Drone Forensics and Machine Learning: Sustaining the Investigation Process
Abstract
:1. Introduction
- Post-crash scattering of individual drone components encumbers routine association of parts to a drone seized at crash site.
- The diverse types of on-device components for a drone imply that the use of a single digital forensic investigation tool will not serve the purpose of investigation; a full range of tools, both hardware and software, would be needed to run a thorough forensic procedure.
- Physical data acquisition of forensic images from a drone may not be practicable as certain drones only permit wireless transfer of images.
- Access control and protection mechanisms may prevent certain data elements from being acquired as part of the forensic image. Moreover, drone controller chips may be accessible only through an owner-signed remote controller, which can be difficult to emulate by law enforcement.;
- Certain drones have multiple file systems on them, thus encumbering the process of identifying the right tool to be able to carry out data acquisition.
- Add-on software makes it difficult to forecast the software platform, file system and the corresponding hardware configuration for a seized drone.
- Flash memory and RAM can lose data after a crash, if the battery of the drone runs out;
- Data logs may be partial or programmed to not hold any data depending on the drone model.
- Deliberate attempts by a remote controller to wipe out data on a confiscated drone does not help the law enforcement procedure.
2. Background
2.1. Digital Forensics Frameworks
2.2. Forensic Readiness for Popular Drone Families
3. Machine Learning from Drone Forensics
3.1. Machine Learning Primer
3.2. Machine Learning for Drone Data
3.3. Machine Learning for Drone Data
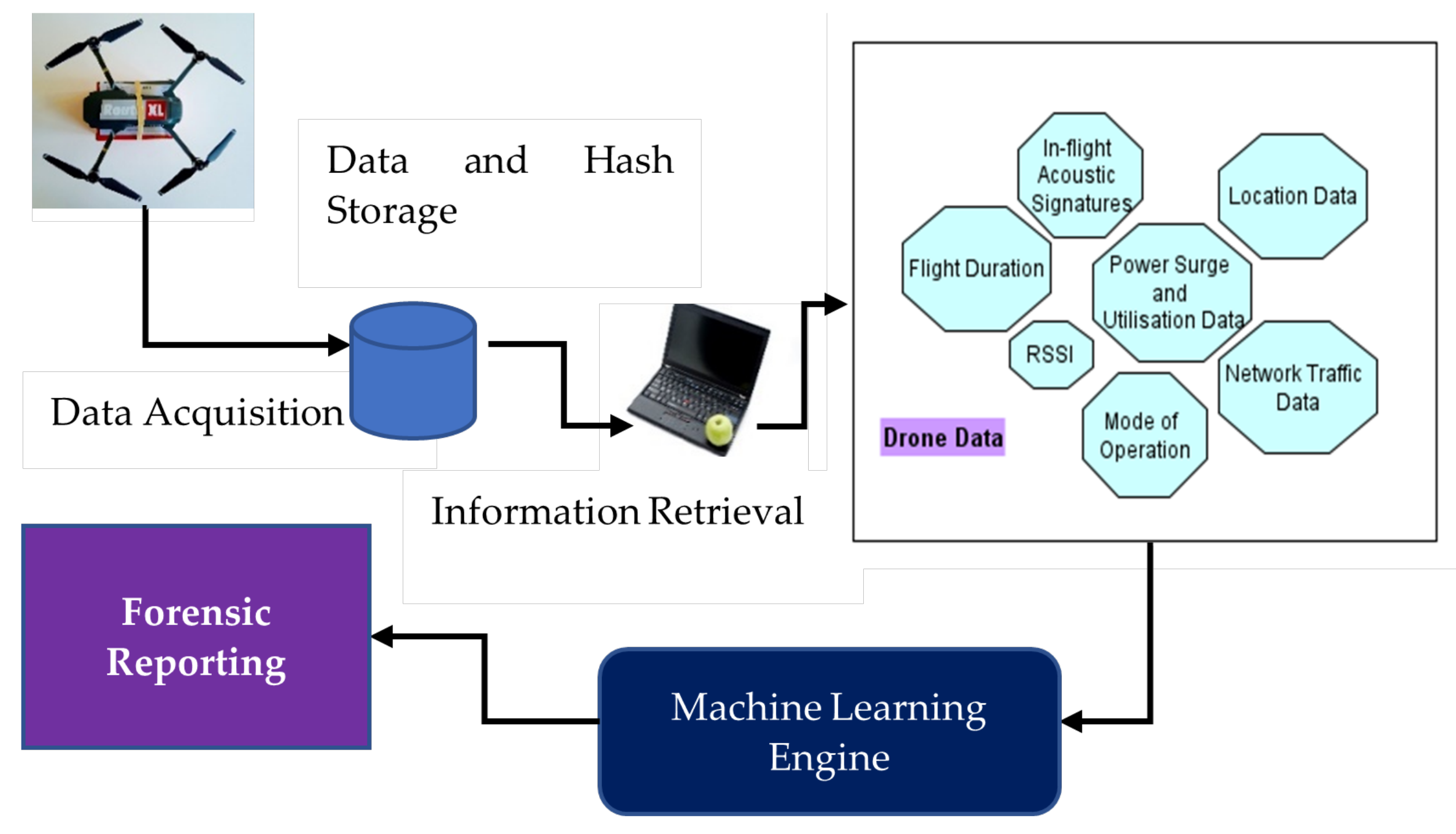
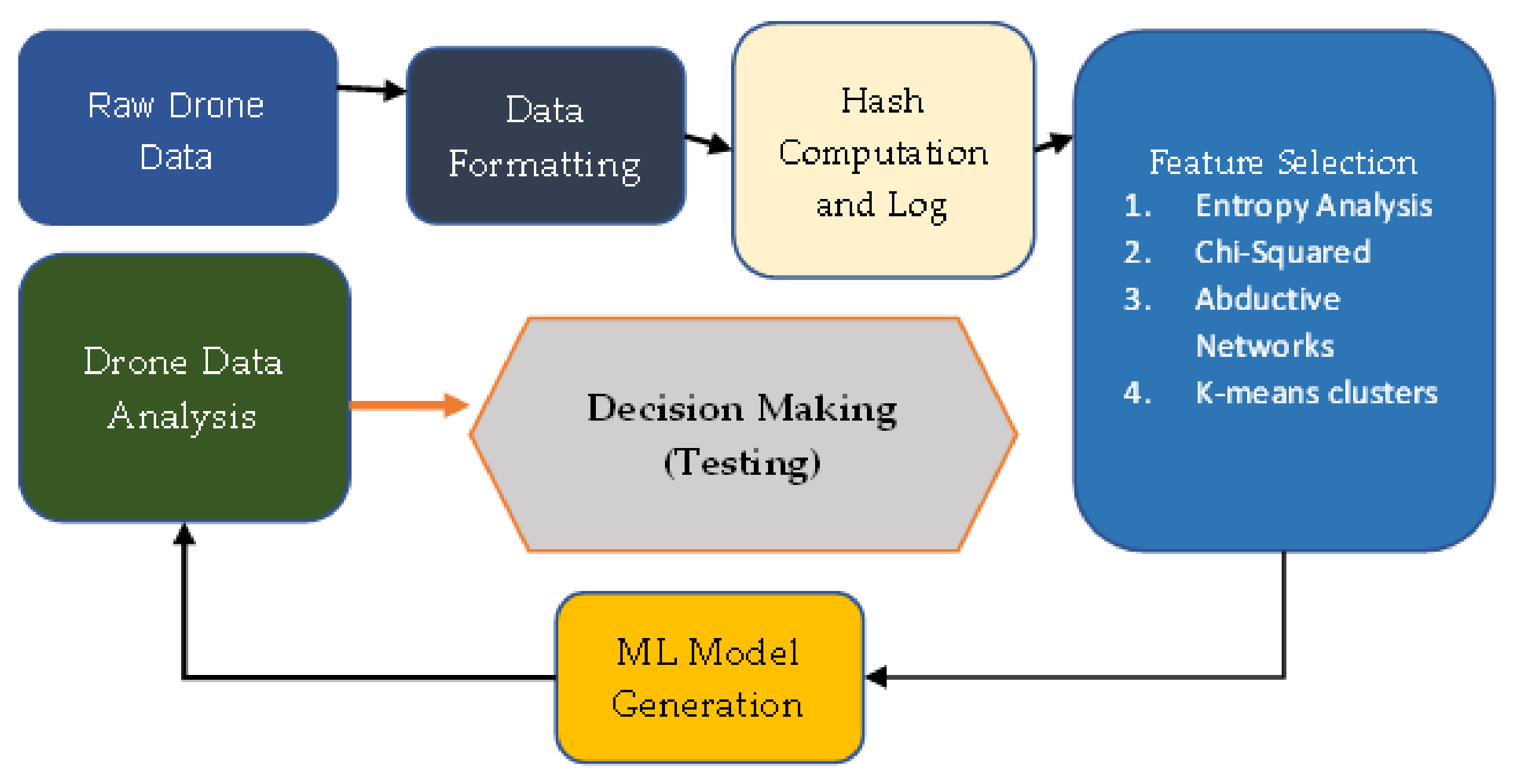
4. A Machine-Learning-Based Drone Forensics Framework
- Drone coordinates;
- Flight trajectory;
- Flight duration;
- Battery life;
- Drone-to-controller communication frequency;
- Drone-to-controller data exchange definitions.
- Data is securely extracted without affecting its integrity;
- Data is securely stored through validation and cross examination, in order to maintain a chain of custody;
- Preprocessing of data is then conducted based on those techniques that were adopted for preprocessing of the training data;
- ML-based data classification is then conducted to identify whether or not the drone was involved in a malicious event.
- Received signal strength indicator (RSSI)–normal ranges;
- Drone in-flight acoustic signatures—noise;
- Flight data as time-series sensory values;
- Power surge or utilization data;
- Location data;
- Network traffic–packet loss data, interarrival times of data packets, packet lengths;
- Mode of operation data–ON, hovering, flying or recording.
- Limits to the volume of training data that may be available during the training phase of the machine-learning process;
- Unclear demarcation in the classes of normal and anomalous data retrieved from previously crashed/confiscated drones;
- Inability of the machine-learning algorithm to accurately classify live drone data into normal or anomalous (with a high degree of admissible accuracy)
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Renduchintala, A.; Jahan, F.; Khanna, R.; Javaid, A.Y. A comprehensive micro unmanned aerial vehicle (UAV/Drone) forensic framework. Digit. Investig. 2019, 30, 52–72. [Google Scholar] [CrossRef]
- Drone Technology Uses and Applications for Commercial, Industrial and Military Drones in 2021 and the Future. 2021. Available online: https://www.businessinsider.com/drone-technology-uses-applications (accessed on 14 April 2022).
- Hummel, K.A.; Pollak, M.; Krahofer, J. A distributed architecture for human-drone teaming: Timing challenges and interaction opportunities. Sensors 2019, 19, 1379. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yanmaz, E.; Quaritsch, M.; Yahyanejad, S.; Rinner, B.; Hellwagner, H.; Bettstetter, C. Communication and coordination for drone networks. In Ad hoc Networks; Springer: Berlin/Heidelberg, Germany, 2017; pp. 79–91. [Google Scholar]
- Tanaka, H.; Matsumoto, Y. Autonomous Drone Guidance and Landing System Using AR/high-accuracy Hybrid Markers. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 15–18 October 2019; pp. 598–599. [Google Scholar]
- Yousef, M.; Iqbal, F. Drone forensics: A case study on a DJI Mavic Air. In Proceedings of the 2019 IEEE/ACS 16th International Conference on Computer Systems and Applications (AICCSA), Abu Dhabi, United Arab Emirates, 3–7 November 2019; pp. 1–3. [Google Scholar]
- Bouafif, H.; Kamoun, F.; Iqbal, F.; Marrington, A. Drone forensics: Challenges and new insights. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–6. [Google Scholar]
- Flynt, J. How Much Weight Can a Drone Carry? Available online: https://3dinsider.com/drone-payload/ (accessed on 14 April 2022).
- Flynt, J. 5 Best Heavy Lift Drones-Large Drones That Have High Lift Capacity. Available online: https://www.dronethusiast.com/heavy-lift-drones/ (accessed on 14 April 2022).
- Al-Room, K.; Iqbal, F.; Baker, T.; Shah, B.; Yankson, B.; MacDermott, A.; Hung, P.C. Drone Forensics: A Case Study of Digital Forensic Investigations Conducted on Common Drone Models. Int. J. Digit. Crime Forensics (IJDCF) 2021, 13, 1–25. [Google Scholar] [CrossRef]
- Renduchintala, A.L.S.; Albehadili, A.; Javaid, A.Y. Drone forensics: Digital flight log examination framework for micro drones. In Proceedings of the 2017 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2017; pp. 91–96. [Google Scholar]
- Yousef, M.; Iqbal, F.; Hussain, M. Drone forensics: A detailed analysis of emerging DJI models. In Proceedings of the 2020 11th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 7–9 April 2020; pp. 66–71. [Google Scholar]
- Iqbal, F.; Alam, S.; Kazim, A.; MacDermott, Á. Drone forensics: A case study on DJI phantom 4. In Proceedings of the 2019 IEEE/ACS 16th International Conference on Computer Systems and Applications (AICCSA), Abu Dhabi, United Arab Emirates, 3–7 November 2019; pp. 1–6. [Google Scholar]
- Lan, J.K.W.; Lee, F.K.W. Drone Forensics: A Case Study on DJI Mavic Air 2. In Proceedings of the 2022 24th International Conference on Advanced Communication Technology (ICACT), Seoul, Korea, 13–16 February 2022; pp. 291–296. [Google Scholar]
- Bouafif, H.; Kamoun, F.; Iqbal, F. Towards a better understanding of drone forensics: A case study of parrot AR drone 2.0. Int. J. Digit. Crime Forensics (IJDCF) 2020, 12, 35–57. [Google Scholar] [CrossRef]
- Barton, T.E.A.; Azhar, M.H.B. Forensic analysis of popular UAV systems. In Proceedings of the 2017 Seventh International Conference on Emerging Security Technologies (EST), Canterbury, UK, 6–8 September 2017; pp. 91–96. [Google Scholar]
- Carrier, B. Open Source Digital Forensics Tools: The Legal Argument. 2002. Available online: http://www.atstake.com/ (accessed on 14 April 2022).
- Harvey, P. Exiftool for Linux. Available online: http://www.sno.phy.queensu.ca/phil/exiftool/ (accessed on 14 April 2022).
- Trujano, F.; Chan, B.; Beams, G.; Rivera, R. Security analysis of dji phantom 3 standard. Mass. Inst. Technol. 2016. Available online: https://courses.csail.mit.edu/6.857/2016/files/9.pdf (accessed on 14 April 2022).
- Clark, D.R.; Meffert, C.; Baggili, I.; Breitinger, F. DROP (DRone Open source Parser) your drone: Forensic analysis of the DJI Phantom III. Digit. Investig. 2017, 22, S3–S14. [Google Scholar] [CrossRef]
- Kao, D.Y.; Chen, M.C.; Wu, W.Y.; Lin, J.S.; Chen, C.H.; Tsai, F. Drone forensic investigation: DJI spark drone as a case study. Procedia Comput. Sci. 2019, 159, 1890–1899. [Google Scholar] [CrossRef]
- Alhawiti, K.M. Advances in artificial intelligence using speech recognition. Int. J. Comput. Inf. Eng. 2015, 9, 1432–1435. [Google Scholar]
- Nadkarni, P.M.; Ohno-Machado, L.; Chapman, W.W. Natural language processing: An introduction. J. Am. Med. Inform. Assoc. 2011, 18, 544–551. [Google Scholar] [CrossRef] [Green Version]
- Murphy, R.R. Introduction to AI Robotics; MIT Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Abdallah, A.; Maarof, M.A.; Zainal, A. Fraud detection system: A survey. J. Netw. Comput. Appl. 2016, 68, 90–113. [Google Scholar] [CrossRef]
- Kulik, S. Neural network model of artificial intelligence for handwriting recognition. J. Theor. Appl. Inf. Technol. 2015, 73, 202–211. [Google Scholar]
- Voronin, V.; Marchuk, V.; Semenishchev, E.; Makov, S.; Creutzburg, R. Digital inpainting with applications to forensic image processing. Electron. Imaging 2016, 28, 1–7. [Google Scholar]
- Francisca, O.; Ogbuju, E.; Alayesanmi, F.; Musa, A. The State of the Art in Machine Learning-Based Digital Forensics. SSRN Elec. J. 2020. [Google Scholar] [CrossRef]
- Bertino, E.; Kantarcioglu, M.; Akcora, C.G.; Samtani, S.; Mittal, S.; Gupta, M. AI for Security and Security for AI. In Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy, Virtual, 26–28 April 2021; pp. 333–334. [Google Scholar]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hachimi, M.; Kaddoum, G.; Gagnon, G.; Illy, P. Multi-stage jamming attacks detection using deep learning combined with kernelized support vector machine in 5g cloud radio access networks. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–5. [Google Scholar]
- Luo, P.; Wang, B.; Li, T.; Tian, J. ADS-B anomaly data detection model based on VAE-SVDD. Comput. Secur. 2021, 104, 102213. [Google Scholar] [CrossRef]
- Xiao, L.; Xie, C.; Min, M.; Zhuang, W. User-centric view of unmanned aerial vehicle transmission against smart attacks. IEEE Trans. Veh. Technol. 2017, 67, 3420–3430. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Tuan, H.D.; Lambotharan, S.; Hanzo, L. Physical layer security: Detection of active eavesdropping attacks by support vector machines. IEEE Access 2021, 9, 31595–31607. [Google Scholar] [CrossRef]
- Carrio, A.; Sampedro, C.; Rodriguez-Ramos, A.; Campoy, P. A review of deep learning methods and applications for unmanned aerial vehicles. J. Sens. 2017, 2017, 3296874. [Google Scholar] [CrossRef]
- Rydén, H.; Redhwan, S.B.; Lin, X. Rogue drone detection: A machine learning approach. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar]
- Al-Emadi, S.; Al-Ali, A.; Al-Ali, A. Audio-Based Drone Detection and Identification Using Deep Learning Techniques with Dataset Enhancement through Generative Adversarial Networks. Sensors 2021, 21, 4953. [Google Scholar] [CrossRef]
- Lee, D.; La, W.G.; Kim, H. Drone detection and identification system using artificial intelligence. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 17–19 October 2018; pp. 1131–1133. [Google Scholar]
- CVOnline-Image Databases. Available online: https://homepages.inf.ed.ac.uk/rbf/CVonline/Imagedbase.htm (accessed on 14 April 2022).
- Ahn, H. Deep learning based anomaly detection for a vehicle in swarm drone system. In Proceedings of the 2020 International Conference on Unmanned Aircraft Systems (ICUAS), Athens, Greece, 1–4 September 2020; pp. 557–561. [Google Scholar]
- Jeong, S.; Bito, J.; Tentzeris, M.M. Design of a novel wireless power system using machine learning techniques for drone applications. In Proceedings of the 2017 IEEE Wireless Power Transfer Conference (WPTC), Taipei, Taiwan, 10–12 May 2017; pp. 1–4. [Google Scholar]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. PiNcH: An effective, efficient, and robust solution to drone detection via network traffic analysis. Comput. Netw. 2020, 168, 107044. [Google Scholar] [CrossRef] [Green Version]
- Nemer, I.; Sheltami, T.; Ahmad, I.; Yasar, A.U.H.; Abdeen, M.A.R. RF-Based UAV Detection and Identification Using Hierarchical Learning Approach. Sensors 2021, 21, 1947. [Google Scholar] [CrossRef]
- Shoufan, A.; Al-Angari, H.M.; Sheikh, M.F.A.; Damiani, E. Drone Pilot Identification by Classifying Radio-Control Signals. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2439–2447. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. Detecting Drones Status via Encrypted Traffic Analysis. In Proceedings of the ACM Workshop on Wireless Security and Machine Learning (WiseML 2019), Miami, FL, USA, 15–17 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 67–72. [Google Scholar] [CrossRef]
- Park, J.; Kim, Y.; Seok, J. Prediction of information propagation in a drone network by using machine learning. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016; pp. 147–149. [Google Scholar]
- Al-Dhaqm, A.; Ikuesan, R.A.; Kebande, V.R.; Razak, S.; Ghabban, F.M. Research Challenges and Opportunities in Drone Forensics Models. Electronics 2021, 10, 1519. [Google Scholar] [CrossRef]
- Viswanathan, S.; Baig, Z. Digital Forensics for Drones: A Study of Tools and Techniques. In International Conference on Applications and Techniques in Information Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 29–41. [Google Scholar]
- Mekala, S.H.; Baig, Z. Digital Forensics for Drone Data–Intelligent Clustering Using Self Organising Maps. In Future Network Systems and Security; Doss, R., Piramuthu, S., Zhou, W., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 172–189. [Google Scholar]
- Fei, B.; Eloff, J.; Venter, H.; Olivier, M. Exploring forensic data with self-organizing maps. In Ifip International Conference on Digital Forensics; Springer: Berlin/Heidelberg, Germany, 2005; pp. 113–123. [Google Scholar]
- Feyereisl, J.; Aickelin, U. Self-organizing maps in computer security. In Computer Security: Intrusion, Detection and Prevention; Hopkins, R.D., Ed.; University of Melbourne: Melbourne, VIC, Australia, 2009; pp. 1–30. [Google Scholar]
- Adelstein, F. Live forensics: Diagnosing your system without killing it first. Commun. ACM 2006, 49, 63–66. [Google Scholar] [CrossRef]
- He, H.; Ma, Y. Imbalanced Learning: Foundations, Algorithms, and Applications; Wiley-IEEE Press: Hoboken, NJ, USA, 2013. [Google Scholar]
| Drone Family | Data Extracted | Encryption | Memory | Forensic Readiness |
|---|---|---|---|---|
| 3DR Solo [1] | Text-based Logs and Flight path | No | 16 GB | High |
| Yuneec Typhon H [1] | Text-based Logs and Flight Path | No | 128 GB | Med |
| DJI Phantom 4, DJI Mavic DJI Spark [11] | .dat and .txt files EXIF for images Date/time stamps GPS Coordinates Flight Path | Yes (3rd party tools req.) | 8 GB | High (if decryption enabled) |
| Parrot AR [7] | Flight Path Images and Video EXIF for images | No | 8 GB | Med |
| Paper | Year | Short Description | Scope | Evaluation Type |
|---|---|---|---|---|
| [30] | 2019 | Machine-Learning Techniques used for UAV-based Communications | ML use to address communication concerns including channel modeling, resource management, positioning and security within UAV-based communication. | Survey Paper |
| [35] | 2017 | Deep-Learning Techniques used in UAV problem domain | Survey paper highlighting work performed on use of deep learning for feature extraction, planning, situational awareness and motion control aspects of UAV systems based on Aerostack architecture. | Survey Paper |
| [36] | 2019 | Rogue drone detection | A novel machine-learning approach to identify the rogue drones in mobile networks based on radio measurements | In Lab (Simulated data) |
| [37] | 2021 | Deep-Learning-based technique for drone detection and identification using acoustic data | Uses CNN, RNN and CRNN-based architectures to identify drones using acoustic fingerprints of flying drones. | In Lab (Real data with augmentation) |
| [38] | 2018 | Drone detection and identification system using Artificial Intelligence | Uses Haar classifier to detect a drone in an image and then uses CNN model to identify the type of drone. | In Lab (Real data) |
| [40] | 2020 | Deep-learning-based anomaly detection for a vehicle in swarm drone system | The proposed anomaly detection model uses a deep neural network-based generation model to create a training model with normal data and perform tests with abnormal data. | In Lab (Real data) |
| [41] | 2017 | Novel wireless power transfer system for drones using machine-learning techniques | Machine-learning model (using naïve Bayes) is used to identify position of the drone for enhancing wireless power transfer efficiency. | In Field |
| [42] | 2020 | Drone detection via network traffic analysis | Detect presence, status and movement of drones by applying standard classification algorithms to the eavesdropped traffic, analyzing features such as packets inter-arrival time and size. | In Field |
| [43] | 2021 | RF-Based UAV Detection and Identification | UAV detection and identification based on radio frequency (RF) data using hierarchical ensemble learning approach. The first classifier detects UAVs, second one identifies the type of UAV and the remaining two are used to identify the mode of operations. | In Lab (Real data) |
| [44] | 2018 | Drone Pilot Identification based on Radio Control Signals | Describes an approach where radio control signal sent to an unmanned aerial vehicle (UAV) using a typical transmitter can be captured and analyzed to identify the controlling pilot using machine-learning techniques. | In Lab (Real data) |
| [45] | 2019 | Detecting drones status via encrypted traffic analysis | Detect the current status of a powered-on drone (flying or at rest), leveraging just the communication traffic exchanged between the drone and its remote controller (RC) analyzing features such as packets inter-arrival time and size. | In Field |
| [47] | 2021 | Research Challenges and Opportunities in Drone Forensics Models | It provides a detailed review of existing digital forensic models. It highlights the research challenges and opportunities through which an effective investigation can be carried out on drone-related incidents. | No evaluation |
| [49] | 2019 | Digital forensics for drone data using SOM | Proposes a methodology based on self-organizing map (SOM) for digital forensic analysis of drone data. | In Lab (Real data) |
| [46] | 2016 | Prediction of information propagation in a drone network by using machine learning | The packet transmission rates of a communication network with 20 drones were simulated, and results were used to train the linear regression and support vector machine with quadratic kernel (SVM-QK). | In Lab (Simulated data) |
| [48] | 2020 | Digital Forensics for Drones: A Study of Tools and Techniques | Proposes a methodology that can help forensic investigators identify the most pertinent forensic investigation tools | In Lab (Real data) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Baig, Z.; Khan, M.A.; Mohammad, N.; Brahim, G.B. Drone Forensics and Machine Learning: Sustaining the Investigation Process. Sustainability 2022, 14, 4861. https://doi.org/10.3390/su14084861
Baig Z, Khan MA, Mohammad N, Brahim GB. Drone Forensics and Machine Learning: Sustaining the Investigation Process. Sustainability. 2022; 14(8):4861. https://doi.org/10.3390/su14084861
Chicago/Turabian StyleBaig, Zubair, Majid Ali Khan, Nazeeruddin Mohammad, and Ghassen Ben Brahim. 2022. "Drone Forensics and Machine Learning: Sustaining the Investigation Process" Sustainability 14, no. 8: 4861. https://doi.org/10.3390/su14084861
APA StyleBaig, Z., Khan, M. A., Mohammad, N., & Brahim, G. B. (2022). Drone Forensics and Machine Learning: Sustaining the Investigation Process. Sustainability, 14(8), 4861. https://doi.org/10.3390/su14084861







