Advanced Authentication Scheme with Bio-Key Using Artificial Neural Network
Abstract
:1. Introduction
- We have proposed a new architecture for an advanced authentication scheme that utilized a binarized form (bio-key) of ECG signals in combination with ANN to improve the authentication process.
- We have designed a testbed using the AD8232 ECG recording module and acquired ECG signals of 47 subjects (including males and females) under a controlled environment.
- The bio-keys are generated using an algorithm and the template is constructed along with selected ECG features. These selected features besides bio-keys are further utilized for training/testing of the ANN model to enhance the accuracy of the authentication process.
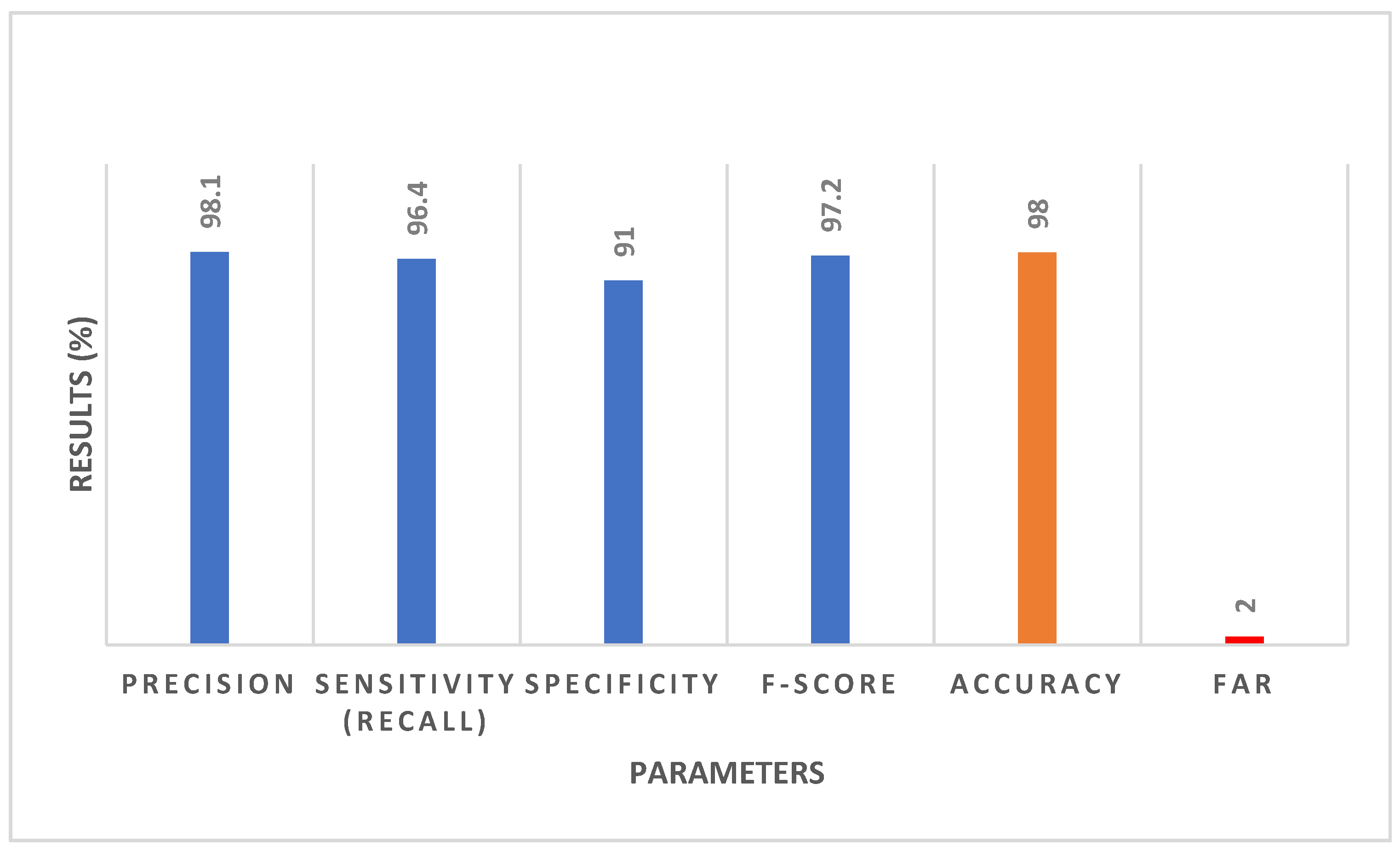
- The performance results of the proposed authentication scheme depicted high precision (98.1%), authentication accuracy (98%), and minimized equal error rate (EER) (0.02).
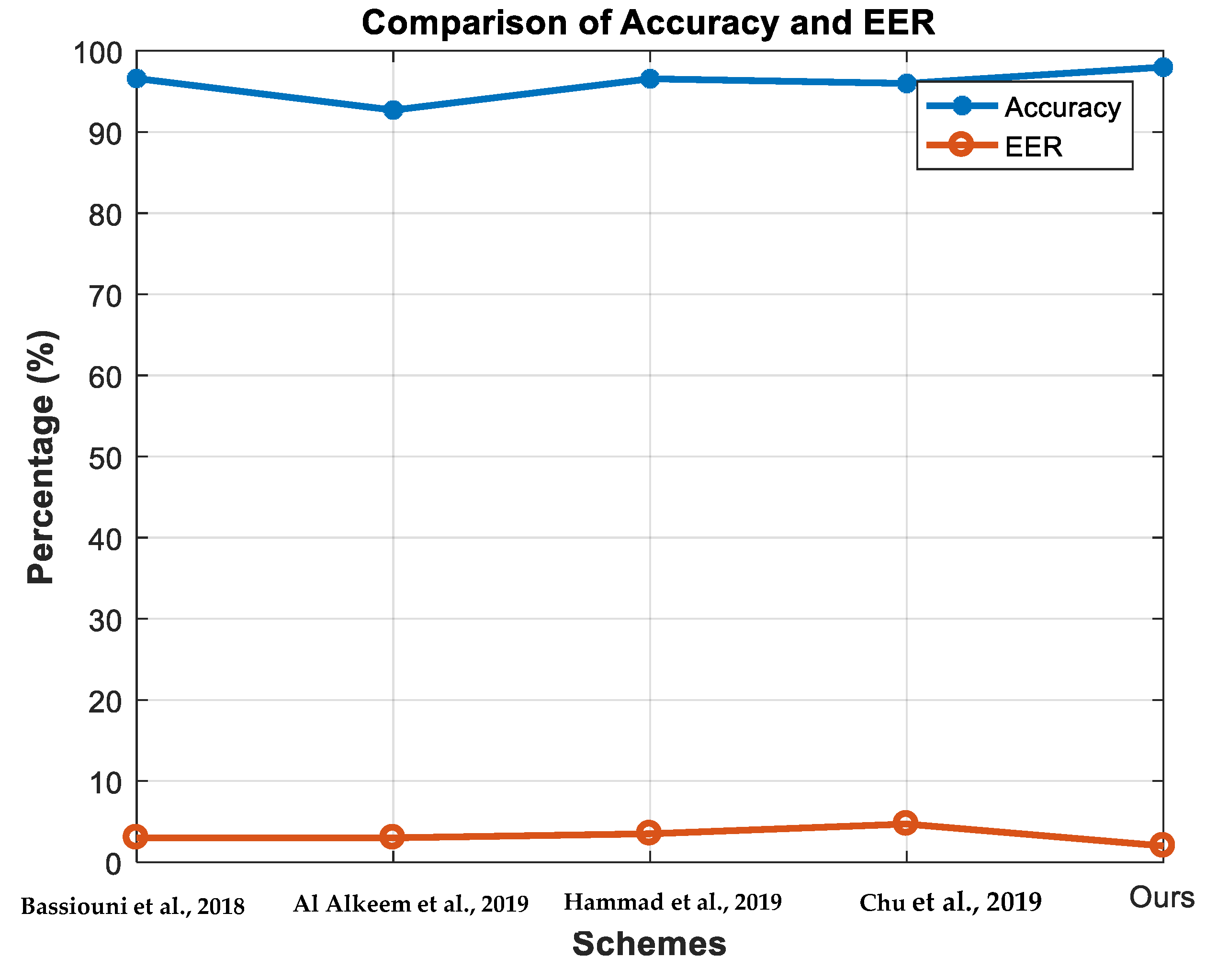
- The performance comparison results proved that the proposed authentication scheme outstands with peer schemes. This proved that it is highly applicable, efficient, and robust.
- The rest of the article is organized as follows: section II unveiling the proposed authentication scheme; section III detailing experimentation, performance evaluation, and comparison with peers; section IV covering the discussion; and, finally, the conclusion in section V.
2. Proposed Authentication Scheme
2.1. Preprocessing
2.2. Feature Extraction
2.3. Bio-Key Generation
| Algorithm 1 Pseudo-code algorithm used for bio-key extraction. |
|
2.4. Template Construction & Store
2.5. Authentication
2.6. Criteria for Authentication
- During the comparison, if a match is found in the template store with accuracy of more than or equal to 80% then it is authenticated
- Otherwise, a person is considered an intruder
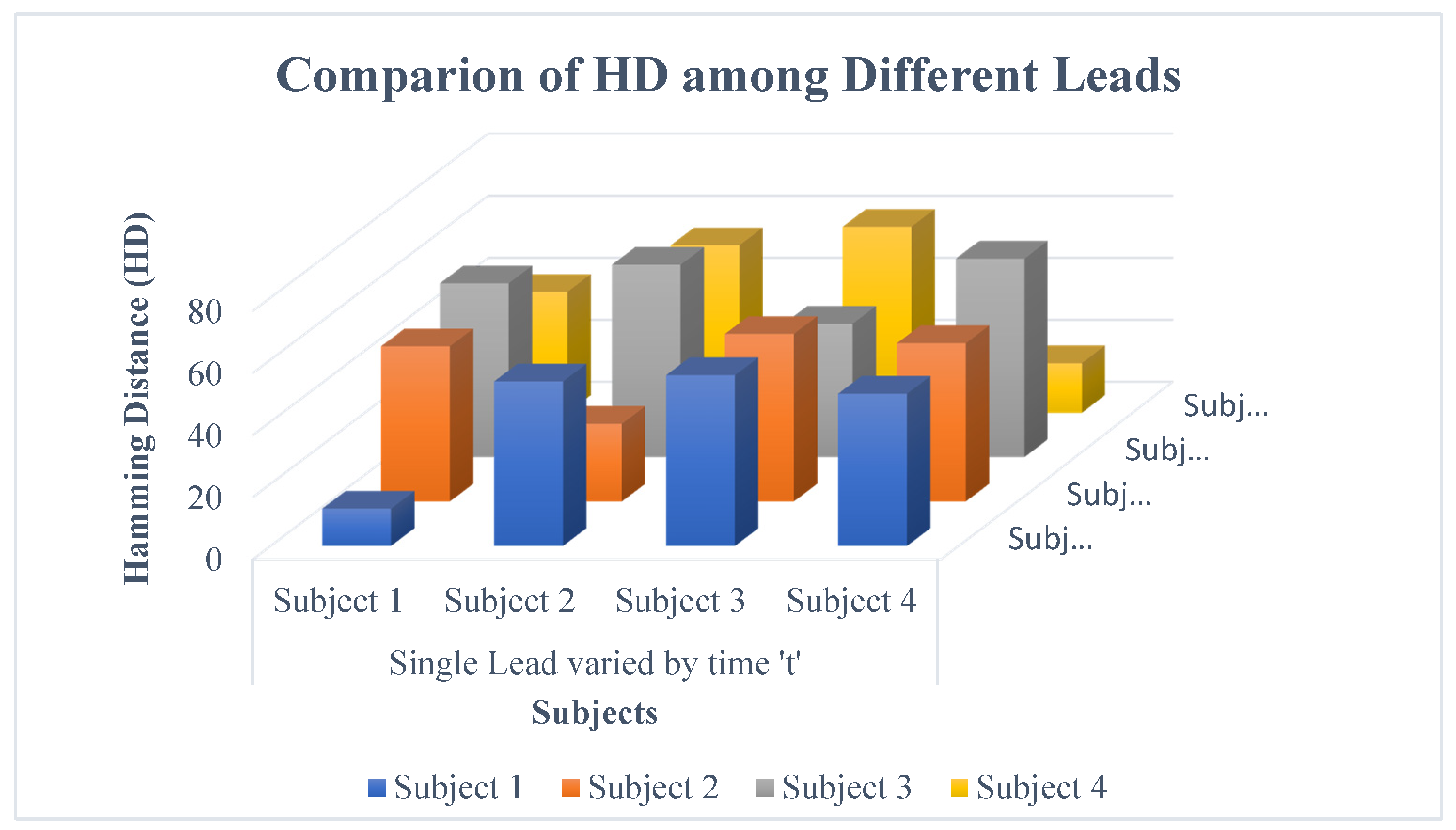
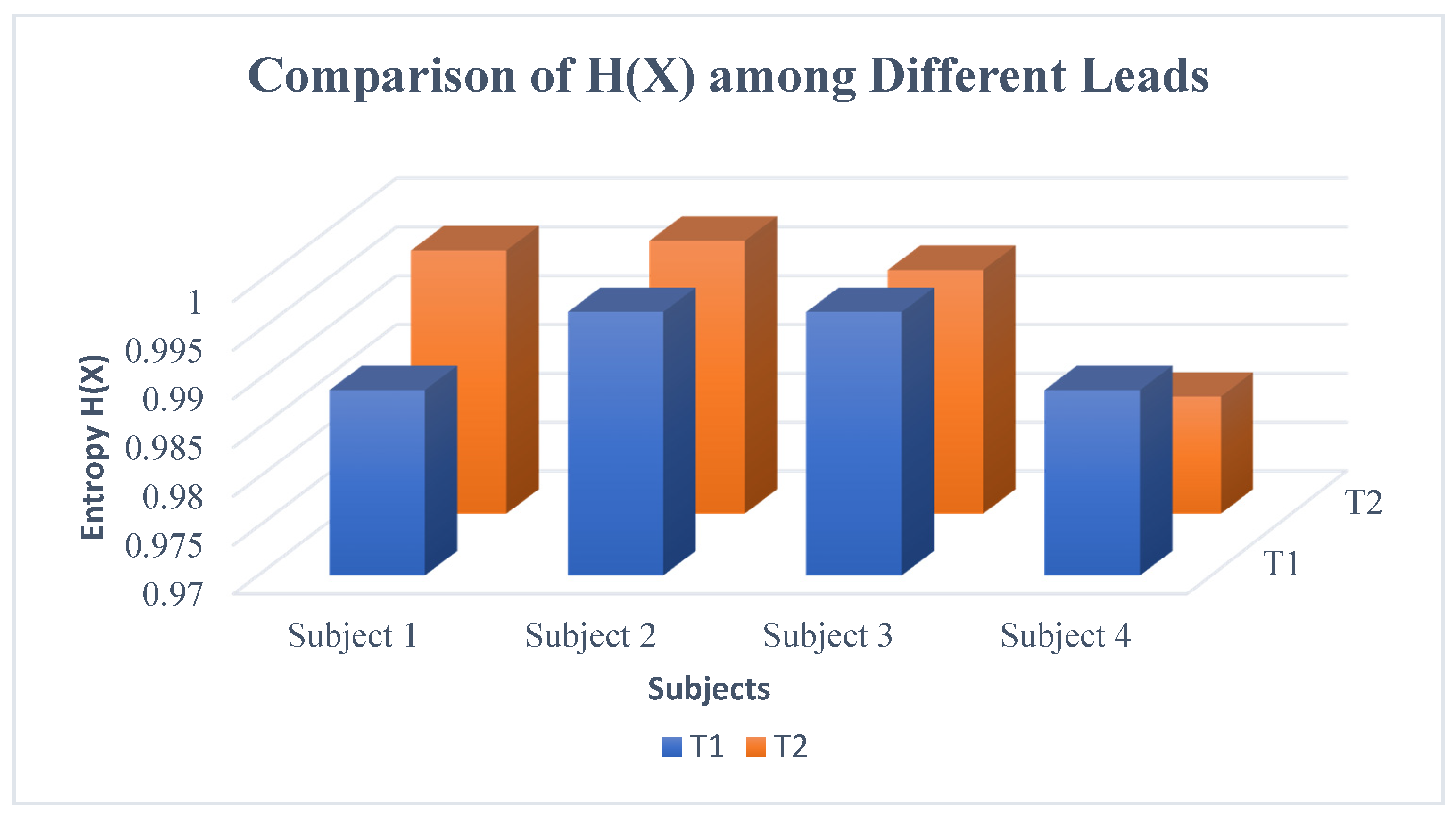
2.7. Performance Evaluation
- Performance accuracy defines the percentage of correct prediction over a total number of testing samples.
- Equal Error Rate (EER): It is utilized for determining the threshold value among FAR and FRR.
3. Experimentation and Results
3.1. Experimental Setup
3.2. ECG Authentication
3.3. Comparison with Peers
4. Discussion
5. Conclusions and Future Direction
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Elshahed, M.A. Personal identity verification based ECG biometric using non-fiducial features. Int. J. Electr. Comput. Eng. 2020, 10, 3007–3013. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Zhang, J.; Li, H.; Li, J. Key Establishment Scheme for Wireless Sensor Networks Based on Polynomial and Random Key Predistribution Scheme. Ad Hoc Netw. 2017, 71, 68–77. [Google Scholar] [CrossRef]
- Ribeiro Pinto, J.; Cardoso, J.S.; Lourenco, A. Evolution, current challenges, and future possibilities in ECG Biometrics. IEEE Access 2018, 6, 34746–34776. [Google Scholar] [CrossRef]
- Teodoro, F.G.S.; Peres, S.M.; Lima, C.A.M. Feature selection for biometrie recognition based on electrocardiogram signals. In Proceedings of the 2017 International Joint Conference on Neural Networks (IJCNN), Anchorage, AK, USA, 14–19 May 2017; pp. 2911–2920. [Google Scholar] [CrossRef]
- Hejazi, M.; Al-Haddad, S.A.R.; Hashim, S.J.; Aziz, A.F.A.; Singh, Y.P. Non-fiducial based ECG biometric authentication using one-class Support Vector Machine. In Proceedings of the 2017 Signal Processing: Algorithms, Architectures, Arrangements, and Applications (SPA), Poznan, Poland, 7 September 2017; pp. 190–194. [Google Scholar] [CrossRef]
- Tobore, I.; Li, J.; Kandwal, A.; Yuhang, L.; Nie, Z.; Wang, L. Statistical and spectral analysis of ECG signal towards achieving non-invasive blood glucose monitoring. BMC Med. Inform. Decis. Mak. 2019, 19, 266. [Google Scholar] [CrossRef] [PubMed]
- Bassiouni, M.M.; El-Dahshan, E.S.A.; Khalefa, W.; Salem, A.M. Intelligent hybrid approaches for human ECG signals identification. Signal Image Video Process. 2018, 12, 941–949. [Google Scholar] [CrossRef]
- Kim, S.K.; Huh, J.H. Artificial neural network blockchain techniques for healthcare system: Focusing on the personal health records. Electronics 2020, 9, 763. [Google Scholar] [CrossRef]
- Al Alkeem, E.; Kim, S.K.; Yeun, C.Y.; Zemerly, M.J.; Poon, K.F.; Gianini, G.; Yoo, P.D. An enhanced electrocardiogram biometric authentication system using machine learning. IEEE Access 2019, 7, 123069–123075. [Google Scholar] [CrossRef]
- Chu, Y.; Shen, H.; Huang, K. ECG Authentication method based on parallel multi-scale one-dimensional residual network with center and margin loss. IEEE Access 2019, 7, 51598–51607. [Google Scholar] [CrossRef]
- Donida Labati, R.; Muñoz, E.; Piuri, V.; Sassi, R.; Scotti, F. Deep-ECG: Convolutional Neural Networks for ECG biometric recognition. Pattern Recognit. Lett. 2019, 126, 78–85. [Google Scholar] [CrossRef]
- Zhao, Z.; Zhang, Y.; Deng, Y.; Zhang, X. ECG authentication system design incorporating a convolutional neural network and generalized S-Transformation. Comput. Biol. Med. 2018, 102, 168–179. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Q.; Zhou, D.; Zeng, X. HeartID: A Multiresolution Convolutional Neural Network for ECG-Based Biometric Human Identification in Smart Health Applications. IEEE Access 2017, 5, 11805–11816. [Google Scholar] [CrossRef]
- Ibtehaz, N.; Chowdhury, M.E.H.; Khandakar, A.; Kiranyaz, S.; Rahman, M.S.; Tahir, A.; Qiblawey, Y.; Rahman, T. EDITH:ECG biometrics aided by Deep learning for reliable Individual auTHentication. ArXiv 2021, e-prints. arXiv:2102.08026. [Google Scholar]
- Hammad, M.; Wang, K. Parallel score fusion of ECG and fingerprint for human authentication based on convolution. Comput. Secur. 2019, 81, 107–122. [Google Scholar] [CrossRef]
- Rehman, Z.U.; Altaf, S.; Iqbal, S. An Efficient Lightweight Key Agreement and Authentication Scheme for WBAN. IEEE Access 2020, 8, 175385–175397. [Google Scholar] [CrossRef]
- Rehman, Z.U.; Altaf, S.; Iqbal, S. Survey of Authentication Schemes for Health Monitoring: A Subset of Cyber Physical System. In Proceedings of the 2019 16th International Bhurban Conference on Applied Sciences and Technology, IBCAST 2019, Islamabad, Pakistan, 8–12 January 2019; pp. 653–660. [Google Scholar]
- Rehman, Z.U.; Altaf, S.; Ahmed, S.; Huda, S.; Al-Shayea, A.M.; Iqbal, S. An Efficient, Hybrid Authentication using ECG and Lightweight Cryptographic Scheme for WBAN. IEEE Access 2021, 9, 133809–133819. [Google Scholar] [CrossRef]
- Salloum, R.; Kuo, C.-C.J. ECG-based biometrics using recurrent neural networks. In Proceedings of the 2017 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 2062–2066. [Google Scholar]
- Kim, S.K.; Yeun, C.Y.; Damiani, E.; Lo, N.W. A machine learning framework for biometric authentication using electrocardiogram. IEEE Access 2019, 7, 94858–94868. [Google Scholar] [CrossRef]
- Hosseinzadeh, M.; Vo, B.; Ghafour, M.Y.; Naghipour, S. Electrocardiogram Signals-Based User Authentication Systems Using Soft Computing Techniques; Springer: Dordrecht, The Netherlands, 2020; Volume 54, ISBN 0123456789. [Google Scholar]
- Aileni, R.M.; Pasca, S.; Florescu, A. EEG-brain activity monitoring and predictive analysis of signals using artificial neural networks. Sensors 2020, 20, 3346. [Google Scholar] [CrossRef] [PubMed]
- Diab, M.O.; Seif, A.; Sabbah, M.; El-Abed, M.; Aloulou, N. A review on ecg-based biometric authentication systems. In Hidden Biometrics; Springer: Berlin/Heidelberg, Germany, 2020; pp. 17–44. [Google Scholar]
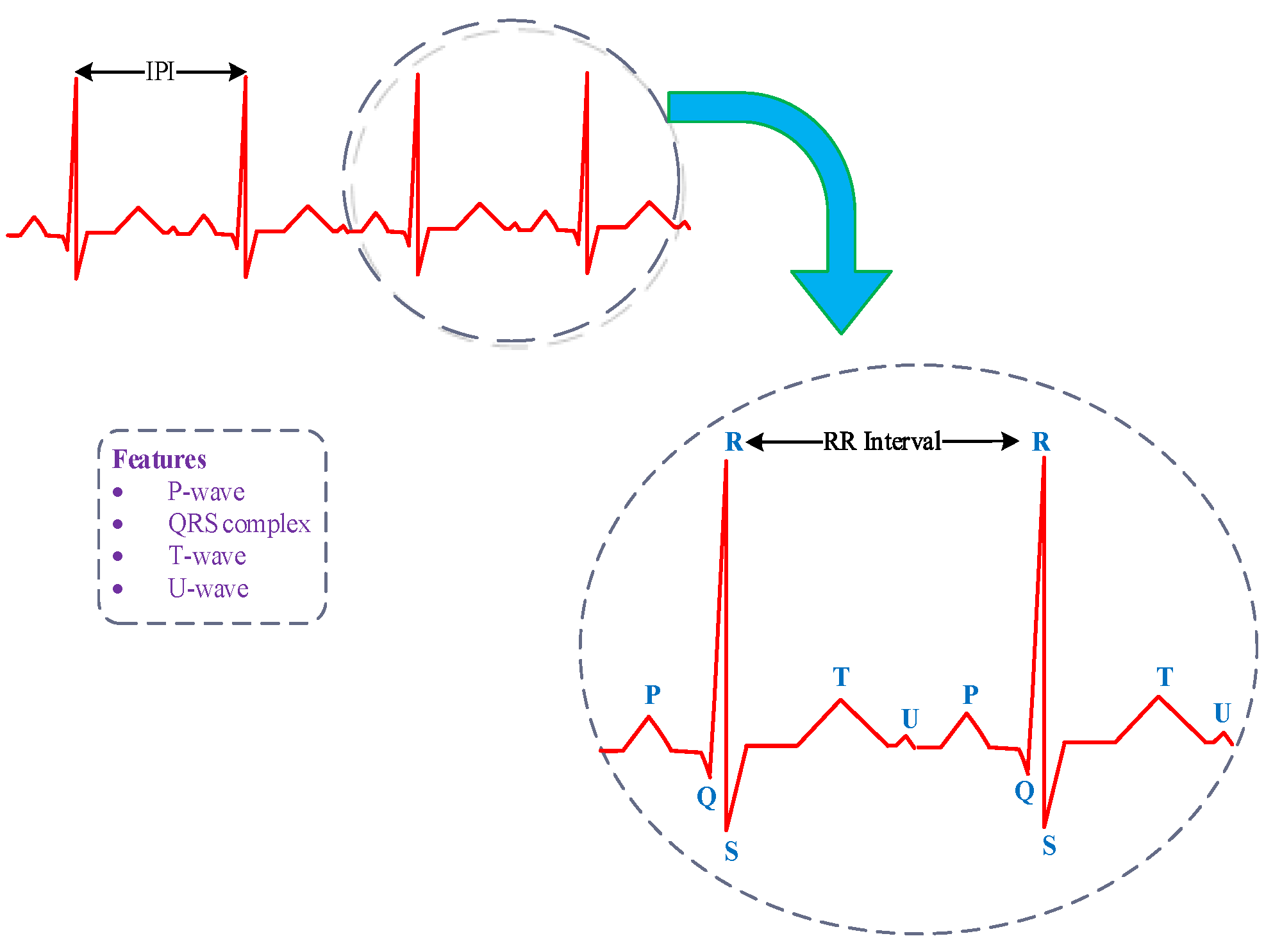
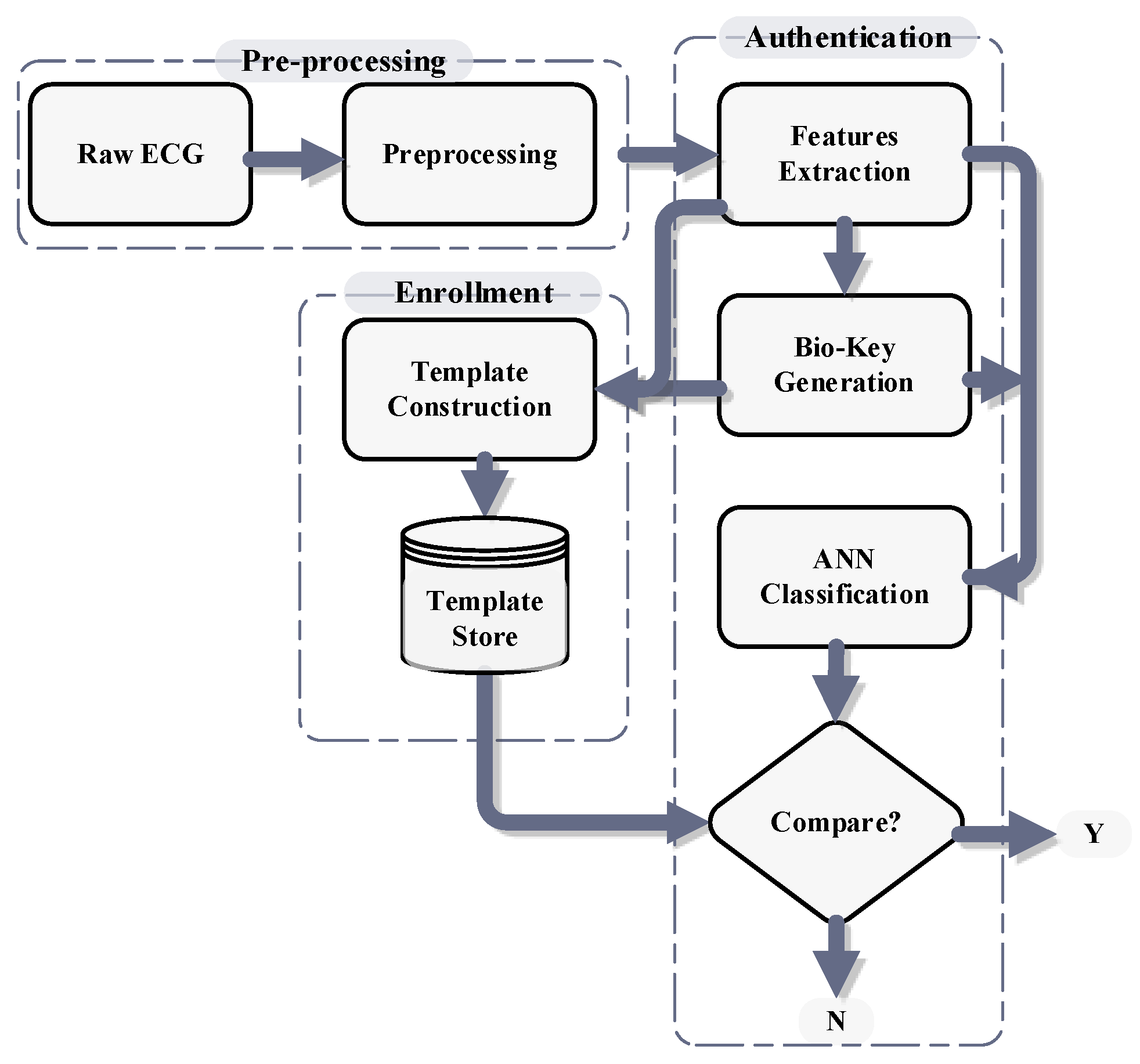
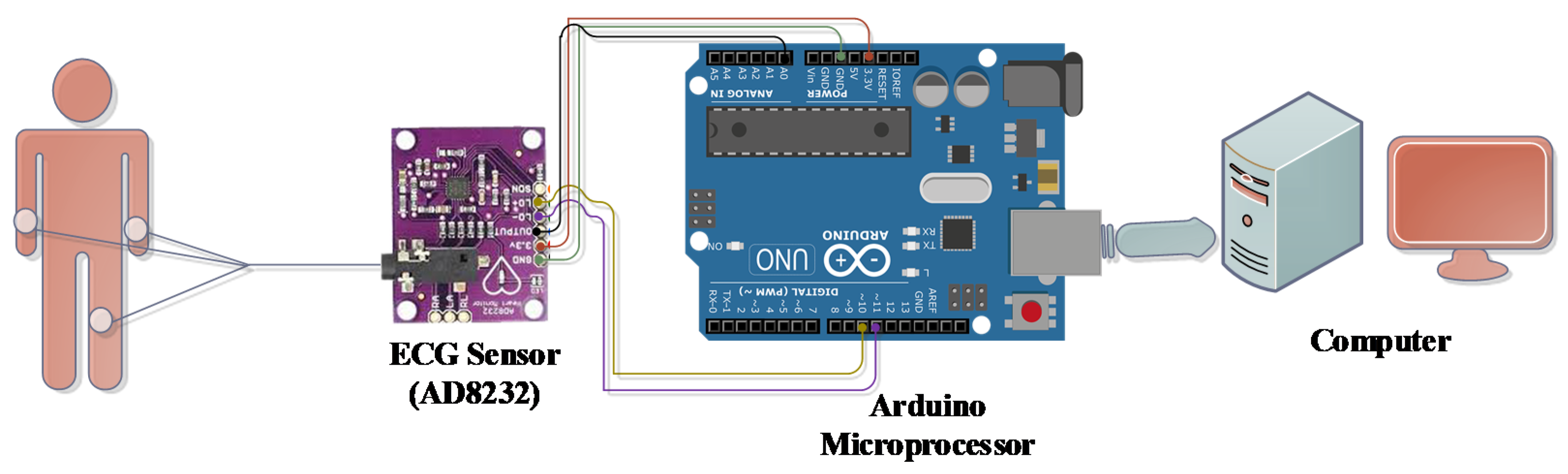

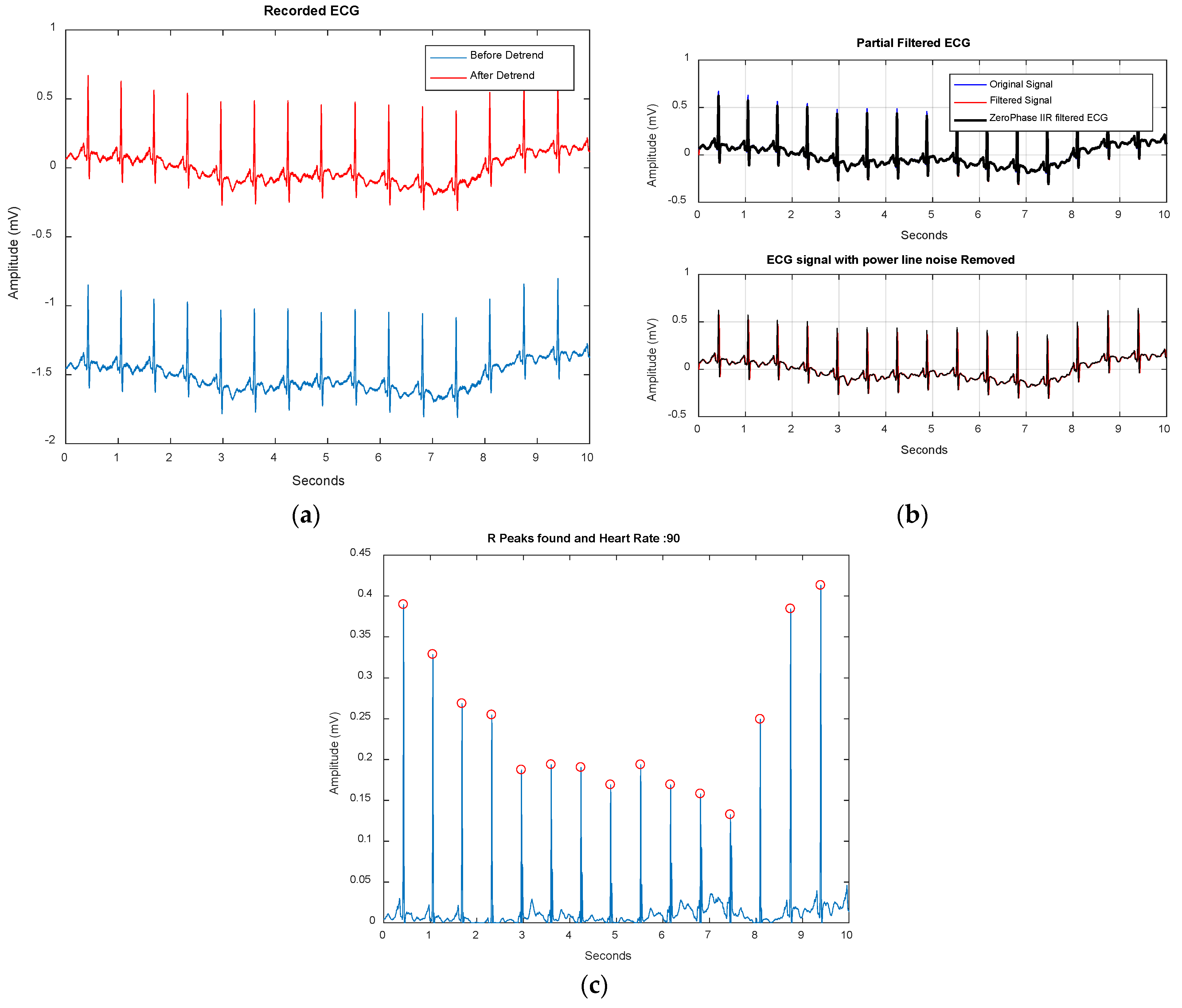
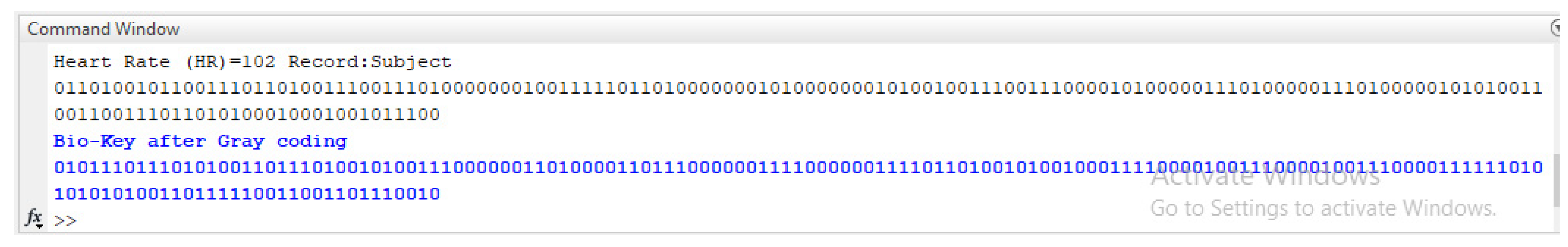
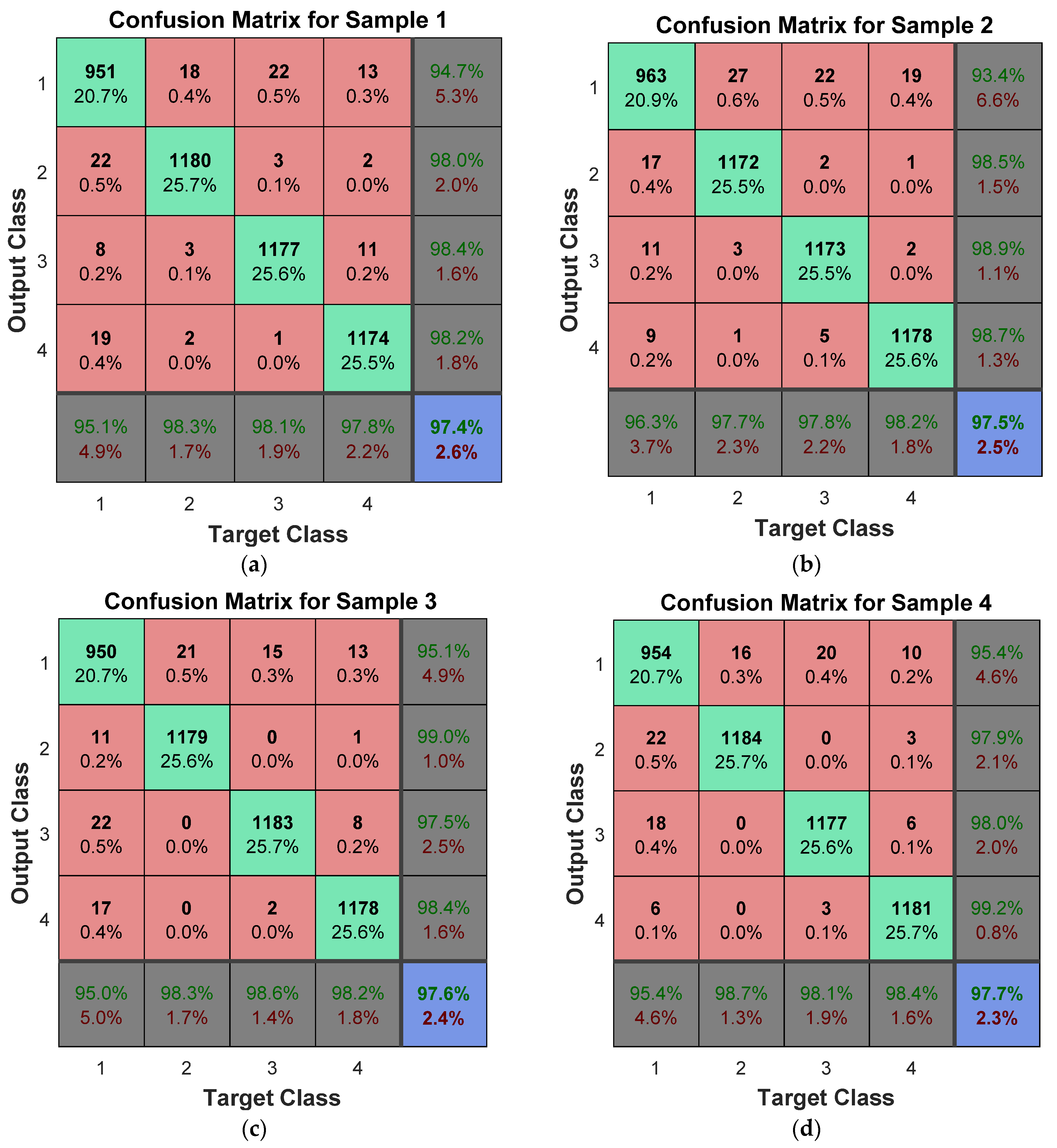
| Samples | Pinter | Average | Kurtosis | Bio-Key |
|---|---|---|---|---|
| S1 | [1 × 18 double] | 5.97 × 10−4 | 47.5186 | 110110101110110110110010010110010010110010010110110100 110011110011010101110111000010110110110010011010011111 |
| S2 | [1 × 16 double] | 4.05 × 10−4 | 47.9453 | 101001011110101101110011101110001000111100001011101010111 11001111101100011001100101010111010101010100010100011001011 011010101010100010000101 |
| S3 | [1 × 18 double] | 5.30 × 10−4 | 87.3044 | 1001110010000110111100010100000001110110100110110110010011010 011000010100101010010011100111001011001 |
| S4 | [1 × 19 double] | 3.18 × 10−4 | 83.3642 | 10011100100010001001111000001001000011101001101010011100100001 00100011000001100110011100100111100001110010011011 |
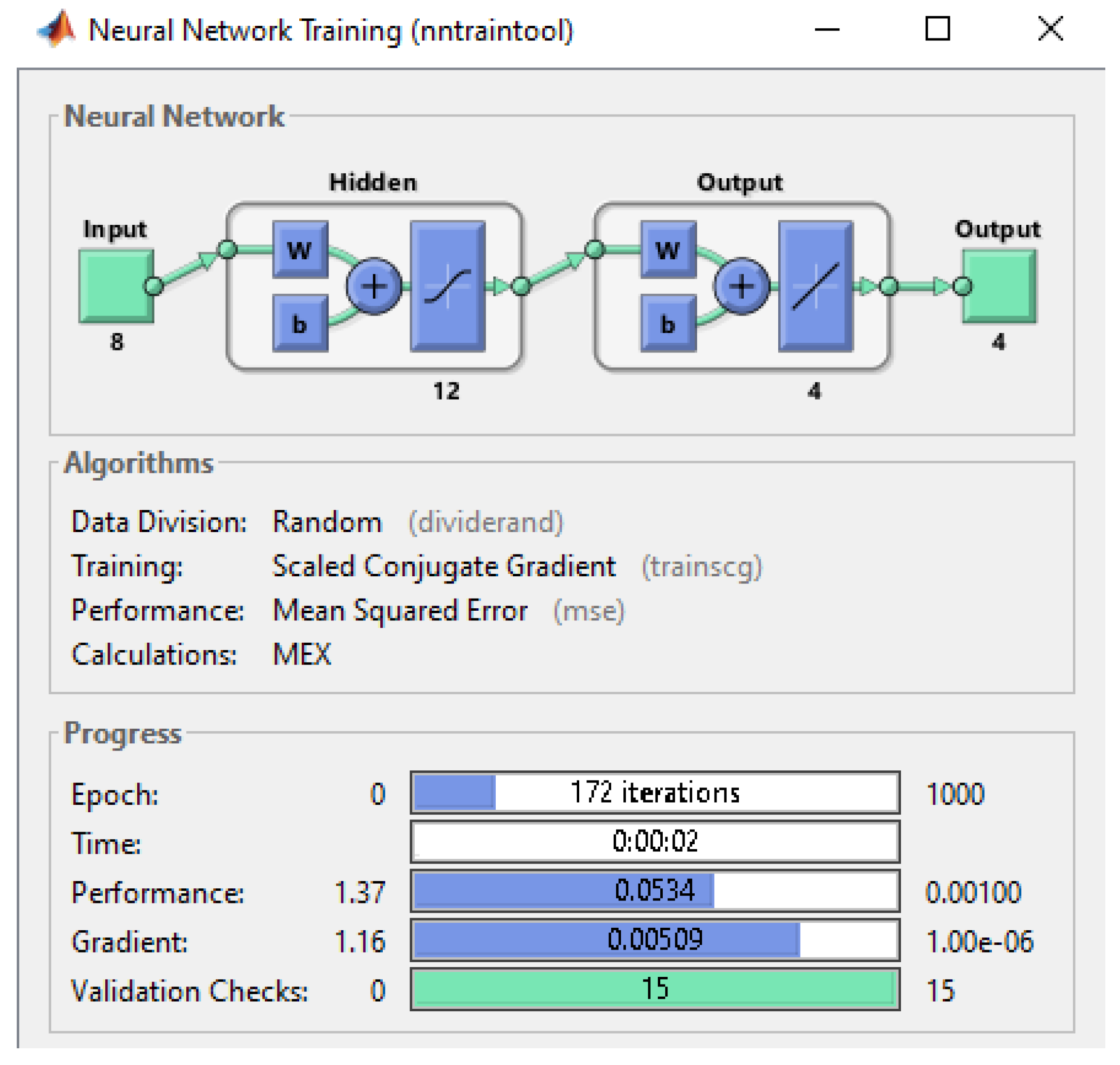
| Arch | Sample | MSE | No. of Epoch | Accuracy | Classification Error |
|---|---|---|---|---|---|
| [4 × 8 × 3] | S1 | 7.79 × 10−2 | 71 | 92.3 | 7.7 |
| S2 | 7.45 × 10−2 | 76 | 92.4 | 7.6 | |
| S3 | 7.99 × 10−2 | 102 | 91.9 | 8.1 | |
| S4 | 7.01 × 10−2 | 65 | 90.2 | 9.8 | |
| [4 × 12 × 3] | S1 | 8.29 × 10−2 | 143 | 97.4 | 2.6 |
| S2 | 9.05 × 10−2 | 186 | 97.5 | 2.5 | |
| S3 | 7.49 × 10−2 | 110 | 97.6 | 2.4 | |
| S4 | 9.291 × 10−2 | 168 | 97.7 | 2.3 | |
| [4 × 15 × 3] | S1 | 7.99 × 10−2 | 405 | 92.9 | 7.1 |
| S2 | 7.15 × 10−2 | 398 | 90.2 | 9.8 | |
| S3 | 6.91 × 10−2 | 312 | 89.1 | 10.9 | |
| S4 | 7.19 × 10−2 | 399 | 91.5 | 8.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, Z.u.; Altaf, S.; Ahmad, S.; Alqahtani, M.; Huda, S.; Iqbal, S. Advanced Authentication Scheme with Bio-Key Using Artificial Neural Network. Sustainability 2022, 14, 3950. https://doi.org/10.3390/su14073950
Rehman Zu, Altaf S, Ahmad S, Alqahtani M, Huda S, Iqbal S. Advanced Authentication Scheme with Bio-Key Using Artificial Neural Network. Sustainability. 2022; 14(7):3950. https://doi.org/10.3390/su14073950
Chicago/Turabian StyleRehman, Zia ur, Saud Altaf, Shafiq Ahmad, Mejdal Alqahtani, Shamsul Huda, and Sofia Iqbal. 2022. "Advanced Authentication Scheme with Bio-Key Using Artificial Neural Network" Sustainability 14, no. 7: 3950. https://doi.org/10.3390/su14073950
APA StyleRehman, Z. u., Altaf, S., Ahmad, S., Alqahtani, M., Huda, S., & Iqbal, S. (2022). Advanced Authentication Scheme with Bio-Key Using Artificial Neural Network. Sustainability, 14(7), 3950. https://doi.org/10.3390/su14073950









