Conclusions and Future Scope
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-lin, I.; Wang, Z. Nonorthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Yuan, Y.; Yuan, Z.; Yu, G.; Hwang, C.-h.; Liao, P.-k.; Li, A.; Takeda, K. Non-orthogonal transmission technology in LTE evolution. IEEE Commun. Mag. 2016, 54, 68–74. [Google Scholar] [CrossRef]
- Sun, Y.; Ng, D.W.K.; Ding, Z.; Schober, R. Optimal joint power and subcarrier allocation for full-duplex multicarrier non-orthogonal multiple access systems. IEEE Trans. Commun. 2017, 65, 1077–1091. [Google Scholar] [CrossRef]
- Fang, F.; Zhang, H.; Cheng, J.; Roy, S.; Leung, V.C.M. Joint user scheduling and power allocation optimization for energy-efficient NOMA systems with imperfect CSI. IEEE J. Sel. Areas Commun. 2017, 35, 2874–2885. [Google Scholar] [CrossRef]
- Li, A.; Lan, Y.; Chen, X.; Jiang, H. Non-orthogonal multiple access (NOMA) for future downlink radio access of 5G. China Commun. 2015, 12, 28–37. [Google Scholar] [CrossRef]
- Higuchi, K.; Benjebbour, A. Non-orthogonal multiple access (NOMA) with successive interference cancellation for future radio access. In Proceedings of the 2013 IEEE 77th Vehicular Technology Conference (VTC Spring), Dresden, Germany, 2–5 June 2013; pp. 403–414. [Google Scholar]
- Nguyen, H.V.; Kim, H.M.; Kang, G.-M.; Nguyen, K.-H.; Bui, V.-P.; Shin, O.-S. A Survey on Non-Orthogonal Multiple Access: From the Perspective of Spectral Efficiency and Energy Efficiency. Energies 2020, 13, 4106. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Avazov, N.; Dobre, O.A.; Kwak, K.-S. Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges. IEEE Commun. Surveys Tuts. 2017, 19, 721–742. [Google Scholar] [CrossRef]
- Akbar, A.; Jangsher, S.; Bhatti, F.A. NOMA and 5G emerging technologies: A survey on issues and solution techniques. Comput. Netw. 2021, 190, 107950, ISSN 1389-1286. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Ding, Z.; Wang, Z.; Chen, S.; Hanzo, L. A survey of non-orthogonal multiple access for 5G. IEEE Commun. Surveys Tuts. 2018, 20, 2294–2323. [Google Scholar] [CrossRef]
- Sun, Y.; Ng, D.W.K.; Ding, Z.; Schober, R. Optimal joint power and subcarrier allocation for MC-NOMA systems. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- He, J.; Tang, Z.; Che, Z. Fast and efficient user pairing and power allocation algorithm for non-orthogonal multiple access in cellular networks. Electron. Lett. 2016, 52, 2065–2067. [Google Scholar] [CrossRef]
- Ali, S.; Hossain, E.; Kim, D.I. Non-orthogonal multiple access (NOMA) for downlink multiuser MIMO systems: User clustering, beamforming, and power allocation. IEEE Access 2017, 5, 565–577. [Google Scholar] [CrossRef]
- Fu, Y.; Chen, Y.; Sung, C.W. Distributed downlink power control for the non-orthogonal multiple access system with two interfering cells. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Li, A.; Benjebbour, A.; Harada, A. Performance Evaluation of nonorthogonal multiple access combined with opportunistic beamforming. In Proceedings of the 2014 IEEE 79th Vehicular Technology Conference (VTC Spring), Seoul, Republic of Korea, 18–21 May 2014; pp. 1–5. [Google Scholar]
- Chen, Z.; Ding, Z.; Dai, X. Beamforming for Combating Inter-cluster and Intra-cluster Interference in Hybrid NOMA Systems. IEEE Access 2016, 4, 4452–4463. [Google Scholar] [CrossRef]
- Jiang, X.; Lu, H.; Chen, C.W. Enabling quality-driven scalable video transmission over multi-user NOMA system. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 1–9. [Google Scholar]
- Kumar, S.; Srivastava, P.K.; Pal, A.K.; Mishra, V.P.; Singhal, P.; Srivastava, G.K.; Mamodiya, U. Protecting location privacy in cloud services. J. Discret. Math. Sci. Cryptogr. 2022, 25, 1053–1062. [Google Scholar] [CrossRef]
- Çalhan, A.; Cicioğlu, M. Handover scheme for 5G small cell networks with non-orthogonal multiple access. Comput. Netw. 2020, 183, 107601, ISSN 1389-1286. [Google Scholar] [CrossRef]
- Higuchi, K. NOMA for Future Cellular Systems. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Luo, F.; Zhang, C. Non-orthogonal multiple access (NOMA): Concept and design. In Signal Processing for 5G: Algorithms and Implementations; Wiley: Hoboken, NJ, USA, 2016; pp. 143–167. [Google Scholar]
- Nonaka, N.; Kishiyama, Y.; Higuchi, K. Non-orthogonal multiple access using intra-beam superposition coding and SIC in base station cooperative MIMO cellular downlink. In Proceedings of the 2014 IEEE 80th Vehicular Technology Conference (VTC2014-Fall), Vancouver, BC, Canada, 14–17 September 2014; pp. 1651–1659. [Google Scholar]
- Sun, Q.; Han, S.; Xu, Z.; Wang, S.; Chih-lin, I.; Pan, Z. Sum rate optimization for MIMO non-orthogonal multiple access systems. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 747–752. [Google Scholar]
- Priyanka, P.; Singhai, R.; Shukla, P. Design and implementation of optimum LSD coded signal processing algorithm in the multiple-antenna system for the 5G wireless technology. Wirel. Commun. Mob. Comput. 2022, 2022, 7628814. [Google Scholar]
- Chen, Z.; Dai, X. MED precoding for multiuser MIMO-NOMA downlink transmission. IEEE Trans. Veh. Technol. 2017, 66, 5501–5505. [Google Scholar] [CrossRef]
- Kamayani, S.; Yadav, R.P.; Jain, K.C. Cyclic gradient descent optimization for joint MAP estimation of channel and phase noise in orthogonal frequency division multiplexing. IET Commun. 2018, 12, 1485–1490. [Google Scholar]
- Ding, Z.; Adachi, F.; Poor, H.V. The Application of MIMO to Non-Orthogonal Multiple Access. IEEE Trans. Wirel. Commun. 2016, 15, 537–552. [Google Scholar] [CrossRef]
- Timotheou, S.; Krikidis, I. Fairness for Non-Orthogonal Multiple Access in 5G Systems. IEEE Signal Process. Lett. 2015, 22, 1647–1651. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Zeng, M.; Dobre, O.A.; Kwak, K.-S. Resource allocation for downlink NOMA systems: Key techniques and open issues. IEEE Wireless Commun. 2018, 25, 40–47. [Google Scholar] [CrossRef]
- Kumar, S.; Dubey, K.K.; Gautam, A.K.; Verma, S.; Kumar, V.; Mamodiya, U. Detection of recurring vulnerabilities in computing services. J. Discret. Math. Sci. Cryptogr. 2022, 25, 1063–1071. [Google Scholar] [CrossRef]
- Kamayani, S.; Yadav, R.P.; Jain, K.C. Joint MAP channel estimation and data detection for OFDM in presence of phase noise from free running and phase locked loop oscillator. Digit. Commun. Netw. 2021, 7, 55–61. [Google Scholar]
- Ali, M.S.; Tabassum, H.; Hossain, E. Dynamic user clustering and power allocation for uplink and downlink non-orthogonal multiple access (NOMA) systems. IEEE Access 2016, 4, 6325–6343. [Google Scholar] [CrossRef]
- Shahab, M.B.; Kader, M.F.; Shin, S.Y. A virtual user pairing scheme to optimally utilize the spectrum of unpaired users in nonorthogonal multiple access. IEEE Signal Process. Lett. 2016, 23, 1766–1770. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, D.; Kumar, V.; Gupta, B.B.; El-Latif, A.A.A. Secure and Energy Efficient-Based E-Health Care Framework for Green Internet of Things. IEEE Trans. Green Commun. Netw. 2021, 5, 1223–1231. [Google Scholar] [CrossRef]
- Mohanta, H.C.; Geetha, B.T.; Alzaidi, M.S.; Dhanoa, I.S.; Bhambri, P.; Mamodiya, U.; Akwafo, R. An Optimized PI Controller-Based SEPIC Converter for Microgrid-Interactive Hybrid Renewable Power Sources. Wirel. Commun. Mob. Comput. 2022, 2022, 6574825. [Google Scholar] [CrossRef]
- Al-Abbasi, Z.Q.; So, D.K.C. User-pairing based non-orthogonal multiple access (NOMA) system. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Datta, S.N.; Kalyanasundaram, S. Optimal power allocation and user selection in non-orthogonal multiple access systems. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Cai, W.; Chen, C.; Bai, L.; Jin, Y.; Choi, J. Subcarrier and power allocation scheme for downlink OFDM-NOMA systems. IET Signal Process. 2017, 11, 51–58. [Google Scholar] [CrossRef]
- Liu, X.; Wang, X. Efficient Antenna Selection and User Scheduling in 5G Massive MIMO-NOMA System. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Saito, Y.; Benjebbour, A.; Kishiyama, Y.; Nakamura, T. Systemlevel performance evaluation of downlink non-orthogonal multiple access (NOMA). In Proceedings of the 2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 611–615. [Google Scholar]
- Saito, Y.; Kishiyama, Y.; Benjebbour, A.; Nakamura, T.; Li, A.; Higuchi, K. Non-orthogonal multiple access (NOMA) for cellular future radio access. In Proceedings of the 2013 IEEE 77th Vehicular Technology Conference (VTC Spring), Dresden, Germany, 2–5 June 2013; pp. 1–5. [Google Scholar]
- Priyanka, P.; Singhai, R.; Shukla, P.; Singhai, J. Realization of New Radio 5G-IoT Connectivity Using mmWave-Massive MIMO Technology. In 5G and Beyond; Chapman and Hall/CRC: Boca Raton, FL, USA, 2022; pp. 69–89. [Google Scholar]
- Balyan, V. Cooperative relay to relay communication using NOMA for energy efficient wireless communication. Telecommun. Syst. 2021, 77, 271–281. [Google Scholar] [CrossRef]
- Alzaidi, M.S.; Subbalakshmi, C.; Roshini, T.V.; Shukla, P.K.; Shukla, S.K.; Dutta, P.; Alhassan, M. 5G Telecommunication Allocation Network using IoT Enabled Improved Machine Learning Techniques. Wirel. Commun. Mob. Comput. 2022, 2022, 6229356. [Google Scholar] [CrossRef]
- Asim, A.; Seet, B.-C.; Hasan, M.A.; Li, X.J. A survey on the application of non-orthogonal multiple access to different wireless networks. Electronics 2019, 8, 1355. [Google Scholar]
- Yuan, Z.; Hu, Y.; Li, W.; Dai, J. Blind Multi-User Detection for Autonomous Grant-Free High-Overloading Multiple-Access without Reference Signal. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018; pp. 1–7. [Google Scholar]
- Yuan, Z.; Li, W.; Hu, Y.; Tang, H.; Dai, J.; Ma, Y. Blind Multi-user Detection Based on Receive Beamforming for Autonomous Grant-Free High-Overloading Multiple Access. In Proceedings of the 2019 IEEE 2nd 5G World Forum (5GWF), Dresden, Germany, 30 September–2 October 2019; pp. 520–523. [Google Scholar]
- Ding, Z.; Fan, P.; Poor, H.V. Impact of User Pairing on 5G Nonorthogonal Multiple-Access Downlink Transmissions. IEEE Trans. Veh. Technol. 2016, 65, 6010–6023. [Google Scholar] [CrossRef]
- Dutta, P.; Manna, G.C. Designing a Cognitive Radio with Enhancement in Throughput and Improved Spectrum Sensing Technique. In Proceedings of the 2016 2nd International Conference on Control Science and Systems Engineering (ICCSSE), Singapore, 27–29 July 2016. [Google Scholar]


| Parameter | Technique | Value |
|---|---|---|
| Channel Coding | LDPC | 1/2 |
| Modulation | QPSK | - |
| Channel | Rayleigh | - |
| FFT size | - | 64 |
| Number of Data Subcarriers | - | 52 |
| Walsh | 64 Length | |
| Multiple Access | PN | 64 Length |
| MUSA | 8 Length | |
| Signal to Noise Ratio | - | 1–20 dB |
| Number of Users | - | 12,16 |
| User Overload | - | 150%,200% |
| MIMO configurations | - | (1 × 6 × 30) |
| (Nt × N rr × Nr) | - | (1 × 30 × 30) |
| Detectors | MMSE | - |
| (1 × 26 × 30) K = 12 | (1 × 30 × 30) K = 12 | (1 × 26 × 30) K = 16 | (1 × 30 × 30) K = 16 | |
|---|---|---|---|---|
| Walsh | 0.0006593 | 0.0001083 | 0.004657 | 0.001864 |
| PN | 0.001593 | 0.0005998 | 0.006406 | 0.00559 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dutta, P.; Ramyasree, J.; Sridhar, V.; Minchula, V.K.; Mohanta, H.C.; Mahfoudh, S.; Shah, S.B.H.; Singh, S.P. Evaluating the Efficiency of Non-Orthogonal MU-MIMO Methods in Smart Cities Technologies & 5G Communication. Sustainability 2023, 15, 236. https://doi.org/10.3390/su15010236
Dutta P, Ramyasree J, Sridhar V, Minchula VK, Mohanta HC, Mahfoudh S, Shah SBH, Singh SP. Evaluating the Efficiency of Non-Orthogonal MU-MIMO Methods in Smart Cities Technologies & 5G Communication. Sustainability. 2023; 15(1):236. https://doi.org/10.3390/su15010236
Chicago/Turabian StyleDutta, Papiya, Jvl Ramyasree, V. Sridhar, Vinodh Kumar Minchula, Harish Chandra Mohanta, Saoucene Mahfoudh, Syed Bilal Hussain Shah, and Santar Pal Singh. 2023. "Evaluating the Efficiency of Non-Orthogonal MU-MIMO Methods in Smart Cities Technologies & 5G Communication" Sustainability 15, no. 1: 236. https://doi.org/10.3390/su15010236
APA StyleDutta, P., Ramyasree, J., Sridhar, V., Minchula, V. K., Mohanta, H. C., Mahfoudh, S., Shah, S. B. H., & Singh, S. P. (2023). Evaluating the Efficiency of Non-Orthogonal MU-MIMO Methods in Smart Cities Technologies & 5G Communication. Sustainability, 15(1), 236. https://doi.org/10.3390/su15010236












