SAKAP: SGX-Based Authentication Key Agreement Protocol in IoT-Enabled Cloud Computing
Abstract
:1. Introduction
- (1)
- We propose a lightweight AKA in the IoT-enabled cloud computing environment. In our protocol, the user, cloud server, and control server achieve mutual authentication, and the session key is successfully established for communication.
- (2)
- We first introduce SGX into an IoT-enabled cloud computing environment and use it on the cloud server and control server. Because SGX has limitations in both storage and computation, we only use it to store the shared key. According to the safety features of SGX, even if an attacker can access the data in memory, he/she cannot obtain the shared key in SGX. Thus, privileged insider attacks are invalid for our protocol.
- (3)
- We use the real-or-random (ROR) model and ProVerif tool to verify the security of the proposed protocol, and informal security analysis shows that the protocol protects against known attacks.
- (4)
- Finally, we compare the security and performance with current protocols, and the results show that our protocol ensures greater security under a similar efficiency.
2. Related Work
3. Proposed Protocol: SAKAP
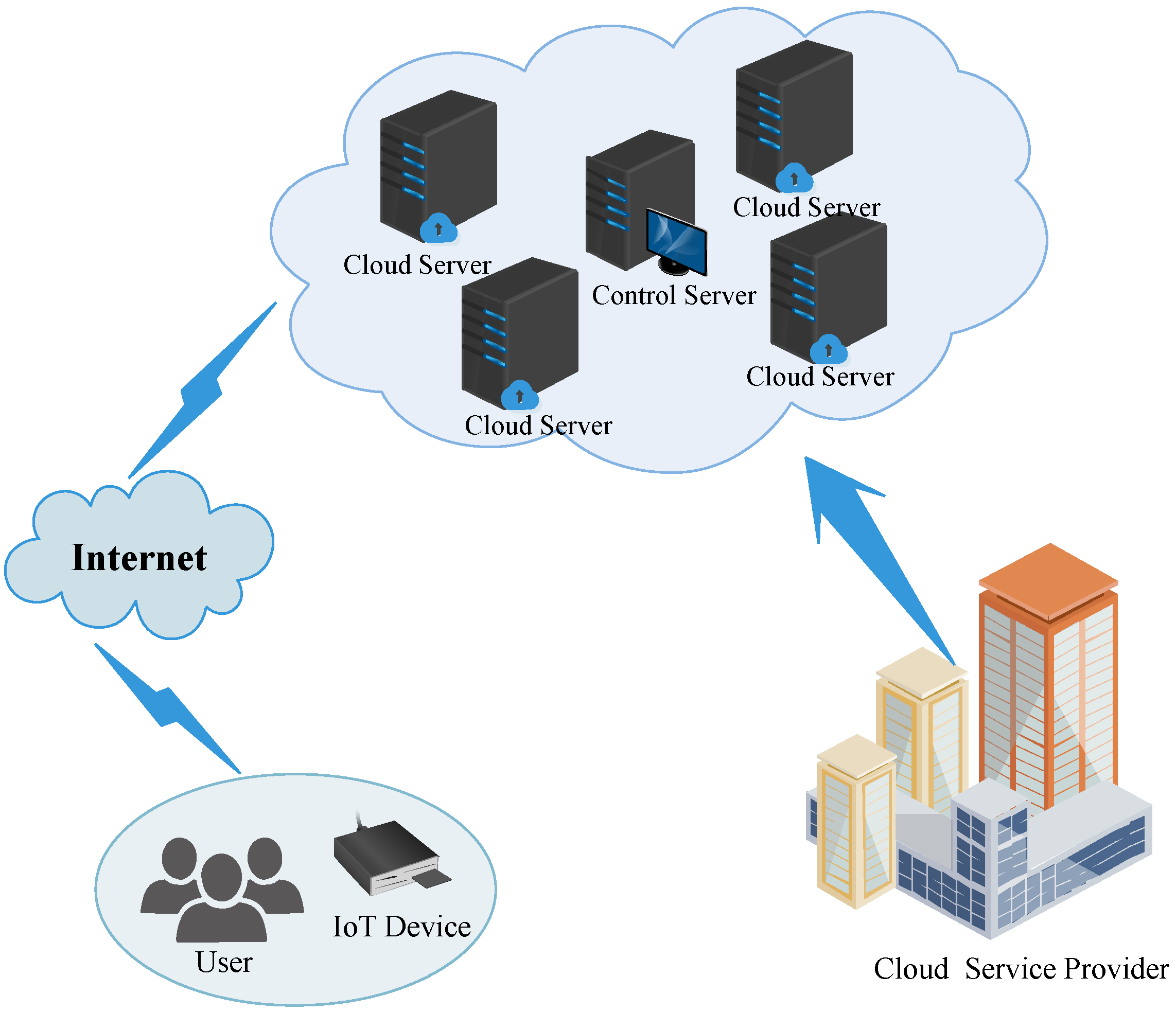
3.1. System Model
- (1)
- User (): refers to people who intend to use cloud computing services in the IoT-enabled cloud computing environment. Only legitimate can use cloud computing services through IoT devices.
- (2)
- Cloud server (): is deployed in the area to provide services to process and store the data of IoT devices. is a semi-trusted entity; it can misbehave, but cannot collaborate with other participants. In addition, has powerful storage capacity and computing power.
- (3)
- Control server (): is the control center for the cloud service provider to manage the in the service area. is a semi-trusted entity; it can misbehave, but cannot collaborate with other participants. Furthermore, is in charge of registration and authentication.
3.2. Concrete Protocol
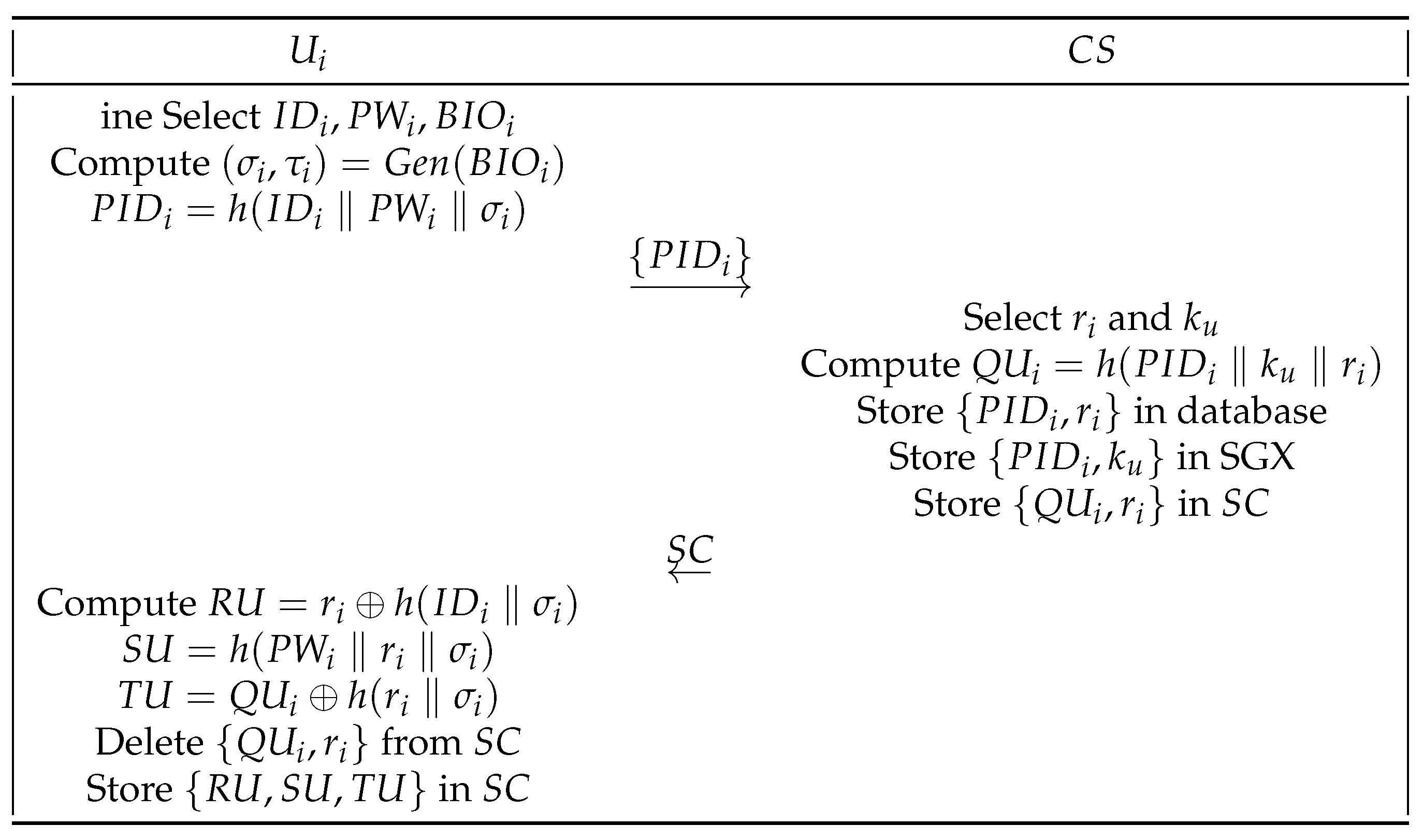
3.2.1. Registration Phase
- (1)
- Initially, selects , , and . Next, computes and = and transmits to through a secure channel.
- (2)
- When receives the , it chooses a random number and a shared key , to compute . Next, stores in its database, in SGX, and in the smart card . Finally, transmits to via the secure channel.
- (3)
- Upon receiving the from , calculates , , . Finally, deletes from and stores in .
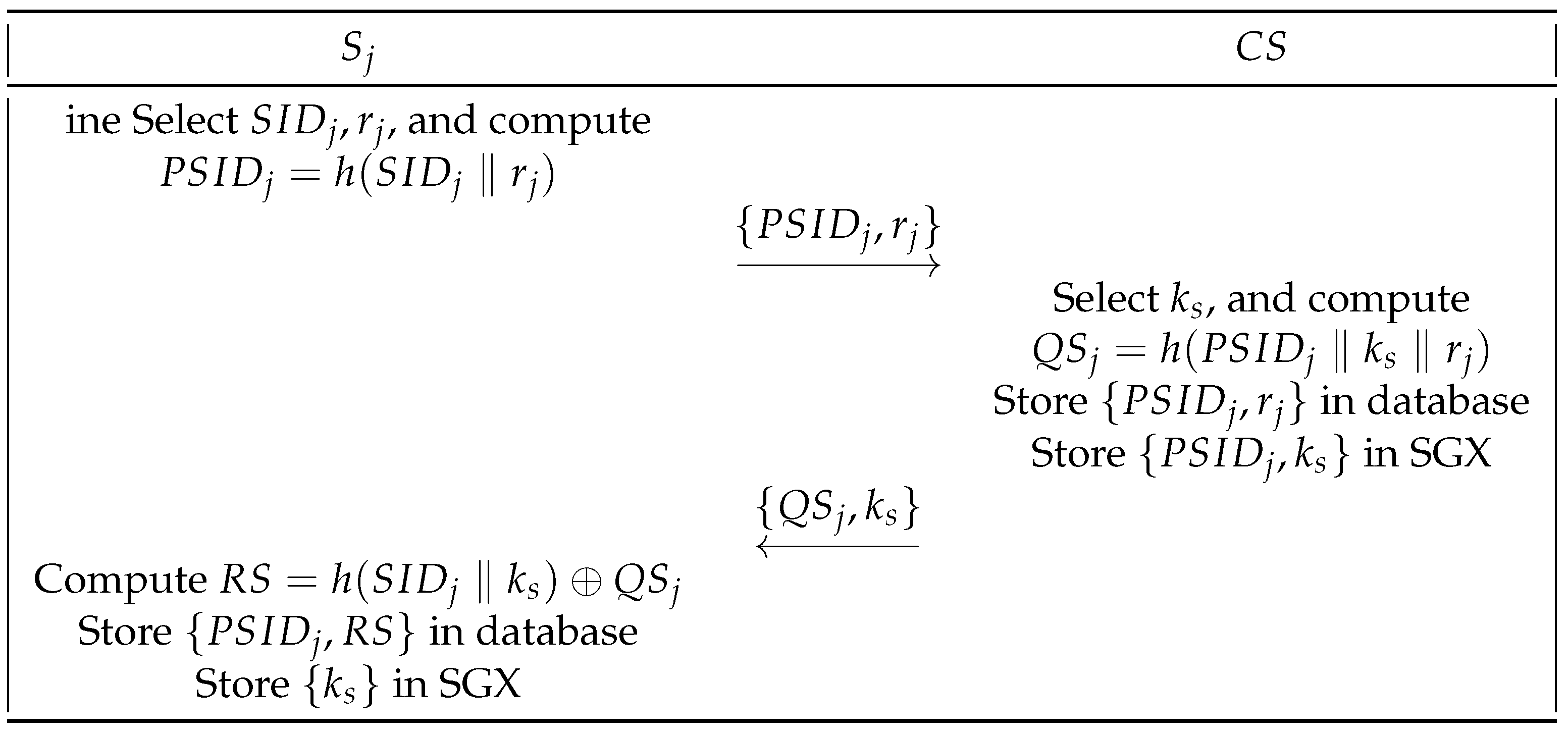
- (1)
- First, selects and a random number . Next, computes and transmits to via the secure channel.
- (2)
- Upon receiving the , first selects a shared key and computes the value . stores in its database and stores in SGX. Then, transmits to through the secure channel.
- (3)
- Upon receiving , computes the value . Finally, stores in the database and stores in SGX.
3.2.2. Login and Key Agreement Phase
- (1)
- First, inputs , , and . Subsequently, computes , , , and checks . If it is equal, logs in successfully. Otherwise, the device rejects the login of . Next, computes , generates a random number , and chooses an , which is the private cloud server ’s identity. Then, computes , , and . Finally, retrieves the current timestamp and sends the message to through the public channel.
- (2)
- Upon receiving , checks the freshness of . Then, sends to the security interface of SGX and invokes the interface. The interface finds the and uses it to calculate . Then, SGX sends to through the interface. Next, selects a random number and computes , . Finally, retrieves the current timestamp and transmits the message to via the public channel.
- (3)
- When receives the , it first verifies the freshness of . Then, retrieves in the database using and sends to the security interface of SGX. Then, SGX invokes the interface and uses to match , then it computes . Then, SGX sends to through the interface. Next, computes , , and . Then, checks whether . If it holds, retrieves in the database using and sends to the security interface of SGX. Then, SGX invokes the interface and uses to match , then it computes . Then, SGX sends to through the interface. Next, computes , and checks the correctness of . If it holds, authenticates the . Otherwise, rejects the session. Further, selects a random number and calculates , , , and . Finally, generates the current timestamp and transmits the message to through the public channel.
- (4)
- Upon receiving the , first checks the freshness of . Then, computes , , and . Then, checks . If , retrieves the current timestamp and sends the message to .
- (5)
- When receives the , it first verifies the freshness of . Then, calculates , and . Finally, checks . If it holds, authenticates the , and the entire authentication process is achieved.
4. Security Analysis
4.1. Formal Security Analysis
- (1)
- has the ability to eavesdrop, intercept, tamper with, and replay messages sent between entities over a public channel.
- (2)
- can be a malicious insider in the or and has access to the database’s information.
- (3)
- can steal the user’s and use power analysis [49] to extract information from the .
- (4)
- can affect the protocol’s security by obtaining random numbers.
4.1.1. Security Model
- (1)
- : executing this query can intercept the messages transmitted over the public channel between , , and , where .
- (2)
- : When executes the query, sends an to , then receives a response from the .
- (3)
- : Through executing this query, can obtain the hash value of the after the input .
- (4)
- : can obtain some private values by executing this query, such as the long-term private key, temporary value, and parameters in the .
- (5)
- : When performs this operation, he/she flips the coin c. If , can obtain a random value with the same length as . Otherwise, if , can obtain the correct .
4.2. Informal Security Analysis
4.2.1. Replay Attacks
4.2.2. Privileged Insider Attacks
4.2.3. Man-in-the-Middle Attacks
4.2.4. User Impersonation Attacks
4.2.5. Cloud Sever Impersonation Attacks
4.2.6. Anonymity and Untraceability
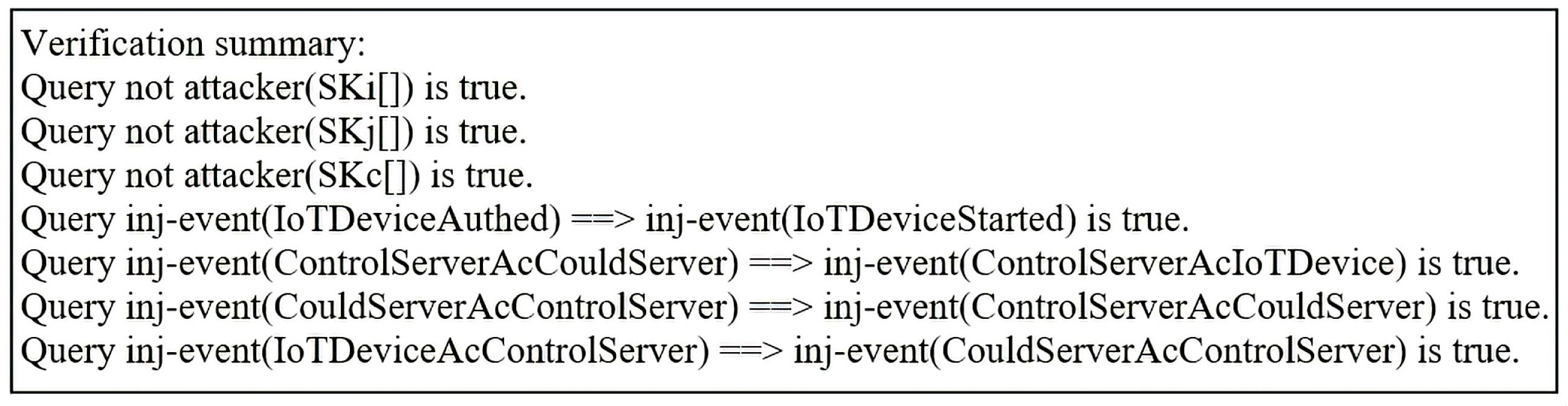
4.3. ProVerif
5. Security and Performance Comparisons
5.1. Security Comparisons
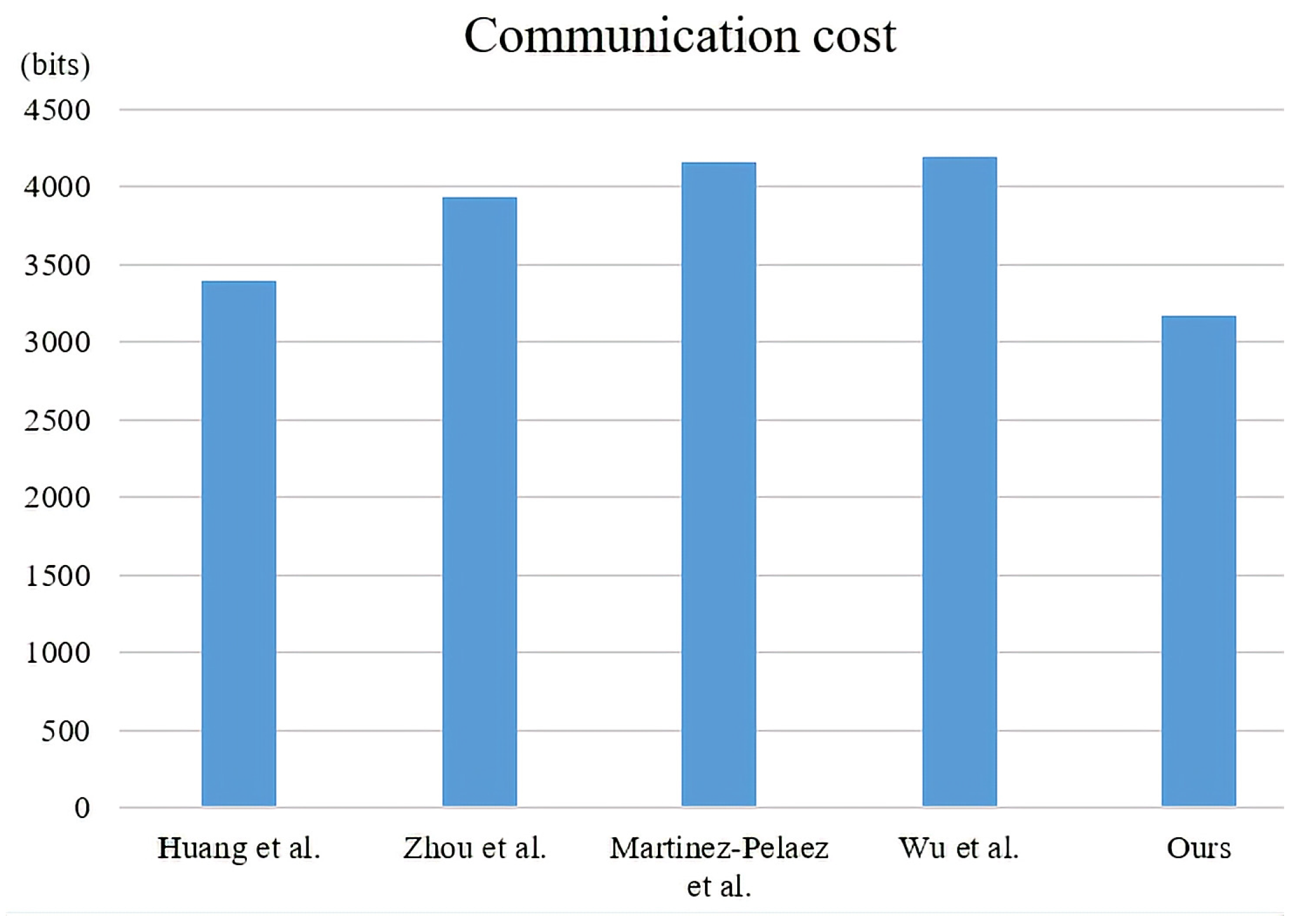
5.2. Performance Comparisons
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| SGX | Software guard extensions |
| ROR | Real-or-random |
| AKA | Authentication and key agreement |
References
- Goudos, S.K.; Dallas, P.I.; Chatziefthymiou, S.; Kyriazakos, S. A survey of IoT key enabling and future technologies: 5G, mobile IoT, sematic web and applications. Wirel. Pers. Commun. 2017, 97, 1645–1675. [Google Scholar] [CrossRef]
- Xue, X.; Wu, X.; Jiang, C.; Mao, G.; Zhu, H. Integrating sensor ontologies with global and local alignment extractions. Wirel. Commun. Mob. Comput. 2021, 2021, 6625184. [Google Scholar] [CrossRef]
- Huang, X.; Xiong, H.; Chen, J.; Yang, M. Efficient revocable storage attribute-based encryption with arithmetic span programs in cloud-assisted internet of things. IEEE Trans. Cloud Comput. 2021. [Google Scholar] [CrossRef]
- Shen, S.; Yang, Y.; Liu, X. Toward data privacy preservation with ciphertext update and key rotation for IoT. Concurr. Comput. Pract. Exp. 2021, e6729. [Google Scholar] [CrossRef]
- Meng, Z.; Pan, J.S.; Tseng, K.K. PaDE: An enhanced Differential Evolution algorithm with novel control parameter adaptation schemes for numerical optimization. Knowl. Based Syst. 2019, 168, 80–99. [Google Scholar] [CrossRef]
- Xue, X.; Zhang, J. Matching large-scale biomedical ontologies with central concept based partitioning algorithm and adaptive compact evolutionary algorithm. Appl. Soft Comput. 2021, 106, 107343. [Google Scholar] [CrossRef]
- Liu, G.; Zhu, Y.; Xu, S.; Chen, Y.C.; Tang, H. PSO-based power-driven X-routing algorithm in semiconductor design for predictive intelligence of IoT applications. Appl. Soft Comput. 2022, 114, 108114. [Google Scholar] [CrossRef]
- He, Z.; Yu, C. Clustering stability-based evolutionary k-means. Soft Comput. 2019, 23, 305–321. [Google Scholar] [CrossRef]
- Chaudhry, S.A. Combating identity de-synchronization: An improved lightweight symmetric key based authentication scheme for IoV. J. Netw. Intell. 2021, 6, 656–667. [Google Scholar]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020, 19, 2089–2104. [Google Scholar] [CrossRef]
- Wu, T.; Guo, X.; Chen, Y.; Kumari, S.; Chen, C. Amassing the security: An enhanced authentication protocol for drone communications over 5G networks. Drones 2021, 6, 10. [Google Scholar] [CrossRef]
- Luo, Y.; Zheng, W.M.; Chen, Y.C. An anonymous authentication and key exchange protocol in smart grid. J. Netw. Intell. 2021, 6, 206–215. [Google Scholar]
- Huang, H.; Lu, S.; Wu, Z.; Wei, Q. An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 150. [Google Scholar] [CrossRef]
- Wu, T.Y.; Wang, T.; Lee, Y.Q.; Zheng, W.; Kumari, S.; Kumar, S. Improved authenticated key agreement scheme for fog-driven IoT healthcare system. Secur. Commun. Netw. 2021, 2021, 6658041. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Guo, W.; Liu, X.; Chang, V. Privacy-preserving fusion of IoT and big data for e-health. Future Gener. Comput. Syst. 2018, 86, 1437–1455. [Google Scholar] [CrossRef]
- Mushtaq, M.F.; Akram, U.; Khan, I.; Khan, S.N.; Shahzad, A.; Ullah, A. Cloud computing environment and security challenges: A review. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 183–195. [Google Scholar]
- Wu, T.Y.; Meng, Q.; Kumari, S.; Zhang, P. Rotating behind Security: A Lightweight Authentication Protocol Based on IoT-Enabled Cloud Computing Environments. Sensors 2022, 22, 3858. [Google Scholar] [CrossRef]
- Chen, X.; Zhang, J.; Lin, B.; Chen, Z.; Wolter, K.; Min, G. Energy-efficient offloading for DNN-based smart IoT systems in cloud-edge environments. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 683–697. [Google Scholar] [CrossRef]
- Zhang, J.; Li, M.; Chen, Z.; Lin, B. Computation offloading for object-oriented applications in a UAV-based edge-cloud environment. J. Supercomput. 2022, 78, 10829–10853. [Google Scholar] [CrossRef]
- Kang, B.; Han, Y.; Qian, K.; Du, J. Analysis and improvement on an authentication protocol for IoT-enabled devices in distributed cloud computing environment. Math. Probl. Eng. 2020, 2020, 1970798. [Google Scholar] [CrossRef]
- Iqbal, U.; Tandon, A.; Gupta, S.; Yadav, A.R.; Neware, R.; Gelana, F.W. A Novel Secure Authentication Protocol for IoT and Cloud Servers. Wirel. Commun. Mob. Comput. 2022, 2022, 7707543. [Google Scholar] [CrossRef]
- Amin, R.; Kumar, N.; Biswas, G.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Martínez-Peláez, R.; Toral-Cruz, H.; Parra-Michel, J.R.; García, V.; Mena, L.J.; Félix, V.G.; Ochoa-Brust, A. An enhanced lightweight IoT-based authentication scheme in cloud computing circumstances. Sensors 2019, 19, 2098. [Google Scholar] [CrossRef]
- Costan, V.; Devadas, S. Intel SGX Explained. Cryptology ePrint Archive, 2016. Available online: https://ia.cr/2016/086 (accessed on 21 February 2017).
- Liu, X.; Guo, Z.; Ma, J.; Song, Y. A secure authentication scheme for wireless sensor networks based on DAC and Intel SGX. IEEE Internet Things J. 2021, 9, 3533–3547. [Google Scholar] [CrossRef]
- Wu, T.Y.; Guo, X.; Chen, Y.C.; Kumari, S.; Chen, C.M. SGXAP: SGX-Based Authentication Protocol in IoV-Enabled Fog Computing. Symmetry 2022, 14, 1393. [Google Scholar] [CrossRef]
- Jain, P.; Desai, S.J.; Shih, M.W.; Kim, T.; Kim, S.M.; Lee, J.H.; Choi, C.; Shin, Y.; Kang, B.B.; Han, D. OpenSGX: An Open Platform for SGX Research. In Proceedings of the NDSS, San Diego, CA, USA, 21–24 February2016; Volume 16, pp. 21–24. [Google Scholar]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar]
- Liu, H.; Ning, H.; Xiong, Q.; Yang, L.T. Shared authority based privacy-preserving authentication protocol in cloud computing. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 241–251. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Khan, M.K.; Wang, L.; Shen, J. Efficient privacy-aware authentication scheme for mobile cloud computing services. IEEE Syst. J. 2016, 12, 1621–1631. [Google Scholar] [CrossRef]
- Kumar, V.; Jangirala, S.; Ahmad, M. An efficient mutual authentication framework for healthcare system in cloud computing. J. Med Syst. 2018, 42, 142. [Google Scholar] [CrossRef] [PubMed]
- G Lopes, A.P.; Gondim, P.R. Mutual authentication protocol for D2D communications in a cloud-based e-health system. Sensors 2020, 20, 2072. [Google Scholar] [CrossRef]
- Wang, F.; Xu, G.; Xu, G.; Wang, Y.; Peng, J. A robust IoT-based three-factor authentication scheme for cloud computing resistant to session key exposure. Wirel. Commun. Mob. Comput. 2020, 2020, 3805058. [Google Scholar] [CrossRef]
- Yu, S.; Park, K.; Park, Y. A secure lightweight three-factor authentication scheme for IoT in cloud computing environment. Sensors 2019, 19, 3598. [Google Scholar] [CrossRef]
- Wu, H.L.; Chang, C.C.; Zheng, Y.Z.; Chen, L.S.; Chen, C.C. A Secure IoT-Based Authentication System in Cloud Computing Environment. Sensors 2020, 20, 5604. [Google Scholar] [CrossRef]
- Fisch, B.; Vinayagamurthy, D.; Boneh, D.; Gorbunov, S. Iron: Functional encryption using Intel SGX. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 765–782. [Google Scholar] [CrossRef]
- Sun, H.; Xiao, S. DNA-X: Dynamic network authentication using SGX. In Proceedings of the 2nd International Conference on Cryptography, Security and Privacy, Guiyang, China, 16–19 March 2018; pp. 110–115. [Google Scholar] [CrossRef]
- Condé, R.C.; Maziero, C.A.; Will, N.C. Using Intel SGX to protect authentication credentials in an untrusted operating system. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 158–163. [Google Scholar] [CrossRef]
- Song, T.; Wang, W.; Lang, F.; Ouyang, W.; Wang, Q.; Lin, J. P2A: Privacy Preserving Anonymous Authentication Based on Blockchain and SGX. In Proceedings of the International Conference on Information Security and Cryptology, Guangzhou, China, 11–14 December 2020; Springer: Berlin/Heidelberg, Germany, 2020; Volume 12612, pp. 257–276. [Google Scholar]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3386, pp. 65–84. [Google Scholar]
- Wu, T.Y.; Meng, Q.; Yang, L.; Guo, X.; Kumari, S. A provably secure lightweight authentication protocol in mobile edge computing environments. J. Supercomput. 2022, 78, 13893–13914. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Blanchet, B. An efficient cryptographic protocol verifier based on prolog rules. In Proceedings of the CSFW; Citeseer: Princeton, NJ, USA, 2001; Volume 1, pp. 82–96. [Google Scholar]
- Wu, T.Y.; Lee, Z.; Yang, L.; Luo, J.N.; Tso, R. Provably secure authentication key exchange scheme using fog nodes in vehicular ad hoc networks. J. Supercomput. 2021, 77, 6992–7020. [Google Scholar] [CrossRef]
- Wang, J.; Hao, S.; Li, Y.; Fan, C.; Wang, J.; Han, L.; Hong, Z.; Hu, H. Challenges towards protecting vnf with sgx. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Tempe, AZ, USA, 21 March 2018; pp. 39–42. [Google Scholar] [CrossRef]





| Notations | Description |
|---|---|
| i-th user | |
| Identity of | |
| Pseudo-identity of and | |
| Password and biometric of | |
| j-th cloud server | |
| Identity of | |
| The control server | |
| Shared key between and | |
| Shared key between and | |
| Session key | |
| Timestamp | |
| Fuzzy generator/reproduction function | |
| Secure hash function |
| Query | Description |
|---|---|
| For a query , start), suppose selects , and , and compute , , in a normal state. Then, the query returns the output . | |
| On a query , suppose is in a normal state and performs the following operations: computes , and selects ; then, computes . The query is answered by . | |
| On a query , upon receiving the send query message (), computes and checks . If it is equal, then it computes and checks . If it is equal, it generates and computes . Then, returns the output . | |
| For a query , suppose computes , and checks in a normal state. If holds, it selects . Then, the query returns the output . | |
| For a query ), upon receiving the send query message (), computes , and checks . If is incorrect, the query process is terminated. Finally, accepts and terminates. | |
| We proceed with the send query for the query as follows. ⟵(, start), ()⟵( , ⟵(, ⟵(. The query is answered with transcripts ,(),, and (). | |
| For a query, if the query is executed and a record () appears in the query, is returned. Otherwise, an element s is selected, and () is added to the list and returns s. | |
| For a , if the is accepted, executing the query returns the parameters in . | |
| The coin c is flipped; if , return a random value with the same length as ; otherwise, return the correct . |
| Attack Methods | Huang et al. [13] | Zhou et al. [23] | Martinez-Pelaez et al. [24] | Wu et al. [40] | Ours |
|---|---|---|---|---|---|
| S1 | √ | √ | × [39] | √ | √ |
| S2 | √ | √ | × [39] | √ | √ |
| S3 | √ | × [38] | √ | √ | √ |
| S4 | √ | √ | × [39] | √ | √ |
| S5 | √ | × [38] | √ | √ | √ |
| S6 | √ | × [38] | × [39] | √ | √ |
| S7 | √ | √ | × [39] | √ | √ |
| MI 8 | Lenovo Desktop Computer | Lenovo Laptop | |
|---|---|---|---|
| Operating System | Android system | Windows 10 | Windows 10 |
| CPU | Qualcomm Snapdragon 845 | Intel(R) Core(TM) i5-9500 CPU @ 3.00 GHz | Intel(R) Core(TM) i7-6700HQ CPU @ 2.60 GHz |
| Running memory | 6 GB | 16 GB | 8 GB |
| Symmetric key encryption/decryption | 0.2554 ms | 0.1385 ms | 0.1874 ms |
| Hash function | 0.0045 ms | 0.0026 ms | 0.0035 ms |
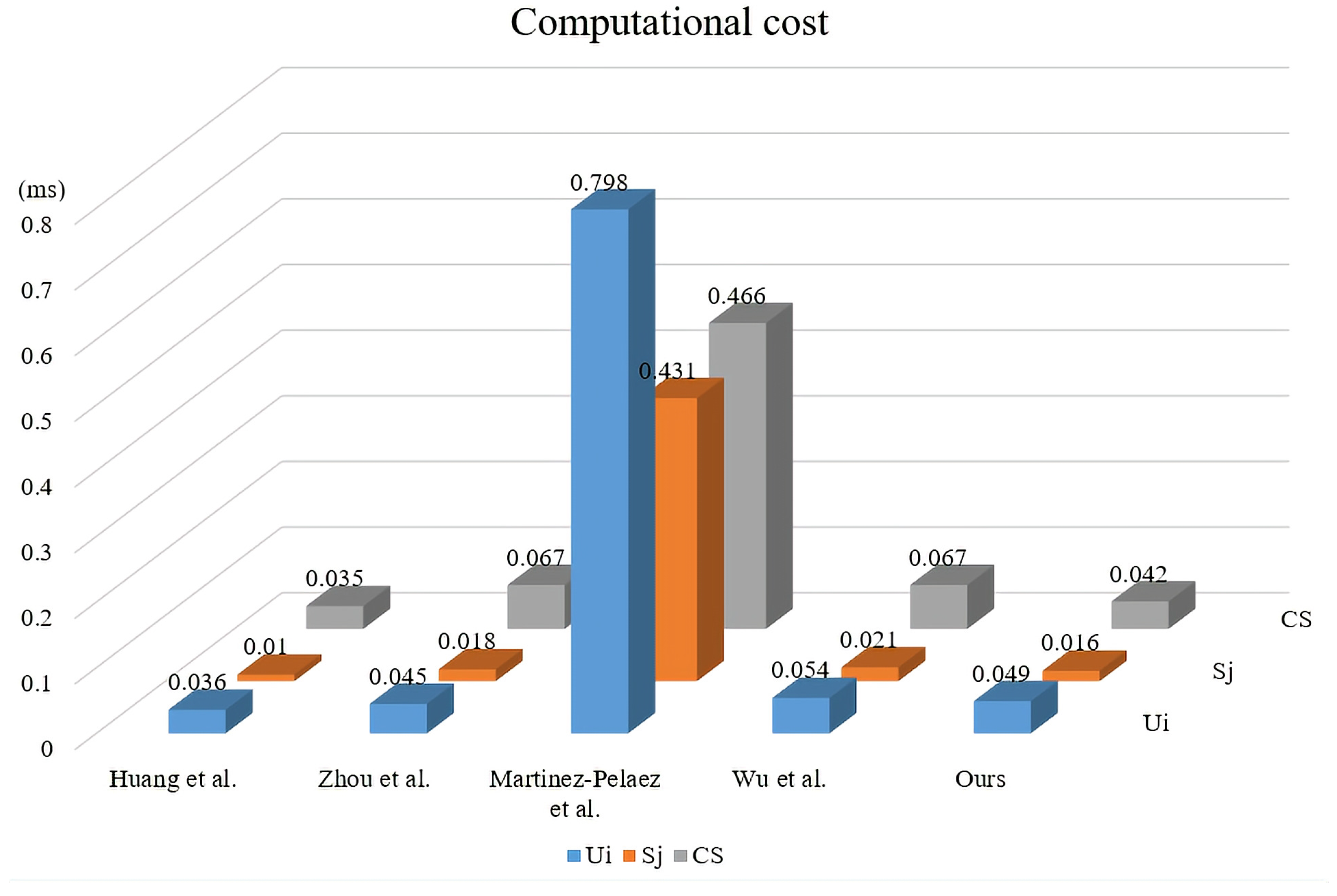
| Protocols | (ms) | (ms) | (ms) | Total (ms) |
|---|---|---|---|---|
| Huang et al. [13] | ≈ 0.036 | ≈ 0.010 | ≈ 0.035 | 0.081 |
| Zhou et al. [23] | ≈ 0.045 | ≈ 0.018 | ≈ 0.067 | 0.130 |
| Martinez-Pelaez et al. [24] | ≈ 0.798 | ≈ 0.431 | ≈ 0.466 | 1.695 |
| Wu et al. [40] | ≈ 0.054 | ≈ 0.021 | ≈ 0.067 | 0.142 |
| Ours | ≈ 0.049 | ≈ 0.016 | ≈ 0.042 | 0.107 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, T.-Y.; Wang, L.; Guo, X.; Chen, Y.-C.; Chu, S.-C. SAKAP: SGX-Based Authentication Key Agreement Protocol in IoT-Enabled Cloud Computing. Sustainability 2022, 14, 11054. https://doi.org/10.3390/su141711054
Wu T-Y, Wang L, Guo X, Chen Y-C, Chu S-C. SAKAP: SGX-Based Authentication Key Agreement Protocol in IoT-Enabled Cloud Computing. Sustainability. 2022; 14(17):11054. https://doi.org/10.3390/su141711054
Chicago/Turabian StyleWu, Tsu-Yang, Liyang Wang, Xinglan Guo, Yeh-Cheng Chen, and Shu-Chuan Chu. 2022. "SAKAP: SGX-Based Authentication Key Agreement Protocol in IoT-Enabled Cloud Computing" Sustainability 14, no. 17: 11054. https://doi.org/10.3390/su141711054
APA StyleWu, T.-Y., Wang, L., Guo, X., Chen, Y.-C., & Chu, S.-C. (2022). SAKAP: SGX-Based Authentication Key Agreement Protocol in IoT-Enabled Cloud Computing. Sustainability, 14(17), 11054. https://doi.org/10.3390/su141711054